Most enterprise buyers now expect proof of a working security program before they sign a contract. Without an operational Information Security Management System (ISMS) and continuous evidence, deals stall—even when teams think they're audit‑ready on paper. ISO 27001 has become the de‑facto international benchmark for information security. It defines how to build, operate and improve an ISMS, and it requires verifiable documentation. Companies selling into regulated sectors, especially healthcare and financial services, must show that their controls work over time and that they have the artefacts to prove it. In this piece, I draw on Konfirmity’s experience supporting more than 6,000 audits and over 25 years of combined expertise to show how an ISO 27001 Documentation Toolkit can help. We’ll demystify mandatory documents, show where toolkits fit into the audit journey, compare popular kits and outline a step‑by‑step approach to building a reliable ISMS.
What Is an ISO 27001 Documentation Toolkit?
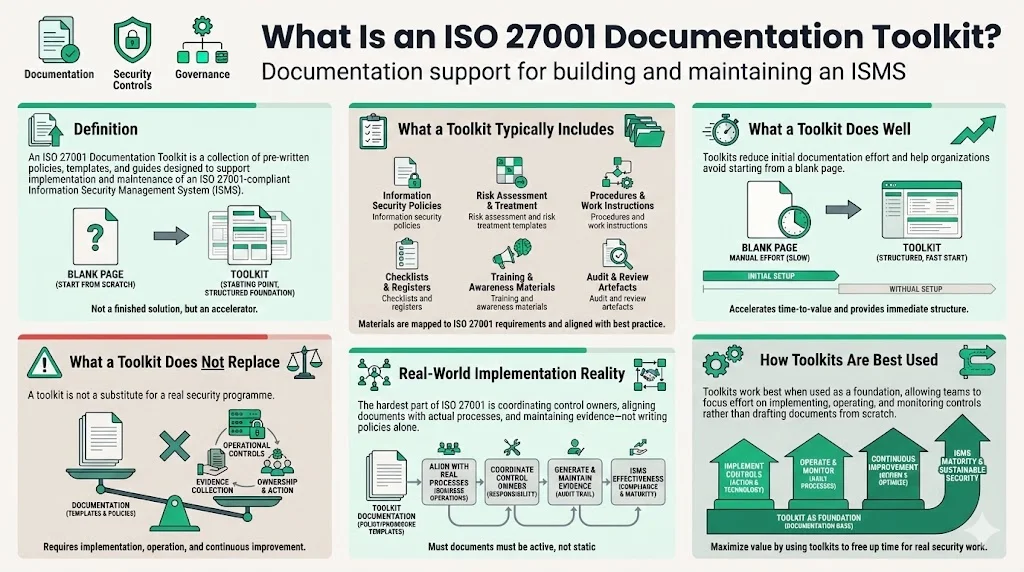
An ISO 27001 Documentation Toolkit is a pack of pre‑written documents, templates and guides designed to help organizations implement and maintain an ISMS that complies with ISO 27001. HighTable’s definition explains that a toolkit is a comprehensive collection of resources mapped to the ISO 27001 standard that “should include the mandatory policies and be pre‑populated with best practice”. Toolkits typically cover policies, procedures, risk assessments, checklists, training materials and other artefacts needed to run a secure programme. They are not a substitute for a proper security programme, but they can reduce the initial workload.
As Konfirmity’s delivery teams have seen across thousands of audits, what slows down ISO projects isn’t just writing policies—it’s orchestrating dozens of control owners, gathering evidence, and keeping documents aligned with real processes. Toolkits address the first part of that challenge: they give you a starting point for documentation so you can focus on implementing and operating controls.
Why Documentation Matters in ISO 27001
Documentation is a fundamental requirement of ISO 27001. The 2022 version of the standard lists multiple clauses where documentation or evidence is mandatory: the scope of the ISMS, the information security policy, risk assessment processes, risk treatment processes, information security objectives, evidence of competence, results of risk assessments and treatment, monitoring results, audit programmes and results, management reviews, and evidence of corrective actions. Annex A controls also call for documented policies and procedures, such as inventories of assets, acceptable use rules, information labelling, transfer rules, access control procedures and more. During an audit, an assessor asks to see how a control is designed (the policy), how it operates (the procedure) and where the evidence lives (logs, records). Missing or inconsistent documentation means non‑conformities that must be remediated.
Strong documentation also makes enterprise engagements smoother. Many procurement questionnaires, Business Associate Agreements (BAAs) and vendor security assessments look for concrete artefacts: access review records, risk assessments, third‑party due diligence reports, incident response playbooks and proof of training. Without these, deals can stall for weeks or months. Documentation establishes a single source of truth that aligns stakeholders across engineering, security, HR and legal. It also reduces operational drift: when processes are written down and updated, they are easier to follow and audit.
Failing to document controls can have direct financial consequences. IBM’s 2025 Cost of a Data Breach Report shows that the global average cost of a breach fell from USD 4.88 million in 2024 to USD 4.44 million in 2025, partly because organizations using security automation and AI reduced breach lifecycles by 80 days and saved nearly USD 1.9 million. In contrast, the United States saw breach costs rise to USD 10.22 million—the highest on record—due to regulatory fines and escalating detection costs. These figures underscore that ungoverned systems and undocumented processes lead to longer investigations, higher remediation costs and greater business disruption. 86 percent of organizations reported operational disruptions following a breach, and nearly half raised prices to offset the expense. A documented ISMS with clear incident response procedures and evidence management can shorten detection and recovery times, directly reducing the financial impact of incidents.
Key Components of an ISO 27001 Documentation Toolkit
A well‑rounded ISO 27001 Documentation Toolkit should contain templates that address mandatory ISO 27001 documents and provide the scaffolding for day‑to‑day operations. Below are common components and why they matter.
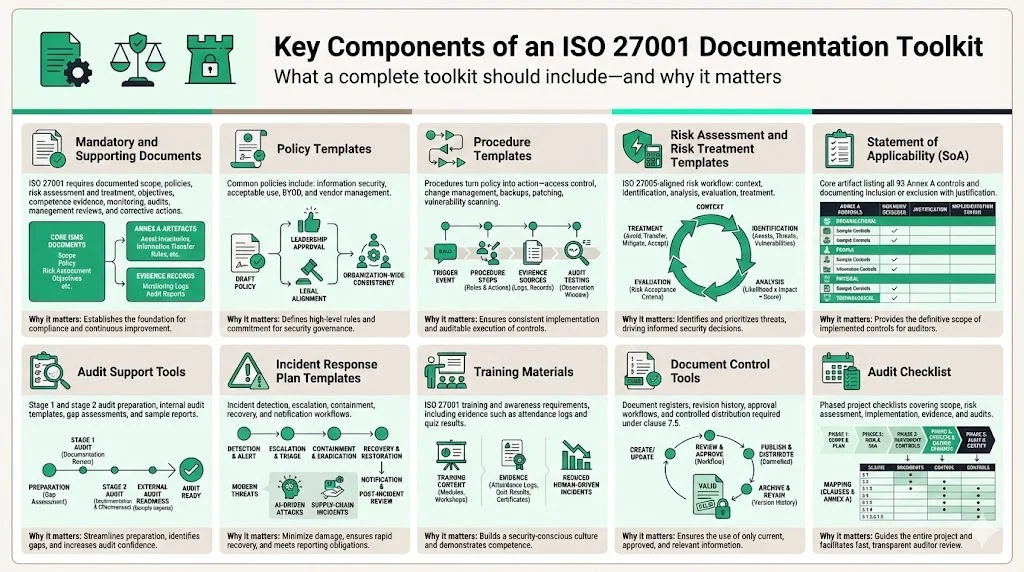
1. Mandatory and Supporting Documents
ISO 27001:2022 requires documentation for the scope of the ISMS, information security policies, risk assessment and treatment processes, objectives, evidence of competence, risk assessment results, risk treatment results, monitoring, audits, management reviews and corrective actions. Toolkits provide templates for these documents so you can document your context, leadership commitment, planning, support, operation, performance evaluation and improvement. Supporting documents, such as asset inventories, acceptable use rules and information transfer procedures, help satisfy Annex A controls.
2. Policy Templates
Policies set expectations and delegate authority. Common policies include:
- Information Security Policy: outlines the organisation’s security objectives, roles and responsibilities.
- Acceptable Use Policy: governs how employees use company systems, devices and data.
- Bring Your Own Device (BYOD) Policy: defines security requirements for personal devices.
- Vendor Management Policy: establishes criteria for selecting and monitoring third‑party providers.
A toolkit ensures these policies reference applicable laws (e.g., GDPR, HIPAA), align with your business context and incorporate leadership approval.
3. Procedure Templates
Procedures translate policies into actionable steps. Typical procedures include access control, user provisioning and de‑provisioning, change management, secure coding, backup and restoration, patch management and vulnerability scanning. Documented procedures should specify triggers, roles, inputs and outputs, and reference evidence sources (logs, tickets). When audits occur, reviewers will test whether the procedure is followed consistently across the observation window. Scytale’s SOC 2 guide notes that evidence collection and policy implementation during the pre‑audit phase is where a large portion of SOC 2 effort lies. ISO audits are similar: without detailed procedures and evidence, your controls cannot demonstrate effectiveness.
4. Risk Assessment and Risk Treatment Plan Templates
ISO 27005:2022, the risk management standard aligned with ISO 27001, introduced a five‑step process: context establishment, risk identification, risk analysis, risk evaluation and risk treatment. Modern toolkits supply templates and worksheets for each step, including asset lists, threat lists, vulnerability assessments, likelihood and impact scoring and risk treatment options. Secureframe’s overview of ISO 27005 notes that the 2022 revision consolidates 12 clauses and six annexes into 10 clauses and emphasises two approaches—event‑based and asset‑based risk identification. Toolkits should guide you through selecting a risk methodology and help draft your Statement of Applicability (SoA), which links each chosen control to specific risks and legal or contractual requirements.
5. Statement of Applicability (SoA)
The SoA is a core artifact in ISO 27001. It lists all 93 controls in Annex A and states whether each control is applicable to your organisation. The 2022 update condensed Annex A from 114 to 93 controls, grouped them into four categories—Organisational, People, Physical and Technological—and made Annex A controls mandatory as a starting point. The SoA explains why a control is included or excluded and references the risks it mitigates. A well‑designed toolkit provides a pre‑formatted SoA table and instructions for completion.
6. Audit Support Tools
ISO 27001 audits occur in two stages: stage 1 is a documentation review, and stage 2 is an implementation audit. Certification lasts three years and includes annual surveillance audits. Toolkits often include internal audit templates, checklists and sample audit reports so you can test your controls before engaging an external auditor. High‑quality kits also provide gap assessment tools to evaluate clauses and control coverage. CertiKit’s focus packs, for example, offer separate gap assessment, risk assessment and internal audit packs.
7. Incident Response Plan Templates
When breaches occur, fast and consistent action is critical. Incident response plans should define detection, escalation, communication, containment, eradication and recovery steps. They should also include data breach notification procedures to comply with laws such as GDPR and HIPAA. Toolkits that provide ready‑to‑use incident response templates enable you to respond within hours rather than days and provide evidence for auditors. Given the rise of AI‑driven attacks and shadow AI, IBM’s report warns that 97 percent of AI‑related breaches occur in organisations without proper AI access controls. A good incident plan should address AI risks, deepfake scenarios and supply‑chain compromise, ensuring you can identify and contain modern threats.
8. Training Materials
ISO 27001 clause 7.3 requires awareness and training. Without proof of employee training, auditors may issue non‑conformities. A robust toolkit includes slide decks, quizzes and tracking logs for security awareness training, acceptable use training and role‑specific briefings. Evidence may include attendance records, quiz scores and completion certificates. Continuous training reduces human‑driven incidents such as phishing, which overtook stolen credentials as the most common initial attack vector in 2025, responsible for 16 percent of breaches at an average cost of USD 4.8 million.
9. Document Control Tools
Document control is essential for versioning, approvals and distribution. Clause 7.5 of ISO 27001 requires that documented information be controlled and accessible to relevant people. Toolkits should include document registers, revision history logs and approval workflows. These logs help prove that documents were reviewed and approved by authorised personnel and that only the latest versions are in use.
10. Audit Checklist
An audit checklist ensures you have covered all clauses and controls. For example, Scytale’s SOC 2 timeline table shows that a Type II audit includes pre‑audit preparation (1–3 months), an observation period (3–12 months), the official audit (1–3 weeks) and report creation (2–6 weeks). Similarly, ISO 27001 projects benefit from a phased checklist that covers scope definition, risk assessment, control implementation, evidence collection and internal audit. An audit checklist from your toolkit should map documents to ISO clauses and Annex A controls so you can quickly demonstrate conformity.
Step‑by‑Step Walkthrough: Using the Toolkit
Konfirmity recommends the following seven‑step approach to implementing an ISMS using a toolkit. This approach draws from our experience delivering thousands of audits and aligns with ISO 27001 requirements.
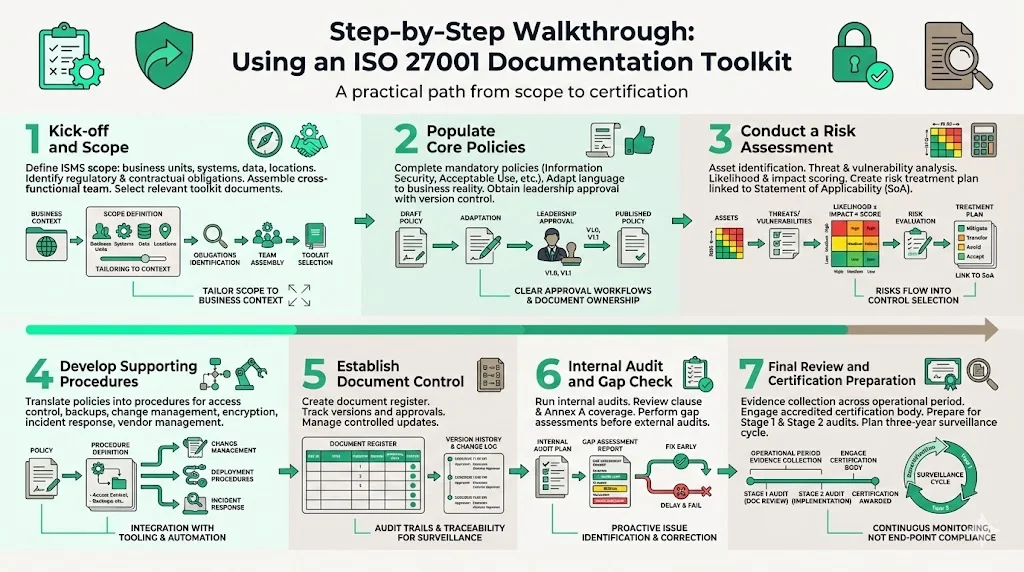
Step 1: Kick‑off and Scope
- Define your ISMS scope: Identify business units, systems, data types and locations that fall within the ISMS. Consider contractual obligations (e.g., BAAs, DPAs) and regulatory requirements (e.g., HIPAA, GDPR, CMMC). ISO 27001 clause 4 emphasises context and stakeholder expectations.
- Assemble your project team: Include representatives from security, engineering, HR, legal and operations. Assign an executive sponsor to ensure resourcing.
- Select relevant documents: Review your toolkit and decide which templates are applicable to your scope. Small SaaS providers may not need every form that a global enterprise uses; advisera’s toolkit acknowledges that its documents are tailored for smaller businesses and exclude unnecessary documents.
Step 2: Populate Core Policies
- Fill out mandatory policies: Use the Information Security Policy, Acceptable Use Policy and other core policy templates to capture your company’s objectives, roles and responsibilities. Adapt the language to match your culture and regulatory environment. Use the AI wizards in your toolkit (if available) to insert company name, logos and job titles.
- Get approvals: Route policies through legal and leadership for approval. Document approval dates and maintain version histories.
Step 3: Conduct a Risk Assessment
- Identify assets and threats: Use the risk assessment templates to list assets (applications, infrastructure, data), threats (cyberattack, insider threat, natural disaster) and vulnerabilities (unpatched systems, misconfigurations).
- Analyse risks: Evaluate likelihood and impact. ISO 27005:2022 introduces a semi‑quantitative approach combining qualitative and quantitative methods.
- Draft the risk treatment plan: Decide whether to mitigate, avoid, transfer or accept each risk. Document owners and deadlines. Include your Statement of Applicability to link controls to risks.
Step 4: Develop Supporting Procedures
- Operationalise policies: Write procedures for access control, backup, change management, encryption, incident response and vendor management. Include steps, triggers, roles and evidence requirements.
- Align with tooling: Ensure procedures integrate with your existing systems—ticketing platforms (e.g., JIRA), configuration management (e.g., Terraform), CI/CD pipelines and logging tools. For example, least‑privilege access reviews can be automated to run quarterly, with results exported as evidence.
Step 5: Establish Document Control
- Set up a document register: Track documents, versions, owners, approval dates and distribution lists. Use your toolkit’s document control templates.
- Implement change control: When policies or procedures change, update the register, communicate changes to stakeholders and archive old versions. This is critical during surveillance audits to show a clear audit trail.
Step 6: Internal Audit and Gap Check
- Conduct an internal audit: Use the audit checklist and templates from your toolkit to review clause coverage and control effectiveness. Identify gaps and remediate them before external auditors arrive. AuditBoard’s readiness guide emphasises that stage 1 of the ISO 27001 audit is a documentation review. Fixing documentation gaps early prevents delays.
- Perform a gap assessment: Compare your documentation and controls to ISO 27001 clauses and Annex A controls. CertiKit’s gap assessment pack is an example of a tool that helps prioritise remediation.
Step 7: Final Review and Certification Preparation
- Evidence collection: Ensure that logs, tickets, training records and incident reports are stored securely and mapped to the relevant controls. For SOC 2, Scytale notes that the observation period lasts 3–12 months and that only controls active during this period are evaluated. ISO audits follow a similar principle: evidence must cover your operational period.
- Engage a certification body: After the internal audit, engage an accredited certification body for stage 1 and stage 2 audits. Your toolkit should help you prepare a documentation package and audit trail.
- Plan for surveillance audits: Certification is valid for three years, with surveillance audits typically in years 1 and 2. Schedule these audits and maintain continuous monitoring to remain compliant.
Comparing Popular ISO 27001 Documentation Toolkits
Below is a high‑level comparison of three widely used toolkits based on publicly available information.
In practice, the choice depends on your organisation’s size, internal expertise and budget. Large enterprises may need to customize templates heavily and integrate them with existing control frameworks such as SOC 2, HIPAA or GDPR. Smaller companies may prioritise speed and ease of use. Regardless of the provider, ensure the toolkit is updated for ISO 27001:2022 and that it includes both document templates and risk assessment tools.
How to Choose Between Toolkits
When selecting a toolkit, consider the following criteria:
- Template Coverage: Does the toolkit include all mandatory ISO 27001 documents and Annex A controls? CertiKit’s 215+ templates provide broad coverage, while Advisera focuses on around 45 core documents.
- Support Materials: Look for guidance notes, implementation guides and video tutorials. Toolkits with builtin AI wizards or wizards that insert company‑specific information can accelerate the process.
- Ease of Use: Consider how documents are organised and whether there are instructions for next steps. Step‑by‑step folder structures and wizards reduce confusion.
- Training Materials: Verify that the kit includes training slides, quizzes and tracking tools for awareness programmes. Training evidence is a common audit requirement.
- Pricing and Licensing: Compare one‑time purchase versus subscription. CertiKit offers a perpetual licence with no subscription; Advisera and HighTable may have different tiers. Check whether support hours are included.
- Update Frequency: ISO 27001 evolves. AuditBoard’s guide notes that ISO updates occur every four to five years and that another version may appear in the next two years. Ensure your provider commits to updating templates accordingly.
- Integration with Other Frameworks: If you are also pursuing SOC 2, HIPAA or GDPR, look for toolkits that map controls across frameworks. This reduces duplicate work.
Best Practices for Documentation in Enterprise Environments
Implementing ISO 27001 in an enterprise context requires more than filling in templates. Below are field‑tested practices from Konfirmity’s delivery work:
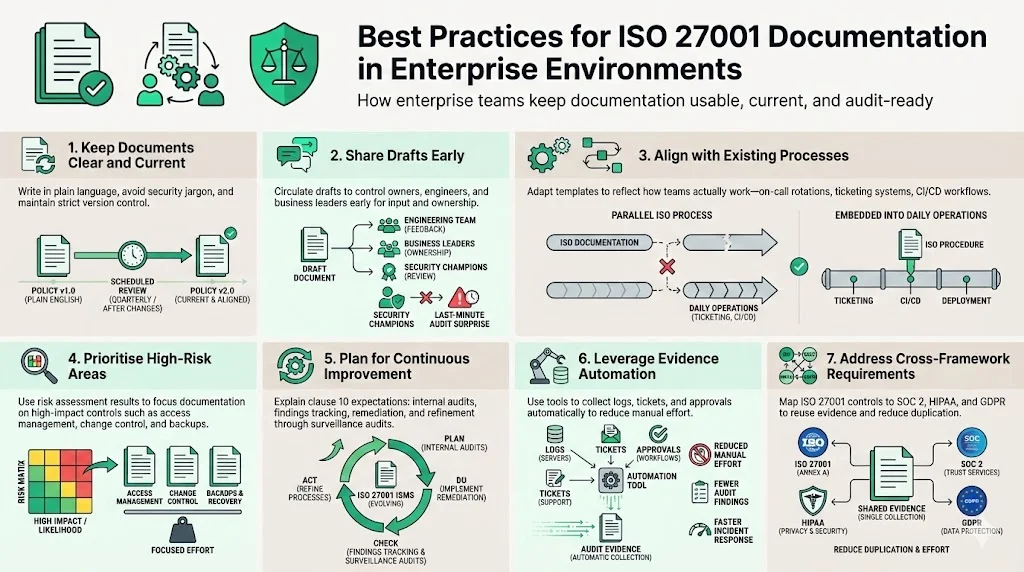
- Keep Documents Clear and Current: Write in plain language. Avoid jargon that non‑security stakeholders will misunderstand. Use version control and review documents quarterly or after major changes.
- Share Drafts Early: Circulate draft policies and procedures to control owners, engineers and business leaders. Early feedback prevents last‑minute surprises. Encourage security champions in each team to own specific policies.
- Align with Existing Processes: Don’t create parallel processes just for ISO 27001. Adapt templates to reflect how your teams actually work (e.g., integrate incident response with your existing on‑call rotation and ticketing system). Controls without real ownership fail under pressure.
- Prioritise High‑Risk Areas: Focus first on controls that mitigate the most significant risks, such as access control, change management and backup. Use risk assessment results to guide documentation priorities.
- Plan for Continuous Improvement: ISO 27001 clause 10 emphasises improvement. Schedule regular internal audits, track findings and remediate quickly. Use the surveillance audits as an opportunity to refine processes.
- Leverage Evidence Automation: Use tools that automatically collect evidence (logs, tickets, approvals). IBM’s report shows that automation reduces breach lifecycle and costs. In Konfirmity’s experience, automated evidence collection cuts manual effort by up to 75 percent and reduces audit findings.
- Address Cross‑Framework Requirements: Many enterprise buyers ask for SOC 2, HIPAA and GDPR assurance. Map ISO 27001 controls SOC 2’s Trust Services Criteria and HIPAA's administrative, physical and technical safeguards. Reuse evidence across frameworks whenever possible.
Conclusion
An effective security programme starts with secure design and ends with reliable documentation. ISO 27001 provides the blueprint, but organisations still need to build controls inside their own stacks, collect evidence and keep it current. A well‑designed ISO 27001 Documentation Toolkit accelerates the documentation process by providing pre‑written policies, procedures, risk assessment tools and audit checklists. Toolkits from Advisera, CertiKit and HighTable offer different mixes of templates, guidance and support—choose based on your size, budget and integration needs. Even with a toolkit, success hinges on implementing controls, training people and operating the programme daily.
Konfirmity’s managed service model complements toolkits by embedding our team into your environment. We design and implement controls across frameworks (ISO 27001, SOC 2, HIPAA, GDPR), collect evidence automatically, monitor continuously and support audits year‑round. Our clients typically achieve SOC 2 Type II readiness in 4–5 months versus 9–12 months when self‑managed, and they reduce internal effort from 550–600 hours to under 75 hours per year. By combining human‑led programme design with the right documentation toolkit, you start with security and arrive at compliance.
FAQ
Q1. What is included in an ISO 27001 Documentation Toolkit?
Most toolkits include mandatory policy and procedure templates (e.g., Information Security Policy, risk assessment process), risk registers, Statement of Applicability tables, SoA templates, incident response plans, training materials, document registers and audit checklists. CertiKit’s toolkit, for example, offers more than 215 template documents plus guidance and support.
Q2. How does a toolkit support the risk assessment process?
Toolkits aligned with ISO 27005 provide worksheets for asset lists, threat and vulnerability identification, risk scoring and treatment planning. The 2022 update to ISO 27005 consolidates risk management into five steps—context establishment, risk identification, risk analysis, risk evaluation and treatment. Templates walk you through each step and link to the SoA.
Q3. Can I use the toolkit for ISO 27001 certification?
Yes. When documentation is complete and reflects your actual controls, toolkits help you meet the mandatory document requirements and Annex A controls. However, you must still implement and operate controls. External auditors will test both design and effectiveness.
Q4. Do toolkits come with training materials?
Many do. Advisera’s toolkit includes awareness training materials and video tutorials. CertiKit also offers cyber awareness training as a complementary product. Training evidence is essential for audit readiness.
Q5. Are document templates customizable?
Most toolkits are fully editable. Advisera’s documents are 90 percent pre‑written and include placeholders for company‑specific information. CertiKit’s templates are in Microsoft 365 format and can be tailored to your branding. HighTable emphasises that toolkits provide a starting point but must be adapted to your context.





.svg)





.svg)
.svg)