Large clients now ask tough questions before they commit to a vendor. They ask how data is protected, who can access it, and how often controls are tested. Without a credible track record, deals stall. IBM’s 2025 breach report shows that the global average cost of a breach is about $4.44 million while the U.S. average is $10.22 million, a reminder that security lapses carry real price tags. In this environment, SOC 2 Evidence Collection Templates have become a practical tool for demonstrating operational security. By organising logs, approvals, and test results into a structured format, vendors can satisfy auditors and procurement committees. This article draws on Konfirmity’s experience supporting more than 6 000 audits over 25 years. It offers actionable guidance for security and engineering leaders who need to deliver continuous evidence rather than one‑off reports.
Why evidence programs are a sales enabler
A credible evidence program connects day‑to‑day operations to the promises made in policies. When evidence is scattered across personal drives or remembered only by individual team members, producing proof during an audit becomes a mad scramble. The Cogent compliance guide warns that the era of scrambling for logs, screenshots and scattered evidence at the last minute is over—customers, regulators and auditors expect continuous assurance. Teams that fail to provide ongoing proof risk regulatory fines and lost deals. Advantage Partners points out that documenting everything—logs, screenshots, reports and training records—in a central location makes the audit easier and faster. Centralised evidence not only helps auditors but also supports internal governance by ensuring control owners know where to find proof.
Evidence is more than a bureaucratic burden; it is a requirement for entering enterprise markets. Procurement questionnaires often include dozens of security and privacy questions. If a vendor can’t supply recent access review reports, vulnerability scan results or incident response logs, the buyer may walk away. Thus, building a disciplined evidence program is not a nice‑to‑have; it is a competitive necessity. SOC 2 Evidence Collection Templates provide that structure by mapping each control to specific artifacts and owners.
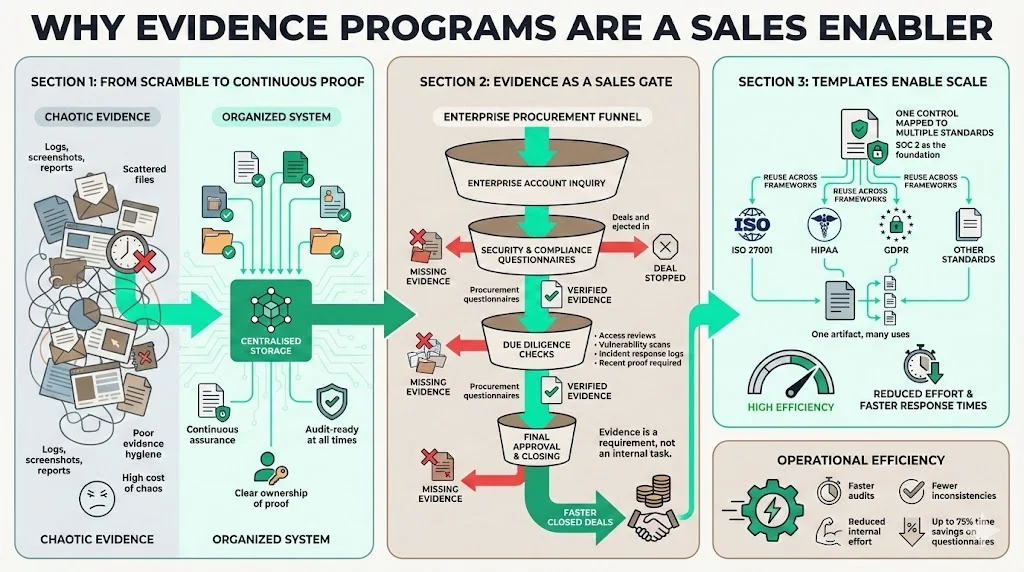
Enterprise buyers often require proof of compliance with ISO 27001, HIPAA and GDPR in addition to SOC 2. Without a unified evidence program, teams must prepare separate packages for each standard, increasing workload and the chance of inconsistencies. By basing documentation on SOC 2 Evidence Collection Templates and mapping each control to multiple frameworks, organisations can reuse artifacts and streamline due diligence. In Konfirmity’s work, procurement questionnaires frequently include more than five hundred security and privacy questions, ranging from encryption settings to vendor risk management. A central template helps teams respond quickly, reducing internal effort by up to seventy‑five percent.
What is SOC 2 evidence collection?
SOC 2 is an attestation framework overseen by the American Institute of Certified Public Accountants. It evaluates how well a service provider meets the Trust Services Criteria: Security, Availability, Processing Integrity, Confidentiality and Privacy. Evidence collection in this framework refers to gathering artifacts—logs, screenshots, reports, approvals, test results—that prove each control is both designed and operating as intended. Evidence is distinct from general documentation. A policy might say that all administrative access requires multi‑factor authentication; evidence includes a screenshot of the identity provider showing MFA settings enabled for each administrator and the records of quarterly access reviews. For change management, evidence could comprise pull request approvals, pipeline logs and risk analysis notes.
Another reason evidence collection matters is the difference between Type I and Type II attestation. A Type I report focuses on the design of controls at a specific point in time. Evidence mainly comprises policies, procedures and limited samples to show controls are designed properly. A Type II report, on the other hand, tests how controls operate over an observation period—usually three to twelve months. Auditors expect to see continuous evidence that controls functioned correctly throughout the period. Without continuous collection, teams may face gaps they can’t fill retroactively. SOC 2 Evidence Collection Templates help by prompting teams to record data at regular intervals so they are ready for both Type I and Type II audits.
Type II reports require logs and artifacts that show controls operated correctly week after week. For example, a password rotation control must provide records for each rotation event across the period, and a vulnerability management control should produce monthly scan results and remediation tickets. Auditors use these artifacts to confirm that the controls were not merely designed but were working throughout the period. Without such continuous evidence, reports may be delayed or qualified.
Why organised evidence matters
Evidence underpins three pillars of a compliance program: internal controls, policy adherence and risk management. A well‑structured evidence portfolio shows that employees follow defined procedures, that technical controls like access restrictions and encryption work as advertised, and that risks are identified and mitigated. Typical audit documentation includes screenshots of system settings, audit logs, policy documents, risk assessment reports and control testing results. These artifacts allow auditors to trace events back to specific controls and verify that processes were executed.
The risk of missing or disorganised evidence is significant. Cogent’s audit readiness guide notes that common pitfalls include incomplete evidence such as missing logs, access records or policies, manual error‑prone processes and delayed reporting. These issues lead to higher audit costs, longer timelines and credibility loss. Conversely, a central evidence repository with version control and time‑stamps makes it easier to retrieve documents and defend their integrity. SOC 2 Evidence Collection Templates encourage teams to capture evidence promptly and store it in a single location, reducing the risk of missing data.
Core components of SOC 2 evidence
The evidence required for a SOC 2 audit can be grouped into four main categories: control testing, compliance documentation, risk assessment and security control validation.
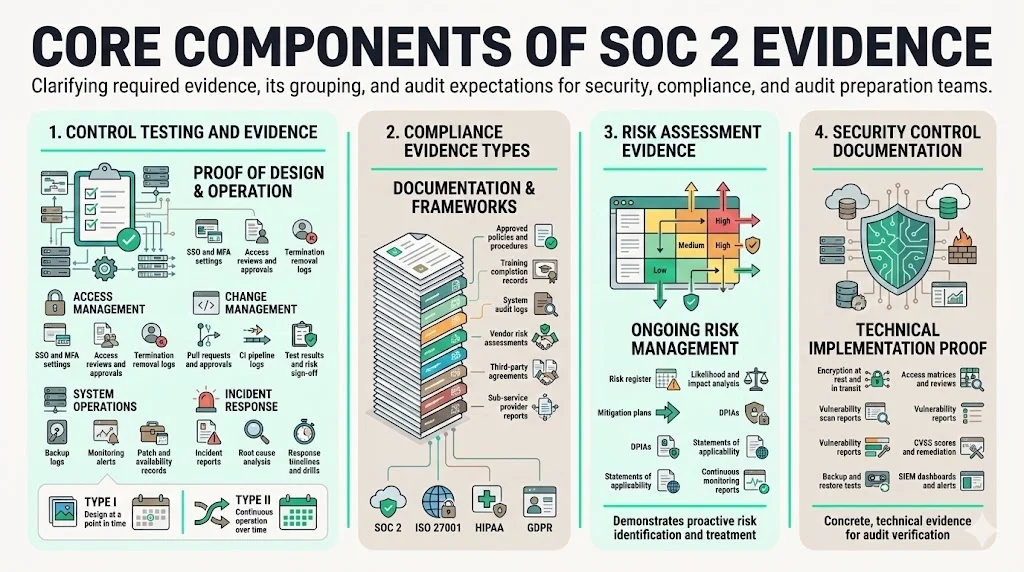
1. Control testing and evidence
Auditors want proof that security controls are both designed and functioning effectively. For each control, teams should collect design documents (policies, diagrams), configuration evidence (screenshots, configuration files), and operational evidence (logs, approvals, test results). The AuditBoard checklist explains that Type I audits focus on design at a point in time, while Type II audits test control execution over a period. That means teams must produce continuous logs and activity records for Type II. For example:
- Access management: Provide identity provider settings showing single sign‑on with multi‑factor authentication for all administrators, access review records and sign‑off evidence. Include logs demonstrating that terminated employees were removed promptly.
- Change management: Compile pull request records, approval workflows, pipeline logs and test results to show that each change was reviewed and tested before deployment. Include risk analyses for high‑risk changes and sign‑off from appropriate stakeholders.
- System operations: Maintain logs of backups, monitoring alerts and system performance. Show that patches were applied and that service availability met service commitments.
- Incident response: Gather incident reports, root cause analyses and post‑incident drills. Evidence should show that incidents were detected, escalated and resolved within defined service agreements.
2. Compliance evidence types
Compliance evidence covers policies, procedures and supporting documents that show how the organisation meets frameworks such as SOC 2, ISO 27001, HIPAA and GDPR. Examples include:
- Typical compliance evidence: Approved policies and procedures covering information security, change management, vendor management, business continuity, privacy and data retention; system audit logs capturing access and configuration events across the observation period; training completion records; and third‑party documentation such as vendor risk assessments, business associate agreements, data processing agreements and sub‑service provider reports.
3. Risk assessment evidence
Risk assessments are the foundation of a risk‑based compliance program. Evidence should show that management identifies, analyses and addresses risks on a regular basis. Artifacts may include risk registers describing threats, likelihood and impact; mitigation plans outlining corrective actions; documentation such as DPIAs for GDPR and statements of applicability for ISO 27001; and continuous monitoring reports summarising scans, tests and remediation.
4. Security control documentation
Evidence of security controls proves that technical safeguards are implemented. Typical control evidence includes proof of encryption at rest and in transit; access matrices and quarterly review logs demonstrating least privilege; vulnerability scan reports with CVSS scores and remediation status; backup job logs and restore tests; and logging or monitoring artifacts such as SIEM dashboards and alert tickets.
Building SOC 2 evidence collection templates
A SOC 2 Evidence Collection Template is a structured tool that helps teams track what artifacts are needed for each control. A typical template includes the following fields:
- Control: The name or identifier of the control, such as CC6.1 for logical access controls or CC8.1 for change management.
- Description: A short description of the purpose of the control.
- Control owner: The person or team responsible for executing the control.
- Evidence type: Category of evidence (policy, procedure, log, report, screenshot).
- Artifact location: Where the evidence is stored (file path, link to repository or compliance platform).
- Date collected: When the evidence was captured, to support observation period requirements.
- Comments: Any context or cross‑references to frameworks (e.g., “maps to GDPR Article 32”).
- Audit status: Flags indicating whether the evidence has been reviewed and approved by the compliance team or auditor.
These templates connect each control with the necessary artifacts and owners, making it clear who is responsible for collecting and updating evidence. They also serve as a single source of truth during audits, enabling auditors to find information quickly. By including dates and locations, templates help satisfy the requirement for continuous evidence across the observation period.
Examples of evidence fields
Common entries include policy attachments, monitoring logs, risk assessment outputs, testing results and change management records. For each item, record the location and date and cross‑reference the relevant controls.
Customising templates for busy teams
Teams often struggle to keep templates up to date because they are either too complex or not tailored to their systems. To make these templates workable:
- Keep them simple: Use concise fields and avoid unnecessary categories. The goal is to capture essential information without creating extra work. For example, a column for “evidence type” can have standard values (policy, log, report) instead of free text.
- Reuse across frameworks: Map controls across SOC 2, ISO 27001 and HIPAA. If a control addresses multi‑factor authentication, mark that it also satisfies GDPR Article 32 and HIPAA 164.308(a)(4). Cross‑mapping reduces duplication and ensures that evidence collected once can serve multiple attestations.
- Automate population: Where possible, use compliance platforms or scripts to pull logs, configuration snapshots and ticketing records directly into the template. The Cogent guide recommends automating evidence collection through dashboards that capture logs, configurations and access records continuously.
- Review quarterly: Schedule periodic reviews to update the template, archive outdated evidence and confirm that control owners are capturing new artifacts. This rhythm supports the three‑ to twelve‑month observation window of SOC 2.
Best practices for evidence gathering
A strong evidence program does not rely on a scramble at audit time. It integrates evidence collection into daily operations. Using such templates as part of routine tasks ensures that artifacts are captured consistently. The following practices support year‑round readiness.
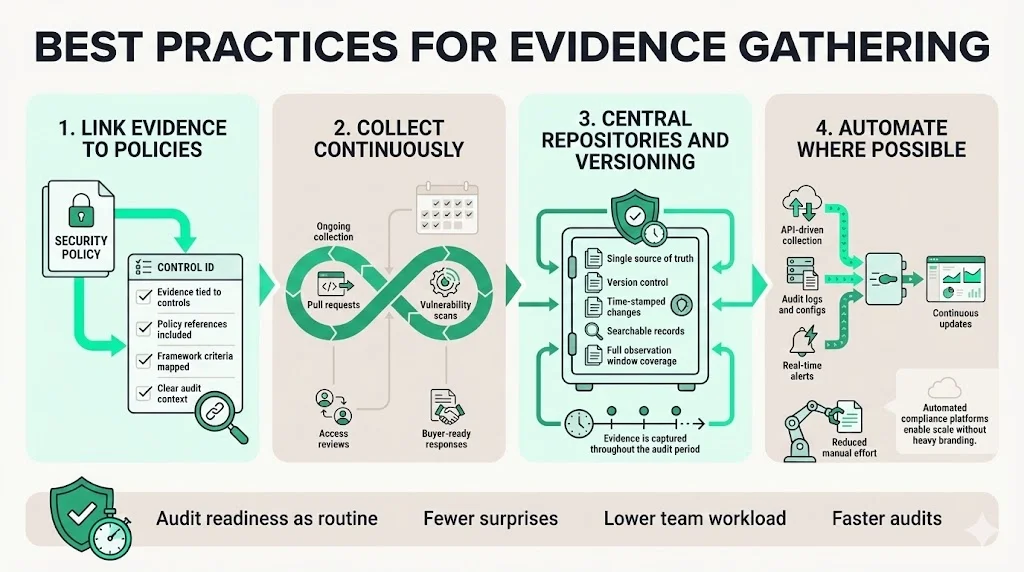
1. Link evidence to policies
Tie each control’s evidence to the relevant policy and framework requirement. For example, a quarterly access review record should cite the Access Management Policy and the Trust Services Criterion it supports. This helps auditors understand the purpose of the evidence.
2. Collect continuously
Waiting until the end of the observation window invites gaps. Build evidence collection into routine tasks—link pull‑request approvals and vulnerability scan reports to your template as they occur. Collect data regularly to prevent surprises and enable quick responses to buyer questionnaires.
3. Use central repositories and versioning
Keep evidence in a central, auditable repository with version control and search. Time‑stamp changes and use consistent file names so auditors can trace actions across the observation period.
4. Automate where possible
Manual collection is slow and error‑prone. Automated tools can pull audit logs, configuration snapshots and access events. The Cogent guide emphasises API‑driven data feeds, real‑time alerts and audit‑ready reporting. Platforms like Drata and Vanta collect and update evidence automatically across cloud services, send alerts for policy violations and maintain dashboards for auditors and executives. Automation reduces the workload on security teams and ensures that evidence is captured consistently. By following these practices and using SOC 2 Evidence Collection Templates, teams can streamline evidence management and make audit readiness a routine part of operations.
Templates in action
To illustrate how such templates work, consider two approaches: static spreadsheets and automated systems.
Static templates (spreadsheets)
Spreadsheets offer a flexible, low‑cost way to list controls, required evidence and status. They work for small environments but rely on manual updates—if owners forget to upload logs or approvals, gaps appear. Schedule regular reviews and enforce naming conventions to keep spreadsheets manageable.
Automation tools
Compliance platforms like Drata, Vanta and Wiz pull logs, configurations and access data directly from cloud services and automatically update evidence and alerts. They reduce manual work and speed audits but still require proper configuration and human oversight to define policies and handle exceptions. A balanced approach combines automation with expert guidance.
Integrating control testing outputs
Modern DevOps and security operations produce a wealth of data. Integrating these outputs into your templates ensures nothing falls through the cracks. Examples include:
- CI/CD pipelines: Capture deployment logs, security checks and configuration change records as audit artifacts.
- Vulnerability scanners: Feed scan results and ticket status into the template. Include severity ratings and remediation deadlines.
- Access reviews: Pull identity governance reports that show who has access, when reviews were performed and what changes were made.
- Incident management: Link incident tickets, root cause analysis documents and post‑incident drill reports to the relevant controls.
Integrating these outputs reduces manual effort and ensures that evidence is tied directly to operational workflows. It also promotes continuous improvement; recurring issues become visible in the template, prompting process changes or control enhancements.
Staying audit‑ready throughout the year
SOC 2 is an ongoing process. Self‑managed programs often run nine to twelve months and consume more than 550 internal hours, whereas Konfirmity often delivers readiness in four to five months with about 75 hours of client effort. Stay audit‑ready by reviewing controls and risk registers quarterly, scheduling scans and drills ahead of the audit period, and keeping vendor documentation current. Maintain communication with auditors and update your evidence templates regularly. Year‑round readiness smooths audits and accelerates sales because buyers can see proof of compliance at any time. These templates support this by making continuous evidence management manageable.
Common Challenges in SOC 2 Evidence Collection
- Missing logs or policies
- Disorganised repositories without version control
- Mismatches between evidence and policies
- Overreliance on automation without human oversight
- Change fatigue due to frequent control updates
- Failing to use SOC 2 Evidence Collection Templates (leading to missing or misaligned artifacts and delays)
Strategies to Address Challenges
- Assign clear ownership.
- Centralise evidence storage.
- Maintain a cross-reference matrix.
- Combine automation with expertise.
- Build institutional memory.
Conclusion
Evidence is the bridge between intention and assurance. In 2025, enterprise buyers and regulators expect continuous proof that vendors protect data, monitor controls and respond to incidents. SOC 2 Evidence Collection Templates transform evidence from a scattered set of documents into a structured system that supports security, compliance and sales. By mapping controls to artifacts, assigning owners and scheduling regular updates, teams reduce audit friction and demonstrate operational maturity. When combined with automation and expert guidance, templates cut readiness timelines from nine months to four, save hundreds of hours, and lower the risk of findings. Security that appears solid on paper but collapses during an incident is a liability. Build controls that work, record evidence as you operate, and let compliance follow.
Frequently asked questions
1. What is SOC 2 evidence collection?
It is the process of gathering audit‑ready artifacts—logs, screenshots, policies, procedures, approvals and test results—that prove each control is designed and operating effectively according to the SOC 2 Trust Services Criteria. Evidence collection supports attestation and builds trust with customers and auditors.
2. What types of evidence are required for SOC 2?
Auditors usually request policies and procedures, audit logs, access review records, change management records, vulnerability and incident reports, risk assessments, training records, and proof of vendor diligence. Evidence must show both the design and the operation of controls.
3. How often should SOC 2 evidence be collected?
Evidence should be collected continuously or at defined intervals (e.g., weekly or monthly) throughout the audit observation period. Waiting until the end leads to gaps that can’t be filled. Continuous collection makes audits smoother and reduces the risk of findings.
4. Can SOC 2 evidence be automated?
Yes. Compliance platforms such as Drata, Vanta and Wiz automatically collect logs, configurations and access events across cloud services, send alerts for violations and maintain dashboards. Automation reduces manual effort but still requires oversight and correct configuration.
5. What happens if evidence is missing during an audit?
Auditors may flag the gap, which can delay the report or result in findings that require remediation. Missing evidence also erodes buyer trust and may jeopardize deals. A structured template, central repository and continuous collection help avoid these outcomes.





.svg)





.svg)
.svg)