Most enterprise buyers now ask for proof of operational security before they will sign a contract. In healthcare, it goes even further. Regulators in the United States enforce the Health Insurance Portability and Accountability Act (HIPAA), and the rules set expectations for how laptops, tablets, and connected devices must be secured. Failing to meet those expectations disrupts care, delays sales, and exposes providers to reputational harm. HIPAA Endpoint Security For HIPAA should therefore be more than a checkbox. It’s about creating lasting safeguards around electronic protected health information (ePHI) and being able to show auditors and buyers the evidence. This article explains what the HIPAA Security Rule expects, why unmanaged devices are risky, and how a managed program combines encryption, access controls, monitoring, and training to reduce incidents.
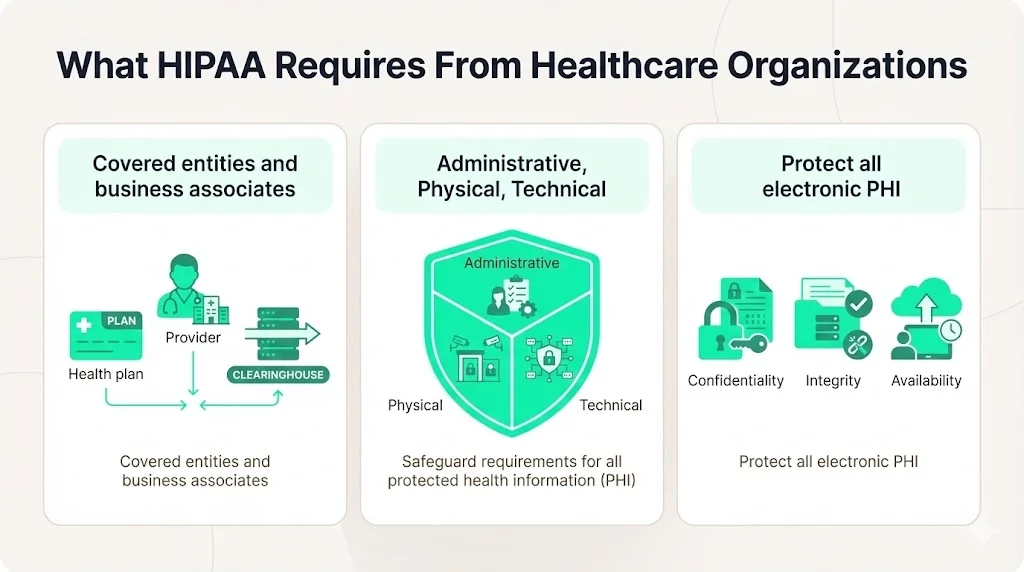
What HIPAA Requires From Healthcare Organizations
The HIPAA Security Rule sets a national baseline for protecting ePHI. It applies to covered entities (health plans, providers, and clearinghouses) and their business associates and requires a mix of administrative, physical, and technical safeguards. These safeguards aim to ensure the confidentiality, integrity, and availability of all ePHI that organizations create, receive, maintain, or transmit. Administratively, the rule expects a security management process, assigned responsibilities, workforce security, information access management, training, incident procedures, contingency planning, and ongoing evaluation. Physical safeguards control facility access and workstation/device security, while technical safeguards deal with access controls, audit controls, authentication, integrity, and transmission security.
HIPAA is intentionally technology‑neutral. The rule doesn’t dictate specific products but requires organizations to select controls appropriate for their size, complexity, and risk exposure. NIST Special Publication 800‑66 revision 2 echoes this flexibility, explaining that regulated entities must protect ePHI against reasonably anticipated threats, hazards, and impermissible uses or disclosures and adjust their controls as threats change. This guidance highlights that laptops, mobile devices, and Internet‑of‑Things (IoT) medical equipment can store, process, or transmit ePHI and that mobile devices and apps pose greater risks due to theft or loss.
What Counts as an Endpoint in Healthcare
An endpoint is any device that connects to a network. Compliancy Group explains that endpoints include laptops, smartphones, tablets, servers, and anything else that links to internal systems. In healthcare this list grows to include medical devices (infusion pumps, portable imaging systems), remote access terminals in home healthcare settings, and even voice assistants if they capture patient information. NIST points out that IoT devices used in healthcare often hold ePHI and therefore must be considered in risk assessments.
Unmanaged endpoints raise data protection risks because they multiply the places where data resides. Every laptop, mobile app, and USB drive becomes a possible entry point for attackers or a source of loss if the device is stolen. HIPAA settlement history shows the consequences. In 2019 the U.S. Department of Health and Human Services Office for Civil Rights (OCR) imposed a $3 million penalty on the University of Rochester Medical Center after an unencrypted laptop and USB drive containing information on 43 patients were lost. OCR stressed that repeated failure to encrypt mobile devices was unacceptable. Those incidents make it clear: ignoring endpoints can lead to financial penalties, corrective action plans, and reputational damage.
Why Endpoint Security Matters for HIPAA Compliance
The HIPAA Security Rule aims to protect ePHI wherever it exists. If laptops or tablets that store ePHI are not encrypted, a thief can read the data. If a physician uses personal email to send lab results, the information might transit unprotected. If a remote worker’s home network lacks strong passwords, attackers may pivot into a hospital’s network. As threats evolve, endpoint security becomes the frontline defense.
Healthcare is a prime target for cybercrime because patient records are rich with personal and financial data. HIPAA Journal reports that the average cost of a healthcare data breach in the United States fell in 2025 but still averaged $7.42 million, the highest across all industries. Breaches also take longer to identify and contain in healthcare—an average of 279 days, five weeks longer than the global average. Detection and escalation ($1.47 million), lost business ($1.38 million), and post‑breach response ($1.2 million) are the largest cost components. Those costs dwarf the investment required to secure devices. A single lost laptop—such as the case cited by OCR—can trigger millions in fines.
HIPAA Endpoint Security For HIPAA supports patient trust and legal obligations. It ensures that devices storing ePHI have proper controls (encryption, authentication, remote wipe) and that organizations can demonstrate compliance through documented policies and evidence. When enterprise customers ask for assurance that their data will be safe, the ability to point to a managed endpoint security program can accelerate due‑diligence processes.
Risks Facing Healthcare Endpoints
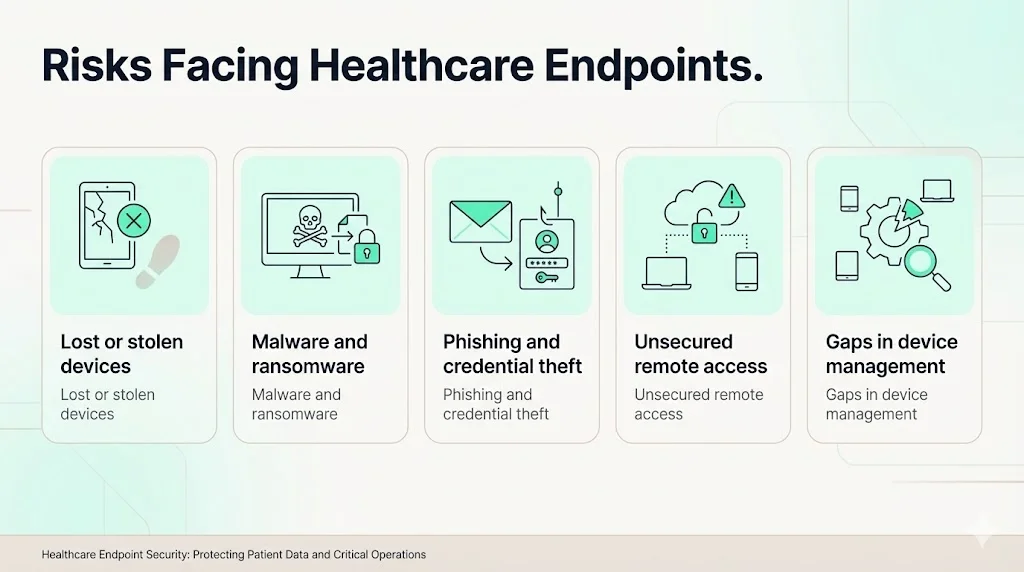
1) Lost or Stolen Devices
Mobile devices are easily misplaced. When a clinician loses a tablet in a parking lot or a laptop is stolen from a vehicle, unencrypted ePHI can be exposed. Compliancy Group notes that full‑disk encryption on laptops, smartphones, and other devices is critical because even a single unencrypted device can lead to a major fine. The 2019 OCR settlement shows that regulators expect encryption to be a basic control.
2) Malware and Ransomware Attacks
Ransomware has surged in healthcare, with attackers encrypting medical systems and demanding payment. The Cobalt 2025 breach statistics report that healthcare is the top target for ransomware, accounting for 17 % of attacks across all industries, and attackers demand an average of $7 million. Misconfigured endpoints—such as devices with disabled volume shadow copy or quarantine settings—provide an easy path for ransomware. NIST recommends identifying reasonably anticipated threats like phishing and ransomware when conducting risk assessments, emphasizing the need to protect endpoints.
3) Phishing and Credential Theft
Phishing remains the leading access vector for healthcare breaches. Attackers send convincing emails to trick staff into entering credentials or downloading malware. Compromised accounts often lead to lateral movement and the theft of patient data. The same Cobalt report notes that 74 % of healthcare organizations running in cloud environments and 44 % in on‑premises environments experienced account compromise. Endpoint security tools with phishing detection and multi‑factor authentication (MFA) reduce these risks.
4) Unsecured Remote Access
The shift to remote work in healthcare—telemedicine, home health monitoring, and administrative staff working from home—means more connections over home Wi‑Fi. Without a properly configured virtual private network (VPN) and MFA, attackers can sniff credentials and pivot into hospital networks. RapidFire Tools advises ensuring that both sending and receiving endpoints are secure and that the devices, networks, and applications involved in data transmission are hardened. Organizations that use remote desktop protocols without MFA are particularly vulnerable.
5) Gaps in Device Management
Many healthcare organizations have hundreds or thousands of devices, including systems managed by third‑party contractors. Tracking, updating, and configuring them consistently is challenging. Unpatched operating systems and outdated applications open vulnerabilities. Without centralized device management, teams often miss remote devices or fail to apply critical patches. HIPAA’s proposed updates for 2024–2025 aim to make technology asset inventories and network maps mandatory, requiring organizations to update them at least annually and after changes. These inventories help identify unmanaged endpoints and ensure they receive updates.
The Impact of Endpoint Breaches on Patient Data
An endpoint breach is not just a technical issue; it affects patients directly. When ePHI is exposed, patients may face identity theft, insurance fraud, or embarrassment if sensitive diagnoses become public. HIPAA requires providers to notify affected individuals, HHS, and sometimes the media when certain breaches occur. This leads to reputational harm and loss of trust. Operationally, ransomware can halt scheduling systems, lab orders, and telehealth platforms, causing delays in treatment. Financially, the costs include incident response, legal fees, credit monitoring for victims, and potential OCR penalties. The $3 million OCR settlement over an unencrypted laptop underscores the legal consequences. Finally, endpoint breaches often prompt comprehensive audits and corrective action plans, diverting resources from patient care.
Core Principles of HIPAA Endpoint Security
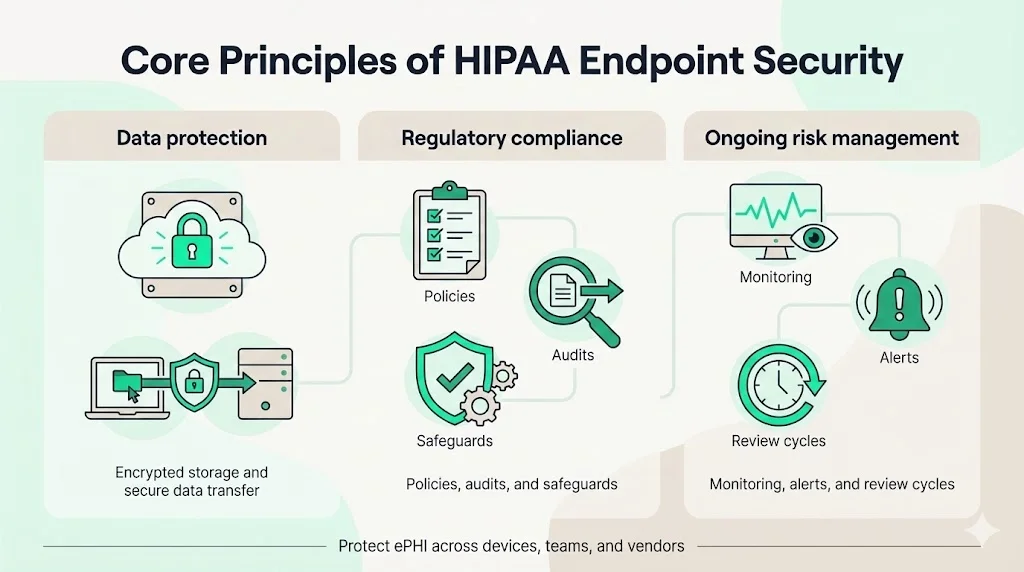
1) Data Protection and Health Information Security
Securing endpoints starts with protecting data at rest and in transit. Full‑disk encryption renders stolen devices unreadable. Compliancy Group stresses that encryption hides sensitive data and protects it from theft or corruption. For removable media, encryption ensures that USB drives or external hard drives do not expose ePHI if lost. Transmission security requires encryption protocols (TLS, VPNs) to protect ePHI when it moves between systems. CrowdStrike’s overview of HIPAA notes that transmission security is a core technical safeguard, requiring integrity controls to prevent data modification and encryption to protect data during transmission.
Reducing the attack surface also involves limiting where ePHI resides. Minimizing local storage, using secure cloud services, and applying data classification help ensure that sensitive data is stored only where necessary. Devices should be configured to store minimal patient data and automatically upload data to secure servers. When data must remain on a device (e.g., offline home health equipment), robust encryption and remote wipe features are essential.
2) Privacy Compliance and Regulatory Standards
HIPAA endpoint controls must align with regulatory requirements and support audits. The Security Rule’s administrative, physical, and technical safeguards are well established. The proposed NPRM will make all implementation specifications mandatory rather than designating some as “addressable,” and it will require documented policies, procedures, and analyses. New provisions would require technology asset inventories and network maps updated at least every 12 months. A regulated entity’s risk analysis must identify all reasonably anticipated threats, vulnerabilities, and predisposing conditions and assess risk levels. These changes will increase the evidentiary burden on healthcare organizations and make rigorous endpoint management essential.
Consistency across teams is also vital. HIPAA applies to covered entities and business associates. Third‑party service providers, such as medical billing companies or telehealth vendors, must implement the same safeguards. Business associate agreements should spell out responsibilities for encryption, device management, incident reporting, and access controls. Without clear agreements, a breach at a vendor can become the covered entity’s liability.
3) Risk Management as an Ongoing Process
HIPAA treats risk management as a continuous effort. The Security Rule requires regulated entities to perform an accurate and thorough assessment of potential risks and vulnerabilities to ePHI and to regularly review and update their security measures. NIST SP 800‑66 advises preparing by identifying all devices, systems, and data flows, including laptops, mobile devices, and IoT medical devices. Step 2 of NIST’s risk assessment process calls for identifying reasonably anticipated threats such as phishing, ransomware, and insider attacks. Step 3 involves identifying vulnerabilities and predisposing conditions that threats could exploit. A business impact analysis helps prioritize risks by evaluating the criticality of organizational assets and determining acceptable downtime.
Risk assessments must be updated regularly—especially when new devices enter the network or when the organization adopts new technologies. Under the proposed NPRM, regulated entities will be required to update risk analyses and network maps whenever there is a change in environment or operations that may affect ePHI. In practice, this means adding a new remote monitoring device or telehealth platform triggers a review of potential threats and adjustments to controls.
Best Practices for HIPAA Endpoint Security
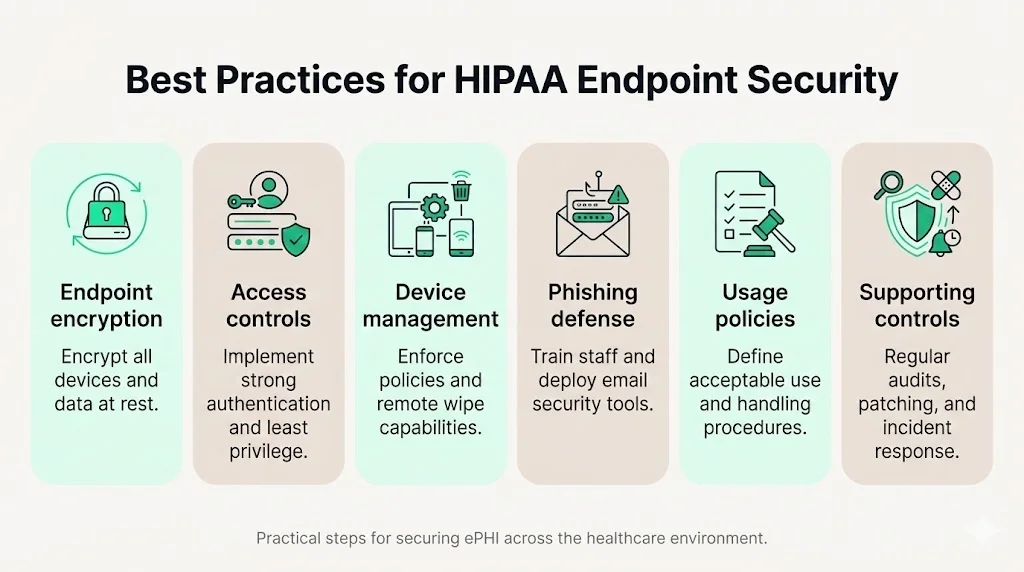
1) Endpoint Encryption
Full‑disk encryption is non‑negotiable. Compliancy Group requires encryption on all devices that connect to or store ePHI, including servers, desktops, laptops, and smartphones. Without encryption, lost or stolen devices become reportable breaches. Encryption should be enabled by default and centrally enforced. Removable media (USB drives, external hard drives) should also be encrypted or banned. Devices that support hardware‑based encryption (e.g., TPM chips) can offer stronger protection, and encryption keys should be managed securely—ideally by an enterprise key management system.
2) Strong Access Controls
Access controls ensure that only authorized individuals can access ePHI. HIPAA requires unique user IDs, password management, automatic logoff, and encryption/decryption processes. MFA is now considered a best practice and will likely become mandatory under the NPRM. According to CrowdStrike’s HIPAA guide, access controls and audit controls are core technical safeguards. Role‑based access ties user privileges to job duties; clinicians should see only the records needed for treatment, while billing staff should not access clinical notes. Automatic session timeouts prevent unattended devices from being exploited. Strong passwords or passphrases, rotated regularly, reduce the risk of credential theft.
3) Device Management and Monitoring
Centralized device management platforms (mobile device management (MDM) or unified endpoint management (UEM)) allow administrators to enforce policies, push patches, and track inventory. Regulators want evidence that every device is known and controlled; the NPRM’s requirement for a technology asset inventory every 12 months formalizes this. MDM tools enable remote lock and wipe capabilities—critical for lost devices. They also support application whitelisting, which limits devices to approved software, reducing the risk of malware. Compliancy Group lists features of endpoint protection systems, including data loss prevention, encryption, network access control, endpoint detection and response, insider threat protection, application whitelisting, data classification, and privileged user control. These features collectively provide visibility and control across the fleet.
Monitoring goes beyond patching. Endpoint detection and response (EDR) tools track real‑time behaviors, detect anomalies, and block malicious activity. Security information and event management (SIEM) platforms aggregate logs from endpoints and network devices to correlate events and identify attack patterns. RapidFire Tools emphasizes the role of intrusion detection systems (IDS) and intrusion prevention systems (IPS) in identifying unauthorized access and anomalies. For HIPAA compliance, logs must be kept to support incident investigations and audits. Audit trails should record logins, file accesses, configuration changes, and remote connections.
4) Phishing Prevention and Malware Defense
Since phishing remains the top attack vector, organizations should implement layered defenses. Email filtering systems block known malicious domains and attachments. Advanced threat detection can identify suspicious file behavior and sandbox attachments. Staff need regular training to recognize phishing attempts. CrowdStrike notes that security awareness training is part of the administrative safeguards. Anti‑malware and anti‑virus tools should be installed on all endpoints and centrally managed. Browser isolation or endpoint protection platforms can prevent drive‑by downloads. DNS filtering blocks malicious websites, and application control prevents unauthorized software from running.
5) Security Policies for Endpoint Use
Policies translate technical controls into human expectations. Acceptable use policies set clear rules for employees: no sharing of passwords, no storing ePHI on personal devices, no installation of unauthorized apps. Bring‑your‑own‑device (BYOD) policies should define whether personal devices may access ePHI and under what conditions (e.g., enrollment in MDM, mandatory encryption, remote wipe). Remote work policies must mandate the use of VPNs, MFA, and secure Wi‑Fi networks. Staff should know how to report lost or compromised devices immediately. RapidFire Tools reminds organizations to ensure both sending and receiving endpoints are secure and to harden devices, networks, and applications involved in data transmission.
6) Supporting Controls That Strengthen Endpoint Security
- Audit Trails and Activity Logging: HIPAA requires logging of system activity to support incident response and investigations. CrowdStrike explains that audit controls help organizations know when specific users access particular files. Logs should capture logins, file access, changes to system configurations, and remote connections. Retain logs for an appropriate period (often six years under HIPAA) and protect them from tampering.
- Security Training for Healthcare Staff: People are often the weakest link. HIPAA mandates security awareness training, and NIST recommends ongoing training rather than one‑time sessions. Training should cover phishing identification, safe handling of patient data, secure use of mobile devices, and the organization’s incident response procedures. Simulation exercises (e.g., phishing drills) help reinforce learning. Staff should know where to report suspicious emails or device issues.
- Vulnerability Assessment and Testing: Regular scans of endpoints and networks identify outdated software, misconfigurations, and unpatched vulnerabilities. RapidFire Tools offers tools for vulnerability management, and the Cobalt study highlights that misconfigured endpoints are a significant target for ransomware. Penetration testing and red‑team exercises can validate controls and expose weaknesses before attackers do. Vulnerability management programs should prioritize remediation based on risk (e.g., CVSS scores) and track closure within defined service‑level agreements (SLAs). Combined with continuous monitoring, these assessments ensure that controls remain effective.
How Endpoint Security Fits Into a HIPAA Cybersecurity Program
Endpoint security is part of a larger ecosystem. Firewalls, intrusion detection systems, and network segmentation prevent lateral movement. Vulnerability management reduces the number of exploitable flaws. SIEM platforms provide centralized visibility across endpoints and networks. Incident response plans coordinate people and technology to contain breaches. Under the proposed NPRM, regulated entities must develop a technology asset inventory and network map that illustrate the movement of ePHI. This underscores that endpoints are not isolated; they connect to servers, databases, and cloud services. Controls must therefore operate across these boundaries.
Integration is key. Endpoint agents should send logs to the SIEM, which correlates with firewall and intrusion detection alerts. Endpoint encryption must align with backup and disaster recovery plans. Identity and access management should extend from endpoints into cloud systems. In our experience at Konfirmity—having conducted over 6,000 audits and with 25 years of combined technical expertise—organizations struggle when controls are siloed. For example, one hospital had strong password policies but lacked device management; unpatched laptops were exploited despite strong credentials. Conversely, a health‑tech startup used an integrated approach with UEM, MFA, SIEM, and managed detection and response. They reduced the mean time to detect incidents by 60 % and passed their SOC 2 Type II and HIPAA audits within five months. The lesson is clear: endpoint security must be coordinated with broader cybersecurity measures and continuously operated.
Common Endpoint Security Mistakes to Avoid
- Relying on encryption alone. Encryption is necessary but insufficient. Without access controls, attackers who obtain valid credentials can still decrypt data. Without logging, you won’t know a breach occurred.
- Ignoring mobile and remote devices. Bring‑your‑own‑device is common in healthcare, but personal devices without MDM control expose ePHI. Remote staff must use secure VPNs and MFA.
- Delaying updates and patches. Attackers exploit known vulnerabilities quickly. Without an automated patching process, endpoints fall behind. Misconfiguration of Windows services (e.g., volume shadow copy) has enabled ransomware.
- Lacking clear ownership. Endpoint security spans IT, security, compliance, and clinical teams. Without a designated owner accountable for inventory, policies, and monitoring, gaps appear.
- Treating HIPAA as a one‑time task. Compliance is not a project to complete and forget. Regulators expect continuous monitoring and evidence of ongoing risk management. Auditors look for consistent logs and updated risk assessments.
Implementation Steps for Healthcare Organizations
Implementing HIPAA Endpoint Security For HIPAA requires a structured approach. We recommend the following steps, based on our managed service experience:
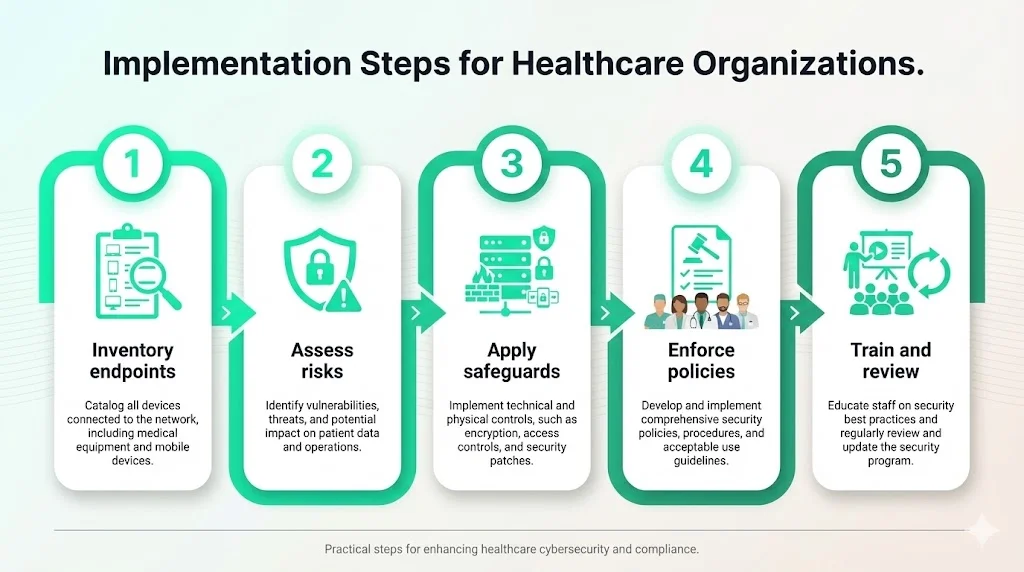
Step 1: Inventory All Endpoints
List every device that accesses patient data—laptops, desktops, tablets, smartphones, IoT medical equipment, remote workstations, and third‑party devices. Under the proposed rule, you must maintain a technology asset inventory and network map that shows how ePHI flows. Use automated discovery tools to detect devices connecting to the network. Include personally owned devices authorized through BYOD programs.
Step 2: Assess Risks and Gaps
Perform a thorough risk assessment focusing on confidentiality, integrity, and availability. Identify threats (phishing, ransomware, insider misuse) and vulnerabilities (unpatched software, weak passwords, missing encryption). Assess predisposing conditions like poor physical security or high staff turnover. Prioritize risks based on potential impact on patient care and operations. Konfirmity often finds that endpoints outside of corporate offices—home health tablets, BYOD smartphones—present the highest unmanaged risk.
Step 3: Apply Technical Safeguards
Implement full‑disk encryption on all devices storing ePHI. Enforce MFA and strong password policies. Use MDM/UEM for centralized control and remote wipe. Install endpoint detection and response tools and ensure logs are forwarded to a SIEM. Configure automatic patching and vulnerability scanning. Limit administrative privileges and enable application whitelisting. Use VPNs and TLS encryption for data in transit.
Step 4: Set and Enforce Security Policies
Develop acceptable use, BYOD, remote work, and mobile device policies. Require employees to report lost or stolen devices immediately. Define consequences for policy violations. Align policies with the administrative safeguards (risk management, sanction policies, workforce security) described in the HIPAA Security Rule. Ensure that business associate agreements include endpoint security requirements.
Step 5: Train Staff and Review Regularly
Provide ongoing security awareness training. Teach staff to recognize phishing emails, secure their devices, and report incidents promptly. Conduct simulations and tabletop exercises. Review and update policies, inventories, and risk assessments annually or after significant changes. Use audit logs to verify that controls are working. The NPRM’s proposal to require written documentation and regular updates underscores the importance of continuous improvement.
Conclusion
HIPAA Endpoint Security For HIPAA is not a marketing phrase; it’s a commitment to protecting patients and meeting regulatory obligations. Healthcare endpoints—laptops, tablets, smartphones, and medical devices—are prime targets for attackers. Lost devices, ransomware, and phishing all threaten ePHI. Regulators have increased enforcement, with penalties like the $3 million settlement for unencrypted devices. Meanwhile, the average cost of a healthcare breach remains the highest among all industries at $7.42 million, and breaches take nearly nine months to contain. The HIPAA Security Rule and its proposed updates require comprehensive administrative, physical, and technical safeguards.
Konfirmity’s view, grounded in more than 6,000 audits and over 25 years of combined expertise, is that security must precede compliance. We implement controls inside your environment—encryption, MFA, device management, monitoring, and training—then maintain them year‑round. Customers often reach audit readiness in 4–5 months with our managed service versus 9–12 months when self‑managed, and they save hundreds of internal hours. Real security design delivers lower breach costs, faster sales cycles, and stronger trust. Security that reads well on paper but fails during an incident is a liability. Build your program once, operate it daily, and let compliance follow.
Frequently Asked Questions
1. What are the three types of security in HIPAA?
The HIPAA Security Rule defines administrative, physical, and technical safeguards. Administrative safeguards include risk management, access management, workforce security, and training. Physical safeguards govern facility access, workstation use, and device security. Technical safeguards cover access controls, audit controls, authentication, integrity, and transmission security.
2. Does HIPAA require end‑to‑end encryption?
HIPAA doesn’t prescribe specific technologies but requires that ePHI be protected against unauthorized access. Encrypting data at rest and in transit is an effective way to meet these requirements. Compliancy Group emphasizes full‑disk encryption on all devices connecting to or storing ePHI. CrowdStrike notes that transmission security must include encryption and integrity controls to protect data during transmission.
3. What does endpoint security protect against?
Endpoint security defends against malware, ransomware, phishing, unauthorized access, and data loss. It includes encryption, MFA, patching, EDR, and policies that govern device use. The Cobalt study finds that ransomware attackers demand an average of $7 million from healthcare targets, while phishing remains a leading access vector. Proper endpoint security reduces the attack surface and enables rapid detection.
4. Is a firewall required for HIPAA compliance?
Firewalls are part of network security rather than endpoint security, but they complement endpoint controls. The HIPAA Security Rule doesn’t specifically mention firewalls, yet technical safeguards require protection against unauthorized access and transmission security. Firewalls, intrusion detection systems, and network segmentation help enforce these requirements. RapidFire Tools highlights that both sending and receiving endpoints and the networks connecting them must be secure. In practice, auditors expect to see firewalls configured to block unauthorized traffic and logs integrated with SIEM systems.





.svg)






.svg)
.svg)