In a healthcare ecosystem where cyber‑attacks, ransomware and regulatory scrutiny keep rising, it is no longer enough to have compliance “on paper.” The only sustainable way to protect patients and move deals forward is through strong operational security and rigorous documentation. The HIPAA Evidence Collection Templates approach helps covered entities and business associates build this foundation. Instead of scrambling during audits or breaches, teams embed evidence collection into everyday processes—saving time, reducing risk and improving trust.
Why evidence collection matters under HIPAA
Under HIPAA, evidence encompasses any record that demonstrates compliance. Policies and procedures, access logs, risk assessments, breach reports, training records and vendor agreements all count. These records support compliance across the three core HIPAA rules:
- Privacy Rule (45 CFR Part 160 & Subparts A and E of Part 164) – governs how individually identifiable health information may be used and disclosed.
- Security Rule (45 CFR Part 160 & Subparts A and C of Part 164) – requires administrative, physical and technical safeguards for electronic protected health information (ePHI).
- Breach Notification Rule (45 CFR §§ 164.400‑414) – mandates that covered entities notify affected individuals, the U.S. Department of Health and Human Services (HHS) and sometimes the media after certain breaches.

The risk of failing to collect and maintain proper evidence has grown dramatically. Data breach incidents in the healthcare sector have surged: in 2024 alone, 276 million individuals’ information was exposed or stolen, and large breaches such as the Change Healthcare hack affected 190 million people. The HHS Office for Civil Rights (OCR) responded by launching a “Risk Analysis Initiative” in late 2024. By April 2025 the initiative resulted in seven enforcement actions, and OCR noted that failures to perform comprehensive risk analysis are a leading finding in investigations. OCR’s new initiative highlights that ransomware incidents increased 264 % since 2018 and that inadequate risk analysis significantly increases the likelihood of such attacks.
The business impact is equally sobering. IBM’s 2024 Cost of a Data Breach study found that healthcare breaches have the highest average cost, at $10.93 million per incident. Breaches often go undetected for a long time: the average healthcare breach lasts 213 days before discovery. Even when incidents are identified, failing to maintain proper evidence can result in multimillion‑dollar civil monetary penalties. The 2025 HIPAA penalty tiers range from $141 to $2,134,831 per violation, and small clinics face the same penalties as large hospitals.
Evidence strengthens privacy, security and accountability
Evidence collection under HIPAA serves four critical functions:
- Safeguarding patient privacy and data security – well‑designed policies, encryption controls and access logs show that the organization is proactively protecting ePHI. OCR’s guidance stresses that regulated entities must conduct “an accurate and thorough assessment of the potential risks and vulnerabilities to the confidentiality, integrity and availability of ePHI” and implement measures to reduce risks.
- Enforcing confidentiality protocols – logs and training records demonstrate that staff follow the principle of least privilege. The Security Rule NPRM proposes requiring written incident response plans, asset inventories and multi‑factor authentication, all of which require documentation.
- Supporting breach investigations and regulatory audits – detailed access logs and incident reports help reconstruct events. Having documentation ready can reduce containment time; IBM found that organizations using automation and AI cut breach costs by $1.76 million and shortened the breach life cycle by 108 days.
- Improving operational resilience – regular risk assessments and vendor reviews allow teams to identify vulnerabilities, plan remediation and measure progress. OCR advises organizations to perform thorough security risk analyses, align policies and training with findings, develop documented implementation plans and track progress.
Key types of evidence to collect

Policy and procedure documents
- What to include: HIPAA privacy and security policies, data access policies, data retention and disposal policies, encryption standards, incident response plans, disaster recovery procedures, business associate agreements (BAAs) and privacy notices.
- Why it matters: Formal policies provide proof that the organization commits to privacy and security. The Security Rule NPRM proposes requiring written documentation of all policies, procedures, plans and analyses. BAAs are especially important when PHI is shared with vendors; HHS explains that contracts must limit permissible uses of PHI, require safeguards, mandate reporting of incidents and make the business associate directly liable under the HIPAA Rules. Having standardized policy templates ensures consistent language and reduces gaps in coverage.
Risk assessment records
- What to include: Risk assessment plans, data flow diagrams identifying where ePHI is stored and transmitted, lists of assets (servers, devices, cloud services), vulnerabilities, threat likelihood and impact scores, remediation action plans and timelines.
- Why it matters: Risk analysis is fundamental to HIPAA compliance. OCR requires regulated entities to conduct “an accurate and thorough assessment of the potential risks and vulnerabilities to the confidentiality, integrity and availability of ePHI”. NIST SP 800‑66 emphasizes that organizations must identify where ePHI is created, received, maintained or transmitted across physical and logical boundaries—including remote workforces and IoT devices—and document threats, vulnerabilities, existing security measures, and risk levels. The NPRM proposes requiring a technology asset inventory and network map updated at least annually, identification of anticipated threats and vulnerabilities, assessment of risk levels and review of business associate arrangements.
Access logs and audit trails
- What to include: User access logs, system login history, file access and change logs, API call logs, remote session records and audit trails for all systems storing or processing ePHI.
- Why it matters: Access logs enable confidentiality enforcement, incident investigation and audit readiness. OCR’s settlement agreements often cite the absence of audit controls as a violation. The NPRM proposes requiring organizations to implement technical controls such as anti‑malware protection, network segmentation and multi‑factor authentication. Evidence templates help ensure that logs capture user identity, timestamp, actions performed and justification.
Training and employee acknowledgement records
- What to include: Records showing completion of HIPAA training for all workforce members, employee signatures acknowledging policies, role‑based access assignments, periodic re‑training logs and disciplinary actions for violations.
- Why it matters: Section 164.530(b) of the Privacy Rule requires covered entities to train all members of their workforce on policies and procedures relating to protected health information. Training must be provided by the compliance date, for new staff within a reasonable period after hiring and whenever material changes occur. Covered entities must document that training has been provided. Training records show regulators that staff understand their obligations and support role‑based access control.
Incident and breach reports
- What to include: Security incident logs, root‑cause analyses, breach notification forms, remediation plans, communications to affected individuals and regulators, and evidence of post‑incident lessons learned.
- Why it matters: The Breach Notification Rule requires covered entities to notify HHS and affected individuals within 60 days after discovering a breach. OCR emphasises that incident and breach documentation must include evidence of investigation and corrective actions. Maintaining structured incident reports ensures teams can swiftly reconstruct events and demonstrate compliance.
Vendor/business associate documentation
- What to include: Business Associate Agreements (BAAs), vendor risk assessment questionnaires, vendor security policies, third‑party attestations (e.g., SOC 2 reports), evidence of encryption and access controls, and service‑level agreements.
- Why it matters: When a covered entity engages a business associate, it must have a written contract that specifies permitted uses of PHI and requires safeguards and incident reporting. Business associates are directly liable for unauthorized uses or disclosures of PHI. Evidence templates help centralize BAAs and track vendor compliance.
Audit and review records
- What to include: Internal audit reports, audit checklists, corrective action plans, results of periodic policy reviews, management review meeting notes and annual compliance review logs.
- Why it matters: Evidence of continuous monitoring and internal audits shows that compliance is a living program, not a one‑time event. The NPRM proposes requiring regulated entities to conduct a compliance audit at least once every 12 months and requiring business associates to verify annually that they have implemented required safeguards. Having a template for audit records ensures completeness and supports rapid retrieval during external audits.
Building or adapting HIPAA evidence collection templates
Below is a step‑by‑step approach to creating usable templates for HIPAA evidence collection, informed by the practices we have implemented across 6,000+ audits and 25+ years of combined security experience at Konfirmity.
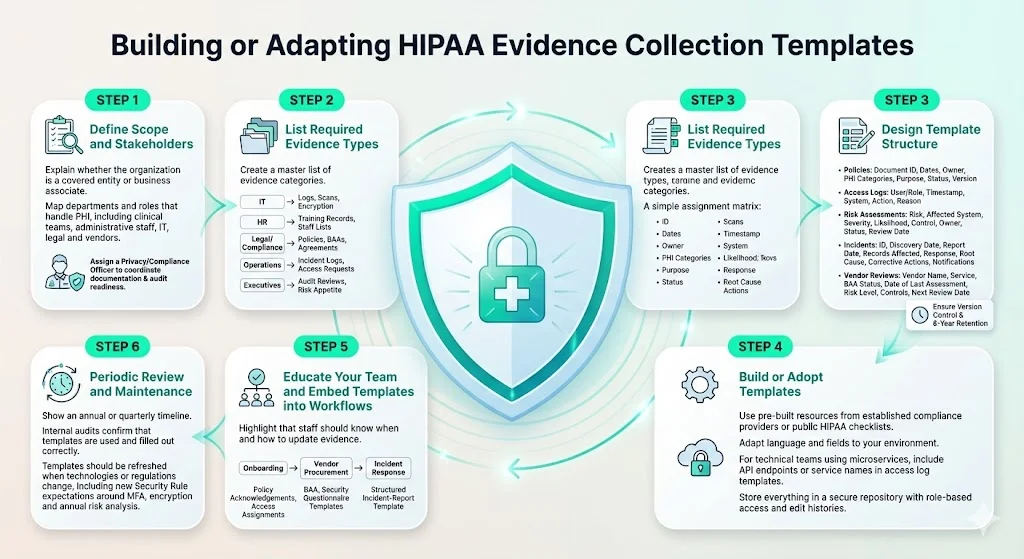
Step 1: define scope and stakeholders
- Identify whether you are a covered entity or a business associate. HHS defines covered entities as health care providers, health plans or clearinghouses, and business associates as entities that perform functions involving access to PHI on behalf of a covered entity.
- Map all departments and roles handling PHI. Include clinical teams, administrative staff, IT operations, legal counsel and third‑party vendors.
- Assign a privacy or compliance officer. This role should oversee documentation, coordinate across departments and serve as the point of contact during audits.
Step 2: list required evidence types
Use the evidence categories described above to create a master list tailored to your organization. Assign ownership for each category: IT may handle access logs and vulnerability scans; HR manages training records; legal or compliance teams oversee policies and BAAs; operations teams maintain incident logs; and executives review audit reports. Mapping responsibilities early prevents gaps.
Step 3: design template structure
Every evidence template should include standard fields to ensure consistency and enable automated checks. For example:
- Common fields for policies and procedures: document name/ID, date created, last updated, responsible person, PHI categories covered, purpose, status (active/archived), version number, and notes.
- Access log fields: user or role, timestamp, system accessed, action performed, reason, and notes. If logs are exported from systems, use templates to define the columns expected.
- Risk assessment fields: identified risk, affected system, severity, likelihood, mitigating control, responsible owner, remediation status, review date.
- Incident report fields: incident ID, date discovered, date reported, description, affected records, initial response, root cause, corrective actions, notification details.
- Vendor review fields: vendor name, service provided, BAA status, date of last assessment, risk level, summary of controls, next review date.
Version control is critical. Each template should track revisions and maintain an archive of superseded versions. HIPAA retention requirements state that documentation of policies, procedures and assessments must be retained for at least six years from creation or the last date in effect.
Step 4: build or adopt templates
- Leverage pre‑built resources. Konfirmity provides policy templates, compliance checklists and risk assessment worksheets built from thousands of audits. Many organizations also use publicly available checklists from the HIPAA Journal and OCR.
- Customize to fit workflows. Adapt template language and fields to align with your operations. For example, if your environment uses containerized microservices, your access log template should include API endpoints and microservice names.
- Store in a secure repository. Use a document management system or compliance platform with role‑based access controls. The repository should maintain audit trails of who accessed or modified templates.
Step 5: educate your team and embed templates into workflows
- Training on evidence collection duties. Beyond generic HIPAA training, staff should understand when and how to update templates. For instance, project managers should know that a new information system triggers an update to the asset inventory and risk assessment.
- Integrate into existing processes. Onboarding should require completion of training acknowledgements and assignment of access privileges; vendor procurement should include BAA and security questionnaire templates; incident response should reference the incident report template.
Step 6: periodic review and maintenance
- Schedule regular audits. Internal audits should verify that evidence templates are being used and completed accurately. OCR recommends tracking mitigation activities and evaluating their effectiveness.
- Update templates after changes. When technologies, processes or regulations evolve—such as the proposed Security Rule changes requiring multi‑factor authentication, encryption of ePHI at rest and in transit, and annual risk analyses—update templates accordingly.
Example use cases and sample templates
To help visualize how templates work in practice, here are sample outlines for three evidence types. These tables include representative fields and example entries.
Incident / breach report log
Risk assessment summary
Access log for ePHI
In real scenarios, these templates ensure continuity. During an OCR audit, the audit team can retrieve the access log to confirm that only authorized personnel viewed specific records. If a breach occurs, the incident log provides a clear timeline of discovery, notification and remediation actions, demonstrating diligence and reducing penalties. For vendor reviews, the BAA repository and vendor risk assessments show that due diligence is performed, which is critical when sharing PHI with third parties.
Common pitfalls and how to avoid them
- Inconsistent documentation across departments – Without standard templates, each team documents evidence differently. The solution is to adopt centralized templates with required fields and enforce their use across the organization. Periodic internal audits should verify consistency.
- Missing or outdated records – Policies may be superseded without archives, and BAAs may expire. Implement version control and retention schedules to maintain historical records. HIPAA requires retaining policies, procedures and assessments for at least six years.
- Lack of accountability – When no one owns evidence collection, tasks slip. Assign clear ownership for each template type, with escalation paths when data is missing. Many organizations assign evidence owners and have weekly check‑ins.
- Overlooking vendor documentation – Organizations sometimes forget to collect BAAs or risk assessments from subcontractors. Create a vendor onboarding checklist that requires a signed BAA and evidence of security controls before any data sharing. OCR’s guidance emphasises that covered entities must have written contracts with business associates and that associates are directly liable for safeguarding ePHI.
- Poor log retention or deletion policies – Some systems discard logs after 30 days. Define retention periods based on risk and compliance needs, and store logs securely. For example, keep access logs for the HIPAA‑required six years and replicate them to a secure archive.
- Templates not tailored to operations – A one‑size‑fits‑all template might not capture necessary details in specialized environments like telehealth platforms or IoT devices. Customize templates to reflect actual workflows and data flows, and revise them when operations change.
How evidence collection supports audits, breach investigation and regulatory compliance
Audits: During internal or external audits, auditors will request a sample of policies, risk assessments, training records and BAAs. Well‑organized evidence allows the audit team to quickly verify compliance. SOC 2 Type II audits, for example, require evidence over an observation period of 3 to 12 months. Scrut’s 2025 SOC 2 timeline guide notes that Type II audits typically last 6 to 12 months because controls must operate consistently over time. Having templates ensures evidence is continuously collected rather than assembled at the last minute.
Breach investigations: When incidents occur, logs and incident reports enable organizations to reconstruct events, identify root causes and demonstrate compliance with breach notification requirements. OCR’s enforcement initiative shows that regulated entities failing to conduct thorough risk analyses or maintain logs are penalized. Evidence templates ensure that investigators have immediate access to details such as affected systems, compromised records and remediation actions.
Regulatory reporting: HIPAA requires organizations to notify HHS and individuals when breaches occur. Templates standardize the breach report, ensuring all required information—incident timeline, affected individuals, remediation actions—is collected. Clear documentation simplifies drafting regulatory notifications and reduces risk of incomplete reporting.
Continuous risk management: Evidence collection supports ongoing security operations. Risk assessments identify new vulnerabilities; access logs reveal unauthorized attempts; vendor reviews uncover weak third‑party controls. By continuously collecting and reviewing evidence, organizations implement a cycle of improvement. The Security Rule NPRM proposes requiring annual compliance audits and continuous updates to the technology asset inventory and risk analysis.
Where to get good starting templates and resources
- Secureframe: Secureframe offers policy templates, compliance checklists and risk assessment templates covering HIPAA, ISO 27001, SOC 2 and other frameworks. Their resources include an updated control mapping for ISO 27001:2022, which reduced the number of controls from 114 to 93 and introduced 11 new controls.
- HHS and OCR resources: OCR publishes sample BAAs, training materials and guidance on risk analysis. Use these to align templates with regulatory expectations.
- HIPAA Journal and other compliance journals: HIPAA Journal provides retention requirement guidance, noting that certain HIPAA documents (policies, risk assessments, training records, BAAs, incident documentation, audit logs) must be retained for at least six years.
- Konfirmity: Our managed compliance service provides a library of templates and checklists derived from thousands of audits. We integrate evidence collection into the product development lifecycle, embed security controls, and manage continuous monitoring and remediation tracking.
Conclusion
The stakes for healthcare security and privacy are higher than ever. Massive breaches, rising penalties and OCR’s aggressive enforcement show that HIPAA evidence collection templates are more than paperwork. They are the operational backbone that supports patient privacy, health data security and confidentiality protocols. By systematizing the collection, storage and updating of policies, risk assessments, access logs, training records and BAAs, organizations build a resilient security posture.
Templates alone are not enough. Teams must design controls that stand up during breaches and audits, embed evidence collection into daily workflows and maintain documentation as operations evolve. Human‑led, managed security—like the services offered by Konfirmity—helps organizations implement controls inside their stack, monitor them continuously and prepare evidence year‑round. With structured evidence in place, healthcare organizations can respond quickly to incidents, satisfy regulators and reassure business partners. Security that looks good in documents but fails under incident pressure is a liability. Build the program once, operate it daily and let compliance follow.
FAQs
Q1. What counts as “evidence” under HIPAA compliance?
Evidence includes any documentation that demonstrates HIPAA compliance, such as privacy and security policies, risk assessment reports, access logs, training records, incident and breach reports, business associate agreements and audit logs. These documents must be retained for at least six years.
Q2. Do we need to keep all records forever?
No. HIPAA does not require indefinite retention. Section 164.316(b)(2) and 164.530(i) require that policies, procedures and associated documentation be kept for at least six years from the date of creation or when they last were in effect. Other laws or contracts (e.g., CMS, state medical record rules) may require longer retention.
Q3. If we use third‑party vendors or business associates, do we still need to collect evidence?
Yes. Covered entities must have written business associate contracts that limit uses of PHI, require safeguards and mandate breach reporting. Business associates are directly liable for unauthorized uses or disclosures. Evidence collection must include BAAs, vendor risk assessments and periodic attestations of compliance.
Q4. How often should we review or update evidence templates?
Review templates at least annually and whenever operations, technology or regulations change. OCR’s proposed rule recommends updating the technology asset inventory and network map at least once every 12 months and conducting annual compliance audits. Regular updates ensure templates remain aligned with current risk and compliance requirements.
Q5. Can evidence collection be automated?
Yes. Many organizations leverage compliance platforms or managed services to automate evidence collection from systems, identity providers, ticketing tools and cloud platforms. Automation reduces manual work and ensures continuous monitoring. IBM’s study shows that organizations using automation and AI reduce breach costs and breach lifecycles significantly. However, automation should complement—not replace—human oversight. A human‑led program ensures that evidence is contextualized, accurate and ready for auditors and incident responders.





.svg)






.svg)
.svg)