Most enterprise buyers and regulators now demand proof that healthcare providers can protect patient information. Deals stall and fines mount when documentation is thin. Under HIPAA Evidence Requirements you need to demonstrate not only that you have controls but that those controls actually operate day‑to‑day. Understanding HIPAA Evidence Requirements helps you stay audit‑ready. This article, written as Amit Gupta from Konfirmity, unpacks what evidence means under HIPAA, why it matters, and how to build and maintain the right records without slowing your operations.
What Does HIPAA Cover?
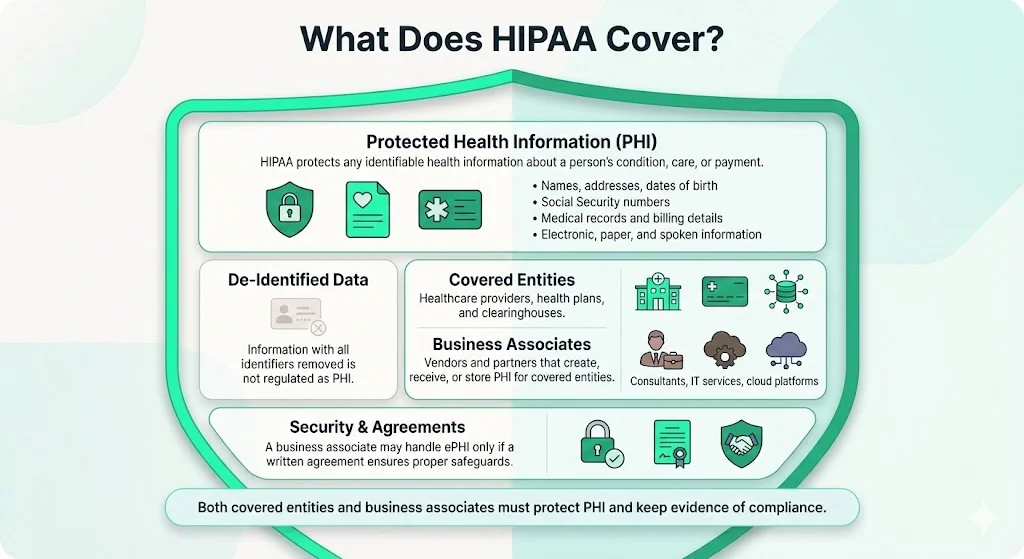
HIPAA’s Privacy Rule defines protected health information (PHI) as any individually identifiable health information related to a person’s health condition, provision of care or payment. PHI can be electronic (ePHI), on paper or spoken; it includes names, addresses, dates of birth, Social Security numbers and payment data. De‑identified information, from which identifiers have been removed, is not covered.
Healthcare providers, insurers (health plans) and clearinghouses are “covered entities.” Vendors, consultants and cloud providers that create, receive or store PHI on behalf of covered entities are “business associates.” The Security Rule notes that a regulated entity may allow a business associate to handle ePHI only if a written business associate agreement ensures that the associate will safeguard the data. Both covered entities and business associates must implement safeguards and maintain evidence to prove compliance.
HIPAA Rules Relevant to Evidence and Documentation
Privacy Rule – Governs the use and disclosure of all PHI. Covered entities must limit disclosures to what is necessary, respond to patient requests for records, and track how information is shared. They must maintain records of patient consent and signed authorization forms for disclosures that fall outside treatment, payment or healthcare operations.
Security Rule – Focuses on protecting ePHI. It requires administrative, physical and technical safeguards. Technical safeguards include access controls, unique user IDs and audit controls: regulated entities must implement hardware, software and procedural mechanisms to record and examine activity in systems containing ePHI. Policies and procedures must be documented and retained for six years. Business associate agreements must require partners to notify of breaches and to maintain safeguardshhs.gov.
Breach Notification Rule – Requires covered entities to notify affected individuals, HHS and sometimes the media when unsecured PHI is impermissibly used or disclosed. The American Medical Association explains that covered entities must notify relevant parties “without unreasonable delay” and no later than 60 days from discovery. If more than 500 individuals are affected, notice must be sent to prominent media outlets; for smaller breaches, entities may log the incident and report annually.
Administrative Simplification also includes the Transactions and Code Sets Rule, the Unique Identifiers Rule and the Enforcement Rule. These rules standardize electronic claims, require unique identifiers for providers and health plans, and give HHS authority to impose penalties when entities fail to comply. While these rules don’t directly prescribe evidence, they underpin the requirement for complete and auditable records.
Why Evidence and Documentation Matter
Evidence is not optional. Regulators, auditors and enterprise customers increasingly demand proof that controls are in place and effective. Under the Security Rule, regulated entities must document policies, assessments and activities and retain them for six years. Without logs and records, it is impossible to demonstrate compliance during an OCR audit or to defend against lawsuits.
Documentation also supports internal visibility. A mature program includes documented policies, procedures, risk assessments, staff training and audit logs. These artifacts help identify gaps early, measure adherence and drive continuous improvement. During the 2024–2025 HIPAA audit program, OCR noted that substantial increases in hacking and ransomware have impacted hospital operations and patient care; the audits will review selected provisions of the Security Rule for 50 entities. In other words, failure to maintain evidence now directly influences operational risk and revenue.
Key Types of Evidence and Documentation
The table below summarises core evidence categories. Each row identifies what to maintain and why it matters. These records demonstrate HIPAA Evidence Requirements and support incident response, audits and enterprise sales cycles.
Building HIPAA‑Ready Evidence: A Step‑by‑Step Guide
Meeting HIPAA Evidence Requirements does not have to paralyse operations. Below is a pragmatic workflow that Konfirmity has implemented across thousands of audits. The steps integrate security into daily work and reduce the long‑term effort required during an audit.
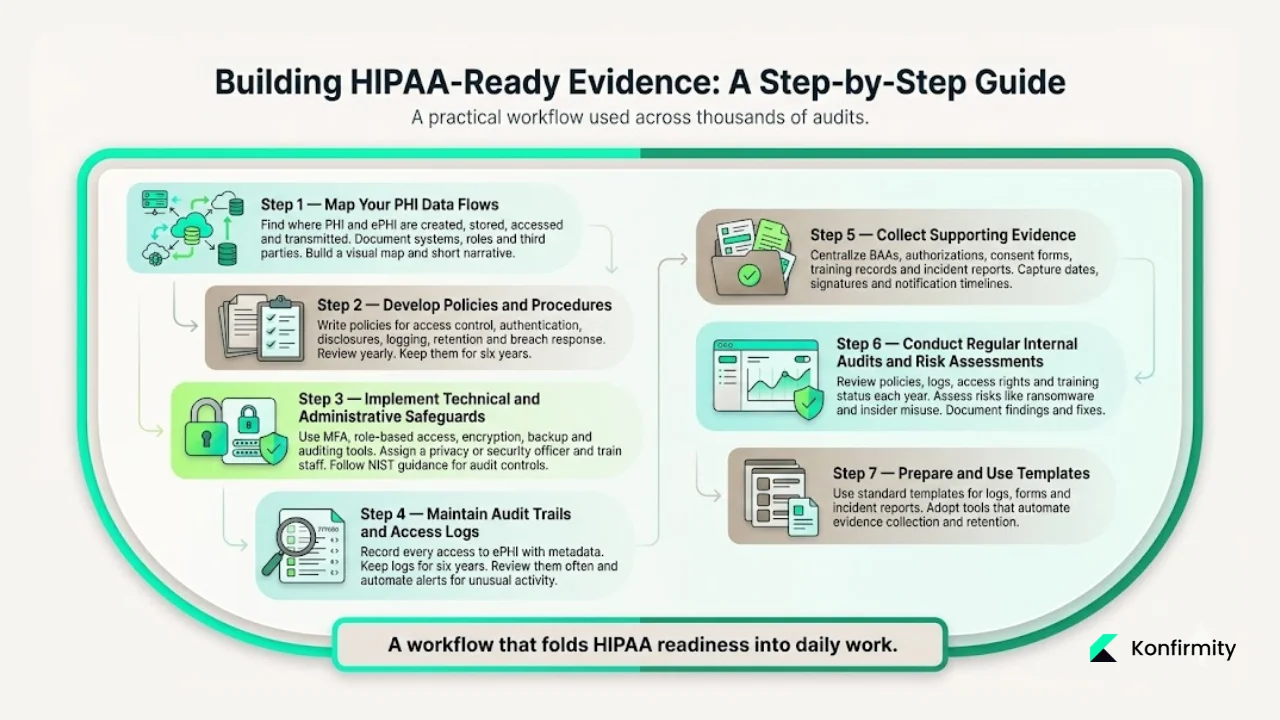
1. Map Your PHI Data Flows
Identify where PHI and ePHI are created, stored, accessed and transmitted. Document systems (EHRs, billing platforms, cloud storage), user roles and third parties. Create a visual diagram and a narrative describing the flow. This map informs risk assessments and helps locate where audit logs and controls are needed.
2. Develop Policies and Procedures
Draft privacy and security policies covering access control, minimum‑necessary disclosures, authentication, authorizations, incident response, audit logging, data retention and destruction. Include procedures for handling access requests, patient requests for accounting of disclosures and breach response. These documents should be reviewed at least annually and updated when systems or workflows change. The Security Rule requires that written policies be retained for six years.
3. Implement Technical and Administrative Safeguards
Deploy authentication, role‑based access control, encryption, backup and auditing tools. Ensure each user has a unique ID and multi‑factor authentication where feasible. Administrative safeguards include designating a privacy/security officer, defining roles and responsibilities, and training staff. NIST guidance for audit controls advises determining the activities to be monitored, selecting appropriate tools and establishing a review policy.
4. Maintain Audit Trails and Access Logs
Configure systems to record every access to ePHI with metadata (user, action, record, timestamp, device). For paper files, use a check‑in/check‑out log. Retain logs for at least six years. Regularly review them for anomalies; automate alerts for unusual patterns. HHS emphasises that audit controls must record and examine activity in systems containing ePHI.
5. Collect Supporting Evidence
Centralise signed authorisations, minimum‑necessary analyses, BAAs, training logs and incident reports. Use digital forms to reduce errors. When a disclosure requires patient consent, capture the form and link it to the disclosure log. For vendors, store signed BAAs and scope statements. Keep training attendance records and materials. Document incidents: the AMA notes that notification must occur within 60 days of discovery, so record the date of discovery and each notification sent.
6. Conduct Regular Internal Audits and Risk Assessments
At least annually, review policies, logs, access privileges, vendor relationships and training status. Perform a risk analysis to identify threats such as ransomware or insider misuse. Document findings, corrective actions and follow‑ups. During the 2024–2025 OCR audits, ransomware and hacking were highlighted as ongoing threats; a regular internal review helps you stay ahead of these risks.
7. Prepare and Use Templates
Busy teams benefit from standardized templates. Create templates for audit logs, authorization forms, incident reports, training records and BAAs. Adopt software or managed services that automate evidence collection and retention. Konfirmity’s clients shorten readiness timelines and reduce evidence‑gathering effort by roughly three‑quarters. The result: HIPAA Evidence Requirements are met as part of normal work.
Practical Examples
Real scenarios illustrate how evidence supports compliance:
- Detecting unauthorized access. During a Konfirmity‑supported audit, a healthcare client’s access logs showed that a receptionist logged into the EHR at 2 a.m. from an offsite IP and attempted to export a patient list. Because the audit trail captured the user, time, and action, the security team responded quickly, revoked access and launched an investigation. The evidence supported an incident report and allowed the organisation to demonstrate its monitoring capability.
- Lost laptop with ePHI. A physician’s unencrypted laptop containing appointment schedules was stolen from a vehicle. Incident records documented the date, device details, number of patients affected, risk assessment and mitigation. Notifications were sent within the 60‑day window. During an OCR inquiry, the organisation produced the incident report and proof of encryption being rolled out since.
- Vendor access to PHI. A billing vendor accessed claims data under a BAA. When a breach occurred at the vendor’s system, the provider produced the signed BAA, access logs showing the vendor’s use, and the authorization records allowing the disclosure. This evidence showed that the provider had exercised due diligence.
- Training documentation. In a 2024 audit, auditors requested proof of workforce training. The provider supplied a log of quarterly training sessions, attendance sheets and acknowledgements. Evidence showed that staff were trained on data handling, phishing awareness and incident reporting.
These cases show how meeting HIPAA Evidence Requirements helps manage incidents and satisfy auditors.
Ready‑to‑Use Templates
Below are simplified template structures. Adjust fields to suit your environment.
Access / Audit Log Template
Authorization Form Template
Incident / Breach Report Template
Training Log Template
Business Associate Agreement Template
Data‑Flow Checklist
List sources of PHI, storage systems, access points, transmission channels and third‑party connections. Include diagrams where possible.
Tips and Best Practices
- Automate evidence collection. Use tools that generate and store audit logs, manage BAAs and track training. Manual spreadsheets break under scale.
- Review regularly. Audit logs and policies should be reviewed periodically and after any significant change. Automation helps identify anomalies quickly.
- Train continuously. Conduct onboarding and refresher training and maintain attendance records. Well‑trained staff reduce the risk of incidents.
- Align with other frameworks. Map HIPAA controls to SOC 2 Trust Services Criteria, ISO 27001 Annex controls and GDPR requirements. Cross‑framework reuse reduces duplication. Konfirmity clients commonly build a single evidence repository that satisfies SOC 2, ISO 27001 and HIPAA.
- Engage partners responsibly. Ensure BAAs specify obligations, reporting timelines and security controls. Monitor vendors’ compliance through periodic reviews and require breach notices.
- Focus on security first. Evidence flows naturally from real security programs. In Konfirmity’s 6,000+ audits, teams that implemented least‑privilege access, vulnerability management and incident response processes passed audits with fewer findings and closed deals faster.
Conclusion
The regulatory and threat landscape is unforgiving. OCR’s 2024–2025 audit programme targets ransomware and hacking, while the HIPAA Journal reports that 2023 saw 168 million healthcare records exposed and 2024 breaches surpassed 276 million records. IBM’s 2024 study shows healthcare breaches cost $10.93 million on average and remain undetected for months. These facts underscore why HIPAA Evidence Requirements cannot be an afterthought.
Building durable evidence is about more than ticking boxes. It requires mapping data flows, designing robust controls, logging every access and training your people. Start with security and arrive at compliance. Konfirmity’s human‑led managed service delivers continuous control operation and year‑round evidence collection while reducing manual effort. Insist on controls that withstand auditors and attackers. Make documentation part of your routine so that audits, deals and patient trust follow naturally.
Frequently Asked Questions
1. What are the five rules of HIPAA?
HIPAA’s Administrative Simplification provisions include the Privacy Rule, Security Rule, Transactions and Code Sets Rule, Unique Identifiers Rule and Enforcement Rule. The Privacy Rule protects PHI, the Security Rule mandates safeguards, the Transactions and Code Sets Rule standardises electronic billing, the Unique Identifiers Rule mandates identifiers for providers and plans, and the Enforcement Rule outlines penalties and investigatory powers.
2. What are the three main rules most people refer to?
The Privacy Rule governs PHI uses and disclosures, the Security Rule covers ePHI safeguards and the Breach Notification Rule requires notification after impermissible uses or disclosures.
3. What are the three requirements of the “minimum necessary” rule?
There is no formal three‑part test, but complying means: (a) disclose only the least PHI needed for the purpose; (b) evaluate whether the purpose can be achieved using de‑identified data or limited datasets; and (c) document the decision and justification for each use or disclosure.
4. What documentation is legally required under HIPAA?
Covered entities and business associates must maintain policies, procedures, risk analyses, audit logs, access logs, incident reports, training records and BAAs. Documentation must be retained for at least six years. Without these records, it is impossible to meet HIPAA Evidence Requirements or respond to audits and breach investigations.





.svg)






.svg)
.svg)