Most enterprise health‑tech buyers now request proof of cybersecurity readiness before procurement. Without a credible HIPAA Incident Response Plan and continuous evidence, business development stalls—even when teams think they’re audit‑ready on paper. In 2025–2026 the U.S. Department of Health and Human Services (HHS) sharpened its enforcement posture, highlighting record‑setting breaches, new cybersecurity performance goals and an ongoing audit program revival. For covered entities and business associates, the only viable way to satisfy regulators and assure customers is to combine strong security controls with rigorous incident response, documentation and compliance reporting. This article walks through the essential components of a HIPAA Incident Response Plan and shows how Konfirmity’s human‑led, managed security service keeps healthcare organizations audit‑ready year‑round.
Why Have a HIPAA Incident Response Plan?
At its core, a HIPAA Incident Response Plan is a documented playbook for recognizing, containing, and reporting events that threaten protected health information (PHI). Unlike generic incident response documents, a HIPAA Incident Response Plan integrates specific regulatory requirements under the HIPAA Security Rule, Breach Notification Rule and Privacy Rule. It addresses not just the technical aspects of containment but the legal obligations to patients, regulators and business partners.
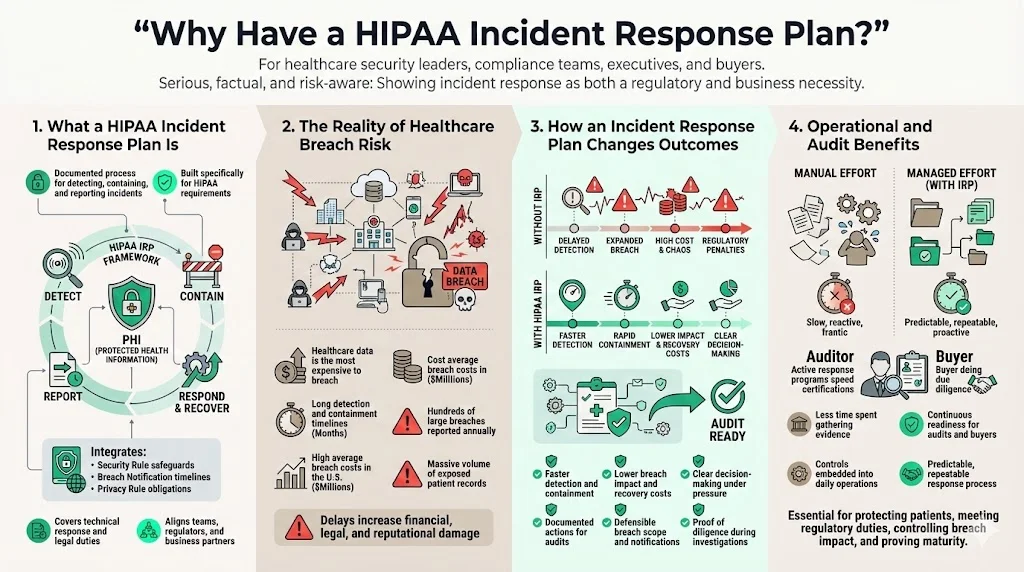
Healthcare data remains the costliest target for attackers. IBM’s 2025 Cost of a Data Breach report found that U.S. breach costs reached $10.22 million on average—more than double the global average of $4.44 million—with healthcare breaches averaging $7.42 million. These incidents take an average of 279 days to detect and contain. Meanwhile, HHS logged 747 large healthcare data breaches in 2023, exposing more than 168 million records. A carefully designed HIPAA Incident Response Plan shortens breach lifecycles, reduces costs and proves compliance during audits and due‑diligence reviews.
Konfirmity has supported more than 6,000 audits across SOC 2, ISO 27001, HIPAA and GDPR. Our experience shows that organizations who operate an active incident response program achieve certification in 4–5 months and spend around 75 hours per year on evidence collection, compared to 9–12 months and 550–600 hours when attempting a self‑managed approach. By embedding control implementation, monitoring and remediation into your stack, we keep your program ready for both auditors and buyers.
What Is a HIPAA Incident Response Plan?
A HIPAA Incident Response Plan is a structured set of policies, roles, procedures and technologies that guide an organization’s actions when a security incident or breach involving PHI occurs. It has several distinguishing features:
- Regulatory scope: The plan explicitly addresses HIPAA’s Security Rule, Breach Notification Rule and Privacy Rule. It ensures that incidents are assessed against the definition of a breach (“acquisition, access, use or disclosure of PHI in a manner not permitted under the Privacy Rule that compromises the security or privacy of the PHI”) and that reporting obligations are met.
- PHI‑centric: PHI is subject to heightened confidentiality and integrity protections. The plan defines how to protect PHI in electronic, paper and verbal form and documents where PHI flows across systems and vendors.
- Comprehensive evidence management: The plan covers documentation required during audits and breach investigations—log reviews, incident timelines, forensic reports and risk assessments. These artifacts demonstrate that the organization acted promptly and followed industry standards.
How It Differs from Generic Cybersecurity Plans
Most organizations maintain some form of incident response process, but general plans often focus narrowly on containment and recovery. A HIPAA Incident Response Plan adds several layers:
- Regulatory obligations: Under 45 CFR 164.400‑414 the Breach Notification Rule obligates covered entities to notify affected individuals and the HHS Secretary within 60 days (or by the end of the calendar year for breaches affecting fewer than 500 individuals). Media notification is also required for incidents impacting more than 500 individuals. A generic plan typically lacks these legal triggers.
- Distinguishing incidents from breaches: HIPAA requires organizations to decide whether an event constitutes a breach. An incident is any attempted or successful unauthorized access, use, disclosure, modification or destruction of information. A breach is presumed unless the organization demonstrates a “low probability that the PHI has been compromised”. This assessment drives notification.
- Business associate obligations: Business associates must notify covered entities of breaches within 60 days and may be delegated responsibility for breach notifications. The plan addresses coordination between covered entities and business associates.
- Evidence depth: HIPAA auditors often review security logs, access reviews, vulnerability scans and evidence of continuous monitoring. The plan integrates these controls and maps them to other frameworks such as SOC 2 Trust Services Criteria and ISO 27001 Annex A controls, facilitating cross‑framework reuse of controls and evidence.
Why It Matters for Healthcare
Protecting patients and managing risk. Healthcare data drives care decisions, billing and research. A breach can disrupt operations, delay treatment and erode trust. According to IBM’s 2025 report, nearly all organizations studied suffered operational disruption after a breach and took more than 100 days to recover. Longer breach lifecycles mean greater exposure of PHI, higher remediation costs and regulatory penalties. A HIPAA Incident Response Plan helps reduce the time to detect and contain incidents and provides steps to minimize harm.
Compliance and financial impact. HIPAA penalties can reach $1.5 million per violation category per year, and settlements now share funds with victims under the HITECH Act. OCR’s 2025 revival of the HIPAA audit program focuses on risk analysis and risk management, making a documented plan critical. Implementing recognized security practices for 12 months can reduce penalties and audit duration.
Trust and market access. Enterprise buyers, insurers and partners increasingly require proof of a mature security program, including an incident response playbook and evidence of continuous monitoring. Lacking a credible plan delays procurement and can disqualify vendors. By aligning with SOC 2, ISO 27001 and GDPR requirements, a HIPAA Incident Response Plan demonstrates disciplined operations and opens doors to larger contracts.
Core Components of a HIPAA Incident Response Plan
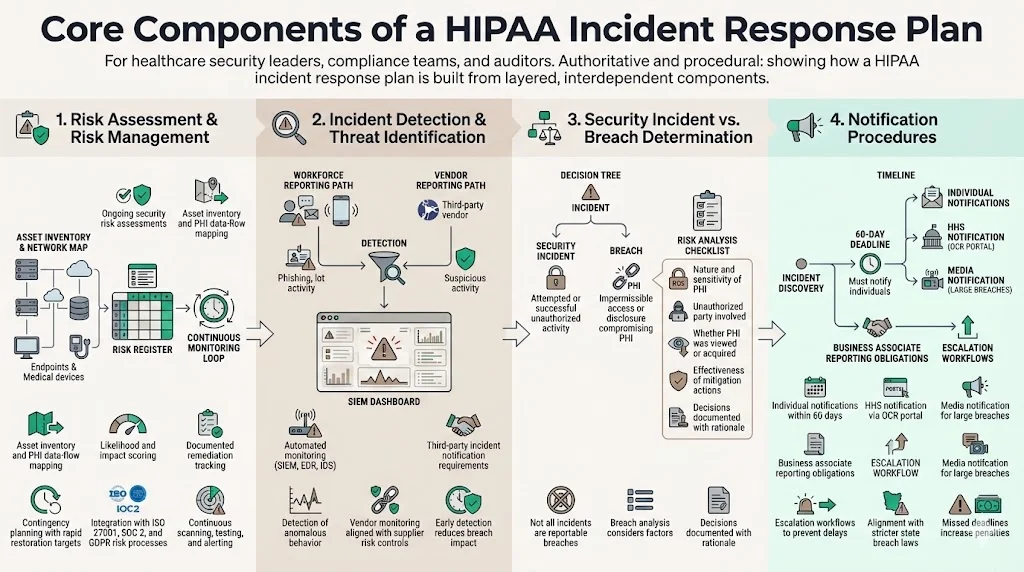
1. Risk Assessment & Risk Management
The foundation of any HIPAA Incident Response Plan is a rigorous, ongoing risk assessment program. Under the proposed 2025 HIPAA Security Rule update, covered entities must develop and maintain a technology asset inventory and network map and review them at least annually. Risk analysis must identify reasonably anticipated threats, vulnerabilities and predisposing conditions, and assess likelihood that threats will exploit vulnerabilities. Formal contingency planning must ensure data restoration within 72 hours.
Best practices include:
- Annual security risk assessments: Identify threats to confidentiality, integrity and availability of ePHI. Document vulnerabilities, assign risk levels based on likelihood and impact, and track remediation actions.
- Asset inventory and data flow mapping: Understand where PHI resides and how it moves across systems and vendors. This mapping is essential for scoping incident investigations and verifying that containment actions cover all affected systems.
- Continuous monitoring: Conduct vulnerability scans every six months and penetration tests at least annually. Integrate alerting with security information and event management (SIEM) tools to detect anomalies early.
- Integration with other frameworks: Map risk assessments to ISO 27001 risk treatment plans, SOC 2 security and availability criteria, and GDPR Data Protection Impact Assessments (DPIAs). This cross‑framework approach reduces duplication and provides consistent evidence across audits.
2. Incident Detection & Threat Identification
Early detection reduces breach costs. The average breach lifecycle in healthcare is 279 days, which is five weeks longer than the global average. A HIPAA Incident Response Plan should define detection mechanisms that shorten this timeframe:
- Automated monitoring: Deploy SIEM tools, endpoint detection and response (EDR) solutions and intrusion detection systems to identify unusual patterns such as excessive login attempts, suspicious outbound traffic or unauthorized file transfers. Align detection thresholds with baseline behaviors and update them as the environment evolves.
- Human reporting: Train staff to report phishing, lost devices or suspicious behavior. Encourage a “see something, say something” culture. Under HIPAA, attempted unauthorized access counts as a security incident; prompt reporting ensures incidents are assessed quickly.
- Third‑party monitoring: Require business associates to notify you of security incidents and provide logs or evidence necessary for investigation. Integrate vendor risk management into detection processes, aligning with SOC 2 vendor risk criteria and ISO 27001 control A.15.
3. Defining Security Incident vs. Breach
Understanding when an event triggers HIPAA’s breach notification requirements is crucial. A “security incident” is any attempted or successful unauthorized access, use, disclosure, modification or destruction of information. A breach, under the Breach Notification Rule, is “the acquisition, access, use or disclosure of PHI in a manner not permitted under the Privacy Rule which compromises the security or privacy of the PHI”. Not all incidents are breaches: for example, a failed login attempt or an encrypted data theft might be a security incident but not a reportable breach if risk analysis concludes there is a low probability that PHI has been compromised.
Assessing whether an incident is a breach involves:
- Evaluating the nature and extent of PHI involved: Was sensitive information such as diagnoses or financial data exposed? The more sensitive the data, the higher the risk.
- Identifying the unauthorized party: Was the information acquired by an employee, a vendor or an outside attacker? Determine the potential for re‑use of the data.
- Assessing whether the PHI was actually viewed or acquired: If an unauthorized party never accessed the data (for instance, an encrypted laptop stolen but never decrypted), it may not be a breach.
- Mitigation measures: If prompt actions (e.g., remote wipe, encryption) reduce risk of compromise, the event might remain classified as an incident. Document the analysis and rationale.
4. Notification Procedures
The HIPAA Breach Notification Rule specifies who must be notified and when. A HIPAA Incident Response Plan should outline these steps clearly:
- Notify individuals: All individuals whose unsecured PHI was accessed, acquired, used or disclosed must be notified within 60 days of discovery. Notifications should explain what happened, what information was involved, steps taken to mitigate harm, future preventive measures and how individuals can protect themselves.
- Notify HHS: For breaches affecting 500 or more individuals, a covered entity must notify the HHS Secretary without unreasonable delay and no later than 60 days after discovery. Breaches affecting fewer than 500 individuals must be reported within 60 days of the end of the calendar year. Notifications are submitted via the OCR portal.
- Notify the media: For breaches impacting 500 or more individuals, the entity must inform prominent media outlets in the affected jurisdictions within 60 days. This ensures individuals who cannot be reached directly are alerted.
- Business associate reporting: Business associates must report breaches to the covered entity without unreasonable delay and no later than 60 days from discovery. The HIPAA Incident Response Plan should define how business associates communicate incidents and provide details needed for notifications.
Failing to meet these timelines can lead to significant penalties. In 2017, Presence Health paid $475,000 to settle a case solely for exceeding the 60‑day notification window. The plan should require escalation procedures to avoid delays and include workflows to verify compliance with state breach notification laws, which may have shorter timelines.
Assembling Your Incident Response Team
NIST’s 2025 incident response guidance emphasizes that modern cybersecurity incidents are complex, requiring diverse expertise. It identifies roles such as leadership (decision‑making and resource allocation), incident handlers (verification and containment), technology professionals (security engineers, administrators, developers), legal counsel, public relations, human resources and, when necessary, third‑party responders. A HIPAA Incident Response Plan should define:
- Response team lead: Oversees the incident from detection through recovery, coordinates communication, and ensures regulatory deadlines are met. Often the CISO or a senior security manager.
- Technical responders: Security analysts, incident handlers and system administrators who investigate alerts, isolate affected systems, remove malware and restore services. They should have access to forensic tools and logging infrastructure.
- Compliance and legal counsel: Interpret HIPAA requirements, determine breach status, advise on notification obligations and engage with OCR or state regulators.
- Communications: Public relations or marketing professionals who craft statements for patients, partners and media, ensuring transparency while protecting the organization’s reputation.
- Executives: Provide funding, approve major actions (e.g., shutting down systems or paying for emergency services) and liaise with the board and external stakeholders.
- Third‑party specialists: Managed security service providers, digital forensics firms or law enforcement agencies may be engaged for complex incidents. Contracts should define scope, timelines and evidence handling.
Konfirmity’s model assigns a dedicated response leader supported by audit and technical specialists. We act as an extension of your team, ensuring that alerts, evidence and notifications are managed continuously and consistently across your infrastructure. This shared‑responsibility approach mirrors NIST’s recommendation for “federated” incident response teams.
Step‑by‑Step Incident Response Workflow
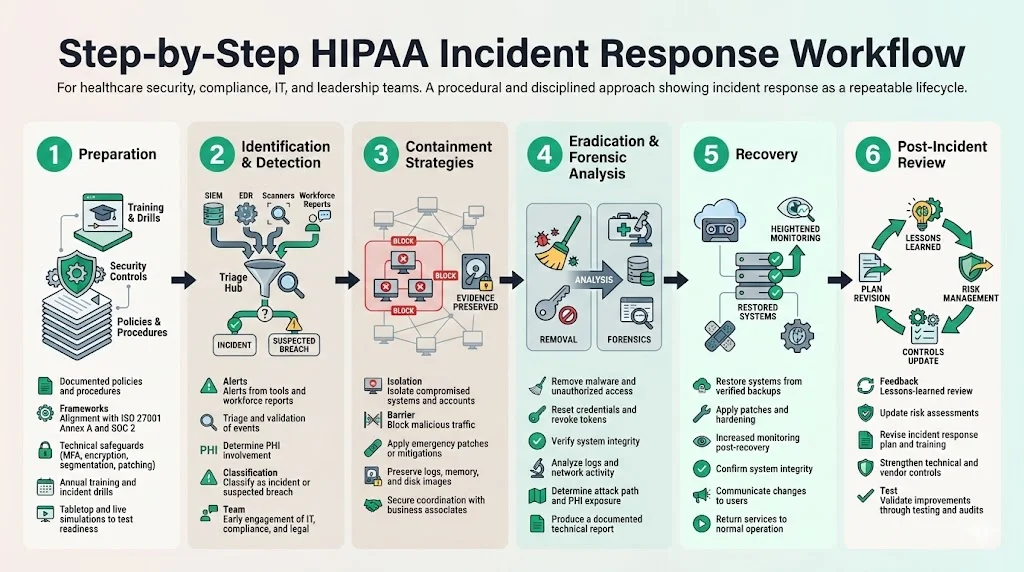
1. Preparation
Preparation lays the groundwork for effective response. Key actions include:
- Policies and procedures: Maintain formal policies covering acceptable use, encryption, access control, device management and incident response. Ensure alignment with SOC 2 security, availability and confidentiality criteria and ISO 27001 Annex A controls.
- Security architecture and controls: Deploy technical safeguards such as multifactor authentication, network segmentation, encryption of ePHI at rest and in transit, anti‑malware, and patch management. Ensure business associates adhere to similar controls.
- Training: Conduct annual HIPAA training and incident response drills for all workforce members. Provide scenario‑based exercises—ransomware, phishing, lost device—that test detection, escalation and communication procedures. Training reduces the risk of breaches and ensures timely detection.
- Tabletop and live drills: Simulate incidents with cross‑functional teams. Evaluate decision‑making, information flow and regulatory compliance. Use results to refine the plan and correct control gaps.
2. Identification & Detection
When potential incidents surface, responders must quickly determine whether an event has occurred and its scope. Steps include:
- Receive alerts: From SIEM tools, intrusion detection systems, endpoint agents, vulnerability scanners or employee reports.
- Triage: Validate the alert, gather relevant context (e.g., affected system, user activity, network traffic) and determine whether it relates to PHI.
- Classify: Decide if the event is a security incident or a suspected breach. If PHI may be involved, document all details to support breach risk analysis and potential regulatory reporting.
- Activate the team: Notify the response team lead and assemble appropriate stakeholders (IT, compliance, legal) to plan containment. Early involvement of legal counsel helps interpret breach definitions and privileges.
3. Containment Strategies
Containment aims to limit further damage while preserving evidence. Options vary based on incident type:
- Isolate affected systems: Remove compromised devices from the network, disable user accounts, block malicious IP addresses or quarantine endpoints. Network segmentation and least‑privilege access reduce lateral movement opportunities.
- Apply emergency patches or configuration changes: If a vulnerability is exploited, patch systems or implement temporary mitigations (e.g., disable services, restrict ports). Document all changes for later review.
- Preserve forensic data: Capture memory dumps, disk images, system and network logs. Record the timeline of events, who performed actions and what data was accessed. Evidence preservation is critical for root cause analysis, regulatory inquiries and potential legal proceedings.
- Coordinate with business associates: If the incident involves a vendor, instruct them to contain systems and share forensic information. Ensure that communication channels are secure and that evidence is not compromised.
4. Eradication & Forensics Analysis
Once immediate threats are contained, focus turns to removing malicious artifacts and understanding the root cause:
- Remove malware or unauthorized users: Use antivirus tools, EDR and manual procedures to eradicate malicious code. Reset credentials and revoke tokens.
- Assess system integrity: Verify that system files and configurations haven’t been tampered with. Restore clean versions from backups if necessary.
- Conduct forensic analysis: Analyze logs, network traffic and file hashes to identify how the attacker gained access, what actions were performed, and whether PHI was exfiltrated. Document every finding. Where required, involve external forensic experts to ensure impartiality.
- Communicate findings: Provide leadership with a technical report summarizing the root cause, the attack path and systems affected. Include recommendations for remediation and improvements.
5. Recovery
Recovery focuses on restoring normal operations while ensuring that vulnerabilities have been mitigated:
- Restore systems: Bring systems back online from clean backups. Ensure that backups are free of malware and that patched software is installed.
- Monitor closely: After systems are restored, monitor for signs of reinfection or residual attacker activity. Tighten logging and alerting thresholds temporarily.
- Return to service: Once the system’s integrity is confirmed, return operations to business owners. Communicate to users any changes (e.g., new passwords or multi‑factor authentication) and ensure they understand how to avoid similar incidents.
6. Post‑Incident Review
After recovery, the organization must analyze the incident and improve its controls:
- Debrief: Conduct a “lessons learned” meeting with all stakeholders. Review the timeline, detection effectiveness, containment actions, communications and decision‑making. Identify what worked well and what needs improvement.
- Update risk assessments: Incorporate new threats and vulnerabilities identified during the incident. Adjust the risk register and prioritize remediation actions.
- Revise the plan: Modify policies, procedures and training based on lessons learned. For example, if detection lagged because logs were incomplete, update logging configurations or invest in improved monitoring.
- Strengthen controls: Address the root cause—patch vulnerabilities, harden configurations, enhance access controls, improve vendor assessments. Verify that improvements have been implemented through follow‑up audits and tests.
Training and Drills
Human error remains a leading cause of security incidents. Regular training ensures staff understand how to protect PHI and how to respond when something goes wrong. Key elements:
- Role‑based training: Tailor training to different roles—clinical staff, IT administrators, developers, executives and vendors. Emphasize that unauthorized access attempts, lost devices and misdirected communications should be reported immediately.
- Annual refreshers and updates: HIPAA requires that training occur periodically, and NIST recommends continuous improvement. Update training as threats evolve (e.g., new phishing techniques, AI‑driven attacks) and as policies change.
- Simulation exercises: Conduct tabletop and live‑fire drills. Use realistic scenarios (ransomware, insider breach, third‑party compromise) to test detection, containment and notification procedures. Evaluate performance against key metrics (time to detection, time to containment, time to notification) and refine the plan.
Documentation and Regulatory Reporting
Documentation provides evidence that the organization acted appropriately and supports audits, investigations and due‑diligence inquiries. A HIPAA Incident Response Plan should specify how to document:
- Incident timeline: Start and end times, detection method, actions taken, system changes and notifications issued. This timeline demonstrates adherence to the 60‑day notification requirement and shows how quickly the incident was contained.
- Forensic evidence: Logs, memory images, network packets and any other artifacts collected. Store evidence securely and ensure chain of custody.
- Risk analysis and decision rationale: Document how the organization determined whether the incident was a breach. Explain factors considered (type of data, risk of re‑identification, mitigations) and conclusions.
- Notifications: Keep copies of letters sent to individuals, HHS and media, along with dates of mailing and responses received.
- Remediation actions: Record patches applied, configuration changes, policy updates and training improvements.
Regulatory reporting deadlines require careful tracking. The plan should include checklists and templates for breach notifications to individuals and the HHS Secretary. For multi‑state operations, maintain a matrix of state breach notification laws. Leverage automation where possible to generate and submit reports.
Integrating Incident Response with Broader Security Protocols
A HIPAA Incident Response Plan must operate within the organization’s overall security program. Integration points include:
- Risk management framework: Align incident response with your ISO 27001 risk treatment plans and Statement of Applicability. Use SOC 2 Type II Trust Services Criteria (security, availability, confidentiality) to define control objectives and measure effectiveness. Map controls across frameworks to reuse evidence and reduce duplication.
- Continuous monitoring: Incorporate incident response metrics into continuous control monitoring. For example, track mean time to detect (MTTD), mean time to respond (MTTR) and compliance with vulnerability remediation SLAs. Use these metrics to inform board reports and procurement questionnaires.
- Vendor risk management: Integrate business associate security reviews into vendor onboarding and periodic assessments. Require evidence of incident response capabilities (e.g., playbooks, training records) and update contracts with reporting obligations.
- Data privacy: Coordinate with GDPR and other privacy regulations. Conduct Data Protection Impact Assessments (DPIAs) when new systems or vendors process PHI. Ensure that incident response covers cross‑border data transfers and privacy rights (e.g., right to be informed, right to access).
Conclusion
Security programs that look good on paper but fail under incident pressure create business risk. In a time of escalating breach costs and heightened regulatory scrutiny, healthcare organizations must build controls that stand up to auditors, buyers and attackers. A HIPAA Incident Response Plan provides the blueprint: continuous risk assessment, early detection, clear criteria for distinguishing incidents from breaches, defined notification procedures, a trained response team, a step‑by‑step workflow and rigorous documentation.
Konfirmity’s human‑led, managed service goes further by embedding these controls inside your technology stack, monitoring them daily and executing on your behalf. We start with security and arrive at compliance. By implementing durable security and evidence collection—from risk assessments to access reviews and vendor risk management—we help you stay audit‑ready and maintain the trust of patients and enterprise partners. Build the program once, operate it every day, and let compliance follow.
FAQs
1. What counts as a reportable breach under HIPAA?
A breach is an impermissible acquisition, access, use or disclosure of PHI that compromises its security or privacy. Incidents are presumed to be breaches unless the covered entity demonstrates a low probability that the PHI has been compromised through risk analysis. Factors include the nature of data, unauthorized parties, whether data was actually viewed and mitigation actions.
2. How soon must I notify individuals after discovering a breach?
Covered entities must notify affected individuals without unreasonable delay and no later than 60 days after discovery. Do not wait for the end‑of‑year reporting period for smaller breaches; letters should be sent promptly and include details about the breach, mitigation steps and how individuals can protect themselves.
3. Do all employees need incident response training?
Yes. NIST stresses that incident response requires participation from leadership, technical staff, legal counsel, communications and human resources. All employees should know how to report suspected incidents and follow the organization’s escalation procedures. Role‑based training ensures that each group understands its responsibilities during a security event.
4. What’s the difference between incident detection and response?
Detection involves identifying potential cybersecurity attacks or compromises through monitoring and reporting. Response encompasses the actions taken to manage, prioritize, contain, eradicate and recover from the incident, as well as communications and regulatory reporting. Both stages are critical: rapid detection minimizes damage, while an organized response ensures timely containment and compliance with HIPAA and other frameworks.





.svg)




.svg)
.svg)