Healthcare has become an information‑centric industry. Providers and insurers now operate cloud‑native platforms, handle remote monitoring devices and rely on real‑time data flows. To support this scale they are moving from monolithic applications to HIPAA Microservices architectures. Each service can be developed and deployed independently, enabling teams to add new features or fix issues without halting the entire system. However, this agility introduces fragmentation. More components and interfaces mean more ways data can be exposed. For organizations handling electronic protected health information (ePHI), the stakes are high. Regulatory fines in the United States are rising; an IBM study published in July 2025 reported that the average cost of a data breach climbed to $10.22 million in the U.S., up 9.2% from 2024.
The same report showed that healthcare breaches remain the costliest across industries, averaging $7.42 million, and that breaches take an average of 279 days to identify and contain. These figures illustrate why security and compliance cannot be an afterthought when designing distributed systems. This article explains how HIPAA’s administrative, physical and technical safeguards apply to microservices. It draws on government publications, industry best practices and Konfirmity’s experience supporting over 6,000 audits across HIPAA, SOC 2, ISO 27001 and GDPR. The goal is to help chief technology officers, security leaders and compliance officers build systems that scale while protecting patient privacy.
Why microservices are becoming common in healthcare systems
Traditional healthcare software consists of large, tightly coupled applications that rely on a single database. Changes require coordinated releases and long maintenance windows. Microservices break this up. Each service implements a discrete capability—like patient registration, scheduling or billing—runs on its own infrastructure and communicates with other services through APIs. HealthManagement.org notes that breaking large, complex applications into smaller, self‑contained units allows providers to iterate and modernize more efficiently without disrupting entire systems. Independent services also allow teams to use different languages and technologies suited to their tasks, simplifying scaling and maintenance. Another advantage is resilience: if one service fails, others continue operating, reducing downtime in critical environments. Microservices align with container orchestration platforms such as Kubernetes, which automate deployment, scaling and fail‑over. For healthcare organizations dealing with changing regulations and insurance models, these properties make microservices attractive.
Despite these benefits, distributed systems increase the number of network edges. Each service exposes an API, often publicly via the internet. Without careful design, microservices can become chatty, exchanging sensitive data unnecessarily or replicating patient records across multiple databases. Attackers target these new surfaces. The 2025 IBM breach report found that supply‑chain compromises and shadow IT significantly raise breach costs. Healthcare networks already face relentless ransomware campaigns and credential theft; microservices amplify these risks. Balancing speed and security is therefore central to any modern healthcare platform.
What HIPAA actually regulates
HIPAA sets out standards for protecting health information in the United States. Two groups must comply: covered entities (providers, insurers and clearinghouses) and business associates that handle ePHI on their behalf. HIPAA defines electronic protected health information as individually identifiable health information created, received, maintained or transmitted in electronic form. The 2024 NIST guidance emphasises that risk assessment and risk management processes are foundational to HIPAA compliance and that no specific methodology is prescribed. Instead, organizations must implement policies and procedures to prevent, detect, contain and correct violations. Two of the Security Rule’s required implementation specifications are particularly relevant: Risk Analysis, which requires a thorough assessment of potential risks and vulnerabilities to the confidentiality, integrity and availability of ePHI, and Risk Management, which mandates security measures to reduce risks to a reasonable and appropriate level.
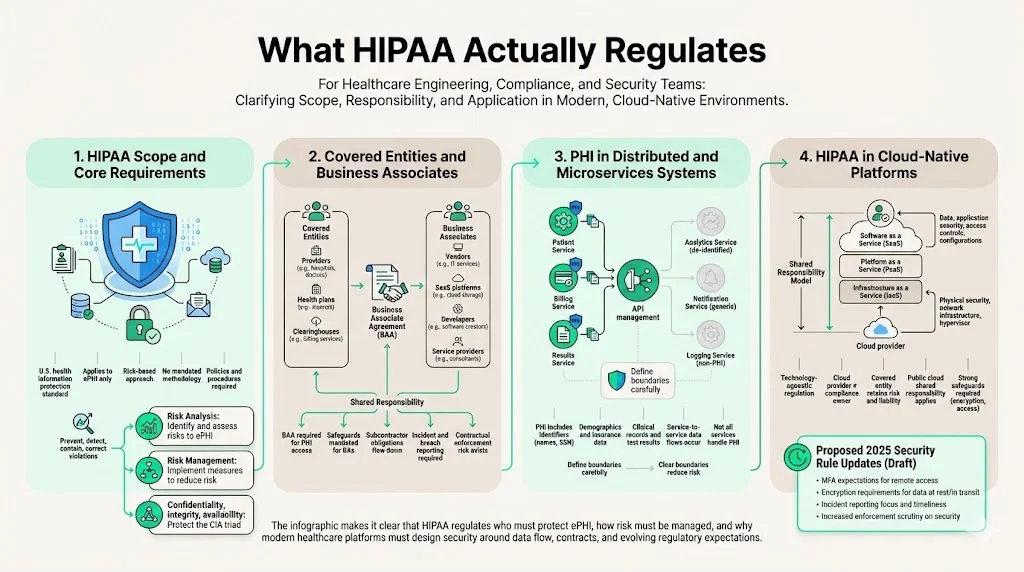
Covered entities and business associates
Covered entities include healthcare providers, health plans and clearinghouses. Business associates are vendors, software developers and service providers that create, receive, maintain or transmit ePHI on behalf of a covered entity. Under HIPAA, both must sign a business associate agreement (BAA) specifying how ePHI will be protected. The NIST guide notes that contracts must require business associates to implement administrative, physical and technical safeguards and to ensure that any subcontractors do the same. The BAA should include provisions for reporting security incidents and breaches. Microservices teams must understand these contractual obligations, as failing to establish BAAs has resulted in enforcement actions. In 2024 the Office for Civil Rights (OCR) issued 22 settlements and civil monetary penalties, many citing the absence of BAAs or failure to restrict access to ePHI.
Protected Health Information in distributed systems
PHI can include demographic data, medical histories, test results, insurance information and any identifiers that link to an individual. In a microservices architecture, PHI may flow between services for scheduling, billing and clinical decision support. Each service must know whether it handles PHI. Some components, such as a notification service that sends appointment reminders, may only process patient names and phone numbers; others, like an EHR service, hold detailed medical histories. Defining these boundaries is critical to minimise risk.
How HIPAA applies to cloud‑native healthcare platforms
HIPAA is technology‑agnostic. It requires covered entities and business associates to implement safeguards appropriate to the level of risk. A cloud‑native platform may use infrastructure managed by public cloud providers. The covered entity still owns the risk. The proposed updates to the HIPAA Security Rule released by HHS in January 2025 underscore this responsibility. The Notice of Proposed Rulemaking explains that the revisions aim to address changes in the healthcare environment, significant increases in breaches and common deficiencies observed in OCR investigations. The rule would strengthen the security of ePHI by revising standards to better protect confidentiality, integrity and availability. While still pending, these changes signal more stringent requirements around cybersecurity hygiene, such as multi‑factor authentication, encryption and incident reporting. Healthcare microservices platforms must be prepared to meet these evolving standards.
Why microservices change the security conversation
Moving from monoliths to a distributed application architecture fundamentally alters the threat model. In a monolithic system, security controls—authentication, authorization, logging—are implemented centrally. A microservices architecture decentralizes these controls across many independently deployed services. This increases the attack surface; each service has its own API, network configuration and dependencies. Attackers can probe for misconfigured endpoints, weak authentication or insecure communication. They can move laterally between services if internal communication is not properly authenticated.
Regulators are paying attention. The 2024 NIST guide highlights that audit controls must be scaled to match the scope of systems containing ePHI. For microservices, this means capturing and reviewing logs from every service, not just at the edge. The HIPAA Security Rule also requires mechanisms to authenticate that ePHI has not been altered or destroyed improperly. If services pass data between each other, organizations must verify the integrity of that data at each hop. Moreover, business associate agreements must flow down to subcontractors and require subcontractors to meet the same security standards. In a microservices environment where third‑party APIs and cloud services are common, these contractual chains become complex. Failure to manage them has led to penalties; for example, Montefiore Medical Center paid $4.75 million in 2024 for not conducting a thorough risk analysis and for failing to implement procedures to regularly review system activity.
Core HIPAA requirements that affect microservices
Administrative safeguards
The Security Rule’s administrative requirements focus on risk management, workforce training and policies. The NIST guide stresses that risk assessment and management are required but flexible processes. For microservices, risk analysis should map each service’s data flows, dependencies and potential threats. Questions include: Which services handle ePHI? Where is ePHI stored? How is access controlled? In Konfirmity’s experience conducting over 6,000 security audits, many healthcare startups underestimate the effort needed to inventory services and document data flows. A proper risk analysis often takes 4–5 months when done manually, whereas teams using managed services can reduce that timeline to 4–5 weeks for initial readiness. Once risks are identified, organizations must implement controls to reduce them to an acceptable level. This may mean choosing encryption at rest, implementing multi‑factor authentication for administrative APIs or limiting network ingress.
Vendor oversight is another administrative requirement. The Security Rule’s section on business associate contracts mandates that contracts require vendors to implement appropriate safeguards. In distributed systems, vendors may provide cloud infrastructure, identity management, messaging queues or analytics. Each vendor relationship must include a BAA, and the covered entity must verify that the vendor’s security program aligns with HIPAA requirements. Konfirmity often sees teams adopt SaaS tools without reviewing whether they handle ePHI or whether a BAA is required. This oversight becomes a common finding in audits.
Policies before code means documenting procedures for access control, incident response, change management and workforce training. Policies must exist and be communicated before services are deployed. During audits, evidence that these policies are followed is as important as the documents themselves. SOC 2 and ISO 27001 audits examine whether change‑management tickets, access reviews and security training logs exist over an observation period of three to twelve months. In a microservices environment, automated pipelines should enforce policy compliance by requiring security scans and approvals before deployment.
Physical safeguards
Physical safeguards refer to controlling physical access to systems and protecting equipment. In cloud environments, physical security is primarily the responsibility of the cloud provider. Covered entities must ensure that their providers offer secure data centers and that they implement device encryption and access controls for on‑premises equipment. The NIST guide advises covered entities to consider encryption and automatic logoff on devices that access ePHI. When using public cloud services, review the provider’s SOC 2 and ISO 27001 reports to verify that data centers are protected and that proper environmental controls, backup power and disaster recovery measures exist. Business associates should be willing to share evidence such as penetration test results, audit reports and physical security certifications.
Technical safeguards
Technical safeguards cover access control, audit controls, integrity and transmission security. The NIST guide lists required implementation specifications, including:

- Access control: Implement unique user identification, emergency access procedures, automatic logoff and encryption. Organizations must assign unique IDs to each user and restrict access based on job functions. They must ensure that only authorized personnel or services can access ePHI. Fine‑grained authorization should be implemented at the API level using role‑based or attribute‑based policies, and tokens should be short‑lived. The OWASP and Kong security guides recommend mutual TLS (mTLS) and token-based systems for service‑to‑service authentication and authorization.
- Audit controls: Record and examine system activity. NIST provides sample questions to determine what activities should be audited: creating, accessing, modifying, transmitting or deleting ePHI; what the audit record should include (user, event type, date/time); and whether audit records are generated for all systems that create, store or transmit ePHI. For microservices, centralized logging is essential. Each service should emit structured logs that include user IDs, request identifiers, and access scopes. Logs should be forwarded to a secure, tamper‑evident repository. Automating log collection ensures evidence for HIPAA and SOC 2 audits.
- Integrity and authentication: Implement policies to protect ePHI from improper alteration or destruction. The guide suggests identifying all authorized users who can alter or destroy ePHI, detecting unauthorized sources and implementing mechanisms to authenticate ePHI. In microservices, this means implementing checksums or digital signatures on messages, enforcing immutability on critical data stores and using file integrity monitoring.
- Transmission security: Protect ePHI during transmission. HIPAA treats encryption as addressable rather than required, meaning organizations must assess whether encryption is appropriate. The NIST guide provides questions to evaluate whether encryption is needed and if available algorithms are of sufficient strength. Microservices should use TLS 1.2 or higher for all external and internal communication, with certificate rotation. Mutual TLS ensures both client and server are authenticated.
HIPAA Microservices and architecture alignment
Designing a HIPAA‑aware microservices architecture
A secure architecture starts with clearly defined service boundaries. Each service should handle only the data it requires. Segregating services by data sensitivity reduces the blast radius of a breach. For example, an appointment scheduling service may only handle patient identifiers and appointment times, while a clinical service handles diagnostic reports. The two communicate via an API that transmits only the necessary data fields. Avoid creating shared databases across services. Instead, use event-driven messaging or APIs to transfer data. Data minimization is a core principle; by limiting unnecessary replication, you reduce the risk of unauthorized access and simplify compliance with patient access requests.
Data minimization between services means designing APIs that return only required information and avoid embedding entire patient records. Implement field‑level encryption or tokenization for sensitive fields when possible. Where replication is unavoidable—such as caching for performance—ensure that caches are encrypted and have strict TTLs.
Healthcare interoperability without overexposure
Healthcare systems must interoperate internally and externally. Internally, services can communicate via private APIs or messaging queues. Externally, they may integrate with third‑party billing systems, laboratories or telehealth platforms. To avoid overexposure:
- Internal vs external APIs: Use private network segments for internal service communication. Expose only necessary endpoints through an API gateway. Apply strict authentication and authorization to both.
- Secure data exchange: Use standards such as HL7 FHIR for structured data exchange. When transferring ePHI to external systems, encrypt data in transit and use signed tokens or mutual TLS for authentication. Maintain a BAA with each external partner and verify their security posture.
- Managing third‑party integrations safely: Evaluate whether partners are business associates. Ensure contracts include reporting obligations for breaches. Validate third‑party APIs for input sanitation, rate limiting and encryption. Avoid directly connecting internal services to external endpoints; instead, use a brokered integration layer that can enforce policies and monitor traffic.
Securing APIs in HIPAA‑compliant microservices
API gateways are critical in a microservices architecture. They provide a centralized point to enforce authentication, authorization, rate limiting and logging. The Kong best practices article describes how API gateways authenticate tokens or API keys, enforce scopes, block unauthenticated requests and handle rate limiting to prevent denial‑of‑service attacks. Gateways also validate requests against OpenAPI specifications, sanitize input data and remove sensitive headers. By standardizing these controls, organizations can simplify compliance and reduce the chance of misconfiguration in individual services.
To align with HIPAA, API policies should tie access controls to user roles and service scopes. Transmission security must be enforced at the gateway using TLS. Centralized logging should capture request metadata, user identity and authorization decisions. For external APIs, implement signed tokens with short expiration to prevent token reuse and replay attacks. Rate limiting should consider both per-user and per-application thresholds to detect abuse. The gateway can also integrate with intrusion detection systems to trigger alerts on suspicious patterns.
Service‑to‑service security in healthcare systems
Securing internal communication
Within a microservices architecture, services communicate over the network. To prevent impersonation or man‑in‑the‑middle attacks, implement mutual TLS for all internal traffic. Kong’s guide recommends deploying SPIFFE/SPIRE to issue unique service identities and rotate certificates regularly. mTLS ensures that both client and server authenticate each other. Certificates should be short‑lived (24 hours or less) and managed by an automated certificate authority integrated with the service mesh.
Token-based authentication may be used in addition to mTLS. Services can exchange JSON Web Tokens (JWTs) issued by a centralized identity provider. The tokens include scopes and roles, enabling fine‑grained authorization at each service boundary. Use open standards such as OAuth 2.0 and OpenID Connect for issuing and validating tokens. Tokens should expire within minutes and be validated using a central policy engine (e.g., Open Policy Agent). Enforcing short-lived tokens reduces the window for replay attacks.
Preventing lateral movement inside the network requires network segmentation. Use Kubernetes network policies or cloud VPC segmentation to restrict which services can communicate. Default‑deny rules should block all traffic except explicitly allowed paths. The Kong guide provides sample policies for isolating services and controlling ingress and egress. Isolate sensitive data stores in private subnets and restrict administrative access. In addition, monitor east‑west traffic for anomalies and enforce micro‑segmentation within clusters.
Encryption in distributed healthcare systems
Encryption must protect ePHI both in transit and at rest. In transit, use TLS 1.2 or 1.3 with strong cipher suites. Mutual TLS provides service authentication and confidentiality. At rest, encrypt databases, message queues, caches and backups using AES‑256 or similar algorithms. Ensure that encryption keys are stored in a hardware security module (HSM) or a managed key management service. Rotate keys regularly and limit access to key custodians.
Key management strategies should address generation, rotation and revocation. Use separate keys for different environments (development, staging, production) and different data classifications. Maintain key metadata in a configuration management system and enforce versioning. Handling backups and replicas securely includes encrypting backup files, storing them separately from production systems and verifying restore procedures. Do not store secrets in container images or source code. Use secret management tools like HashiCorp Vault or cloud secret managers.
Data privacy compliance in a microservices world
Managing PHI across multiple services
In distributed systems, each service that handles ePHI must know what data it owns and its responsibilities under HIPAA. Establish data ownership by assigning a service owner responsible for security controls and compliance evidence. Avoid shared databases across services. Instead, implement domain‑driven design where each service owns its data. This reduces the risk of unauthorized cross‑service access and simplifies fulfilling patient access or deletion requests. When multiple services need to read or write the same data, use event sourcing or data pipelines to replicate only the required information, not entire records.
Handling patient consent and access requests requires coordination. When a patient exercises their right of access or requests restrictions, each service that stores the patient’s data must respond. Maintain a central registry mapping patients to services and automate retrieval. Logging and auditing are essential evidence that requests were fulfilled.
Logging, monitoring and audit trails
HIPAA requires mechanisms to record and examine system activity. The NIST guide provides detailed questions for implementing audit controls: what activities will be audited, what information each record should include, and how often audit logs will be reviewed. For microservices, each service should emit logs that include: service name, instance ID, timestamp, user or service identity, request and response metadata, authorization scope and outcome. Logs should be forwarded to a centralized platform that supports search and retention policies. Configure log retention to meet regulatory requirements and store logs in a write‑once, read‑many format to prevent tampering. Implement alerts for suspicious activity, such as repeated failed authentication attempts or unusual call patterns. Regularly review logs and perform audits as part of continuous monitoring.
Konfirmity’s managed service integrates logging with evidence collection. By automating log ingestion and linking logs to controls, clients reduce the audit preparation effort by 75% compared to manual processes. Evidence is collected continuously rather than during a hectic audit window, increasing audit success rates.
Common HIPAA risk areas in microservices
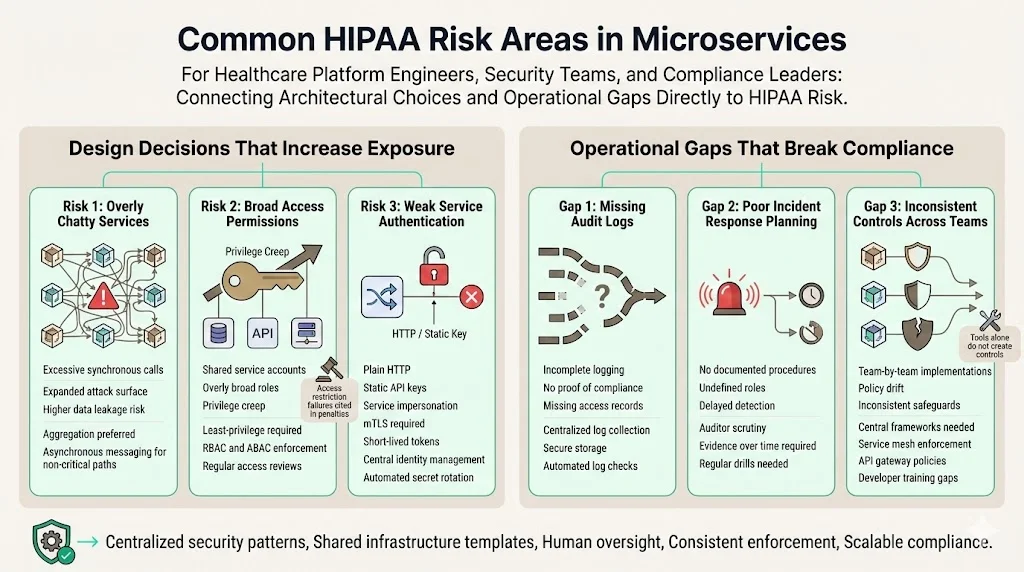
Design decisions that increase exposure
- Overly chatty services: Excessive inter‑service calls increase the attack surface and risk of data leakage. Design services to aggregate necessary information and minimize synchronous calls. Use asynchronous messaging for non‑critical operations.
- Broad access permissions: Assigning broad roles or using shared service accounts can lead to privilege creep. Implement the principle of least privilege. Use role‑based or attribute‑based access control and grant each service only the permissions it needs. Regularly review roles and rotate credentials. In 2024 several settlements cited failure to restrict access or review system activity as reasons for penalties.
- Weak service authentication: Using plain HTTP or static API keys allows impersonation. Always use mTLS and short‑lived tokens. Centralize identity management and rotate secrets automatically.
Operational gaps that break compliance
- Missing audit logs: Without comprehensive logs, organizations cannot demonstrate compliance. Ensure that services generate logs and that logs are collected and stored securely. Use automation to detect missing logs.
- Poor incident response planning: Auditors will examine how organizations detect and respond to incidents. The SOC 2 observation period requires evidence of incident handling over months. Document procedures, assign roles and conduct drills.
- Inconsistent security controls across teams: When multiple teams build services independently, controls may be inconsistent. Use centralized frameworks and infrastructure templates. Deploy service meshes and API gateways to enforce common policies. Provide training so that development teams understand HIPAA requirements. Konfirmity often observes that companies attempt to build compliance programs with off‑the‑shelf GRC software but struggle to implement real controls. A human‑led managed service helps establish standardized security practices across teams.
Practical templates and checklists
While each organization has unique requirements, standard templates can speed up implementation. Below are illustrative examples of what a HIPAA‑aware microservices security program might include. These are not exhaustive but offer a starting point.
HIPAA microservices security checklist
Pre‑deployment review
- Service inventory: List all microservices, their functions and data classifications.
- Risk analysis: Identify threats, vulnerabilities and potential impacts for each service.
- Access control review: Confirm unique user and service identities, least‑privilege roles and multi‑factor authentication.
- Encryption readiness: Ensure TLS is enabled for all communication and that databases, message queues and caches use encryption at rest.
- BAA status: Verify that business associate agreements exist with all vendors and subcontractors.
- Policy compliance: Confirm that policies (incident response, change management, backup) are documented and enforced.
Ongoing operational checks
- Audit log review: Schedule weekly or monthly reviews of logs across services.
- Vulnerability management: Track dependencies, scan containers and libraries regularly; apply patches within defined SLAs.
- Access reviews: Conduct quarterly user and service access reviews to remove unused privileges.
- Incident drills: Perform periodic tabletop exercises to test detection and response procedures.
- Vendor audits: Review vendor SOC 2 or ISO 27001 reports annually; update BAAs when services or scopes change.
Sample service security template
- Service Name: e.g., patient-service.
- Service Owner: Responsible individual or team.
- Data Classification: ePHI, PII, analytics.
- Authentication Method: mTLS, OAuth 2.0, service account.
- Authorization Policy: RBAC or ABAC details.
- Dependencies: Databases, message brokers, external APIs.
- Logging: Fields captured; destination (e.g., ELK stack, Splunk).
- Encryption: In transit (TLS 1.2/1.3); at rest (AES‑256). Keys managed via HSM or cloud KMS.
- Backup and Restore: Frequency, location, encryption.
- Monitoring: Metrics collected; alerts configured.
- Compliance Evidence: Records of access reviews, incident response tests, vulnerability scans.
API security policy template
- Authentication: Require OAuth 2.0 with short‑lived tokens; mTLS for client and server.
- Authorization: Validate scopes; enforce least privilege at the gateway.
- Headers: Require Authorization, Content-Type, X-Request-ID; drop unnecessary headers.
- Rate limiting: Set per‑user and per‑client limits; implement burst control and circuit breakers.
- Input validation: Enforce schema validation; block unknown fields; sanitize inputs.
- Logging and monitoring: Log request metadata, response status and authorization decisions; integrate with SIEM for anomaly detection.
- Encryption: Enforce TLS 1.2/1.3; disable weak ciphers; rotate certificates.
Conclusion
Microservices have transformed how healthcare platforms are built. They offer agility, scalability and resilience; they also introduce a multiplicity of components, each a potential gateway to sensitive data. The HIPAA Security Rule, as clarified by the 2024 NIST guidance, requires organizations to conduct thorough risk analysis, implement risk management, control access, record system activity and protect data integrity and transmission. Proposed amendments to the rule show that regulators are responding to increases in breaches and evolving threat landscapes. Compliance is not a document exercise; it demands real operational security.
A HIPAA Microservices architecture can support both innovation and compliance when designed with security in mind. Service boundaries based on data sensitivity, encryption at every layer, zero‑trust authentication, centralized logging and regular risk assessments are critical building blocks. Human expertise is indispensable. Konfirmity’s experience shows that companies relying solely on software tools often miss key requirements. A human‑led, managed service can reduce effort hours (from hundreds to around 75 hours per year) and compress audit readiness timelines by providing guidance, implementing controls within your stack and handling continuous evidence collection. This approach lets engineering teams focus on delivering value while ensuring that compliance is maintained throughout the year. Security that exists only on paper invites risk; security embedded in operations builds trust with patients, buyers and regulators.
FAQs
1) Are microservices allowed under HIPAA?
Yes. HIPAA is technology‑neutral. It requires that covered entities and business associates implement administrative, physical and technical safeguards appropriate to their risks. Microservices must follow the same security principles as monoliths: risk analysis, access controls, encryption, audit logging and incident response. Architecture alone does not determine compliance; control design and evidence matter more.
2) How do you secure service‑to‑service communication?
Use mutual TLS to authenticate both ends of a connection and encrypt traffic. Deploy a service mesh or identity platform like SPIFFE/SPIRE to issue service identities and rotate certificates. Supplement mTLS with short‑lived JWTs issued by a centralized identity provider and enforced via a policy engine. Combine these mechanisms with network segmentation to prevent lateral movement.
3) What HIPAA safeguards apply to APIs?
API endpoints must implement access controls tied to user roles, authenticate clients and encrypt data in transit. API gateways enforce authentication and authorization, rate limiting, input validation and logging. HIPAA also requires audit controls to record system activity and mechanisms to protect the integrity of ePHI. Centralizing logging and policy enforcement simplifies compliance.
4) How does encryption work in distributed healthcare systems?
Encrypt all network communication using TLS 1.2/1.3 and use mTLS for mutual authentication. Encrypt data at rest using strong algorithms (e.g., AES‑256) and store keys in a secure key management system. Rotate keys regularly and avoid storing secrets in code. Apply encryption to backups and replicas as well. Evaluate whether field‑level encryption or tokenization is needed for particularly sensitive elements.
5) What common mistakes break HIPAA compliance in microservices?
Failing to conduct a thorough risk analysis, leaving services unauthenticated, using broad access permissions, neglecting audit logging and ignoring vendor responsibilities are frequent pitfalls. Settlements in 2024 highlight failures to conduct risk assessments, manage logs and restrict access. Another mistake is treating compliance as a one‑time effort. Controls must operate continuously, and evidence must be collected over observation periods of up to twelve months for SOC 2 and similar frameworks. Implement automated monitoring and engage experienced practitioners to avoid these issues.





.svg)






.svg)
.svg)