Most enterprise and healthcare buyers now request assurance artifacts before procurement. Deals routinely stall when teams rely on paperwork rather than operational security. In 2025 the global average cost of a data breach dropped to $4.44 million, yet breaches in the United States averaged $10.22 million. Healthcare breaches remain the costliest, with an average cost of $7.42 million and breach lifecycles that last roughly 279 days. These losses, together with new enforcement actions—such as the $1.5 million penalty imposed against Warby Parker for poor risk analysis and weak audit controls—underscore the need for robust, resilient designs. Healthcare systems are turning to HIPAA Multi‑Region Architectures to achieve compliance, protect ePHI, and ensure uninterrupted service. This guide explains how to design and operate such architectures. It is written for chief technology officers, CISOs, VPs of Engineering, and compliance officers who manage healthcare applications in the cloud.
HIPAA and Cloud Architecture: A Foundation
HIPAA’s Security Rule sets the baseline for protecting electronic protected health information (ePHI). It requires covered entities to implement administrative, physical, and technical safeguards, conduct risk analysis, and document decisions. Technical safeguards include access control, audit controls, integrity protections, person or entity authentication, and transmission security. The rule emphasises encryption as a method for keeping ePHI confidential and instructs organizations to adopt reasonable and appropriate mechanisms to prevent unauthorized access. Audit controls must record and examine activity on systems containing ePHI. Integrity controls require procedures to prevent improper alteration or destruction of data. Authentication procedures verify that a person or entity seeking access is who they claim to be. Transmission security addresses integrity controls and encryption when data travels across networks.
The regulatory environment also hinges on contractual arrangements. A business associate agreement (BAA) is required whenever a third party processes or stores PHI. HHS explains that BAAs must set out permissible uses of PHI, require safeguards to prevent unauthorized disclosure, oblige the associate to report incidents, and make internal practices available to HHS for review. The Warby Parker enforcement case demonstrates that inadequate risk analysis, missing security measures, and lack of audit control procedures can lead to substantial penalties. Together, these requirements form the core of a shared responsibility model: cloud providers secure the infrastructure, while healthcare organizations remain accountable for data classification, access control, key management, and compliance.
What Is Multi‑Region Deployment?
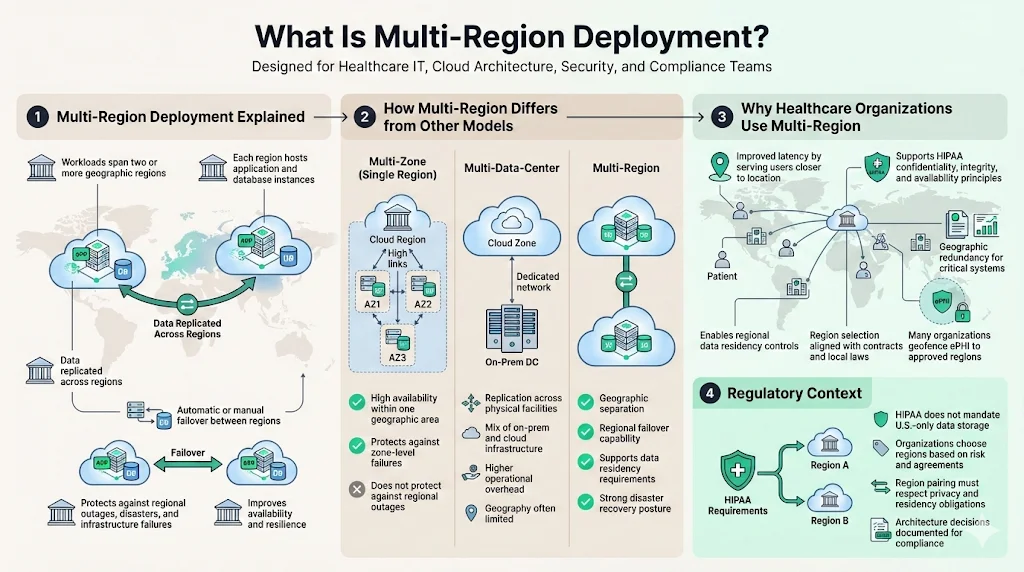
In the cloud context, a multi‑region deployment spans two or more geographic regions within a single provider. Each region hosts redundant application and database instances so that if one region fails, another can take over. By replicating data and workloads across regions, organizations improve availability and mitigate risks from natural disasters, ransomware, or infrastructure failures. Multi‑region deployment is distinct from multi‑zone (within a single region) and multi‑data‑center approaches. Multi‑zone strategies provide availability within one geographic area but do not protect against regional outages. Multi‑data‑center setups replicate data across on‑premises facilities and cloud availability zones. In contrast, multi‑region designs distribute workloads across separate physical regions to meet data residency rules and provide geographic redundancy. Secureframe’s disaster recovery guidance advises replicating workloads and data across multiple regions and availability zones so systems can fail over if the primary region becomes unavailable.
Healthcare organizations adopt multi‑region deployment for several reasons: to improve latency by serving patients closer to their location, to satisfy data residency requirements by ensuring ePHI stays within approved jurisdictions, and to satisfy availability objectives required by HIPAA’s confidentiality, integrity, and availability principles. Because HIPAA does not mandate that data remain within U.S. borders, organizations can choose region pairs that align with contractual and local laws, though many prefer to geofence PHI to U.S. regions or to specific countries per privacy agreements.
Key Drivers for Adopting HIPAA‑Ready Multi‑Region Designs
Compliance and Regulatory Requirements
HIPAA demands that regulated entities safeguard ePHI, conduct risk analysis, and maintain audit controls. Multi‑region architecture supports these requirements by enabling robust replication, backup, and failover. Censinet notes that while HIPAA does not explicitly require data to stay within U.S. borders, it does require stringent safeguards; multi‑region setups help deliver those safeguards by providing redundancy and backup across regions. BAAs require that business associates implement appropriate safeguards, report breaches, and disclose internal practices to HHS. Multi‑region designs allow organizations to enforce these obligations uniformly across geographic boundaries. Importantly, data residency rules may be driven by state laws or contractual commitments with providers and insurers. AccountableHQ advises geofencing storage, backups, logs, and analytics to approved regions and blocking cross‑region replication unless data is de-identified.
Data Privacy and Security
Security protections must travel with data across regions. The HIPAA Security Rule encourages encryption as a way to protect ePHI from unauthorized access. Audit controls should record and examine activity on systems containing ePHI, while integrity controls ensure that data has not been altered or destroyed without authorization. In its enforcement guidance following the Warby Parker penalty, OCR recommends that organizations identify where ePHI resides, integrate risk analysis into business processes, ensure audit controls are in place, and encrypt ePHI in transit and at rest. Encryption at rest should use strong algorithms (AES‑256) and customer‑managed keys stored in hardware security modules; encryption in transit should use TLS 1.3 with mutual authentication where possible. Cross‑region replication should re‑encrypt data in the destination region with a region‑specific key. Key rotation policies and strict access controls must restrict who can decrypt ePHI.
Access control ties identity to data. Person or entity authentication is a standard under the Technical Safeguards. Healthcare systems should implement role‑based access, enforce multi‑factor authentication, and apply the principle of least privilege across all regions. For cross‑region operations, identity and access management should centralize policy but allow region‑specific enforcement. Warby Parker’s case shows that failures to implement adequate security measures and to review system logs can lead to fines. Continuous monitoring, regular access reviews, and automated alerting across regions help detect unauthorized access quickly.
Uptime and Disaster Recovery
Redundancy is vital for maintaining service during outages. Secureframe’s disaster recovery guidance lists multi‑region redundancy, automated infrastructure provisioning, pilot‑light environments, and failover routing as critical elements. Pilot‑light environments run core services at low capacity in a secondary region so they can scale quickly if the primary region fails. Automated backups and snapshots stored in multiple locations strengthen resilience. A failover DNS service with health checks can redirect traffic to the secondary region during an outage. When combined with regular disaster recovery tests and tabletop exercises, these measures align with HIPAA’s requirement for contingency planning and ensure that ePHI remains available even during regional disruptions.
Core Components of a HIPAA‑Ready Multi‑Region Architecture
Designing HIPAA Multi‑Region Architectures involves stitching together several technical and procedural elements to meet regulatory and operational requirements.
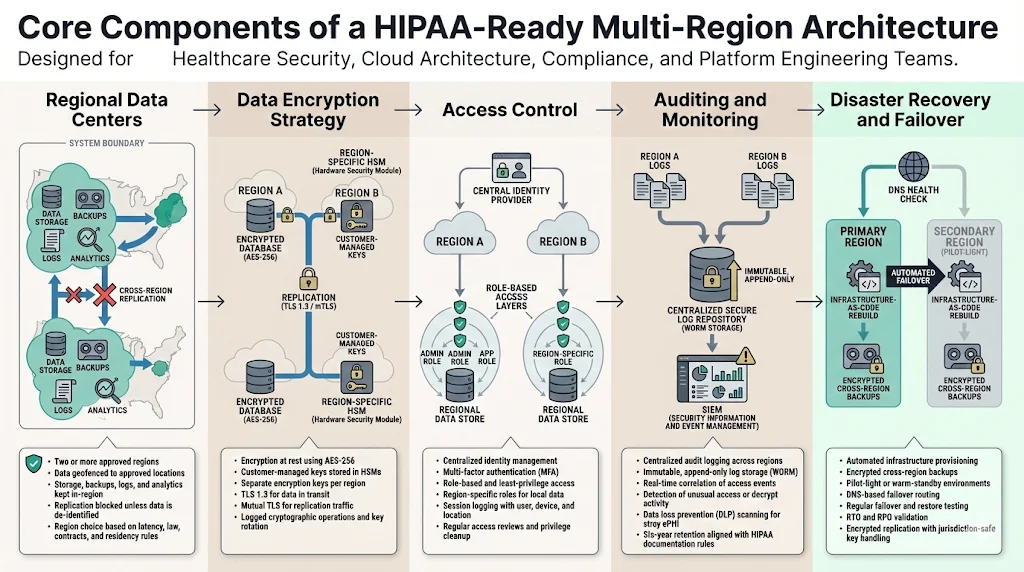
Regional Data Centers
Selecting regions involves balancing latency, legal considerations, cost, and data residency obligations. For healthcare applications in the United States, many organizations choose two U.S. regions (e.g., eastern and western) to satisfy domestic residency requirements. AccountableHQ recommends geofencing all storage, backups, logs, and analytics to approved regions and blocking cross‑region replication unless data is de-identified. Censinet observes that multi‑region architecture simplifies compliance because it stays within one provider’s ecosystem, making it easier to maintain consistent security policies and meet HIPAA requirements. However, data may need to stay within specific countries or states if required by contracts or local law, so organizations must map ePHI storage to regions accordingly.
Data Encryption Strategy
HIPAA makes encryption an addressable implementation specification: organizations must decide whether encryption is reasonable and appropriate based on risk analysis. In practice, encryption is essential when replicating data across regions. At rest, use AES‑256 or stronger ciphers and customer‑managed keys stored in hardware security modules (HSMs). Each region should have its own encryption key to avoid cross‑region key dependency. Transport encryption should use TLS 1.3 or later and mutual TLS for replication channels. OCR advises encrypting ePHI in transit and at rest and incorporating lessons from incidents into security programs. To support regulatory audits, log every cryptographic operation and enforce regular key rotation.
Access Control
Access control policies must ensure that only authorized individuals can access ePHI. The Technical Safeguards require implementing procedures to verify that a person or entity seeking access to ePHI is the one claimed. Controls should include multi‑factor authentication, role‑based access, and least‑privilege policies across all regions. Centralized identity systems, such as an enterprise identity provider, enforce consistent policies, while region‑specific roles restrict access to local data. Session management should log identity assertions, including location and device information. Regularly review access logs and remove unused privileges. Warby Parker’s penalty underscores the need to review information system activity and implement mechanisms to authenticate information.
Auditing and Monitoring
Audit controls are required under the Technical Safeguards. Systems must record and examine activity in information systems that contain or use ePHI. These records should be centralized across regions in an immutable, append‑only store (e.g., WORM storage) to support investigations and compliance reporting. OCR recommends ensuring audit controls are in place, implementing regular reviews of information system activity, and making logs available to HHS. To achieve real‑time detection across regions, feed logs into a security information and event management (SIEM) platform with correlation rules for unusual access patterns or unauthorized decrypt operations. Integrate data loss prevention (DLP) tooling to scan for stray ePHI in logs and replication streams. Retain HIPAA documentation for at least six years and align log retention with legal and business requirements.
Disaster Recovery and Failover
Disaster recovery requires planning for regional outages and ransomware attacks. Secureframe’s blueprint lists automated infrastructure provisioning, pilot‑light environments, and failover routing as key components. Configure infrastructure as code (e.g., Terraform or CloudFormation) to rebuild stacks in a recovery region quickly. Use automated backups such as EBS snapshots and database replication across regions. Route 53 health checks and DNS failover can shift traffic to the secondary region during an incident. Conduct regular failover drills and test backup restorations to validate recovery time objectives (RTO) and recovery point objectives (RPO). Align these tests with HIPAA’s contingency plan requirements and incorporate findings into the risk management process. When replicating PHI, ensure that data remains encrypted and that keys are not transported across jurisdictions; AccountableHQ advises blocking cross‑region replication unless data is de-identified.
Putting It All Together: Sample Architecture Flow
The following high‑level flow brings the components together. Each region hosts stateless application servers, managed databases (e.g., encrypted relational or document databases), and storage buckets encrypted with region‑specific keys. User traffic is routed through a global load balancer configured with health checks. When a request hits Region A, the application processes it locally; PHI is stored in Region A’s encrypted database. An asynchronous replication pipeline copies encrypted data to Region B and re‑encrypts it with Region B’s key. Both regions publish logs (accfess events, key usage, API calls) to a central audit log service housed in an immutable log storage account. Identity and access management uses a centralized directory with per‑region roles. If Region A fails, DNS failover redirects traffic to Region B, where the application can service requests using replicated data.
This diagram illustrates encrypted replication between two regions, dedicated audit logging, and centralized identity management. It demonstrates how HIPAA Multi‑Region Architectures combine physical and logical controls to protect ePHI, maintain availability, and support compliance audits.
Best Practices for Deploying Multi‑Region HIPAA Architectures
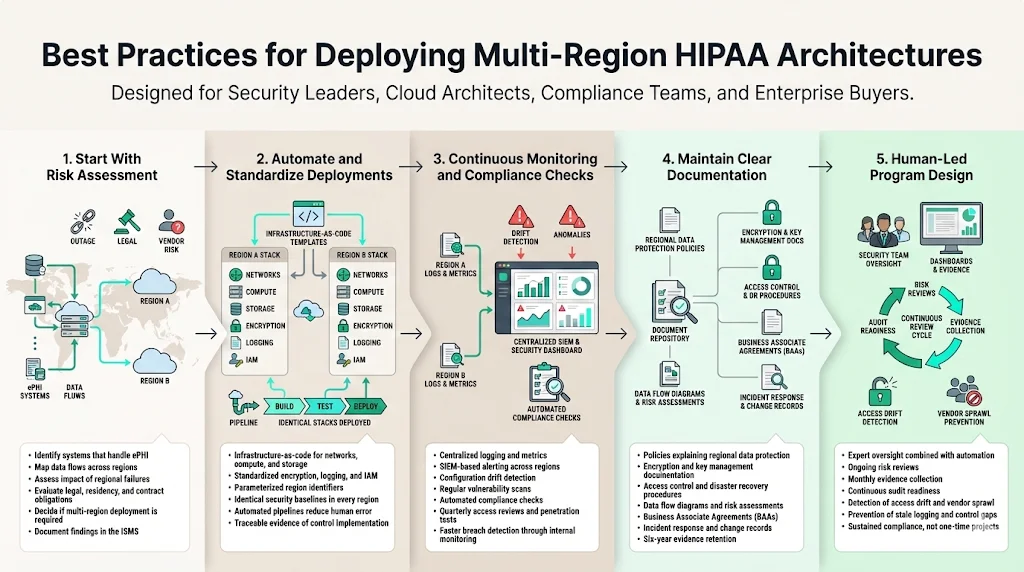
Start With Risk Assessment
Risk assessment is the foundation of compliance and security. HIPAA requires covered entities to conduct an accurate and thorough risk analysis of potential risks to ePHI. Identify which systems handle PHI, where data flows, and the impact of regional failures. Evaluate legal obligations, data residency requirements, and vendor contracts. Use this assessment to determine whether multi‑region deployment is necessary and which regions meet business and regulatory needs. Document the risk analysis and incorporate it into your Information Security Management System (ISMS).
Automate and Standardize Deployments
Consistency across regions is essential. Use infrastructure‑as‑code (IaC) tools to define networks, compute instances, load balancers, and storage. Standardize encryption settings, logging configurations, and IAM policies. Parameterize region identifiers so that code can deploy identical stacks in multiple regions. Automated pipelines reduce human error, shorten deployment times, and provide traceable evidence of control implementation. For example, typical SOC 2 readiness projects take six to eighteen months when self‑managed. Konfirmity’s managed service compresses this timeline to four or five months by automating control implementation and evidence collection, allowing organizations to achieve sustained audit readiness with less internal effort.
Continuous Monitoring and Compliance Checks
Compliance is not a one‑time event. Implement continuous monitoring to detect configuration drift, unauthorized changes, and anomalous behaviour across regions. Centralize logs and metrics; feed them into a SIEM with automated alerts. Regularly scan infrastructure for misconfigurations and vulnerabilities. Implement automated compliance checks against HIPAA, SOC 2, and ISO 27001 control libraries. Conduct quarterly access reviews and penetration tests. According to IBM’s 2025 report, organizations that detect breaches internally reduce the time to contain incidents; continuous monitoring enables early detection.
Maintain Clear Documentation
Documentation bridges technical controls and compliance requirements. Maintain policies and procedures that explain how ePHI is protected in every region, including encryption schemes, key management, access control procedures, and disaster recovery processes. Document BAAs, data flow diagrams, and risk assessments. HHS advises that BAAs must specify permitted uses of PHI, require safeguards, and mandate breach reporting. Keep audit logs, incident response records, and change management tickets for at least six years. Clear documentation supports audits and due diligence from enterprise buyers.
Human‑Led Program Design
Technology alone does not achieve compliance. Konfirmity’s experience with more than 6,000 audits shows that durable security programs blend expert oversight with automation. A dedicated team designs controls, reviews evidence, and coordinates with auditors year‑round. This human‑led managed service contrasts with software tools that leave clients to figure out implementation details. It also differs from one‑and‑done consulting projects that deliver a report and depart. A sustained program includes weekly risk reviews, monthly evidence collection, and readiness rehearsals. Through our work with hundreds of healthcare organizations, we’ve seen common pitfalls: access control drift, change‑management gaps, vendor sprawl, and stale logging. Ongoing operations catch these issues before they become audit findings.
Challenges and How to Handle Them
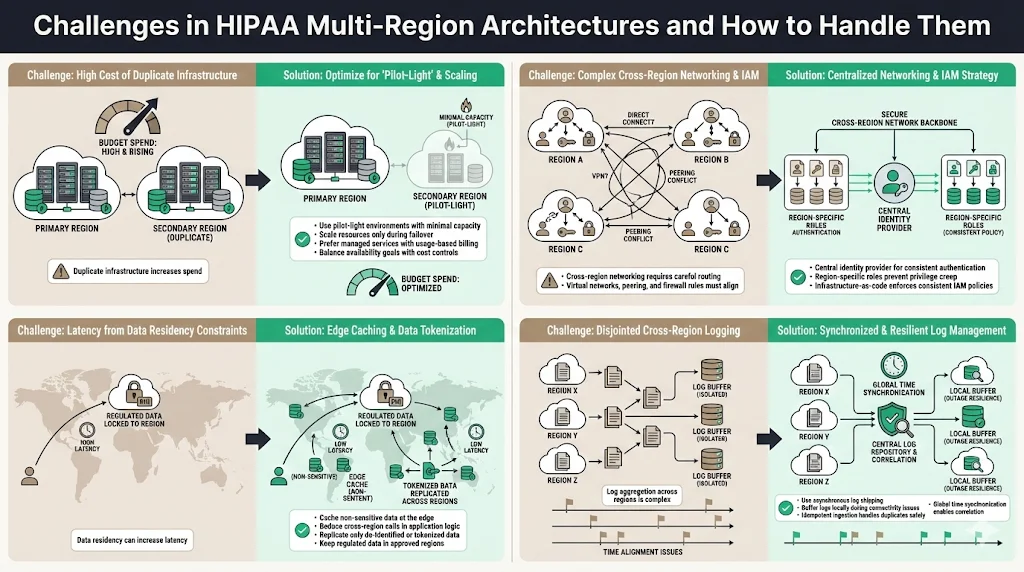
Deploying HIPAA Multi‑Region Architectures presents several challenges:
- Cost of redundancy: Maintaining duplicate infrastructure in multiple regions increases spending. Censinet notes that multi‑region setups incur higher infrastructure costs. Organizations can mitigate this by adopting pilot‑light environments (low‑capacity replicas that scale during failover) and using managed services that bill per use rather than per instance.
- Complexity of networking and IAM: Cross‑region networking requires careful design of virtual networks, peering connections, and routing policies. IAM must scale across regions without introducing privilege creep. Use central identity providers and region‑specific roles to manage this complexity. Automate policy deployment through IaC to ensure consistency.
- Performance vs compliance: Latency can increase when data must remain in a specific region. Address this by caching non‑sensitive data at the edge and by optimizing application logic to minimize cross‑region calls. If data must remain in‑region, replicate only de‑identified or tokenized data across borders.
- Consistent audit logging: Aggregating logs from multiple regions can be challenging, particularly when network connectivity is disrupted. Implement asynchronous log shipping with local buffering. Use idempotent log ingestion services that can tolerate duplicates and maintain order. Adopt global time synchronization to ensure log correlation.
Conclusion
Well‑designed multi‑region architectures help healthcare organizations align with HIPAA’s confidentiality, integrity, and availability requirements while boosting resilience against outages and cyberattacks. HIPAA’s technical safeguards encourage encryption, audit controls, integrity mechanisms, and authentication. BAAs mandate that business associates implement appropriate safeguards and report incidents. Enforcement actions show the cost of ignoring these requirements: Warby Parker’s $1.5 million penalty resulted from poor risk analysis and missing security measures. By deploying HIPAA Multi‑Region Architectures, encrypting data in transit and at rest, centralizing audit logs, and automating failover, healthcare teams can meet regulatory obligations and deliver continuous service. Invest in risk assessment, standardized deployment, continuous monitoring, and clear documentation. Build controls that withstand scrutiny from auditors, regulators, and attackers, and let compliance follow from robust security practices.
FAQ
1. Does HIPAA mandate multi‑region deployment?
No. HIPAA does not specify multi‑region deployment. It requires that organizations implement administrative, physical, and technical safeguards to protect ePHI. Multi‑region setups help satisfy availability and contingency planning requirements but are not mandated.
2. How does multi‑region deployment improve disaster recovery?
By replicating applications and data across geographically separated regions, multi‑region deployment ensures that if one region fails, another can continue operating. Secureframe’s guidance recommends multi‑region redundancy, pilot‑light environments, and automated failover routing, which together reduce downtime and preserve access to ePHI.
3. What are the biggest security risks in multi‑region setups?
Key risks include inconsistent access controls, misconfigured encryption, and uncentralized logging. Warby Parker’s penalty shows that lack of risk analysis and audit controls can lead to fines. Encryption must be applied in transit and at rest, and audit logs must be collected across regions.
4. How should audit logging work in multi‑region environments?
Audit controls should record and examine system activity. Logs from all regions should be streamed to a central immutable store. OCR recommends regular review of system activity and making logs available for compliance audits.
5. Is data residency a major concern for HIPAA?
HIPAA does not mandate specific countries for data storage, but BAAs and state laws may impose residency requirements. Censinet notes that HIPAA calls for stringent safeguards rather than explicit geographic limits. AccountableHQ advises geofencing ePHI to approved regions and blocking cross‑region replication unless data is de‑identified.




.svg)






.svg)
.svg)