Enterprise buyers have changed. Five years ago, a compelling feature set and a competitive price were often enough to close a deal. Today, before a procurement officer even looks at your pricing model, a security team scrutinizes your infrastructure. They demand assurance artifacts, penetration test results, and, increasingly, ISO 27001 certification.
For SaaS founders and CTOs, this shift creates friction. Deals stall in "security review" purgatory. Your team, already stretched thin building the product, gets pulled into weeks of answering 300-question spreadsheets.
ISO 27001 For SaaS is no longer just a badge of honor; it is a fundamental requirement for revenue protection and market entry. It is the international standard for Information Security Management Systems (ISMS), defining how organizations manage and protect their information assets.
However, many SaaS leaders view ISO 27001 as a bureaucratic hurdle—a "check-the-box" task to satisfy a stubborn auditor. This view is a strategic error. When implemented correctly, ISO 27001 provides the operational structure needed to scale securely. It transforms security from a reactive scramble into a predictable business function.
In this guide, we will analyze exactly what this standard entails for cloud-native companies. We will move past the theoretical jargon and examine the operational demands, the implementation steps, and how a human-led, managed service approach builds a security posture that stands up to auditors and attackers alike.
What ISO 27001 Means for SaaS
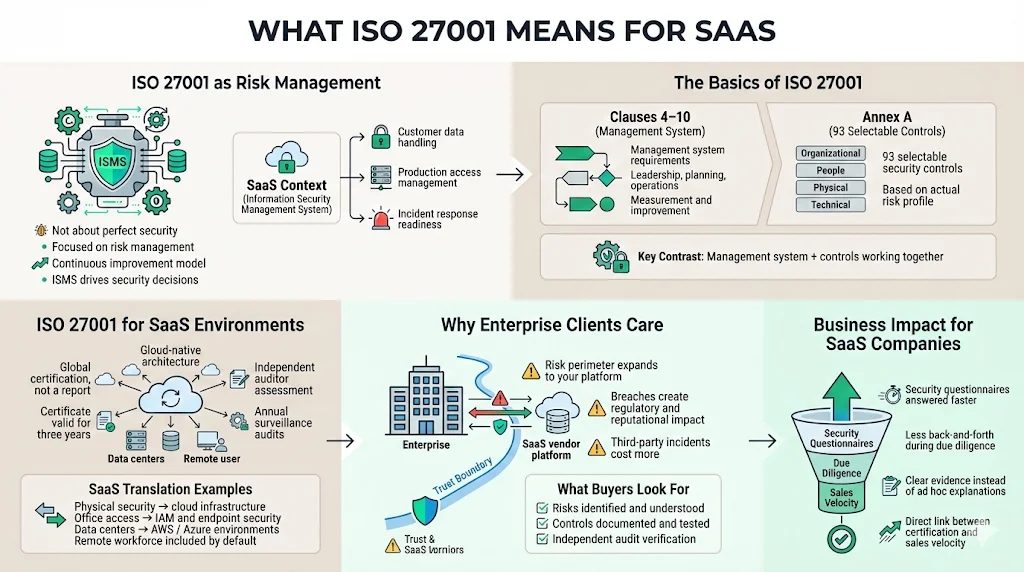
At its core, ISO/IEC 27001 is not about absolute security—such a state does not exist. Instead, it is about risk management. It provides a framework for establishing, implementing, maintaining, and continually improving an Information Security Management System (ISMS).
For a SaaS company, your ISMS is the engine that drives your security decisions. It dictates how you handle customer data, how you manage access to production environments, and how you respond when (not if) a security incident occurs.
The Basics of ISO 27001
The standard consists of two main parts:
- The Clauses (4–10): These define the mandatory requirements for the management system itself. They cover context, leadership, planning, support, operation, performance evaluation, and improvement.
- Annex A: This is a set of security controls (updated in the 2022 version to 93 controls) that you select based on your specific risks.
Unlike SOC 2, which is an attestation report primarily popular in North America, ISO 27001 is a globally recognized certification. An independent auditor assesses your ISMS against the standard's requirements. If you meet them, you receive a certificate valid for three years, subject to annual surveillance audits.
In a SaaS context, applying ISO 27001 For SaaS means translating these requirements into cloud-native practices. It means mapping "physical security" not just to your office doors (if you even have them), but to your AWS or Azure data centers and the endpoint security of your remote workforce's laptops.
Why Enterprise Clients Care
Why do enterprise buyers insist on this specific standard? It comes down to liability and trust.
When an enterprise uses your SaaS product, they extend their risk perimeter to include your infrastructure. If you suffer a breach, their data is exposed. They face regulatory fines—under GDPR, CCPA, or HIPAA—and reputational damage. According to the 2024 IBM Cost of a Data Breach Report, the global average cost of a data breach has reached $4.88 million, with costs rising significantly higher when third-party software is involved.
By demanding ISO 27001, they are not just asking for a logo. They are looking for objective evidence that:
- You have identified your risks. You know where the sensitive data lives and what threatens it.
- You have controls in place. You are not winging it; you have documented, tested procedures for security.
- You are audited independently. A third party has verified your claims.
In our experience supporting over 6,000 audits, we see a direct correlation between certification and sales speed. Companies with a functioning ISMS answer security questionnaires 60–70% faster because the answers are already documented and verified.
Core Concepts Explained
To implement ISO 27001 effectively, you must understand the mechanisms that drive it. Installing antivirus software is insufficient. The standard requires a systematic approach.
Information Security Management & Risk Assessment
The heart of ISO 27001 is the risk assessment. This is where many SaaS companies fail by either over-engineering or under-scoping.
An ISMS allows you to decide which risks are acceptable and which require mitigation. For a SaaS platform, a risk assessment involves:
- Asset Identification: Listing your information assets (customer database, source code, production servers, employee laptops).
- Threat Mapping: Identifying what could go wrong (ransomware, accidental deletion by a developer, AWS credential theft).
- Vulnerability Analysis: Finding weaknesses (unpatched software, lack of Multi-Factor Authentication).
- Risk Treatment: Deciding how to handle the risk. You can avoid it, transfer it (insurance), accept it, or mitigate it (implement controls).
The output of this process is the Statement of Applicability (SoA). This document lists every control in Annex A and states whether you apply it and why. It serves as the menu of your security program.
Data Protection and Access Control
For SaaS, data is the most valuable asset. ISO 27001 places heavy emphasis on the Confidentiality, Integrity, and Availability (CIA) of data.
- Confidentiality: Only authorized users access the data. This requires rigorous Access Control protocols. In a modern stack, this means implementing Role-Based Access Control (RBAC) and the Principle of Least Privilege. A junior developer must not have root access to the production database.
- Integrity: The data is accurate and untampered with. This involves change management controls—ensuring code changes are reviewed and tested before deployment so they don't corrupt the database.
- Availability: The data is accessible when needed. This maps to uptime, backups, and disaster recovery planning.
Cybersecurity Controls and Monitoring
The Annex A controls in the 2022 version of the standard are grouped into four themes:
- Organizational: Policies, roles, threat intelligence.
- People: Screening, training, remote work terms.
- Physical: Office security, clear desk policy, device security.
- Technological: Encryption, secure coding, logging, monitoring.
For a SaaS firm, the technological controls are vital. You must demonstrate logging and monitoring. If an attacker breaches your perimeter, how will you know? ISO 27001 requires you to have the capability to detect anomalous events and review logs regularly.
Security Policies & Training
Documentation is often the most hated part of compliance, but it is necessary. Auditing undefined processes is impossible.
Policies serve as the laws of your organization. An Access Control Policy states who gets access. An Acceptable Use Policy tells employees what they can do on company devices.
However, a policy saved in a dormant Google Drive folder is useless. The standard requires awareness and training. Your team must know these policies exist and understand their role in upholding them. At Konfirmity, we integrate policy acknowledgement into the onboarding workflow, ensuring that human error—the leading cause of breaches—is minimized through education.
SaaS-Specific Challenges and Solutions
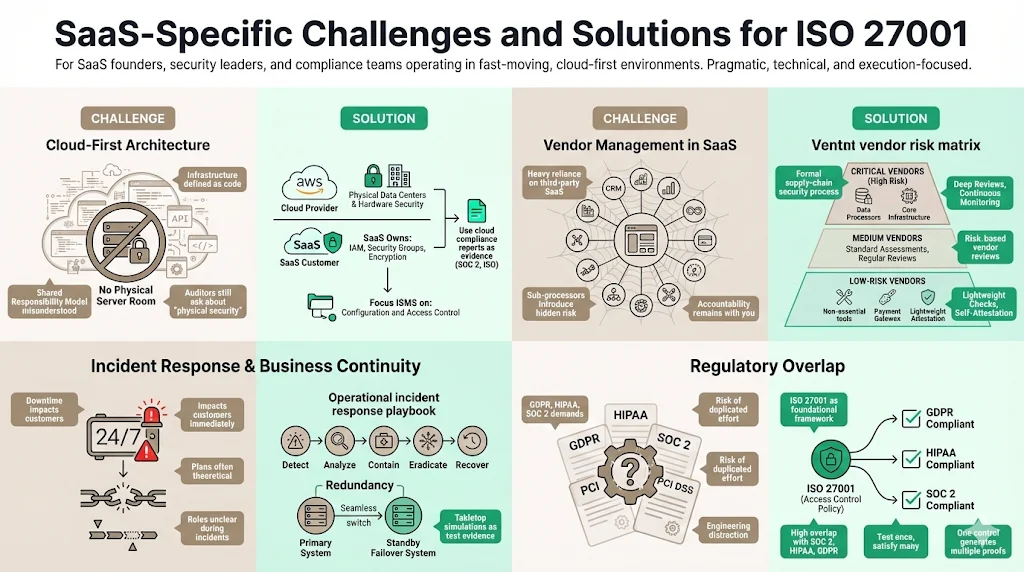
Applying a standard written for general business to a high-velocity SaaS environment presents unique difficulties. You move fast; ISO 27001 demands you move deliberately.
1) Cloud-First Architecture
Traditional IT audits involved walking into a server room and checking door locks. In SaaS, your infrastructure is code.
You must define the Shared Responsibility Model clearly. If you use AWS, Amazon handles the physical security of the data center. You are responsible for the security in the cloud—firewall configurations (Security Groups), IAM roles, and encryption settings.
The Challenge: Auditors may ask for evidence of physical server security. The Solution: You provide the compliance artifacts from your cloud provider (e.g., AWS's SOC 2 report or ISO certificate) and focus your ISMS on the configuration and management of those resources.
2) Vendor Management
SaaS companies rely heavily on other SaaS tools—Slack, GitHub, Jira, HubSpot, Datadog. Each of these is a third-party vendor that processes your data or your code.
ISO 27001 For SaaS requires a supply chain security process. You must evaluate your vendors before onboarding them and review them periodically. The 2025 Verizon Data Breach Investigations Report (DBIR) highlights that 30% of breaches now involve third parties, a significant increase from previous years. If a sub-processor is breached, you are accountable to your customers. We help clients automate this by establishing a vendor risk rubric: critical vendors get a deep dive, while low-risk tools get a basic review.
3) Incident Response and Business Continuity
SaaS implies 24/7 availability. Your Incident Response Plan (IRP) must not be a theoretical document. It needs to be an operational playbook. Who gets the PagerDuty alert? Who decides to shut down the API if an active attack is detected? Who communicates with customers?
Business Continuity Planning (BCP) focuses on keeping the service running during a disruption. For SaaS, this often involves redundancy—multi-region database replication and failover mechanisms. ISO 27001 requires you to test these plans. A tabletop simulation, where the team acts out a ransomware attack or an AWS region failure, provides the evidence auditors need and the practice your team requires.
4) Regulatory Compliance Overlaps
SaaS companies often face a regulatory mix: GDPR for European users, HIPAA for healthcare clients, SOC 2 for US enterprises.
The good news is that ISO 27001 is foundational. If you implement the 93 controls of Annex A, you cover approximately:
- 80–90% of SOC 2 Trust Services Criteria.
- High overlap with HIPAA Security Rule technical safeguards.
- Significant portions of GDPR technical measures.
Konfirmity’s approach is "test once, satisfy many." We map a single control (e.g., "Review access quarterly") to satisfy ISO 27001, SOC 2, and HIPAA requirements simultaneously. This eliminates redundant work and keeps your engineering team focused on shipping code.
Step-by-Step Guide to ISO 27001 for SaaS
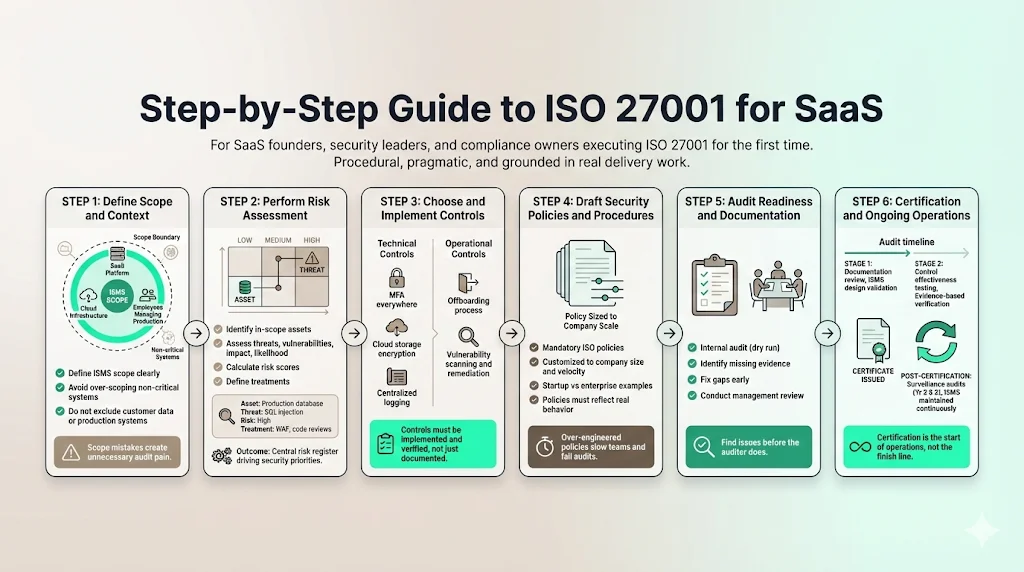
Implementing ISO 27001 is a process that typically spans 4 to 6 months for a focused SaaS company. Here is how we execute this program.
Step #1: Define Scope and Context
The first step is determining the "Scope of the ISMS." Do not over-scope. If you include your marketing website (which holds no customer data) or your HR portal in the initial scope, you increase your audit burden unnecessarily. Do not under-scope. Excluding the database containing customer PII is not an option.
For most SaaS firms, the scope is: The development, operation, and maintenance of the SaaS platform, including the supporting cloud infrastructure and the employees who manage it.
Step #2: Perform Risk Assessment
With the scope defined, we execute the risk assessment. We identify the assets within that scope and apply a risk methodology (often based on ISO 27005).
- Asset: Production Database.
- Threat: SQL Injection.
- Vulnerability: Unsanitized user input.
- Impact: High (Data Breach).
- Likelihood: Medium.
- Risk Score: High.
- Treatment: Implement WAF (Web Application Firewall) and code reviews (Controls).
We repeat this for all critical assets. This creates a risk register that guides your security roadmap.
Step #3: Choose & Implement Controls
This is the heavy lifting. Based on the SoA, we implement the controls.
- Technical Controls: Turning on MFA for all Google Workspace and Cloud accounts. Encrypting S3 buckets. configuring centralized logging.
- Operational Controls: Setting up a process for employee offboarding (revoking access immediately). Implementing a vulnerability management program (scanning for CVEs).
In a managed service model, Konfirmity works inside your stack to help configure these settings. We don't just tell you to "encrypt data"; we help verify that the encryption is active and the keys are managed correctly.
Step #4: Draft Security Policies and Procedures
We draft the mandatory policies customized to your operational reality. A 5-person startup does not need the same Change Management policy as a 5,000-person bank.
- Startup Policy: "All code must be reviewed by a peer and pass automated tests before merging to main."
- Enterprise Policy: "All code requires approval from the Change Advisory Board (CAB)."
Using the enterprise policy for a startup will kill your speed. We ensure policies are right-sized and practical.
Step #5: Audit Readiness and Documentation
Before the external auditor arrives, we conduct an Internal Audit. This is a dry run where we check your own compliance against your own policies. We find the gaps—the missing evidence, the unsigned documents—and fix them.
Then comes the Management Review, a formal meeting where leadership reviews the ISMS performance. This is a mandatory requirement.
Step #6: Certification and Operations
The external audit happens in two stages:
- Stage 1 (Document Review): The auditor checks your documentation (policies, risk assessment, SoA) to ensure the ISMS is designed correctly.
- Stage 2 (Certification Audit): The auditor tests your controls. They will ask to see evidence: "Show me the logs from last Tuesday," "Show me the background check for the new hire," "Show me the proof that you tested your backups."
If you pass, you get the certificate. But the work isn't done. You must maintain this system for the surveillance audits in years 2 and 3.
Benefits of ISO 27001 for SaaS Businesses
Why go through this effort? The ROI is measured in revenue and resilience.
1) Builds Enterprise-Grade Trust
Trust is the currency of B2B sales. When you present an ISO 27001 certificate, you signal maturity. You tell the enterprise buyer, "We take this as seriously as you do." It removes the perceived risk of working with a smaller vendor. The ISO Survey 2024 reveals that certifications for Information Security have nearly doubled, reaching almost 97,000 certificates globally, proving this standard is now the baseline expectation.
2) Strengthens Overall Security Posture
Compliance often gets a bad reputation as "security theater," but ISO 27001 forces you to look at the blind spots. By mandating vendor reviews, disaster recovery testing, and access reviews, you catch issues before they become breaches. You harden your attack surface.
3) Improves Sales Conversations
Negotiating security addendums in contracts becomes simpler. Instead of redlining every clause about "right to audit," you can often substitute your ISO certification and audit summary. This shortens the legal review cycle, bringing revenue in the door faster.
4) Helps Standardize Policies
As you scale from 10 to 100 employees, tribal knowledge breaks. "Ask Dave how to deploy" doesn't work anymore. ISO 27001 forces you to document processes. This standardization helps onboard new engineers faster and reduces the chaos of rapid growth.
Common Pitfalls to Avoid
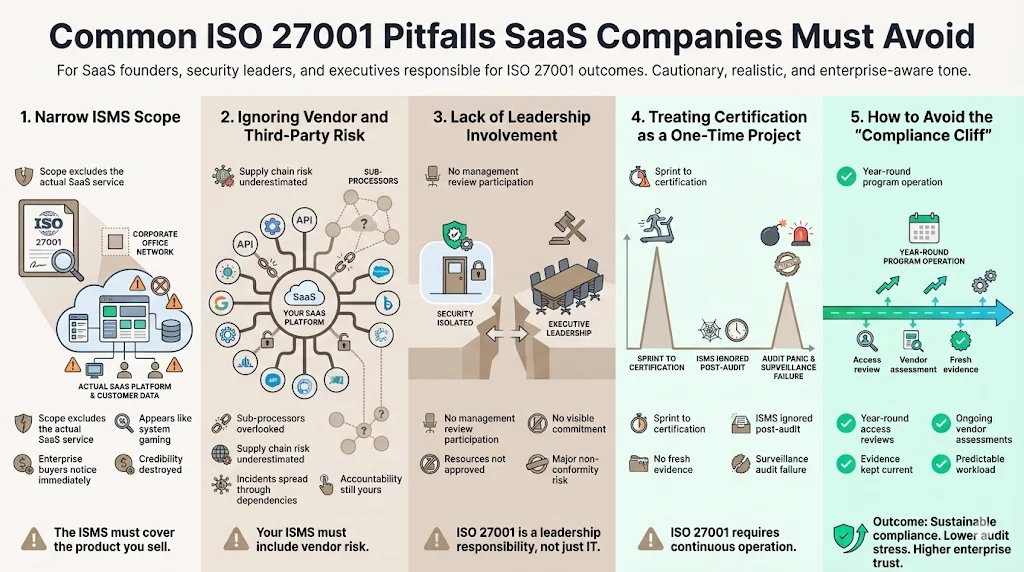
We have seen many companies stumble on their path to ISO 27001 For SaaS. Here are the recurring patterns of failure.
1) Narrow ISMS Scopes
Some companies try to "game" the system by defining a scope so narrow it's meaningless. If your certificate only covers "The HR Department" and not your SaaS product, enterprise buyers will spot this immediately. It destroys credibility. The scope must cover the service you are selling.
2) Ignoring Vendor and Third-Party Risk
SaaS apps are often a mesh of APIs. Ignoring the risk of your sub-processors is a critical vulnerability. The "SolarWinds" and "Log4j" incidents taught us that supply chain risk is real. Your ISMS must address the tools you use.
3) Not Involving Leadership
ISO 27001 requires "Management Commitment." If the CEO views security as an IT problem and refuses to participate in management reviews or approve resources, the auditor will issue a major non-conformity. Security must be a boardroom topic.
4) Treating Certification as a One-Time Project
This is the biggest trap. Companies sprint to the audit, get the certificate, and then ignore the ISMS for 11 months. When the surveillance audit comes, they have no evidence, no logs, and no records of meetings. They fail or have to scramble frantically.
Konfirmity prevents this "compliance cliff." As a managed service, we operate the program year-round. We perform the quarterly access reviews, we track the vendor assessments, and we keep the evidence fresh. We turn a spike of effort into a manageable, flat line of operation.
Conclusion
The demand for ISO 27001 For SaaS is not going away. As cyber threats evolve and data privacy regulations tighten, enterprise buyers will only raise the bar higher.
You have two choices. You can treat this as a distraction—buying a low-cost software tool, generating templates you don't understand, and hoping the auditor doesn't look too closely. Or, you can view it as an opportunity to build a resilient, enterprise-grade company.
A well-implemented ISMS is a competitive advantage. It proves you are a safe pair of hands for your customer's most sensitive data.
At Konfirmity, we believe that you shouldn't have to choose between building your product and securing it. We provide the human expertise to design, implement, and run your security program. We don't just advise; we execute. We bring the 6,000+ audits of experience to your team, reducing the internal burden from 600 hours a year to roughly 75.
Build the program once, operate it daily, and let compliance follow as a natural output of good security.
FAQs
1) Is ISO 27001 required for SaaS companies?
Legally, no. Commercially, yes—if you sell to enterprises. While no law explicitly mandates ISO 27001, global privacy laws (GDPR) and enterprise procurement standards make it the de facto requirement for doing business with mid-market and large organizations.
2) How is ISO 27001 applied in cloud-based systems?
In cloud systems, the focus shifts from physical security to logical security. You focus on Identity and Access Management (IAM), encryption, network segmentation (VPCs), and secure configuration of cloud resources. You rely on the cloud provider's certification for the physical layer.
3) What are the main risks SaaS firms face under ISO 27001?
The primary risks usually center on:
- Data Leakage: Misconfigured S3 buckets or databases exposed to the public internet.
- Access Control: Over-privileged employees or lack of MFA.
- Supply Chain: Vulnerabilities introduced by third-party libraries or vendors.
- Availability: Downtime due to poor redundancy or successful DDoS attacks.
4) How long does ISO 27001 take for a SaaS company?
For a typical Series A or B SaaS company, it takes 4 to 6 months to go from zero to "Stage 1 Audit ready." The timeline depends heavily on how quickly your team can remediate gaps (e.g., setting up MFA, writing disaster recovery plans). With Konfirmity’s managed service, we often accelerate this by handling the documentation and project management, allowing your team to focus solely on technical controls.
5) Does ISO 27001 help with enterprise sales?
Absolutely. It acts as a trust accelerant. It answers 80% of the questions in a security questionnaire upfront. It allows your sales team to say, "We are ISO 27001 certified," which often bypasses the initial stages of vendor risk assessment and moves the deal straight to contract negotiation.





.svg)





.svg)
.svg)