Enterprise procurement teams have changed how they buy. Five years ago, a security questionnaire was a formality. Today, it is a gatekeeper. If you are selling software or services to large organizations, you know the drill: the deal stalls until you prove your security posture. While SOC 2 dominates the North American market, international enterprise deals—and increasingly US-based ones—demand ISO 27001 compliance.
Many technical leaders believe they are ready because they use secure cloud infrastructure or have strong engineering practices. However, operational security often differs significantly from audit-ready compliance. This is where an ISO 27001 Gap Assessment Guide becomes critical. It is the only way to know exactly where you stand before an external auditor enters the room.
At Konfirmity, we have supported over 6,000 audits. We see a consistent pattern: companies that skip the gap assessment face "audit shock." They discover too late that their informal processes, while effective for engineering, fail to meet the evidence requirements of an ISO 27001 auditor. This guide covers what a gap assessment entails, why it reduces sales friction, and how to execute one effectively.
What Is an ISO 27001 Gap Assessment?
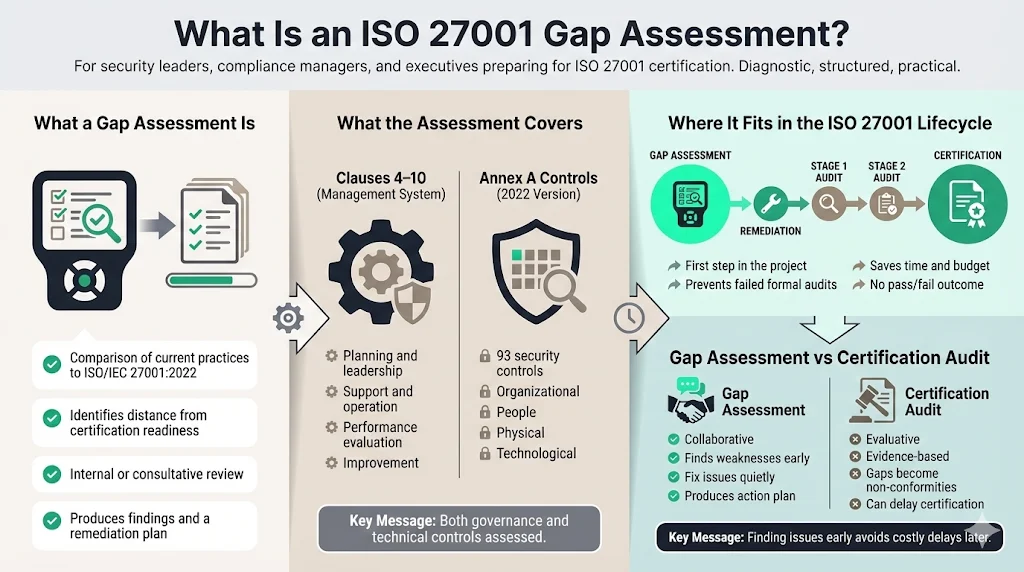
An ISO 27001 gap assessment is a detailed review of your organization's current information security practices compared to the requirements of the ISO/IEC 27001:2022 standard. Think of it as a dry run or a diagnostic test. It identifies the distance between your current operations and the requirements for certification.
The assessment looks at two distinct areas:
- Clauses 4–10: The mandatory management system requirements (planning, support, operation, performance evaluation).
- Annex A Controls: The specific security controls (now 93 controls in the 2022 version) covering organizational, people, physical, and technological areas.
How It Fits the Lifecycle
This assessment happens at the very start of the certification project. It prevents the waste of budget on formal audits that you are destined to fail. Unlike the Stage 1 or Stage 2 certification audits conducted by a registrar, a gap assessment is internal or consultative. It results in a remediation plan, not a pass/fail certificate.
Assessment vs. Certification Audit
A gap assessment is collaborative. The goal is to find holes in the armor so you can fix them. A certification audit is evaluative. The auditor’s job in a certification audit is to verify conformity based on evidence provided. If a gap appears during a certification audit, it becomes a "Non-Conformity" that can delay your certificate by months. Finding that same issue during a gap assessment allows you to fix it quietly on your own terms.
Why Enterprise-Focused Companies Need a Gap Assessment
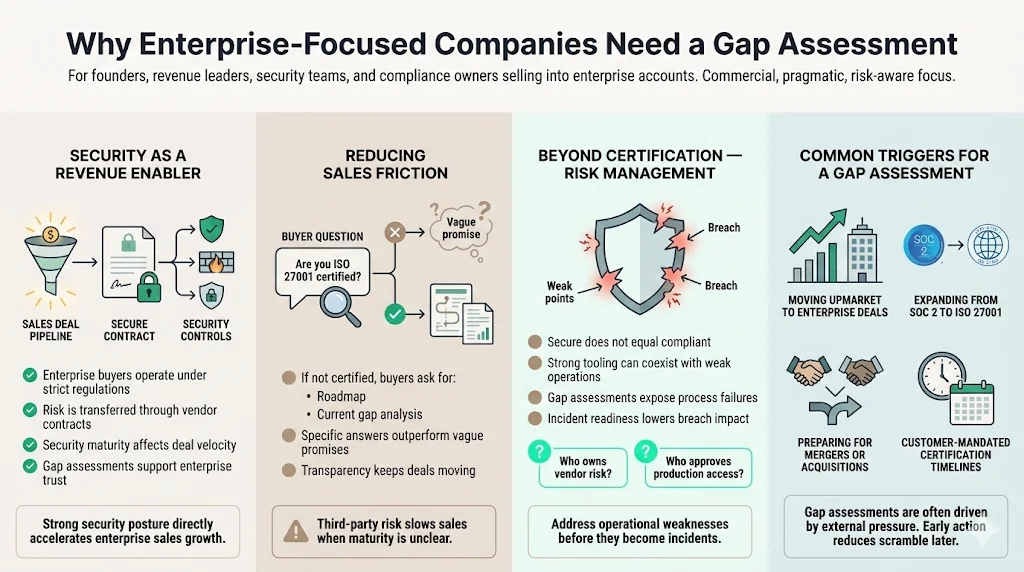
If you sell to the enterprise, security is a revenue enabler. Your customers operate under strict regulatory regimes—GDPR, HIPAA, DORA, and internal governance mandates. They transfer this risk to you via vendor contracts.
Reducing Sales Friction
When a Global 2000 buyer asks, "Are you ISO 27001 certified?" and the answer is "No, but we are working on it," their next question is, "Can you share your roadmap and current gap analysis?"
Having a structured gap assessment allows you to answer security questionnaires with precision. Instead of vague promises, you can state, "We have identified gaps in access control logging and are implementing a solution by Q3." This transparency builds trust and keeps the deal moving. Research from Gartner's Audit Priorities indicates that third-party risk remains a top concern for boards, extending sales cycles by weeks when vendors cannot prove maturity.
Beyond Certification: Risk Management
Startups and growth-stage companies often confuse "secure" with "compliant." You might have excellent code scanning but weak employee offboarding processes. A gap assessment exposes these operational risks. The 2025 IBM Cost of a Data Breach Report found that organizations with high levels of incident response planning and testing saved nearly $2.5 million compared to those with low levels. A gap assessment is the first step in establishing that planning.
It forces a discussion about ownership. Who owns vendor risk? Who approves access to production?
Frequent Triggers
We typically see companies initiate an ISO 27001 Gap Assessment Guide review during:
- New Enterprise Sales Motion: Moving upmarket from SMB to Enterprise deals.
- SOC 2 to ISO 27001 Transition: Expanding from US-only sales to Europe or Asia. The ISO Survey consistently shows double-digit growth in certifications, reflecting global demand.
- M&A Activity: Preparing for due diligence during an acquisition.
- Customer Deadlines: A major client contractually requiring certification within 12 months.
Understanding ISO 27001 Scope and Requirements
Before starting the assessment, you must understand what ISO 27001 actually requires. It is not just an IT checklist. It is a standard for an Information Security Management System (ISMS).
The ISMS Concept
An ISMS is the framework of policies, procedures, and controls that manage information risk. The standard does not tell you how to encrypt data; it requires you to decide how you will encrypt it based on risk, document that decision, do it, and prove you did it.
Core Components Reviewed
A gap assessment evaluates:
- Context of the Organization: Do you understand legal and contractual obligations?
- Leadership: Is management actually involved, or is this just an IT project?
- Planning: How do you address risks?
- Support: Do you have the resources and competence?
- Operation: How do you control processes?
- Performance Evaluation: Do you monitor and audit yourself?
- Improvement: How do you fix broken things?
Annex A Overview
The 2022 update reorganized controls into four themes:
- Organizational: Policies, asset return, information classification.
- People: Screening, awareness training, remote work.
- Physical: Security zones, equipment maintenance.
- Technological: Access rights, malware protection, logging, secure coding.
Step-by-Step ISO 27001 Gap Assessment Process
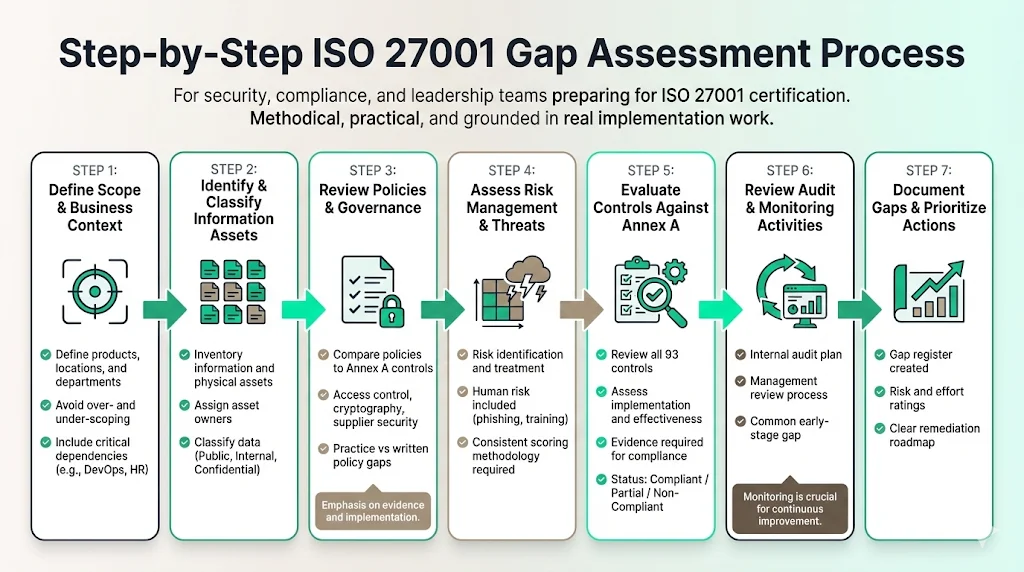
This section details the practical execution. This ISO 27001 Gap Assessment Guide approach mirrors the methodology Konfirmity uses for our managed service clients.
Step 1: Define Scope and Business Context
You cannot assess what you have not defined. The most common error is over-scoping (including the entire company when only one product line matters) or under-scoping (excluding the HR team that hires the engineers).
- Action: Define the boundaries. Which products, locations, and departments are included?
- Pitfall: Excluding dependencies. If your SaaS platform relies on a specific DevOps team, they are in scope.
Step 2: Identify and Classify Information Assets
ISO 27001 focuses on asset protection. You need an inventory.
- Action: List information assets (customer data, code repositories, intellectual property) and physical assets (laptops, servers).
- Action: Assign owners to these assets.
- Gap Check: Does every laptop have an owner? Is data classified (e.g., Public, Internal, Confidential)?
Step 3: Review Existing Security Policies and Governance
Most companies have a few policy documents in a Google Drive folder.
- Action: Compare current policies against the Annex A controls. Do you have an Access Control Policy? A Cryptography Policy? A Supplier Security Policy?
- Gap Check: The gap is often "practice vs. written policy." You might have 2FA enabled everywhere (good practice) but no policy stating it is mandatory (compliance gap).
Step 4: Assess Risk Management and Threat Processes
This is the engine of the ISMS. With the Verizon Data Breach Investigations Report (DBIR) highlighting that 74% of breaches involved the human element, your risk assessment must account for phishing and awareness training, not just technical vulnerabilities.
- Action: Review how you identify and treat risks. Do you have a risk register?
- Action: Verify if you evaluate threats regularly.
- Gap Check: Many companies lack a formal methodology for scoring risk (e.g., Likelihood x Impact). ISO requires a consistent criteria.
Step 5: Evaluate Security Controls Against ISO 27001
This is the deep dive into Annex A.
- Action: Go through the 93 controls. For each, ask: Is this implemented? Is it effective? Is there evidence?
- Action: Document the status: "Compliant," "Partial," or "Non-Compliant."
- Gap Check: Look for evidence trails. A control is not compliant just because you say it is.
Step 6: Review the Audit Process and Monitoring Activities
ISO 27001 requires you to audit yourself (Internal Audit) and for management to review the system (Management Review).
- Action: Check if there is a plan for internal audits.
- Gap Check: Startups almost never have this. It is usually a 100% gap that needs building from scratch.
Step 7: Document Gaps and Prioritize Actions
- Action: Create a report listing every gap.
- Action: Rate them by effort (Low/Med/High) and risk (Critical/Major/Minor).
- Outcome: A remediation roadmap.
What Evidence Is Reviewed During a Gap Assessment
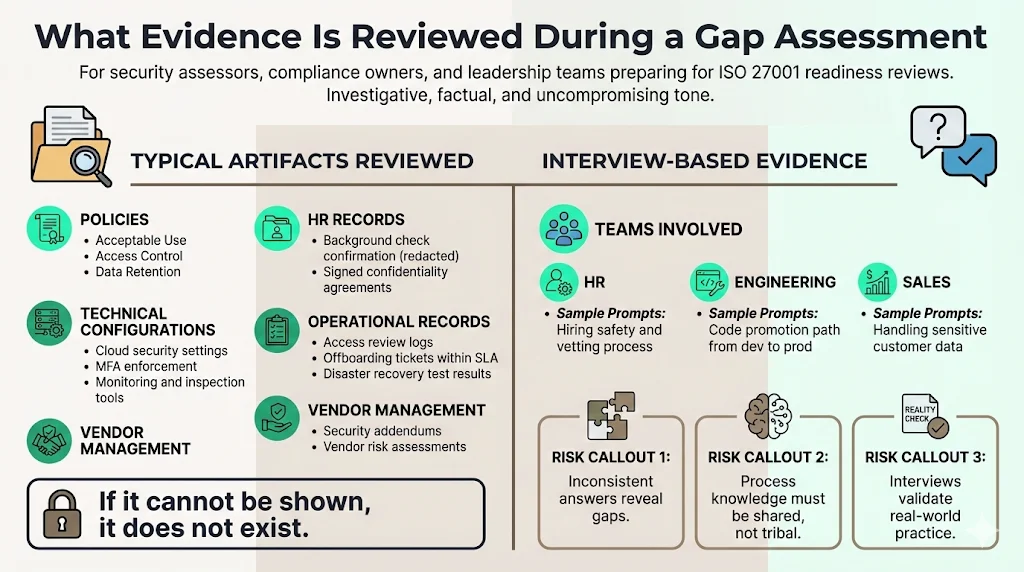
A gap assessment is not a conversation; it is an investigation. If you cannot show it, you do not do it.
Typical Artifacts
- Policies: Acceptable Use, Access Control, Data Retention.
- HR Records: Background check confirmations (redacted), signed confidentiality agreements.
- Technical Configs: Screenshots of AWS Inspector, Cloudflare settings, MFA enforcement settings in Google Workspace/Okta.
- Operational Records: Logs of access reviews, tickets showing employee offboarding within SLA, evidence of disaster recovery tests.
- Vendor Management: Contracts with security addendums, vendor risk reviews.
Interview Evidence
Assessors will talk to HR, Engineering, and Sales.
- Ask HR: "How do you know a candidate is safe to hire?"
- Ask Engineering: "Show me how code moves from development to production."
- Ask Sales: "What do you do if a customer sends a contract via unencrypted email?"
The gap often lies in the inconsistency of answers across the team.
Who Should Conduct an ISO 27001 Gap Assessment
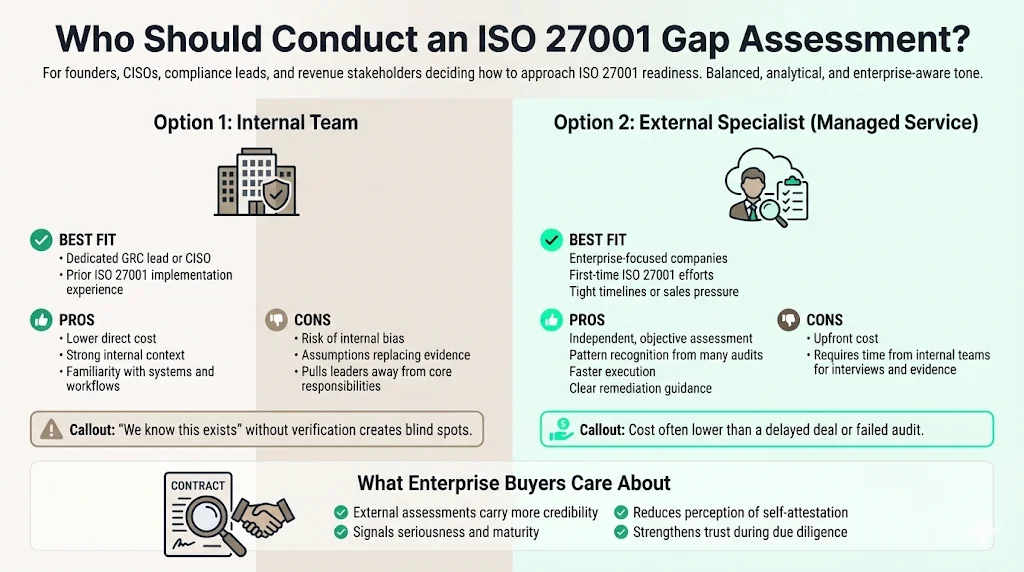
You have two choices: internal or external.
Internal Team
If you have a dedicated GRC lead or CISO with prior ISO 27001 implementation experience, they can do this.
- Pros: Cost-effective, deep knowledge of internal politics.
- Cons: internal bias ("I know we do this, so I won't check the logs"), distraction from core duties.
External Specialist (Managed Service)
This is where firms like Konfirmity operate.
- Pros: Objectivity. We see what you miss. Benchmarking against 6,000+ other audits. Speed.
- Cons: Cost (though often lower than the cost of a failed audit or delayed sales deal).
For enterprise sellers, an external assessment carries more weight. It shows buyers you are treating the process seriously, not just marking your own homework.
How Long an ISO 27001 Gap Assessment Takes
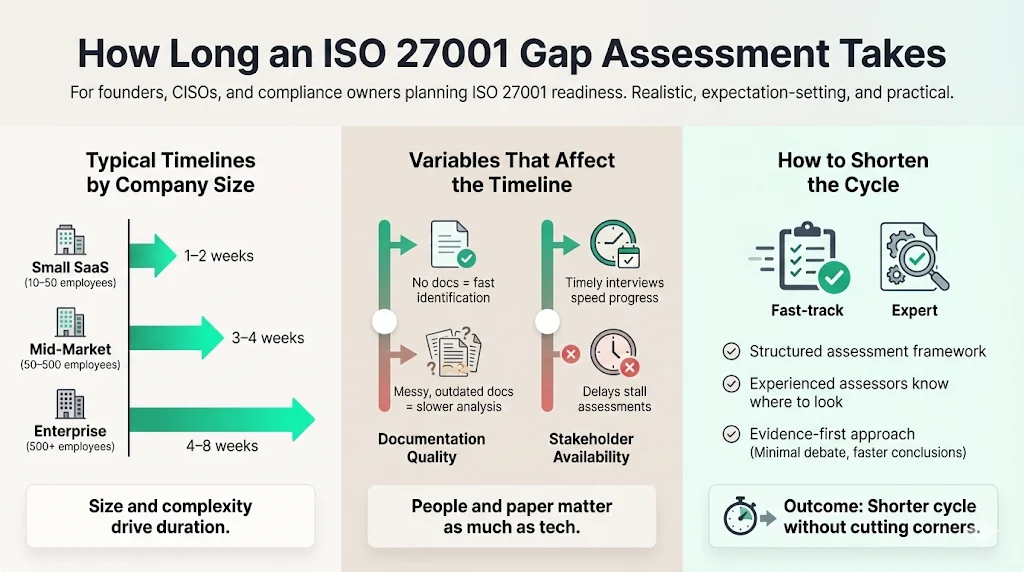
The duration varies based on organizational size and complexity.
- Small SaaS (10–50 employees): 1–2 weeks.
- Mid-Market (50–500 employees): 3–4 weeks.
- Enterprise (500+ employees): 4–8 weeks.
Variables Affecting Timeline
- Documentation Quality: If you have nothing written down, the assessment is fast (it's all a gap). If you have messy, outdated docs, it takes longer to parse.
- Stakeholder Availability: Can we get 30 minutes with the CTO this week or next month?
Shortening the Cycle
Using an ISO 27001 Gap Assessment Guide framework helps, but experienced human guidance moves faster. We know exactly what to look for. We don't waste time debating the meaning of a control; we check the evidence and move on.
Common Gaps Found in Enterprise-Facing Companies
After decades in this field, we see the same issues repeatedly.
1. Informal Offboarding
You remove their Slack access, but their GitHub account stays active for three weeks. This is a critical non-conformity.
2. Lack of Asset Inventory
"We are in the cloud, AWS manages hardware." True, but you manage the virtual instances, the S3 buckets, and the laptops developers use. Missing a clear inventory is a major gap.
3. Weak Vendor Risk Management
You buy SaaS tools with a credit card but never check their security. ISO 27001 requires you to evaluate the security of your suppliers.
4. No Internal Audit Function
You cannot certify without an internal audit. Most companies have no one qualified to perform this impartial review.
5. Over-reliance on Tools
Buying a GRC automation tool is not a gap assessment. Tools often mark controls as "green" because a setting is on, failing to catch that the process surrounding it is broken.
Turning Gap Assessment Results Into Certification Readiness
The assessment is useless if it sits in a drawer. You must convert findings into a project plan.
Remediation Planning
Group gaps into logical projects:
- Project A: HR Security. Fix background checks and onboarding/offboarding.
- Project B: Engineering Controls. Automate change management evidence and access reviews.
- Project C: Governance. Write policies and set up the risk register.
Assigning Ownership
Assign tasks to specific people, not departments. "Engineering to fix logging" fails. "DevOps Lead to enable CloudTrail logs by Friday" works.
The Role of Konfirmity
This is where our Human-Led Managed Service model differentiates itself. We don't just hand you a PDF of gaps. We help close them. We write the policies. We configure the evidence collection. We sit with your team to design controls that fit your workflow.
Tools, Templates, and Frameworks That Help
While human expertise is primary, tools support the process.
Templates
Structured spreadsheets for the Gap Analysis and Risk Register are standard. They provide a clear view of the 93 controls and your status against them.
Automation Platforms
Tools like Drata or Vanta are useful for continuous monitoring after you have designed your processes. During a gap assessment, they can help pull configuration data, but they cannot assess your physical security or HR interview responses.
Control Tracking
We use proprietary tracking systems that map your controls to ISO 27001, SOC 2, and HIPAA simultaneously. This allows you to "test once, comply many times."
Conclusion
Security is a fundamental requirement for doing business with the enterprise. An ISO 27001 Gap Assessment Guide is your roadmap to revenue. It creates clarity, reduces risk, and provides the confidence needed to sign six-figure contracts.
Skipping this step leads to "compliance manufacturing"—a frantic, expensive scramble before an audit that usually results in a fragile system. Instead, build a durable program. Start with a gap assessment. Understand your reality. Then, close the gaps with engineered controls that protect your business and satisfy your customers.
At Konfirmity, we believe in outcomes. We don't just advise on the gaps; we execute the fix. If you are ready to move from uncertainty to audit readiness, the gap assessment is your first move.
Frequently Asked Questions (FAQ)
1) What is an ISO 27001 gap assessment?
A structured review that compares current information security practices against ISO 27001 requirements to identify missing or weak areas.
2) Who should conduct an ISO 27001 gap analysis?
It can be done internally by a trained team or by an external specialist, depending on skills, time, and the need for independent review.
3) How long does an ISO 27001 gap assessment take?
Most organizations complete it within a few weeks, though timing varies based on scope and readiness.
4) What evidence is reviewed during a gap assessment?
Policies, risk documentation, asset inventories, access controls, incident records, and interviews with critical staff.
5) How often should a gap assessment be done?
At minimum before starting certification and again after major business, system, or regulatory changes.





.svg)





.svg)
.svg)