Most enterprise buyers now request security assurance artifacts before procurement. Healthcare companies face even greater scrutiny because they handle electronic protected health information (ePHI). In 2025 there were more than sixty reported healthcare breaches every month, affecting about 71,000 records on average. The average cost of a breach in the United States remains high at $10.22 million and it takes roughly 279 days to identify and contain one. When you add enforcement actions from the Office for Civil Rights (OCR)—from $25,000 settlements for failing to perform a risk assessment to multi‑million dollar penalties for neglecting audit controls—it becomes clear why a systematic HIPAA Readiness Guide is essential.
A HIPAA readiness program means preparing your systems, processes, and teams to meet the Privacy, Security, and Breach Notification Rules. This guide is written for healthcare CTOs, CISOs, compliance officers, and enterprise buyers who need to demonstrate compliance without sacrificing delivery velocity. It offers actionable steps and practical examples, alongside checklists and templates drawn from Konfirmity’s experience managing more than six thousand audits and twenty‑five years of combined security expertise. By the end, you’ll have a blueprint for continuous compliance across HIPAA, SOC 2, ISO 27001, and GDPR.
What is HIPAA and who must comply?
The Health Insurance Portability and Accountability Act (HIPAA) protects the confidentiality, integrity, and availability of PHI. Covered entities include healthcare providers, insurers, and clearinghouses. Business associates that process PHI on behalf of covered entities—such as billing firms, cloud service providers, or analytics vendors—must also comply.
Core HIPAA Rules
- Privacy Rule – Governs uses and disclosures of PHI, grants individuals rights over their health information, requires notice of privacy practices, and mandates that only the minimum necessary information be disclosed.
- Security Rule – Establishes administrative, physical, and technical safeguards to protect ePHI. Covered entities must ensure confidentiality, integrity, and availability; protect against reasonably anticipated threats; and train workforce members. The rule is technology neutral but requires documented policies and risk management.
- Breach Notification Rule – Requires covered entities and business associates to notify affected individuals, the OCR, and in some cases the media following a breach of unsecured PHI. A breach risk assessment must consider the nature of the PHI, whether it was viewed or acquired, the unauthorized person, and the extent of mitigation.
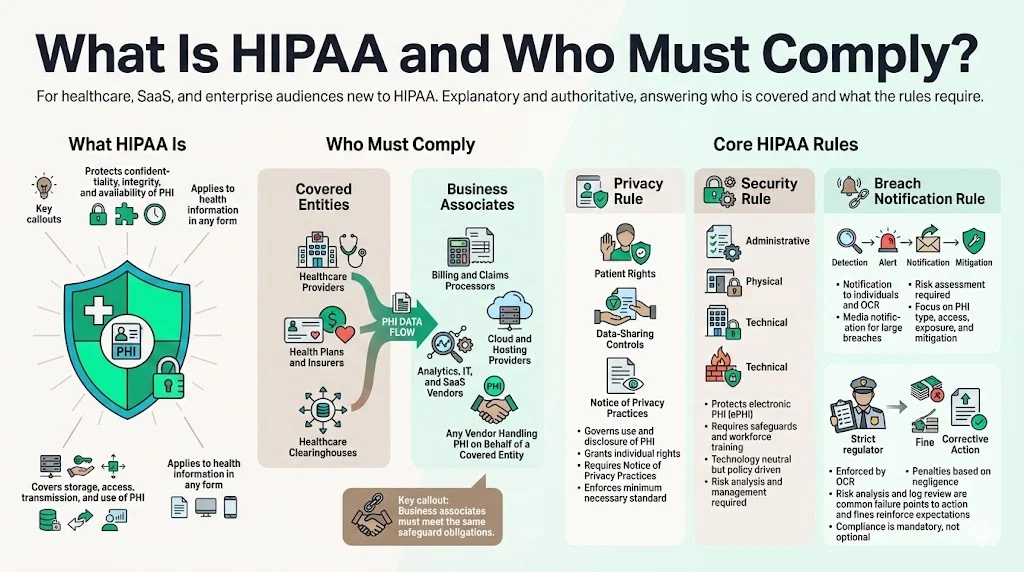
HIPAA also includes enforcement provisions. OCR can impose civil monetary penalties based on the level of negligence. In 2025 Warby Parker agreed to a $1.5 million penalty for failing to conduct a risk analysis, implement security measures, and regularly review system activity. Vision Upright MRI entered a corrective action plan for similar lapses. These cases reinforce that compliance is not optional.
Understanding regulatory requirements
Risk assessment and documentation
HIPAA does not prescribe specific technologies but demands a risk‑based approach. NIST Special Publication 800‑66 describes the required methodology: identify where ePHI resides, assess threats and vulnerabilities, and evaluate the likelihood and impact of harm. The assessment must be “accurate and thorough” and updated after significant changes to systems or vendors. OCR expects documentation of risk analysis results, remediation plans, and periodic reviews. Ongoing risk management is also required: organizations must implement security measures to reduce risks to a “reasonable and appropriate” level.
Privacy and security expectations
The Privacy Rule requires policies covering permissible uses of PHI, individual rights (access, amendment, accounting of disclosures), and the minimum necessary standard. It also obligates organizations to issue a Notice of Privacy Practices that describes how PHI may be used and shared and explains how individuals can assert their rights.
The Security Rule divides safeguards into administrative (policies and procedures, workforce training, risk management), physical (facility access controls, device and media controls), and technical (access controls, audit controls, integrity controls, and transmission security). At a high level, your program must ensure that only authorized individuals can access ePHI, that audit logs are retained and reviewed, and that data are protected during storage and transmission.
Finally, the Breach Notification Rule mandates prompt notification. OCR expects notifications to individuals and HHS within 60 days for breaches affecting 500 or more individuals; smaller breaches must be logged and reported annually. Timely notification not only fulfills your legal obligation—it also demonstrates transparency to customers and partners.
HIPAA readiness checklist: your step‑by‑step roadmap
Konfirmity’s HIPAA Readiness Guide provides a structured path to compliance. Rather than treating compliance as a one‑off project, the checklist helps you build a living program that integrates with SOC 2 and ISO 27001 controls. Each task below includes roles, example controls, and metrics.
The HIPAA Readiness Guide breaks tasks into manageable components and supports cross‑framework reuse, helping teams reuse security evidence for HIPAA, SOC 2, ISO 27001, and GDPR.
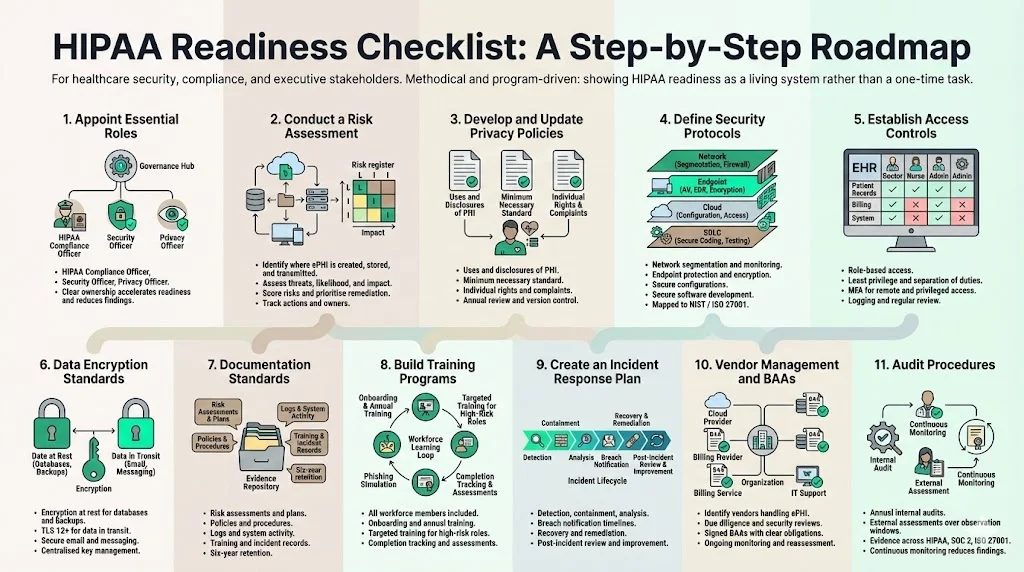
1) Appoint essential roles
- HIPAA Compliance Officer – Responsible for overall HIPAA program design, policy creation, training, and liaison with OCR. Should have authority to drive changes across departments.
- Security Officer – Oversees technical safeguards (access control, encryption, logging) and risk assessments; often the CISO or a senior security engineer.
- Privacy Officer – Focuses on privacy policies, patient rights, and minimum necessary disclosures.
Assigning clear ownership ensures accountability. In Konfirmity’s work, organizations with dedicated officers complete readiness programs 30–40 percent faster and experience fewer findings during audits.
2) Conduct a risk assessment
Conducting a thorough risk assessment is the foundation of any compliance effort. NIST SP 800‑66 outlines the following steps:
- Prepare: Identify where ePHI is created, received, maintained, or transmitted. Map data flows across clinical systems, cloud providers, personal devices, and backup media. Don’t forget remote workers and contractors.
- Identify threats and vulnerabilities: Consider malicious actors (external hackers, insiders), accidental exposure (misconfiguration, lost devices), and environmental events.
- Assess likelihood and impact: Assign risk scores based on the probability of occurrence and potential harm to patients. For example, insecure email may have a high likelihood of phishing and a moderate impact if it’s the only path to PHI. Ransomware on imaging servers might have a lower likelihood but high impact due to service disruption. Use frameworks such as Common Vulnerability Scoring System (CVSS) to quantify technical risks.
- Analyze and prioritize: Document high‑risk items and plan mitigation actions—patch vulnerabilities, segment networks, train users, or retire legacy systems.
- Record findings: Risk analysis documentation should include methodology, findings, and remediation steps.
A practical risk scoring template might include: asset name, location of ePHI, vulnerability description, threat actor, likelihood (low/medium/high), impact (low/medium/high), risk rating (product of likelihood and impact), proposed control, and responsible owner. Konfirmity clients often use spreadsheets or dedicated GRC tools integrated with ticketing systems to track remediation.
3) Develop and update privacy policies
Policies translate legal requirements into operational guidance. Your privacy policy must:
- Describe how PHI is used and disclosed for treatment, payment, and healthcare operations.
- Explain the minimum necessary standard and role‑based disclosures.
- Outline individual rights (access, amendment, restriction, confidential communications).
- Provide contact information for complaints and questions.
- Reference your Notice of Privacy Practices and how individuals can obtain it.
Konfirmity typically drafts policies using plain language, crossreferences them with existing SOC 2/ISO 27001 control maps, and schedules reviews at least annually or whenever there are regulatory updates. Version control and record retention are essential—OCR may request historical policies during investigations.
4) Define security protocols
Technical and organizational controls protect ePHI in transit and at rest:
- Network and infrastructure security: Deploy firewalls and intrusion detection/prevention systems. Segment sensitive networks and restrict inbound/outbound traffic.
- Endpoint protection: Ensure workstations, servers, and mobile devices have up‑to‑date antimalware and intrusion protection. Use disk encryption for laptops and portable media.
- Configuration management: Apply secure baselines and continuous configuration monitoring. Tools like AWS Config, Azure Policy, or Kubernetes audit logs can catch misconfigurations early.
- Secure software development: Use secure coding standards, code scanning, and penetration testing.
A practical approach is to map your program to the NIST Cybersecurity Framework or ISO 27001 Annex A controls. For example, SOC 2 requires evidence across roughly 80 controls—many of these overlap with HIPAA’s technical safeguards. Konfirmity integrates these controls into the client’s CI/CD pipelines and infrastructure‑as‑code templates, reducing manual effort.
As prescribed by the HIPAA Readiness Guide, these security protocols should map to recognized frameworks, ensuring that your HIPAA controls reinforce and are reinforced by SOC 2 and ISO 27001 practices.
5) Establish access controls
Only authorized personnel should access ePHI:
- Role‑based access: Define roles for clinicians, billing staff, administrators, and contractors. Each role should have the minimum permissions necessary for its duties.
- Least privilege and segregation of duties: Limit write and delete privileges; separate administrative functions (system administration vs. security management).
- Multi‑factor authentication (MFA): Implement MFA for remote access and privileged accounts. Use hardware tokens or mobile authenticators.
- Logging and monitoring: Maintain audit logs of all user access to ePHI. Audit controls were a specific violation in the Warby Parker case—the organization failed to regularly review system activity. Logs should record user IDs, timestamps, action types, and success/failure.
A sample access control policy might state: “Access to the Electronic Health Record (EHR) system is granted based on job role and documented on the access control matrix. All users must authenticate using username, password, and an approved MFA method. Security operations reviews logs weekly for unauthorized access attempts and retains logs for six years.”
6) Data encryption standards
While the Security Rule does not explicitly require encryption, it is an addressable implementation specification. Encryption is strongly advised because it can mitigate breach notification obligations—encrypted data are considered “secured” under the Breach Notification Rule. Implement encryption at rest for databases, file systems, and backups. In transit, use TLS 1.2 or higher and enforce HTTPS for web applications and APIs. Consider email encryption and secure messaging platforms for clinical communication. Select tools that integrate with key management systems to enforce rotation and least privilege.
7) Documentation standards
Compliance is demonstrated through evidence. Maintain documentation for:
- Risk assessments and risk management plans – including methodologies, results, and remediation tracking.
- Policies and procedures – privacy, security, incident response, training.
- Audit logs and system activity reports – accessible upon request and reviewed regularly.
- Training records – date, content, and participant signatures.
- Incident reports and breach notifications – documented decisions, notifications, and remediation actions.
OCR expects documentation to be retained for six years. Konfirmity organizes documentation using secure, searchable repositories integrated with ticketing and project management systems. Tag documents by control requirement and cross‑framework mapping; this makes audits more efficient and reduces time to produce evidence.
8) Build training programs
Human error contributes to many breaches. For instance, phishing remains a leading attack vector for credential compromise. Training should be practical and continuous:
- Audience: All workforce members, including executives, clinicians, contractors, and volunteers.
- Format: A mix of live sessions, web‑based modules, and simulated phishing drills.
- Frequency: At hire and annually thereafter; quarterly micro‑ training for high‑risk roles.
- Content: Overview of HIPAA rules, privacy rights, security best practices, acceptable use, incident reporting procedures, and real‑world case studies.
- Tracking: Maintain records of completion and assessment results.
A training schedule might look like: orientation training during onboarding (two hours), annual full training in March (two sessions), quarterly phishing simulations with debrief, and targeted deep dives for administrators and developers.
9) Create an incident response plan
When a security event occurs, response must be swift and coordinated. A strong plan should include:
- Detection: Define how incidents are identified (SIEM alerts, user reports, monitoring tools).
- Containment: Steps to isolate affected systems, preserve evidence, and prevent further damage.
- Analysis: Determine whether ePHI was compromised, assess severity, and document findings.
- Notification: Follow Breach Notification Rule timelines—notify individuals and HHS within 60 days for major breaches. Include a description of what happened, what data were involved, and mitigation steps.
- Recovery and remediation: Restore systems, rotate credentials, patch vulnerabilities, and update controls.
- Post‑incident review: Record lessons learned and improve policies and technologies.
Example scenario: A lost laptop containing unencrypted patient data triggers the incident response plan. The security officer determines the laptop belonged to a billing manager; it was lost at a conference. Because the device lacked disk encryption, this constitutes a breach. Within 24 hours the team assessed that the laptop contained billing records for 750 patients. Within 60 days they notify the individuals and the OCR, providing credit monitoring and detailing encryption measures being implemented. Documentation of these steps will demonstrate compliance.
10) Vendor management and Business Associate Agreements (BAAs)
The HIPAA Readiness Guide stresses vendor management as a critical component of compliance. Many breaches originate through vendors. In October 2025 business associates accounted for a significant portion of reported healthcare breaches. To manage vendor risk:
- Identify vendors that handle or can access ePHI. Examples include cloud providers, payment processors, and telehealth platforms.
- Perform due diligence: Assess each vendor’s security practices, certifications (SOC 2, ISO 27001), and history. Use questionnaires covering administrative, technical, and physical safeguards.
- Execute BAAs: A BAA must define permitted uses/disclosures, require compliance with HIPAA, and obligate the vendor to report breaches. Ensure indemnification and right-to-audit clauses.
- Ongoing monitoring: Review vendors annually, track security incidents, and require updated third‑party audit reports.
Konfirmity often builds vendor risk processes into procurement. For example, a healthcare client needed to onboard a telehealth platform quickly. We mapped vendor controls to the client’s HIPAA and SOC 2 requirements, negotiated stronger encryption clauses, and scheduled quarterly security review calls. This prevented compliance delays during due diligence.
11) Audit procedures
Audits verify that controls operate effectively. Prepare for both internal and external reviews:
- Internal audits: Conduct at least annually. Review compliance with policies, test controls, and verify documentation. Use sampling methods to check access logs, training completion, and incident response records.
- External audits/assessments: Independent auditors (like AICPA‑accredited firms for SOC 2 or ISO 27001 certifying bodies) evaluate controls over an observation period. Evidence must show consistent control operation—not just point‑in‑time compliance.
- Audit artifacts: Provide risk assessments, policies, logs, training records, and evidence of remediation. For SOC 2 Type II audits, evidence spans 64 trust services criteria and roughly 80 controls.
Konfirmity’s managed service includes pre‑audit dry runs and auditor liaison. Our clients cut time spent gathering evidence by up to 75 percent and reduce findings by focusing on continuous monitoring rather than last‑minute document sprints.
Technology safeguards that work
Technology can accelerate compliance but must be implemented thoughtfully. Our HIPAA Readiness Guide outlines how tools support HIPAA readiness without replacing the fundamental need for risk management. Here are tools that support HIPAA readiness:
- Security Information and Event Management (SIEM): Aggregates logs from EHR systems, network devices, and applications; detects anomalies; and triggers alerts. Integration with ticketing systems facilitates response.
- Audit logging and configuration management: Tools like OSQuery, AWS CloudTrail, or Kubernetes Audit Logs track system activity. Configuration management platforms ensure systems remain in a compliant state and alert on drift.
- Encryption solutions: Full‑disk encryption for endpoints, database encryption (e.g., Transparent Data Encryption), and secrets management systems.
- Identity and access management: Single Sign‑On (SSO), MFA, and privileged access management systems maintain controlled access across on‑premises and cloud workloads.
- Continuous compliance platforms: Managed services like Konfirmity connect your environment to compliance frameworks, map controls to requirements, and automate evidence collection. Unlike self‑serve GRC tools that shift burden to your team, a human‑led managed service implements and operates controls.
Technology should support, not replace, a strong risk management process. Tools must be configured correctly and monitored to ensure effectiveness.
Examples of practical implementation
The HIPAA Readiness Guide includes templates, sample language, and schedules to simplify implementation. The following examples illustrate how to apply the principles discussed in this guide.
Risk assessment summary template
Sample access control policy language
The organization restricts access to ePHI based on job roles documented in the access control matrix. The Security Officer provisions user accounts upon receipt of a written request approved by the HIPAA Compliance Officer. All access requires password and multi‑factor authentication. Privileged accounts must use hardware tokens. The Security Officer reviews user access quarterly and removes accounts for terminated or transferred personnel. Audit logs are retained for at least six years and are reviewed weekly.
Breach notification timeline example
Training program schedule
Common challenges and tips to overcome them
The HIPAA Readiness Guide not only charts the optimal path but also calls attention to obstacles that organizations often encounter. Recognizing these challenges early lets you allocate resources proactively.
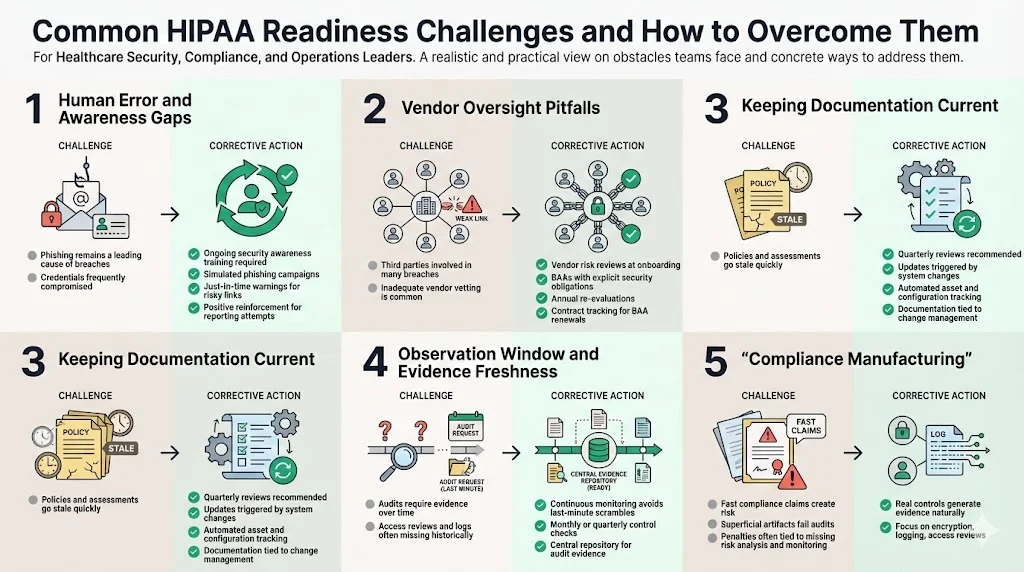
1) Human error and awareness gaps
Phishing remains prevalent: 74 percent of healthcare organizations reported credential compromise via phishing in recent years. Combat this by integrating ongoing training, simulated phishing campaigns, and just‑in‑time warnings when users encounter suspicious links. Use positive reinforcement when employees report suspected phishing.
2) Vendor oversight pitfalls
Over a third of reported breaches involve third parties. Many organizations fail to rigorously vet vendors or monitor their compliance. Build a vendor risk program that assesses security practices at onboarding, includes BAAs with explicit security obligations, and re‑evaluates vendors at least annually. Ensure your contract management system tracks BAA expiration and renewal.
3) Keeping documentation current
Policies, risk assessments, and inventory lists can quickly become stale. Set calendar reminders to review them quarterly or whenever significant changes occur (e.g., new EHR module). Use automated configuration and inventory tools to generate up‑to‑date lists of systems, devices, and data flows. Integrate documentation updates into change management processes.
4) Observation window and evidence freshness
For SOC 2 Type II and ISO 27001 surveillance audits, auditors expect evidence covering an observation period—often 3–12 months. Many organizations scramble when auditors request proof of access reviews from six months ago. Avoid this by adopting continuous monitoring tools and establishing monthly or quarterly control performance checks. Document each review in a repository accessible to auditors. Konfirmity clients using automated evidence collection reduce auditor requests by two‑thirds.
5) Compliance manufacturing
Beware of promises like “SOC 2 ready in two weeks.” Real compliance requires design, implementation, and operation of controls over time. OCR penalties often stem from superficial efforts: Warby Parker’s penalty noted failure to conduct risk analysis and monitor system activity. Instead of manufacturing artifacts, invest in real security controls—encryption, logging, access reviews—that produce evidence naturally.
Measuring HIPAA readiness and continuous improvement
Your HIPAA Readiness Guide should be a living document. Use performance indicators (KPIs) to measure progress:
- Reduction in high‑risk findings: Track number of critical risks identified in successive assessments. Aim for a downward trend as you remediate.
- Time to detect and respond: Measure mean time to detect (MTTD) and mean time to respond (MTTR) for security incidents.
- Audit success rate: Count the number of findings in external audits and reduce them over time. Konfirmity clients often cut findings by 50–70 percent after implementing continuous monitoring.
- Training completion rate: Aim for 100 percent workforce participation and track improvements in phishing simulation performance.
- Vendor compliance score: Percentage of business associates with current BAAs and acceptable security ratings.
Continuous improvement means revisiting your risk assessment at least annually and after major changes—acquisitions, new vendors, or deploying new systems. Document all updates and train staff on new procedures. As regulations evolve (for example, the 2025 OCR guidance on Telehealth), incorporate changes into policies and controls.
Conclusion
Security that looks good on paper but fails under incident pressure is a liability. Healthcare organizations operate in an environment where cyber‑attackers have both financial and espionage motives, and where regulators impose significant penalties for lapses. A HIPAA Readiness Guide helps you build a durable program that withstands audits and real‑world threats. Start by appointing responsible officers, conducting a thorough risk assessment, and developing policies that reflect your operations. Implement strong technical and organizational controls, train your workforce, and prepare for incidents. Vet your vendors and insist on strong BAAs. Treat your checklist as a living tool—review, update, and improve continuously. With the right foundation and support from human‑led managed services like Konfirmity, compliance becomes a by‑product of good security, not a drain on your team.
FAQ
1. What’s the first thing to do for HIPAA readiness?
Begin with a thorough risk assessment to identify where PHI is stored and what threats exist, then prioritize mitigation efforts. Without understanding your environment, you cannot design appropriate controls or policies.
2. How often should HIPAA risk assessments be done?
Conduct a risk assessment at least annually and after major changes (new systems, vendors, mergers). Ongoing risk management and periodic reviews ensure your program remains effective.
3. Do all vendors need a HIPAA Business Associate Agreement (BAA)?
Yes. If a vendor handles or could access PHI on your behalf, you must have a BAA defining permitted uses, security obligations, and breach notification requirements.
4. What documentation must be kept for HIPAA compliance?
Maintain risk assessments, policies, training records, access logs, incident reports, and evidence of BAAs. Documentation should be retained for at least six years.
5. Is encryption required?
HIPAA does not mandate encryption in every case, but it is strongly advised because encrypted data are considered secure and may exempt you from breach notification requirements. Encrypt data at rest and in transit to protect ePHI.





.svg)






.svg)
.svg)