Most enterprise buyers and healthcare operators ask for assurance artifacts before signing business associate agreements or letting third‑party tools into their workflows. Without demonstrable security and continuous evidence, deals stall—even when teams have paper policies. HIPAA Training Requirements aren’t just regulatory hoops; they set expectations for how you protect sensitive patient data. As the founder of Konfirmity and someone who has shepherded more than 6,000 audits over 25 years, I’ve seen that training is the backbone of a credible compliance program. This article breaks down the legal requirements, offers a step‑by‑step plan, and provides templates so busy leaders can build a training program that satisfies auditors, reduces breach risk and builds trust.
What is HIPAA and why it matters
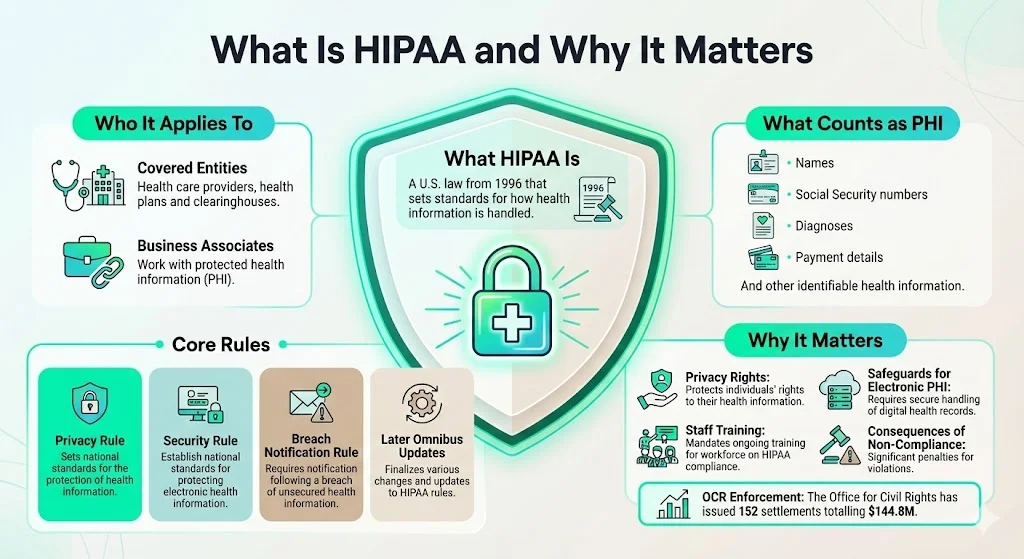
The Health Insurance Portability and Accountability Act (HIPAA) was enacted in 1996 to standardise privacy and security rules for health data. Over time it has expanded through the Privacy Rule (2000), Security Rule (2003), Breach Notification Rule (2009) and subsequent omnibus amendments. HIPAA applies to covered entities—health care providers, health plans and clearinghouses—and to business associates that handle protected health information (PHI). PHI includes identifiers such as names, Social Security numbers, diagnoses and payment details whether recorded on paper, verbal or electronic.
The Privacy Rule requires organisations to notify individuals about their privacy rights, adopt privacy procedures and train employees to follow them. The Security Rule mandates administrative, technical and physical safeguards for electronic PHI (ePHI), including a comprehensive security awareness and training program. Failing to comply can lead to civil or criminal penalties—the U.S. Office for Civil Rights (OCR) has imposed 152 settlements totalling $144.8 million as of October 2024.
HIPAA rules related to training
Privacy Rule
The Privacy Rule governs how PHI may be used and disclosed. It obligates covered entities to train all workforce members on their policies and procedures. “Workforce members include employees, volunteers, trainees, and may also include other persons whose conduct is under the direct control of the entity”. Training must cover patients’ rights, permitted uses, the minimum necessary standard and sanctions for non‑compliance.
Security Rule
The Security Rule focuses on ePHI. Section 164.308(a)(5) requires regulated entities to implement “a security awareness and training program for all members of its workforce”. NIST’s SP 800‑66 Rev. 2 provides practical guidance on implementing this program. Key activities include:
- Conducting a training needs assessment to identify gaps and tailor content.
- Developing a training plan that sets scope, goals, target audiences, learning objectives and evaluation methods.
- Educating staff on guarding against malware, monitoring log‑in attempts and managing passwords.
- Creating evolving content covering topics such as phishing, email security and device protection.
The proposed HIPAA Security Rule update (January 2025) reinforces this by explicitly requiring regulated entities to provide periodic security updates, malicious software training, log‑in monitoring procedures and password management. It also highlights business associate responsibilities, emphasising that covered entities should obtain written assurances that associates will safeguard ePHI.
Breach Notification and Enforcement Rules
The Breach Notification Rule requires organisations to notify affected individuals, the HHS Secretary and sometimes the media within 60 days when unsecured PHI is disclosed. Training should therefore include how to recognise and report incidents, and who to notify. The Enforcement Rule outlines civil money penalties with tiers based on culpability. Fines can range from $141 per violation when there was reasonable diligence to over $2.1 million per violation for willful neglect.
Why HIPAA training is more than a checkbox
A risk‑based training program builds a culture of privacy and security. It educates staff on how their daily actions—sending emails, accessing records, using personal devices—affect compliance. IBM’s 2024 Cost of a Data Breach report found that healthcare breaches cost $10.93 million on average—more than twice the global average and the highest of any industry. Stolen credentials took 292 days to identify on average. Training helps employees recognise phishing emails, secure mobile devices, encrypt data, and follow proper disposal procedures, reducing the likelihood and impact of breaches.
It also reduces regulatory risk. Common enforcement actions involve impermissible disclosures, lack of safeguards, failure to conduct risk analyses and failure to provide HIPAA training or security awareness training. OCR’s enforcement highlights show that many entities misunderstand or misapply the rules. Effective training demonstrates a good‑faith effort toward compliance, which can mitigate penalties even when incidents occur.
Who needs HIPAA training
Under HIPAA, “workforce” includes employees, volunteers, trainees and other persons whose conduct is under direct control of the entity. Anyone who accesses PHI or ePHI must be trained. This includes:
- Clinical staff (physicians, nurses, therapists) who document care and use electronic health record (EHR) systems.
- Administrative staff handling billing, scheduling, coding, claims and patient communications.
- IT teams managing systems, networks, devices and data storage.
- Business associates such as billing companies, cloud service providers, software vendors, telemedicine platforms and external consultants. Covered entities must have a written business associate agreement requiring the associate to protect ePHI.
- Volunteers, interns and contractors, including research fellows, trainees, and temporary staff whose conduct is under the organisation’s control.
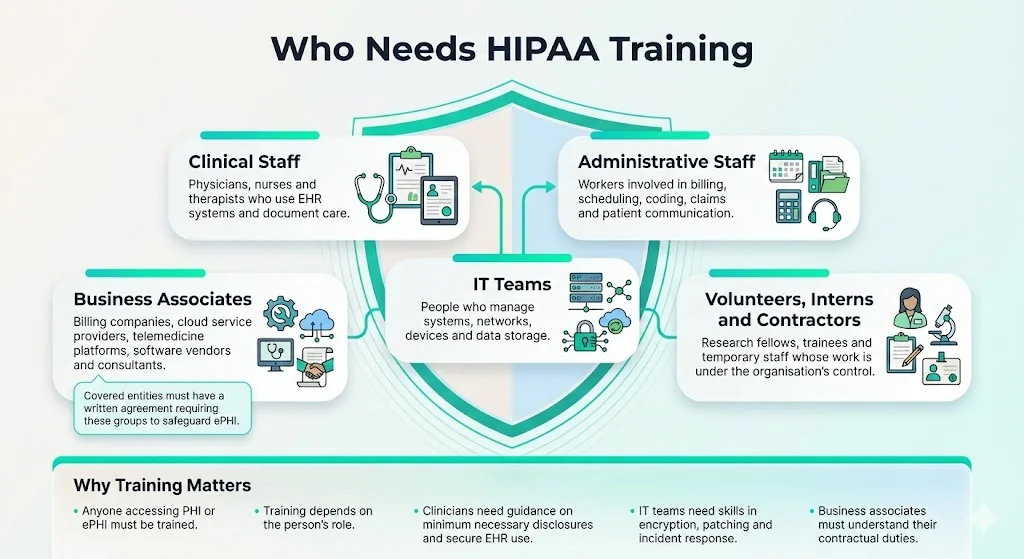
Role‑based training is essential. For example, clinicians need to understand minimum necessary disclosures and how to use EHRs securely, while IT teams must know about encryption, patch management and incident response. Business associates must understand their contractual obligations and security standards.
What HIPAA training should cover
Core topics
- HIPAA fundamentals: Purpose, scope, covered entities, definition of PHI, and why protecting it matters.
- Privacy Rule: Allowed uses and disclosures, patients’ rights (access, correction, restrictions), minimum necessary standard, and sanctions for violations.
- Security Rule: Administrative, technical and physical safeguards. Topics include risk assessment, access controls, audit trails, password policies, multi‑factor authentication, device and media controls, encryption and secure transmission. NIST emphasises that training should address guarding against malware, monitoring log‑ins and managing passwords.
- Breach procedures: How to recognise potential incidents (lost devices, phishing emails, misdirected faxes), steps to contain the incident, documentation and reporting within mandated timelines.
- Policies and procedures: How to handle record requests, consent forms, secure messaging, remote work guidelines and sanction processes.
Extended and role‑specific topics
- EHR and technology use: How to access, edit and store ePHI securely. For example, avoid leaving screens unattended, use secure log‑out, and follow device encryption policies.
- Business associate interactions: Understanding the terms of business associate agreements (BAAs). Covered entities must ensure that associates implement appropriate safeguards and report breaches.
- Sensitive data categories: Extra privacy protections for mental health records, substance‑abuse treatment, HIV status or reproductive health require special care. Highlight applicable state laws and consent requirements.
- Patient communications: Secure portals, SMS messaging, telehealth platforms, and email. Emphasise encryption and explicit consent for unencrypted communication.
- Social media and public disclosures: Posting patient information on social media without consent is prohibited. Use case studies to illustrate what constitutes a violation.
- Real‑world threats: Phishing and spear‑phishing, ransomware, lost/stolen laptops and USB drives, misconfigured cloud storage. Provide incident playbooks for detection and response.
Real‑world examples & case studies
Training resonates when staff see the consequences of poor practices. Recent enforcement actions provide instructive cases:
- Stolen devices and lack of BAAs: Advocate Health Care (AHC) settled for undisclosed millions after four desktop computers and a laptop containing ePHI were stolen, and the organisation had failed to obtain a business associate agreement with a vendor. The OCR cited failure to encrypt devices, poor physical security and missing BAAs.
- Unencrypted laptops: The Feinstein Institute for Medical Research paid $3.9 million after a stolen unencrypted laptop exposed more than 13,000 patient records. Investigators found the institute lacked policies for removing devices, device encryption and risk assessment.
- Phishing attack: In April 2025, the OCR settled with PIH Health for $600,000 after a phishing attack compromised 189,763 individuals’ ePHI, including names, addresses, SSNs, diagnoses and financial data. The investigation identified failures to conduct a thorough risk analysis, to use or disclose PHI only as permitted, and to provide timely breach notifications. As part of the corrective action plan, PIH Health must train its workforce on updated HIPAA policies and procedures.
These cases underscore the importance of encryption, risk analysis, BAAs and ongoing training. They also illustrate how negligence can multiply penalties. Use similar examples internally to make training memorable.
When and how often to deliver HIPAA training
Onboarding and role changes
HIPAA does not specify a strict timeline, but new hires should complete training before they handle PHI or ePHI. This is often within the first week of employment. Role changes—such as moving from an administrative position to an IT role—should trigger additional, role‑specific training. Material changes in policies, regulations, technologies or threat landscape also necessitate retraining.
Recurring and refresher training
While HIPAA doesn’t mandate annual training, industry best practice is to provide refresher sessions at least annually for all staff and more often for high‑risk roles. NIST recommends that training be an ongoing process with periodic updates to address evolving threats. For example:
- Quarterly phishing simulations and security reminders.
- Annual privacy rule reviews and policy updates.
- Just‑in‑time training after an incident or when new systems are implemented.
Documenting training
Proper documentation is crucial for audits. Maintain a training log that records who attended, dates, topics covered, and acknowledgement of completion. The Breach Notification Rule requires that entities be able to demonstrate compliance; well‑kept records show due diligence. Use a simple spreadsheet or a learning‑management system (LMS) to track completions and send reminders. Include version control to ensure that evidence maps to the correct policy revision.
Step‑by‑step implementation guide for busy teams
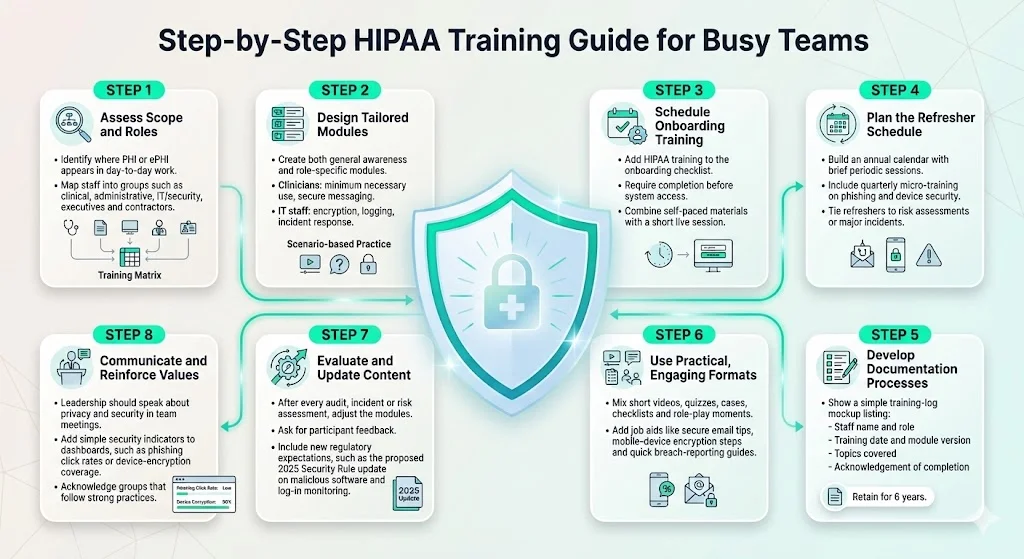
- Assess scope and roles. Identify which functions involve PHI or ePHI. Map roles into categories—clinical, administrative, IT/security, executives, contractors. This mapping informs the training matrix.
- Design tailored modules. Develop separate modules for general awareness and role‑specific content. For example, clinicians need to understand minimum necessary disclosures and secure messaging, while IT staff need training on encryption standards, logging and incident response. Include core topics (privacy, security, breach notification) and add scenario‑based exercises.
- Schedule onboarding training. Make HIPAA training part of the onboarding checklist. Require completion before system access. Provide both online self‑paced materials and an interactive session for questions.
- Plan the refresher schedule. Set an annual calendar with short sessions and security reminders. Use quarterly micro‑ training on phishing and device security. Align refreshers with risk assessments or after major incidents.
- Develop documentation processes. Create a training log capturing:
- Staff name and role
- Training date and module version
- Topics covered
- Acknowledgement of completion
- Staff name and role
- This record should be retained for at least six years, in line with HIPAA documentation requirements.
- Use practical formats. Adult learners retain more information through varied formats. Use short videos, interactive quizzes, case studies, checklists and role‑playing exercises. Provide job aids such as cheat sheets for secure email, steps to encrypt mobile devices, and quick reference on breach reporting.
- Evaluate and update content. After each risk assessment, audit or incident, review the training program. Solicit feedback from participants. Update modules to reflect new regulations (e.g., the proposed 2025 Security Rule update requiring explicit training on malicious software and log‑in monitoring), technology changes or identified gaps.
- Communicate and reinforce culture. Encourage leadership to emphasise privacy and security in town halls and team meetings. Incorporate security metrics (e.g., phishing click rates, device encryption coverage) into performance dashboards. Celebrate teams that demonstrate best practices.
Sample templates & resources
Below are simple templates that can be adapted for your organisation. They are meant to jump‑start implementation rather than replace legal counsel.
Onboarding HIPAA Training Acknowledgement Form
Annual Refresher Training Log
Incident Reporting Form (Suspected PHI Breach)
- Reporter’s Name and Role: __________________________________
- Date and Time of Incident: __________________________________
- Description of Incident: Provide a concise description of what happened, including systems involved, data exposed, and immediate actions taken.
- Persons Involved or Witnesses: _______________________________
- Type of PHI Involved: (e.g., names, SSN, diagnoses, credit card info)
- Has the device or information been recovered?
- Notified Parties: Who has been informed (e.g., supervisor, privacy officer, IT)?
- Immediate containment measures taken: ________________________
Role‑Based Training Matrix (who needs what modules)
Daily/Weekly Security Hygiene Checklist
- Lock screens when stepping away from workstations.
- Use strong, unique passwords and avoid sharing credentials.
- Encrypt devices and portable media; store them securely when not in use.
- Check email senders and links before clicking; report suspicious messages.
- Verify recipient information before faxing or emailing PHI.
- Keep software and systems updated; apply patches promptly.
- Follow the minimum necessary rule when accessing or sharing PHI.
Free resources
- NIST SP 800‑66 Rev. 2: Guidance on implementing the Security Rule.
- CMS HIPAA Basics for Providers: Fact sheet outlining requirements for the Privacy, Security and Breach Notification Rules.
- HHS Enforcement Highlights: Statistics and common compliance issues.
- HHS OCR listservs and training materials: Sign up for updates on HIPAA guidance.
Common pitfalls and how to avoid them
- One‑time training with no refreshers. Compliance is dynamic; policies and threats evolve. Annual and event‑driven refreshers ensure staff stay current.
- Generic, one‑size‑fits‑all training. Role‑based training addresses specific responsibilities. IT staff need deeper technical instruction, while clinicians need guidance on disclosures and patient communication.
- Poor documentation. Lack of training records can jeopardise audits and breach investigations. Use logs and acknowledgement forms.
- Outdated materials. Regulations change. The proposed 2025 Security Rule update requires periodic security updates and stronger contingency planning. Monitor regulatory announcements and update materials accordingly.
- Ignoring business associates. Business associates are directly liable for certain HIPAA provisions and must sign BAAs. Covered entities must obtain assurances and provide relevant training. Failing to extend training expectations to vendors leaves gaps.
- Complacency after passing an audit. HIPAA compliance is continuous. Many organisations pass an audit but later experience breaches due to lax daily practices. Maintain ongoing monitoring, access reviews and vendor risk management.
Konfirmity’s human‑led, managed approach
At Konfirmity, we believe that you should start with security and arrive at compliance. Having supported over 6,000 audits across SOC 2, ISO 27001, GDPR and HIPAA, we know that robust training is just one control among many. Our human managed service builds and operates your security program end‑to‑end: mapping controls, collecting evidence, and maintaining readiness throughout the year. We don’t simply advise; we execute, taking the burden of continuous monitoring, access reviews, vulnerability remediation and vendor oversight off your internal teams.
For example, typical SOC 2 Type II readiness takes 9–12 months when self‑managed and consumes 550–600 internal hours. With Konfirmity, our clients are audit‑ready in 4–5 months with roughly 75 hours of internal effort. By implementing controls directly inside your stack—such as least‑privilege access reviews, CVSS‑based vulnerability triage and automated risk reminders—we reduce findings and accelerate enterprise procurement cycles.
In the context of HIPAA Training Requirements, our experts design a tailored program, deliver live and recorded sessions, manage LMS tracking, conduct periodic phishing drills and update content as regulations change. We also map HIPAA controls to SOC 2 and ISO 27001 requirements, allowing cross‑framework reuse of evidence. This integrated approach protects patient data while speeding due diligence.
Conclusion
HIPAA training is not a one‑time checkbox; it’s a continuous process of educating and reminding everyone who touches PHI or ePHI about their responsibilities. By following the legal standards under the Privacy and Security Rules—training all workforce members, implementing a security awareness and training program and preparing for evolving threats—healthcare organisations can reduce breach risk, avoid costly penalties and maintain patient trust. Use the templates and step‑by‑step guide above to build a program that stands up under audit. And remember: strong security practices produce compliance as a by‑product; superficial training leaves you vulnerable.
FAQs
1) What are the HIPAA training requirements?
Under the Privacy Rule, covered entities must train all workforce members—including employees, volunteers, trainees and contractors—on the policies and procedures relevant to their role. The Security Rule requires a security awareness and training program for all workforce members, addressing periodic security updates, malware protection, log‑in monitoring and password management. Training must be documented and updated as policies or technologies change.
2) How often is HIPAA training mandatory?
HIPAA does not prescribe an exact frequency. However, industry practice and NIST guidance suggest providing refresher training at least annually and whenever there are material changes to policies, systems or roles. Onboarding and role‑change training must occur before accessing PHI. Periodic security reminders and phishing simulations are recommended to keep awareness high.
3) What are the core HIPAA requirements?
Organisations must implement the Privacy, Security and Breach Notification Rules. This includes adopting privacy procedures, providing notice of privacy practices, granting patients access to their records, implementing administrative, technical and physical safeguards for ePHI, conducting risk analyses, entering into business associate agreements, providing workforce training, and establishing breach detection and response mechanisms.
4) Is HIPAA certification mandatory?
No. HIPAA does not require formal certification for individuals or organisations. Certifications offered by training providers may demonstrate effort but do not confer legal immunity. Compliance is achieved through implementing required safeguards, performing risk assessments and training the workforce. OCR evaluations focus on whether your practices meet regulatory standards, not whether you hold a certificate.





.svg)






.svg)
.svg)