Most enterprise buyers now request assurance artefacts before procurement, and the healthcare sector faces the same scrutiny. 2026 is set to be a watershed year for health‑care privacy and security. The U.S. Department of Health and Human Services Office for Civil Rights (OCR) issued a Notice of Proposed Rulemaking (NPRM) in January 2025 that would overhaul the HIPAA Security Rule and tighten requirements for protecting electronic protected health information (ePHI). OCR still lists finalisation of this rule on its regulatory agenda for May 2026.
At the same time, a 2024 final rule on reproductive‑health privacy was partially vacated by a federal court in June 2025, leaving only certain notice requirements that must be implemented by February 16 2026. These developments raise the question “HIPAA What Changed In 2026?” — the phrase that anchors this article and will be revisited throughout.
HIPAA’s evolution
HIPAA’s original purpose was to ensure portability of health coverage and to establish national standards for protecting individually identifiable health information. The Privacy Rule and Security Rule, released in the early 2000s, defined administrative, physical and technical safeguards for covered entities and their business associates. The 2009 Health Information Technology for Economic and Clinical Health (HITECH) Act introduced breach‑notification requirements and expanded direct liability to business associates. The 2013 Omnibus Rule unified four interim rules and marked the last major overhaul: it made business associates directly liable for technical, administrative and physical safeguards, strengthened breach‑notification provisions (presumption of breach unless low probability of compromise) and established a tiered civil penalty structure.
Since 2013 there have been few substantive updates. The increasing use of electronic health records (EHRs), cloud services and telehealth platforms has exposed large attack surfaces. High‑profile ransomware events, including the 2024 Change Healthcare attack that cost more than $2 billion, underline how legacy HIPAA security provisions are insufficient. OCR’s 2024–2025 work therefore seeks to modernise HIPAA security for today’s threat landscape.
The 2025–2026 proposals: key changes

1) Removal of “addressable” implementation specifications
The existing Security Rule allows organisations to treat many safeguards as “addressable,” meaning they can implement alternatives if they document justification. The NPRM proposes to remove the distinction and make nearly all implementation specifications required. Organisations will no longer be able to defer controls such as audit logging or access termination.
2) Comprehensive documentation and asset inventory
Under the proposed rule, regulated entities must document all policies, procedures and analyses related to the Security Rule. They must also develop a technology asset inventory and network map illustrating the movement of ePHI, updated at least annually or whenever systems change. This inventory is not a trivial inventory of laptops; it requires mapping data flows across on‑premises and cloud environments — a practice familiar to SOC 2 and ISO 27001 audits.
3) Rigorous risk analysis and incident response
Risk analysis must explicitly review the asset inventory and network map, identify threats and vulnerabilities, and assess risk levels. Organisations must create written incident response and disaster‑recovery plans. These plans must enable restoration of critical systems within 72 hours and include documented procedures for reporting and responding to security incidents. Business associates must notify covered entities of contingency‑plan activation within 24 hours, accelerating the breach‑notification timeline.
4) Mandatory technical safeguards
The NPRM would make several technical controls obligatory:
- Encryption at rest and in transit: ePHI must be encrypted both when stored and when transmitted.
- Multi‑factor authentication (MFA): all users must authenticate using at least two factors. NIST explains that MFA “requires a user to verify their identity by providing more than just a username and password” and should combine something the user knows, something they have, and something they are.
- Vulnerability scanning and penetration testing: entities must perform vulnerability scanning at least every six months and penetration testing annually.
- Network segmentation, anti‑malware protection and standardised configurations: systems must be hardened, ports disabled according to risk analysis, and anti‑malware deployed.
- Access control rules: access must be terminated within one hour of employee separation, and role‑based controls must be defined.
6) Contingency plans and audits
Written contingency plans must restore critical systems within 72 hours. Regulated entities must conduct a compliance audit at least annually to verify adherence. Business associates must provide written verification annually that they have deployed required safeguards.
7) Stricter business‑associate agreements (BAAs)
The NPRM mandates BAAs to include explicit security obligations, including MFA, encryption, and incident‑notification timelines. Entities must verify their business associates’ technical controls annually. Vendors will need to provide evidence, not just attestations, similar to the SOC 2 “system description” and ISO 27001 “statement of applicability.”
Privacy Rule modifications and reproductive‑health data
A separate final rule issued in April 2024 aimed to strengthen privacy protections for reproductive‑health services. It prohibited covered entities and business associates from using or disclosing PHI to investigate or impose liability on individuals seeking, providing or facilitating reproductive health care. However, on June 18 2025 the U.S. District Court for the Northern District of Texas vacated most of this rule. OCR notes that the court’s order invalidated specific provisions (164.520(b)(1)(ii)(F), (G) and (H)) of the revised Notice of Privacy Practices (NPP), but other NPP modifications remain valid and must be implemented by February 16 2026. Organisations must therefore update their NPPs to reflect permissible uses of PHI for reproductive‑health privacy while excluding vacated language.
Drivers behind the overhaul
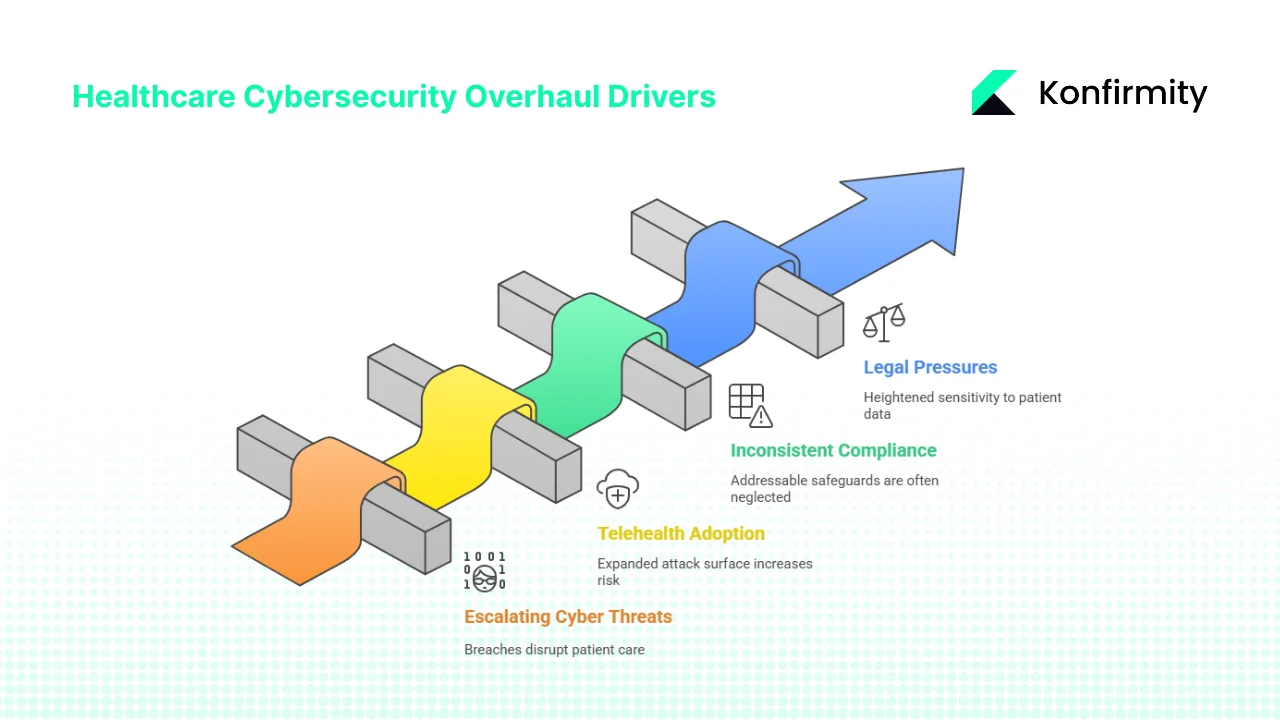
1) Escalating cyber threats
Healthcare is consistently the most expensive industry for data breaches. IBM and the Ponemon Institute reported that the average cost of a healthcare breach in 2024 was $9.8 million, compared with $6.1 million in finance. Attacks often involve ransomware that shuts off access to EHR systems and disrupts patient care. The median breach lifecycle lasts over 200 days, giving attackers extended access. These figures, and the 2024 Change Healthcare breach, have convinced regulators that flexible, addressable controls no longer suffice.
2) Telehealth and cloud adoption
Rapid adoption of telehealth and cloud‑based EHR platforms has expanded the attack surface. Each remote connection or third‑party app becomes a potential entry point. The NPRM’s emphasis on asset inventories, MFA and network segmentation directly addresses these modern realities. NIST guidance on MFA stresses that passwords alone are insufficient and that two or more factors are essential.
3) Inconsistent compliance and business‑associate risk
OCR observed inconsistent Security Rule compliance across the industry. Many entities treated “addressable” safeguards as optional and neglected them entirely. The proposed rule aims to standardise baseline controls, reduce variability and close gaps in vendor oversight. Law firm analyses note that commenters have raised cost concerns, particularly for small practices, yet the need for stronger security is indisputable.
4) Legal and societal pressures
Since the U.S. Supreme Court’s Dobbs decision, there has been heightened sensitivity to reproductive‑ and behavioral‑health data. Patients expect robust privacy protections. OCR’s 2024 final rule sought to address this, and even though parts were vacated, the remaining NPP updates signal a continued emphasis on sensitive data. Meanwhile, the tiered civil penalty structure under HIPAA remains: fines range from $100 to $50,000 per violation, with annual caps from $25,000 to $1.5 million depending on culpability. Stronger safeguards will make penalties more enforceable.
What’s still unclear
The 2025 Security Rule changes are still proposals. OCR’s regulatory agenda lists May 2026 for finalisation, but industry pushback may influence the timeline and content. Some smaller practices have argued that mandatory encryption and annual penetration testing are burdensome. The final rule may include phased deadlines or alternative options. If finalised as proposed, regulated entities could have as little as 240 days to comply. At the same time, ongoing litigation over reproductive‑health privacy illustrates that courts can undo regulations mid‑stream. Organisations must monitor legal developments and plan for multiple scenarios.
Practical steps: preparing your program
The proposed changes are extensive, but healthcare organisations can begin today. Based on Konfirmity’s experience supporting over 6,000 audits across SOC 2, ISO 27001 and HIPAA, and drawing on our 25+ years of combined expertise, the following roadmap can help you be ready if the final rule resembles the NPRM. Our approach is human‑led, managed security and compliance: we build controls inside your environment and keep them operating year‑round.
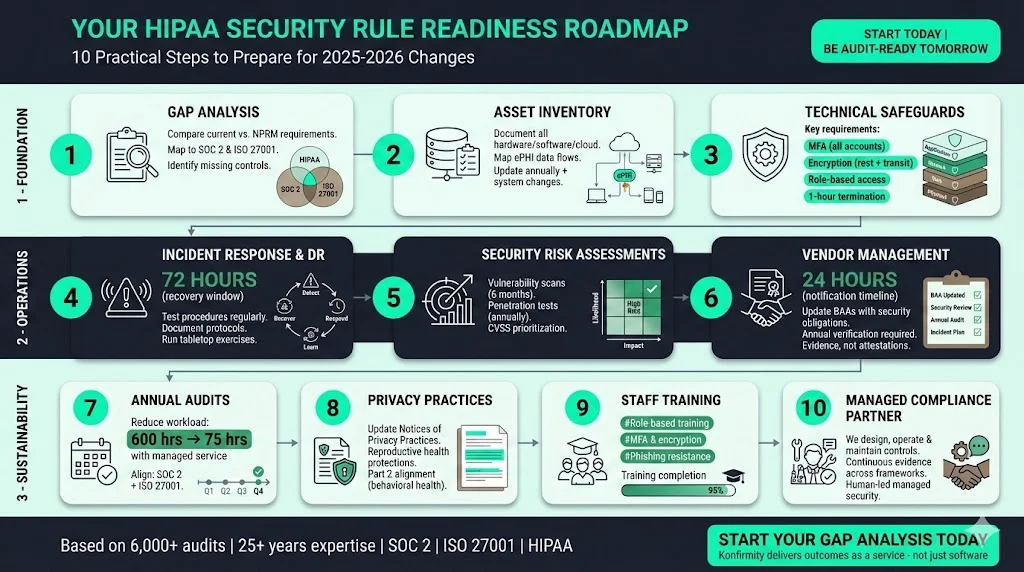
- Perform a gap analysis. Compare current policies, technical controls and vendor agreements against the NPRM requirements. Identify missing controls, undocumented processes and unclear roles. Map requirements to existing frameworks like SOC 2 (security, availability, confidentiality, processing integrity and privacy criteria) and ISO 27001:2022 (93 controls across organisational, people, physical and technological clauses) to see where evidence can be reused.
- Build and maintain an asset inventory. Document all hardware, software, cloud services, data repositories and data flows that handle ePHI. Update the inventory annually and whenever systems change. Link each asset to responsible owners and classify data sensitivity. This practice is also fundamental to ISO 27001 Annex A controls and NIST risk assessments.
- Implement strong technical safeguards. Enable MFA for all accounts — especially those with ePHI access — using at least two different factors. Encrypt data at rest and in transit. Harden systems by standardising configurations, deploying anti‑malware and disabling unnecessary ports. Use role‑based access and ensure that access revocation occurs within one hour of termination.
- Develop incident response and disaster‑recovery plans. Draft and test procedures for detecting, reporting and responding to security incidents. Identify critical systems and design recovery strategies to restore them within 72 hours. Document communication protocols and escalation paths. Run tabletop exercises and adjust plans based on lessons learned.
- Conduct formal security risk assessments (SRAs). Perform risk analyses that consider threats, vulnerabilities and likelihood; document results and mitigation plans. Schedule vulnerability scans every six months and penetration tests annually. Use CVSS scores to prioritise remediation and track metrics like mean time to remediate (MTTR).
- Update vendor agreements and oversight. Review and renegotiate BAAs to include explicit security obligations: MFA, encryption, incident‑notification timelines (24 hours) and annual verification of safeguards. Create a vendor‑risk management workflow that categorises vendors, collects documentation and monitors compliance.
- Prepare for annual audits. Plan internal or external audits to validate compliance with the Security Rule and track evidence. Align SOC 2 and ISO 27001 audits to reduce duplication; for example, the security TSC’s control environment and monitoring activities map to ISO 27001 clause 6 and Annex A. Konfirmity’s end‑to‑end managed service reduces internal workload from ~550–600 hours self‑managed to ~75 hours per year by automating evidence collection and maintaining controls.
- Revise privacy practices and notices. Update Notices of Privacy Practices to reflect valid reproductive‑health protections and remove vacated language. Ensure policies address behavioral health and substance‑use data (Part 2 alignment). Educate patients on their rights and restrictions.
- Train staff and build awareness. Provide role‑based training on new technical safeguards, incident‑response procedures and data‑handling protocols. Ensure employees understand MFA, encryption and phishing‑resistant practices. Use training logs as evidence for audits.
- Engage a managed compliance partner. Working with a provider that delivers outcomes as a service can accelerate readiness. Unlike software platforms that require teams to implement controls themselves, Konfirmity embeds experts who don’t just advise—we execute: we design controls, operate them daily and supply continuous evidence across frameworks.
CTA: Book a demo
Implications for key areas
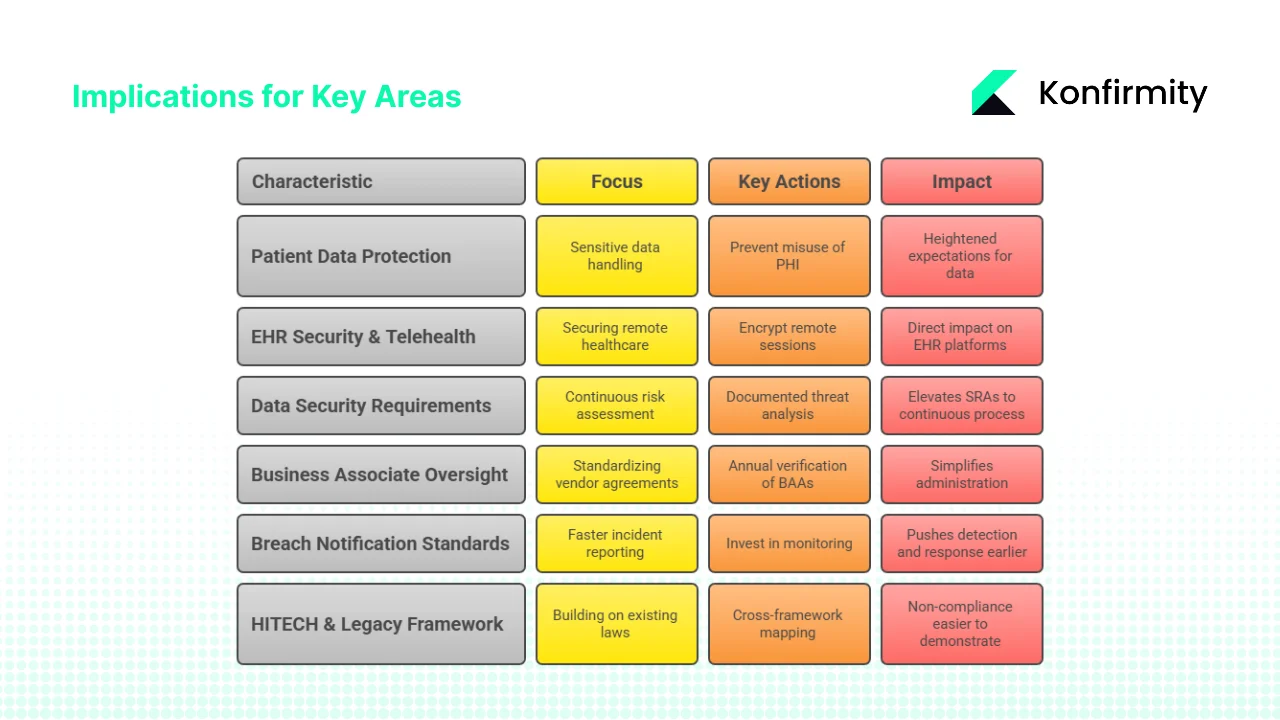
1) Patient data protection and privacy
The reproductive‑health rule underscores heightened expectations for sensitive data. While parts of the rule were vacated, remaining NPP updates and OCR guidance aim to prevent misuse of PHI for investigations. The security overhaul complements these aims by mandating encryption, MFA and documented risk analyses, raising the bar for confidentiality. Behavioral‑health and substance‑use data will also require careful handling and explicit consent under Part 2 integration.
2) EHR security and telehealth
Mandatory encryption and MFA directly affect EHR platforms, telehealth portals and cloud storage. Providers must ensure that remote sessions are encrypted end‑to‑end and that users authenticate through multiple factors. Network segmentation and asset inventories will help isolate telehealth systems from other networks, reducing the blast radius of breaches. Telehealth providers should prepare for more frequent vulnerability scans and penetration tests.
3) Data‑security requirements and SRAs
The NPRM elevates SRAs from periodic paperwork to a continuous, documented process with explicit requirements for threat and vulnerability analysis. Continuous monitoring aligns with SOC 2 Type II audits, which require evidence over an observation period. Organisations that already follow NIST SP 800‑53, CISA’s Cybersecurity Performance Goals or ISO 27001 Annex A controls will find synergies in asset inventories, access reviews and incident response.
4) Business‑associate oversight and administrative simplification
Standardising BAAs and requiring annual verification simplifies administration by creating a uniform baseline for vendors. However, the workload of renegotiating and monitoring large vendor ecosystems will be substantial. Managed services can streamline this by integrating vendor questionnaires, evidence collection and tracking.
5) Breach‑notification standards
The proposed rule shortens timelines: business associates must notify covered entities within 24 hours of activating contingency plans. This pushes detection and response earlier in the breach lifecycle. For reference, IBM’s report found that organisations using AI and automation reduced breach costs by $1.76 million. Healthcare entities should invest in monitoring and automation to meet these timelines.
6) HITECH and legacy framework implications
The HITECH Act’s breach‑notification and business‑associate provisions remain relevant; the proposed rule builds on them with modern requirements. The Omnibus Rule’s penalty tiers still apply. The NPRM does not change enforcement structure but will make non‑compliance easier to demonstrate. Cross‑framework mapping can yield efficiencies: encryption, access control and logging satisfy requirements across HIPAA, SOC 2 security and confidentiality criteria, ISO 27001 controls and even GDPR articles on data protection.
Challenges and risks for healthcare companies
Implementing the proposed controls will not be easy. Smaller practices may struggle with the cost of encrypting every device, deploying MFA and paying for annual penetration tests. Law firm analyses note that commentators have raised concerns about increased documentation and verification burdens. Tight timelines — potentially 240 days from final publication — leave little room for gradual adoption. Vendor readiness adds another layer: business associates must upgrade their systems and processes, and renegotiating hundreds of BAAs will consume resources. Mapping data flows, classifying ePHI and coordinating across IT, compliance and clinical teams requires cross‑functional collaboration. Finally, legal uncertainty remains: court challenges could delay or alter rules, requiring organisations to pivot quickly.
Conclusion
The HIPAA What Changed In 2026 question reflects a turning point. OCR’s proposed overhaul would transform the Security Rule from a flexible, risk‑based standard into a prescriptive, control‑heavy framework. Key changes include removing “addressable” specifications, mandating asset inventories, MFA, encryption, vulnerability scanning and annual audits. A separate privacy rule aimed at protecting reproductive‑health data was largely vacated by a court, leaving only certain notice requirements effective February 16 2026. While the final form of these changes remains uncertain until May 2026, the direction is clear: regulators expect healthcare organisations to demonstrate modern security practices and documented compliance.
Preparation is essential. Conduct gap analyses, build detailed asset inventories, implement MFA and encryption, formalise incident response and disaster recovery, perform SRAs and vulnerability tests, renegotiate BAAs, and train staff. Mapping requirements across HIPAA, SOC 2 and ISO 27001 can reduce duplicate work and accelerate evidence collection. Engaging a human‑led, managed security and compliance partner like Konfirmity can shorten readiness from 9–12 months to 4–5 months and reduce internal effort to around 75 hours per year.
Security that looks good on paper but fails under real attack is a liability. Build a program that operates daily, maintain continuous evidence, and let compliance follow.
FAQs
1) What are the changes in HIPAA in 2026?
The main changes revolve around the proposed overhaul of the Security Rule. The NPRM removes the “addressable vs. required” distinction, making almost all safeguards mandatory. It requires detailed technology asset inventories and risk analyses, encryption of ePHI at rest and in transit, mandatory multi‑factor authentication, vulnerability scanning every six months and penetration testing annually, 72‑hour disaster recovery and 24‑hour incident‑notification timelines, annual compliance audits and stricter BAAs. In privacy, portions of the 2024 reproductive‑health final rule were vacated, but remaining Notice of Privacy Practices changes must be implemented by February 16 2026.
2) What are the new HIPAA changes for 2025?
In January 2025 OCR published the NPRM proposing the Security Rule overhaul. It introduced prescriptive requirements for MFA, encryption, asset inventories, risk analyses and incident response. Comments were due in March 2025, and the final rule is expected in May 2026. Separately, in April 2024 HHS issued a final rule to protect reproductive‑health data. That rule prohibited using PHI to investigate lawful reproductive services and required revisions to NPPs; however, a court vacated most provisions in June 2025, leaving only certain NPP modifications in effect.
3) What is the fine for HIPAA in 2025?
HIPAA’s penalty framework has four civil tiers. For unknowing violations, fines range from $100 to $50,000 per violation with an annual cap of $25,000. For violations due to reasonable cause, fines range from $1,000 to $50,000 with a $100,000 annual cap. If the violation results from willful neglect but is corrected, fines range from $10,000 to $50,000 with a $250,000 cap. For willful neglect not corrected, each violation can incur a $50,000 fine with an annual maximum of $1.5 million. These tiers remain unchanged by the proposed rule, but stricter safeguards will make violations more apparent.
4) What was the last major update to HIPAA?
The last major overhaul was the 2013 Omnibus Rule, which implemented HITECH’s provisions. It made business associates directly liable for complying with technical, administrative and physical safeguards, finalised breach‑notification rules and expanded individuals’ rights to their PHI. Minor updates have occurred since then, but the 2025 NPRM represents the most significant shift in over a decade.





.svg)






.svg)
.svg)