Most enterprise buyers now demand evidence of operational security before they will sign a contract. Templates, slide decks and “compliance certificates” are no longer enough. The global cost of a data breach reached US$4.44 million in 2025 according to the Ponemon Institute and IBM’s annual survey. Healthcare breaches remain the most expensive at US$7.42 million. Deals stall when vendors cannot provide assurance that they operate effective information security management systems (ISMS) aligned with recognised standards. Many buyers list ISO 27001 certification in their questionnaires because it offers a comprehensive, internationally recognised framework for managing risk.
This article is written for CTOs, CISOs and compliance officers at companies that sell to enterprises and handle sensitive data such as protected health information (PHI) or financial records. It explains what the ISO 27001 Audit Timeline looks like in practice, why it matters for enterprise sales cycles, and how a human‑led, managed security programme can reduce effort, shorten timelines and improve deal velocity. The guide draws on authoritative sources—including AuditBoard, ISMS.online, Secureframe and ISOQAR—plus lessons from 6 000+ audits conducted by Konfirmity’s delivery teams over the past decade. By the end you will understand the phases of an ISO 27001 audit, the typical durations for each phase, key milestones, and best practices for staying on schedule and achieving certification with fewer findings.
What ISO 27001 Is and Why Auditing Matters
ISO 27001 is an international standard that specifies requirements for establishing, implementing, maintaining and continually improving an ISMS. Organisations pursue certification to demonstrate that they have implemented risk‑based controls, documented policies and procedures, and can produce evidence that those controls operate effectively.
A certified ISMS signals to enterprise buyers that a vendor takes security seriously. For regulators, ISO 27001 demonstrates compliance with statutes such as the Health Insurance Portability and Accountability Act (HIPAA) and the General Data Protection Regulation (GDPR) when combined with sector‑specific requirements. For the vendor, certification leads to faster procurement, improved trust, and less friction when negotiating Data Processing Agreements (DPAs), Business Associate Agreements (BAAs) and other security addenda.
But certification is not just a piece of paper. It requires a thorough external audit by an accredited certification body. Auditors examine documentation, interview personnel, sample evidence and observe operational practices. The process involves several phases—pre‑audit preparation, Stage 1 document review, Stage 2 implementation assessment, remediation and corrective actions, and ongoing surveillance audits. Understanding the ISO 27001 Audit Timeline helps companies plan resources, set realistic milestones, and win enterprise deals by being able to provide accurate certification dates.

What Readers Will Learn
- A clear breakdown of the ISO 27001 Audit Timeline from initial gap analysis through certification and surveillance audits.
- Factors that influence the duration of each phase, including company size, ISMS maturity and scope.
- Examples of typical schedules for small technology vendors versus large enterprise suppliers.
- Best practices for staying on schedule—drawing on more than two decades of hands-on experience delivering compliance programmes.
- A comparison between human‑led, managed security services and self‑managed programmes.
- Answers to frequently asked questions, including the difference between internal and external audits and the timing between Stage 1 and Stage 2.
Why Understanding the ISO 27001 Audit Timeline Helps Win Enterprise Deals
Enterprise procurement teams are risk‑averse. They must ensure that vendors handling PHI, financial data or other regulated information have implemented robust controls. Without certification, deals can be delayed or cancelled. Even when a vendor claims to be “ISO‑ready”, procurement teams ask for Stage 1 and Stage 2 reports, internal audit evidence and corrective action plans. A clear timeline allows vendors to:
- Align sales and compliance teams. Sales can communicate realistic certification dates in proposals and respond confidently to questions in security questionnaires.
- Resource planning. Knowing that Stage 2 requires at least three months of operating evidence helps allocate staff time for documentation, internal audits and evidence collection.
- Avoid surprises. Delays often occur when teams underestimate the gap assessment or ignore the required time between Stage 1 and Stage 2. A timeline with milestones prevents last‑minute scrambles.
- Leverage certification as a differentiator. A vendor who completes an ISO audit ahead of competitors can accelerate contracting and close deals faster.
What an ISO 27001 Audit Involves
ISO 27001 Compliance and Audit Basics
ISO 27001:2022 requires organisations to implement an ISMS, conduct risk assessments, define a Statement of Applicability (SoA), and establish controls covering people, processes and technology. Compliance involves two types of audits:
- Internal audits (1st party) – The organisation itself checks whether the ISMS conforms to ISO 27001 and whether controls are effective. ISO 27001 Clause 9.2 requires internal audits at planned intervals, with documented programs and objective auditors. These audits identify gaps before the external certification audit.
- External audits (3rd party) – Performed by an accredited certification body. Stage 1 focuses on documentation review; Stage 2 assesses implementation and evidence. After certification, surveillance audits occur annually and recertification audits occur every three years.
Second‑party audits (2nd party) refer to audits by customers or partners, typically during due diligence. They may look similar to internal or external audits but are not part of the certification process.
Key Goals of an ISO 27001 Audit
The audit ensures that the ISMS:
- Conforms to ISO 27001 requirements – For example, the organisation must define the ISMS scope, perform risk assessments, and document policies and procedures.
- Is effectively implemented – Auditors verify that controls operate as described and that the organisation can produce evidence (logs, change records, access reviews, vendor risk assessments) covering the required observation period.
- Supports continual improvement – Findings from audits feed into corrective actions and management reviews. Surveillance audits confirm that improvements are sustained across the certification cycle.
- Protects information assets – Ultimately, an effective ISMS reduces the likelihood and impact of data breaches, protecting clients, patients and business partners.
High‑Level ISO 27001 Audit Timeline
ISO 27001 audits are not one‑day events. They span several months and require sustained effort from cross‑functional teams. The ISO 27001 Audit Timeline typically ranges from six to twelve or more months, depending on a company’s size and ISMS maturity. The phases include:
- Pre‑audit preparation (gap assessment, ISMS documentation, internal audit)
- Stage 1 audit (documentation review)
- Stage 2 audit (implementation and on‑site assessment)
- Report submission, certification issuance and corrective actions
- Surveillance audits (annual)
- Recertification audit (every three years)
The figure below illustrates the general timeline for a small technology vendor versus a large enterprise supplier. The durations are typical ranges drawn from multiple sources and from Konfirmity’s experience across 6 000+ audits.
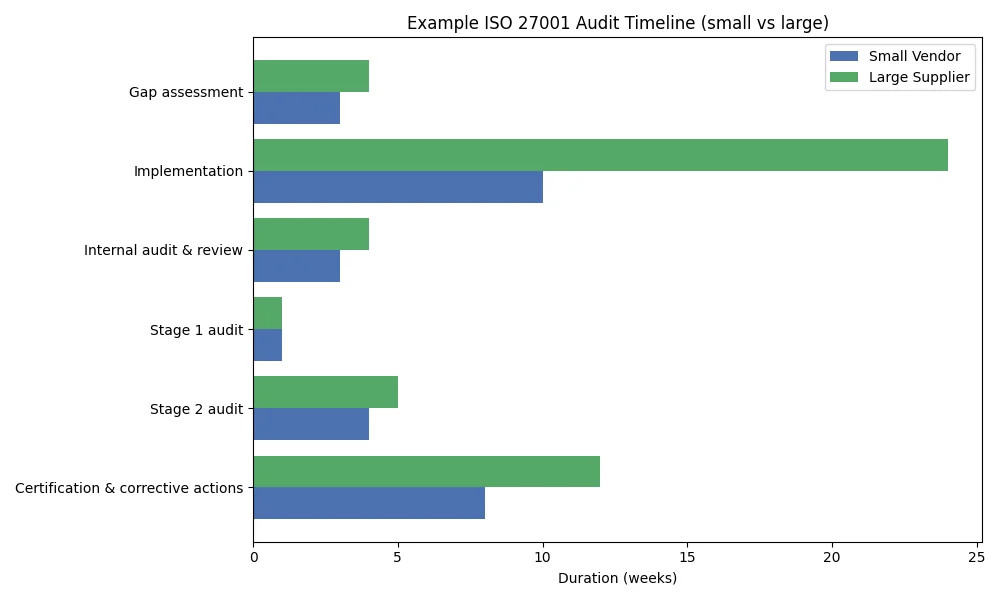
Figure 1: Sample ISO 27001 audit timeline for a small tech vendor (short bars) versus a large enterprise supplier (long bars). Durations are illustrative; actual timelines vary depending on scope and maturity.
How Company Size and ISMS Maturity Affect the Schedule
- Small tech vendors often have fewer business processes and a narrower ISMS scope. With dedicated support, they can complete the gap assessment and documentation in 2–4 months, followed by Stage 1 and Stage 2 audits within another 2–3 months, leading to a 6–8 month certification timeline.
- Large enterprise suppliers usually operate complex systems, multiple data centres, and distributed teams. Defining the scope, implementing controls and gathering evidence across departments may take 6–12 months or longer. External audit phases can extend when auditors must visit multiple sites or sample more controls.
- ISMS maturity matters: organisations with existing controls (e.g., SOC 2 Type II or HIPAA programmes) can reuse evidence and shorten preparation. Others starting from scratch may spend months writing policies and training staff.
Phase 1: Pre‑Audit Preparation
What Pre‑Audit Preparation Covers
Gap analysis and risk assessment. A gap assessment compares the current security posture against ISO 27001 controls and Annex A requirements. It identifies missing policies, inadequate technical controls, and gaps in evidence collection. Risk assessments determine which threats and vulnerabilities are relevant, evaluate impact and likelihood, and define risk treatment plans.
ISMS scope definition and documentation. The organisation must document the boundaries of the ISMS, specifying systems, locations and processes that fall under the scope. It must produce policies such as information security, access control, asset management, incident response and business continuity. A Statement of Applicability lists controls and their implementation status.
Internal audit, management review and remediation. Internal auditors or independent parties evaluate the ISMS against ISO 27001 requirements. Management reviews ensure leadership involvement, assess audit results, and allocate resources for remediation. During remediation, teams implement missing controls, improve processes, and ensure evidence collection mechanisms (e.g., logging, access reviews) are operating.
Key Actions During Pre‑Audit Preparation
- Audit schedule planning. Determine desired certification date and work backwards. Identify holiday periods and busy times (e.g., product releases) that could constrain availability.
- Build policies and procedures. Use templates aligned with ISO 27001:2022 but adapt them to the organisation’s processes. Avoid copying generic policies; auditors test whether they are practical.
- Training and readiness checklists. Educate employees on roles (e.g., incident response procedures, change management workflows). Conduct tabletop exercises to ensure teams know what evidence to produce during the audit.
- Evidence collection. Automate as much evidence collection as possible. Tools that capture change management tickets, vulnerability scans, vendor assessments and access review logs reduce manual effort.
Example: Week‑by‑Week Schedule for a Mid‑Size Company
Below is a hypothetical eight‑week pre‑audit preparation schedule for a mid‑size technology vendor with 150 employees. The timing assumes some existing security practices.
A larger organisation may add several weeks to each activity, particularly documentation and technical implementation. External support from a managed security service can compress these timelines by providing ready‑made policies and pre‑integrated evidence pipelines.
Phase 2: Stage 1 Audit – Documentation Review
What Happens During Stage 1
Stage 1 is an external audit focusing on documentation. The auditor reviews the ISMS scope, policies, risk assessment, Statement of Applicability and documented procedures to confirm that the organisation is ready for Stage 2. This phase typically takes a few days to a few weeks depending on the complexity of documentation.
Deliverables and Milestones
- Audit plan. The certification body provides a plan outlining the scope, the audit agenda and the expected schedule for Stage 1 and Stage 2.
- Documented evidence review. The auditor examines the risk assessment, SoA, procedures, control mapping and internal audit reports. Missing or inadequate documents are flagged as findings.
- Readiness report. At the end of Stage 1, the auditor issues a report identifying nonconformities and recommendations for remediation. The organisation must address these before Stage 2.
Typical Issues That Delay Stage 1
- Incomplete documentation or policies that do not reflect actual practices.
- Lack of a documented risk assessment or SoA.
- Ambiguities in ISMS scope boundaries.
- Incorrect references to outdated versions of ISO 27001.
Konfirmity has found that up to 40 % of organisations entering Stage 1 without a managed security programme must reschedule Stage 2 due to incomplete evidence. A human‑led programme ensures documents are audit‑ready and reduces back‑and‑forth with auditors.
Phase 3: Stage 2 Audit – Implementation & On‑Site Assessment
How Stage 2 Differs from Stage 1
Stage 2 verifies that the ISMS operates effectively. Auditors visit the organisation—physically or remotely—to sample controls, observe operations and interview personnel. While Stage 1 focuses on whether the organisation says the right things, Stage 2 ensures they do the right things.
Auditor Visits and Verification Activities
- Evidence gathering. Auditors review log files, change tickets, access reviews, vulnerability scans, incident reports and training records. They cross‑check evidence with documented policies.
- Interviews. They speak with engineers, administrators and management to understand how policies translate into daily operations.
- Site tours. For organisations with data centres or offices, auditors verify physical security controls such as access badges, CCTV, and environmental controls.
Timeline Quantification
Stage 2 typically lasts 4–6 weeks. Some certification bodies require a gap of 4–6 weeks between Stage 1 and Stage 2 to allow for remediation and evidence collection. ISOQAR states that Stage 2 should be scheduled no more than six months after Stage 1 and that the ISMS must have operated for at least three months before Stage 2.
Typical Day‑by‑Day Activities During Stage 2
Checklist of What Auditors Will Test
- Risk assessment process and risk treatment plans.
- Control implementation such as access control (least privilege), encryption, patch management and vulnerability remediation.
- Operational evidence: logs from SIEM platforms, change management systems, identity providers, and vendor risk tools.
- Training records and awareness programs: onboarding checklists, annual security awareness records, phishing simulations.
- Incident management and response: ticketing system logs, timeline of incidents, root cause analysis.
- Physical security: keycard access logs, CCTV footage retention policies, environmental controls.
- Business continuity and disaster recovery: backup schedules, restoration tests, failover drills.
What Happens After Stage 2
1) Report Submission and Certification
After Stage 2, the auditor compiles evidence, writes the report and submits it to the certification body’s review committee. According to ISOQAR, this process typically takes up to three months; the certificate is issued only after all nonconformities are addressed. If the organisation passes, they receive an ISO 27001 certificate valid for three years.
2) Remediation Period and Corrective Actions
If auditors identify nonconformities, the organisation must develop a corrective action plan specifying how and when the issues will be resolved. Minor nonconformities might be addressed with updated policies or training. Major nonconformities—such as missing logs or ineffective access control—can delay certification. Certification bodies often allow three months for remediation. Once corrective actions are implemented, evidence is submitted to the auditor, who verifies the fixes and issues the certificate.
3) Certification Maintenance and Follow‑Up Audits
ISO 27001 certification is not a one‑time event. The standard requires ongoing surveillance audits and recertification within a three‑year cycle.
- Surveillance audits occur annually (or more frequently for high‑risk scopes). Auditors review a subset of controls to ensure the ISMS continues to operate as designed. They check that management reviews and internal audits occur as planned.
- Internal audit schedule: Organisations must perform internal audits at planned intervals (e.g., quarterly or bi‑annually) across the three‑year cycle. Evidence from internal audits and corrective actions must be available for surveillance.
- Recertification audit: At the end of three years, a full audit is performed (similar to Stage 2) to renew the certificate. Organisations must plan for this and avoid leaving remediation to the last minute.
Example Audit Schedules
Example #1: Small Tech Vendor
A start‑up providing cloud‑based analytics to healthcare providers decides to pursue ISO 27001 certification to satisfy HIPAA Business Associate Agreements and secure enterprise deals. They have 40 employees and some existing security practices from a SOC 2 programme. A typical eight‑month ISO 27001 Audit Timeline for such a company could look like this:
- Months 1–2: Gap assessment; risk assessment; policy drafting; implement missing controls such as encryption at rest and vendor risk assessments. Estimate about 150 hours of internal time plus 80 hours of external assistance.
- Month 3: Internal audit and management review; remediation of minor findings; schedule Stage 1.
- Month 4: Stage 1 audit (documentation review) lasting 3 days; receive readiness report; remediate minor documentation issues.
- Month 5: Evidence collection, run operations under the new ISMS for at least three months.
- Month 6: Stage 2 audit (4 days); minor corrective actions; auditor submits report.
- Months 7–8: Certification issued after report review and closure of findings.
With human‑led assistance, the start‑up invests roughly 75 hours per year maintaining compliance rather than 550–600 hours in a self‑managed approach. The reduction comes from automated evidence collection, pre‑built policy templates and dedicated compliance advisors.
Example #2: Large Enterprise Supplier
A multinational SaaS vendor with 1 500 employees aims to meet enterprise clients’ security addenda across three regions. Their ISMS scope includes multiple products, development pipelines, support operations and third‑party data centres. A typical 12–18 month timeline might look like this:
- Months 1–3: Comprehensive gap assessment across all business units; risk assessment with cross‑functional workshops; map existing controls to ISO 27001 Annex A and other frameworks (SOC 2, HIPAA).
- Months 3–6: Policy harmonisation and control implementation; integrate logging and evidence collection across cloud platforms; deploy single sign‑on and multi‑factor authentication for all services.
- Months 7–8: Internal audit across regional teams; management reviews; allocate budget for improvements (e.g., dedicated security engineers, vulnerability management tools).
- Month 9: Stage 1 audit; documentation review across global operations; remediate any issues.
- Months 10–12: Operating period under new ISMS; collect evidence from multiple sites; train staff in incident response, vendor risk workflows and DPIA processes.
- Months 13–15: Stage 2 audit spanning multiple sites, with remote and on‑site visits over 4–6 weeks; compile evidence samples; address nonconformities.
- Months 16–18: Certification issuance after closure of major findings; plan for first surveillance audit within 12 months.
Large organisations benefit from a dedicated compliance team and centralised tooling. Without external support, delays are common due to competing priorities, complex change management and vendor onboarding processes.
Sample Gantt Chart / Table
Below is an illustrative table showing key dates for a 12‑month ISO 27001 implementation at a large vendor.
Best Practices for Staying on Schedule
1) Efficient Documentation Review
- Centralise policies and evidence. Use a compliance management tool or a shared repository to store policies, risk assessments and audit evidence. Auditors appreciate organised documentation.
- Keep documents current. Policies should reference the latest ISO 27001:2022 clauses and your actual processes. Outdated or generic documents lead to findings and delays.
- Review cross‑framework mappings. If you have SOC 2 or HIPAA controls, map them to ISO 27001 Annex A. This reduces duplication and evidence collection effort.
2) Preparing Teams for Auditor Visits
- Conduct mock interviews. Simulate audit questions with engineers and administrators. Ensure they can describe how the change management process works and how access reviews are conducted.
- Assign subject‑matter experts. Identify individuals responsible for each control area (e.g., vulnerability management, vendor risk). Provide them with the audit schedule and ensure they are available during Stage 2.
- Ensure physical readiness. For site visits, verify that access badges function, visitor logs are complete and CCTV retention meets policy requirements.
3) Prioritising Compliance Before Deadlines
- Start early. Build controls and evidence collection mechanisms months before the desired certification date. ISOQAR requires three months of operating history before Stage 2.
- Plan remediation windows. Reserve at least six weeks between Stage 1 and Stage 2 to address documentation gaps.
- Avoid last‑minute change freezes. Auditors may want to see evidence of ongoing change management. A change freeze for the sole purpose of passing the audit can raise questions about normal operations.
4) Using Tools and Automation to Track Audit Readiness
- Automated evidence collection. Integrate ticketing systems (Jira, ServiceNow), code repositories (GitHub), cloud platforms and identity providers to automatically capture change logs, deployment records, access reviews, vendor assessments and training completions.
- Continuous monitoring. Implement vulnerability scanning, configuration management and log aggregation to produce real‑time evidence of control operation. Automation reduces detection and escalation costs by US$1.76 million on average.
- Status dashboards. Use dashboards to track progress against milestones, track open nonconformities, and ensure readiness for surveillance audits.
Summary Table of Phases, Activities and KPIs
Conclusion
Understanding the ISO 27001 Audit Timeline is critical for enterprise‑focused vendors. It is not enough to produce policies or “pass an audit”; you must operate a living ISMS that withstands scrutiny from auditors, customers and regulators. By planning each phase—gap assessment, documentation, internal audit, Stage 1, Stage 2 and ongoing surveillance—you reduce uncertainty, allocate resources effectively and avoid delays that jeopardise deals.
At Konfirmity, we believe in starting with security and arriving at compliance. We provide a human‑led, managed service that embeds controls into your stack and operates them daily. With more than 6 000 audits supported and 25+ years of combined expertise, we implement controls, collect evidence and manage audits so your team can focus on product and growth. Our clients achieve certification faster, with fewer findings and less internal effort. Compliance that looks good on paper but fails in practice is a liability. Build your programme once, operate it every day, and let compliance follow.
FAQ Section
1. What is the audit lifecycle of ISO 27001?
The ISO 27001 audit lifecycle starts with pre‑audit preparation, where organisations conduct a gap analysis, risk assessment and internal audit. They then undergo Stage 1 (documentation review) and Stage 2 (implementation audit). After certification, the organisation must undergo annual surveillance audits and a recertification audit every three years.
2. Does ISO 27001 require annual audits?
Yes. After certification, accredited bodies perform surveillance audits each year to verify that the ISMS continues to operate effectively. These audits review a subset of controls, management reviews and internal audit results. Failure to maintain surveillance can lead to suspension of the certificate.
3. What is the time gap between Stage 1 and Stage 2 audit?
The gap between Stage 1 and Stage 2 is typically 4–6 weeks to allow organisations to remediate documentation issues and collect additional evidence. Certification bodies generally require that Stage 2 occurs within six months of Stage 1 and that the ISMS has operated for at least three months before Stage 2.
4. What are 1st, 2nd and 3rd party audits?
- 1st party audits are internal audits performed by the organisation itself to assess its ISMS and identify gaps. They must be objective, impartial and documented.
- Customers or partners conduct 2nd party audits on your organisation to verify compliance with their security requirements, often during procurement due diligence.
- 3rd party audits are conducted by accredited certification bodies to certify that the ISMS meets ISO 27001 requirements. These include Stage 1 and Stage 2 audits, surveillance audits and recertification audits.





.svg)






.svg)
.svg)