Most buyers at large companies now require tangible evidence of operational security before they sign contracts. According to IBM’s 2025 Cost of a Data Breach report the global average cost of a breach dropped from $4.88 million in 2024 to $4.44 million in 2025, yet U.S. incidents still averaged $10.22 million. The 2026 edition paints a grimmer picture: human‑driven attacks pushed the global average up to $4.88 million, and under the European NIS2 directive executives can be personally liable with fines up to €10 million or 2 percent of global turnover. With these stakes, procurement teams insist on ISO 27001 certification as part of vendor due‑diligence. This ISO 27001 Auditor Selection Guide explains how the right auditor helps enterprise‑selling vendors demonstrate security maturity, meet client expectations, and avoid costly delays. Written from the perspective of Amit Gupta, co-founder of Konfirmity and practitioner of 6,000+ audits, it blends operational insight with current statistics and cited guidance.
Konfirmity operates as a human‑led, managed security and compliance service. We implement controls inside your stack, monitor evidence continuously, and support audits year‑round, reducing internal effort by roughly 75% compared with self‑managed programs. Our managed service handles ISO 27001, SOC 2, HIPAA and GDPR readiness across thousands of vendors. This guide draws on our experience delivering audit readiness for enterprise customers and regulated healthcare providers.
What Is ISO 27001 and the Role of an Auditor
ISO 27001 is a widely acknowledged standard for information security management systems, governed by the International Organization for Standardization and the International Electrotechnical Commission. The 2022 revision remains the most current and organizations must recertify against it by October 31 2025. The standard outlines requirements for establishing, implementing, maintaining and improving an ISMS. It promotes a risk‑based approach: organizations define the scope of their ISMS, conduct risk assessments, implement controls and continuously monitor their effectiveness. Annex A provides 114 suggested controls across domains such as access control, cryptography, physical security, supplier relationships and incident management. A Statement of Applicability (SoA) documents which controls are adopted and why.
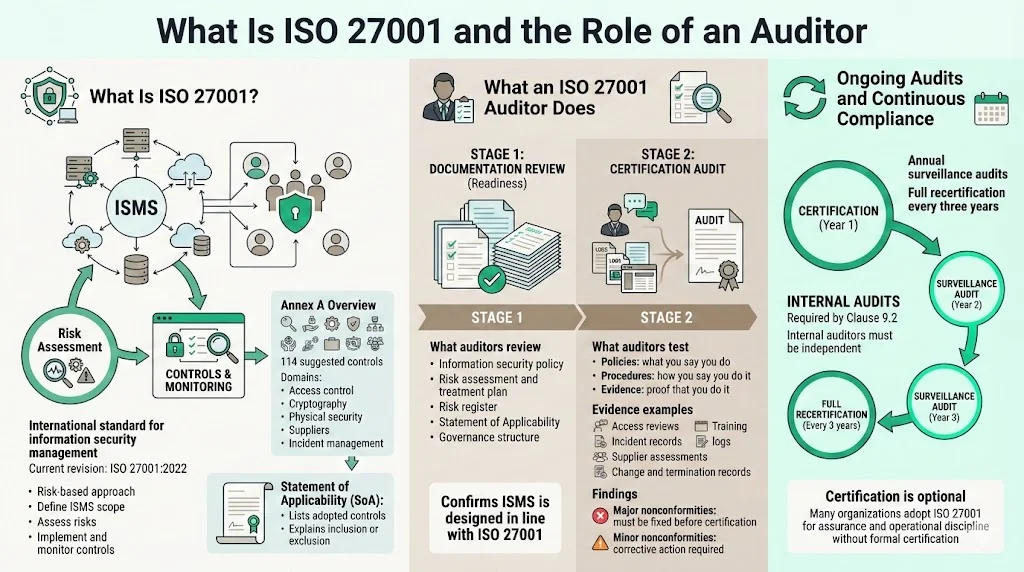
What an ISO 27001 Auditor Actually Does
The ISO 27001 certification process involves independent audits performed by accredited certification bodies. The audit has two stages. During Stage 1—the documentation review or readiness assessment—the auditor examines your policies, procedures, risk assessments, SoA and other ISMS documentation to confirm it is likely to meet the standard. Bridewell summarises Stage 1 as a broad review where the auditor checks that the ISMS has been developed in line with ISO 27001’s requirements. The StrongDM guide notes that documentation prepared in Stage 1 must clearly describe the ISMS implementation and supporting business processes. URM Consulting lists typical documents required at Stage 1: information‑security policy, risk assessment and treatment plan, risk register, SoA and documented governance arrangements.
Stage 2—the certification audit—tests whether controls operate as documented. Bridewell explains that auditors conduct on‑site or remote interviews with managers and staff, review activities in depth and seek evidence that the organization follows its documented processes. URM Consulting describes the “3 P’s” approach: auditors examine what you say you do (policy), how you say you do it (procedure) and whether you actually do it (prove it). Evidence may include access reviews, incident reports, training records, supplier assessments, change logs and samples of terminated accounts being disabled. Nonconformities identified during Stage 2 are classified as major or minor. Major issues must be resolved before certification; minor issues require corrective action but may not prevent certification unless numerous minor issues occur.
After Stage 2, surveillance audits are conducted annually to confirm continued compliance, and recertification occurs every three years. Internal audits are also mandated by Clause 9.2 of ISO 27001; organizations must perform them at planned intervals and ensure internal auditors are independent of the process being audited. The AuditBoard guide reminds readers that certification is optional—many organizations adopt ISO 27001 for operational improvements and stakeholder assurance without seeking certification.
Internal vs. External Audits and Accreditation
Internal ISO 27001 audits serve as a self‑assessment. The Penti comparison notes that internal audits aim to evaluate and improve the organization’s ISMS by identifying areas for improvement. Internal auditors should be independent and impartial within the organization but are still employees or contractors. By contrast, external audits are conducted by certification bodies or registrars to provide an independent assessment of the ISMS and determine eligibility for certification. These auditors must be completely independent of the organization.
Only accredited certification bodies can issue ISO 27001 certificates. URM Consulting explains that certification bodies perform audits and issue certificates, while accreditation bodies supervise certification bodies to ensure their competence. Examples of accreditation bodies include the United Kingdom Accreditation Service (UKAS) in the UK, the German accreditation body DAkkS, and the Japan Accreditation Board (JAB). Certificates issued by non‑accredited bodies may be valid but provide less assurance. Secureframe advises vendors to verify accreditation on the registrar’s website and confirms that UKAS, JAB and DAkkS are trustworthy sources.
KirkpatrickPrice warns against hiring one firm to perform both the audit and certification. To avoid conflicts of interest, best practice is to engage separate firms; a provider offering both services indicates a potential lack of integrity. Independence protects objectivity and ensures that regulators and enterprise buyers respect the final certificate.
Why Auditor Selection Matters for Enterprise‑Selling Companies
For vendors selling into large enterprises, ISO 27001 certification isn’t just a checkmark—it’s a competitive necessity. Secureframe reports that some enterprises require all vendors to be ISO 27001 certified. A credible certificate communicates that your ISMS meets international security benchmarks and is consistent with other frameworks like SOC 2, HIPAA and GDPR. Regulatory fines and breach costs illustrate the business impact: in 2026 the global average breach cost climbed to $4.88 million, and NIS2 introduces personal liability for executives. Enterprise clients expect vendors to manage risk proactively across their supply chain; failing to pass an ISO 27001 audit can therefore derail sales and damage trust.
Audit outcomes also shape contractual commitments. Customers often request the final Stage 2 audit report and may incorporate control obligations into contracts. A certificate issued by a non‑accredited body can undermine credibility; URM Consulting notes that non‑accredited certificates provide less assurance than accredited ones. Choosing an inexperienced auditor can lead to delays. URM highlights that Stage 1 and Stage 2 audits must be completed within six months and emphasises that organizations should schedule them five to five‑and‑a‑half months apart to avoid auditor availability issues. If your auditor lacks capacity or mismanages the process, you may miss that window and have to restart.
Konfirmity’s data backs this up. Among the 6,000+ audits we’ve supported, clients who selected inexperienced auditors experienced an average six‑month delay in certification and incurred additional remediation costs. Conversely, enterprise clients that engaged experienced auditors and adopted our managed compliance service completed SOC 2 and ISO 27001 readiness in four to five months, compared with nine to twelve months when self‑managed. That time savings translates directly into earlier revenue recognition.
Step‑by‑Step Guide to Selecting an ISO 27001 Auditor
This section breaks down a pragmatic process for choosing an auditor. Follow these steps to meet enterprise client expectations and minimize certification risk.
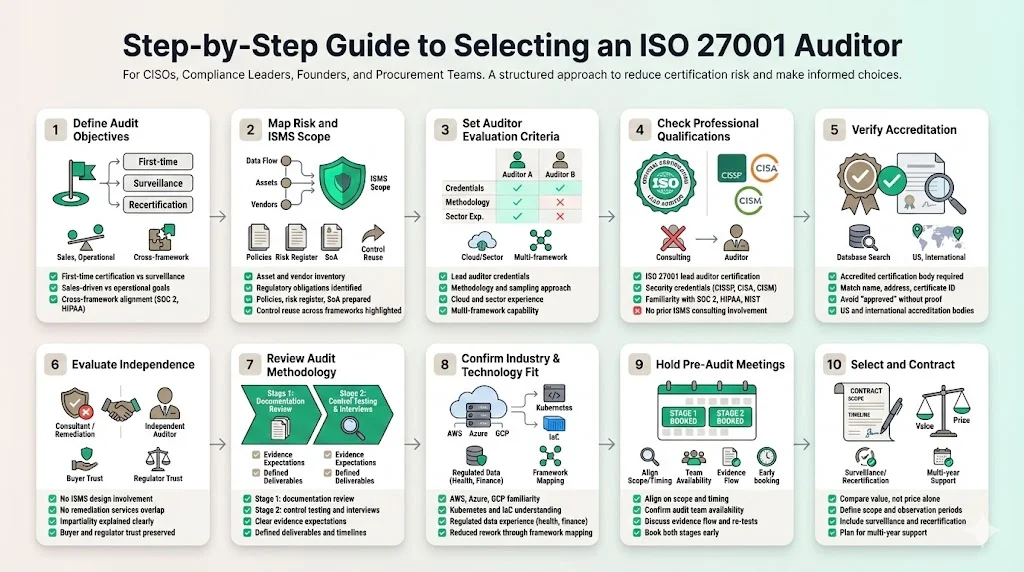
1) Define Your Audit Objectives Early
Clarify why you are pursuing ISO 27001 now. Objectives could include first‑time certification to open enterprise sales, surveillance audits to maintain compliance, or an internal readiness assessment before a future certification. Tie these goals to broader compliance requirements—for example, mapping SOC 2 and HIPAA controls with ISO 27001 to streamline evidence collection. A clear objective helps you articulate scope, timeline and deliverables when interviewing auditors.
2) Map Your Information Security & Risk Profile
Use your existing risk management documentation as a baseline. Inventory assets, data flows and vendors; identify regulatory obligations (GDPR, HIPAA, PCI DSS); and map current controls. This preparation is essential for two reasons: it guides your discussions with prospective auditors and helps them scope the effort accurately. URM advises compiling policies, risk assessments, SoA and governance documentation for Stage 1. A well‑structured ISMS not only accelerates Stage 1 but also reveals overlap with SOC 2 Trust Services Criteria or HIPAA safeguards. Konfirmity often finds that 60–70 percent of controls can be reused across frameworks when properly mapped.
3) Set Your Assessment Criteria
Develop criteria to evaluate prospective auditors. These should cover:
- Functional requirements. Look for auditors with ISO/IEC 27001:2022 lead auditor certifications, deep experience assessing cloud‑native environments and knowledge of your sector. Ask about their methodology, evidence collection, sampling techniques and risk‑based approach. URM’s “3 P’s” framework illustrates what a mature methodology looks like.
- Enterprise fit. Large vendors operate complex multi‑cloud stacks, handle regulated data (ePHI, financial information), and depend on numerous sub‑processors. Choose auditors familiar with such environments and who can assess microservices, infrastructure‑as‑code, CI/CD pipelines and vendor risk management. Secureframe notes that auditors experienced in your industry can speed the process and provide more meaningful insight.
- Compliance coverage. If your roadmap includes SOC 2, FedRAMP or PCI DSS, seek auditors accredited to perform multiple certifications. Secureframe advises working with one firm capable of issuing several certifications to reduce rework. However, ensure certification functions remain separate to avoid conflicts of interest.
4) Check Professional Qualifications
Verify that lead auditors hold ISO/IEC 27001 lead auditor certificates and have completed recognized training. Look for designations like CISA, CISSP or CISM that indicate broader information security expertise. Auditors should also be familiar with other frameworks (SOC 2, HIPAA, NIST SP 800‑53) to provide cross‑framework insight. Confirm that the auditor is independent of any consulting services you’ve used to design your ISMS; ISO 27001 requires internal auditors to be independent, and external auditors must avoid conflicts.
5) Verify Certification Bodies and Accreditation
Always verify that the certification body is accredited. URM explains that accreditation bodies supervise certification bodies to ensure competence. Secureframe lists UKAS, JAB and DAkkS as official accreditation sources, and URM notes that certification from a non‑accredited body provides less assurance. In the United States, the ANSI National Accreditation Board (ANAB) plays a similar role. Confirm an auditor’s accreditation by checking the accreditation body’s directory: the company name, address and certificate number should match. Avoid auditors who claim to be “approved” without a clear accreditation reference.
6) Evaluate Auditor Independence and Impartiality
Ensure that the auditor has no financial stake in your ISMS design or remediation work. KirkpatrickPrice advises hiring separate firms for audit and certification to prevent conflicts. Similarly, avoid contracting an auditor who previously consulted on building your ISMS. True independence builds trust with enterprise buyers and regulators. During due diligence, ask prospective auditors to describe how they avoid conflicts of interest and how they manage independence within multi‑service firms.
7) Review Audit Methodology and Deliverables
Ask candidates to explain their audit process, sample sizes and evidence collection methods. URM’s 3 P’s—policy, procedure and prove it—serves as a useful reference. Bridewell notes that Stage 1 is often remote and focuses on documentation, while Stage 2 involves on‑site or hybrid interviews and detailed testing. Confirm that the auditor will provide a gap analysis report after Stage 1 and a detailed findings report after Stage 2, including nonconformities and opportunities for improvement. Clarify timelines for report delivery and expectations for evidence submission.
8) Consider Industry and Technology Expertise
Enterprise environments often use microservices, container orchestration, infrastructure‑as‑code and multi‑region cloud deployments. Auditors must understand these architectures and be fluent in AWS, Azure, Google Cloud, Kubernetes and data processing platforms. Secureframe emphasises that auditors experienced with cloud computing, emerging technologies and industry‑specific requirements can provide better insight and accelerate Stage 1. For healthcare vendors handling ePHI, look for auditors familiar with HIPAA’s administrative, physical and technical safeguards and NIST’s guidance on protecting health data. For FinTech providers, auditors should understand PCI DSS and SOC 1/2 implications. Experience across frameworks enables auditors to map ISO 27001 controls to SOC 2 trust services criteria and HIPAA requirements, reducing duplicate effort.
9) Conduct Pre‑Audit Meetings
Before signing a contract, meet with prospective auditors to set expectations. Discuss timeline, scope, required documentation, and evidence submission. Confirm availability for Stage 1 and Stage 2 within your desired timeframe—URM urges booking both stages simultaneously to stay within the six‑month window. Ask about the audit team composition, communication cadence, and how they handle observations or questions during the audit. Clarify the process for addressing minor nonconformities and scheduling re‑tests.
10) Select and Contract Your Auditor
After evaluating qualifications, methodology, independence and fit, compare proposals on cost and value. Don’t choose based on price alone. Consider the auditor’s track record in your industry, their familiarity with your technology stack, and their ability to support cross‑framework certifications. Ensure that the contract clearly defines scope, deliverables, timeline, and fees. Specify the observation period if you are pursuing SOC 2 Type II concurrently—a typical observation window is three to six months. Finally, ensure that your auditor is prepared to support surveillance audits and recertification in years two and three.
What to Expect During the Audit Itself
Stage 1: Documentation Review
The documentation review assesses whether your ISMS is ready for certification. The auditor requests evidence of policies, procedures, risk assessments, the SoA and governance documentation. Bridewell describes Stage 1 as a broad assessment where the auditor examines documentation to see if the ISMS has been developed in accordance with ISO 27001 and the organization’s needs. Stage 1 can be completed on‑site or remotely. You will receive a report detailing any gaps or areas requiring improvement. If major gaps exist, address them before proceeding to Stage 2.
Stage 2: Certification Audit
Stage 2 is more thorough. The auditor tests the implementation and effectiveness of your controls, interviews stakeholders across departments and reviews evidence. As Bridewell explains, the auditor verifies that activities match the documentation reviewed in Stage 1 and checks that internal audits and management reviews have been conducted. URM describes how auditors use the policy‑procedure‑proof approach: they examine what the organization claims to do, how it claims to do it, and whether evidence supports those claims. Evidence may include access logs, incident management records, training attendance, supplier assessments and change‑management documentation. The Stage 2 team may include multiple auditors and will identify major and minor nonconformities and opportunities for improvement.
Surveillance and Recertification
After certification, expect annual surveillance audits to ensure ongoing compliance and continual improvement. Auditors will sample different control areas across the three‑year cycle, and any nonconformities must be addressed promptly. Recertification occurs in the third year and resembles another Stage 2 audit. Plan for resource availability and evidence collection year‑round; Konfirmity operates continuous monitoring to avoid last‑minute scrambles.
Common Pitfalls Companies Face When Choosing Auditors
- Choosing on price alone. A low‑cost auditor may lack experience or accreditation. Non‑accredited certificates provide less assurance and can hurt credibility with enterprise buyers.
- Hiring auditors with limited industry or enterprise experience. Secureframe notes that auditors familiar with your sector and technologies can accelerate the process and offer more meaningful insights. Inexperienced auditors may misinterpret controls or overlook critical risks, leading to delays and rework.
- Ignoring methodology and communication. Ask how auditors collect evidence, interview stakeholders and report findings. URM’s 3 P’s framework is a good benchmark. An unclear or rigid methodology can cause friction with your teams.
- Failing to verify accreditation or independence. Always confirm the certification body’s accreditation with UKAS, JAB, DAkkS or ANAB. Avoid firms that perform both audit and certification or that provide consulting services on your ISMS.
- Not coordinating timelines. URM warns that Stage 1 and Stage 2 audits must occur within six months. If you delay scheduling or choose an auditor with limited availability, you may have to restart the process, increasing cost.
Best Practices for Smooth Audit Preparation
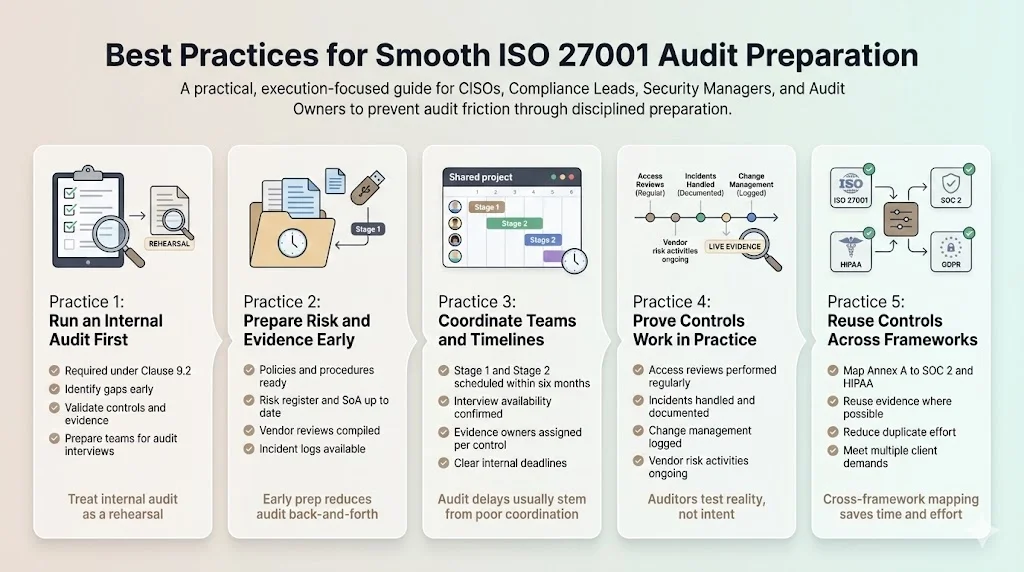
- Conduct an internal audit. Clause 9.2 requires internal audits at planned intervals. Use this as a dry run to identify gaps, validate controls and familiarise teams with evidence collection. Consider engaging a separate firm or experienced consultant if you lack internal capacity.
- Prepare risk assessments and evidence early. Compile policies, risk registers, SoA, vendor assessments and incident logs before Stage 1. This reduces back‑and‑forth with auditors and ensures control documentation reflects current practices.
- Coordinate internal teams around audit timelines. Schedule Stage 1 and Stage 2 audits within the six‑month window. Coordinate availability of critical personnel for interviews and evidence submission. At Konfirmity we create shared calendars and assign evidence owners for each control.
- Focus on control implementation, not just documentation. The Stage 2 audit tests whether controls work in practice. Monitor access reviews, incident responses, change‑management logs and vendor risk activities continuously to ensure evidence is current. Many failed audits stem from stale or incomplete evidence.
- Use cross‑framework synergies. Map ISO 27001 Annex A controls to SOC 2 trust services criteria, HIPAA safeguards and GDPR principles. This enables reuse of controls and evidence across frameworks and satisfies multiple client requirements. Konfirmity’s programs reuse roughly 70 percent of controls across ISO 27001 and SOC 2.
Conclusion
Investing in strong security controls and choosing the right ISO 27001 auditor pays dividends in both risk reduction and revenue generation. Data shows that breaches cost millions of dollars and regulatory fines can reach €10 million. ISO 27001 certification demonstrates to enterprise clients that your organization has implemented a risk‑based ISMS in line with international standards. However, the quality of your certificate hinges on the auditor. Select an accredited, experienced, independent auditor with a methodology that fits your environment. Prepare thoroughly, conduct internal audits, and integrate continuous monitoring so that controls stand up under observation. In our experience at Konfirmity, when you build real security controls, compliance becomes a natural result. Security that looks good on paper but fails under incident pressure is a liability. Build the program once, operate it daily, and let certification follow.
FAQ
1. Who can perform an ISO 27001 audit?
Both internal and external auditors can use the ISO 27001 framework to assess an ISMS. Internal audits evaluate and improve the ISMS and must be performed by personnel independent of the function being audited. External certification audits are conducted by independent certification bodies or registrars to determine eligibility for certification. Only accredited certification bodies can issue valid ISO 27001 certificates.
2. What questions should be asked before selecting an auditor?
Ask about the auditor’s accreditation (UKAS, ANAB, JAB, DAkkS), industry experience, lead auditor qualifications, methodology (policy‑procedure‑proof), sampling approach, independence (ensure they didn’t consult on your ISMS), evidence collection tools, timeline availability and deliverables. Verify their ability to support multiple frameworks if needed.
3. How much experience should an auditor have?
Seek auditors with formal ISO/IEC 27001 lead auditor certification and several years of hands-on experience performing audits for organizations similar in size and complexity to yours. Experience with cloud infrastructure, DevOps pipelines and regulated data (ePHI, financial information) is critical. Multi‑framework expertise enables control reuse and reduces cost.
4. What is the difference between certification bodies?
Certification bodies conduct ISO 27001 audits and issue certificates. Accreditation bodies oversee certification bodies to ensure competence. Examples include UKAS in the UK, JAB in Japan and DAkkS in Germany. Certificates from non‑accredited bodies provide less assurance. Choose a certification body accredited by a recognized national accreditation board (such as ANAB or UKAS) to ensure your certificate is widely accepted.
5. How long does an ISO 27001 audit take?
Audit duration depends on factors such as number of employees, physical sites and scope. URM explains that certification bodies use a calculator to determine audit time and that a small single‑site organization may receive a one‑day audit, while a large multi‑site organisation may need several days. Stage 1 and Stage 2 must occur within six months. Surveillance audits occur annually and recertification happens every three years.





.svg)






.svg)
.svg)