ISO 27001:2022 is an international standard that defines how organizations build an Information Security Management System (ISMS). An ISMS is a structured set of policies, processes, and controls that protect the confidentiality, integrity, and availability of information. The standard’s Annex A outlines specific controls that should be considered, but it allows organizations to apply them in a risk‑based manner. One of those controls—Annex A 8.13 “Information Backup”—states that “Backup copies of information, software and systems should be maintained and regularly tested in accordance with the agreed topic‑specific policy on backup”. This explicit reference shows that backup and recovery are not optional; they are foundational to information security.
Backup and recovery are critical for two reasons. First, they protect data integrity and availability. In 2024 the IBM Cost of a Data Breach report found that the average global breach cost reached USD 4.88 million, while the 2025 edition reported a decline to USD 4.44 million after organizations improved containment times. The difference highlights the financial impact of quick recovery. Second, backup and recovery underpin business continuity. When a ransomware attack, hardware failure, or accidental deletion occurs, organizations need to restore operations quickly. Without a tested backup, no amount of documentation will satisfy auditors or customers.
For enterprise buyers, backup and recovery correspond to risk management, service commitments, and operational resilience. Organizations risk losing contracts if they fail to guarantee that client data will be recoverable. The following sections explain how ISO 27001 Backup And Recovery For ISO 27001 fits into the ISMS, how to build a program that meets the standard, and how Konfirmity supports these efforts through a human‑led managed service.
ISO 27001 and the Role of Backup & Recovery
What the Standard Says
ISO 27001 Backup And Recovery For ISO 27001 is central to Annex A 8.13 because it requires organizations to decide what to back up, when, and how to test those backups.
Annex A 8.13 requires organizations to decide what to back up, when to back it up, and how to test the backups. It implies several sub‑activities:
- Identifying information assets and classifying them based on sensitivity and criticality.
- Defining a backup policy that covers frequency, media types, encryption, retention periods, and testing.
- Verifying that backups are recoverable through regular restore tests.
Annex A 17 (information security aspects of business continuity) complements Annex A 8.13. Annex A 17 ensures information security continuity is integrated into business continuity management so that operations relying on data and systems can be resumed during disaster recovery. Control A.17.1.1 requires organizations to plan their information security continuity requirements, A.17.1.2 addresses implementation of those requirements, A.17.1.3 requires testing and evaluation, and A.17.2.1 stresses the need for redundancies. Together, these controls require a holistic program that includes backup, redundancy, and continuity planning.
How Backup & Recovery Fit Into the ISMS
In ISO 27001 Backup And Recovery For ISO 27001, the integration of backups into the ISMS ensures that recovery processes are woven into risk management, data protection, business continuity, and incident response. An ISMS must link backups to risk management, data protection, business continuity, and incident response without treating them as separate activities.
An effective ISMS ties backup and recovery into broader security processes:
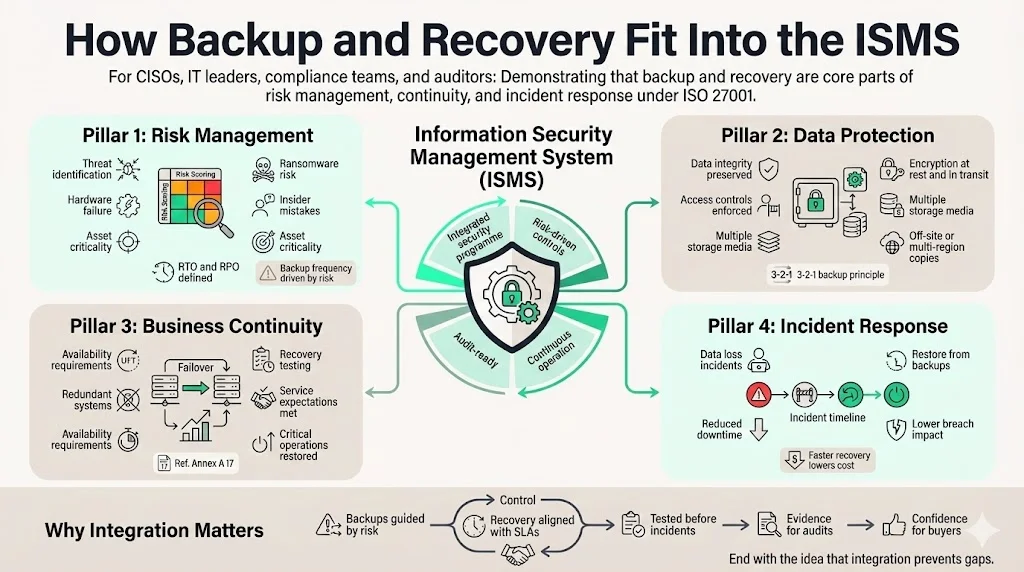
- Risk management: The risk assessment identifies threats—such as ransomware, hardware failure, or insider mistakes—that could lead to data loss. ISO 27001 calls for treatment plans that select controls proportional to the risk. According to the NIST NCCoE guide, organizations should identify files to back up based on business value and determine restoration time (RTO) and backup timing (RPO). A risk assessment informs which assets need backups and how often they need to be updated.
- Data protection: Backups support data integrity by preserving accurate copies. Encryption and access controls protect confidentiality. Storing copies on different media and in geographically distinct locations improves availability. NIST’s 3‑2‑1 rule advocates keeping three copies of important files, using two different media types, and storing one copy off‑site.
- Business continuity: Annex A 17 stresses the availability of information processing facilities. Redundancy ensures that if one system fails, another can take over. Recovery processes must be tested to confirm that critical operations can resume within agreed service expectations.
- Incident response: When data loss occurs, teams need to respond quickly. IBM reports that in 2024 it took organizations an average of 168 days to identify and 51 days to contain a breach. Faster response reduces breach costs, and the ability to restore data promptly is part of that response.
Essential Concepts Enterprise Buyers Should Understand
Backup vs. Disaster Recovery
ISO 27001 Backup And Recovery For ISO 27001 differentiates between making copies of data and restoring entire systems; a core theme is drawing a clear line between routine backups and wider disaster recovery planning.
Backup refers to creating copies of data so it can be restored if lost. Disaster recovery is a broader plan that restores systems, services, and business processes after a major disruption. Both are essential, but they serve different purposes.
- Backups: They provide point‑in‑time copies of data. NIST emphasizes that organizations should determine which files to back up, including event logs, user files, and applications. Backups may be full (complete copies), incremental (changes since the last backup), or differential (changes since the last full backup). Each type affects storage requirements and recovery time.
- Disaster recovery: It extends past simple data copies. A disaster recovery plan defines how to restore infrastructure—servers, networks, databases—and resume business services. It includes procedures for alternate facilities, failover mechanisms, and communication protocols. Annex A 17 requires planning for information security continuity and verifying the availability of information processing facilities.
Data Integrity, Confidentiality, and Availability
An essential requirement of ISO 27001 Backup And Recovery For ISO 27001 is maintaining the integrity, confidentiality, and availability of stored data, ensuring that backups uphold these qualities.
Backup programs must uphold the classic security triad:
- Integrity: Backups preserve the correctness of data. Organizations should verify backups through checksums and restore tests. Incomplete or corrupted backups compromise integrity.
- Confidentiality: Backups often contain sensitive information. Encrypt data at rest and in transit to prevent unauthorized access. Implement strong encryption mechanisms and restrict access to backup media. HIPAA guidance requires storing backups securely in a physically separate location and ensuring secure transmission.
- Availability: Data must be accessible when needed. Redundancy across multiple storage locations and media types helps. The NIST 3‑2‑1 rule specifically addresses availability by keeping three copies, using two media types, and storing one copy off‑site.
Building a Backup & Recovery Program
Establishing an ISO 27001 Backup And Recovery For ISO 27001 program involves a step‑by‑step methodology that aligns with disciplined risk assessment, scope definition, and implementation.
Konfirmity’s experience with more than 6,000 audits shows that a strong program requires clear steps, defined roles, and rigorous testing. Here is a step‑by‑step approach tailored for enterprise buyers.
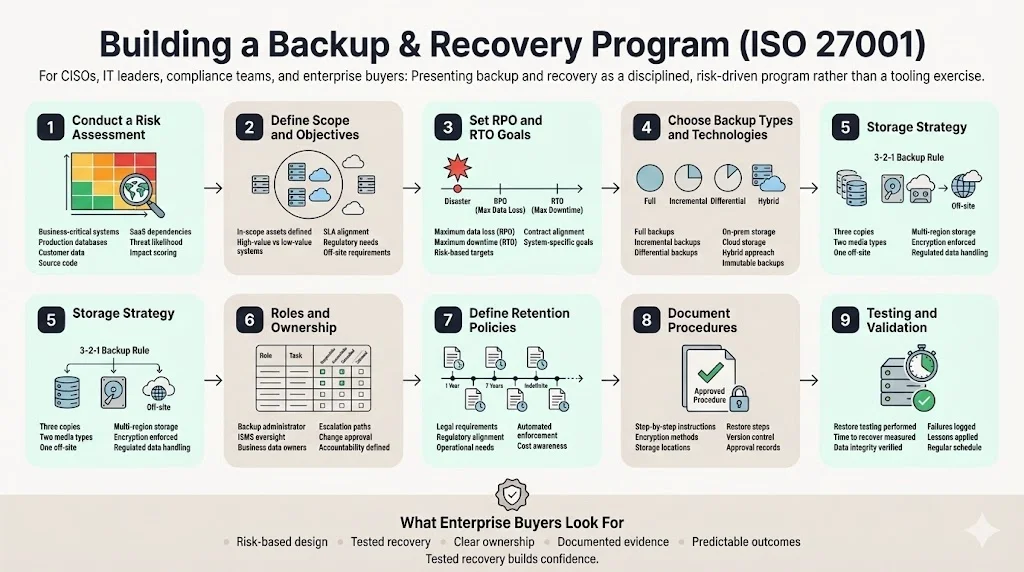
1 – Conduct a Risk Assessment
Identify business‑critical systems and data, including production databases, customer files, source code repositories, and SaaS services. The assessment should evaluate the impact of losing each asset and the likelihood of threats such as ransomware, hardware failure, or insider error. Use a structured risk methodology (e.g., ISO 27005 or NIST 800‑30) to prioritize assets and assign risk scores. NIST guidance says that organizations should identify files to back up and understand dependencies between systems.
2 – Define Scope & Objectives
Decide which assets fall within the backup program. For high‑value systems with aggressive uptime requirements, backups should be continuous or near real time. For less critical systems, daily or weekly backups may suffice. Ensure the scope fits with business use cases and customer SLAs. HIPAA, for example, requires healthcare organizations to have a documented plan for backing up electronic protected health information (ePHI) and storing copies in a secure off‑site location.
3 – Set RPO and RTO Goals
The Recovery Point Objective (RPO) defines the maximum age of data that can be lost before it affects the business. The Recovery Time Objective (RTO) defines how long you can take to restore operations. NIST guidance advises that organizations determine restoration time and backup frequency based on risk. Real‑time systems such as payment gateways may require near‑zero RPO and RTO, while archival data might permit longer windows. Document these objectives and confirm that they correspond to contractual commitments.
4 – Choose Backup Types and Technologies
Select backup methods that match RPO and RTO goals:
- Full backups copy all data. They provide straightforward restoration but consume storage and time.
- Incremental backups capture only changes since the last backup. They minimize storage but may lengthen restoration time because multiple increments must be applied.
- Differential backups copy changes since the last full backup. They balance storage and restoration complexity.
Choose storage locations: on‑premises (disk, tape), cloud, or hybrid. The NIST guide urges a mix of media types and off‑site storage. Cloud storage offers scalability and a variety of geographic options but may introduce bandwidth limitations. Immutable storage options protect backups against ransomware by preventing modifications. Evaluate vendors’ retention, encryption, and immutability features. Konfirmity often deploys immutable cloud storage for critical systems and local disk for rapid restores, combining them through automation.
5 – Storage Strategy
Implement the 3‑2‑1 rule: maintain three copies of data on two different media types and keep one off‑site. Use multiple geographic locations to mitigate regional disasters. Apply encryption at rest and in transit to protect confidentiality. HIPAA’s contingency plan standard requires secure transmission and storage. For regulated data (ePHI, personal data under GDPR), ensure storage providers meet compliance requirements and sign Business Associate Agreements (BAAs) where applicable.
6 – Roles and Ownership
Assign responsibilities clearly. A backup administrator or DevOps engineer performs the backups, ensures the process runs, and troubleshoots failures. An information security officer or ISMS manager verifies that backups meet policy requirements and approves changes. Stakeholders from business units determine RPO and RTO requirements and are accountable for data classification. Define escalation procedures for backup failures and document these roles in the Statement of Applicability.
7 – Define Retention Policies
Retention policies specify how long backups are kept. They should conform to legal, regulatory, and operational requirements. For example, financial records may need to be retained for seven years, whereas system logs may be kept for one year. Retention policies also affect storage costs and restore complexity. Document retention periods and ensure they are enforced automatically through backup software.
8 – Document Procedures
ISO 27001 requires that procedures be documented, version controlled, and approved. Document step‑by‑step processes for backup creation, storage, and restoration. Include details on file naming conventions, encryption methods, off‑site transfer processes, and restoration steps. Document exceptions and planned maintenance windows. Store procedures within the ISMS alongside other policy documents, with a version history and approval signatures. This documentation becomes evidence during audits.
9 – Testing and Validation
The most common gap Konfirmity encounters is the absence of restore tests. Teams schedule backups but fail to prove that data can be recovered. NIST advises testing recovery plans for both individuals and the entire organization. Perform periodic restore drills—quarterly for high‑value systems and at least annually for others. Tests should measure the time to restore and verify data integrity. Track test results, log failures, and refine procedures based on lessons learned. HIPAA guidance encourages regular testing and revision of contingency plans. For critical systems, integrate automated test restores to catch corruption early.
Best Practices to Strengthen Backup & Recovery
To strengthen ISO 27001 Backup And Recovery For ISO 27001, enterprises should adopt automated workflows, redundancy, secure infrastructure, and continuous improvement.
Implement these tactics to build resilience:
- Automate backups and monitoring: Use orchestration tools to schedule backups, verify completion, and alert on failures. Automate retention enforcement and off‑site replication.
- Maintain redundancy: Avoid single points of failure. Use multiple storage vendors or replicate data across regions. NIST guidance advises keeping a set of systems disconnected from the business network for emergency use.
- Secure the backup infrastructure: Restrict administrative access through multi‑factor authentication. Apply the principle of least privilege. Regularly patch backup servers and storage devices. Store encryption secrets separately from backups.
- Integrate alerts: Configure alerts for backup failures, high error rates, or missed schedules. Connect alerts to the incident response team so that corrective action happens quickly.
- Update plans after changes: Major system changes, migrations, or new regulatory obligations require updating backup plans. Document changes and re‑test.
- Include metrics in ISMS reviews: ISO 27001 demands continuous improvement. Track metrics such as backup success rate, test restore success rate, average restore time versus RTO, and storage utilization. Review these metrics in management meetings and adjust controls accordingly.
Common Mistakes and How to Avoid Them
Common pitfalls in implementing backup and recovery for ISO 27001 include untested backups, single storage locations, weak encryption, and unclear ownership.
Through our work supporting thousands of audits, we see recurring issues:
- Untested backups: Organizations back up data but rarely test restores. Without testing, hidden corruption or configuration errors remain unnoticed. Schedule regular restore drills and verify integrity.
- Single backup location or vendor: Relying on one provider or one geographical location creates a single point of failure. The 3‑2‑1 rule advises multiple media types and off‑site storage.
- Incomplete documentation: Auditors look for policies, procedures, and test logs. Missing documentation or outdated versions cause nonconformities. Maintain versioned procedures and evidence.
- Weak encryption or access controls: Backups often contain sensitive data. Failing to encrypt or restrict access may violate HIPAA and GDPR. Encrypt data at rest and in transit and enforce strict permissions.
- Unclear ownership: When ownership is ambiguous, backup tasks may be overlooked. Define roles, responsibilities, and escalation paths.
- Stale evidence: Evidence collected during readiness but not maintained over time becomes stale. Continuous monitoring is essential for SOC 2 Type II audits, which assess controls over an observation period (often 6–12 months). The SOC 2 framework comprises five Trust Services Criteria organized into 64 individual requirements; auditors expect evidence that controls operate consistently throughout this period.
Audits and Compliance Checks
When reviewing backup and recovery controls under ISO 27001, auditors focus on documented policies, evidence of backup jobs, restore tests, and adherence to RPO/RTO objectives.
How Auditors Review Backup Controls
Auditors examine whether the organization has documented policies, procedures, and evidence that controls operate effectively. For ISO 27001, they will look for a backup policy approved by management, risk assessments identifying critical data, documented RPO and RTO, and test records. They also expect to see evidence of backup jobs—logs that show when backups were executed, whether they succeeded, and how errors were addressed. Annex A 8.13 requires regular testing; auditors will ask for restore test reports. For SOC 2 Type II, auditors assess controls over the observation period; they may sample backup logs and test results across months to see whether controls operated consistently..
What Causes Nonconformities
Common nonconformities include:
- Missing test logs: Without evidence that backups were tested, auditors are unable to verify that the control works.
- Undocumented procedures: ISO 27001 requires documented procedures; failing to document backup procedures violates Annex A 8.13.
- Inconsistent backups: If backup schedules are irregular or not aligned with RPO/RTO, auditors may raise findings.
- Insufficient storage protections: Lack of encryption or off‑site storage may lead to violations of confidentiality and availability principles.
- Lack of ownership: Without assigned roles, responsibilities may fall through the cracks.
Making Audit‑Ready Evidence Easy
A managed service like Konfirmity automates evidence collection. Backup jobs produce logs stored in a centralized evidence store. Restore tests generate reports that show start time, end time, results, and issues found. The backup policy and procedures reside in a versioned document repository. During an audit, clients provide auditors access to evidence dashboards rather than manually collecting artifacts. This reduces internal effort and ensures evidence is current.
Disaster Recovery and Business Continuity
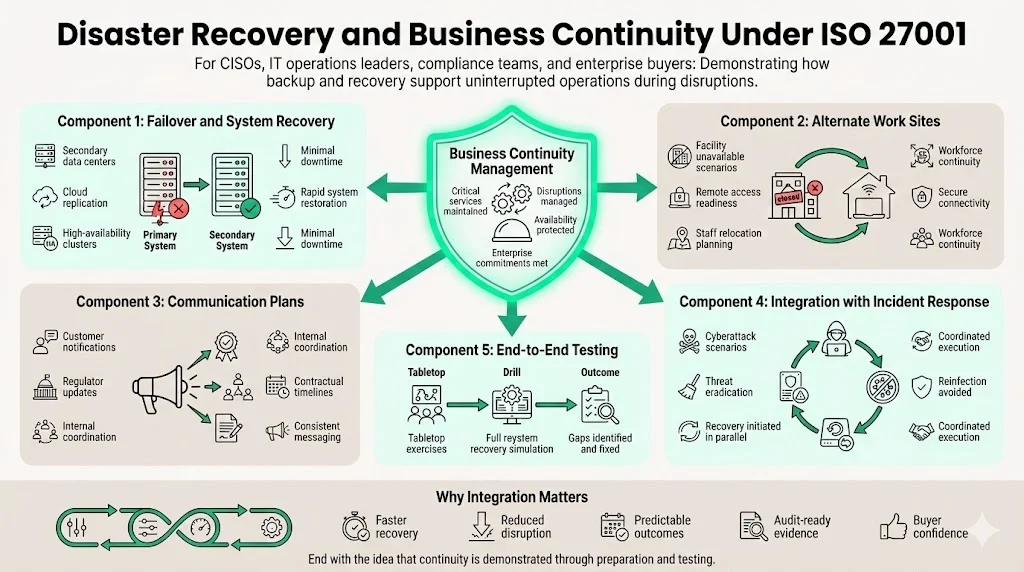
ISO 27001 Backup And Recovery For ISO 27001 links directly to business continuity planning by ensuring that systems and data remain available during disruptive events.
Backup and recovery are cornerstones of a broader business continuity strategy. Annex A 17 integrates information security continuity into business continuity management. Disaster recovery planning should cover:
- Failover options: Secondary data centers, cloud replication, and high‑availability clusters ensure that systems can be restored quickly.
- Alternate work sites: NIST advises considering workplace relocation options in case a facility is unavailable. Business continuity plans must account for staff relocation and remote access.
- Communication plans: Define how to notify customers, regulators, and internal teams during a major disruption. Communication should be consistent with legal and contractual obligations.
- Integration with incident response: Disaster recovery plans should link to incident response procedures. If data loss results from a cyberattack, response teams should simultaneously eradicate the threat and initiate recovery. Coordination ensures that restored systems are not re‑infected.
- Testing end‑to‑end: Conduct tabletop exercises and full recovery drills to verify that business processes can continue. NIST advises testing response and recovery processes to identify gaps. Tests should involve cross‑functional teams and third‑party providers..
Closing Thoughts
Effective backup and recovery extends past certification; it builds trust with enterprise customers and supports resilience across frameworks.
Backup and recovery are not just technical tasks; they are critical controls that underpin enterprise trust and regulatory compliance. ISO 27001 calls for a risk‑based ISMS, and Annex A 8.13 and A.17 embed backup and continuity into that system. NIST guidance highlights the importance of RPO, RTO, and the 3‑2‑1 rule. HIPAA requires healthcare organizations to maintain backup and disaster recovery plans. SOC 2 audits evaluate whether controls operate consistently across an observation period, with 64 individual requirements across the five trust services criteria.
Konfirmity’s human‑led, managed service helps organizations build and operate these programs. Our teams conduct risk assessments, implement controls within customer environments, automate evidence collection, and support audits year‑round. We emphasize real security outcomes—tested backups, reliable restores, and continuous monitoring—so that compliance follows naturally. Security controls must stand up not only during audits but also under attack. Building a resilient backup and recovery program grounded in ISO 27001 gives enterprise buyers confidence that you can meet service commitments, protect data, and restore operations quickly when incidents occur.
FAQ: ISO 27001 Backup and Recovery
1. Does ISO 27001 require backups?
Yes. While ISO 27001 does not prescribe specific tools, Annex A 8.13 states that backup copies of information, software, and systems must be maintained and regularly tested. The standard expects organizations to establish a policy, implement backups, and verify recoverability. Annex A 17 complements this by requiring information security continuity planning.
2. How often should backups be tested for ISO 27001?
The frequency of testing depends on risk and business requirements. NIST advises planning and testing recovery processes for both individuals and the entire organization. Many enterprises test critical system restores quarterly and perform full restores annually. Backup testing should also occur after significant system changes or incidents.
3. What is the difference between backup and disaster recovery?
Backups are copies of data that allow restoration to a specific point in time. Disaster recovery encompasses the broader strategy to restore systems and services after a major disruption. It includes infrastructure failover, alternate work sites, communication plans, and coordinated response. Both are necessary; one without the other leaves gaps.
4. How do auditors review backup controls?
Auditors examine documented policies, backup schedules, evidence of backup jobs, and restore test logs. They verify that RPO and RTO objectives are defined and met. For SOC 2 Type II, auditors look at evidence over the observation period (usually 6–12 months) to ensure consistency. For ISO 27001, they check that Annex A 8.13 and A.17 controls are implemented and effective.
5. What backup failures cause ISO 27001 nonconformities?
Common failures include untested backups, missing documentation, reliance on a single storage location, lack of encryption, and ambiguous ownership. Auditors also flag inconsistent backup schedules and failure to meet defined RPO/RTO objectives. Addressing these issues involves automating backups, enforcing the 3‑2‑1 rule, documenting procedures, and assigning clear roles





.svg)






.svg)
.svg)