Most enterprise buyers now ask for assurance documents before procurement. Deals stall when teams rely on paperwork rather than real security operations. Over decades of guiding companies through ISO 27001, SOC 2, HIPAA and GDPR audits, I’ve learned that the gap between what’s written and what’s operating can make or break a sale. ISO 27001 Board Reporting isn’t about ticking a box. It gives directors a clear view of whether controls work, whether risk is moving up or down, and how security investments support growth. Done well, ISO 27001 Board Reporting turns technical data into business insight and wins trust with enterprise clients.
This article explains what ISO/IEC 27001 is, why reporting to the board matters and how to craft reports executives can use. ISO 27001 Board Reporting turns technical output into business context. You’ll find a step‑by‑step process, templates and examples drawn from Konfirmity’s delivery work—more than 6,000 audits across 25 years of combined expertise. We’ll also answer common questions about ISO 27001, audit reporting, control categories and mandatory clauses. The aim is to help you build reports that satisfy enterprise buyers, reduce risk and streamline audits.
Why Board Reporting for ISO 27001 Matters
ISO 27001 Board Reporting is essential because ISO 27001 is an international standard that guides organizations in building an information security management system (ISMS). Its principles—confidentiality, integrity and availability—ensure authorised access, accuracy and availability.
Reporting to the board connects these technical objectives with business goals. Directors increasingly view cyber security as a strategic risk, yet many lack confidence in assessing it. Clear reports on risks, incidents and mitigation give leadership the visibility needed to govern and invest.
For vendors selling to regulated enterprises, board reporting is often required. Contracts may demand evidence of ISO 27001 certification and regular reporting on security posture. Recent SEC rules also require public companies to disclose cybersecurity governance structures and material incidents. Demonstrating strong reporting accelerates procurement and shows due diligence.
CTA: Book a demo
What to Include in an ISO 27001 Board Report
When preparing ISO 27001 Board Reporting, keep in mind that a strong package covers more than audit findings. It paints a holistic picture of the ISMS and its impact on business results. It integrates technical oversight with business insight. Below are the important content areas to include. These sections act as semantic lenses—different ways to view the same underlying program.
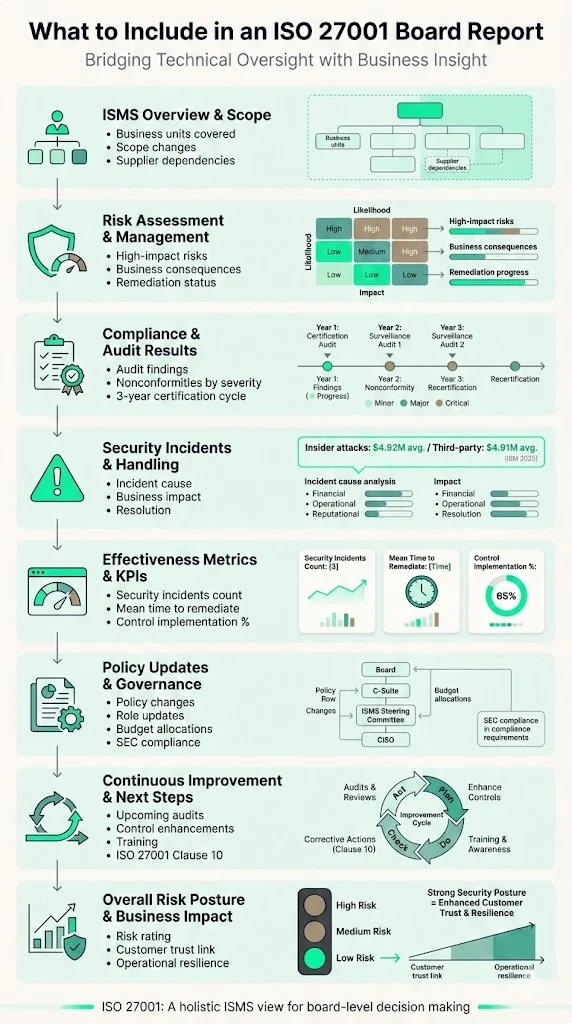
- ISMS overview & scope – Explain what parts of the organization fall under the ISMS. If scope changes occurred since the last report, describe them. Make sure to address business units, products or geographies covered, and mention any dependencies on suppliers or cloud services. A clear scope helps directors understand what is included and where gaps might exist.
- Risk assessment & management overview – Provide an overview of recent risk assessments, focusing on high‑impact risks, their potential business consequences and the status of remediation plans. Quantify risk where possible (for example, tie a misconfigured cloud bucket to projected breach costs or regulatory penalties).
- Compliance & audit results – Provide condensed results of internal and external audits. List nonconformities by severity, explain corrective actions and describe surveillance or recertification timelines. ISO 27001 certifications last three years and require two surveillance audits in years one and two, with a recertification audit at year three.
- Security incidents & incident handling – Outline any incidents since the last report. For each, describe the cause, business impact and resolution. IBM’s 2025 Cost of a Data Breach report found that malicious insider attacks averaged USD 4.92 million and third‑party compromises USD 4.91 million—data that can help contextualize your own risk.
- Effectiveness metrics & KPIs – Use metrics that illustrate ISMS health and progress. Examples include number of security incidents, mean time to remediate and percentage of controls implemented.
- Policy updates & governance changes – Report updates to policies, procedures, roles and responsibilities. Describe any changes in executive sponsorship, budget allocations or cross‑functional committees. For regulated buyers, mention compliance with external requirements such as SEC disclosure rules.
- Continuous improvement & next steps – Outline planned actions, including upcoming audits, control enhancements, new risk mitigation measures, awareness training, or technology deployments. Emphasize the iterative nature of ISO 27001; clause 10 of the standard requires organizations to act on audit findings and continually improve the ISMS.
- Overall risk posture & business impact overview – Translate technical details into business terms. Provide an overall risk rating, link risks to customer trust, operational resilience and revenue, and explain whether risk is increasing or decreasing. Use simple visual indicators (e.g., red/yellow/green) to make the information accessible to non‑technical directors. This section bridges the gap between security operations and enterprise strategy.
Step‑by‑Step Process to Build a Board‑Ready ISO 27001 Report
A disciplined process makes ISO 27001 Board Reporting repeatable and efficient. Here’s a practical workflow drawn from our managed service experience.

- Define scope and audience – Clarify which business units, systems and locations are included in the ISMS and who will receive the report (board, executive team, compliance committee, major clients). Match the depth of detail to the audience’s needs—boards need broad insights; security teams need operational details.
- Gather inputs from the essential teams – Engage security, IT, compliance, audit, legal and operations to collect data on controls, incidents, audits, metrics and policy changes. This cross‑functional collaboration prevents blind spots and ensures that the report reflects reality.
- Carry out a fresh risk assessment (if due) – ISO 27001 requires periodic risk assessments. Update your risk register with new threats, business changes and vulnerabilities and prioritize risks using accepted methods.
- Compile audit & compliance data – Consolidate internal and external audit results and list nonconformities and corrective actions. For external audits, record the stage of the review and surveillance timelines.
- Summarize incidents and remediation – Provide a concise list of incidents since the last board meeting, their causes, impact and the remediation taken. Transparency is important; hiding incidents erodes trust and may breach disclosure requirements.
- Collect effectiveness metrics – Select KPIs that reflect ISMS effectiveness such as incident counts, mean time to detect and remediate, control coverage and training participation. Use historical data to show trends.
- Review policies & control status – Report updates to policies and the status of Annex A controls (implemented, partial or planned), and record any exceptions in the Statement of Applicability.
- Write the risk posture and business impact narrative – Translate technical risks into business consequences, describe potential disruptions to operations or clients and provide an overall rating (low/medium/high).
- Define next steps / roadmap – Outline upcoming audits, improvements, resource needs and training.
- Present in a structured format – Use an executive overview followed by the sections described earlier; include charts for quick scanning and append detailed artifacts (risk register, control matrix, audit logs and incident reports) for reference.
Examples & Templates (Structure + Sample Content)
A clear structure helps your audience follow the report and find what they need. The table below offers a suggested skeleton for your report. Adapt it to your organization’s scope and maturity. Keep the table narrow and use prose in the body for explanations.
Use the template above as a starting point. Populate each section with your own risk snapshots, effectiveness dashboards and audit observations so that directors receive concise and relevant information.
Special Considerations for Enterprise‑Client Selling Companies
For regulated buyers, ISO 27001 Board Reporting is particularly important. Enterprise clients scrutinize vendor security posture through questionnaires, security addenda and direct audits. Demonstrating compliance and risk governance builds trust and accelerates sales. Clear reports showing that the ISMS covers relevant systems and that risks are managed boost confidence.
Enterprise agreements often include right‑to‑audit clauses, and buyers require evidence of continuous compliance. Structured reporting allows quick responses to these requests and smoother contract renewals. Board reporting also connects security strategy with business objectives—leadership can see how security investments support revenue, customer satisfaction and operational stability. Without visibility at the board, security budgets risk becoming an opaque cost rather than a driver of value.
Common Pitfalls & How to Avoid Them
Many teams struggle with ISO 27001 Board Reporting. Common mistakes include:
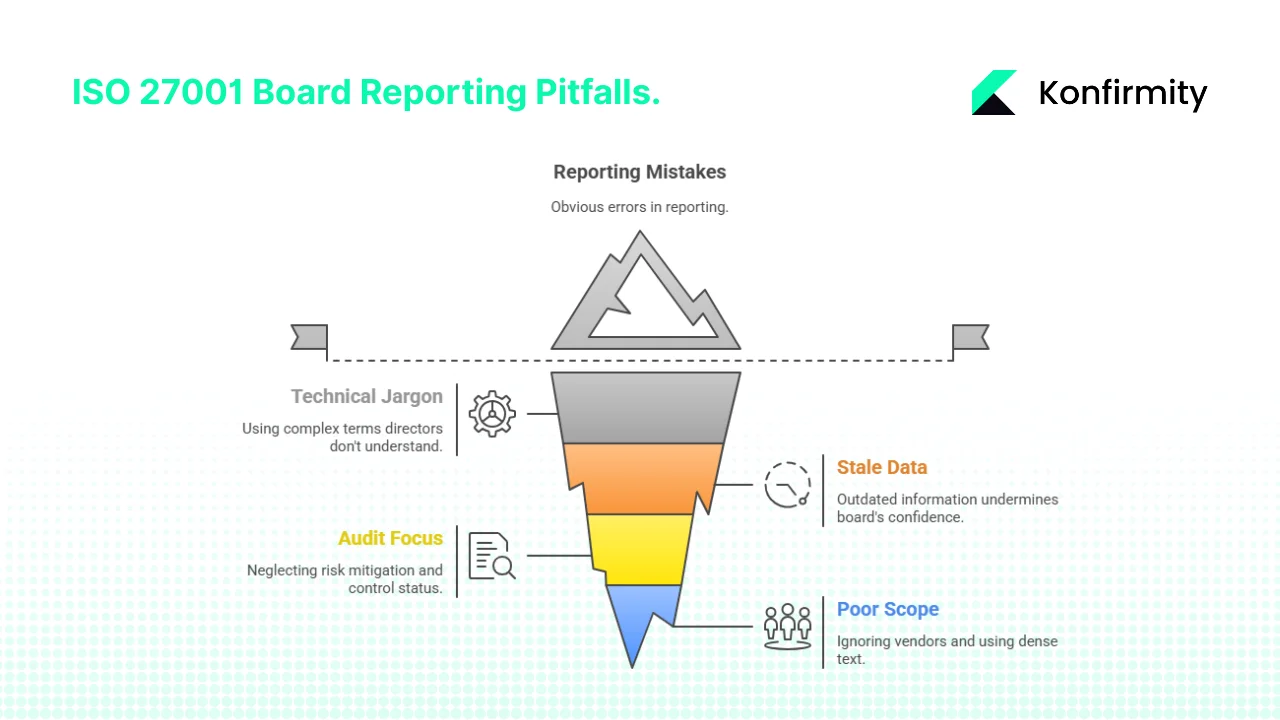
- Too much technical language – Jargon can alienate directors. Translate metrics into business impact and use plain terms like “probability of data loss.”
- Stale or incomplete data – Out‑of‑date metrics undermine trust. Update incidents and control data regularly and maintain a cadence for reporting.
- Audit‑only focus – Audits capture a point in time. Boards also need to know the status of risk mitigation initiatives, control implementation and improvement plans.
- Poor scope, visuals or vendor coverage – Reports that ignore vendors or pack dense text mislead directors. Review scope regularly, include supply‑chain assessments and use simple visuals to show trends. IBM’s data show third‑party compromises cost about USD 4.91 million.
Tools & Automation Tips for Busy Teams
Tools can pull data from your systems, but ensure they meet ISO 27001 requirements and support your scope. Automation supports rather than replaces human judgment, and Konfirmity pairs technology with experts to interpret data and maintain continuous evidence.
Our managed service cuts internal effort from roughly 600 hours per year to about 75 and reduces readiness timelines. We implement controls inside your stack, carry out ongoing monitoring and execute risk assessments so you stay audit‑ready.
CTA: Book a demo
Conclusion
ISO 27001 Board Reporting is more than an administrative task; it builds trust, reduces risk and improves governance. By translating technical controls into business insights and maintaining a consistent cadence, leaders can make informed decisions and allocate resources wisely. It also signals to customers that the company values security as a core commitment and invests accordingly. Boards and executives should demand evidence of continuous monitoring, risk mitigation and improvement and handle security as an ongoing program rather than a one‑time hurdle. Security that looks good in documents but fails under pressure is a liability—build controls that stand up to auditors, buyers and attackers and let compliance follow.
This clarity builds overall trust among stakeholders across the organization.
FAQs
1) What is an ISO 27001 report?
It communicates the status of your ISMS—summarising scope, risk assessments, controls and audit results. Reports to the board translate this information into business risk terms, while operational reports provide detailed evidence for auditors and security teams.
2) How do you make an ISO audit report?
Define the scope and criteria, conduct the internal audit, document nonconformities and corrective actions and provide an overview of findings and evidence. External auditors will carry out a similar review. Certifications last three years and require surveillance audits in years one and two.
3) What are the four categories of ISO 27001 controls?
The 2022 update groups the 93 Annex A controls into four categories: organizational, people, physical and technological.
4) What are the mandatory requirements of ISO 27001?
Clauses 4 through 10 cover context and scope, leadership, planning, support, operation, evaluation and improvement. Maintaining strong board reporting helps demonstrate compliance and earn the trust of enterprise clients.





.svg)






.svg)
.svg)