Most enterprise buyers now request assurance artifacts before procurement. Without operational security and continuous evidence, deals stall—even when teams think they are "ready" on paper.
In the current market, a certification badge on your footer is no longer enough to satisfy a Fortune 500 procurement team. Enterprise security questionnaires have shifted from asking if you are secure to asking how you are secure. They demand proof of specific technical configurations, vulnerability management SLAs, and access controls. This is where the concept of ISO 27001 Controls Mapped To CIS becomes a critical business asset.
For companies selling to enterprise clients, the intersection of ISO/IEC 27001 (governance) and the Center for Internet Security (CIS) Controls (technical execution) is where trust is actually established. It is the difference between having a policy that says you encrypt data and proving that your endpoints actually enforce encryption standards.
At Konfirmity, having supported over 6,000 audits across 25 years of combined expertise, we see a distinct pattern: companies that rely solely on high-level policies struggle to close deals with sophisticated buyers. Companies that map their governance to hard technical baselines move through security reviews 40-50% faster.
This guide explains why mapping these frameworks matters, how to do it, and why it changes the conversation from "compliance" to revenue assurance.
Why This Mapping Matters for Enterprise-Focused Companies

Enterprise buying behavior has fundamentally changed. In 2025-2026, the average cost of a data breach has continued to rise, and regulatory pressure from GDPR, CCPA, and sector-specific laws (like HIPAA) has forced large organizations to treat their vendors as extensions of their own attack surface.
When a bank, a healthcare provider, or a SaaS aggregator evaluates your product, they are performing risk management, not just compliance checking. They need to know that your Information Security Management System (ISMS) is not a "paper tiger"—a set of documents that exist only to pass an audit.
Why Buyers Ask for Proof of Strong Information Security Management
Buyers ask for granular details because they have been burned by vendors who claimed to be secure but lacked basic hygiene.
A standard ISO 27001 certification proves you have a management system. It demonstrates that you have identified risks and established policies. However, ISO 27001 is often descriptive, not prescriptive. It tells you to "manage vulnerabilities," but it does not explicitly dictate that you must patch critical flaws within 7 days or disable unused ports.
That creates a gap in trust. The buyer sees your ISO certificate but sends a 300-question spreadsheet asking about your firewall configurations, malware defenses, and administrative privileges.
How Control Mapping Reduces Friction During Reviews
This is where mapping saves time. By proactively creating a set of ISO 27001 Controls Mapped To CIS benchmarks, you connect your high-level governance to specific, verifiable actions.
When a questionnaire asks, "How do you manage device security?" you do not just cite "ISO Policy 8.1." You cite the policy and the underlying CIS Control (e.g., CIS Control 4: Secure Configuration of Enterprise Assets and Software) that provides the technical evidence.
This turns a vague answer into a definitive one. It shows the buyer that your security program is operational, not theoretical.
Understanding the Two Frameworks at a Practical Level
To understand why mapping is powerful, we must first look at what each framework achieves in isolation. They are not competitors; they are counterparts.
What Is ISO/IEC 27001?
Overview of ISO/IEC 27001 ISO/IEC 27001 is the international standard for information security. It focuses on the Information Security Management System (ISMS)—a systematic approach to managing sensitive company information so that it remains secure. It includes people, processes, and IT systems by applying a risk management process.
Purpose of an ISMS The goal of an ISMS is to protect three things:
- Confidentiality: Only authorized people can access data.
- Integrity: Data is not altered or tampered with.
- Availability: Data is accessible when needed.
Annex A Controls Explained The core "checklist" within ISO 27001 is found in Annex A. In the 2022 version, these were consolidated into 93 controls across four themes:
- Organizational
- People
- Physical
- Technological
Why Enterprises Treat ISO 27001 as a Trust Signal Enterprises value ISO 27001 because it requires an external audit by an accredited certification body. It proves that management is involved in security and that there is a cycle of continuous improvement.
What Are CIS Controls?
Overview of CIS Controls The Center for Internet Security (CIS) Controls are a prioritized set of actions to protect organizations and data from known cyber attack vectors. Unlike ISO, which starts with risk assessment, CIS starts with threat defense. It assumes you are a target and tells you exactly what to do to stop attacks.
Focus on Real-World Cybersecurity CIS Controls (currently version 8) are technical. They deal with inventory of assets, data protection, secure configuration, account management, and log management. They are derived from analyzing actual attack data.
Structure of CIS Controls v8 CIS v8 consists of 18 controls (formerly 20), organized into Implementation Groups (IGs).
- IG1: Basic cyber hygiene (essential for everyone).
- IG2: Mainstream enterprise security.
- IG3: Advanced protection for highly sensitive data.
Why Security Teams Prefer CIS Engineering and Operations teams prefer CIS because it is actionable. "Implement MFA for all remote access" is a clear instruction. "Manage access rights" (ISO) is a directive that requires interpretation.
ISO 27001 vs. CIS Controls: How They Differ and Connect
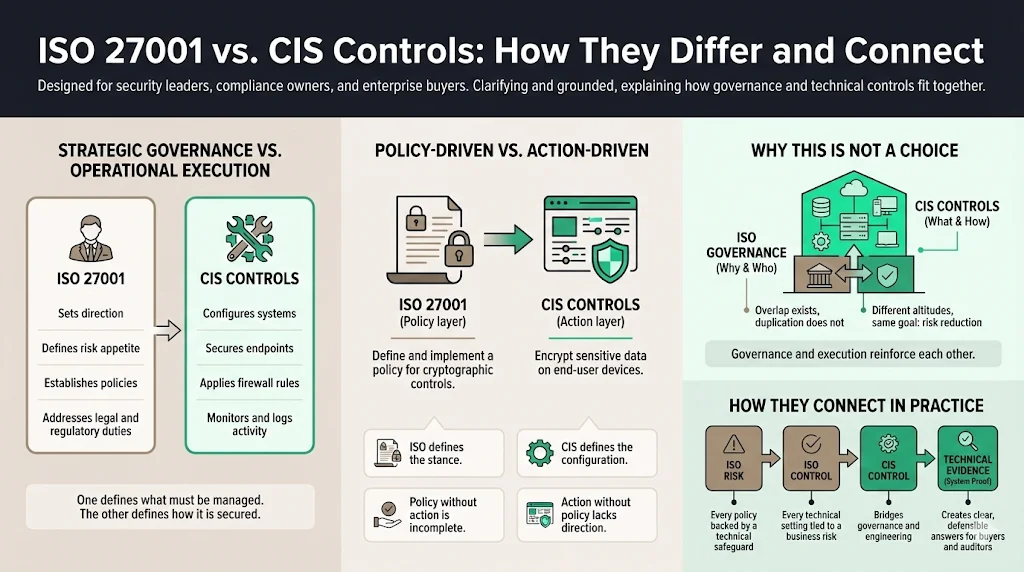
The most common confusion we see at Konfirmity involves companies trying to choose between ISO 27001 and CIS. This is a false choice.
Strategic Governance vs. Operational Execution
Think of ISO 27001 as the CEO of your security program. It sets the direction, allocates the budget, defines the risk appetite, and handles the legal obligations.
Think of CIS Controls as the Lead Engineer. It configures the servers, locks down the endpoints, sets the firewall rules, and monitors the logs.
You cannot have a secure building with only a CEO (policy) and no Engineer (locks). Conversely, having great locks (CIS) without a CEO (ISO) means you might be securing the wrong building or ignoring legal requirements like GDPR.
Policy-Driven vs. Action-Driven
- ISO 27001 (Policy): "The organization shall define and implement a policy on the use of cryptographic controls."
- CIS Control 3 (Action): "Encrypt data on end-user devices containing sensitive data."
The ISO standard requires you to have a stance on encryption. The CIS control dictates that you actually turn on BitLocker or FileVault.
Why the Frameworks Overlap But Are Not Duplicates
There is significant overlap because both aim to reduce risk. However, they approach it from different altitudes. ISO provides the wrapper—the "why" and the "who." CIS provides the payload—the "what" and the "how."
Connecting them bridges the gap between IT governance and security best practices. It ensures that every technical setting exists to satisfy a business risk, and every business risk is mitigated by a technical setting.
What Is Control Mapping Between ISO 27001 and CIS?

ISO 27001 Controls Mapped To CIS is the process of linking the high-level requirements of the ISO standard to the specific technical safeguards of the CIS framework.
Definition of Control Mapping
In plain language, mapping is a translation layer. It creates a matrix where you say: "To satisfy ISO Control A.8.7 (Protection against malware), we implement CIS Control 10 (Malware Defenses), specifically safeguards 10.1, 10.2, and 10.3."
How One ISO Control Links to Multiple CIS Safeguards
Because ISO controls are broad, a single ISO control often requires multiple CIS safeguards to be fully effective.
For example, ISO Control A.8.12 (Data Leakage Prevention) is a broad requirement. To actually achieve it, you might map it to:
- CIS 3.3 (Configure Data Access Control Lists)
- CIS 3.13 (Deploy a Data Loss Prevention Solution)
- CIS 3.14 (Log Sensitive Data Access)
The Role of Mapping in Information Assurance
Mapping creates a chain of custody for security.
- Risk: We might lose customer data.
- ISO Policy: We must prevent data leakage (A.8.12).
- CIS Safeguard: We deploy DLP agents (CIS 3.13).
- Evidence: Here is the screenshot of the DLP console showing active agents.
When an auditor or a buyer follows this chain, assurance is absolute. There is no ambiguity.
Common Misunderstandings
Teams often think mapping means "compliance is done." It is not. Mapping is just the plan. You still have to do the work. Another misunderstanding is that the mapping is 1:1. It rarely is. It is usually one-to-many or many-to-many.
Why Enterprises Expect ISO 27001 Controls Mapped To CIS
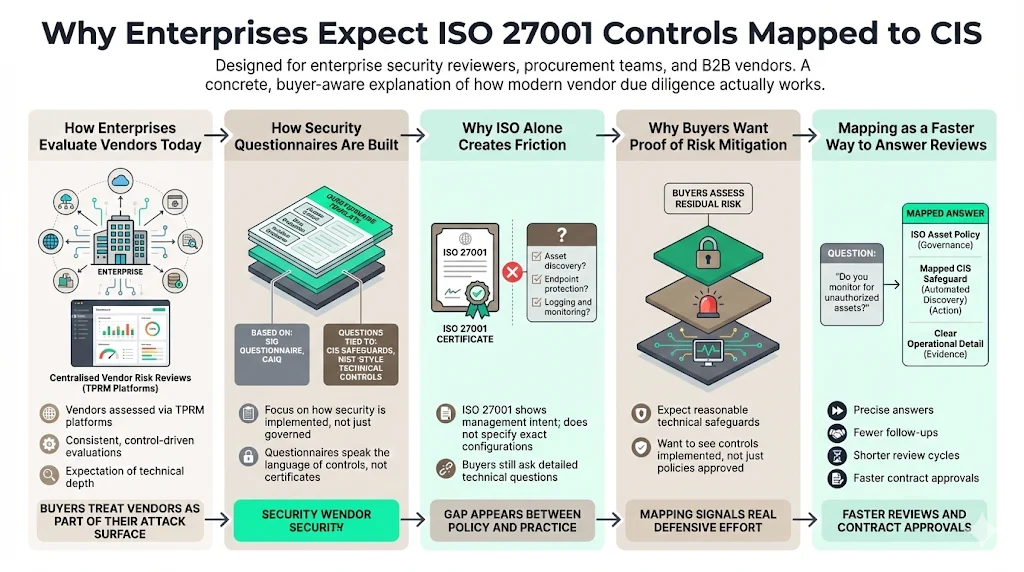
If you are selling a B2B SaaS platform, a healthcare application, or an enterprise tool, your customers are likely using a Third-Party Risk Management (TPRM) tool like OneTrust, Whistic, or Vanta.
How Enterprise Security Questionnaires Are Structured
These questionnaires rely on the Standardized Information Gathering (SIG) questionnaire or the CAIQ (Consensus Assessments Initiative Questionnaire). These industry-standard templates are built on specific controls, heavily influenced by CIS and NIST.
If you only speak "ISO," you will struggle to answer questions that ask about specific technical implementations found in CIS.
Why Buyers Want Proof of Risk Mitigation
Buyers are looking for residual risk. They know no system is unhackable. They want to know that you have applied reasonable technical measures to make a hack difficult.
A certificate says "we check our homework." A mapping to CIS says "we have locked the doors, barred the windows, and set the alarm." The latter is what lowers the buyer's anxiety.
Mapping as a Faster Way to Answer Reviews
When you have ISO 27001 Controls Mapped To CIS, you can pre-fill security questionnaires with precision.
- Question: Do you use automated tools to monitor for unauthorized assets?
- Answer: Yes. As per our Asset Management Policy (ISO A.5.9), we utilize automated active discovery (CIS 1.1) running weekly scans.
This level of detail signals competence. It stops the back-and-forth clarification emails that delay contract signatures by weeks.
Which CIS Version Aligns With ISO/IEC 27001:2022?
The security industry moves fast. Using outdated versions of standards renders your mapping useless.
Overview of ISO/IEC 27001:2022 Updates
The 2022 update of ISO 27001 was significant. It modernized the controls, merging 114 controls down to 93 and introducing 11 new ones, including:
- Threat Intelligence
- Information Security for Cloud Services
- ICT Readiness for Business Continuity
- Physical Security Monitoring
- Configuration Management
- Information Deletion
- Data Masking
- Data Leakage Prevention
- Monitoring Activities
- Web Filtering
- Secure Coding
Why CIS Controls v8 is the Reference Point
CIS Controls v8 is the current standard, designed specifically to handle modern environments—cloud, mobile, and remote work. Previous versions (v7) focused heavily on network perimeter defense, which is less relevant in a SaaS-first world.
Core Alignment Themes
- Asset Management: ISO A.5.9 requires an inventory. CIS 1 and 2 provide the rigorous technical requirements for hardware and software inventory.
- Access Control: ISO A.5.15 requires access control rules. CIS 5 and 6 provide the specifics on account management and access control management.
- Incident Response: ISO A.5.24 requires planning for incidents. CIS 17 dictates the tactical steps for incident handling.
- Continuous Monitoring: ISO A.8.16 requires monitoring activities. CIS 13 (Network Monitoring) and CIS 8 (Audit Log Management) provide the "how."
High-Level Mapping Overview: ISO 27001 Annex A to CIS Controls
While a full spreadsheet is too large for this article, understanding the logical grouping is essential for building your program.
How Annex A Groups Map to CIS
Why Mapping Is Rarely One-to-One
Take ISO A.8.9 (Configuration Management). This simple line in ISO requires you to manage configurations. In CIS, this touches almost everything:
- CIS 4 (Secure configuration of assets)
- CIS 5 (Account management configurations)
- CIS 7 (Vulnerability management)
You must map the intent of the ISO control to every technical area where that intent is executed.
Practical Benefits for Companies Selling to Enterprise Clients
Implementing ISO 27001 Controls Mapped To CIS is not just an academic exercise for your compliance team. It is a sales enablement tool.
Faster Enterprise Security Reviews
We have seen Konfirmity clients reduce the time spent on security reviews by 75%. When you have a mapping, you can often provide a "standard response package" that satisfies 90% of buyer questions immediately. Instead of hunting for answers, your sales engineering team hands over a pre-validated document.
Clearer Answers During Audits
External auditors love mapping. It makes their job easier. If you can show an ISO auditor exactly how you satisfy a requirement using a CIS benchmark report, you reduce the likelihood of a non-conformity. You are speaking their language of evidence.
Less Duplication Across Standards
If you aim for SOC 2, HIPAA, or GDPR later, the CIS Controls serve as a universal translator. Most frameworks map back to CIS. By anchoring your ISO program to CIS now, you are pre-building your SOC 2 technical evidence.
Better Internal Coordination
The biggest friction point in compliance is between the CISO/GRC lead and the DevOps team. DevOps hates vague policy requirements. They love clear technical specs. Mapping ISO to CIS translates "Policy" into "Jira Tickets."
Common Mapping Challenges and How Teams Handle Them

Despite the benefits, mapping is difficult work. It requires deep knowledge of both frameworks.
Control Overlap Confusion
Sometimes, three different ISO controls seem to point to the same CIS safeguard. This is normal. It is better to map a CIS safeguard to multiple ISO controls than to miss a connection.
Different Wording for Similar Safeguards
ISO uses terms like "information processing facilities." CIS uses "enterprise assets." You must look past the terminology to the underlying object (servers, laptops, clouds).
Over-Documentation Slowing Teams Down
Do not create a map that is so complex it requires a PhD to read. Keep it operational. Use a simple tagging system in your GRC tool or spreadsheet.
Keeping Mappings Usable
A map that sits in a PDF on a SharePoint drive is useless. The mapping should live where the work happens—in your ticketing system or your continuous monitoring dashboard.
How to Build and Maintain an ISO 27001 to CIS Mapping

Building this requires a deliberate process. This is the methodology we use at Konfirmity when implementing managed security programs.
1. Start with Existing ISO 27001 Controls
Take your Statement of Applicability (SoA). This is your list of ISO controls that apply to your business. This is your "Scope."
2. Map to CIS Controls v8 Safeguards
Go through your SoA line by line. For each control, ask: "What technical action makes this true?" Look for that action in the CIS v8 list.
- Example: ISO requires backup (A.8.13). CIS 11 covers Data Recovery. Map them.
3. Document Rationale, Not Just References
Don't just write "CIS 11." Write "We satisfy ISO A.8.13 by implementing automated daily snapshots (CIS 11.2) utilizing AWS Backup."
4. Assign Ownership
Who owns the CIS side? Usually, it is a specific engineer or the VP of Engineering. Ensure they know that their daily work (backups) is satisfying a legal requirement (ISO).
5. Tie Mapping to Risk Mitigation
If a CIS control fails (e.g., backups fail), flag it as a risk to the ISO certification. This connects operations to governance.
Is CIS Mapping Mandatory for ISO 27001 Compliance?
This is a frequent question.
The direct answer is no. ISO 27001 does not mandate that you use CIS Controls. You are free to design your own controls or use NIST SP 800-53, or COBIT.
However, the business answer is yes. While the auditor might not demand it, your customer effectively does. Enterprise buyers respect CIS. It is the de facto standard for technical due diligence.
If you choose not to map ISO 27001 Controls Mapped To CIS, you are choosing to invent your own framework. That means every time a buyer asks a question, you have to explain your unique, custom logic. That is slow. Using CIS is utilizing a standard shorthand that everyone understands.
How Often Should Control Mappings Be Reviewed?
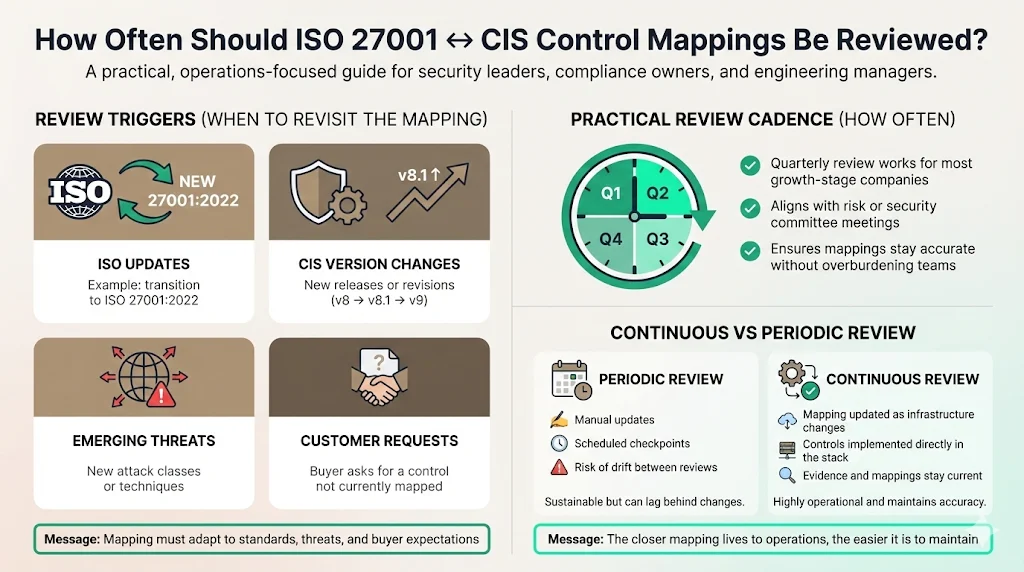
Security is not static. Your mapping cannot be static either.
Review Triggers
You should review your mapping when:
- ISO Updates: Like the shift to the 2022 version.
- CIS Version Changes: When CIS moves from v8 to v8.1 or v9.
- New Threats: If a new class of attack emerges (like AI-driven social engineering), check if your current mapping covers it.
- Customer Requests: If a key customer asks for a control you don't have, map it and add it.
Practical Review Cadence
For most growth-stage companies, a quarterly review is sufficient. This aligns with standard risk committee meetings.
At Konfirmity, we handle this continuously as part of our managed service. Because we implement the controls inside your stack, we update the mapping in real-time as your infrastructure changes.
Conclusion
The goal of security is not to produce paperwork; it is to protect the business and enable revenue.
By establishing ISO 27001 Controls Mapped To CIS, you move your organization out of the reactive cycle of "audit panic" and into a state of continuous readiness. You demonstrate to enterprise buyers that you understand the details of defense.
This approach transforms security from a cost center into a competitive advantage. When your competitor is struggling to explain their patching policy, you are providing automated evidence of patch SLAs.
However, building and maintaining this map takes time and expertise. It requires translating between legal requirements and engineering realities.
This is where Konfirmity fits in.
We are not a GRC software tool that gives you a blank template and wishes you luck. We are a human-led, outcome-driven managed service. We don't just advise you on the mapping; we execute the controls.
- Self-Managed: Typically requires 550–600 internal hours per year to maintain ISO/CIS alignment and evidence.
- With Konfirmity: We reduce your internal effort to approximately 75 hours per year.
We implement the controls, monitor the evidence, and handle the mapping updates. We ensure you are audit-ready year-round, so you can focus on building your product while we handle the proof that sells it.
Security that looks good in documents but fails under incident pressure is a liability. Build controls that stand up to buyers, auditors, and attackers.
Frequently Asked Questions
1) What is control mapping between ISO 27001 and CIS?
Control mapping is the process of linking the governance policies of ISO 27001 (e.g., "We shall manage access") to the specific technical safeguards of CIS Controls (e.g., "Use MFA"). It creates a clear path from policy to evidence.
2) Why do enterprises map ISO 27001 to CIS Controls?
Enterprises map ISO 27001 Controls Mapped To CIS to prove operational security. Buyers want assurance that policies are technically enforced. Mapping provides the granular evidence required for procurement and risk reviews.
3) Which CIS version aligns with ISO/IEC 27001:2022?
CIS Controls v8 is the best alignment for ISO/IEC 27001:2022. Both are modernized for cloud, remote work, and current threat environments.
4) Is CIS mapping mandatory for ISO 27001 compliance?
No, it is optional for the certification itself. However, it is highly recommended for operational efficiency and is often expected by enterprise procurement teams during due diligence.
5) How often should control mappings be reviewed?
Mappings should be reviewed at least annually, or quarterly if your infrastructure changes frequently. Triggers include updates to the ISO or CIS standards, or significant changes to your tech stack.





.svg)






.svg)
.svg)