Data lakes have become central to enterprise strategies because they can store enormous volumes of information from many sources. Social media interactions, IoT telemetry, log files and transaction records pour into organisations at high speed. A data lake absorbs this volume, variety and velocity by accepting raw data in its original format. SAS defines a data lake as a storage repository that rapidly ingests large amounts of raw data in its native format. Business users and data scientists can access this information quickly and apply analytics.
But flexibility brings risk. When sensitive personal data, intellectual property or compliance evidence is stored in one place, the attack surface grows. Poorly controlled data lakes become single points of failure: a compromised account or misconfigured bucket could expose hundreds of gigabytes of restricted information. Privacy laws such as the EU GDPR and India’s Digital Personal Data Protection Act impose large penalties for mishandling personal data. Regulators and customers expect evidence that security controls are operational, not just promises written in policies.
The solution is to combine a modern data‑lake platform with the structured discipline of ISO/IEC 27001:2022. ISO 27001 is the leading standard for information security management systems (ISMS). It helps organisations identify, assess and treat information security risks. Annex A lists 93 controls grouped into four themes—organisational, people, physical and technological. The 2022 revision introduced controls for cloud services, threat intelligence, secure coding and data leakage prevention (DLP). Control A.8.12 explicitly requires data leakage prevention measures for systems processing sensitive data.
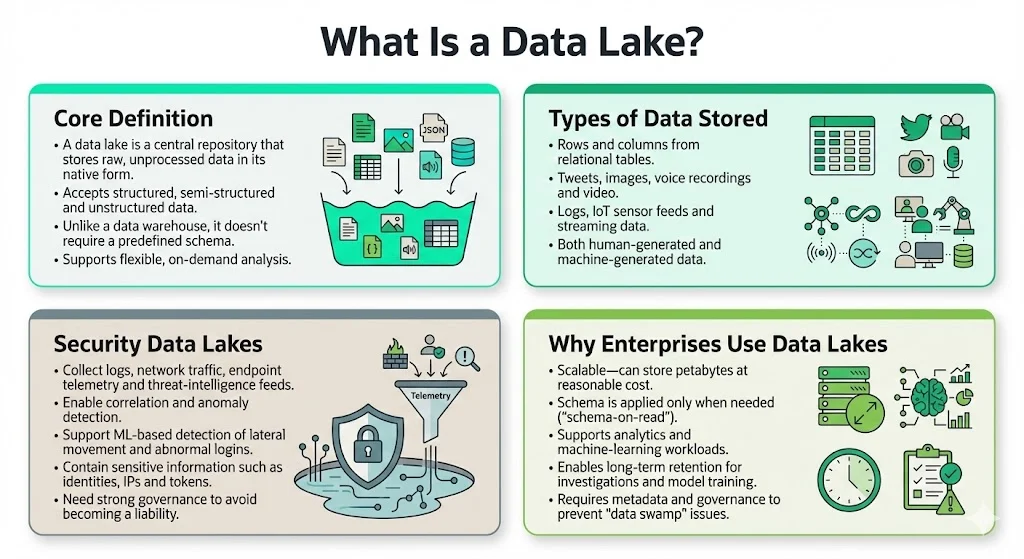
What Is a Data Lake?
A data lake is a central repository that stores raw, unprocessed data in its native format. Unlike a data warehouse, which imposes a predefined structure, a data lake accepts structured, semi‑structured and unstructured data. SAS explains that a data lake is ideal for storing unstructured big data like tweets, images, voice and streaming data, and can also store rows and columns from relational tables. Formats range from delimited text files to social media posts and IoT sensor readings. By retaining data until it is needed, a lake supports exploratory analysis, machine‑learning training and long‑term retention.
Security teams also build “security data lakes” that collect logs, network traffic, endpoint telemetry and threat‑intelligence feeds. These repositories enable correlation and anomaly detection across varied sources. Machine‑learning models can detect lateral movement, unusual login patterns or emerging threats. However, they also contain sensitive information: user identities, IP addresses, access tokens and potential evidence of intrusions. Without strong governance, a security data lake can quickly become a liability.
Enterprises adopt data lakes for several reasons. They scale horizontally to store petabytes of data at a reasonable cost. They offer flexibility because data is stored before any schema is applied. They support analytics and machine learning by providing self‑service access for data scientists. Finally, they support long‑term retention—a requirement for forensic investigations and model training. The challenge is to keep the lake usable and secure, not a chaotic “data swamp,” which early implementations became when metadata and governance were ignored.
What Is ISO/IEC 27001 and Why It Matters
ISO/IEC 27001 is a global standard that defines requirements for an information security management system. Organisations implement an ISMS to identify, assess and mitigate information security risks, to protect confidentiality, integrity and availability of information. Annex A lists 93 controls grouped into four categories—organisational, people, physical and technological. The standard requires a Statement of Applicability (SoA) explaining which controls apply and why.
ISO 27001 is not tied to any industry. Financial services, healthcare, technology and public-sector organisations can all use the same framework. Certification signals to customers and regulators that security practices are structured and risk‑based. The 2022 revision introduced updated controls to address cloud environments, remote workforces, decentralised identity and new threats. Importantly, control A.8.12 mandates data leakage prevention for systems processing sensitive information. Organisations certified under ISO 27001:2013 must transition to the 2022 edition by 31 October 2025.
Why Combining Data Lake and ISO 27001 Makes Sense
A data lake concentrates vast and diverse data sets, many of which are sensitive. The average cost of a data breach reached USD 4.88 million in 2024, a 10% increase over the previous year. Attackers often remain undetected for months; IBM found that organisations took an average of 194 days to identify and 64 days to contain a breach. An unsecured data lake could allow attackers to view or exfiltrate data during this dwell time.
ISO 27001 provides a structured approach to risk management across people, processes and technology. When applied to a data lake it ensures that ingestion sources are authorised, data is classified, access is controlled, logs are collected and incidents are handled systematically. Combining Data Lake And ISO 27001 mitigates risk by identifying vulnerable ingestion paths and enforcing encryption, DLP and access reviews, aligns with privacy laws such as GDPR and HIPAA for compliance readiness, clarifies ownership through classification and ultimately builds client trust by shortening procurement cycles. At Konfirmity we typically reduce internal effort from hundreds of hours to around 75 hours per year and help clients reach audit readiness in four to five months instead of nine to twelve months when self‑managing.
A security data lake also becomes a hub for compliance data—logs of access reviews, network traffic and identity events feed into the lake. When this data is secured under an ISMS, it supports continuous monitoring and audit readiness.
Mapping ISO 27001 to Data‑Lake Security
This section explains how the main parts of ISO 27001 align with data‑lake security. Each subsection summarises the requirement and offers practical suggestions.
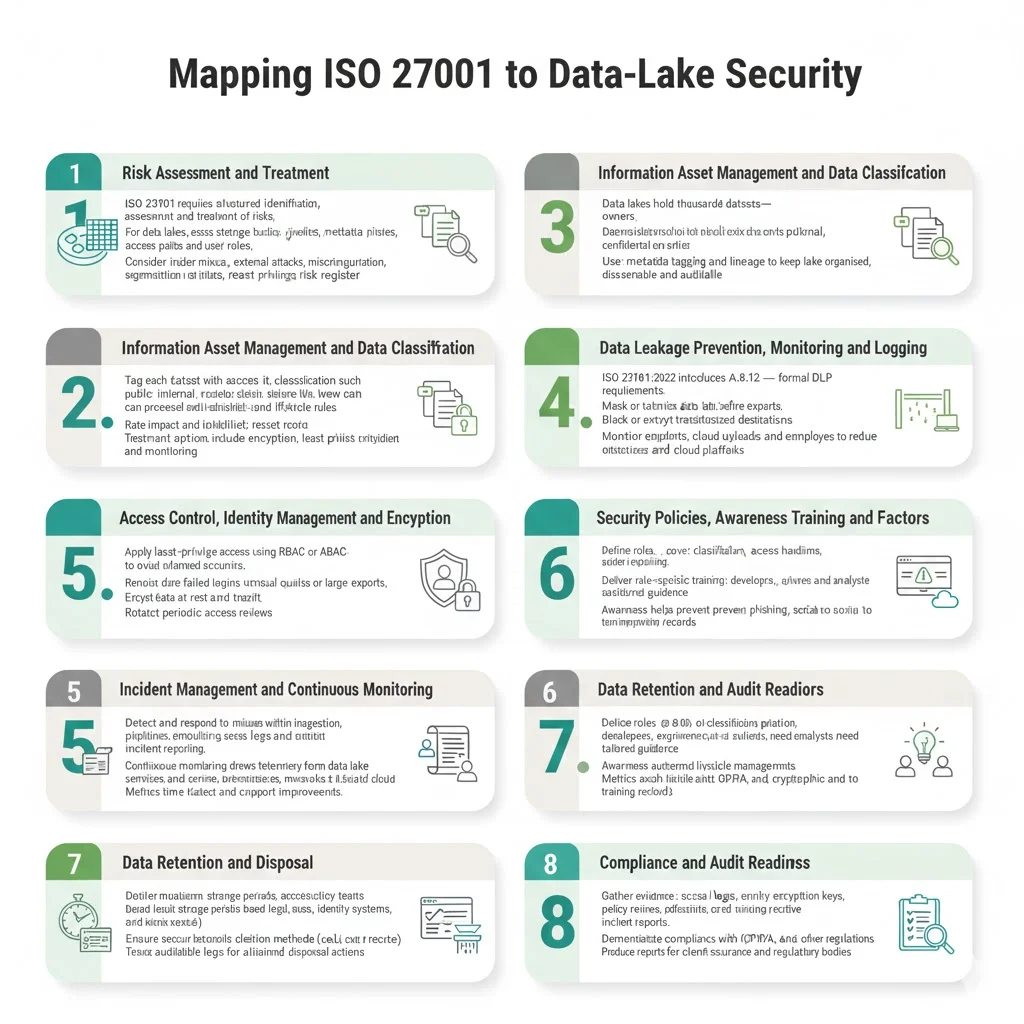
Risk Assessment and Treatment
ISO 27001 requires organisations to systematically identify, assess and treat information security risks. The NIST guide on risk assessments notes that assessments provide senior leaders with information to determine appropriate action. For a data lake, risk assessment must cover ingestion pipelines, storage buckets, access paths, metadata repositories and user roles. Threats include insider misuse, external attacks and misconfiguration. The assessment should rate the impact and likelihood of each threat. Treatment strategies may include encryption, segmentation, least‑privilege access and monitoring. A living risk register records threats, vulnerabilities, risk ratings and treatment plans and provides evidence to auditors.
Information Asset Management and Data Classification
Data lakes contain thousands of objects and datasets. ISO 27001 requires organisations to catalogue these assets and assign owners. IT Governance notes that organisational controls include asset management and classification. Each dataset should be tagged with a classification—public, internal, confidential or restricted—based on sensitivity and compliance requirements. Governance policies define who owns the data, who can access it, how it can be processed and when it must be retained or deleted. Metadata tagging and data lineage make the lake discoverable and auditable.
Access Control, Identity Management and Encryption
Controlling who can read or modify data in the lake is critical. ISO 27001 includes controls for identity management, authentication and cryptography. Organisations should implement least‑privilege access using role‑based or attribute‑based models. Provisioning and de‑provisioning should be automated to prevent orphaned accounts. Multi‑factor authentication is essential for administrative users. Encryption should protect data at rest and in transit. Keys must be managed and rotated. Regular access reviews ensure that permissions remain appropriate.
Data Leakage Prevention, Monitoring and Logging
The 2022 revision of ISO 27001 introduced control A.8.12, which explicitly requires data leakage prevention measures. Endpoint Protector notes that the new control formalises DLP and requires organisations to monitor and block unauthorised exfiltration. A DLP strategy for the data lake includes scanning for sensitive patterns at ingestion, enforcing masking or tokenisation for exports, and blocking or encrypting transfers to unauthorised destinations. Logs must record every access, query and modification. Logging supports forensic investigations and demonstrates compliance. Because most data leaks result from employee misuse, monitoring must cover endpoints, cloud uploads, messaging apps and removable media.
Incident Management and Continuous Monitoring
ISO 27001 requires processes to detect, respond and recover from security incidents. In a data‑lake environment, incident management includes monitoring ingestion pipelines, access logs and system health for signs of misuse. Metrics such as failed login attempts, unusual query patterns or large data exports should trigger investigation. Organisations need runbooks with defined roles, escalation paths and communication channels. Continuous monitoring feeds telemetry from the data lake, identity provider, network devices and cloud services into analytics systems. Metrics like time to detect and time to contain incidents support continual improvement.
Security Policies, Awareness Training and Human Factors
Technology alone cannot secure a data lake. ISO 27001 emphasises human controls. Policies must cover data classification, access, handling, retention, acceptable use, incident reporting, DLP procedures and access reviews. Roles and responsibilities should be documented—data owners, custodians, security officers and compliance contacts. Training ensures that staff understand how to handle data properly, recognise phishing and social‑engineering attempts, and report incidents. Training should be role‑specific: developers need secure coding guidance, data engineers need to understand raw data handling, and analysts must know how to interpret classification tags. Policy acknowledgement and record keeping demonstrate compliance.
Practical Walkthrough and Template Structure
Implementing Data Lake And ISO 27001 requires clear documentation. The following outlines describe documents that organisations can tailor.
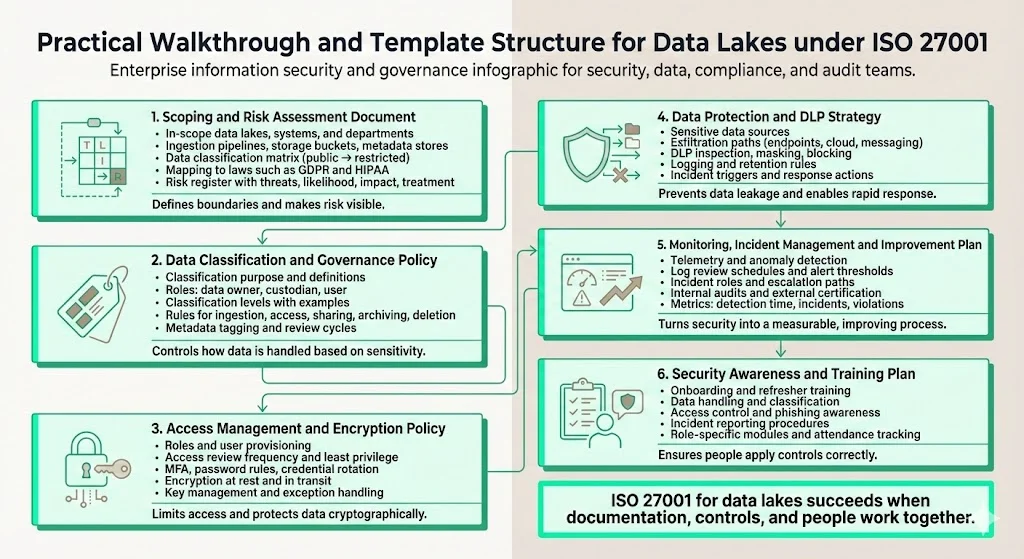
Scoping and Risk Assessment Document
Define which data lakes, systems and departments fall under the ISMS. List all ingestion pipelines, storage buckets and metadata stores. Create a data‑classification matrix with categories such as public, internal, confidential and restricted, and map relevant laws like GDPR and HIPAA. Maintain a risk register that records threats, vulnerabilities, impact, likelihood, risk ratings and treatment plans. Update this register regularly.
Data Classification and Governance Policy
Describe the purpose of classification and define terms like data lake, data owner, custodian, sensitive data and retention. Define classification levels and criteria, provide examples and map responsibilities. Describe how data can be ingested, stored, accessed, transformed, shared, archived or deleted based on its classification. Include metadata tagging requirements and review intervals.
Access Management and Encryption Policy
Define roles, user‑provisioning procedures, access review frequency and least‑privilege principles. Specify multi‑factor authentication, password policies and credential rotation. Describe encryption at rest and in transit, key management and rotation. Outline how users request and obtain access and how exceptions are handled.
Data Protection and DLP Strategy
Identify sensitive data sources and potential exfiltration channels such as endpoints, cloud uploads and messaging apps. Describe DLP tools for content inspection, pattern matching, masking and blocking. Specify which events are logged and how long logs are retained. Define triggers for incident investigation and outline escalation and remediation steps.
Monitoring, Incident Management and Improvement Plan
Define which telemetry is collected and how anomalies are detected. Establish a schedule for reviewing logs and define alert thresholds. Describe incident response roles, escalation paths and communication channels. Schedule internal audits and external certifications. Define metrics such as number of incidents, time to detect and contain, number of access violations and remediation time. Use these metrics to guide improvement.
Security Awareness and Training Plan
Outline onboarding and periodic training. Cover topics such as data classification, secure data handling, access control, phishing risks and incident reporting. Provide specialised modules for developers, data engineers and administrators. Require policy acknowledgement and track attendance.
Challenges and How to Address Them
Large data lakes introduce challenges. The scale and complexity of data make manual classification and access management impractical. Automated tagging and policy‑based frameworks can apply controls based on sensitivity. Many departments need access to different subsets of the lake; role‑based or attribute‑based models with just‑in‑time credentials meet this need.
Encryption, DLP scanning and logging may affect performance. Organisations can encrypt only sensitive partitions or use tiered storage and asynchronous logging. Security policies can appear burdensome, so they must be integrated into development pipelines and supported with clear training. Finally, maintaining audit‑ready documentation requires automation: evidence collection for access reviews, vulnerability scans and backups should be continuous, and change logs should track policy updates.
Why This Matters for Companies Selling to Enterprise Clients
Enterprise buyers evaluate vendors rigorously. Procurement questionnaires, business associate agreements and security addenda ask for risk assessments, statements of applicability, penetration test results, access review logs and DLP evidence. Vendors with a credible ISMS avoid delays. Combining Data Lake And ISO 27001 demonstrates that security and governance are built into the product.
Based on Konfirmity’s experience, vendors who adopt this approach enjoy shorter sales cycles and increased trust. They reduce internal effort because a managed service collects evidence continuously. They lower liability, as documented controls show due diligence. They build long‑term customer relationships by demonstrating transparency and improvement. In competitive markets, security posture often makes the difference between winning and losing deals.
Conclusion
Data lakes offer scale and flexibility but concentrate risk. ISO/IEC 27001 provides a structured way to manage that risk through risk assessment, classification, access control, DLP, monitoring and training. Combining Data Lake And ISO 27001 produces a secure platform for analytics and machine learning. This is not merely a compliance exercise; it is a strategic investment in trust and sustainability. Human‑led managed services like Konfirmity’s help organisations implement controls, monitor continuously and maintain audit readiness. As data continues to grow, those who build secure data platforms will be better positioned to meet regulatory demands and win customer trust. When you invest in people, processes and tools together, you create a secure environment where innovation and compliance can thrive for years. Start with security and let compliance follow.
Frequently Asked Questions
1. What are the four categories of ISO 27001?
ISO 27001:2022 groups its 93 Annex A controls into four categories: organisational, people, physical and technological. Organisational controls cover policies, responsibilities and management processes; people controls include pre‑employment screening and training; physical controls protect the physical environment; technological controls include malware protection, backups, logging, network security and development practices.
2. What is a data lake in cyber security?
A data lake is a central repository that stores large volumes of raw data in its native format. In cyber‑security contexts, a “security data lake” aggregates logs, network traffic, alerts and endpoint telemetry. SAS notes that a data lake rapidly ingests raw data and allows business users and data scientists to access it. Security teams use these repositories for threat detection, anomaly analysis and long‑term retention. Because they contain sensitive information, they must be secured with classification, access control, encryption and DLP.
3. Does ISO 27001 require data leakage prevention?
Yes. ISO 27001:2022 introduced control A.8.12, which requires organisations to implement data leakage prevention measures across systems, networks and devices handling sensitive data. The update formalises DLP as a requirement and organisations must adopt these controls by 31 October 2025.
4. What is the official name of ISO 27001?
The full title is “ISO/IEC 27001:2022—Information security, cybersecurity and privacy protection—Information security management systems—Requirements.” Most people refer to it simply as ISO 27001.





.svg)






.svg)
.svg)