Today’s enterprise buyers want proof that vendors can protect information and comply with global regulations before they purchase. They routinely send security questionnaires, insist on detailed data‑processing agreements, and scrutinise third‑party risk. Sellers who rely on a last‑minute audit risk losing deals or incurring costly remediation. In 2025 the global average data‑breach cost reached $4.44 million and U.S. breaches averaged $10.22 million, with 68% of incidents linked to human error or phishing. Healthcare providers must also follow the HIPAA Security Rule, which requires administrative, physical, and technical safeguards to protect electronic health information. Cross‑border transfers add more complexity: the UK’s Data (Use and Access) Act 2025 introduces a risk‑based test for moving data overseas. Against this backdrop, the standards ISO 27001 Data Residency and ISO 27002 provide a structure for proving that data is protected wherever it resides. This article discusses why enterprise clients care, how to map controls effectively, and how a human‑led service like Konfirmity helps organisations stay ready for audits.
Why Enterprise Clients Demand Security and Compliance
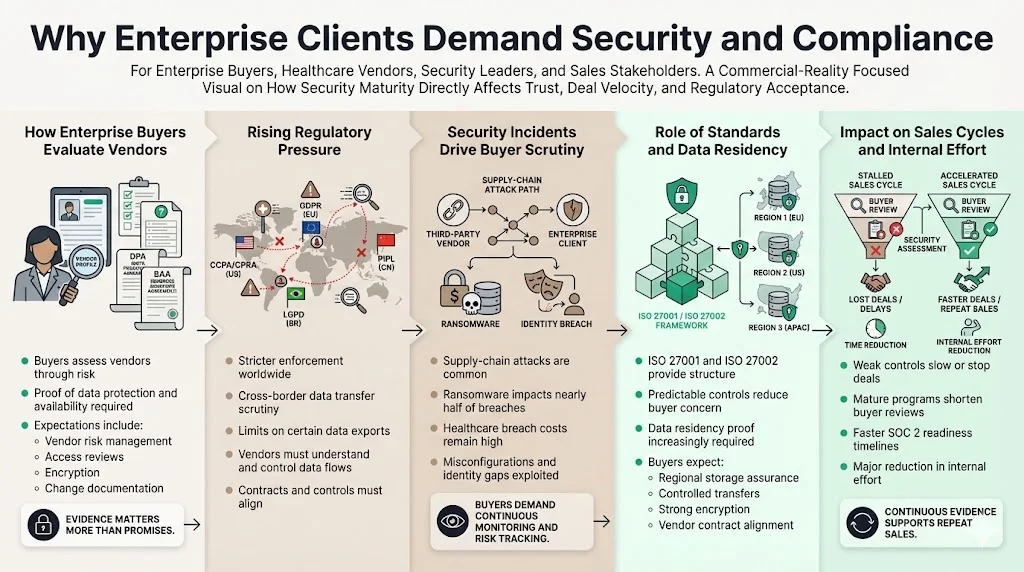
Enterprise and healthcare buyers look at vendors through a risk lens. They ask for proof of data protection, availability, and compliance via questionnaires, DPAs, and BAAs. Buyers expect vendors to manage vendor risk, conduct access reviews, encrypt sensitive data, and document change management. Regulators are becoming stricter: the EU–US Data Privacy Framework is under scrutiny, European regulators have raised fines for unlawful transfers, and the Protecting Americans’ Data from Foreign Adversaries Act limits certain exports. Vendors must therefore show they understand cross‑border data flows and have controls to manage them.
Security incidents amplify this scrutiny. In 2025 supply‑chain attacks caused about 30% of breaches and ransomware appeared in 44% of cases. Healthcare breaches cost roughly $7.42 million on average. Attackers exploit misconfiguration and identity gaps, so buyers want evidence of continuous monitoring, risk assessment, and up‑to‑date documentation. ISO 27001 and ISO 27002 provide a framework for that.
Programmes focused on ISO 27001 Data Residency emphasise another buyer demand: proof that personal and regulated data stays within approved regions. Buyers want to see not only where data is stored but also that transfer mechanisms, encryption, and vendor contracts are consistent with residency commitments.
Based on more than 6,000 audits, Konfirmity sees how security maturity influences sales cycles. Without implemented controls and continuous evidence, deals stall. With a managed security program, vendors can answer buyer questionnaires quickly and demonstrate a predictable control environment. Clients typically achieve SOC 2 Type II readiness in 4–5 months, compared with 9–12 months when organisations manage the process alone. Internal effort drops from 550–600 hours to roughly 75 hours, because our experts implement controls, collect evidence, and monitor continuously.
What Is ISO 27001?
ISO 27001 defines the requirements for an information security management system (ISMS). It is a process‑driven standard that guides organisations through scoping, risk assessment, control implementation, internal audits, and continual improvement. Clauses 4–10 set out mandatory elements such as context, leadership, planning, support, operation, evaluation, and improvement.
The 2022 update reduced the number of controls from 114 to 93 and reorganised them into four themes—Organisational, People, Physical, and Technological. Controls are no longer optional: if a control does not apply, the organisation must justify its exclusion and provide equivalent measures. The themes cover everything from policy and roles to training, secure areas, and technology such as encryption and system configuration. A 2024 amendment added an environmental‑sustainability consideration.
Clauses vs. Controls
In programs focusing on ISO 27001 Data Residency, the SoA must document where data resides and why each control applies.
Clauses specify what an ISMS must achieve, while controls describe how to achieve it. Clauses cover governance, resources, competence, communication, evaluation, and continual improvement. Annex A controls provide the mechanisms—such as asset management, access control, and cryptography—to meet those requirements. The Statement of Applicability (SoA) lists all controls, records whether each is applied, and explains exclusions based on the risk assessment.
What Is ISO 27002?
ISO 27002 is a code of practice that expands on the controls listed in Annex A. It is not certifiable. Instead, it explains how to implement each control effectively.
In the 2022 edition the guidance is grouped into the four themes of ISO 27001; each control now includes objectives, suggested practices, and attributes (such as preventive or detective type). These attributes help classify controls and understand dependencies. Certification bodies assess compliance against ISO 27001 but look to ISO 27002 as a benchmark for implementation quality.
Why Both Matter Together
ISO 27001 defines the ISMS framework, and ISO 27002 supplies the “how.” Using one without the other leads either to policy that lacks substance or to controls that lack context. Together they create a risk‑driven program that meets regulatory demands and produces evidence for auditors.
Our work shows that vendors who adopt both standards reduce findings and speed sales cycles. ISO 27001 Data Residency requires documenting where data is stored and how it flows. ISO 27002 provides guidance on encryption, data masking, and cross‑border transfer procedures. Mapping these controls to cloud services, endpoints, and vendor integrations enables automated evidence collection, so buyer questionnaires can be answered quickly and trust is maintained.
How ISO 27001 Controls and ISO 27002 Match Up
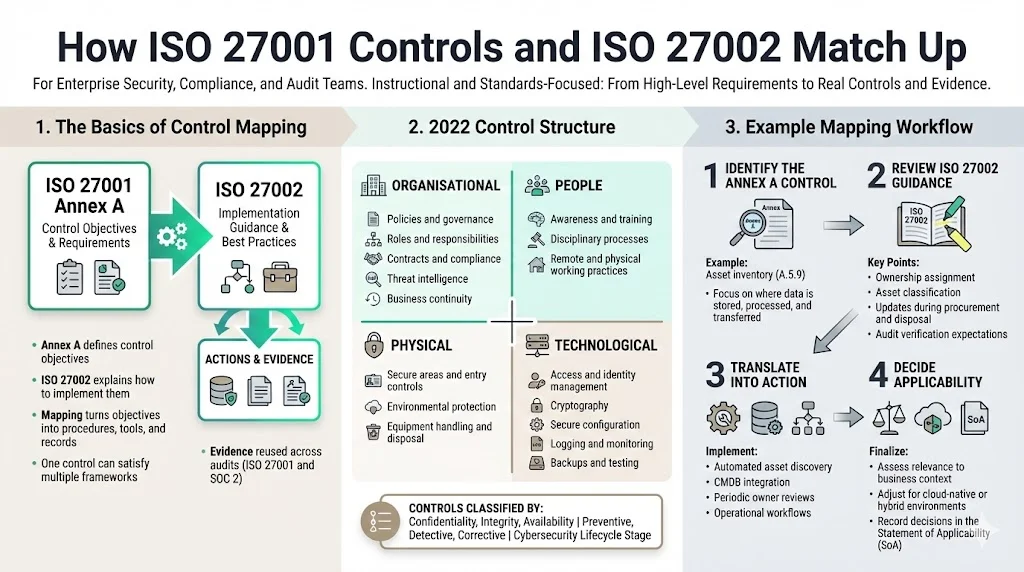
The Basics of Mapping
Mapping connects broad requirements from Annex A to the detailed guidance in ISO 27002. It helps teams turn control objectives into concrete procedures, technologies, and evidence. For example, the control for secure disposal of equipment becomes an asset inventory, media sanitisation, and documented disposal procedure. Mapping also simplifies cross‑framework compliance. Many Annex A controls correspond to SOC 2’s five Trust Services Criteria, which include 64 requirements. One access‑management control can satisfy both ISO 27001 and SOC 2. By mapping once, teams avoid duplication and reuse evidence across audits.
The Structure of Controls in the 2022 Versions
The 2022 versions of ISO 27001 and ISO 27002 reorganised controls into a streamlined structure. Annex A reduced the number of controls from 114 to 93 and grouped them into four themes. ISO 27002 mirrors this structure, providing guidance under the same themes. The organisational theme includes topics such as information security policy, roles and responsibilities, contractual obligations, threat intelligence, business continuity, and compliance. The people theme addresses awareness, training, disciplinary processes, and physical and remote working. The physical theme covers secure areas, entry controls, environmental protection, and equipment management. The technological theme includes access control, identity management, cryptography, secure configuration, log monitoring, backups, and testing. ISO 27002 describes attributes for each control, enabling organisations to classify them by security property (confidentiality, integrity, availability), type (preventive, detective, corrective), and the stage of the cybersecurity lifecycle.
Example Mapping Approach
A practical way to map controls involves four steps:
- Identify the Annex A control. For instance, control 6.4.1 covers asset inventory and requires documenting where data is stored, processed, and transferred.
- Read ISO 27002 guidance. It explains how to assign ownership, classify assets by sensitivity, update the inventory during procurement and disposal, and verify details during audits.
- Translate the guidance into action. Implement automated discovery tools, integrate them with a configuration management database, and require asset owners to review inventories periodically.
- Decide applicability. Assess whether each control is relevant to the organisation’s context. For example, a cloud‑native firm may only need physical disposal controls for endpoints. Record decisions and justifications in the SoA.
This process turns broad objectives into operational practices and yields evidence for audits.
Mapping in Practice
For organisations with ISO 27001 Data Residency obligations, mapping clarifies which controls protect data stored in specific jurisdictions or cloud regions.
Common Mapping Use Cases
Mapping controls supports several practical objectives:
- Integrating with risk management. ISO 27001 requires a risk assessment process; mapping allows organisations to connect each identified risk to specific controls. For example, a risk of unauthorized access to production databases may be mitigated through access reviews, multi‑factor authentication, and network segmentation.
- Matching information assurance with security controls. Assurance refers to the confidence that security measures are functioning as intended. By mapping, organisations can show that their controls protect confidentiality, integrity, and availability; that they are monitored; and that weaknesses trigger remediation.
- Turning broad policies into actionable practices. Policies often state general intentions—such as requiring backups or incident response—but do not specify who performs the task, when, and using which tool. Mapping ties each policy to a procedure, a tool, and evidence. For example, a backup policy becomes a scheduled job, a test restore procedure, and a documented report.
- Matching information assurance with business objectives. Assurance is not only about security; it is also about meeting SLAs and regulatory obligations. Mapping helps teams link control objectives to business outcomes, such as uptime commitments or data residency requirements, and ensures that operational metrics support those outcomes.
Benefits of Control Mapping
Control mapping offers three main benefits:
- Better coverage and clear ownership. Mapping surfaces gaps—such as missing logs or vendor risk assessments—and clarifies who owns each control, so responsibilities do not overlap.
- Faster incident response and maturity. When controls are tied to procedures and evidence, teams detect issues quickly and restore data promptly. Clients report that mapped controls cut the time to produce incident evidence by about 50%.
- Smoother audits and reviews. A mapped control set makes it easy for auditors to trace requirements to evidence, reducing follow‑up questions. Many organisations complete external audits 2–3 weeks faster with control mapping.
Tools and Templates to Help
Effective mapping depends on good documentation. A policy checklist lists each policy—such as access control, encryption, or vendor management—and points to the Annex A controls and ISO 27002 guidance it supports. Mapping matrices link Annex A controls with other frameworks (SOC 2, HIPAA, GDPR) and record the objective, implementation details, evidence location, owner, and associated risks. The Statement of Applicability explains which controls apply, why exclusions are justified, and references the policies, procedures, logs, and reports that prove implementation. At Konfirmity we provide templates for these documents and integrate them with monitoring tools so evidence is collected automatically and gaps are flagged.
Impact on Risk Management and Compliance
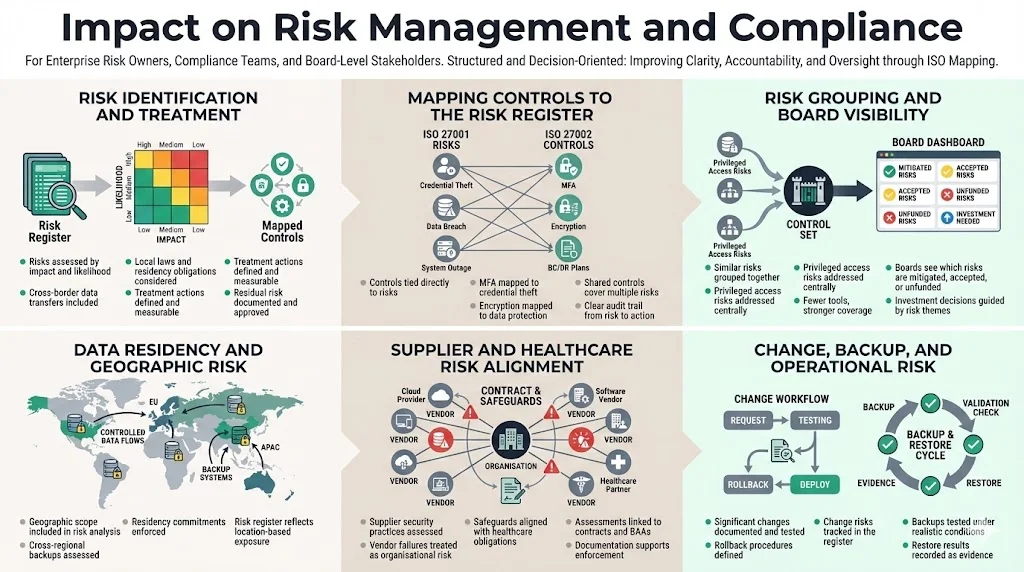
Risk treatment plans must consider cross‑border data transfers and local laws. ISO 27001 requires organisations to identify risks, assess their impact and likelihood, and decide how to mitigate them. ISO 27002 guides control selection—multi‑factor authentication to address credential theft or encryption to protect data at rest. Mapping these controls to the risk register ensures that treatment actions are measurable and that residual risks are acceptable. It also encourages grouping similar risks and addressing them with shared controls, simplifies reporting to boards, and helps auditors verify implementation.
In practice, grouping similar risks reduces complexity. Several risks related to privileged access—such as unauthorized database queries and misuse of administrative privileges—can be mitigated with one privileged access management platform and periodic reviews. Grouping controls by risk categories makes it easier for boards to see which risks are mitigated, accepted, or require investment. Under ISO 27001 Data Residency, groupings must also account for the geographic scope of data: cross‑regional backup systems must satisfy residency constraints, and the risk register should reflect that.
ISO 27002 offers practical insights to refine risk responses. It advocates irreversible masking techniques for production data used in testing and encourages classifying assets based on sensitivity. It also emphasises vendor risk management—assessing suppliers’ security practices and holding them liable for failures. In healthcare, HIPAA mandates that business associates implement safeguards equivalent to covered entities. Mapping ensures these assessments are documented and tied to contractual clauses.
Another useful insight relates to change management. ISO 27002 suggests documenting every significant change, testing it before deployment, and maintaining rollback procedures. Mapping this guidance into the risk register ensures that change‑related risks—such as downtime, data corruption, or security misconfiguration—are mitigated systematically. Similarly, the guidance on backup and restore emphasises not just performing backups but also regularly testing restore procedures under realistic conditions and documenting the results.
Audit Considerations
Auditors view ISO 27002 as the benchmark for control design. They expect evidence that controls were selected based on risk, that procedures match the guidance, and that exclusions are justified. During audits, they trace a control from the SoA to supporting documents and operational evidence. When mapping is thorough and evidence is organised by control, auditors ask fewer questions. Konfirmity clients typically see a 50–60% reduction in audit requests and fewer findings because gaps are found and fixed beforehand.
For example, an auditor assessing privileged access will start with the SoA entry for that control, read the risk assessment to understand why it applies, and then request the access‑control policy, evidence of periodic access reviews, logs showing multi‑factor authentication, and proof that users are removed promptly after termination. For backup controls, they will look for documented schedules, restore‑test reports, and alerts for failed backups. If mapping links each of these artefacts to the control, the evidence is readily at hand and the audit proceeds faster.
Common Audit Pitfalls and How to Avoid Them
Control mapping can be misapplied. Common pitfalls include:
- Policy–practice gaps. Stating that access reviews happen is insufficient; procedures, owners, and evidence must exist.
- Evidence collected only during the audit window. ISO 27001 demands continuous monitoring. Automated tools should gather logs, trigger alerts, and produce reports year‑round.
- Incomplete SoA documentation. Exclusions must be explained with risk justifications and compensating controls.
- Failure to update mapping after change. Cloud migrations, mergers, and new technologies require a fresh risk assessment and revised mapping. Neglecting this is a leading cause of findings.
Best Practices for Teams Mapping Controls
To succeed with programmes driven by ISO 27001 Data Residency and related standards:
- Engage cross‑functional teams. Security, operations, compliance, legal, and engineering should collaborate on control selection, mapping, and applicability decisions.
- Link requirements, guidance, risks, and artefacts. A good mapping matrix references the control objective, ISO 27002 guidance, the risk being treated, associated policies, procedures, and where evidence lives. This traceability simplifies audits.
- Update mapping when things change and use managed services. New cloud platforms, mergers, or major projects can shift the ISMS scope. Revisiting the risk assessment, SoA, and mapping matrix after such events keeps the program harmonised. Managed services like Konfirmity’s reduce the internal burden by implementing and operating controls, collecting evidence, and supporting audits year‑round.
In addition, teams should document rationale and acceptance. When a control is deemed not applicable, record the risk analysis and any compensating controls; this prevents future questions. Continuously monitoring controls—rather than only during an audit window—maintains readiness. A human‑led managed service can coordinate these tasks. Konfirmity’s dedicated experts work with clients’ engineers, product managers, and legal teams to design controls that fit the technology stack, automate evidence collection, and provide real‑time dashboards. This approach ensures that compliance follows naturally from sound security operations.
Conclusion
Security that looks good on paper but fails under incident pressure is a liability. Enterprise buyers and regulators expect vendors to implement controls that function every day, not just during an audit. In a world where data travels across jurisdictions and regulators impose divergent requirements, ISO 27001 Data Residency and ISO 27002 offer a way to manage complexity. Control mapping turns abstract requirements into concrete actions, reduces audit effort, and strengthens risk management. Organisations that invest in mapping, continuous monitoring, and managed services demonstrate to buyers, auditors, and themselves that they take data protection seriously.
At Konfirmity we start with security and arrive at compliance. Our human‑led, outcome‑as‑a‑service model builds and runs the entire program: defining the ISMS scope, implementing controls, automating evidence collection, and managing audits. We have supported more than 6,000 audits and bring over 25 years of combined expertise. Clients who adopt this approach not only pass ISO 27001, SOC 2, HIPAA, and GDPR audits; they also accelerate sales cycles, reduce findings, and improve resilience. Security is a daily practice, not a project. View mapping as a living document that should be updated as your technology, business, and regulatory context changes. By doing so, you can build a program that satisfies enterprise buyers and stands up to both auditors and attackers.
Frequently Asked Questions
1. What is the difference between ISO 27001 and ISO 27002?
ISO 27001 is a certifiable standard that defines the requirements for an information security management system and includes Annex A controls. ISO 27002 is a code of practice that provides detailed guidance on implementing those controls. ISO 27002 is not certifiable but supports ISO 27001 compliance.
2. Why is control mapping needed?
Mapping connects broad requirements to practical implementation steps. It ensures that controls address identified risks, reduces duplication, clarifies responsibilities, and supports audit readiness. Without mapping, policies may remain theoretical and auditors may find gaps.
3. Did ISO 27002 change in recent updates?
Yes. The 2022 update reorganised controls into four themes and reduced the total number from 114 to 93. It also introduced attributes to classify controls and help organisations plan their security architectures. An amendment in 2024 added environmental sustainability considerations.
4. How do auditors use ISO 27002?
Auditors refer to ISO 27002 to evaluate whether controls are designed and implemented properly. They check that controls selected in the Statement of Applicability correspond to risk assessments and that implementation follows ISO 27002 guidance. They also verify that controls operate effectively through evidence such as logs, reports, and test results.
5. Does mapping reduce audit effort?
Mapping can significantly reduce audit effort. When controls are mapped to requirements, risk assessments, and evidence, auditors can trace each requirement quickly. This reduces the number of questions and follow‑up requests. In Konfirmity’s experience, clients with mapped controls reduce audit requests by roughly 50–60% and complete audits weeks sooner.





.svg)





.svg)
.svg)