In today’s procurement cycles, security assurance drives deals. Many buyers won’t finalise contracts until they see proof that vendors keep sensitive information for the right period and destroy it when it is no longer needed. The average cost of a data breach reached $4.88 million in 2024, a 10 percent rise from the previous year. That figure underlines the financial risk of poor data handling. Large customers expect evidence that vendors can limit their attack surface.
This ISO 27001 Data Retention Guide addresses that challenge. It describes why retention matters, what ISO 27001 requires, and how to design a practical policy. The focus is on companies selling into regulated enterprises—teams facing high audit scrutiny. The article is organised into themed sections, with real examples and answers to common questions. The tone is direct and grounded in practice.
Why Data Retention Matters in an ISO 27001 Context
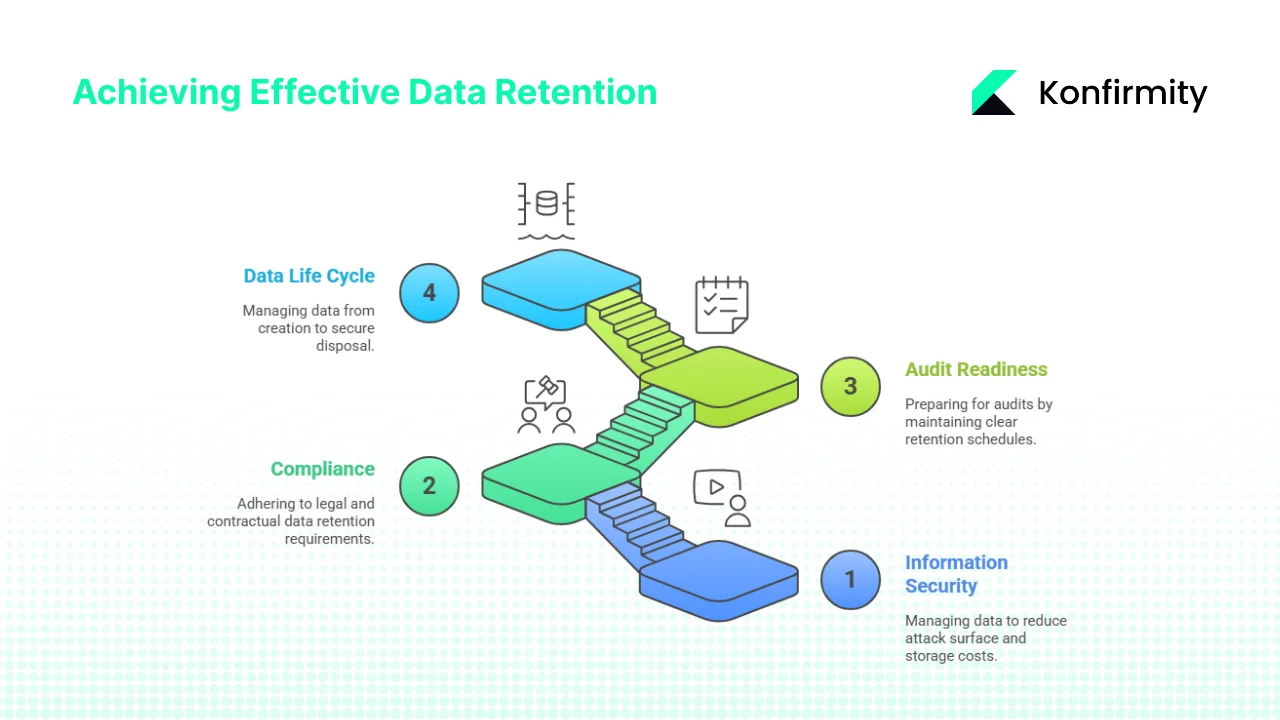
1) Information security and data management
Retention is not about hoarding information; it is about managing confidentiality, integrity, and availability. Every file you keep is part of your attack surface. Limiting how long you retain data reduces the volume an attacker can steal. A small‑business consultant summed it up well: “The less data you store, the less there is to steal. If cybercriminals breach your system and you’ve already deleted old customer data, they can’t steal what isn’t there”. Keeping unnecessary logs, emails, or backups increases storage costs and complicates incident response. On the other hand, deleting information too quickly can undermine your ability to investigate incidents or meet contractual obligations. A sound policy balances these concerns across the life cycle.
2) Compliance and regulatory requirements
Enterprise buyers operate under strict laws and expect their suppliers to match them. General data protection laws such as the GDPR, sector‑specific rules like HIPAA, and payment‑card standards all impose minimum retention or disposal requirements. Customer contracts may require you to retain certain documents for a defined period or destroy them on request. ISO 27001 does not specify those periods. Instead, control 5.33 of ISO/IEC 27002, the companion guidance to ISO 27001, tells organisations to create retention schedules based on legal, statutory, regulatory, and contractual obligations. You must justify the duration of each record type rather than rely on a one‑size‑fits‑all rule. A written schedule demonstrates audit readiness and builds trust with enterprise customers.
3) Audit readiness, risk management and incident response
Clear retention rules support incident response and risk management. When an incident occurs, your team must know what data exists, where it resides, and how long it will be kept. A defined schedule helps forensic teams gather evidence quickly and ensures crucial logs are not deleted prematurely. At the same time, disposing of outdated records reduces the volume of data that could be exposed in a breach and limits legal liability. ISO 27002 asks organisations to maintain a functional retention schedule and to destroy records safely when they are no longer required. Enforcing that schedule reduces the attack surface and shows auditors that your security programme is active rather than theoretical.
4) A data life‑cycle view
Retention sits within the broader information life cycle: creation, classification, storage, use, archiving, and secure disposal. Control 5.33 also addresses how records should be stored, handled, and destroyed. You need to track records from the moment they are created, assign ownership, ensure they are stored securely, decide how long they will be kept, and then dispose of them in a verifiable way. Thinking in terms of a life cycle ensures that you are not just reacting at the end, but managing data from start to finish.
Understanding ISO 27001 Requirements for Data Retention
ISO/IEC 27001:2022 sets the framework for information security management systems. It does not dictate retention periods; it requires you to document them. Its companion guidance ISO/IEC 27002:2022 contains control 5.33, “Protection of records”, which covers retention. The control states that organisations should:
- Publish guidelines for storing, handling, disposing of, and protecting records.
- Keep a schedule specifying how long each type of record is retained and why.
- Build procedures that consider laws, contracts, and societal expectations when storing and disposing of records.
- Destroy records safely once they are no longer needed.
- Classify records based on risk and type (such as accounting, personnel, or legal).
ISO 27001 expects you to integrate these requirements into your information security management system. That means defining retention rules for all information assets—electronic or paper—and documenting how you protect them during retention and how you destroy them when done.
What ISO 27001 expects from vendors
If you sell to large organisations, ISO 27001 expects you to define retention periods for each data type, justify them, and enforce them. You need secure storage and the ability to retrieve records for audits or investigations. Once retention ends, you must delete or destroy the data using secure methods and document the deletion. These rules apply to systems under your control, to backups, and to outsourced services. Assign roles such as Data Owner, Data Custodian, and Compliance Lead to ensure accountability. Without clear ownership, policies are rarely enforced.
Common misunderstandings
Many teams assume ISO 27001 mandates a universal period such as seven years. It does not. That common period comes from tax laws, which may require financial records to be kept for seven years. Others think posting a policy is enough; auditors expect evidence of implementation. Teams often forget about backups, archives, and third‑party systems. ISO 27002 reminds organisations to account for these and to maintain encryption keys and decryption software during the retention period. A retention policy that ignores old backups or outsourced services leaves compliance gaps.
Building a Retention Policy Consistent with ISO 27001
This section walks through the practical steps to design and enforce a policy that satisfies ISO 27001 and meets enterprise client expectations. The process draws on patterns from more than 6,000 audits and decades of experience with security frameworks. For each step, we explain what to do and why it matters.
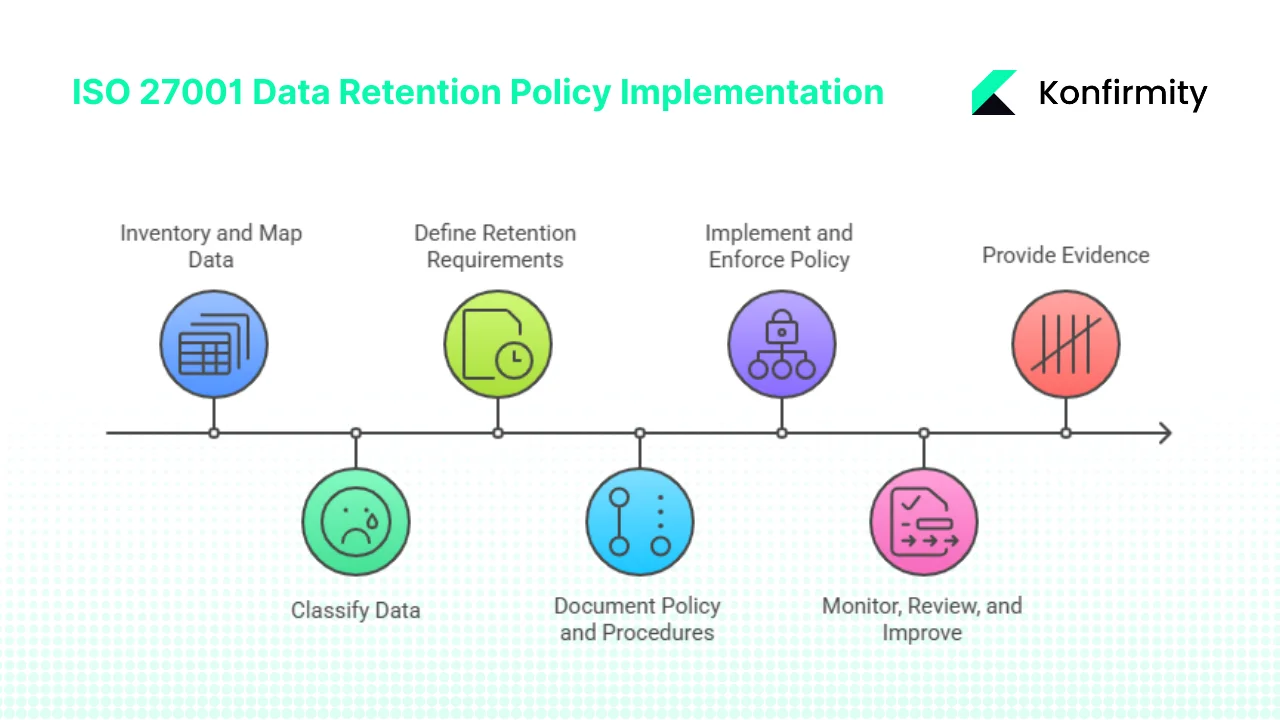
Step 1: Inventory and map your data
You can’t manage what you haven’t identified. Start by listing every type of data your organisation collects, processes, or stores. Map where it lives: on‑premises servers, cloud services, SaaS applications, backups, or archival systems. Document the owners of each data set and its business purpose. Typical categories include client contracts, personal data, system logs, and marketing analytics.
This inventory reveals hidden systems, duplicate data, and third‑party storage you may need to control. Without a complete map, classification and retention will be guesswork.
Step 2: Classify your data
Classification assigns sensitivity based on legal impact, regulatory obligations, and business value. A simple scheme might include three tiers: Confidential for customer personal information, trade secrets, and financial records; Internal use for operational information such as marketing analytics or internal metrics; and Public for information approved for public release. Set clear criteria for each tier. More sensitive data typically requires stronger protection and shorter retention once the business need ends.
Step 3: Define retention requirements per category
For each type of information and classification tier, define:
- Retention period: How long you will keep it. Periods vary: tax records may require seven years due to law; marketing unsubscribe logs may only need two years; customer personal data may be kept for the duration of the contract plus five years.
- Justification: The legal, contractual, or business reason for the period.
- Storage location and format: For example, encrypted archives, secure vaults, or cloud storage with regional restrictions.
- Disposal trigger and method: The event that ends the retention (such as contract termination plus a set number of years) and how you destroy the data (cryptographic deletion, secure overwriting, or cross‑cut shredding).
Use legal counsel to define the periods. Document the rationale so auditors can see that durations are not arbitrary. Below is a sample schedule to illustrate:
This table is only a starting point. Your actual schedule will depend on jurisdiction, contracts, and industry practices. What matters is that each entry has a documented period, rationale, storage method, and disposal plan.
Step 4: Document the policy and procedures
Your retention policy should be an official document within your information security management system. It should cover:
- Purpose and scope: Why the policy exists and which data it covers.
- Roles and responsibilities: Assign Data Owners, Custodians, Compliance Leads, and Internal Audit; define who approves classification and retention, who implements storage and deletion, and who reviews adherence.
- Classification scheme and schedule: Include the table above or its equivalent.
- Protection and disposal: How you secure data during retention—encryption, access controls, regional restrictions—and how you destroy it when the period ends.
- Review and exceptions: When the policy is reviewed and how exceptions are approved.
Supporting procedures should operationalise the policy. They include classification guidelines, disposal checklists, backup retention rules, and processes for collecting evidence for audits.
Step 5: Implement and enforce the policy
Assign roles and embed the schedule into your systems and workflows. Use automation to archive or delete data when periods expire, whether in cloud services or on‑premises systems. Include retention clauses in contracts and train staff so they understand classification and retention. Tools only work when people follow the processes.
Step 6: Monitor, review, and improve
A retention policy needs regular reviews. Audit your processes to verify that data is stored and disposed of according to the schedule, keep logs of classification and disposal events, and track metrics such as the number of overdue records. Update the policy when laws, contracts, or business processes change.
Step 7: Provide evidence to clients and auditors
Enterprise clients and auditors will ask for proof that you are following your policy. Maintain an evidence library with:
- Retention schedule and classification records: Provide the current schedule with rationale and approvals, along with proof that data sets have been categorised and assigned an owner.
- Disposal logs and proof of destruction: Maintain records showing when data was destroyed, who approved it, what method was used, and certificates that electronic data was irreversibly erased or physical records were shredded. ISO 27002 emphasises safe destruction once the period ends.
- Retrieval capability: Demonstrate that you can locate records quickly during an audit or investigation.
These evidence items constitute part of your information security management system. Having them ready will accelerate audits and build trust with enterprise customers.
Important considerations and pitfalls
Keeping data longer than needed increases risk and cost. Review your inventory to remove duplicates and legacy systems, and assign clear ownership so everyone knows how long to keep and how to dispose of each data set. Cover backups and archived systems, bind third parties by contract, and document legal and regional differences. Use cryptographic wiping for electronic media and cross‑cut shredding for paper to ensure secure disposal. Keep thorough documentation—classification decisions, retention schedules, disposal events and policy reviews—so you can demonstrate adherence during audits.
Customising the approach for vendors serving enterprise clients
Enterprise buyers have high expectations. Procurement questionnaires ask detailed questions about information handling, and clients often require evidence of conformity with ISO 27001, SOC 2, GDPR, HIPAA, and other frameworks. They may ask for your Statement of Applicability, classification policies, retention schedules, disposal logs, and risk assessments. If vendors fail to produce these items, they risk losing deals or facing long delays. To prepare, keep your policy concise and easy to read; include a brief overview of your retention approach, the detailed schedule and evidence logs, and describe how subcontractors or cloud providers manage retention. Provide contact details for roles such as Data Protection Officer and Compliance Lead.
You should also be ready to map your retention controls to your information security management system. Provide a Statement of Applicability and demonstrate that control 5.33 has been implemented. Share classification records, retention tables, and disposal logs. Explain how retention ties into incident response, backups, and access controls. Metrics—such as reductions in stored data or the percentage of disposals completed on time—help show that your programme is active. Contracts must include retention and deletion clauses that match customer expectations and local laws. Define responsibilities for data transfer, storage location, and destruction. For cross‑border services, adjust periods for regional requirements and ensure subcontractors follow the same rules.
Large vendors can’t manage retention manually across hundreds of clients. Metadata and automated workflows help drive classification, archiving and deletion. Configure your logging or security information and event management platform to purge events after the required period while preserving those needed for audits. Automation reduces human error and delivers consistent results across your environment.
Linking retention to the wider information security programme
Retention is part of a larger system. It touches classification, document control, incident response, and backups. You need to ensure that backups and disaster recovery plans do not keep data past its retention period and that encryption and access controls protect data during storage. Integrating retention into your information security management system means that controls reinforce each other and compliance arises naturally.
Best practices and practical tips
This ISO 27001 Data Retention Guide concludes with best practices and practical tips.
- Keep instructions clear. Use plain language so that busy teams know what to do without wading through legal jargon.
- Automate retention tasks. Use metadata and workflows to trigger archiving and deletion, and configure systems to purge logs when they pass their retention period.
- Involve the right people. Data owners understand business value, legal teams know regulations, and IT can implement controls. Collaboration ensures the policy is realistic.
- Document and review. Maintain an inventory, classification records, retention schedules, disposal logs, and change history. Review the policy at least once a year or when laws change.
- Secure destruction. Use cryptographic wiping or secure overwrite for electronic media and cross‑cut shredding for paper. Keep proof of destruction for audits.
Conclusion
Data retention is not a dry compliance task—it is a core part of security and trust. With the average breach cost at $4.88 million, companies serving enterprise clients face real financial and reputational stakes. This ISO 27001 Data Retention Guide has explained why retention matters, summarised relevant standards, and offered a practical framework for designing and enforcing a policy. It covered inventorying data, classifying it, defining justified retention periods, documenting procedures, implementing automation, monitoring adherence, and providing evidence.
The guide also addressed pitfalls and customised advice for vendors selling into regulated enterprises. By following these steps, you can reduce risk, demonstrate compliance, and build confidence with buyers and auditors. Security that reads well but fails in practice is a liability. Build a sound programme, operate it daily, and let compliance follow. A human‑led, managed security and compliance service like Konfirmity implements these controls inside your environment and keeps you audit‑ready year‑round.
FAQ
1) What is the data retention clause in ISO 27001?
There is no separate clause titled “data retention” in ISO 27001. Retention is addressed under control 5.33 (“Protection of records”) in ISO/IEC 27002. This control requires organisations to create policies for record storage, handling, and disposal; maintain a retention schedule; and destroy records safely once they are no longer needed. It emphasises authenticity, reliability, integrity, and usability of records and asks organisations to match retention with legal and contractual requirements.
2) What is the seven‑year retention rule?
There is no universal seven‑year rule under ISO 27001. The seven‑year period often comes from tax laws or industry practices, such as maintaining financial statements for seven years after the fiscal year ends. ISO 27001 requires you to set retention periods based on legal, regulatory, contractual, and business factors. For example, financial records may be kept for seven years due to tax laws, while marketing unsubscribe logs may only need to be kept for two years. Your schedule should document the reason for each period and ensure data is destroyed securely once it ends.
3) Is there an ISO standard dedicated to data retention?
There is no separate ISO standard solely for data retention. Retention requirements are part of ISO/IEC 27001 and ISO/IEC 27002. Control 5.33 in ISO/IEC 27002 covers record protection, including retention and disposal. Other controls, such as classification (5.12) and information transfer (5.14), influence how long data is kept. Organisations may also reference ISO 15489 for records management and ISO 27701 for privacy information management, but there is no single “retention standard.”
4) Does ISO 27001 set a fixed retention period?
ISO 27001 does not prescribe fixed retention periods. Organisations must determine periods based on applicable laws, contracts, business needs, and risk. Control 5.33 instructs organisations to establish retention schedules that specify how long each type of record is kept. For example, you might keep customer personal data for five years after contract termination, financial records for seven years after fiscal year end, and marketing unsubscribe logs for two years. The important point is to justify each period, document it, and destroy the data securely once retention ends.





.svg)






.svg)
.svg)