Most organizations conduct Data Protection Impact Assessments only when regulatory pressure forces them to—treating DPIAs as isolated compliance exercises rather than integrated risk management processes. This approach creates a fundamental gap between audit readiness and operational security posture, a gap that becomes apparent when over 4.1 billion records are compromised within a single year or when enforcement actions result in fines up to £8.7 million or 2% of global annual turnover.
For organizations selling to enterprise clients, demonstrating privacy-by-design principles through documented DPIA processes aligned with ISO 27001 controls becomes a competitive differentiator—not merely a regulatory obligation. This guide provides the systematic approach required to integrate DPIAs into your Information Security Management System, complete with implementation steps, risk-assessment frameworks, and ready-to-deploy templates.
What is a DPIA and how does it tie to ISO 27001?
A Data Protection Impact Assessment is a formal process mandated under GDPR Article 35 for high-risk processing operations affecting individual rights and freedoms. The assessment systematically evaluates data-processing activities before implementation, identifying privacy risks and documenting mitigation measures.
GDPR requires a DPIA whenever processing is likely to result in high risk to the rights and freedoms of individuals. Trigger scenarios include large-scale processing of sensitive data, systematic monitoring, automated decision-making with legal effects, use of new technologies, and cross-border data transfers. Organizations serving enterprise clients encounter these triggers frequently—particularly when deploying analytics platforms, cloud migrations, or customer-profiling systems that process end-user data at scale.

Why ISO 27001 and DPIA are a useful pairing
ISO 27001 establishes an Information Security Management System framework through risk-based controls addressing confidentiality, integrity, and availability of information assets. The standard's Requirement 6.1.2 on information security risk assessment aligns closely with DPIA processes by emphasizing assessment and treatment of privacy risks.
This alignment creates operational efficiency for organizations maintaining both ISO 27001 certification and GDPR compliance. Organizations certified under ISO 27701, which extends ISO 27001 to include privacy management, have reported a 50% increase in customer trust and a 30% improvement in alignment with global privacy regulations, with compliance costs reduced by up to 25%.
For enterprise-selling organizations, this pairing strengthens client confidence. When sales teams demonstrate that privacy assessments feed directly into ISO 27001 risk registers, management reviews, and control implementation—rather than existing as parallel documentation—enterprise clients recognize mature security operations rather than performative compliance.
When and why to conduct a DPIA in an ISO 27001 environment
Triggers for a DPIA
GDPR establishes mandatory DPIA requirements for high-risk processing, demanding rigorous documentation encompassing detailed processing specifications, necessity and proportionality evaluations, comprehensive risk assessment protocols, and structured stakeholder consultation records.
Specific triggers include:
- New or changed processing activities: Deployment of biometric authentication, behavioral analytics, or AI-driven profiling systems
- Large-scale processing of sensitive data: Health records, financial information, or special categories under GDPR Article 9
- Systematic monitoring: CCTV surveillance, employee monitoring, or tracking systems across client environments
- Use of new technologies: Internet of Things deployments, blockchain implementations, or novel data-processing architectures
- Cross-border transfers: Data flows outside the European Economic Area requiring adequacy assessments or standard contractual clauses
Business case for enterprise-selling organizations
Enterprise procurement teams increasingly require evidence that vendors perform systematic privacy assessments before processing customer data. Organizations without documented DPIA processes face longer sales cycles, additional security questionnaire rounds, and potential disqualification from enterprise RFPs.
The business case extends beyond sales enablement. The global average cost of a data breach reached $4.44 million in 2025, while US organizations experienced costs of $10.22 million. Systematic DPIA implementation addresses breach prevention through early identification of high-risk processing, documentation of mitigation measures, and integration with incident response planning.
Outcomes and benefits
A prominent European financial institution implemented DPIA at early stages of developing new customer data platforms, reducing potential breaches by 40% through proactive risk mitigation. Organizations conducting systematic DPIAs demonstrate several measurable outcomes:
- Reduced time-to-resolution for client security questionnaires
- Documented evidence for ISO 27001 Clause 6.1.2 risk assessments
- Clear audit trail linking privacy controls to ISMS documentation
- Improved stakeholder engagement through structured consultation processes
- Faster identification and containment of security incidents affecting personal data
Step-by-step DPIA process aligned with ISO 27001
This ten-step process integrates DPIA requirements with ISO 27001 controls, creating documentation that serves both privacy compliance and ISMS audit requirements.
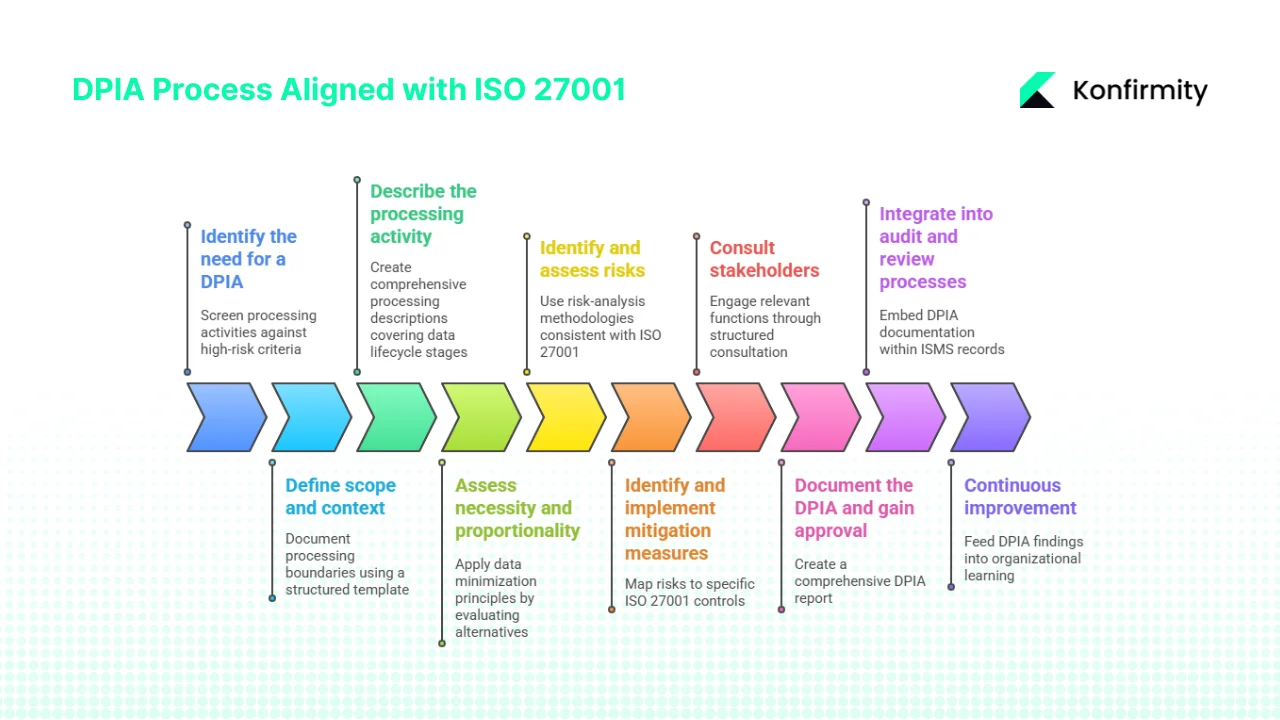
Step 1: Identify the need for a DPIA
Screen processing activities against high-risk criteria before project initiation. Use a standardized screening questionnaire covering:
- Scale of processing (number of individuals, data volume, geographic scope)
- Sensitivity of data categories (special categories, biometric data, financial information)
- Processing context (vulnerable populations, power imbalances, innovative use of technology)
- Potential for automated decision-making or profiling with legal effects
Example: A service provider introduces biometric login tracking across enterprise client environments. Screening reveals large-scale processing of biometric data combined with systematic monitoring—triggering mandatory DPIA.
ISO 27001 alignment: This step supports Clause 6.1.2 (information security risk assessment) by establishing screening criteria that identify processing requiring formal risk evaluation.
Step 2: Define scope and context
Document processing boundaries using a structured template capturing:
ISO 27001 alignment: Aligns with Annex A.5.1 (policies for information security) and A.8.2 (privacy and protection of personally identifiable information).
Step 3: Describe the processing activity
Create comprehensive processing descriptions covering data lifecycle stages:
- Collection methods: APIs, web forms, device sensors, third-party sources
- Storage architecture: Database types, encryption methods, access controls, backup procedures
- Processing operations: Transformation, aggregation, profiling, automated analysis
- Transfer mechanisms: Internal systems, external vendors, cross-border flows
- Retention and deletion: Automated deletion triggers, archival procedures, right-to-erasure processes
This documentation directly supports ISO 27001 Annex A.8 (asset management) and A.18 (compliance with legal requirements).
Step 4: Assess necessity and proportionality
Apply data minimization principles by evaluating whether less intrusive alternatives achieve the same business objectives. Document:
- Necessity: Why this specific data processing is required for stated purposes
- Proportionality: Whether scope, duration, and methods are proportionate to legitimate aims
- Alternatives considered: Less privacy-invasive methods, pseudonymization, aggregation
Practical controls: Implement encryption at rest and in transit (ISO 27001 A.8.24), access controls limiting data exposure to authorized personnel (A.8.3), and automated retention policies enforcing storage limitation (A.8.10).
Step 5: Identify and assess risks
Use risk-analysis methodologies consistent with your ISO 27001 risk management framework:
Consider impacts beyond data protection: reputational damage, contractual breaches, loss of enterprise client trust, regulatory enforcement actions.
Step 6: Identify and implement mitigation measures
Map risks to specific ISO 27001 controls:
- Unauthorized access: Multi-factor authentication (A.8.5), access control policies (A.8.2), privileged access management (A.8.3)
- Vendor-related risks: Supplier relationships management (A.15), contracts addressing security requirements, continuous monitoring
- Configuration risks: Change management procedures (A.8.32), configuration baselines, automated compliance scanning
- Incident response: Security incident management procedures (A.6.8), breach notification protocols, forensic readiness
Document implementation timelines, responsible parties, and verification methods for each mitigation measure.
Step 7: Consult stakeholders
Engage relevant functions through structured consultation:
- Internal stakeholders: Legal, information security, data protection officer, business unit owners, engineering teams
- External stakeholders: Enterprise client contacts (when processing their end-user data), subprocessors, regulatory bodies when residual risks remain high
Document consultation outcomes, concerns raised, and decisions taken. This record demonstrates accountability under GDPR Article 35(9) and supports ISO 27001 Clause 5.2 (policy) stakeholder engagement requirements.
Step 8: Document the DPIA and gain approval
Create a comprehensive DPIA report containing:
- Executive summary stating conclusions and residual risk determination
- Detailed processing description from Steps 2-3
- Risk assessment methodology and findings from Step 5
- Mitigation measures and implementation timeline from Step 6
- Stakeholder consultation summary from Step 7
- Approval signature from data protection officer, CISO, and business owner
ISO 27001 Requirement 7.5.1 mandates maintaining documented information to support process operations, aligning with GDPR requirements that ensure all privacy-related actions are recorded, justified, and accessible for audits.
Step 9: Integrate into audit and review processes
Embed DPIA documentation within ISMS records:
- Reference DPIA assessments in ISO 27001 risk register
- Link mitigation measures to Statement of Applicability control implementation
- Include DPIA outcomes in management review agenda (Clause 9.3)
- Schedule internal audits covering DPIA execution and effectiveness (Clause 9.2)
Set review triggers: significant processing changes, new data flows, technology updates, regulatory developments, or at minimum annually. DPIAs function as living processes to manage and review processing risks and measures on an ongoing basis.
Step 10: Continuous improvement
Feed DPIA findings into organizational learning:
- Update DPIA templates based on lessons learned
- Refine risk assessment methodologies with actual incident data
- Enhance organizational policies addressing identified gaps
- Strengthen security incident response procedures for personal data breaches
- Track mitigation effectiveness through metrics (implementation completion rates, residual risk trends, audit findings)
This approach embeds privacy risk management into continuous improvement cycles required by ISO 27001 Clause 10 (Improvement).
Example use-cases and templates for busy teams
Use-case: Cloud migration for enterprise client
Scenario: Migrating on-premises customer relationship management system containing 500,000 employee and customer records to a public cloud provider in a different jurisdiction.
DPIA application:
- Scope: Customer contact information, employee credentials, transaction history
- High-risk factors: Cross-border transfer, new technology deployment, large scale
- Risks identified: Unauthorized access through cloud misconfigurations, jurisdictional access by foreign governments, vendor security incident
- Mitigations: Encryption with customer-managed keys, standard contractual clauses for transfers, vendor security assessment, data residency controls, continuous cloud security posture management
Use-case: Deployment of analytics-based customer profiling
Scenario: Implementing behavioral analytics processing enterprise client end-user data for predictive recommendations, involving automated profiling that influences service delivery.
DPIA application:
- Scope: Behavioral data, usage patterns, inferred preferences
- High-risk factors: Automated decision-making, profiling, potential for discrimination
- Risks identified: Algorithmic bias, inappropriate profiling criteria, inadequate transparency to data subjects
- Mitigations: Human review of automated decisions, algorithm fairness testing, clear privacy notices explaining profiling, opt-out mechanisms, regular algorithm audits
Templates for download
Organizations implementing DPIAs require standardized templates ensuring consistency:
DPIA Screening Checklist: 12 yes/no questions covering high-risk criteria with automatic DPIA recommendation
Risk Assessment Table: Pre-formatted spreadsheet linking risks to likelihood/impact matrices and ISO 27001 controls
DPIA Report Template: 15-page structured document with sections mapping to GDPR Article 35 requirements and ISO 27001 documentation standards
These templates integrate with common collaboration platforms and include version control fields supporting ISO 27001 Requirement 7.5.3 (control of documented information).
Common pitfalls and how to avoid them
Organizations conducting their first DPIAs consistently encounter these obstacles:
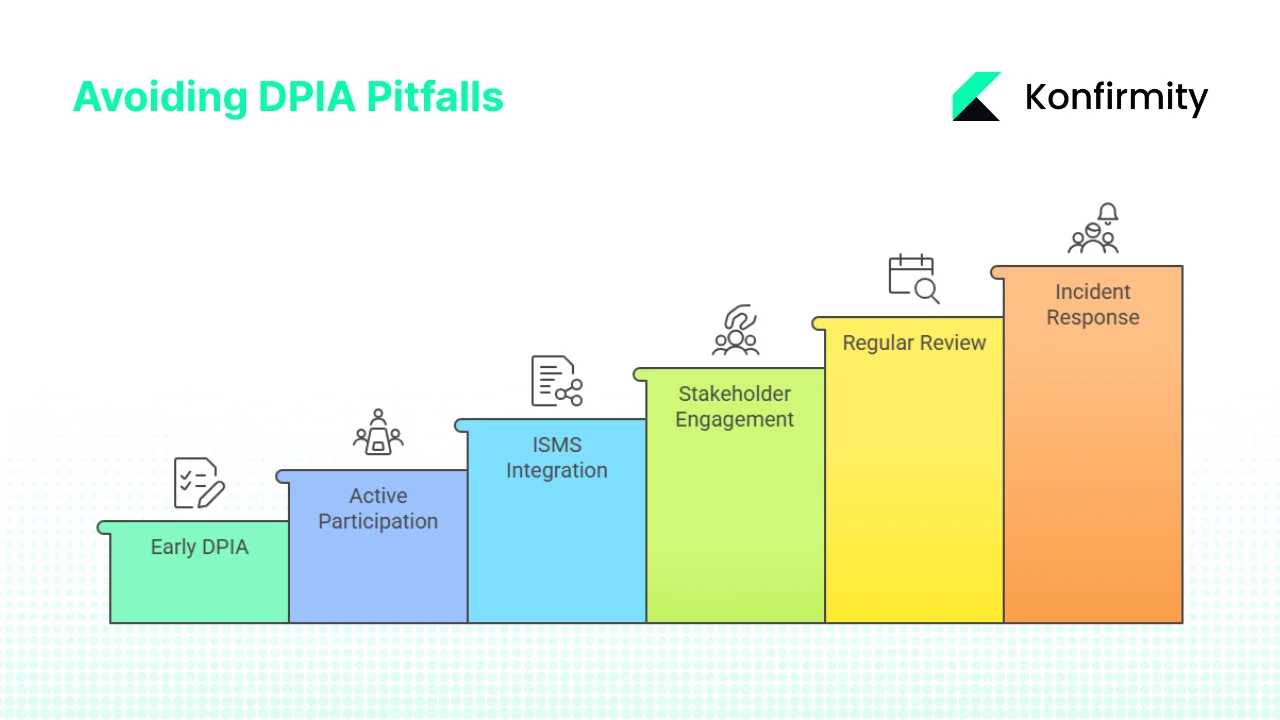
Conducting DPIA after deployment: Defeats privacy-by-design principles and limits mitigation options. Embed DPIA screening into project initiation checklists before development begins.
Treating DPIA as checkbox exercise: Produces documentation satisfying form but not substance. Ensure business owners and engineering teams participate directly in risk identification and mitigation design.
Poor integration with ISMS processes: Creates parallel documentation increasing maintenance burden. Reference DPIAs in risk registers, link to existing ISO 27001 controls, included in management review.
Insufficient stakeholder engagement: Misses risks visible only to specific functions. Establish formal consultation requirements with sign-off from legal, security, business units, and data protection officers.
Failure to review when context changes: Allows DPIA documentation to become stale and ineffective. Set automated review triggers tied to change management processes and project milestones.
Overlooking incident response implications: DPIA identifies personal data at risk but fails to strengthen breach response procedures. Update incident response playbooks to address specific processing activities assessed in DPIAs.
How to align DPIA with enterprise client contracts and ISO 27001 certification
Contractual compliance language for enterprise clients
Enterprise service agreements increasingly require vendors to confirm DPIA completion for processing activities. Standard contract language addresses:
- Commitment to conduct DPIAs when processing likely to result in high risk
- Agreement to provide DPIA summaries or full reports upon reasonable request
- Obligation to consult with client before implementing high-risk processing changes
- Confirmation that DPIA outcomes informed security control implementation
This language translates DPIA processes into contractual commitments demonstrating systematic privacy risk management.
Using DPIA results in ISO 27001 audit and review
Certification auditors assess whether organizations systematically identify and treat information security risks. DPIA documentation provides concrete evidence:
- Risk assessment methodology (Clause 6.1.2)
- Control selection rationale in Statement of Applicability
- Management review inputs demonstrating privacy risk consideration (Clause 9.3)
- Documented information supporting ISMS processes (Clause 7.5)
Present DPIAs as integrated risk assessments rather than separate privacy documentation, demonstrating that personal data protection receives systematic treatment within ISMS operations.
Demonstrating continuous improvement and client confidence
Track DPIA metrics for management review and client reporting:
- Number of DPIAs completed per reporting period
- Residual risk trends across DPIA portfolio
- Mitigation implementation completion rates
- Review frequency and re-assessment triggers
- Integration with security incident response (personal data breach identification and notification)
Enterprise clients evaluating vendor security posture recognize that mature DPIA processes indicate sophisticated privacy risk management—not merely regulatory compliance.
Checklist before you launch the DPIA process
- ✅ Screening completed: High-risk determination documented with supporting rationale
- ✅ Scope defined: Data categories, purposes, flows, controller/processor roles, third parties identified
- ✅ Risk assessment conducted: Threats, impacts, likelihood, existing controls, residual risks evaluated using consistent methodology
- ✅ Mitigation aligned: Controls mapped to ISO 27001 framework, implementation timeline established, verification methods defined
- ✅ Stakeholders engaged: Business, legal, security, DPO, client contacts (where appropriate) consulted with outcomes documented
- ✅ Documentation complete: DPIA report finalized, version controlled, approved by designated authorities
- ✅ ISMS integration confirmed: Risk register updated, Statement of Applicability cross-referenced, audit schedule includes DPIA review
- ✅ Review plan established: Re-assessment triggers defined, review frequency set, responsibility assigned
- ✅ Client readiness achieved: DPIA evidence accessible for enterprise client security reviews and contract negotiations
- ✅ Improvement mechanisms active: Template updates, process refinement, metrics tracking implemented
Conclusion
Organizations selling to enterprise clients face escalating expectations around systematic privacy risk management. The intersection of ISO 27001 certification requirements and GDPR DPIA obligations creates an opportunity: building integrated privacy and security processes that satisfy both regulatory frameworks while demonstrating operational maturity to prospective clients.
The structured DPIA approach outlined here—ten implementation steps, risk-assessment frameworks, stakeholder consultation processes, and ISMS integration—provides the foundation for privacy-by-design principles becoming embedded operational reality rather than aspirational documentation. Organizations implementing these processes report measurable outcomes: reduced security questionnaire cycles, documented audit evidence, proactive risk identification, and strengthened client confidence.
Begin by embedding DPIA screening into project initiation processes, ensuring assessment occurs before processing begins. Leverage existing ISO 27001 risk management frameworks rather than creating parallel privacy assessment processes. Treat DPIA documentation as living records requiring review when processing contexts change. Use standardized templates reducing documentation burden while maintaining consistency across assessments.
Enterprise clients evaluating vendor security practices distinguish between organizations conducting DPIAs to satisfy regulatory minimums and those integrating privacy assessments into systematic risk management. The difference appears in documentation quality, control implementation rigor, and stakeholder engagement depth—characteristics that become apparent during security reviews, audit exchanges, and contract negotiations.
FAQ
1) What are the four stages of a DPIA?
The core stages are: screening and need identification, processing description with risk assessment, mitigation planning with stakeholder consultation, and documentation with approval and ongoing review. These stages map to systematic risk management: identifying when assessment is required, understanding what risks exist, determining how to address risks, and ensuring measures remain effective over time.
2) What should be included in a DPIA?
GDPR compliance demands rigorous documentation encompassing detailed processing operation specifications, thorough necessity and proportionality evaluations, comprehensive risk assessment protocols, and structured stakeholder consultation records. Additional elements include mitigation measures with implementation timelines, residual risk determinations, approval documentation, and review schedules ensuring the assessment remains current.
3) Is a DPIA mandatory for all projects?
DPIA is required whenever processing is likely to result in high risk to the rights and freedoms of individuals—not for all processing activities. High-risk scenarios include large-scale sensitive data processing, systematic monitoring, automated decision-making with legal effects, profiling, and use of new technologies. Organizations should conduct screening assessments to determine whether specific projects trigger DPIA requirements, though best practice suggests performing DPIAs for any major project involving personal data use.
4) How frequently is a DPIA required?
DPIA frequency depends on processing changes rather than fixed time intervals. Organizations must reassess when introducing significant changes to processing activities, implementing new data flows, deploying new technologies, or when external context changes (such as new security vulnerabilities, regulatory developments, or public concerns). Many regulators suggest reviewing DPIAs every three years absent specific change triggers, though organizations with dynamic processing environments may require more frequent reassessment.





.svg)






.svg)
.svg)