Most enterprise buyers now ask for assurance artifacts—security questionnaires, privacy addenda, DPAs—before procurement proceeds. Without a resilient security program and evidence to back it up, deals stall. This article examines how ISO 27001 DPO Responsibilities intersect with real‑world data‑protection obligations and why companies selling into enterprise and healthcare markets must move past paper promises. Drawing on credible sources and Konfirmity’s audit experience, I explain what a Data Protection Officer does, why the role is crucial, and how busy teams can adopt a practical, step‑by‑step approach to compliance and continuous security operations.
What Is ISO 27001 and Why Does a DPO Matter?
ISO/IEC 27001:2022 is the leading standard for an information security management system (ISMS). It sets requirements for establishing, implementing, maintaining, and improving an ISMS with a focus on risk management across confidentiality, integrity, and availability. Certification demonstrates that you operate a robust security program.
Under modern privacy laws like the General Data Protection Regulation (GDPR), organisations that process large volumes of personal or sensitive data must appoint a Data Protection Officer (DPO). A DPO is an expert in data‑protection law who monitors compliance, advises the organisation, and liaises with regulators. They must report directly to senior management and operate without interference. Rather than a checkbox, the DPO role is about trust and risk management.
For firms selling into enterprise markets, appointing a DPO signals that you take privacy seriously. The DPO bridges legal obligations with your ISO 27001 ISMS, supporting operational risk management and building confidence in prospective clients. The following sections describe the DPO’s responsibilities and how they support both certification and enterprise sales.

Definition, Independence and ISO 27001 Context
Understanding the scope of ISO 27001 DPO Responsibilities begins with the legal definition. The GDPR designates a DPO as an expert in data‑protection law who advises and informs the organisation, monitors compliance, trains staff, conducts audits, and liaises with authorities. Article 38 requires DPOs to report directly to the highest management level, ensuring independence and avoiding conflicts of interest. Within an ISO 27001 ISMS, the DPO bridges legal and regulatory requirements with security policies, supports privacy by design, and reinforces the top‑management commitment needed for certification.
Why DPOs Matter for Companies Selling to Enterprises
Enterprise and healthcare clients face strict data‑protection obligations and cannot simply trust vendor assurances. ISO 27001 DPO Responsibilities are central to meeting these expectations. Modern breaches are costly—averaging $4.44 million globally with detection times exceeding 200 days—and 68% of incidents involve human error. Buyers now ask for evidence such as data maps, PIAs, vulnerability reports, and incident plans, while failing to meet contract requirements like Standard Contractual Clauses or BAAs can result in penalties. A DPO brings independence and expertise, coordinating privacy activities, security controls, and legal obligations so that vendors can provide the operational security and assurance enterprise clients demand.
Key Responsibilities of a DPO (Connected to ISO 27001 and Regulatory Compliance)
The role of the DPO can be broken into several responsibilities. Each one should be tied to ISO 27001 requirements and the real-world needs of enterprise clients. Below, we describe these responsibilities and what they look like in practice.
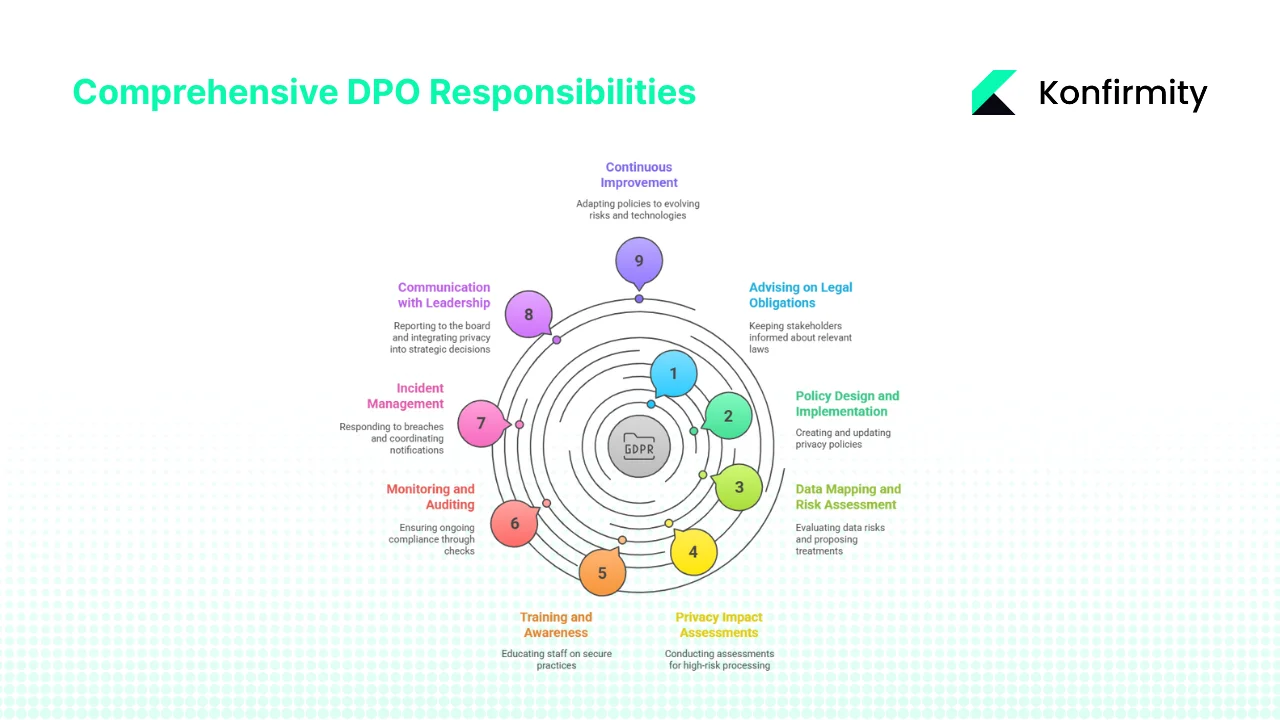
1. Advising on and Informing About Legal Obligations
As part of ISO 27001 DPO Responsibilities, a DPO must keep leadership and staff informed about relevant laws such as GDPR, HIPAA, and local data‑privacy regulation. In practice this means interpreting legal requirements into internal policies, briefing stakeholders on regulatory changes and cross‑border transfer rules, and reviewing contracts such as DPAs and BAAs to ensure they meet regulatory and ISO 27001 control requirements.
2. Designing, Implementing, and Reviewing Policies and Procedures
ISO 27001 requires documented policies covering access control, encryption, asset management, and incident management. The DPO writes or updates privacy policies, embeds them into the ISMS and related frameworks, and keeps them current.
3. Data Mapping and Risk Assessment
ISO 27001 emphasises a risk‑based approach. The DPO maintains an inventory of data types, locations, access rights, and processing activities—including third‑party processors and cross‑border flows—evaluates risks to confidentiality, integrity and availability, and proposes treatments such as encryption and access restrictions based on Annex A controls.
4. Privacy Impact Assessments (PIAs) and Data Protection Impact Assessments (DPIAs)
For high‑risk processing, GDPR mandates a DPIA. A DPO defines triggers for when a PIA/DPIA is needed, provides a template that captures purpose, data types, flows, risks, legal basis, mitigations, and approvals, and keeps records of completed assessments for audits and due diligence.
5. Training, Awareness, and Stakeholder Engagement
Human error accounts for most breaches—68% according to StrongDM—so training is vital. ISO 27001 DPO Responsibilities include designing onboarding and refresher sessions on secure practices and privacy obligations, engaging vendors and staff on their responsibilities, and keeping records of participation.
6. Monitoring, Auditing, and Continuous Compliance Checks
ISO 27001 requires ongoing monitoring and internal audits. ISO 27001 DPO responsibilities therefore include keeping logs, monitoring access reviews and vulnerability scans, performing internal audits, and working with teams to remediate issues and update the risk register.
7. Incident Management, Breach Detection, and Response
Fast response reduces breach costs and penalties. GDPR requires notification to authorities within 72 hours. The DPO builds and executes an incident response plan, detects breaches with security operations, and coordinates notifications.
8. Communication with Leadership and Integration with Enterprise Risk Management
A DPO bridges operational security and executive oversight. They report regularly to the board on compliance, incidents, risks, training, and investment needs, join strategic decisions to embed privacy early, and integrate privacy risks into enterprise risk management.
9. Continuous Improvement in Step with Business Growth
Data volumes grow, regulations evolve, and new technologies introduce fresh risks. The DPO treats privacy and compliance as a continuous program, revises policies when laws change or audits uncover issues, ensures new products or markets are added to the risk register, and stays aware of emerging threats and best practices.
Step‑by‑Step Blueprint for Busy Teams
Implementing ISO 27001 DPO Responsibilities can be broken into nine high‑level actions rather than a complex project. Based on our audits and operations for numerous clients, we suggest the following roadmap:
- Data inventory & mapping: Catalogue data sources, processing flows, access rights, and third‑party processors.
- Risk assessment & gap analysis: Compare current practices against ISO 27001 and other frameworks; identify missing controls and outdated policies.
- Policies & procedures: Draft or update security and privacy policies; define processes for data handling, retention, encryption, access reviews, and incident response.
- PIA/DPIA setup: Define when PIAs/DPIAs are needed; build a template; embed the process into project and vendor workflows.
- Training & awareness: Schedule onboarding and refreshers on secure practices and privacy obligations; track participation and tailor content.
- Monitoring & auditing: Set up logging and vulnerability scans; schedule internal audits; maintain evidence checklists.
- Incident response planning: Prepare a plan for detection, containment, notification, remediation, documentation, and follow‑up; include 72‑hour regulatory notifications.
- Reporting & communication: Schedule regular reporting to leadership on compliance status, risks, incidents, and regulatory changes.
- Continuous improvement: Conduct post‑mortems after audits or incidents and update documentation, risk assessments, and policies accordingly.
Examples and Mini‑Templates
To bring these steps to life, here are concise examples you can adapt:
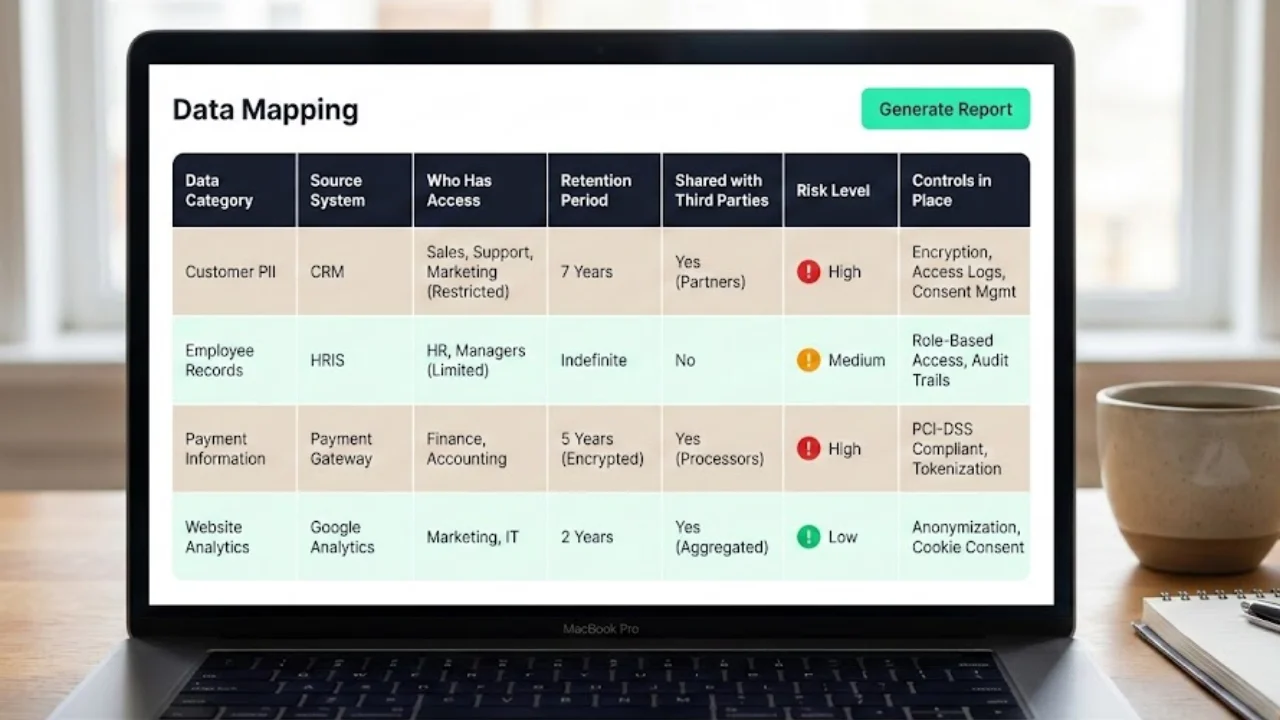
Example 1 – Data mapping: create a table with columns such as Data Category, Source System, Who has access, Retention Period, Shared with third parties, Risk level, and Controls in place. Use it to track personal data flows and identify high‑risk areas.
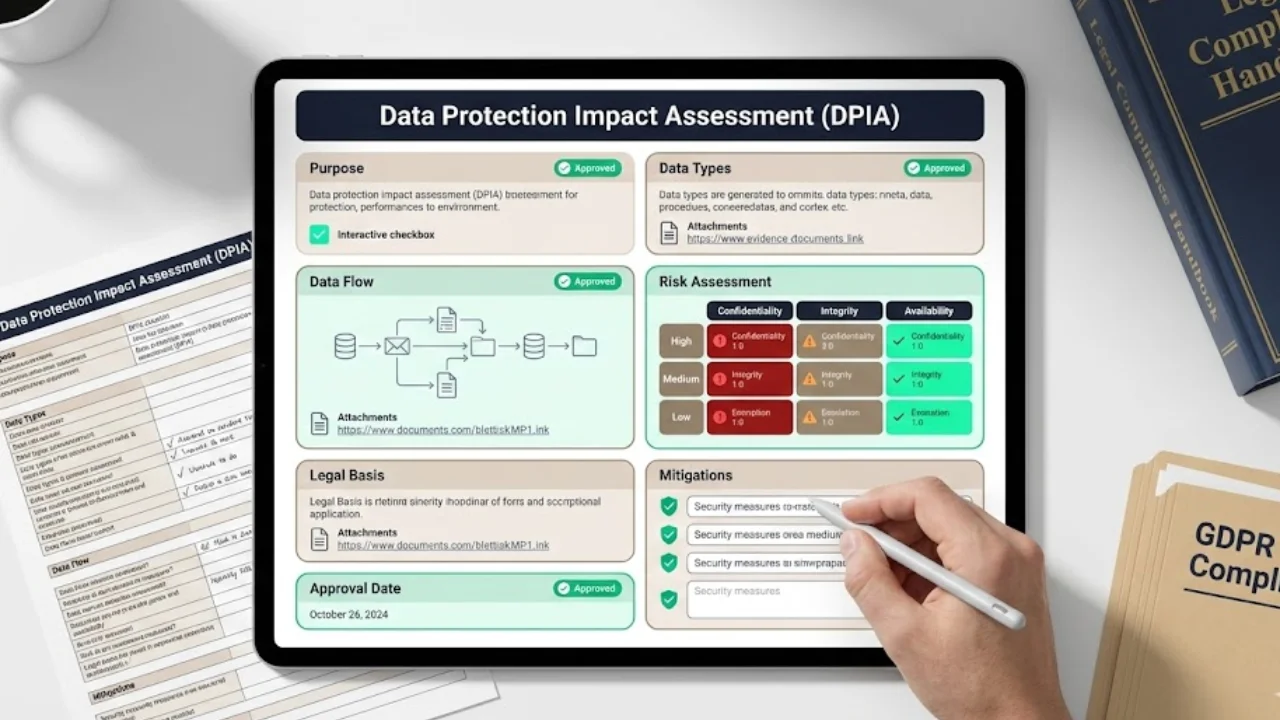
Example 2 – DPIA template: include sections for Purpose, Data types, Data flow, Risk assessment (confidentiality, integrity, availability), Legal basis, Mitigations, and Approval date. Store completed assessments for audit readiness.
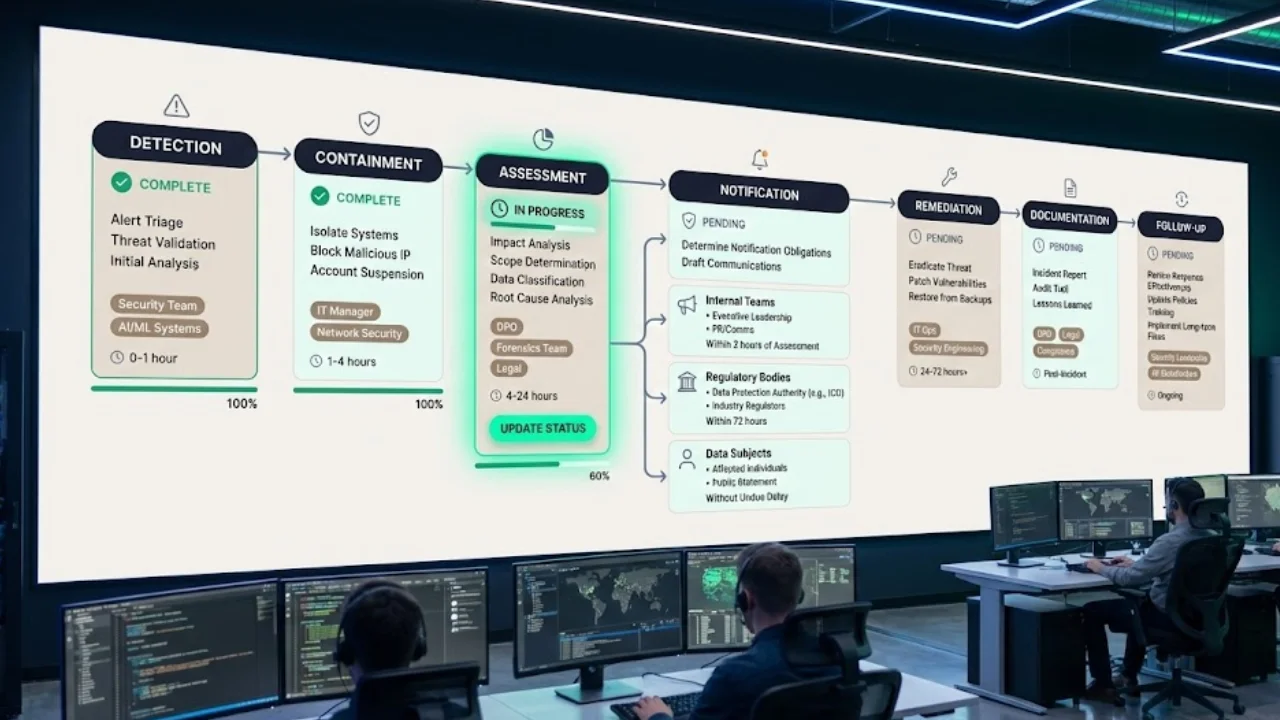
Example 3 – Incident response workflow: outline the stages: Detection, Containment, Assessment, Notification (internal, regulators, or data subjects), Remediation, Documentation, and Follow‑up. Assign roles and timelines to each stage.
Example 4 – Audit checklist: gather evidence such as updated policies, data inventories and risk assessments, PIA/DPIA logs, training records, vendor assessments, incident logs, and proofs of continuous monitoring (access reviews, vulnerability scans, SLA adherence).

Common Challenges and How a DPO Helps
Operating across jurisdictions means navigating different data‑protection rules and localisation mandates. Scaling data volumes and complex ecosystems introduces third‑party risks—30% of breaches involve vendors—while human error causes most incidents. A DPO establishes consistent policies for international transfers, manages vendor risk, builds training programs to reduce human‑factor breaches, and performs PIAs early so product development and data use do not conflict with compliance. They also prepare the documentation enterprise clients need—risk assessments, PIA logs, vendor audits, and incident records—shortening sales cycles and building trust.
How ISO 27001 and DPO Roles Complement Each Other
ISO 27001 provides the framework for a disciplined security program—risk assessment, control selection, documented procedures, and continuous improvement. The DPO role operationalises privacy requirements and integrates regulatory obligations into that framework, extending risk management with DPIAs and data mapping and overseeing continuous monitoring and regulator interactions. Together they offer a clear narrative to buyers: we operate a certified ISMS and have an independent officer who oversees privacy. Adopting ISO 27001 and appointing a DPO strengthens your position by combining technical controls with legal and regulatory expertise.
Quick‑Start Checklist for Setting Up a DPO Function
Busy teams can use this condensed list as a starting point:
- Assign Ownership: Choose a qualified individual with expertise in data protection. Ensure independence and reporting to top management.
- Build Data Inventory and Risk Assessment: Document all data processing activities and evaluate risks.
- Draft Policies and Procedures: Match ISO 27001 controls and embed privacy requirements.
- Set Up PIA/DPIA Processes: Define triggers and create templates.
- Launch Training Program: Educate employees and record participation.
- Establish Monitoring and Audit Schedules: Track access, vulnerabilities, and control effectiveness.
- Develop Incident Response Plan: Include 72‑hour notification obligations.
- Report to Leadership: Provide regular updates and integrate privacy risks into enterprise risk management.
- Plan for Continuous Improvement: Update controls and policies as the business and regulatory environment evolve.
Conclusion
Creating a resilient security and privacy program requires commitment to more than checklists. A Data Protection Officer, working within an ISO 27001 framework, helps translate regulatory requirements into practical controls and builds a culture of accountability and trust. Breaches cost millions and human error drives most incidents, so companies need to show their security holds up under pressure. Embracing ISO 27001 DPO Responsibilities ensures readiness, reduces risk, and supports deals. Start early, implement in steps, and treat privacy and security as ongoing programs—security that reads well but fails in practice is a liability.
FAQs
1) What are the five key responsibilities of a DPO?
A DPO advises on legal obligations, maintains data inventories and risk assessments, drafts policies, conducts DPIAs, oversees training and audits, and manages incident response while acting as a contact point for regulators.
2) Is the DPO role full time?
It depends on size and risk. High‑risk organisations often need a full‑time DPO. Smaller firms can outsource or assign the role part time, as long as independence and expertise are preserved.
3) What laws do DPOs need to know?
DPOs should know the GDPR, relevant local data‑protection laws, sector‑specific rules like HIPAA, and ISO 27001 controls so legal obligations are consistent with technical measures.
4) When is appointing a DPO mandatory?
Appointing a DPO is mandatory under the GDPR for public authorities, organisations conducting large‑scale monitoring, or those processing sensitive data. Many others do so voluntarily to demonstrate commitment to privacy.
5) Can a DPO be outsourced?
Yes. You can outsource the role if you lack internal expertise, but the external DPO must have adequate knowledge and access and still report directly to top management.
6) How does a DPO differ from a CISO or Chief Privacy Officer?
A CISO leads technical security, a Chief Privacy Officer shapes overall privacy strategy, and a DPO focuses on legal compliance; the DPO must remain independent and cannot hold conflicting roles.
7) What are the observation periods for SOC 2 certification?
SOC 2 Type I assesses controls at a moment in time and typically takes 1.5–3.5 months. Type II requires a 3–12‑month observation period and can take 5.5–17.5 months. Integrating ISO 27001 and DPO efforts can streamline evidence collection.





.svg)






.svg)
.svg)