Most enterprise buyers today request detailed assurance artifacts before they sign a contract. A paper‑thin security posture slows or kills deals. For organizations selling to large customers, practical endpoint security is a critical pillar of this assurance. In a distributed workforce — where laptops, tablets, smartphones and other devices connect from remote and hybrid environments — each endpoint becomes a potential entry point for attackers. The expansion of cloud services and bring‑your‑own‑device (BYOD) policies widens the attack surface, while attackers increasingly target endpoints with phishing, infostealers and ransomware. According to data breach research, breaches involving remote work cost an average of USD 131 000 more than breaches without a remote‑work element, and 91 % of cybersecurity professionals reported an increase in cyber attacks due to remote working. In this environment, ISO 27001 Endpoint Security For ISO 27001 is more than a certification requirement — it’s a business imperative.
ISO/IEC 27001:2022 (ISO 27001) defines requirements for an information security management system (ISMS) and uses Annex A as a catalogue of recommended controls. Its companion guidance ISO/IEC 27002:2022 (ISO 27002) explains how to implement those controls. The 2022 revisions merged and streamlined previous control sets, reducing 114 controls to 93 grouped into four themes — organisational, people, physical and technological — reflecting evolving technology and threat patterns. Endpoint protection falls within technological controls, specifically Annex A 8.1: User Endpoint Devices, which states that information stored on, processed by or accessible via user endpoint devices should be protected. This article, written from the perspective of a practitioner who has supported more than 6 000 audits over 25+ years, provides a step‑by‑step roadmap for vendors seeking to meet and exceed ISO 27001 endpoint security standards. You’ll learn how proper endpoint security supports risk reduction, helps pass audits, and builds client trust — so you can sell faster and with confidence.
What Are ISO 27001 and ISO 27002?
ISO 27001 is an international standard for establishing, implementing, maintaining and continually improving an ISMS. It outlines high‑level requirements across clauses 4‑10 (context, leadership, planning, support, operation, performance evaluation and improvement) and includes Annex A controls as an optional catalogue. Organizations determine which controls apply through a risk assessment and document their choices in a Statement of Applicability.
ISO 27002 is a guidance document that elaborates on each Annex A control. It explains the purpose of each control, suggests implementation approaches and lists related controls. When ISO 27001:2022 was released, the number of controls fell from 114 to 93, organized under four themes: organisational, people, physical and technological. Several controls were combined or updated to reflect modern security practices such as identity management, threat intelligence and the rise of cloud services. The revision emphasises a risk‑based approach and encourages organizations to use the controls as building blocks rather than a checklist.
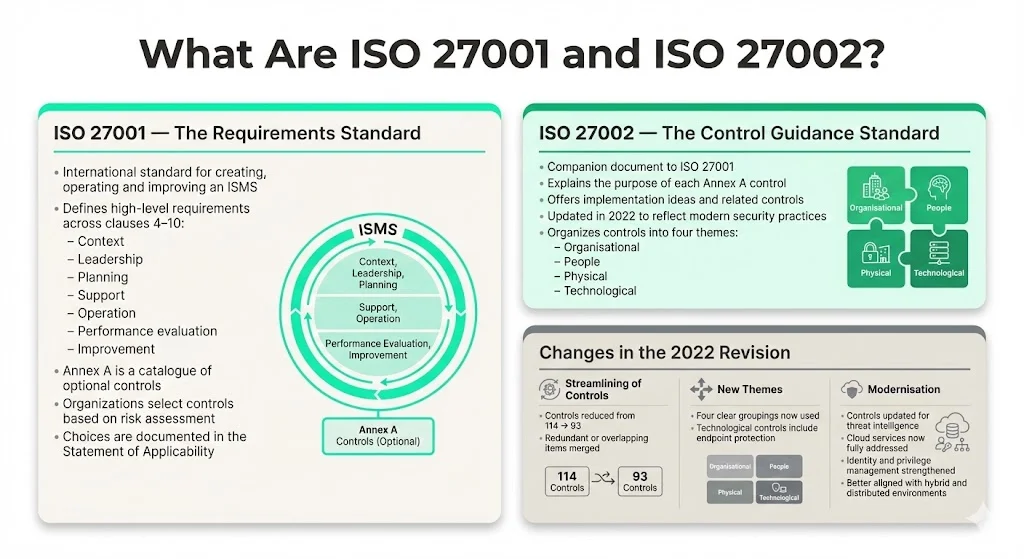
Changes in the 2022 Revision
Compared with the 2013/2017 version, ISO 27001:2022 introduces fewer controls but clearer grouping. For example:
- Streamlining of controls – The overall number was reduced from 114 to 93 by merging related items and eliminating redundancies.
- New themes – Controls are now grouped under organisational, people, physical and technological themes. Endpoint protection is part of the technological controls.
- Modernisation – Controls now reference contemporary topics such as threat intelligence, cloud services, identity and privilege management. These updates better support distributed work and hybrid infrastructure.
Annex A 8.1 — User Endpoint Devices
Annex A 8.1 addresses the protection of information on or accessed through user endpoint devices. The control states: “Information stored on, processed, or accessible via user endpoint devices should be protected”. Endpoint devices include laptops, desktop computers, smartphones, tablets and other ICT devices used by personnel. Because these devices operate outside of controlled office environments and often connect over untrusted networks, they introduce significant risk.
ISO 27002 explains that implementing control 8.1 requires both technical and administrative measures. Organizations must create policies covering device usage, registration, network access, software installation, removable media and acceptable use. Technical measures include full‑disk encryption, anti‑virus/anti‑malware solutions, secure configuration baselines, remote wipe capabilities and endpoint management tools. Training and awareness are also essential, as human error remains a major cause of breaches.
It’s important to recognize that Annex A controls are not automatically mandatory. ISO 27001 requires a risk assessment and an explicit Statement of Applicability. If certain controls are deemed irrelevant based on risk, they can be excluded with justification. However, most organizations that handle sensitive data or work with enterprise clients will find endpoint security essential.
Why Endpoint Security Matters — Risk and Enterprise Sales Perspective
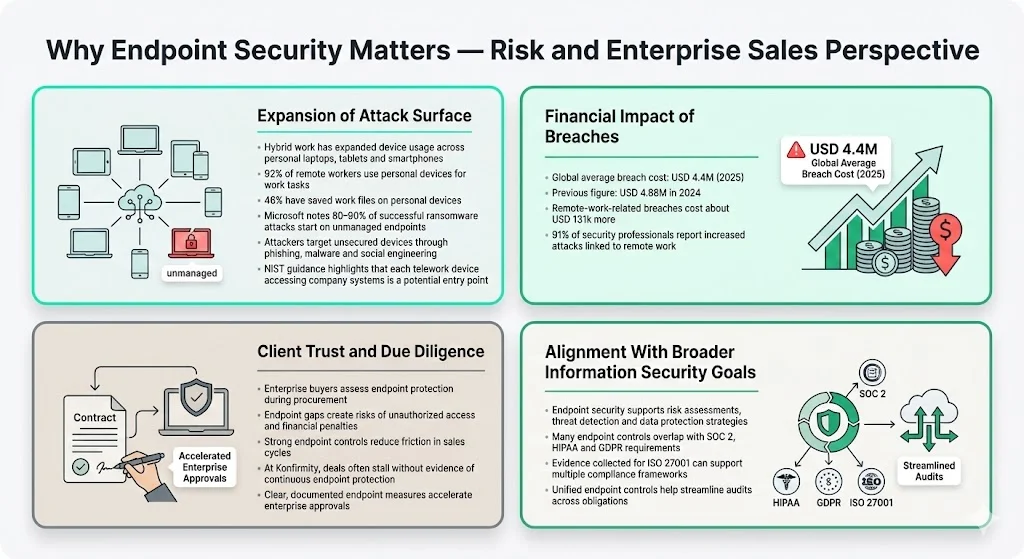
1) Expansion of Attack Surface
The shift to remote and hybrid work has increased reliance on personal devices and home networks. In a 2025 survey of managed service providers (MSPs), 92 % of remote workers said they used personal tablets or smartphones for work tasks, and 46 % had saved a work file on those devices. Microsoft reported that 80–90 % of successful ransomware attacks originated from unmanaged devices. As remote work continues, attackers will exploit these unmanaged endpoints through phishing, malware and social engineering. NIST’s telework guidance notes that teleworkers use various client devices such as desktop and laptop computers, smartphones and tablets to access organizational resources; each device is a potential vector when left unsecured.
2) Financial Impact of Breaches
Data breaches are costly, and the presence of remote work can amplify those costs. IBM’s 2025 Cost of a Data Breach report found the global average breach cost to be USD 4.4 million. The 2024 figure was even higher at USD 4.88 millionibm.com. Research compiled by Varonis shows that breaches involving remote work cost an average of USD 131 000 more than breaches without a remote component. Furthermore, 91 % of cybersecurity professionals reported an increase in cyber attacks due to remote working, underscoring the need to protect off‑premises endpoints.
3) Client Trust and Due Diligence
Enterprise clients typically conduct extensive due diligence before purchasing from a vendor. Procurement questionnaires, data processing addenda, business associate agreements and security addenda often request proof of endpoint protection measures. A single compromised laptop can lead to unauthorized data access across the network, which may result in contractual penalties, regulatory fines and reputational damage. Demonstrating robust endpoint security under ISO 27001 shows maturity, reduces concerns during vendor risk assessments and accelerates sales cycles. From our experience at Konfirmity, deals can stall for months when companies lack evidence of continuous endpoint protection; with proper controls and documentation, enterprise buyers often proceed more quickly.
4) Alignment with Broader Information Security Goals
Endpoint security under ISO 27001 is not an isolated task. It ties into risk assessments, data protection strategies, threat detection and compliance. Strong endpoint controls support other frameworks such as SOC 2 (Trust Services Criteria), HIPAA (administrative, physical and technical safeguards for electronic protected health information) and GDPR (data minimisation, data subject rights and cross‑border transfers). Many controls (for example, encryption, access control and monitoring) are common across frameworks, which means the evidence you collect for ISO 27001 can often serve other compliance efforts. This cross‑framework synergy is critical for vendors that support multiple compliance obligations.
Key Components and Best Practices for Endpoint Security under ISO 27001
The following components form a practical checklist for organizations seeking to meet ISO 27001 Annex A 8.1. Each component contributes to a defence‑in‑depth approach that supports certification readiness and real security.
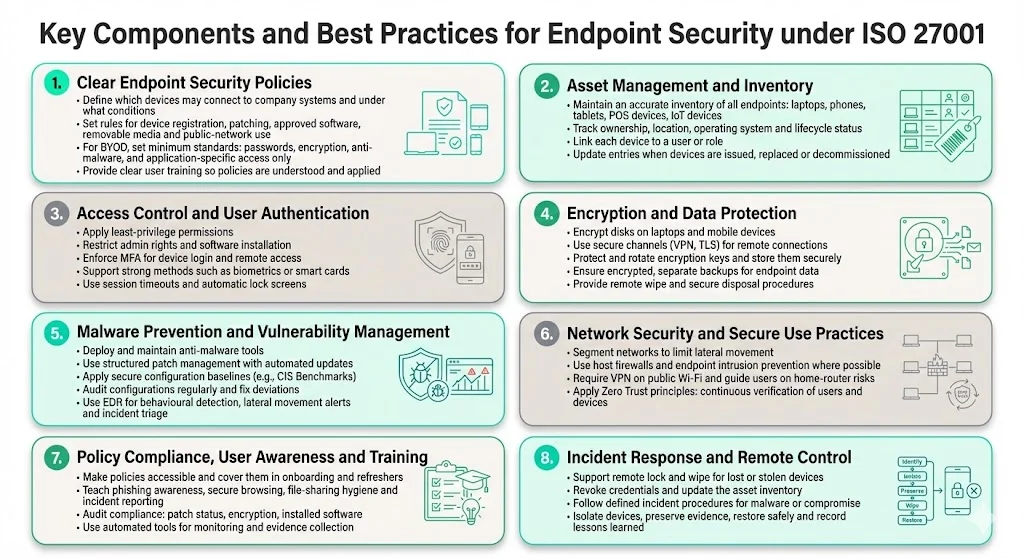
1. Establish Clear Endpoint Security Policies
- Policy scope and acceptable use: Define which devices are permitted (corporate owned vs. personal BYOD), how they may connect (VPN, secure Wi‑Fi), and what classifications of data they may store or process. The policy should cover device registration, approved software, patching requirements, removable media restrictions and rules for connecting to public networks.
- BYOD considerations: For personal devices, specify minimum security requirements (e.g., password protection, encryption, anti‑malware) and clarify whether access is limited to certain applications (VDI, remote desktop, browser‑only). Provide clear instructions for handling sensitive data and prohibitions on storing credentials on personal devices.
- Communication and training: Policies are effective only if users understand them. Provide training on secure device use, phishing awareness and reporting procedures. The AvISO guidance emphasizes that implementing control 8.1 requires a combination of technical and administrative measures, including security training.
2. Asset Management and Inventory
- Maintain an accurate device inventory: Record all endpoint devices that access organizational systems — desktops, laptops, tablets, smartphones, point‑of‑sale terminals and IoT devices. Track device ownership, location, operating system and status. Asset management is highlighted as a key takeaway by HighTable: understanding what devices exist is fundamental to protecting them.
- Associate devices with users and roles: Link each device to the individual or role that uses it. This helps with access control reviews, privileged account management and incident response. Update the inventory promptly when devices are issued, returned, replaced or decommissioned.
3. Access Control and User Authentication
- Least privilege principle: Grant users only the permissions they need. Restrict administrative privileges, installation rights and access to sensitive data. Regularly review privileges to remove or adjust unnecessary rights.
- Strong authentication: Implement multi‑factor authentication (MFA) for device logins and remote access. Where appropriate, use biometrics, smart cards or passkeys. NIST emphasises that teleworkers rely on remote access technologies; enforcing MFA reduces the risk of credential compromise.
- Session and idle timeout controls: Require devices to lock automatically after periods of inactivity and require user re‑authentication to resume work. This helps mitigate the risk of unauthorized access when devices are unattended.
4. Encryption and Data Protection
- Full‑disk encryption: Encrypt storage on laptops and mobile devices to protect data at rest. If devices are lost or stolen, encryption prevents unauthorized parties from reading the data. The HighTable guidance lists encryption as a primary technical control.
- Secure transmission: Use virtual private networks (VPNs) or secure channels (TLS) for remote connections. Ensure data in transit is protected when synchronizing with cloud services or accessing internal resources.
- Key management and backup: Manage encryption keys securely (hardware security modules, key rotation) and back up keys. Implement secure backup mechanisms for endpoint data and ensure backups are encrypted and stored separately.
- Secure disposal and remote wipe: Provide remote wipe capabilities to erase data on lost or stolen devices. Define procedures for wiping devices prior to reuse or retirement.
5. Malware Prevention and Vulnerability Management
- Anti‑malware solutions: Install and maintain anti‑virus and anti‑malware software on all endpoints. Keep signatures and engines up to date. The AvISO guidance explicitly calls for anti‑malware software.
- Patch management: Establish processes for timely operating system and application updates. Automate updates where possible and monitor patch status. Unpatched software is a common entry point for attackers.
- Configuration baselines: Develop secure configuration baselines (e.g., CIS Benchmarks) and deploy them through configuration management tools. Regularly audit configurations and remediate deviations.
- Endpoint detection and response (EDR): Use EDR solutions to detect malicious behaviour, lateral movement and unusual access patterns. Integrate EDR alerts with your security information and event management (SIEM) or managed detection services to enable rapid response.
6. Network Security and Secure Use Practices
- Network segmentation: Restrict endpoints to appropriate network segments to limit lateral movement if a device is compromised. Use host‑based firewalls and intrusion prevention systems where feasible. AvISO suggests segmenting networks to restrict endpoint movement.
- Public and home networks: Provide guidelines for connecting to public Wi‑Fi; require VPN use and encourage avoidance of untrusted networks. Remote work guidance from 360 Advanced highlights that home routers and public Wi‑Fi can be insecure.
- Zero Trust principles: Many organizations are moving towards Zero Trust architectures. In remote environments, assume no device or user is inherently trusted; continuously verify identities and device health before granting access.
7. Policy Compliance, User Awareness and Training
- Communicate policies: Make policies easily accessible and include them in onboarding and periodic refreshers. Provide examples of acceptable and prohibited device usage.
- Security awareness: Train employees on phishing, social engineering, safe browsing, secure file sharing and incident reporting. 360 Advanced notes that remote work has amplified phishing attacks; training helps employees recognise malicious attempts.
- Auditing and monitoring: Conduct regular audits of device compliance, patch status, encryption and installed software. Retain evidence (logs, screenshots, reports) for internal and external audits. Use automated tools to track compliance metrics.
8. Incident Response and Remote Control
- Lost or stolen devices: Plan for device loss by enabling remote lock and wipe capabilities, revoking credentials and updating your asset inventory. Consider geolocation tracking where legally permitted.
- Malware or compromise: Integrate endpoint alerts with your incident response (IR) process. Define procedures for isolating affected devices, collecting forensic evidence, restoring from backups and reporting incidents.
- Lessons learned: After an incident, update policies, controls and training. Document the incident response steps and improvement actions.
Step‑by‑Step Roadmap for Implementation in 2026
To build ISO 27001‑compliant endpoint security, follow these stages. Timelines may vary by organization size and complexity; typical readiness windows for SOC 2 or ISO 27001 certification with Konfirmity are 4–5 months, compared with 9–12 months when self‑managed. We reduce internal effort from more than 550 hours to roughly 75 hours per year by executing controls on your behalf.
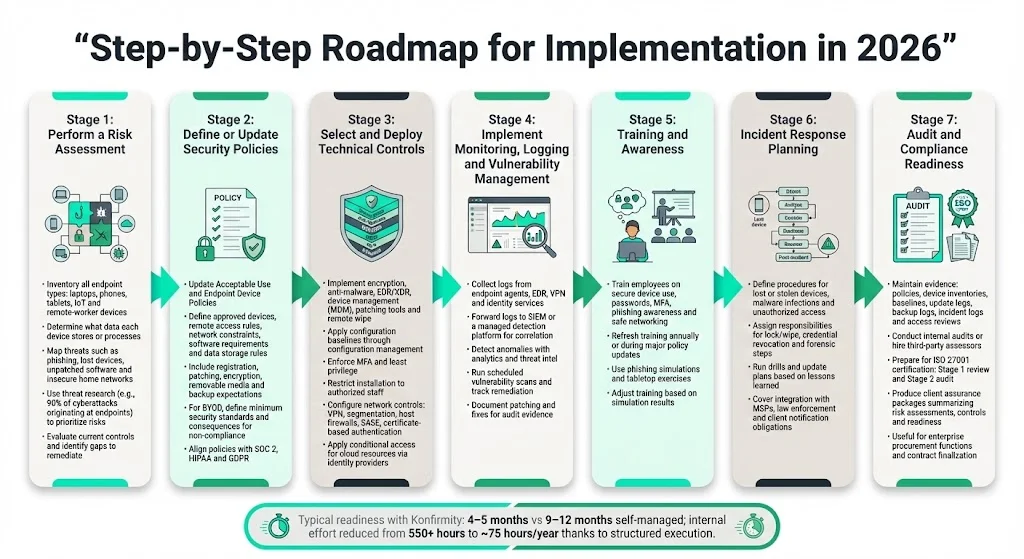
- Perform a Risk Assessment:
- Inventory endpoints: Identify all devices (existing and planned) that access corporate systems. Include desktops, laptops, tablets, smartphones, IoT devices and any device used by remote workers or contractors.
- Classify data: Determine what data each device stores or processes (e.g., personal data, intellectual property, regulated data). Map risks such as theft, malware, unauthorized access and data leakage.
- Identify threats and vulnerabilities: Consider scenarios such as phishing, lost devices, unpatched software and compromised home networks. Use resources like the Verizon Mobile Security Index (which found that 90 % of successful cyberattacks originate at endpoint devices) to prioritise threats.
- Assess existing controls: Evaluate current controls (encryption, patch management, EDR) and identify gaps. Prioritize remediation based on risk severity and business impact.
- Inventory endpoints: Identify all devices (existing and planned) that access corporate systems. Include desktops, laptops, tablets, smartphones, IoT devices and any device used by remote workers or contractors.
- Define or Update Security Policies:
- Acceptable Use Policy and Endpoint Device Policy: Draft or update policies to reflect approved devices, network usage, remote access requirements, data storage rules, classification mapping and behaviour expectations. Include procedures for device registration, software installation and updates, remote access, removable media control, encryption and backups.
- BYOD Policy: If personal devices are allowed, define minimum security requirements, corporate oversight and consequences for non‑compliance.
- Policy integration: Ensure policies align with other frameworks (SOC 2, HIPAA, GDPR). For example, HIPAA requires administrative and technical safeguards for electronic protected health information, which include encryption and audit logging.
- Acceptable Use Policy and Endpoint Device Policy: Draft or update policies to reflect approved devices, network usage, remote access requirements, data storage rules, classification mapping and behaviour expectations. Include procedures for device registration, software installation and updates, remote access, removable media control, encryption and backups.
- Select and Deploy Technical Controls:
- Endpoint protection stack: Implement full‑disk encryption, anti‑malware software, EDR/extended detection and response (XDR), device management (MDM), patch management tools and remote wipe capabilities. Deploy configuration management to enforce baselines.
- Access controls: Enforce least privilege, MFA and strong authentication. Restrict installation privileges to authorized personnel. Review and revoke privileges regularly.
- Network controls: Configure VPN, host‑based firewalls, network segmentation, secure access service edge (SASE) and restrict public network connections. Consider disabling untrusted networks and enforcing certificate‑based authentication.
- Cloud integration: For devices accessing cloud resources, integrate with identity providers (IdP) and implement conditional access policies (device compliance checks before granting access).
- Endpoint protection stack: Implement full‑disk encryption, anti‑malware software, EDR/extended detection and response (XDR), device management (MDM), patch management tools and remote wipe capabilities. Deploy configuration management to enforce baselines.
- Implement Monitoring, Logging and Vulnerability Management:
- Monitoring: Collect logs from endpoint agents, EDR systems, VPN gateways and identity providers. Forward logs to a central SIEM or managed detection platform for correlation and analysis.
- Anomaly detection: Use analytics and threat intelligence feeds to detect unusual activities (e.g., repeated login failures, unusual file transfers). IBM’s threat intelligence report notes that infostealer deliveries via phishing increased by 84 %ibm.com, underscoring the need for real‑time monitoring.
- Vulnerability management: Run scheduled scans to identify missing patches and misconfigurations. Track vulnerabilities (CVEs) and prioritise patching based on severity (CVSS scores) and asset criticality. Document remediation activities for audit evidence.
- Monitoring: Collect logs from endpoint agents, EDR systems, VPN gateways and identity providers. Forward logs to a central SIEM or managed detection platform for correlation and analysis.
- Training and Awareness:
- Initial and periodic training: Educate employees on secure endpoint use, password hygiene, MFA, phishing identification, safe network practices and incident reporting. Reinforce training at least annually or when major policy updates occur.
- Simulations: Conduct phishing simulations and tabletop exercises to assess readiness. Use results to adjust training content.
- Initial and periodic training: Educate employees on secure endpoint use, password hygiene, MFA, phishing identification, safe network practices and incident reporting. Reinforce training at least annually or when major policy updates occur.
- Incident Response Planning:
- Integrate endpoints in IR procedures: Define steps for handling lost or stolen devices, malware infections and unauthorized access. Document who is responsible for remote wipe, credential revocation, forensic analysis and notification.
- Testing and updates: Test the IR plan through drills and update it based on lessons learned. Ensure the plan covers integration with third parties (e.g., managed services providers, law enforcement) and contractual obligations (e.g., breach notifications to clients within a defined timeframe).
- Integrate endpoints in IR procedures: Define steps for handling lost or stolen devices, malware infections and unauthorized access. Document who is responsible for remote wipe, credential revocation, forensic analysis and notification.
- Audit and Compliance Readiness:
- Evidence collection: Maintain documentation such as policy documents, device inventories, configuration baselines, update logs, backup logs, incident logs and access review records. Evidence is required to demonstrate compliance during certification audits and client assessments.
- Internal audits: Conduct internal or third‑party audits to evaluate control effectiveness. Use these audits to refine your Statement of Applicability.
- External certification: If pursuing ISO 27001 certification, prepare for a Stage 1 documentation review and Stage 2 compliance audit. Certification bodies will check that you have implemented the selected controls, maintained records and followed the ISMS processes.
- Client assurance: For vendors serving enterprise clients, compile a security posture report summarising your endpoint security program. Provide evidence of risk assessments, policies, technical controls, monitoring, training and incident response. Many large customers require such evidence before finalizing contracts.
- Evidence collection: Maintain documentation such as policy documents, device inventories, configuration baselines, update logs, backup logs, incident logs and access review records. Evidence is required to demonstrate compliance during certification audits and client assessments.
Common Challenges and Pitfalls
Even with a roadmap, organizations often struggle to implement strong endpoint security. Here are typical pitfalls and how to avoid them.
- Out‑of‑date inventory: Failing to maintain an accurate device list leads to unmanaged devices connecting to the network. Automated discovery tools and periodic audits can help identify unregistered devices.
- Policy enforcement gap: Policies without enforcement are ineffective. Use device management tools to enforce configurations, block unauthorized software and require compliance before granting network access.
- Lack of encryption and remote wipe: Devices without encryption remain vulnerable if lost or stolen. Ensure encryption is enabled by default and remote wipe is available.
- Inadequate user training: Human error is still a leading cause of breaches. Without regular awareness training, employees may ignore policies or fall for phishing. Combine education with simulated phishing campaigns.
- Delayed patching and weak vulnerability management: Attackers exploit unpatched vulnerabilities. Automate patch management and monitor compliance. Use risk‑based prioritization to address critical issues first.
- Siloed endpoint security: Endpoint protection must integrate with other ISMS processes (risk assessment, incident response, vendor management). A fragmented approach leads to gaps and inconsistencies.
Why This Matters for Companies Serving Enterprise Clients
Companies selling to large clients operate under scrutiny. Procurement teams evaluate vendors not only on product capabilities but also on how they manage data and systems. Having strong endpoint security aligned with ISO 27001 offers several advantages:
- Accelerated sales cycles: Enterprise buyers often require security questionnaires, SOC 2 reports or ISO 27001 certificates before committing. By presenting a robust endpoint security program with documented controls, you reduce follow‑up questions and negotiation time.
- Reduced risk and liability: Endpoint breaches can lead to data theft, regulatory penalties and contract breaches. Strong controls reduce the likelihood and impact of incidents, protecting your reputation and bottom line.
- Competitive differentiation: Many vendors claim compliance but lack operational security. At Konfirmity, we implement controls within your stack and provide continuous monitoring and evidence collection. Our human‑led service means dedicated experts manage your program year‑round, not just during audit season. This reduces internal workload by about 75 % and results in fewer audit findings.
- Cross‑framework efficiency: Because endpoint security controls overlap with SOC 2, HIPAA and GDPR requirements, investing in an ISO 27001 program yields benefits across multiple frameworks. For example, encryption, MFA and audit logging satisfy SOC 2 Security and HIPAA technical safeguards, while also demonstrating GDPR accountability.
Conclusion
Endpoint devices are the front lines of a distributed workforce. Attacks targeting these devices can pivot into your network and compromise sensitive data. ISO 27001 and ISO 27002 provide a structured framework to manage this risk, with Annex A 8.1 expressly directing organizations to protect information on or accessed through user endpoint devices. The rise of remote work and BYOD makes endpoint security more important than ever; remote‑work breaches cost more and occur more often.
Meeting ISO 27001 Endpoint Security For ISO 27001 is not about ticking a box. It requires clear policies, comprehensive asset management, strict access controls, encryption, proactive threat detection, continuous monitoring, user training, incident response readiness and audit evidence. When these components are executed thoughtfully, they provide real protection and generate the documentation required for certification and client assurance. Companies serving enterprise clients will find that a mature endpoint security program not only meets ISO 27001 requirements but also builds trust, accelerates sales and protects the organisation against evolving threats.
Security that reads well but fails under real‑world pressure is a liability. Invest in controls that stand up to buyers, auditors and attackers alike. Start with security, operate it daily and let compliance follow.
FAQ
1. What are the three main types of endpoint security?
Endpoint security controls fall into three broad categories:
- Preventive controls – Measures that stop threats before they occur. These include access control, MFA, encryption, secure configuration, device hardening and patch management.
- Detective controls – Mechanisms that identify potential or actual malicious activity. Examples include anti‑malware software, EDR, SIEM monitoring, log analysis and anomaly detection.
- Corrective and responsive controls – Actions taken to remediate incidents or restore normal operations. Examples include remote wipe, incident response procedures, backups and software updates. Together, these categories provide layered defences.
2. Does ISO 27001 require Data Leakage Prevention (DLP)?
ISO 27001 does not mandate specific products or technologies. Annex A controls are selected based on risk. Data leakage prevention is not explicitly required by ISO 27001:2022, but it can support several controls. For example, Annex A 8.1 suggests technical measures such as endpoint device management and data loss prevention to control the use of portable storage and prevent sensitive data from leaving the organisation. Organisations processing regulated or sensitive data often implement DLP tools as part of their data protection strategy.
3. What is the ISO 27001 standard for security?
ISO 27001 is a management system standard for information security. It requires organisations to define the scope of their ISMS, perform risk assessments, implement risk treatment plans, select and justify controls (Annex A), monitor performance through internal audits and management reviews, and continually improve. Unlike prescriptive frameworks, ISO 27001 is risk‑based and allows organisations to tailor controls to their context. Compliance is evidenced through documentation, records and periodic audits by accredited certification bodies.
4. Does ISO 27001 require encryption at rest?
ISO 27001 does not mandate encryption in all situations. The requirement arises when an organisation stores personal, sensitive or classified data on endpoint devices. Annex A 8.1 recommends protecting information on user devices, and encryption is widely accepted as the most effective protection for data at rest. Many organisations implement full‑disk encryption, encrypted removable media or encrypted containers to meet this expectation. The risk assessment and data classification process determine where encryption is needed, and the Statement of Applicability documents the decision.





.svg)






.svg)
.svg)