Most enterprise buyers now request assurance artefacts before procurement. Without operational security and continuous evidence, deals stall—even when teams think they’re “ready” on paper. For organisations pursuing ISO 27001 certification, evidence is the proof that the information security management system (ISMS) isn’t just words; it’s working in practice. This article explains why the ISO 27001 Evidence Collection Templates approach helps busy enterprises‑selling teams stay audit‑ready.
We’ll describe what evidence means within ISO 27001, list common evidence types, offer a step‑by‑step guide for implementing templates, discuss example templates tailored for enterprise contexts, identify common pitfalls, and finish with a practical checklist. The recommendations draw on industry data, standards guidance, and Konfirmity’s experience from over 6,000 audits across 25+ years.
Why evidence collection matters for enterprise sellers
ISO 27001 certification is a recognised trust signal in B2B sales. Enterprise customers increasingly require certified suppliers and request proof during procurement or vendor assessments. Research published in 2025 on data breach costs shows that the average breach cost globally reached USD 4.88 million in 2024, up 10% from the prior year. Breach costs rise as incidents linger longer, and they are higher in regulated industries such as healthcare (USD 9.77 million in the United States). Buyers know that weak security can lead to downtime, fines, and reputational damage. They therefore ask vendors to demonstrate controls, not just share a policy.
In the context of ISO 27001, evidence collection means systematically gathering logs, records, policies, and audit results to prove that controls are designed, implemented, and effective. Clause 5.2 of ISO 27001 requires top management to establish, approve, and communicate an information security policy aligned with the organisation’s strategic direction and risk posture. Clause 4.2 asks organisations to identify interested parties (customers, regulators, suppliers) and understand their security requirements. Annex A 5.28 further emphasises that organisations must have clear procedures for identifying, collecting, acquiring, and preserving evidence related to information security events. These requirements mean evidence isn’t optional. Enterprise clients will ask to see that access controls, risk assessments, and incident management logs are real and up to date.
What are ISO 27001 Evidence Collection Templates?
ISO 27001 Evidence Collection Templates are structured worksheets or forms that help teams capture and organise the proof required by ISO 27001 clauses and controls. Instead of scrambling to gather documents during an audit or client questionnaire, a template‑driven approach standardises how evidence is documented, stored, and linked to controls. Evidence templates typically include fields for dates, owners, version history, links to underlying documents, and status. By centralising this information, organisations can respond quickly to auditors, reduce internal confusion, and onboard new systems or vendors with clarity. For enterprise sellers facing procurement questionnaires and vendor due‑diligence, having templates means being able to produce consistent proof on demand.
This article uses the term ISO 27001 Evidence Collection Templates to refer to these repeatable artefacts. They should not be confused with cookie‑cutter policies; Clause 5.2 warns that generic, copy‑pasted policies undermine trust and that the board must own and tailor policies. Templates provide structure but must be populated with organisation‑specific details.
Why a template‑driven approach makes sense for enterprise B2B teams
Implementing ISO 27001 Evidence Collection Templates is essential for enterprise B2B teams because it provides a standard way to capture evidence across many control areas. This phrase will recur throughout this article because the concept underpins every recommendation that follows.
Enterprise‑selling companies operate complex environments. Sales, engineering, operations, and security teams juggle multiple stakeholders, a large technology stack, and dozens of control areas. When a big customer requests an audit or a detailed security questionnaire, teams often scramble to pull logs, policies, and screenshots. This chaos leads to inconsistent evidence, gaps, and wasted hours.
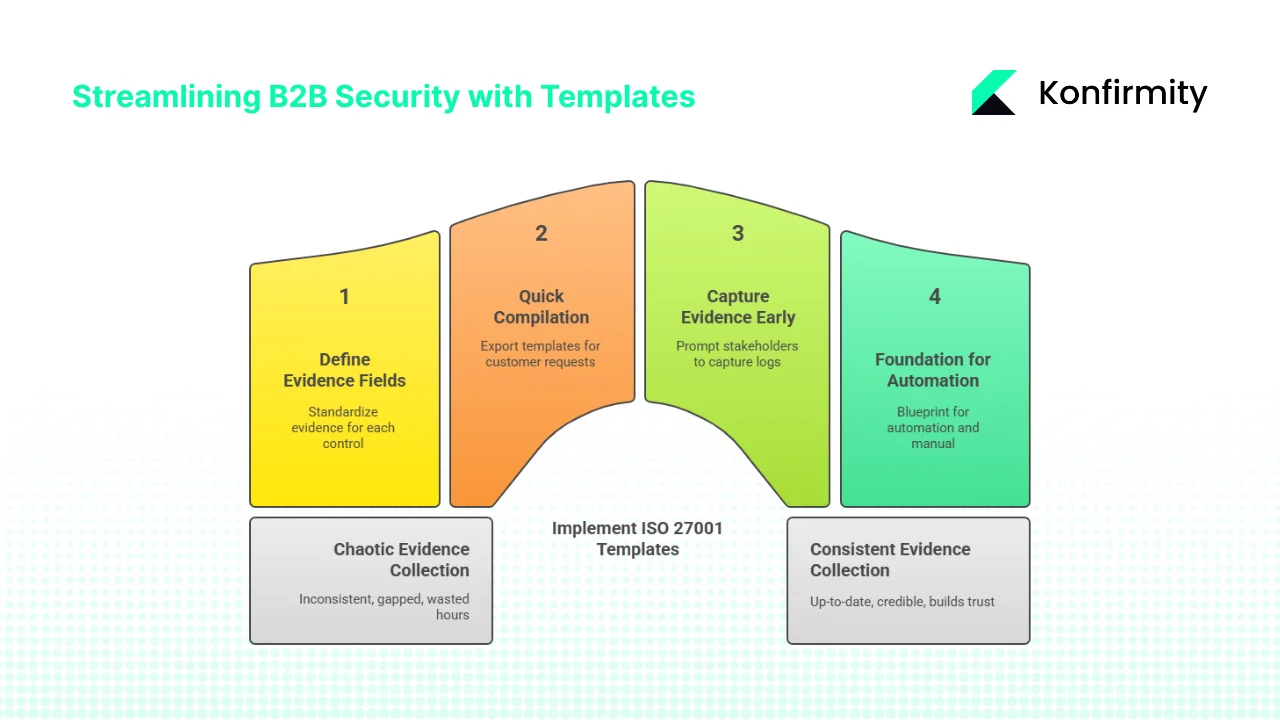
A template‑driven approach delivers several benefits:
- Consistency across controls: Templates ensure each control area—risk assessment, access review, incident response—has a defined set of evidence fields. This prevents omissions and makes audits smoother.
- Faster responses: When procurement teams ask for proof, templates allow quick compilation without starting from scratch. For example, an internal audit checklist template can be exported for a customer request.
- Lower onboarding friction: When adopting new systems or vendors, templates prompt stakeholders to capture the right evidence (e.g., access logs) from day one.
- Foundation for automation: Automation tools can pull logs and populate templates, but without a standard template to map to, automation becomes brittle. Templates provide the blueprint for automation and manual processes.
- Enterprise trust: Being able to show up‑to‑date evidence builds credibility with clients. As the Morgan Lewis article notes, data breaches with lifecycles longer than 200 days cost an average of USD 5.46 million. Demonstrating continuous monitoring and evidence collection reassures buyers that incidents will be detected and contained quickly.
Konfirmity’s experience across 6,000+ audits shows that enterprise sellers who implement templates and continuous evidence collection reduce audit preparation time by 75%, often achieving SOC 2 readiness in 4–5 months compared with 9–12 months for self‑managed programs. In our managed service, clients spend about 75 hours per year on evidence tasks, whereas self‑managed programs consume 550–600 hours. These numbers come from actual delivery work and illustrate the operational savings of a structured approach.
When combined with disciplined ownership and regular reviews, ISO 27001 Evidence Collection Templates make compliance a natural result of good security practices.
Key evidence types
Evidence spans many records and artefacts. Below are common evidence categories, each with a definition, relevance to ISO 27001, a typical template name, and what enterprise teams should capture.
Step‑by‑step guide to using evidence collection templates
The following steps explain how to integrate ISO 27001 Evidence Collection Templates into your compliance workflow.

Step 1: Define scope and responsibilities
Start by defining the ISMS scope (Clause 4.3), listing systems, locations, and processes in and out of scope. Assign ownership for each template: who maintains the asset inventory, who manages training records, and who runs internal audits. Establish a document control process for versioning and approvals. This alignment ensures that evidence reflects actual operations rather than generic text.
Step 2: Map templates to ISO 27001 requirements
Review the ISO 27001 clauses (4–10) and Annex A controls. Create a master matrix mapping each requirement to its supporting template and the person responsible. Include enterprise client requirements, such as vendor due‑diligence requests or customer audit access. This mapping ensures nothing is missed and helps demonstrate alignment with client contracts.
Step 3: Populate initial templates
Gather existing documents and run workshops to fill initial templates. Focus first on critical assets and high‑risk controls; quick wins build momentum. Keep templates lean so busy teams actually use them. Fields like “version”, “owner”, and “evidence link” are more useful than dozens of columns that rarely get filled.
Step 4: Establish regular update and review cycles
Set update frequency based on control criticality. For example, update the asset inventory monthly, access logs daily or weekly, and conduct internal audits quarterly. Schedule non‑conformance reviews following audits and incidents. Maintain version history and retain evidence per policy and contractual requirements; this supports Annex A 5.28’s emphasis on integrity and preservation.
Step 5: Link templates with documentation and evidence storage
Templates should reference where the actual documents live—document repositories, ticketing systems, or compliance portals. Sensitive evidence may require chain‑of‑custody controls; NIST emphasises that handlers must track the chain to ensure evidence has not been compromised. For enterprise customers, ensure the storage environment is audit‑ready and accessible to authorised auditors when requested.
Step 6: Use templates to support internal audit and external certification
During audit preparation, run internal audit checklists to verify that evidence in each template meets ISO 27001 requirements. Use non‑conformance reports to track gaps and corrective actions. When external auditors arrive, be ready to show: the template, the populated data, and the linked evidence for each control. Security vendor Secureframe notes that collecting and organising evidence ahead of an audit prevents last‑minute scramble (this emphasis aligns with Konfirmity’s field observations).
Step 7: Continuous improvement and template evolution
After each audit or incident review, capture lessons learned and update templates accordingly. For example, if a new asset type or training requirement emerges, add fields to the relevant template. Enterprise customer expectations evolve—some clients may demand 12 months of access logs or vendor audit access. Keep templates adaptable. Maintain a version‑controlled library so teams can track changes and rely on consistent definitions.
Example templates and tailoring for enterprise‑selling companies
Below is a list of example template names with suggestions on how to adapt them for enterprise contexts:
Templates can be built in spreadsheets (Excel, Google Sheets) for flexibility, or adopted via cloud‑based platforms and integrated compliance tools. Spreadsheets are simple and cost‑effective but may lack audit logs and access control. Cloud platforms offer version control, user access management, and integration with ticketing or monitoring systems. Automation helps—tools can pull logs and populate fields—but good templates ensure edge cases are covered and busy teams stay organised. Use dropdown lists for repetitive fields, embed links to documents, assign ownership, and add filters for “client impact” to prioritise high‑value data.
Common pitfalls and how to avoid them
- Template overload: Having too many templates or making them overly complex discourages use. Start with the most critical (asset inventory, training register, audit checklist) and expand gradually. Keep each template lean.
- Unclear ownership: Without named owners, templates go stale. Assign responsibility and hold owners accountable. Clause 5.2 encourages visible leadership; apply this to template management.
- Evidence not linked: Templates should include links to actual artefacts. A training record without an attached certificate fails to prove competence. Use a consistent file‑naming convention and store evidence in a central repository.
- Insufficient chain of custody: Evidence must be preserved and protected. NIST guidance states that handlers must ensure evidence isn’t compromised and the chain of custody is tracked. Include chain‑of‑custody fields in incident report templates.
- Ignoring legacy or vendor systems: Evidence collection across legacy systems or third‑party vendors is challenging. Identify all systems in scope during Step 1 and ensure templates cover them. Engage vendors early to obtain logs and reports.
- Misaligned with enterprise expectations: Clients may require access logs for 12 months, but your template may capture only 3 months. Regularly review client security addenda and update templates accordingly.
- Lack of review cycles: Templates and data become stale without scheduled reviews. Use calendars, task management tools, or automation to enforce update cycles.
Checklist: what your team needs to do this week
- Appoint a template lead for the enterprise client business line. This person oversees all evidence collection templates and records.
- Select and customize 3–5 templates (asset inventory, training register, internal audit checklist, risk register, incident report) to suit your business and client needs.
- Map each template to ISO 27001 controls and record who is responsible for each evidence type.
- Populate initial data for high‑risk systems and client‑facing assets. Use existing records and run short workshops with stakeholders.
- Set update schedules and version control. Define who updates each template and when. Establish a central repository with access controls and audit logging.
- Review existing evidence for gaps and plan to collect missing records. Prioritise logs or policies that clients or auditors frequently request.
Conclusion
Evidence is the lifeblood of ISO 27001 certification and enterprise sales. Data breach costs continue to climb—average breach costs rose to USD 4.88 million in 2024—and enterprise buyers are rightly cautious. Being audit‑ready with well‑populated templates shows you’re serious about security. For companies selling to enterprise clients, this isn’t a luxury; it’s a business enabler. Showing strong controls shortens sales cycles, satisfies contractual requirements, and builds trust.
Start with a few high‑value templates, populate them with real data, and assign ownership. Map each template to ISO 27001 clauses and Annex A controls. Update records regularly, link evidence to templates, and track the chain of custody. Use automation wisely but remember that templates are the foundation. With a disciplined, template‑driven evidence program, you won’t scramble during audits or client reviews—you’ll be ready.
With ISO 27001 Evidence Collection Templates and disciplined processes, you will be ready for audits and client reviews.
FAQ
1) What is the ISO 27001 collection of evidence?
The ISO 27001 collection of evidence refers to the process and artefacts by which an organisation gathers, preserves, and presents proof that its ISMS and controls are designed, implemented, and effective. Evidence includes system logs, policy documents, audit records, training certificates, risk assessments, and incident reports. Annex A 5.28 requires clear procedures for identifying, collecting, acquiring, and preserving evidence. Proper evidence collection supports investigations, audits, and legal proceedings and ensures that controls can be demonstrated to clients and auditors.
2) What is Clause 5.2 of ISO 27001?
Clause 5.2 relates to the information security policy. It requires top management to establish, approve, and communicate a policy aligned with the organisation’s strategic direction, risk posture, and compliance obligations. The policy must be documented, maintained, accessible to relevant parties, and regularly reviewed. The clause emphasises that the board must actively shape and review the policy, not simply rubber‑stamp it.
3) What is the ISO 27001 data classification policy template?
A data classification policy template defines how information is categorised (e.g., public, internal, confidential, restricted), who assigns classification, how labels are applied, and how information is handled and disposed of. The template helps organisations implement controls linked to Annex A controls on classification and access control. A good template includes classification levels, responsible roles, handling instructions, retention periods, and links to training records. When properly used, it generates evidence that data is classified and handled according to policy.
4) What is Clause 4.2 of ISO 27001?
Clause 4.2 is titled “Understanding the needs and expectations of interested parties.” It requires organisations to identify the stakeholders relevant to their ISMS (customers, regulators, employees, suppliers, shareholders) and understand what those parties require regarding information security. Organisations must determine which of these requirements will be addressed through the ISMS and document them. This clause ensures that the ISMS is context‑aware, aligns with stakeholder needs, and forms a credible basis for risk assessment.





.svg)






.svg)
.svg)