Most organizations pursuing ISO 27001 certification focus on control implementation while underestimating evidence collection—a gap that becomes immediately apparent when enterprise buyers request audit trails, security logs, or documented proof of operational controls. ISO 27001 Clause 7.5 requires organizations to create and maintain documented information necessary for the effective operation of their Information Security Management System (ISMS), yet vendors routinely face delayed sales cycles or failed audits because they cannot produce comprehensive, organized evidence when required.
This disconnect carries measurable consequences. Enterprise procurement teams increasingly demand evidence-based security validation before contract execution—not aspirational statements about security posture, but verifiable proof that controls function as designed. Organizations without structured evidence collection invest 550-600 hours annually managing compliance reactively, scrambling to reconstruct documentation during vendor assessments or certification audits.
This article provides the technical framework companies selling to enterprise clients need to establish systematic evidence collection across documentation, audit trails, records management, security controls evidence, risk assessment records, training documentation, incident reports, compliance documentation, monitoring logs, and access control records. You will understand what ISO 27001 evidence requirements mean operationally, why they matter for enterprise sales readiness, the precise steps to implement evidence collection, and access to checklists and templates designed to accelerate deployment.
What the Standard Requires: Core ISO 27001 Evidence Concepts
ISO 27001 establishes requirements for an Information Security Management System (ISMS), with Clause 7.5 requiring organizations to maintain documented information necessary for effective ISMS operation. The standard distinguishes between documented information required by the standard itself and information your organization determines necessary for ISMS effectiveness. Your ISMS must meet both Clauses 4-10 requirements and security controls defined in Annex A, which outlines 93 controls grouped into four categories—organizational, people, physical, and technological.

ISO 27001 Annex A contains 93 controls organized into four domains, each requiring specific evidence of implementation and operational effectiveness. Annex A is normative—not informative—making it a mandatory component of the standard. Organizations must document which controls apply to their environment through the Statement of Applicability (SoA) and provide justification for any exclusions.
Evidence vs Documentation vs Records: Critical Distinctions
Why Enterprise Clients Demand Evidence-Based Validation
Enterprise procurement teams require evidence including certifications, audit reports, and process documentation rather than yes/no questionnaire responses. This approach reflects a fundamental shift from trust-based to evidence-based vendor risk assessment. Additional third-party due diligence may require penetration test results and compliance certifications such as SOC or HITRUST.
Enterprise organizations face regulatory obligations that cascade to vendors. Regulations including HIPAA and PCI DSS require vendor compliance, making vendor security posture a direct compliance concern. Organizations cannot outsource compliance risk; they must verify vendor controls through documented evidence. When enterprise procurement requests ISO 27001 certification status, they are validating that your organization maintains systematic, auditable evidence of security control operation—not merely that controls were implemented at some point in the past.
Audit readiness determines sales velocity. Vendors with organized evidence repositories respond to security questionnaires in days rather than weeks, accelerating procurement cycles. Those unable to produce evidence face extended evaluation periods, reduced negotiating leverage, and higher probability of disqualification.
Mapping Your Evidence: What to Collect and How
Effective evidence collection requires systematic mapping across control domains. The following framework organizes evidence types according to ISO 27001 control requirements and enterprise buyer expectations.
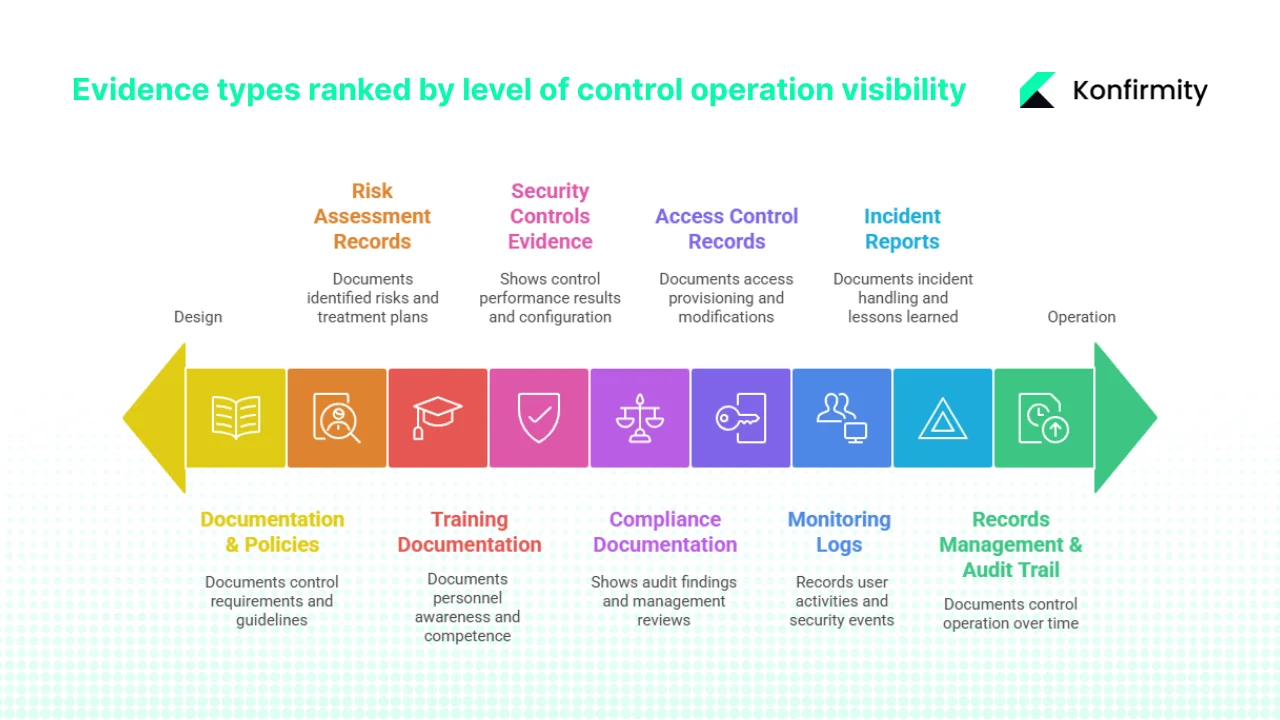
1. Documentation & Policies
Core documented information includes information security policy, asset management policy, access control policy, acceptable use policy, and topic-specific policies addressing control requirements. Mandatory documentation includes ISMS scope, information security policy, risk assessment procedure, Statement of Applicability, risk treatment procedure, information security objectives, and personnel records.
Practical example: A SaaS vendor maintains version-controlled information security policy with documented senior management approval, publication date, review schedule, and communication records to relevant personnel. The policy document includes version history tracking changes, rationale for modifications, and approval signatures.
Template recommendation: Policy template incorporating version control table, approval workflow, document owner designation, review frequency, and communication distribution list.
2. Records Management & Audit Trail
Audit trails document control operation over time. Access control records log who requested access, who approved requests, what access was granted, when implementation occurred, and evidence supporting each transaction. ISO 27001 typically recommends maintaining at least 12 months of logs to demonstrate control effectiveness, with PCI DSS mandating 12 months of history.
Practical example: Access management system generates automated logs capturing access request submission, approval workflow routing, manager authorization, provisioning actions, and access review cycles. Records include requestor identity, business justification, approved access level, implementation timestamp, and quarterly access recertification results.
Template recommendation: Audit trail spreadsheet with standardized fields including date/time stamp, user identifier, action performed, system affected, approver identity, and supporting evidence reference.
3. Security Controls Evidence
Evidence can be gathered from seeing the results of control performance, including system configuration exports, vulnerability scan results, patch management logs, firewall rule documentation, and security tooling output. Controls require both design evidence (documentation) and operating effectiveness evidence (records).
Practical example: Vulnerability management program evidence includes vulnerability scan output, risk-scored findings, remediation tracking logs, patching schedules, exception approvals for risk acceptance, and closure verification. Evidence demonstrates systematic vulnerability identification, prioritization, remediation, and validation.
Template recommendation: Control evidence checklist cross-referencing each Annex A control to required evidence types, collection frequency, responsible party, storage location, and current status.
4. Risk Assessment Records
Risk assessment reports and risk treatment plans constitute mandatory ISMS documentation. Risk registers document identified risks, likelihood and impact scoring, inherent risk calculation, selected treatment approach, implemented controls, residual risk assessment, risk ownership, and review schedule.
Practical example: Risk register identifies vendor management as medium-likelihood, high-impact risk. Treatment plan documents implementation of vendor risk assessment process, due diligence requirements, contract security clauses, and ongoing monitoring. Residual risk assessment demonstrates risk reduction to acceptable threshold following control implementation.
Template recommendation: Risk assessment worksheet incorporating risk identification, threat/vulnerability analysis, likelihood and impact scoring matrix, risk treatment options, control mapping, residual risk calculation, and review frequency.
5. Training Documentation
Personnel awareness and competence evidence includes training attendance records, course completion certificates, assessment results, training material versions, and periodic recertification. Clause 7.3 Awareness, while not explicitly requiring documented information, necessitates evidence of awareness program implementation.
Practical example: Security awareness program maintains training roster documenting employee names, training completion dates, module topics, assessment scores, and annual recertification status. Records demonstrate universal participation and comprehension validation.
Template recommendation: Training log capturing employee identifier, training date, course title, delivery method, assessment score, certificate issuance, and next recertification due date.
6. Incident Reports
Incident management evidence documents detection, response, containment, eradication, recovery, and lessons learned. Records demonstrate systematic incident handling aligned with documented procedures.
Practical example: Security incident record documents initial detection timestamp, incident classification, affected systems, response team activation, containment actions, root cause analysis, remediation steps, communication timeline, and post-incident review findings with corrective actions.
Template recommendation: Incident report form with structured sections for incident timeline, impact assessment, response actions, stakeholder notifications, root cause determination, and improvement recommendations.
7. Monitoring Logs
ISO 27001 Control A.12.4.1 requires organizations to produce, maintain, and regularly review logs recording user activities, exceptions, and security events. System logs, security event logs, intrusion detection output, access logs, and administrative action logs provide evidence of continuous monitoring.
Practical example: Security information and event management (SIEM) system aggregates logs from firewalls, authentication systems, application servers, and cloud infrastructure. Monitoring logs include timestamp, event classification, severity rating, affected systems, and disposition status.
Template recommendation: Monitoring log schema defining required fields (timestamp, source system, event type, severity, user/process, disposition) with retention period specifications.
8. Access Control Records
Access provisioning, modification, and revocation require documented evidence. Access rights printouts signed by authorizing officials constitute acceptable evidence. Periodic access reviews validate that granted access remains appropriate.
Practical example: Quarterly access review extracts current user permissions from identity management system. Security team validates each access grant against role requirements, identifies inappropriate access, documents remediation actions, and obtains management sign-off on review completion.
Template recommendation: Access control review matrix listing user identity, assigned role, current permissions, last review date, review outcome, required actions, and reviewer attestation.
9. Compliance Documentation
Internal audit programs, audit reports, and management review reports constitute mandatory documented information. Compliance evidence includes internal audit findings, corrective action tracking, management review minutes, and external audit reports.
Practical example: Annual internal audit evaluates ISMS conformance across selected controls. Audit report documents scope, methodology, findings classification (conformity/nonconformity/opportunity for improvement), corrective action requirements, and management response. Management review evaluates audit findings, determines strategic direction, and documents improvement commitments.
Template recommendation: Audit report template incorporating executive summary, scope definition, methodology description, detailed findings with evidence references, corrective action requirements, and management response documentation.
Practical Steps for Busy Teams
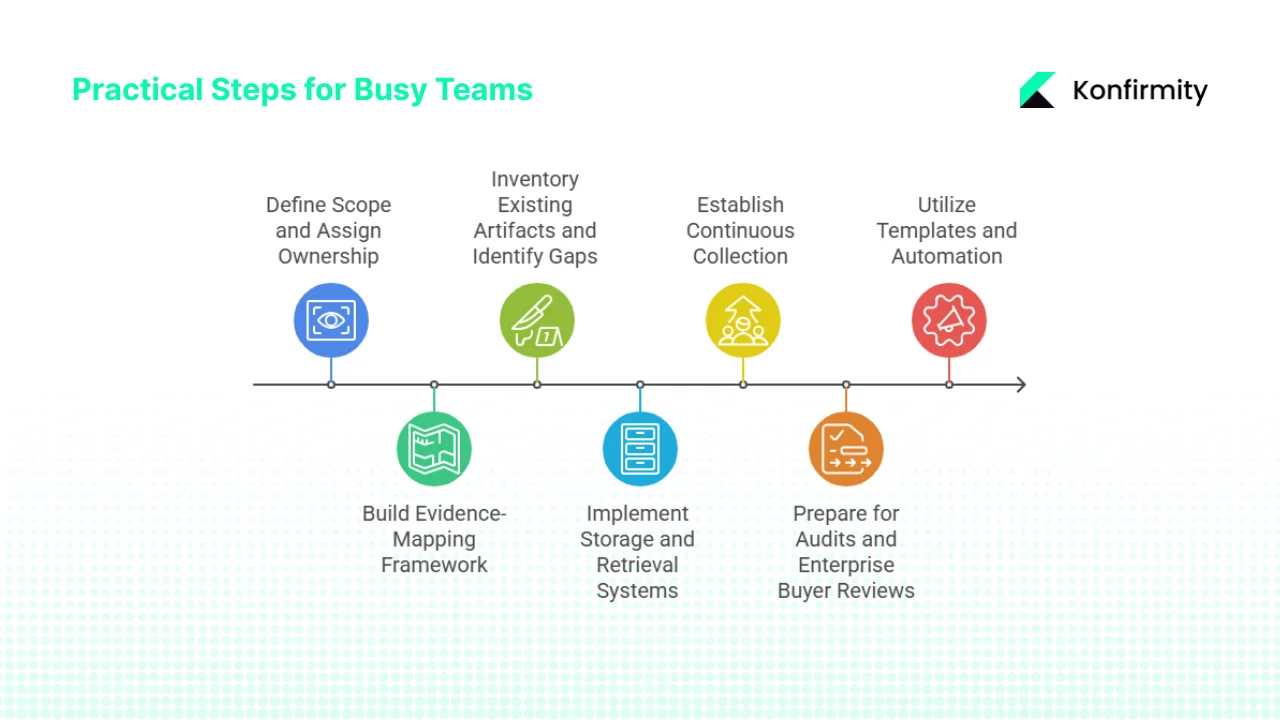
Step 1: Define Scope and Assign Ownership
Organizations must understand their internal and external context, including relevant stakeholders and expectations, to develop an effective ISMS tailored to organizational context. Determine which assets, processes, systems, and locations fall within ISMS scope. Establish clear ownership for evidence collection across control domains.
Create a RACI (Responsible, Accountable, Consulted, Informed) matrix documenting evidence collection responsibilities. IT operations may own monitoring logs; human resources own training records; and the security team owns risk assessments. Accountability prevents gaps where critical evidence goes uncollected because no function assumes ownership.
Step 2: Build Evidence-Mapping Framework
Map each Annex A control applicable to your organization to required evidence types. Use a tracking mechanism—spreadsheet or compliance platform—documenting control reference, control description, required evidence, collection frequency, responsible party, current status, and identified gaps.
Example mapping: Control A.9.2 (User access management) maps to evidence including access request forms, approval workflow records, provisioning logs, periodic access review documentation, and access revocation records. Tracking indicates IT operations collects provisioning logs automatically; security conducts quarterly access reviews requiring manual evidence compilation.
Step 3: Inventory Existing Artifacts and Identify Gaps
Most organizations possess substantial evidence requiring only organization and systematization. Conduct evidence inventory across departments identifying existing policies, procedures, logs, records, and reports potentially satisfying evidence requirements.
Gap analysis identifies missing evidence and implementation priorities. Prioritize evidence supporting high-risk controls, controls frequently questioned during enterprise due diligence, and mandatory documented information. Address highest-impact gaps first—controls protecting sensitive data, controls required by regulations applicable to target customers, and controls most likely to receive audit scrutiny.
Step 4: Implement Storage and Retrieval Systems
Documented information must be available in relevant format when required and protected to maintain integrity and confidentiality, with consideration for distribution, access, retrieval, storage, and preservation. Establish a secure, organized repository for evidence storage with version control, access restrictions, and retrieval capabilities.
Define retention policies addressing regulatory requirements, contractual obligations, and operational needs. Retention periods vary based on information type and applicable regulations, ranging from one year to 30 years. Document retention schedule specifying how long each evidence type requires preservation.
Implement naming conventions and metadata standards enabling rapid evidence retrieval. Enterprise procurement teams evaluating your organization need immediate access to requested evidence; delays signal poor security operations maturity. Structure evidence repositories mirroring ISO 27001 control framework—auditors and buyers familiar with the standard can navigate intuitively.
Step 5: Establish Continuous Collection
Evidence collection cannot constitute an annual exercise preceding certification audits. ISO 27001 recommends maintaining at least 12 months of logs to demonstrate control effectiveness over time. Continuous evidence generation demonstrates controls operate consistently, not just during audit observation periods.
Automate evidence collection wherever feasible. Modern security tooling, identity management platforms, and SIEM systems generate logs automatically. Training platforms track completion. Vulnerability scanners document findings. Automation reduces manual effort while improving evidence completeness and accuracy.
Schedule recurring evidence collection for items requiring manual compilation: quarterly access reviews, annual policy reviews, management review meetings, internal audits. Calendar reminders tied to responsible parties ensure activities occur as scheduled with resulting documentation preserved systematically.
Step 6: Prepare for Audits and Enterprise Buyer Reviews
Internal audit programs constitute mandatory ISMS documentation. Conduct internal audits testing evidence availability, completeness, and accuracy before external certification audits or enterprise security assessments. Internal audits identify evidence gaps allowing remediation before external scrutiny.
Prepare audit-ready evidence packages for frequently-requested items: current ISO 27001 certificate (once obtained), recent SOC 2 report, penetration test results, vulnerability scan output, business continuity test results, incident response documentation, and key policies. Enterprise buyers consistently request these artifacts; maintaining current, organized versions accelerates response.
Practice evidence retrieval exercises. Select random controls and demonstrate ability to produce complete evidence chains showing control design, implementation, operation, and effectiveness. Smooth evidence retrieval during actual audits or vendor assessments demonstrates security operations maturity.
Step 7: Utilize Templates and Automation
Templates eliminate recreating evidence structures repeatedly. Policy templates with version control frameworks, risk register templates with scoring methodologies, audit report templates with standardized sections, and training log templates with required fields accelerate evidence creation while ensuring consistency.
Compliance platforms automate evidence collection, mapping, and organization. These platforms integrate with security tooling to automatically ingest logs, track control implementation status, maintain evidence repositories, and generate audit reports. For organizations managing multiple frameworks simultaneously—ISO 27001, SOC 2, NIST frameworks—platforms mapping controls across standards reduce duplicative evidence collection.
Even without dedicated platforms, process automation improves evidence management. Automated workflows route access requests through approval chains generating documented audit trails. Scheduled scripts extract system configurations for version control. Integration between ticketing systems and incident response processes automatically captures incident documentation.
Real-World Examples for Enterprise-Selling Teams
Scenario A: SaaS Vendor Selling to Financial Services Enterprise

A SaaS platform provider entered the procurement process with a large financial institution. The buyer's security team issued a 300-question vendor risk assessment requesting evidence including access control procedures, monitoring logs, incident response documentation, and penetration test results.
The vendor maintained organized evidence repository mapping controls to collected evidence. Access control records included access request forms with business justification, manager approval documentation, provisioning logs from identity management system, and quarterly access review results with management attestation. Monitoring logs extracted from the SIEM system demonstrated 12 months of security event collection with documented review procedures.
Evidence package response time: three business days. The vendor's security team retrieved requested evidence from a centralized repository, redacted sensitive details, and compiled a comprehensive response. Rapid, complete response signaled security operations maturity to the buyer, accelerating procurement evaluation and strengthening vendor position in contract negotiations.
Scenario B: Managed Service Provider Responding to Healthcare RFP

A managed IT services provider responded to a request for proposal from a healthcare organization requiring HIPAA compliance validation. RFP demanded evidence of security awareness training, business continuity testing, vendor management procedures, and incident response capabilities.
The MSP provided training logs documenting 100% employee completion of annual HIPAA training with assessment results demonstrating comprehension. Business continuity evidence included documented business impact analysis, recovery time objectives, annual DR test results with lessons learned, and management review of continuity adequacy. Vendor management documentation showed a risk assessment process, vendor security requirements, contract security clauses, and ongoing vendor monitoring procedures.
Before implementing systematic evidence collection, the MSP required 4-6 weeks compiling RFP responses, often submitting incomplete evidence due to missing records. After establishing an evidence-mapping framework with continuous collection, RFP response time decreased to 7-10 days with comprehensive, well-organized evidence packages. Improved response capability increased the win rate on enterprise opportunities by 40% over a 12-month period.
Templates & Toolkits
Implementing comprehensive evidence collection requires documented frameworks and structured templates. The following toolkit components accelerate implementation:
Policy Template: Version-controlled policy framework including document metadata (version, approval date, owner, review frequency), approval workflow documentation, distribution tracking, and revision history.
Evidence Mapping Spreadsheet: Control-to-evidence matrix documenting ISO 27001 Annex A controls, applicable/not applicable determination with justification, required evidence types, collection frequency, responsible party, storage location, and current status.
Training Tracker: Personnel training log capturing employee identifier, training completion date, course title, delivery method, assessment score, certificate number, and next recertification due date.
Access Control Review Matrix: Periodic access validation documentation listing user identity, assigned role, current permissions, business justification, last review date, reviewer identity, review outcome, required corrective actions, and attestation signature.
Incident Report Form: Structured incident documentation capturing detection timestamp, incident classification, affected systems/data, initial response actions, containment measures, root cause analysis, remediation steps, stakeholder communications, and lessons learned with improvement recommendations.
Monitoring Log Schema: Standardized log format defining required fields (timestamp, source system, event type, severity level, user/process identifier, action performed, outcome/disposition) with retention specifications.
Audit Report Template: Internal/external audit documentation framework including executive summary, scope definition, methodology description, detailed findings with evidence references, nonconformity classification, corrective action requirements, management response, and follow-up tracking.
Risk Assessment Worksheet: Risk identification and treatment planning template incorporating threat/vulnerability analysis, likelihood and impact scoring, inherent risk calculation, treatment option selection, control mapping, residual risk assessment, risk ownership assignment, and review frequency.
Organizations should tailor templates to operational context, scope, and applicable regulations. The framework remains consistent; specific content reflects organizational environment, risk profile, and compliance obligations.
Common Mistakes & How to Avoid Them
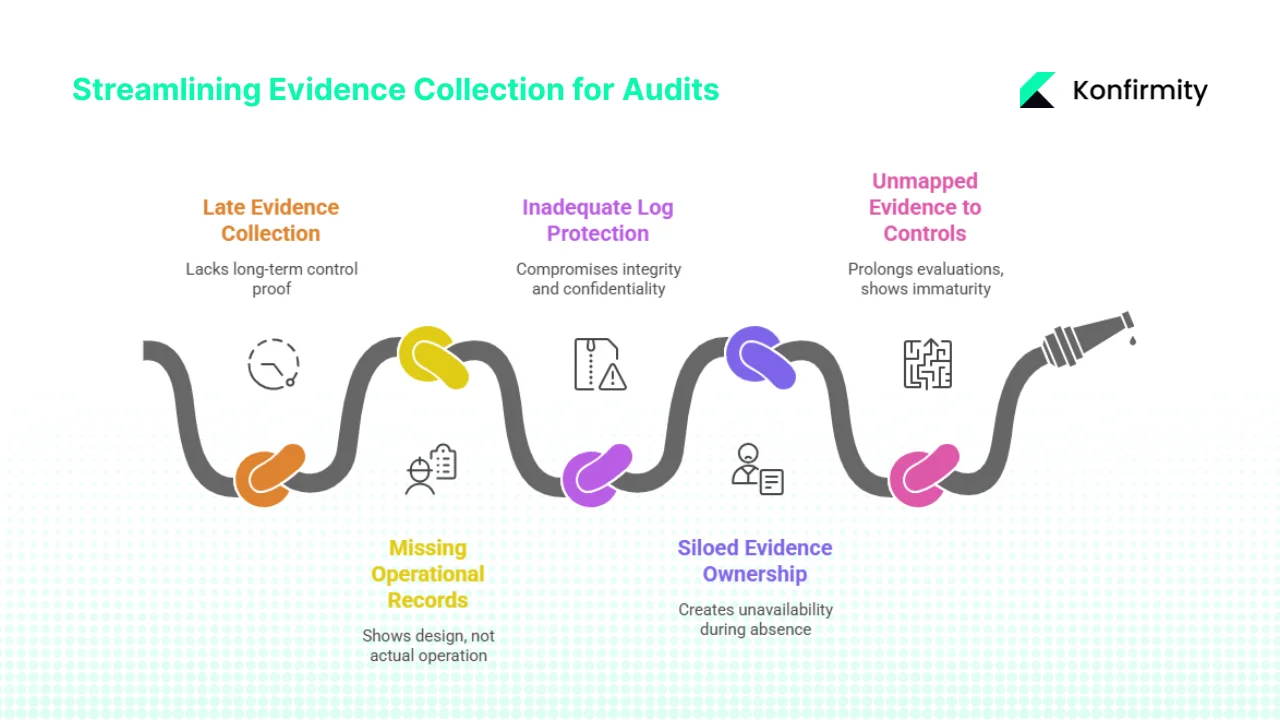
1) Collecting evidence only before audits: Organizations treating evidence collection as pre-audit activity cannot demonstrate control operation over time. ISO 27001 recommends at least 12 months of logs demonstrating control effectiveness. Solution: Implement continuous evidence collection with automated ingestion where possible and scheduled recurring activities for manual evidence.
2) Maintaining policies without operational records: Documentation without corresponding records demonstrates control design but not operation. Auditors require proof controls function as documented. Solution: For every documented procedure, identify resulting records and implement systematic collection.
3) Inadequate log retention or protection: Organizations must ensure documented information is protected to prevent integrity and confidentiality compromise. Logs without adequate retention or modification controls lack audit value. Solution: Implement immutable logging with defined retention periods, access controls restricting log modification, and validation procedures ensuring log integrity.
4) Siloed evidence ownership: When single individuals hold all documentation without organized, accessible storage, evidence becomes unavailable during that person's absence. Solution: Centralized evidence repository with role-based access, documented evidence location mapping, and cross-training ensuring multiple personnel can retrieve evidence.
5) Failing to map evidence to controls: Unorganized evidence collections frustrate auditors and buyers, prolonging evaluations while creating impression of security program immaturity. Solution: Maintain control-to-evidence mapping enabling rapid demonstration of specific control implementation and effectiveness.
How to Scale Evidence for Enterprise Clients
Enterprise buyers in different industries and regulatory environments require tailored evidence. Maintain core evidence set supporting fundamental ISO 27001 controls, then supplement with industry-specific or regulation-specific modules.
Financial services buyers require evidence of PCI DSS compliance for payment data handling. Healthcare buyers demand HIPAA compliance validation. European buyers evaluate GDPR compliance. Rather than maintaining separate evidence collections, implement a modular approach where core security evidence applies universally, with specialized evidence modules addressing industry-specific requirements.
Automation and analytics transform evidence from static artifact collections to dynamic security posture demonstrations. Compliance dashboards visualizing control implementation status, evidence collection progress, remediation tracking, and audit readiness scores demonstrate proactive security operations. Status reports showing evidence freshness, coverage gaps, and collection trends support continuous improvement.
Transparency differentiates enterprise vendors. Organizations confident in security operations proactively share evidence during sales processes—not reluctantly producing minimum required documentation after extensive negotiation. Vendors prepared to demonstrate comprehensive evidence repositories, recent internal audit results, and systematic evidence refresh cycles reduce buyer risk perception and shorten sales cycles. Evidence preparedness becomes a competitive advantage—making evidence management integral to value proposition when selling to enterprises.
Conclusion
ISO 27001 evidence requirements extend beyond certification audit checkbox activities. For vendors selling to enterprise clients, systematic evidence collection determines sales velocity, reduces procurement friction, and demonstrates security operations maturity that trust-based assertions cannot achieve.
ISO 27001 constitutes an information security management system with mandatory documentation at its core—undocumented actions do not exist within the ISO 27001 framework. Organizations must build evidence-mapping frameworks, implement continuous collection, organize secure repositories, and maintain evidence current through systematic refresh cycles.
Start with evidence mapping. Select one control domain—access management, vulnerability management, training—and implement complete evidence collection demonstrating both control design and operating effectiveness. Use templates to standardize evidence structure. Automate wherever feasible to reduce manual effort and improve consistency.
Evidence management constitutes ongoing operational function, not annual certification preparation. Organizations treating evidence systematically accelerate certification timelines, respond rapidly to enterprise security assessments, reduce audit findings, and demonstrate security posture that differentiates them in competitive enterprise markets. Strong evidence practices shorten sales cycles, strengthen negotiating position, and build buyer confidence that your security controls operate as designed—not merely that you claim they do.
FAQs
1) What is the ISO 27001 collection of evidence?
ISO 27001 evidence collection refers to systematic gathering and maintenance of artifacts demonstrating that security controls, policies, and processes required by the standard are implemented and operating effectively. Annex A 5.28 specifically addresses collection of evidence, requiring organizations to maintain proof of control effectiveness through documented procedures, operational records, logs, and audit trails. Evidence must demonstrate both control design (through documentation) and operating effectiveness (through records showing controls function as intended over time).
2) What documents are required for ISO 27001?
Mandatory documentation includes ISMS scope, information security policy, information security risk assessment procedure, Statement of Applicability, information security risk treatment procedure, information security objectives, personnel records, ISMS operational information, risk assessment reports, Risk Treatment Plan, security metrics, ISMS internal audit program and audit reports, and ISMS management review reports. Additional documentation requirements derive from applicable Annex A controls based on organizational risk assessment and scope. The 2022 revision requires fewer mandatory documents compared to ISO 27001:2013.
3) What is a documented information requirement of ISO 27001?
Clause 7.5 of ISO 27001:2022 addresses documented information, requiring organizations to create and maintain documented information necessary for effective ISMS operation. This includes documented information required by the standard and any additional documented information the organization determines necessary for ISMS effectiveness. Documented information must be clearly identified and described with appropriate format and media, then controlled through distribution, access, storage, preservation, version control, and retention activities.
4) What are the core requirements of ISO 27001?
ISO 27001:2022 consists of seven mandatory clauses: Clause 4 requires understanding organizational context and stakeholder expectations; Clause 5 emphasizes leadership commitment and information security roles; Clause 6 addresses risk assessment and information security objectives planning; and Clause 7 covers resources, competence, awareness, communication, and documented information. Clause 8 addresses operational planning and control, Clause 9 requires performance evaluation including internal audits and management review, and Clause 10 mandates continual improvement through corrective actions addressing nonconformities.





.svg)






.svg)
.svg)