Enterprise buyers now demand proof that a service provider operates secure systems day in and day out. Sales cycles stall whenever a vendor can only show a glossy policy document without evidence that controls actually work over time. The ISO 27001 evidence review cadence is more than a compliance checkbox; it’s the rhythm by which a company continually gathers, reviews, and refreshes the artifacts that demonstrate operational security. When an auditor or a prospective client asks, “Show me that your controls protect our data,” there should be living evidence rather than stale paperwork. As someone who has led more than 6,000 audits over the past 25 years, I’ve seen deals hinge on whether a company can produce logs and records on demand. In this article I’ll explain what ISO 27001 requires for evidence, how to design a review cadence that satisfies auditors and enterprise buyers, and why continuous proof beats one‑off preparations.
Why Cadence Is Essential for Ongoing Compliance and Enterprise Sales
The ISO 27001 standard requires an organization to establish, implement and continually improve an information security management system (ISMS). Buyers care about this because they know controls drift over time; a policy written two years ago doesn’t prove that least privilege is enforced today. A predictable evidence cadence keeps the ISMS in tune with real‑world operations and demonstrates three things:
- Ongoing compliance – Clause 7.5 of ISO 27001 requires organizations to create, update and control documented information so that it is fit for use and protected. Without a cadence, documents quickly become outdated.
- Control effectiveness – Logs and records show that controls are doing what the Statement of Applicability claims. For example, log retention guidelines ensure that audit trails are available to investigate events and satisfy frameworks like NIST 800‑53.
- Enterprise trust – Sales teams facing procurement questionnaires often hear, “We need to see proof of access reviews, backups and incident response.” Auditors ask the same. Evidence review cadence provides confidence that controls operate continuously, not just at audit time.
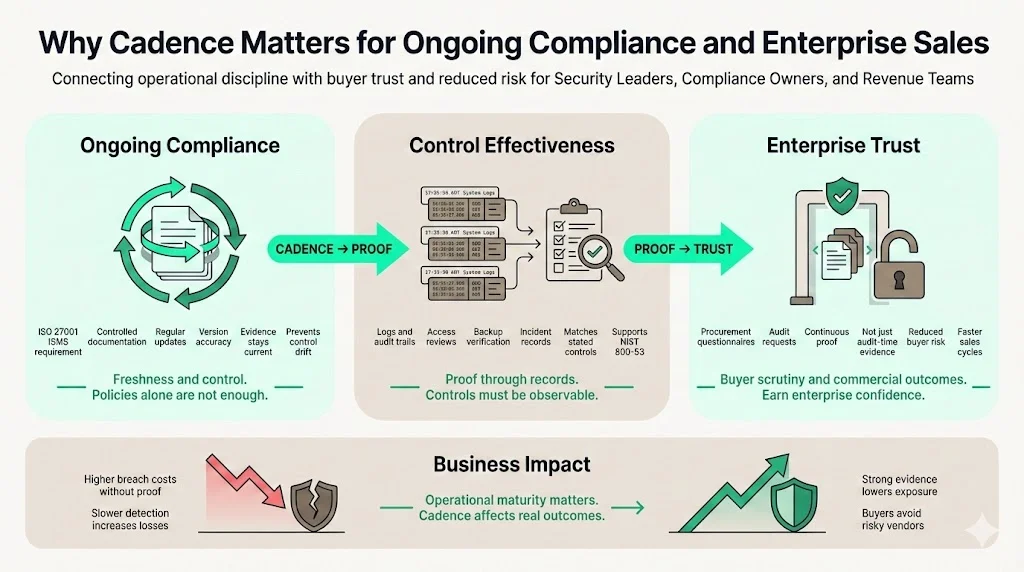
Buyers increasingly rely on operational evidence to make procurement decisions. According to IBM’s 2025 Cost of a Data Breach report, the global average breach cost fell to $4.44 million from $4.88 million in 2024, yet U.S. breach costs climbed to $10.22 million, reflecting increased regulatory penalties and slower detection. Companies that lack evidence‑driven security posture face steeper breach costs and longer downtime. Enterprise customers don’t want to become part of those statistics. They look for vendors with an evidence cadence that reduces risk and demonstrates maturity.
What ISO 27001 Requires for Evidence
ISO 27001 distinguishes between documentation, records and evidence, each serving a different purpose:
- Documentation – Policies, procedures, the scope statement and the Statement of Applicability. Clause 7.5 requires that documents be identified, reviewed and approved by authorized roles; they must be controlled to prevent unintended changes and must be available where needed.
- Records – Logs, risk registers, audit reports and other artifacts showing that activities have occurred. Clause 7.5.3 emphasizes that records must be stored, protected, and retrievable when needed.
- Evidence – The tangible proof that controls operate effectively. This includes system logs, vulnerability scans, incident records, access review attestations, and risk assessment outputs. Evidence is what auditors and enterprise buyers examine.
Evidence ties directly to controls in the ISMS. For example, log retention demonstrates compliance with Annex A 5.7 (monitoring activities), while access review records support Annex A 5.17 (user access management). When building an evidence cadence, map each control to the types of records that prove its effectiveness and ensure those records are collected and refreshed at appropriate intervals.
Document Review
Policies, procedures, the Statement of Applicability (SoA), risk assessment reports and treatment plans form the backbone of an ISMS. Clause 7.5 requires that documents be created, updated and controlled to ensure suitability. Effective document control includes:
- Versioning and review cycles – Define a review frequency (often annual or triggered by significant change) and record approvals. During audits, I always ask for proof that the incident response plan was reviewed within the past year and that version history shows who approved changes.
- Responsibility – Assign owners for each document. Policies without ownership drift. Make sure owners schedule reviews and record decisions.
Records and Logs
Logs are the bedrock of evidence. The AuditBoard guide notes that system, network, application, authentication and security device logs must be retained because they provide critical evidence during investigations. Without logs you can’t show that an access control worked or that an incident was properly contained. Best practices include:
- Centralized collection – Use a Security Information and Event Management (SIEM) system to aggregate logs, enforce retention policies and facilitate correlation.
- Defined retention periods – Align retention with legal and contractual obligations. For example, HIPAA requires audit logs of ePHI access; NIST suggests retaining audit records for at least one year. Decide retention periods in the SoA and justify them.
- Regular review – Establish a cadence for reviewing logs. High‑risk systems may require daily or weekly review; lower risk systems may be monthly. Document your rationale.
Control Effectiveness
Evidence of control effectiveness includes system logs, vulnerability scan results, access review attestations, configuration baselines and control outputs. When a control fails or drifts, evidence helps you detect and remedy issues. For instance:
- System logs show whether multi‑factor authentication is enforced.
- Vulnerability scans provide evidence that patch management is operating. Patch latency and vulnerability backlog are metrics worth tracking.
- Backup tests and recovery drills demonstrate resilience. Keep records of test results, pass/fail status and improvements.
Risk Assessment Artifacts
Risk assessment outputs—risk registers, likelihood and impact scores, risk treatment decisions, residual risk acceptance—are key evidence items. ISO 27001 Clause 8.2 requires organizations to perform ongoing risk assessments, evaluate risks and prioritize treatment. Risk documentation should be accurate, complete and regularly updated. Without up‑to‑date risk records, auditors will question whether controls align with the current threat landscape.
Compliance Monitoring Outputs
Evidence also comes from monitoring compliance itself: internal audit reports, surveillance audit artifacts, and management review minutes. Clause 9.2 mandates internal audits at planned intervals to verify ISMS effectiveness. Clause 9.3 requires top management to review the ISMS at regular intervals and document decisions. Keep audit plans, findings, corrective actions and management review minutes on file; these documents show that leadership is engaged and that issues are addressed.
Understanding Evidence Review Cadence
Cadence refers to the planned rhythm at which different evidence types are reviewed and refreshed. A predictable cadence creates audit readiness, supports continuous improvement and builds trust with buyers. Without a cadence, organizations fall into the trap of collecting evidence only when an audit is scheduled—leading to frantic sprints and unaddressed gaps.
Audit Schedule
ISO 27001 requires both internal and external audits. Schellman notes that after initial certification, organizations must conduct internal audits and ensure that at least one internal audit occurs each year before the external surveillance audit. A common practice is to maintain a rolling internal audit program, reviewing different control domains quarterly. External surveillance audits occur annually, and a full recertification happens every three years. Align your evidence review cadence so that logs, risk assessments and document reviews feed into these audits.
Continuous Compliance vs. Snapshot Compliance
Traditional compliance is reactive: teams scramble to gather evidence before an audit. Continuous compliance embeds monitoring, evidence collection and remediation into daily operations. The GetAstra guide on continuous compliance contrasts real‑time monitoring and automated evidence collection with the scheduled intervals and manual evidence gathering of periodic compliance. The benefits include:
- Always‑on audit readiness – Evidence is collected and tagged in real time. Auditors review proof in real time rather than waiting for last‑minute collections.
- Operational efficiency – Automated monitoring reduces manual effort and surprise findings. According to GetAstra, non‑compliance penalties average $14.82 million, nearly three times the cost of maintaining compliance.
- Stakeholder trust – Buyers and auditors see continuous proof, improving confidence and reducing due diligence cycles.
Risk Assessment Cadence
Risk management is ongoing. Covered entities under HIPAA, for example, should perform an enterprise‑wide risk analysis annually and review the risk register quarterly, with continuous vulnerability scanning and monthly patch verification. High‑change environments may require semiannual assessments and monthly key control testing. Small, low‑change practices can perform annual assessments with monthly confirmations of critical controls. The key principle is that risk assessment frequency should align with risk magnitude and rate of change; update the risk register immediately after material changes or incidents.
Control Effectiveness Checks
Evidence review cadence should include regular verification that controls operate as intended. For high‑risk systems, review access logs and system configurations monthly or even continuously. For medium‑risk systems, quarterly reviews may suffice. For low‑risk systems, annual checks may be appropriate, provided there is documented rationale. The Zluri article on user access review warns that annual access reviews for high‑risk systems violate ISO 27001’s risk‑based approach. Instead, determine review intervals based on asset criticality, access privilege level and user population. Document the rationale and include it in the risk register.
Building the Review Framework
To operationalize cadence, map each control to required evidence and define how often it must be reviewed. A structured framework might look like this:
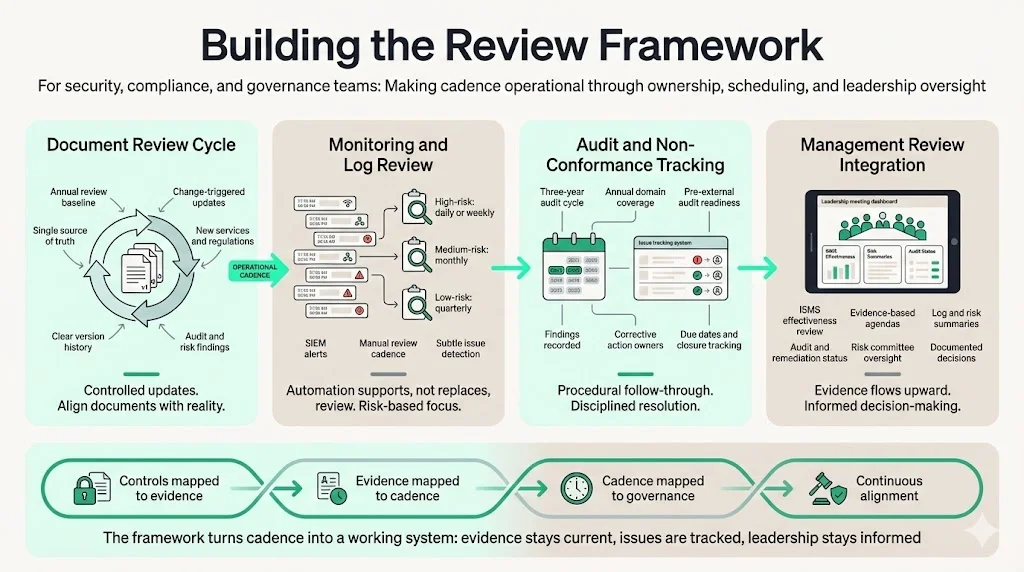
Document Review Cycle
- Frequency – Annual reviews are standard, but updates should be triggered by significant changes such as new services, changes in legal requirements, or findings from audits. For example, if a risk assessment identifies a new threat, update the relevant policy.
- Ownership – Assign a document owner (e.g., Head of Security) who schedules reviews, tracks version history and approves changes. Use a central documentation portal to manage versions and ensure only current versions are in use.
Monitoring and Log Review
- Regular review – High‑risk systems (e.g., production databases) may require weekly or daily log reviews. Medium‑risk systems (e.g., internal collaboration tools) may suffice with monthly reviews. Low‑risk systems can be reviewed quarterly.
- Automated alerting – Implement SIEM rules and alerts. However, do not rely solely on automation—include a manual review cadence to detect subtle issues.
Audit and Non‑Conformance Tracking
- Schedule internal audits – Plan a three‑year audit cycle where each domain (access control, cryptography, vendor management, incident response) is audited at least once per year. Schellman advises at least one internal audit before each external surveillance.
- Track non‑conformances – Record findings, assign corrective action owners, and set due dates. Use the risk register to link non‑conformances to risks and monitor closure.
Management Review Integration
- Integrate evidence reviews into management reviews – Clause 9.3 requires management to evaluate the ISMS’s suitability and effectiveness. Incorporate evidence review outputs—log summaries, risk register updates, audit findings, and corrective action status—into management review agendas.
- Leverage the Risk Committee – A formal risk committee helps align risk management with leadership oversight. The Neumetric guide recommends quarterly meetings where agendas include risk register review, treatment progress, incident summaries and audit findings. Meeting minutes should record discussions and decisions; the risk register should be updated accordingly.
Templates and Tools for Cadence Success
Practical templates and tools make cadence manageable. Here are sample structures to consider:
Audit Schedule Template
Use this template to plan internal audits against each domain, ensuring that evidence is collected and refreshed in the lead‑up to external audits.
Compliance Monitoring Checklist
Create a calendar‑based checklist tied to key control categories. For example, set weekly tasks to review high‑risk system logs; monthly tasks to verify patch status and encryption keys; quarterly tasks to review vendor risk; and annual tasks to refresh policies. As GetAstra notes, continuous compliance requires embedding evidence collection into daily operations.
Evidence Mapping Matrix
Build a matrix that maps each Annex A control to evidence types, owners and review frequency. Example entries:
Performance Metrics Dashboard
Tracking metrics helps teams measure the health of the evidence cadence. Key performance indicators (KPIs) may include:
- Percentage of evidence items reviewed on schedule – Aim for 90–95% timely review.
- Number of overdue reviews – Highlight areas where evidence has not been refreshed.
- Control effectiveness score trends – Aggregate vulnerability scan scores, patch latency, failed login counts and other metrics to identify improvement or deterioration over time.
- Time to close non‑conformances – Average days between finding and closure. Shorter times indicate responsive remediation.
Non‑Conformance and Improvement Log
Maintain a log to register findings from audits, risk assessments, or incidents. Include the description, control reference, owner, target completion date and status. Link each item to risk register entries to ensure risks drive remediation and that residual risks are consciously accepted.
Performance Metrics to Track
Measuring the cadence’s health requires consistent tracking:
- Evidence completion rate – The percentage of evidence items reviewed according to schedule. A low rate suggests process breakdown.
- Risk register update timeliness – The time between a triggering event and the risk register update. According to Kraft Business Systems, risk registers should be reviewed at least quarterly and updated immediately after significant changes.
- Audit findings per cycle – Track the number and severity of non‑conformities per audit. A downward trend indicates maturity; an upward trend signals control drift.
- Mean time to remediate (MTTR) security findings – Measure the time from issue identification to closure. Shorter MTTR demonstrates an effective security operations team.
Tie these metrics to continuous improvement. Use dashboards to present trends to management and adjust the cadence when metrics fall outside targets.
Common Pitfalls and How to Avoid Them
Based on years of auditing and implementing security programs, I’ve seen recurring mistakes that undermine evidence cadences:
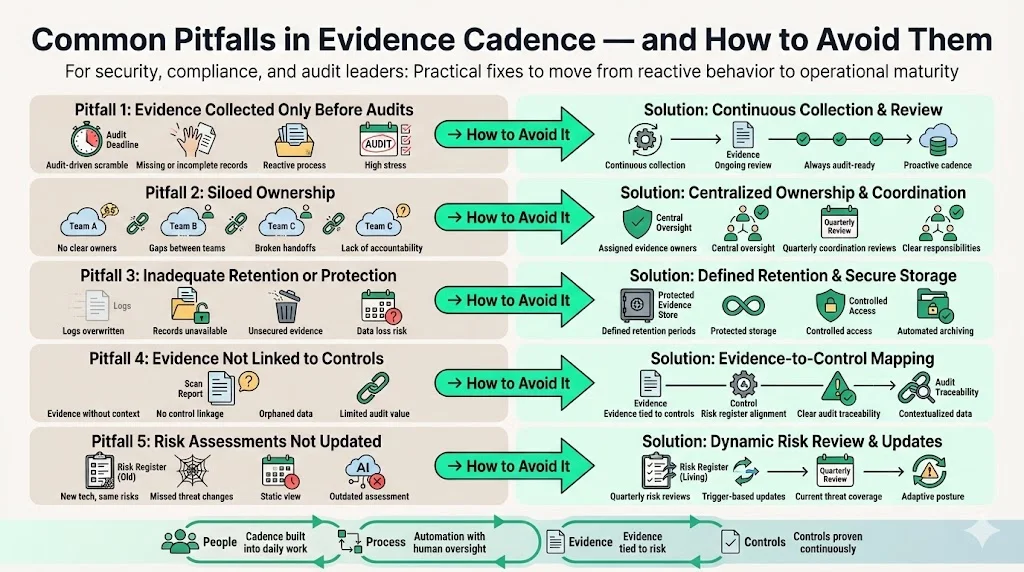
- Collecting evidence only before audits – Teams scramble to assemble logs and documents a few weeks before external audits. This is not sustainable and often results in missing records. Continuous compliance frameworks emphasize real‑time evidence collection and review.
- Siloed ownership – When evidence responsibilities are spread across different teams with no central oversight, gaps occur. Assign clear owners for each evidence type and implement a risk committee to coordinate quarterly reviews.
- Inadequate retention or protection – Logs may be overwritten or inaccessible when needed. Define retention periods and protect logs and records according to Clause 7.5 control requirements.
- Insufficient linking of evidence to controls – Evidence must clearly tie to specific controls and risks. A vulnerability scan is not useful if it doesn’t correspond to Annex A controls or risk register items.
- Not updating risk assessments after changes – Risk assessments must reflect new technologies, vendors or threats. The Accountable guide emphasizes quarterly risk register reviews and immediate updates after triggering events.
Avoid these pitfalls by building cadence into daily operations, using automation where possible but retaining human oversight, and connecting evidence to risk management and control design.
Conclusion
The ISO 27001 evidence review cadence is the heartbeat of a mature security program. It turns policies and procedures into living systems that produce proof. Enterprise buyers and auditors no longer accept assurances without supporting evidence; they require logs, records and decisions that demonstrate controls are functioning over time. By mapping evidence to controls, assigning clear ownership, and scheduling reviews aligned with risk, organizations can remain audit‑ready and speed up sales cycles.
Security that looks good in documents but fails under real‑world pressure is a liability. A structured evidence cadence—anchored in regular audits, risk assessments, log reviews and management oversight—builds resilience. With continuous compliance practices, teams can move from reactive scramble to proactive assurance, providing the proof that buyers expect and delivering tangible security outcomes. In a world of escalating breach costs and sophisticated attacks, the cadence isn’t a luxury; it’s a necessity.
FAQs
1. What is an ISO 27001 evidence review cadence?
It is the scheduled rhythm for gathering, reviewing and refreshing the logs, records and documents that demonstrate your ISMS operates effectively. It includes regular log reviews, risk assessment updates, document control, internal audits and management reviews.
2. How often should internal audits occur?
After initial certification, at least one internal audit should be performed each year before the external surveillance audit. Many organizations spread audits across the year, reviewing different domains quarterly to reduce burden and maintain readiness.
3. What types of evidence are required?
Evidence includes system logs, access review records, vulnerability scan results, backup test reports, risk assessments, risk treatment plans, audit findings and management review minutes. These artifacts prove that controls are designed, implemented and operating effectively.
4. How do I track non‑conformance and corrective actions?
Use a non‑conformance and improvement log linked to your risk register. Record the finding, owner, corrective action, due date and status. Review progress regularly in risk committee meetings and management reviews.
5. Can I automate parts of the evidence cadence?
Yes. Automation can collect logs, perform continuous vulnerability scanning, and enforce access review workflows. However, do not rely solely on automation; human oversight is essential for interpreting data, making risk‑based decisions, and ensuring that evidence truly reflects security posture.





.svg)






.svg)
.svg)