Most enterprise buyers now demand evidence of operational security before procurement. Security questionnaires, data‑processing agreements, business associate agreements (BAAs) and due‑diligence calls ask for artefacts that show policies, processes and controls working in practice. A neatly written security manual is not enough; buyers expect to see logs, access records, and incident reports that demonstrate consistent control operation. In my work leading Konfirmity’s managed security and compliance programs, I’ve seen hundreds of deals stall because evidence was incomplete or scattered. This article examines ISO 27001 Evidence Storage Best Practices — how to store and manage proof of control operation so audits run smoothly and enterprise sales cycles shorten. I’ll use data from Ponemon and IBM research, NIST and HIPAA guidance, and patterns from Konfirmity’s 6,000 audits to outline a durable approach.
Why evidence storage matters for enterprise buyers
Modern procurement processes reflect a wider trend: the cost of security failures is rising. IBM’s 2024 Cost of a Data Breach report found that the global average breach cost reached USD 4.88 million—a 10% increase from 2023. By 2025 the average dipped slightly to USD 4.4 million, but the drop was attributed to faster detection rather than lower impact. In the same study, 70% of breached organisations reported significant disruption. These numbers highlight why enterprise buyers scrutinise suppliers: a single weak link can result in millions in losses and weeks of downtime.
Regulators and frameworks also raise the bar. HIPAA requires covered entities to monitor and log access to electronic protected health information (ePHI), and audit log records must be retained for at least six years. SOC 2 Type 2 audits evaluate control effectiveness over a period of six months to one year. For SaaS and healthcare vendors, timely and complete evidence storage becomes critical not only for certification but also for sales. Enterprise buyers ask for proof that you can protect their data and show it when regulators call.
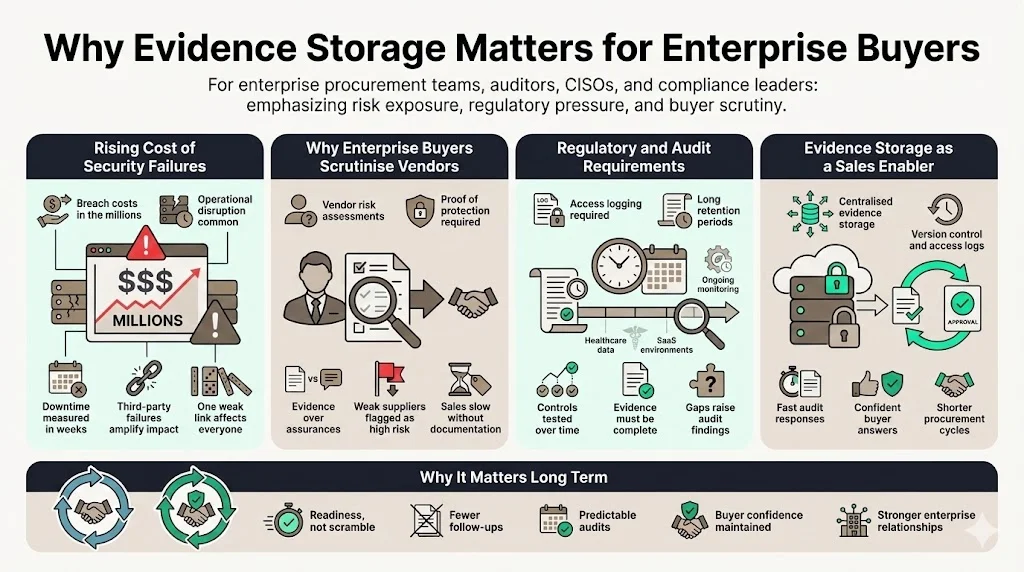
These factors underscore the importance of ISO 27001 Evidence Storage Best Practices for organisations selling to enterprise buyers.
What “evidence storage” means in information security
In an information security management system (ISMS), evidence storage refers to the organised collection, retention and retrieval of artefacts that prove controls operate effectively. It includes:
- Policies and documented information—approved versions of policies, procedures, and standards.
- Records—logs, tickets, and change requests that show controls in action.
- Evidence—specific artefacts (e.g., access approval emails, training certificates) used by auditors to test a control.
ISO 27001 distinguishes between documentation, records, and evidence. Clause 7.5.1 states that an organisation’s ISMS must include “documented information required by this International Standard” and information the organisation determines is necessary “for the effectiveness of the information security management system”. Documentation establishes what should happen; records show what did happen; evidence ties the two together. A change‑control record, for example, becomes evidence when an auditor samples it to confirm the process was followed.
Good evidence storage reduces audit risk and speeds up enterprise sales cycles by making it easy to retrieve proof when requested. During Konfirmity’s engagements, clients with centralised evidence repositories shorten SOC 2 observation periods by 30–50% compared with those who scramble during audits. In enterprise sales, the ability to produce encryption key ceremonies, incident response logs or access reviews within hours builds trust and avoids procurement delays.
What ISO 27001 says about evidence
Clause 7.5 and documented information
ISO 27001:2022 Clause 7.5 covers documented information. It states that an ISMS must include documented information required by the standard and information the organisation deems necessary for effectiveness. This clause underpins evidence storage: policies and procedures must be written, updated and controlled; records must be retained to demonstrate the system’s operation. Without documented processes, there is nothing to audit.
Annex A controls requiring evidence
Several Annex A controls explicitly or implicitly require organisations to collect and preserve evidence:
- Annex A 5.28 – Collection of evidence: the standard requires organisations to “establish and implement procedures for the identification, collection, acquisition and preservation of evidence related to information security events”. This control ties to incident response: when a security event occurs, evidence must be gathered in a manner that is admissible for disciplinary or legal action.
- Annex A 7.10 – Storage media: it states that “storage media should be managed through their life cycle of acquisition, use, transportation and disposal” according to classification requirements. Evidence stored on tapes, drives or cloud media must therefore be secured, tracked and disposed of properly.
- Annex A 8.15 – Logging: the standard defines logging as ensuring that “logs that record activities, exceptions, faults and other relevant events should be produced, stored, protected and analysed”. Audit trails are not optional; they must be generated and safeguarded to provide evidence during investigations.
- Annex A 8.16 – Monitoring activities: networks, systems and applications should be monitored for anomalous behaviour and appropriate actions taken. Monitoring records form part of evidence that detection controls are working.
Other controls implicitly require evidence—for example, Annex A 5.24 (information security incident management planning) expects incident plans and test reports, and Annex A 8.33 (test information) expects proof that testing doesn’t leak data. The Statement of Applicability (SoA) should map each control to the records and evidence your organisation retains.
Documentation vs records vs evidence
- Documentation: policies, procedures, standards, risk assessments and the SoA. These define how the ISMS operates. Example: an access management policy specifying least‑privilege and approval steps.
- Records: operational outputs showing the process was followed. Examples: logs of access requests, change tickets, training attendance lists. NIST states that logs contain records of system and network security and must be “protected from breaches of their confidentiality and integrity”. The confidentiality and integrity of archived logs must also be protected.
- Evidence: a record used to verify a control. For example, an auditor may sample a change request ticket to check that two reviewers approved it. Evidence must be complete, authentic, and retrievable.
ISO 27001 controls relevant to evidence storage
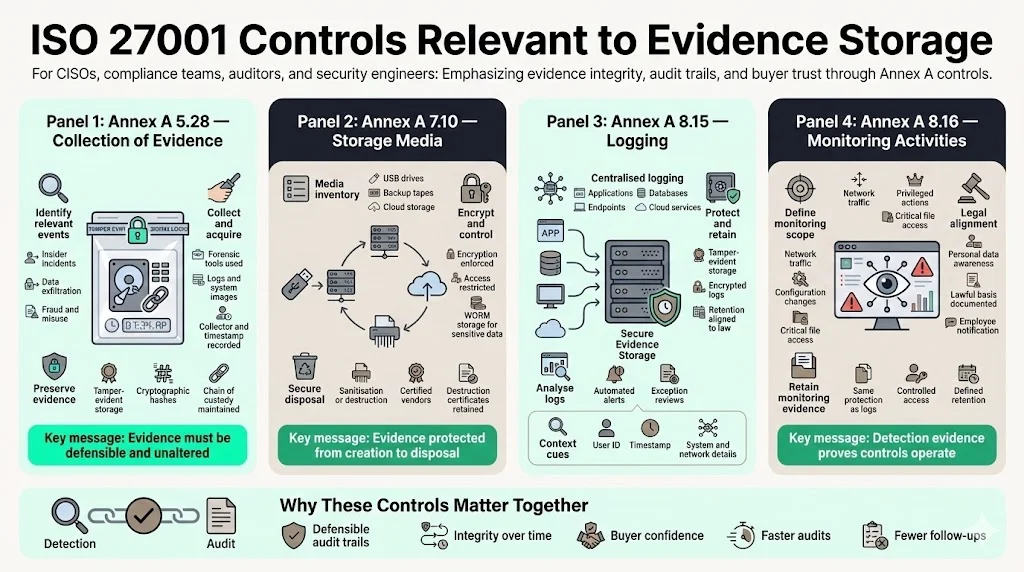
Annex A 5.28 – Collection of evidence
This control focuses on handling evidence related to information security events. The standard states that organisations should have procedures for “identification, collection, acquisition and preservation of evidence”. Key implementation points include:
- Identify: Determine which events require evidence (e.g., insider incidents, data exfiltration, fraud) and classify them by legal or disciplinary relevance.
- Collect and acquire: Use forensic tools to capture logs, system images and other data without altering them. Document who collected the evidence and when.
- Preserve: Store evidence in tamper‑evident repositories. Keep cryptographic hashes to prove integrity and maintain a chain of custody. Your incident response plan should specify how and by whom evidence is collected.
Annex A 7.10 – Storage media
Annex A 7.10 requires that storage media be managed through its life cycle—acquisition, use, transport and disposal—in line with classification and handling rules. Evidence stored on removable drives or cloud storage must be encrypted, labelled, and destroyed securely at the end of its retention period. Implementation tips:
- Inventory media: maintain an asset register for USBs, backup tapes, and cloud buckets. Track ownership and classification.
- Encrypt and control: apply encryption and access controls; restrict removable media use. For sensitive evidence, consider using WORM (write‑once‑read‑many) storage.
- Secure disposal: at end of life, sanitise or physically destroy media using certified vendors. Keep destruction certificates as evidence.
Annex A 8.15 – Logging
Logging is critical for audit trails. The control requires organisations to generate logs of activities, exceptions and faults and to store, protect and analyse them. Logs should capture user IDs, system activities, timestamps, device identifiers and network addresses. Implementation essentials:
- Centralise logs: send logs from applications, databases, endpoints and cloud services to a central log management or SIEM platform. NIST’s Guide to Computer Security Log Management warns that logs must be protected against confidentiality and integrity breaches and that improper storage can allow malicious activities to go unnoticed.
- Protect and retain: store logs in tamper‑evident storage and encrypt them. Establish retention schedules based on legal and business requirements—HIPAA retention is six years, while SOC 2 logs must cover the observation period of six months to one year.
- Analyse: automate log analysis with alerting rules; review exceptions regularly. Ensure logs include context (user, action, timestamp) so they can serve as evidence during audits.
Annex A 8.16 – Monitoring activities
Monitoring ensures that detection controls work. The standard says networks, systems and applications should be monitored for anomalous behaviour and appropriate actions taken. Monitoring evidence includes intrusion detection alerts, antivirus events, and SIEM dashboards. Implementation suggestions:
- Define what to monitor: inbound/outbound traffic, privileged actions, configuration changes, critical file access.
- Be consistent with legal constraints: monitoring may capture personal data; ensure compliance with data protection laws. Record your lawful basis for monitoring and notify employees.
- Retain records: treat monitoring data like logs—retain for the defined period, protect integrity, and restrict access.
Types of evidence you need to store
Enterprise‑oriented vendors should categorise evidence to avoid omissions. The categories below support ISO 27001 Evidence Storage Best Practices while remaining consistent with SOC 2, HIPAA and GDPR.
1. Policies and documented information
- Key documentation: policies, procedures, standards and governance documents such as risk assessments, the Statement of Applicability and risk treatment plans.
2. Operational records and audit trails
- Operational records: evidence of real-world control operation, including system logs (authentication events, firewall logs, database queries), change requests and maintenance or support tickets.
3. Access control and identity management
- Access control evidence: records of user provisioning and deprovisioning, periodic access reviews and authentication logs (e.g., MFA events and privileged access).
4. Training and awareness
- Training and competence records: proof that personnel are trained and competent, such as completion lists, role-specific certificates and security communications.
5. Incident response and monitoring evidence
- Incident response records: incident reports, detection logs (e.g., IDS/IPS alerts) and chain-of-custody documentation with cryptographic hashes verifying integrity.
6. Compliance and audit documentation
- Compliance documentation: internal and external audit reports, management review minutes and certifications or assessments (e.g., SOC 2, ISO 27001, HIPAA).
Core principles of ISO 27001 evidence storage best practices
Evidence storage is not just about retaining files; it’s about ensuring the confidentiality, integrity and availability (CIA) of evidence. The following principles reflect ISO 27001 Evidence Storage Best Practices and our experience running hundreds of audits.
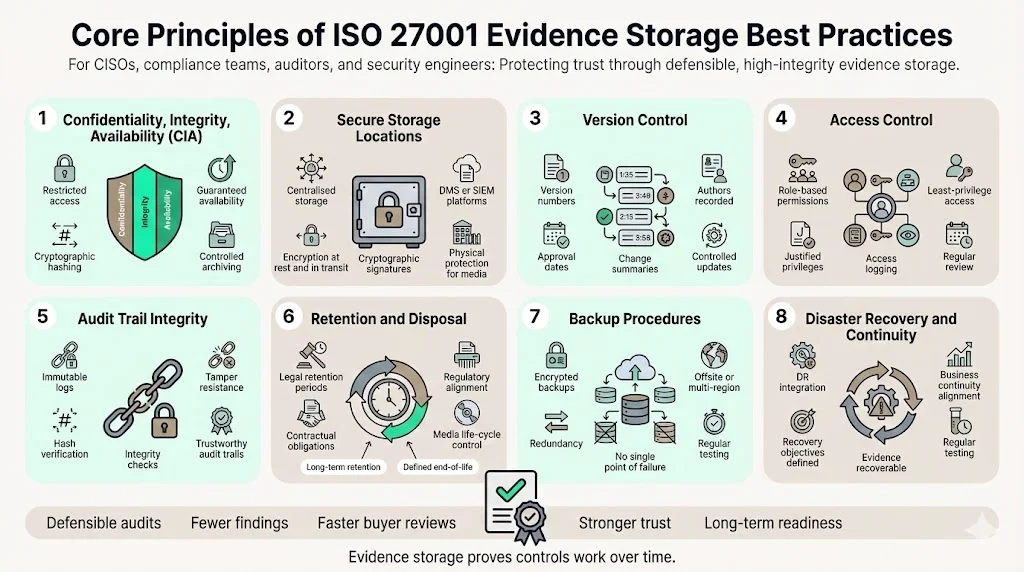
1. Maintain confidentiality, integrity and availability
- Restrict evidence access to those with a need to know; ensure it cannot be altered without detection using cryptographic hashing and signatures; and manage storage capacity and archiving to guarantee availability.
2. Secure storage locations
- Use centralised, secure repositories (DMS or SIEM) to store policies, procedures and logs. Encrypt data at rest and in transit, apply cryptographic signatures or keyed hashes, and ensure physical protections for backups and media.
3. Version control
- Maintain version history with numbers, authors, approval dates and change summaries; track changes using a document management system or version‑controlled repository.
4. Access control
- Implement role‑based access control for evidence repositories, document justification for privileges, and monitor and log all access.
5. Audit trail integrity
- Use immutable log technologies to prevent tampering and periodically verify log integrity by recalculating hashes and comparing with stored values.
6. Retention and disposal policies
- Define retention periods based on legal, regulatory and contractual obligations—HIPAA requires six years, while SOC 2 observation periods cover six months to one year. When retention expires, securely dispose of evidence and manage storage media through its life cycle.
7. Backup procedures
- Perform regular encrypted backups of evidence repositories, store them offsite or in separate cloud regions, and use redundancy to avoid single points of failure.
8. Disaster recovery and business continuity
- Integrate evidence storage into disaster recovery and business continuity plans; ensure recovery objectives match retention requirements and test these plans regularly.
Practical storage approaches and tools
Implementing ISO 27001 Evidence Storage Best Practices involves more than policies; you need the right tools and workflows. Below are approaches used by leading enterprise‑oriented vendors and by Konfirmity’s managed service teams.
1. Document management systems (DMS)
Use document management systems with structured folders, metadata, search, access control, versioning and audit tracking. Adopt naming conventions that include document type, owner, version and date.
2. SIEM & logging platforms
Centralise logs using a SIEM or cloud‑native logging service to correlate events, detect anomalies and meet retention requirements. Export logs to long‑term archive when observation periods demand extended retention.
3. Automation & evidence collection tools
Automation reduces manual effort and ensures continuous evidence collection. Use integrations to pull access logs, policy approvals and vulnerability scans into a central evidence repository and map them to your control framework. In Konfirmity’s managed service, we build pipelines that ingest code commits, ticketing records, identity management logs and cloud activity into a unified evidence store.
4. Naming conventions & metadata
Consistent naming and metadata make retrieval easier. Define prefixes for control categories and include system names, dates and retention periods. Use metadata fields to record classification, owner and sensitivity.
Common mistakes in evidence storage
Through more than 6,000 audits, Konfirmity’s team has seen recurring mistakes that increase audit risk:
- Treating evidence collection as a one‑off: Some companies scramble to gather logs and documents a week before the audit. Evidence should be collected continuously; otherwise logs may be overwritten or missing.
- Storing evidence in silos: Evidence scattered across personal drives, email threads, and shared folders leads to incomplete or inconsistent records. Centralise evidence to maintain integrity and availability.
- Lack of version control: Without versioning, auditors cannot determine whether policies were in force during the audit period. Uncontrolled documents undermine trust.
- Inadequate access control: If everyone can access evidence, confidentiality is compromised. Conversely, if access is overly restricted and undocumented, retrieving evidence becomes painful.
- Poor retention policies: Deleting logs too early violates standards (e.g., HIPAA’s six‑year requirement) while retaining data indefinitely increases privacy risk. Ensure retention matches legal requirements and document your rationale.
How auditors review evidence storage
During an ISO 27001 audit, external auditors review both the design and operation of evidence storage. They typically:
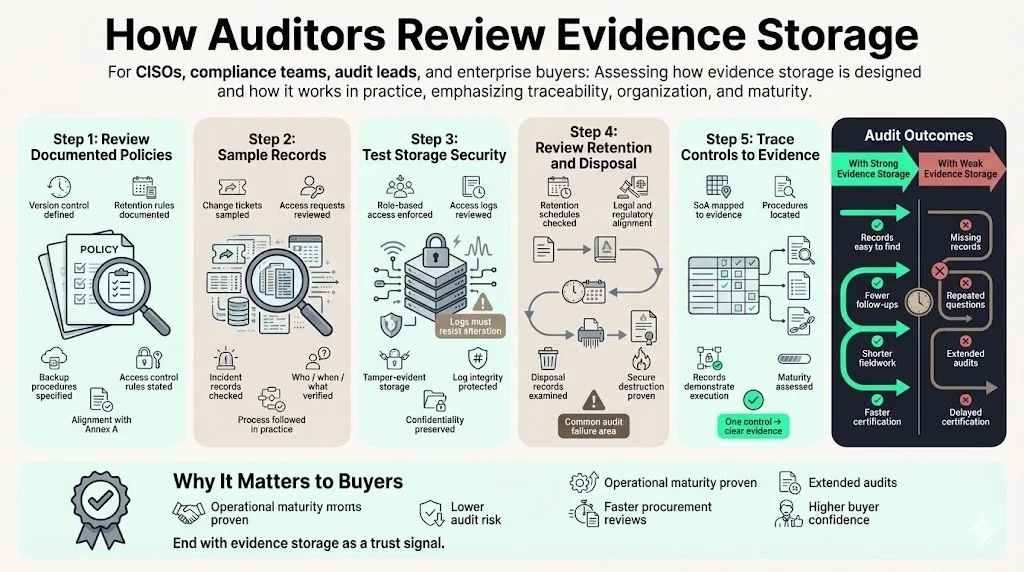
- Examine documented policies: Are there defined procedures for version control, retention, backup and access? Do they conform to ISO 27001 and Annex A controls?
- Sample records: Auditors pick samples (e.g., change tickets, access requests) to verify that the documented process is followed. Evidence must show who, when and what happened.
- Check storage security: They test whether evidence repositories enforce access control and whether logs are tamper‑evident. Many use NIST principles, which stress protecting logs against confidentiality breaches and ensuring log integrity.
- Review retention and disposal: Auditors check retention schedules and disposal records. Failure to prove proper destruction of expired evidence is a common finding.
- Trace controls to evidence: Each control in the SoA should map to specific evidence. Auditors ask: If Annex A 5.28 requires evidence collection, where is the procedure? What records show evidence was collected? How is the chain of custody maintained? Auditors also consider whether your programme follows ISO 27001 Evidence Storage Best Practices; adherence to these practices demonstrates maturity and reassures enterprise buyers.
Strong evidence storage practices shorten audits. When documents, logs and records are readily available and well‑organised, auditors spend less time chasing information. In Konfirmity’s experience, clients with mature evidence storage reduce audit fieldwork by 40% and achieve ISO 27001 certification in 4–5 months compared with 9–12 months for teams that build programs from scratch.
Conclusion
Information security is measured not by the beauty of your policy documents but by proof that controls work every day. The ISO 27001 Evidence Storage Best Practices outlined here support both compliance and enterprise sales. By maintaining confidential, intact and available evidence, centralising storage, applying version control, enforcing access control, ensuring audit‑trail integrity, defining retention and disposal rules, backing up data and integrating evidence storage into disaster recovery plans, organisations build an ISMS that withstands scrutiny. Enterprise buyers gain assurance, audits are less disruptive, and your team can focus on delivering value instead of hunting for records. Security that reads well but fails in practice is risky. Build controls once, operate them daily, and let compliance follow.
FAQ
1. What qualifies as ISO 27001 audit evidence?
Evidence includes any artefact used to verify a control: policies and procedures, logs, tickets, access approval emails, training records, incident reports and audit reports. For example, Annex A 8.15 requires logs of activities, exceptions and faults; these logs become evidence that monitoring controls are operational.
2. How long should ISO 27001 evidence be stored?
Retention depends on legal and contractual obligations. HIPAA audit log records must be kept for six years. SOC 2 Type 2 audits require logs covering six months to one year. ISO 27001 itself does not specify durations but expects you to define retention based on risk, regulatory and business requirements. Keep records long enough to demonstrate control operation during the observation period and any legal limitation period.
3. Where should ISO 27001 evidence be stored securely?
Use centralised and secure repositories: document management systems for policies, SIEM platforms for logs, and encrypted cloud storage for backups. Annex A 7.10 emphasises managing storage media throughout its life cycle—that includes acquisition, use, transport and disposal. Evidence stored on removable media should be encrypted and tracked.
4. How do auditors review evidence storage?
Auditors review policies, sample records, check storage security, verify retention and disposal, and trace each control to evidence. They will check that logs are protected against unauthorised access and tampering as described by NIST and that archived logs retain confidentiality and integrity. Having a clear mapping between controls and evidence speeds up this review.
5. What are common evidence storage mistakes?
Common pitfalls include treating evidence collection as a last‑minute task, storing records in silos, lacking version control, failing to restrict access, and poor retention practices. Logs must be protected from confidentiality and integrity breaches and retained for the required period. Avoiding these mistakes reflects ISO 27001 Evidence Storage Best Practices and reduces both audit findings and deal delays.





.svg)






.svg)
.svg)