Most enterprise buyers now ask for evidence of information security and data‑protection practices during procurement. In our experience supporting more than six thousand audits, the absence of a documented programme stalls deals even when teams feel prepared. The rising cost of breaches reinforces why: the global average breach cost climbed to USD 4.88 million in 2024 before dropping slightly to USD 4.4 million in 2025. Each incident takes months to detect and contain, and vendors account for a significant portion of breaches. In this environment, ISO 27001 For Data Processors is not a marketing badge but a rigorous way to manage security and demonstrate readiness. This article explains why the standard matters today, what it requires, and how to implement it in a way that satisfies enterprise clients.
Why ISO 27001 for data‑processing firms matters now
1) Enterprise buyers demand assurance
Procurement teams no longer take security claims at face value. A 2024 Panaseer survey found that 83 percent of enterprise buyers require SOC 2 compliance before onboarding a software vendor. In our world, similar expectations apply to ISO 27001 For Data Processors; failure to provide independent attestation means elimination from due‑diligence cycles. The average company now relies on roughly 240 third‑party vendors and more than half work with over 100 suppliers. This complexity fuels breaches—88 percent of incidents originate from vendors—so buyers demand proof of security governance, access controls, and risk management.
2) Rising regulatory, privacy, and security expectations
Regulators are tightening enforcement. Panaseer reported a 22.7 percent increase in fines for non‑compliance in 2024. Meanwhile, privacy laws such as the EU’s GDPR, India’s Digital Personal Data Protection Act, and upcoming AI regulations require robust controls over personal data. Healthcare providers and financial institutions operate under additional rules like HIPAA and GLBA, which demand administrative, physical, and technical safeguards for electronic protected health information. Companies handling data on behalf of others must demonstrate that they protect confidentiality, preserve integrity, and maintain availability of information. ISO 27001 For Data Processors offers a recognised framework to meet these expectations.
3) Building trust through a globally recognised standard
Certification under ISO 27001 For Data Processors shows a programmatic approach to information security. It establishes an information security management system (ISMS) that covers people, processes, and technology, and it is audited by accredited bodies. Because the standard is international, enterprise clients across sectors understand what certification means: risk assessment, documented controls, internal audits, and continuous improvement. Security becomes a business enabler, not a compliance afterthought.
Understanding ISO 27001: purpose, scope, and core requirements
Purpose and scope
ISO 27001:2022 defines requirements for establishing, implementing, maintaining, and continually improving an ISMS. It compels organisations to frame security as a management discipline rather than a set of technical tools. The ISMS covers organisational context, leadership commitment, planning, support, operation, performance evaluation, and improvement; these are codified in ten clauses of the standard. Certification is valid for three years, with annual surveillance audits to verify continued operation. After April 2024 new certifications must use the 2022 version, and organisations have until 31 October 2025 to transition.
Risk‑based approach and the C‑I‑A triad
ISO 27001 requires a systematic examination of risks that might impact confidentiality, integrity, and availability. Following guidance from NIST SP 800‑30, risk assessments inform senior leadership about threats, vulnerabilities, and potential impacts. Organisations must decide whether to mitigate, avoid, transfer, or accept each risk. Risk treatment decisions are documented in a Statement of Applicability, which lists the controls selected and the rationale.
The triad of confidentiality, integrity, and availability runs through every clause. Confidentiality means only authorised parties can access data; integrity ensures information remains accurate and unaltered; availability guarantees systems and data are accessible when needed. Effective controls address all three dimensions—for example, encryption (confidentiality), checksums and logging (integrity), and redundancy (availability).
Structure and controls
ISO 27001:2022 includes management clauses and an annex of 93 security controls. The annex, built upon ISO 27002, reorganises controls into four themes: organisational (37 controls), people (8), physical (14), and technological (34). These themes replace the older 14 control categories, making the framework easier to understand. Examples include: information security policies, human‑resource security, access control, cryptographic controls, physical security, and supplier relationships. Personnel awareness and training appear in the people theme, emphasising that technical defences alone are insufficient.
Annex controls are not mandatory by default. Companies perform risk assessments to identify relevant threats, then select appropriate controls and document justifications. Controls may be implemented fully, partially, or not at all, but omissions must be justified in the Statement of Applicability.
Risk assessment and treatment
A robust risk assessment identifies assets, threats, vulnerabilities, and the consequences if an incident occurs. Data processors must assess not only internal systems but also client data flows and third‑party dependencies. For each risk, a treatment plan describes how to address it—through control implementation, risk acceptance, risk avoidance, or transfer via insurance or contractual arrangements. The plan should define owners and deadlines, and updates should be reflected in the risk register.
Continuous improvement
Certification is not a one‑time project. ISO 27001 requires ongoing monitoring, internal audits, management reviews, corrective actions, and continual improvement. Annual surveillance audits verify that controls remain effective and that the ISMS evolves with the business and threat landscape. For cloud‑native service providers, this means integrating security into DevOps pipelines, automating evidence collection, and performing regular access reviews rather than relying on manual checklists.
What ISO 27001 means for data processors
Why data processors need ISO 27001
As data handlers, processors have a custodial duty to protect client information. Certification demonstrates that your organisation operates a managed security programme rather than ad‑hoc controls. It signals to enterprise buyers that your policies and technical measures align with globally accepted practices. By implementing ISO 27001 For Data Processors, you reduce the likelihood of breaches and regulatory fines while accelerating sales cycles through independent assurance.
Key areas covered by ISO 27001 that matter to data processors
- Security governance and leadership: The management clauses mandate top management involvement, define roles and responsibilities, and require resources for the ISMS. This ensures security is not siloed in engineering but is championed by leadership.
- Asset management: A precise inventory of information assets—data sets, hardware, software, documents—and their owners helps processors protect client data. Classification policies dictate how sensitive information is handled and stored.
- Access control: Annex controls require that users have only the access they need. Data processors should implement role‑based access, strong authentication, periodic access reviews, and robust onboarding and offboarding procedures.
- Risk assessment and vendor management: You need to identify data‑handling risks, processing risks, and vendor risks. With more than 88 percent of breaches originating from suppliers, vendor assessments and contracts with clear security obligations are essential.
- Incident management: Procedures to detect, report, and respond to security events must be documented. Data processors often act as sub‑processors; they must notify clients of incidents within contractual timeframes, cooperate on root‑cause analysis, and implement corrective actions.
- Auditing and performance evaluation: Internal audits and management reviews verify whether controls are effective and identify gaps. Metrics such as number of incidents, patch compliance, and audit findings should be tracked to inform leadership.
- Continuous improvement: The ISMS must adapt as the business scales, new services launch, or threats evolve. Regular penetration testing, vulnerability management, and lessons learned from incidents drive improvement.
Aligning with enterprise‑client expectations
Enterprise buyers care about confidentiality, integrity, availability, privacy, and regulatory compliance. Certification under ISO 27001 For Data Processors signals that you understand these priorities. For example, strict access control and encryption assure confidentiality; change management and code‑review processes preserve integrity; redundant infrastructure supports availability. A risk‑based approach aligns with various regulations (HIPAA, GDPR, GLBA) and demonstrates due diligence. When clients audit your controls, you can provide documented policies, risk registers, incident logs, and evidence of continuous monitoring.
Beyond ISO 27001: privacy, cloud, and the need for additional standards
The limitations of ISO 27001 alone
ISO 27001 provides a broad framework for information security, but it does not address the nuances of personal data protection or cloud‑provider relationships. Data processors often handle personally identifiable information (PII) in public clouds or operate as infrastructure providers. In those scenarios, additional standards strengthen your compliance position.
ISO 27017: guidance for cloud services
ISO 27017 offers guidance on implementing security controls in cloud environments, clarifying responsibilities between cloud service providers and customers. It builds on ISO 27002 and addresses topics such as shared responsibility, virtualization controls, and incident reporting. While ISO 27001 sets high‑level requirements, ISO 27017 explains how to apply controls when infrastructure and services are distributed. For example, it clarifies who is responsible for configuring firewall rules in a cloud platform and how to handle multi‑tenant data separation.
ISO 27018: PII protection in public clouds
ISO 27018 sets control objectives and guidelines to protect personally identifiable information in cloud computing. It must be used alongside ISO 27002 and covers requirements for legal, regulatory, and contractual obligations, risk assessment, policies, and user consent. Annex A includes an extended set of controls specifically for PII, such as data deletion on contract termination and disclosure notifications to data subjects. Data processors who host personal data can use ISO 27018 to show that they address privacy laws like GDPR and DPDP.
ISO 27701: privacy information management
The 2025 revision of ISO 27701 turns the previous extension into a standalone privacy information management system (PIMS). It covers context, leadership, planning, support, operation, performance evaluation, and improvement clauses similar to ISO 27001, but specifically for personal data. Annex A lists controls for PII controllers and processors, including data subject rights, consent management, and cross‑border transfer requirements. If your clients process personal data, combining ISO 27001 and ISO 27701 provides a unified approach that addresses both security and privacy obligations.
Why consider these standards together
Regulations such as GDPR require not only security measures but also privacy‑by‑design and accountability. ISO 27001 alone may not address all privacy requirements. Data processors often market “ISO 27001 plus ISO 27017/27018/27701” as a stronger package. These certifications reassure clients that you protect both their business data and personal data, operate responsibly in the cloud, and understand regulatory obligations. For example, a cloud platform offering document processing might pair ISO 27001 with ISO 27018 to demonstrate that personal data is encrypted, processed based on client instructions, and deleted after contract termination.
Practical requirements and templates for data processors
The following sections outline key domains under ISO 27001 For Data Processors and give suggestions on the documents and templates to maintain. These are drawn from Konfirmity’s playbooks and can serve as starting points for teams implementing an ISMS.
1) Scoping and context definition
- Scope document: Define the organisational units, systems, and data flows included in the ISMS. Identify client data, processing activities, and third‑party dependencies.
- Context analysis: Describe internal and external issues, interested parties, and legal requirements. This helps justify the ISMS boundaries and focus resources where they matter.
2) Information security policy and governance
- Security policy: A high‑level statement signed by leadership that sets objectives, commitment to continual improvement, and compliance with applicable laws. It should reference subordinate policies (access control, incident response, vendor management, etc.).
- Roles and responsibilities: A matrix assigning accountability for ISMS maintenance, risk assessment, incident response, and audit preparation. This clarifies who approves exceptions and who reports to the board.
- Governance charter: A document detailing committee structures, meeting frequencies, and escalation paths. It helps ensure regular management reviews of security performance.
3) Asset management
- Asset inventory: Maintain a register of hardware, software, data sets, and documentation. Include owners, classification, location, and life‑cycle status.
- Data classification policy: Define categories such as public, internal, confidential, and highly sensitive. Describe handling rules (encryption, retention, transmission) for each classification.
- Ownership matrix: Map data sets and systems to responsible individuals and departments.
4) Access control
- Access control policy: Set out rules for user provisioning, authentication, least‑privilege, and password complexity. Describe multi‑factor authentication requirements and remote‑access restrictions.
- User access register: Track access rights for each user, including privileges, roles, and review dates. Integrate this register with onboarding/offboarding checklists.
- Role definitions: Document the permissions associated with each job role to standardise access decisions.
- Onboarding/offboarding checklists: Ensure that new employees receive only necessary access and that departing staff or contractors lose access promptly.
5) Risk assessment and treatment
- Risk assessment template: Capture assets, threats, vulnerabilities, impact ratings, likelihood scores, and existing controls. Use a qualitative or quantitative scoring method to prioritise risks.
- Risk register: A living document listing identified risks, their owners, treatment status, and review dates. Link each risk to controls in the Statement of Applicability.
- Risk treatment plan: Outline actions to mitigate, transfer, avoid, or accept each risk. Provide deadlines and responsible parties.
- Periodic review procedure: Schedule quarterly or semi‑annual risk reviews to update the register and ensure new projects undergo risk assessment.
6) Vendor, third‑party, and sub‑processor risk management
- Vendor assessment templates: Questionnaires covering security controls, privacy practices, business continuity, and regulatory compliance. These forms gather evidence from suppliers and sub‑processors.
- Vendor risk evaluation: A scoring model that considers criticality, data sensitivity, and inherent risk. Document due‑diligence findings, risk ratings, and approval decisions.
- Onboarding processes: Steps to conduct due diligence before contracting a new vendor. Include contract clauses on breach notification, data retention, and audit rights.
- Contractual security addenda: Standard clauses requiring vendors to implement controls equivalent to your ISMS and to obtain relevant certifications.
7) Incident management and response
- Incident response policy: Define what constitutes an incident, roles in the response team, escalation paths, and communication protocols. Include timelines for notifying affected clients and regulators.
- Incident reporting form: A standard template for employees to report suspected incidents with details of what occurred, systems affected, and initial response.
- Incident log: A register of all incidents, investigation details, root‑cause analyses, corrective actions, and lessons learned.
- Post‑incident review template: Document improvements to prevent recurrence and track follow‑up actions.
8) Operational controls (technical and physical)
- Data‑handling procedures: Step‑by‑step instructions for collecting, processing, storing, transmitting, and disposing of data. Include encryption, pseudonymization, and secure transfer mechanisms.
- Encryption policy: Specify algorithms, key lengths, rotation schedules, and key‑management responsibilities.
- Backup and recovery procedures: Define backup frequency, storage location, retention period, and restoration testing.
- Secure disposal guidelines: Describe how to sanitize media, decommission systems, and securely delete data.
- Physical security checklists: Document facility controls (access badges, CCTV, environmental monitoring) and visitor policies.
- Network security guidelines: Describe segmentation, firewall configurations, intrusion detection/prevention, and patch management processes.
9) Audit and monitoring
- Internal audit schedule: Plan annual or semi‑annual audits across domains. Identify objectives, scope, and auditors.
- Audit checklist: A list of criteria and evidence to review during internal audits, aligned with ISO 27001 clauses and annex controls.
- Audit reports: Templates to document findings, observations, non‑conformities, and corrective actions.
- Management review agenda: Outline topics for periodic leadership meetings, including risk register status, incident metrics, and changes in legal or regulatory environment.
10) Performance evaluation and continuous improvement
- Metrics dashboard: Track key performance indicators such as incident counts, time to detect and contain incidents, patch compliance percentage, and vendor‑risk scores.
- Improvement action log: Record corrective actions arising from audits, incidents, and management reviews. Assign owners and track completion.
- Review schedule: Set dates for periodic reviews of policies, procedures, and risk assessments.
11) Documentation and record‑keeping
- Document register: Maintain an index of all policies, procedures, logs, and registers. Include version numbers, owners, and review dates.
- Version control procedure: Define how documents are updated, approved, and distributed. Use a secure repository and restrict editing rights.
- Retention policy: Specify how long records are kept, aligning with legal requirements and client agreements. Include secure disposal procedures for expired records.
Implementation roadmap for a data‑processing company
Building an ISMS is a journey with multiple phases. Based on our experience, the following roadmap helps organisations establish ISO 27001 For Data Processors efficiently while minimising disruption. We also compare self‑managed efforts with a human‑led managed service like Konfirmity.
Phase 1: Gap analysis and scoping
Identify current data flows, services, and client obligations. Catalogue assets and third‑party dependencies. Define the ISMS scope, focusing on systems and processes that handle client data. At this stage we often uncover hidden sub‑processors and shadow‑IT, which can become major compliance obstacles later.
Phase 2: Risk assessment and classification
Perform a formal risk assessment. Evaluate threats such as insider misuse, misconfiguration, supply‑chain attacks, and regulatory violations. Assign likelihood and impact scores and populate a risk register. Classify data based on sensitivity to determine where controls must be strongest.
Phase 3: Policies, controls, and governance framework
Draft the core policies described earlier (security, access control, asset management, vendor management, incident response). Assign owners and schedule regular governance meetings. Map existing controls against the annex to identify gaps. Build a Statement of Applicability with justifications for controls you will implement, omit, or partially implement.
Phase 4: Implement controls and technical/organisational measures
Enforce access controls, encryption, data classification, backups, physical security, and secure disposal. Onboard third‑party vendors using your new due‑diligence procedures. For engineering teams, integrate security into CI/CD pipelines, automate infrastructure provisioning with secure defaults, and deploy monitoring tools for logs and vulnerabilities.
Phase 5: Training and awareness
Educate employees and contractors about security policies, acceptable use, social engineering, and incident reporting. Provide role‑based training for developers, system administrators, and support teams. People controls in Annex A emphasize awareness, and auditors will look for training records.
Phase 6: Monitoring, auditing, and review
Schedule internal audits to verify whether policies and controls are effective. Track metrics on incidents, vulnerabilities, and vendor risk. Conduct management reviews to assess the ISMS’s performance and decide on corrective actions. Update the risk register and treatment plans accordingly.
Phase 7: Pre‑audit and certification
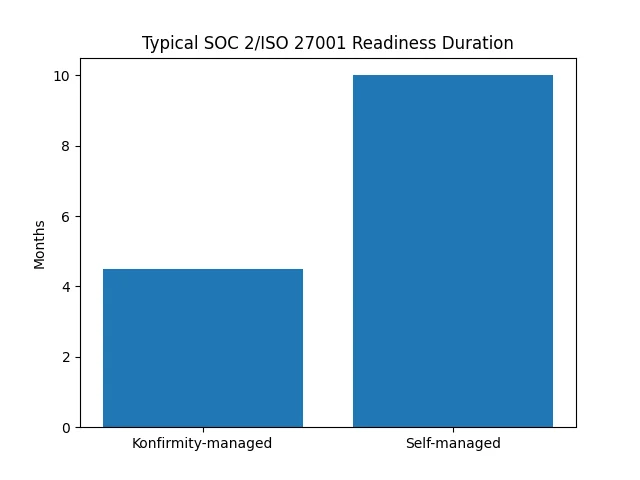
If seeking formal certification, prepare for the external audit. This involves compiling evidence, including the Statement of Applicability, policies, procedures, risk assessments, incident logs, and audit reports. Undergo stage 1 (documentation review) and stage 2 (implementation review) audits, and address any non‑conformities. Expect the observation window to span months for some controls; claims of two‑week certification are often unrealistic. When performed correctly, audit‑ready programmes require sustained evidence across 64+ control points. To illustrate readiness timelines, the chart below compares typical self‑managed ISO 27001 readiness to Konfirmity’s managed service. Clients using our platform often achieve readiness in four to five months, while self‑managed teams take nine to twelve months.
Phase 8: Maintenance and continuous improvement
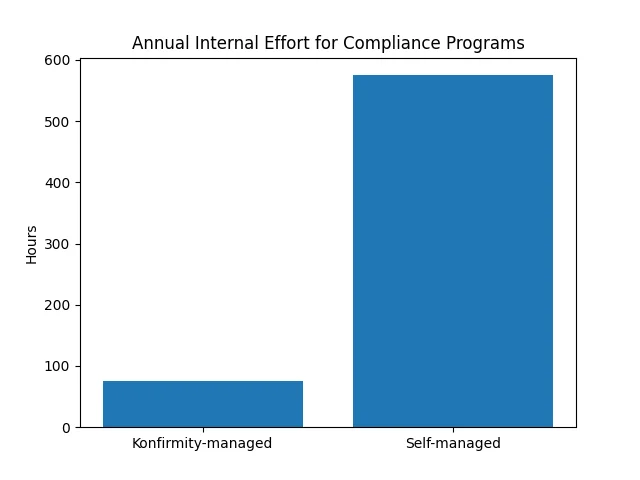
After certification, operate the ISMS daily. Perform annual surveillance audits, re‑assess risks regularly, update controls when business models change, and respond to new threats. With Konfirmity, clients invest roughly 75 hours per year on tasks like evidence review and management meetings, compared with 550–600 hours in a self‑managed programme. The chart below illustrates this difference.
Relevance to enterprise‑client businesses: what clients care about
Enterprise clients evaluate vendors on multiple criteria:
- Data protection compliance: Clients want assurance that you comply with relevant laws and frameworks, not just ISO 27001. They may ask for GDPR records of processing, HIPAA‑specific safeguards, or GLBA controls.
- Confidentiality, integrity, and availability: Buyers check whether you use encryption, backups, redundancy, and change controls to keep their data safe and available. They will ask for vulnerability management and patch management evidence.
- Privacy: If you process personal data, clients expect you to respect data‑subject rights and to provide visibility into how data is used and stored. ISO 27018 and ISO 27701 attestations help here.
- Vendor and sub‑processor governance: Clients need to know you hold your own vendors accountable for equivalent controls. This reduces supply‑chain risks.
- Incident response: Transparent and timely incident handling is critical. Buyers will ask about your incident notification SLAs, breach history, and remediation effectiveness.
- Audit readiness: Clients may conduct their own audits or rely on your third‑party audit reports. Well‑organised documentation and continuous monitoring show that you are always ready to demonstrate compliance.
Certification under ISO 27001 For Data Processors does more than check a box; it gives clients confidence that you have implemented a repeatable, audited programme. When combined with privacy‑focused standards and delivered through a human‑led managed service, it reduces buyer due‑diligence friction and supports faster contract signatures.
Conclusion
Security that looks good in documents but fails under incident pressure is a liability. Enterprises today demand real evidence that their data processors manage risk, protect personal information, and continuously improve their controls. ISO 27001 For Data Processors remains the bedrock for information security, but it must be implemented thoughtfully and complemented by privacy and cloud‑specific standards when you handle personal data or run on shared infrastructure. Starting with a clear scope and risk assessment, building policies and controls, implementing them across people, processes, and technology, and then maintaining them through ongoing monitoring and audits will prepare you for an external certification and, more importantly, for enterprise scrutiny. With a human‑led managed service like Konfirmity, companies can achieve audit readiness in months, spend far fewer internal hours, and maintain confidence that dedicated experts handle security and compliance. Start with security and arrive at compliance—your enterprise clients will thank you.
Frequently asked questions
1. What does ISO 27001 compliance mean for data security?
It means establishing an information security management system that covers governance, risk assessment, control implementation, internal audits, and continuous improvement. For data processors, it signals to clients and regulators that you manage information security systematically and can provide evidence of your practices.
2. What are ISO/IEC 27017 and ISO/IEC 27018?
ISO 27017 provides guidance on applying security controls in cloud environments, clarifying shared responsibilities between providers and customers. ISO 27018 extends ISO 27002 with control objectives for protecting personally identifiable information in public clouds. Both standards supplement ISO 27001 but do not replace it.
3. How is ISO 27001 different from SOC 2?
SOC 2 is an attestation framework issued by the AICPA that focuses on five trust services criteria (security, availability, processing integrity, confidentiality, privacy). ISO 27001 is a certification standard that requires an ISMS and is audited by accredited bodies. SOC 2 audits have one stage, while ISO audits have two stages. About 80 percent of their controls overlap.
4. Is ISO/IEC 27701 mandatory?
No. ISO 27701 is optional, but it becomes valuable when you process personal data under regulations like GDPR. The 2025 revision makes it a standalone privacy management system covering context, leadership, planning, operation, performance evaluation, and improvement. It includes controls for PII controllers and processors.
5. How often do ISO 27001 audits occur?
Certification is valid for three years, but surveillance audits occur annually to ensure the ISMS is maintained. Internal audits should take place at least annually, with continuous monitoring and management reviews in between.
6. Can a data‑processing company use ISO 27001 without being a cloud provider?
Yes. ISO 27001 applies to any organisation that handles information, regardless of hosting model. On‑premise processors must still implement controls for governance, risk management, access control, incident response, and continuous improvement.
7. What minimal documentation is essential for ISO 27001 compliance?
At minimum, processors need a defined scope, an information security policy, asset inventory, access control policy, risk assessment and treatment plan, vendor management procedures, incident response plan, internal audit schedule, and documented evidence of monitoring and corrective actions. These templates help generate the evidence that auditors and clients expect during due diligence.





.svg)






.svg)
.svg)