Most enterprise deals now hinge on whether a vendor can evidence operational security. Procurement questionnaires ask for audit reports, control descriptions and observation‑window evidence before purchasing decisions are made. The average global cost of a data breach surged to USD 4.88 million in 2024 and multi‑environment breaches (public cloud, private cloud and on‑premise) cost more than USD 5 million and took 283 days to contain. Buyers are rightly cautious: paper compliance that falls apart under incident pressure delays contracts and exposes legal liability.
This article explains why ISO 27001 For On-Prem remains essential for vendors that run physical infrastructure, how enterprise buyers evaluate proof, and how to implement an information security management system (ISMS) that stands up to auditors and customers alike. It draws on current research (2024–2025), industry guidance, and more than 6,000 audits delivered by Konfirmity’s teams over the past 25 years. The result is a practitioner’s roadmap written for CTOs, CISOs, engineering leaders and procurement executives who need to make on‑prem security a competitive advantage.
Why ISO 27001 For On-Prem Environments Still Matters
Enterprise and healthcare buyers increasingly ask for security artifacts as a condition of sale. Contracts for sensitive workloads now include data protection addenda, business associate agreements and references to ISO 27001 controls. Buyers use these artifacts to gauge whether a vendor’s security program is operating or merely documented. When an on‑prem vendor cannot produce evidence of access reviews, change‑management records or incident logs, deals stall and security teams mark the supplier as high risk.
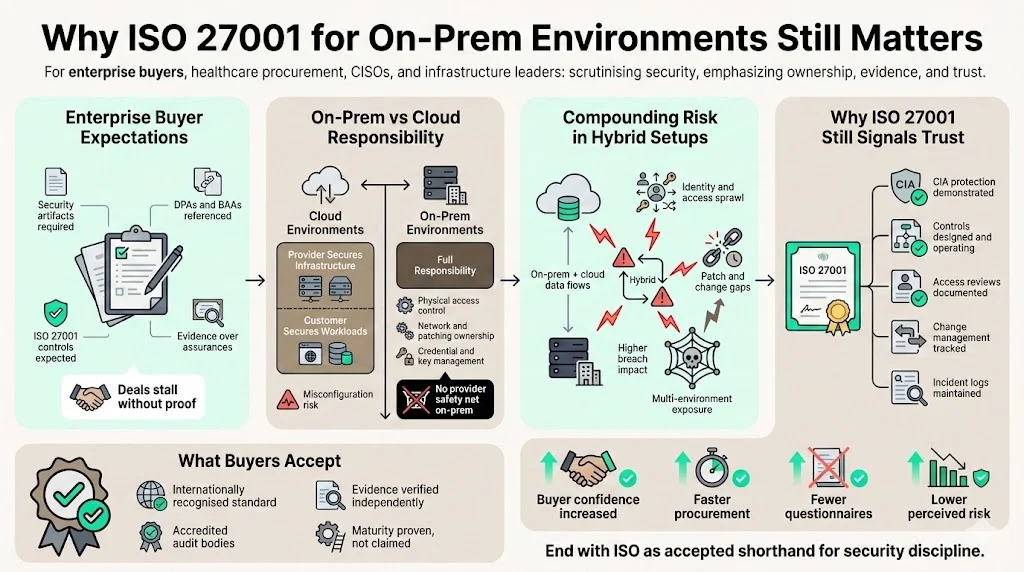
On‑prem environments face even tighter scrutiny than cloud‑only stacks. Public cloud providers follow a shared responsibility model: the provider secures data centers, networking and hypervisors, while customers secure their own workloads. Gartner predicts that 99 percent of cloud security failures arise from misconfigurations and poor identity management. In on‑prem environments there is no shared model; your organisation owns every control, from physical access gates to encryption key storage. Failure to patch a router or rotate credentials is solely your responsibility. In multi‑environment architectures the risk is compounding: IBM’s 2024 breach report notes that 40 percent of breaches involved data stored across multiple environments and these incidents cost more than USD 5 million on average.
For sellers, ISO 27001 For On-Prem certification remains a powerful trust signal. It demonstrates that your team has designed, implemented and maintained a system of controls that protects the confidentiality, integrity and availability (CIA) of data. The standard is an internationally recognised framework for managing information security. Because audits are performed by accredited bodies, enterprise buyers accept ISO certificates as evidence of security maturity. Coupled with ongoing monitoring and operational records, ISO 27001 For On-Prem can speed procurement cycles and reduce repetitive questionnaire cycles.
What ISO 27001 Covers
ISO 27001 is not a checklist; it defines requirements for establishing, implementing, maintaining and continually improving an information security management system. The ISMS must be scoped, risk‑based and supported by top management. The ISO publication stresses that conformity means an organisation has put in place a system to manage risks related to the security of data it owns or handles. The framework is designed to be adaptable—companies can determine which controls apply to their environment and document the rationale in a Statement of Applicability (SoA).
Three principles anchor the standard—confidentiality, integrity and availability (the CIA triad). Data confidentiality ensures that only authorised persons can access information, supported by identity and access management controls. Integrity requires that information remains accurate and complete, with controls like encryption and malware detection. Availability demands that authorised users can access data when needed, supported by redundant hardware and cloud backups. When implementing ISO 27001 For On-Prem, all three principles must be balanced; over‑restrictive controls may harm availability, while lax controls could jeopardize confidentiality and integrity.
The standard includes eleven clauses (0–10) and an annex of controls. Clauses 4–10 define mandatory requirements covering organisational context, leadership, planning, support, operation, performance evaluation and improvement. Annex A lists security controls (e.g., access control, cryptography, physical security, supplier relationships). Because the 2022 revision modernised many controls and introduced new ones (e.g., ICT readiness for business continuity), vendors should adopt the latest version and plan for its amendment in 2024.
Why On‑Prem Is Treated Differently
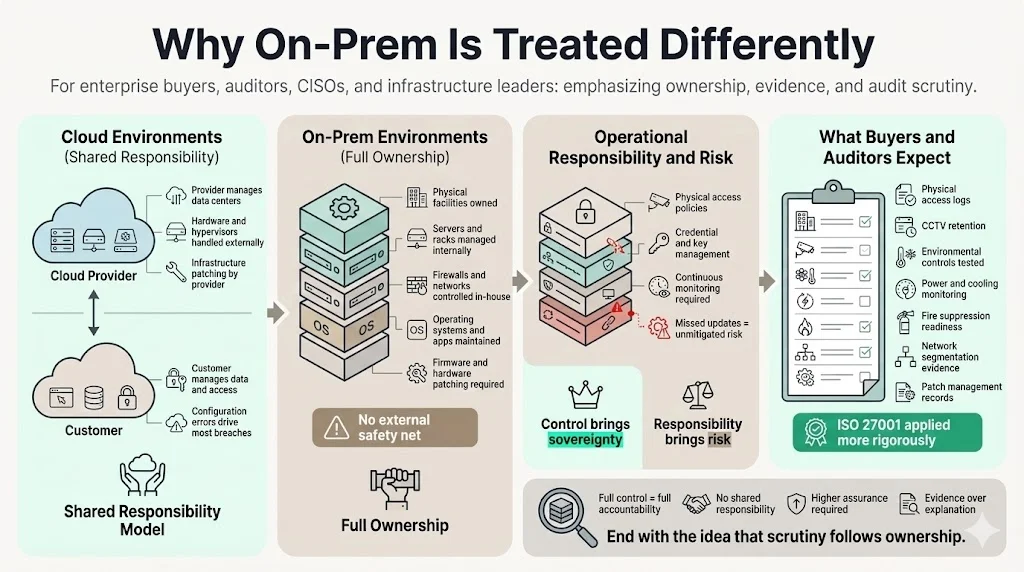
On‑prem infrastructure differs from cloud environments in two key ways: ownership and control. In a cloud context, providers handle physical data centers, hardware maintenance and infrastructure patching, while the customer secures data, access management, encryption and configuration. This shared model means that misconfigurations by customers are the most common cause of breaches.
With on‑premises systems, your organization owns every layer: server rooms, racks, firewalls, networks, operating systems and applications. You define physical access policies, maintain HVAC systems, budget for security teams and purchase tools. There is no external safety net; failing to monitor a firewall or update firmware creates unmitigated risk. This total control can be empowering for highly regulated industries that require strict data sovereignty, but it increases operational responsibility and cost.
Buyers recognise the difference: they ask on‑prem vendors for evidence that physical access to facilities is monitored, CCTV logs are retained and environmental controls (power, cooling, fire suppression) are tested. They also expect proof that network segmentation restricts lateral movement and that patch management policies cover firmware, operating systems and applications. Because there is no shared responsibility, auditors apply ISO 27001 controls more rigorously in on‑prem audits.
Core ISO 27001 For On-Prem Requirements
Information Security Management System (ISMS) Scope
Defining the scope of the ISMS sets the boundaries of your certification. Include all on‑prem data centers, networks and sites that handle enterprise customer data, and describe both physical and logical boundaries. Scoping too narrowly (for example, omitting legacy servers) or too broadly causes delays. Clearly document data flows between on‑prem and cloud services so auditors and stakeholders understand what is in scope and you can prioritise remediation.
Risk Management and Asset Management
Risk management identifies assets and assesses threats, vulnerabilities, likelihood and impact. On‑prem assets include servers, storage, network devices and physical documents. Evaluate both physical risks—such as fire, theft and environmental disasters—and technical risks like malware or misconfiguration. Use a consistent scoring method (for example the NIST Risk Management Framework) to prioritise remediation. Maintain an asset inventory with owners and classification, and align treatment plans with business priorities while documenting residual risks.
Internal Security Policies and Governance
Effective governance requires policies that outline acceptable use, access control, encryption, incident response, vendor management and business continuity. Assign ownership to executives (such as a CISO or CIO) and establish approval flows. Policies must be usable by technical teams, version‑controlled and reviewed regularly. Present evidence of approval, distribution and updates during audits.
Access Control and Identity Management
Annex A.9 emphasises access control. Implement role‑based access control so users receive only the privileges necessary for their roles. Apply multi‑factor authentication for administrators, maintain user registration and de‑registration procedures and conduct periodic access reviews. Log and monitor privileged actions to detect anomalies, and eliminate shared credentials to enforce least‑privilege.
Cybersecurity Controls for On‑Prem Infrastructure
Physical controls include secure site selection, controlled entry points, CCTV, environmental monitoring and cabling security to keep facilities safe and equipment operational. Network controls involve encryption, audit logs, strong passwords, role‑based access, integration with directory services, IP restrictions and regular penetration testing. Segment networks, harden systems, apply patches and use endpoint protection to guard against malware and ransomware. Rely on baseline configurations and maintain offline backups to support recovery.
Data Protection Measures
Protect data at rest and in transit through encryption (for example AES‑256 and TLS) and secure key management. Store backups offsite or in immutable storage with encryption and access controls, define retention periods and ensure secure disposal (such as degaussing). Document backup, retention and destruction activities.
Incident Response and Business Continuity Planning
Prepare for incidents by establishing detection, escalation, containment and recovery procedures. On‑prem plans must address hardware failures, power outages, disasters and cyber attacks. ISO 27001’s disaster recovery controls require secure backups, quick recovery and testing. Business continuity controls demand planning for disruptions and maintaining availability of ICT resources. Define recovery time and point objectives, assign responsibilities and conduct regular drills.
Security Awareness Training
Educate both technical and non‑technical staff about physical tailgating, social engineering, phishing and the proper use of administrator privileges. Provide deeper training for operators on patch management, privileged access and network segmentation. Track participation and test effectiveness through simulations to ensure that knowledge stays current.
ISO 27001 For On-Prem Implementation Steps
Implementing ISO 27001 For On-Prem is a multi‑month effort. Konfirmity’s experience shows that small‑to‑medium organisations can be audit‑ready in about four months, while larger firms may require a year. Self‑managed projects often take 9–12 months; our managed service reduces internal effort from hundreds of hours to about 75 hours annually. A concise plan includes:
- Gap analysis & readiness – Evaluate existing controls against ISO 27001 clauses and Annex A controls. Identify and prioritise gaps across physical and logical assets.
- Define scope & objectives – Decide which data centers, networks, applications and support functions fall under the ISMS. Set measurable security objectives aligned with customer expectations.
- Risk assessment & treatment – Assess risks by considering likelihood and impact of physical, technical and administrative threats. Select Annex A controls and produce a Statement of Applicability that justifies inclusions and exclusions.
- Documentation – Create and maintain policies, procedures, asset inventories, and incident, backup and business continuity plans that reflect actual practices and assign clear ownership.
- Implement controls – Deploy technical measures (network segmentation, patching, encryption, logging) and administrative measures (identity management, multi‑factor authentication and staff training) without disrupting operations.
- Internal audit & management review – Test whether controls are working, gather evidence and plan corrective actions. Management reviews audit results, risk status and performance metrics and agrees on improvements.
- Certification & maintenance – Undergo Stage 1 and Stage 2 audits to validate documentation and control effectiveness. After certification, maintain evidence, update risk assessments and participate in annual surveillance audits. Continuous improvement is not optional.
Required ISO 27001 Documents for On‑Prem Setups
A successful audit requires more than technical controls—it requires evidence. On‑prem teams should prepare the following documents:
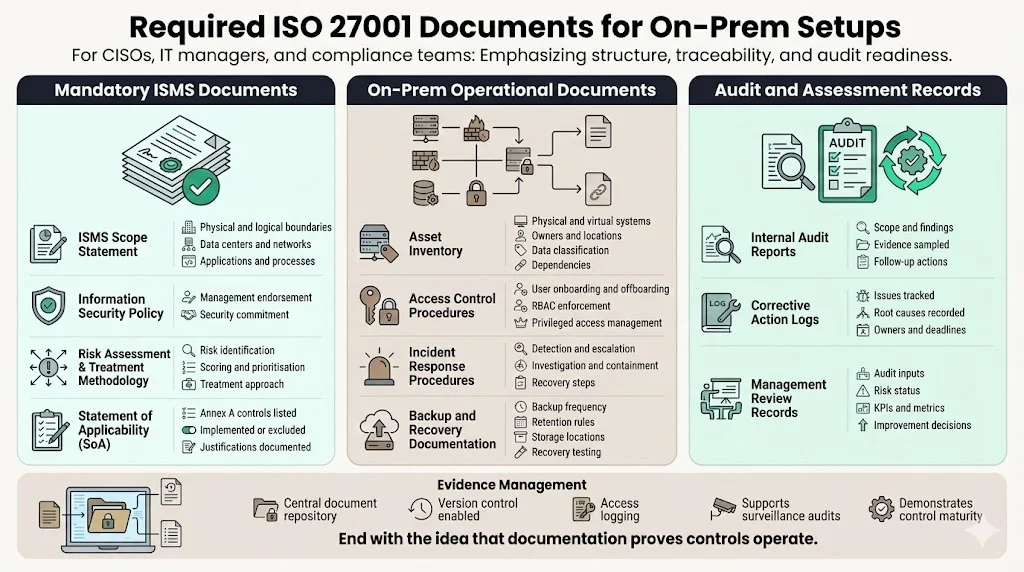
Mandatory ISMS Documents
- ISMS Scope Statement – Defines physical and logical boundaries, data centers, networks, applications and processes included in certification.
- Information Security Policy – High‑level statement endorsed by top management outlining commitment to security.
- Risk Assessment & Treatment Methodology – Describes how risks are identified, scored, prioritised and treated.
- Statement of Applicability (SoA) – Lists each Annex A control and indicates whether it is implemented, excluded or not applicable, with justification.
On‑Prem‑Focused Operational Documents
- Asset Inventory – Records physical and virtual systems, their owners, locations, data classification and dependencies.
- Access Control Procedures – Details user registration/de‑registration, RBAC implementation and privileged access management.
- Incident Response Procedures – Outlines detection, escalation, investigation, containment and recovery steps.
- Backup and Recovery Documentation – Specifies backup frequency, retention, storage locations, encryption, and recovery testing schedules.
Audit and Assessment Records
- Internal Audit Reports – Document findings, evidence sampled, corrective actions and follow‑ups.
- Corrective Action Logs – Track issues, root causes, remediation tasks, responsible owners and due dates.
- Management Review Records – Summarise inputs (audit results, risk status, KPIs), decisions and improvement plans.
Maintaining these documents in a secure repository with version control and access logs demonstrates control over information security and supports surveillance audits.
ISO 27001 Templates, Checklists and Common Challenges
Structured templates and checklists can accelerate ISO 27001 readiness, but they must be adapted to your environment rather than copied verbatim. A risk register template or project plan provides a useful starting point, yet organisations still need to map assets, threats and controls to their own infrastructure. In Konfirmity’s delivery work, we see recurring challenges such as legacy systems with limited security features, incomplete inventories, informal administrative access practices, documentation that does not match real operations and evidence collected only during audit preparation. Addressing these issues early—through segmentation, automated discovery, role‑based access control and continuous monitoring—prevents last‑minute scrambling and improves audit outcomes.
How Enterprise Buyers Evaluate ISO 27001 For On‑Prem Vendors
During procurement, buyers and security teams evaluate both the certificate and the underlying program. For enterprise buyers, achieving ISO 27001 For On-Prem certification provides assurance that physical and logical controls meet rigorous standards. They typically ask for:
- Certification details – Certificate number, issuing body, scope, version (e.g., ISO 27001:2022) and expiration date.
- Statement of Applicability – Evidence that controls relevant to on‑prem environments are implemented. Buyers check that physical security, network segmentation, patch management and backup controls are not excluded.
- Audit reports and corrective action plans – Summary reports from the certification body or internal audits demonstrating how nonconformities were addressed.
- Evidence of continuous monitoring – Logs of access reviews, vulnerability scans, incident response tests and vendor risk assessments. Buyers may request specific documents or screen shares.
A valid ISO 27001 certificate alone is not enough. Buyers verify that controls are operating and that the vendor’s culture supports security. Using ISO 27001 For On‑Prem as a sales trust signal works when combined with transparency and timely responses. Failure to provide evidence or misalignment between documentation and reality undermines trust and can derail sales.
Conclusion
ISO 27001 For On‑Prem remains one of the most effective ways to demonstrate mature, systematic information security to enterprise buyers. The standard’s requirements push organisations to identify assets, assess risks, implement controls, monitor operations and continuously improve. In an era where the average breach costs nearly USD 5 million and multi‑environment breaches are harder to contain, adopting a structured ISMS is not optional—it is fundamental to business survival and growth.
On‑prem vendors bear full responsibility for physical and network security; there is no shared model to fall back on. Building a secure environment therefore demands rigorous physical controls, thoughtful network segmentation, disciplined patch management and robust backup strategies. It also requires organisational investment: clear governance, documented policies, continuous training and regular audits. When done correctly, security becomes integrated into day‑to‑day operations, and compliance follows naturally.
Konfirmity’s human‑led, managed service helps companies start with security and arrive at compliance. We implement controls inside your stack, operate them daily and keep you audit‑ready year‑round. In our experience, durable security that works under pressure not only protects data but accelerates sales, reduces contract friction and builds credibility with enterprise buyers. If you run on‑prem infrastructure, investing in ISO 27001 For On‑Prem is more than a certification—it's a commitment to doing the hard work that buyers and regulators expect.
Frequently Asked Questions (FAQ)
1. What does ISO 27001 mean for on‑prem environments?
ISO 27001 For On‑Prem applies the same principles as for any environment: organisations must establish an ISMS, identify risks, implement controls and continuously improve. The difference lies in control ownership. On‑prem teams control physical access to server rooms, network gear, power, cooling and storage. They must implement and document physical security measures like anti‑tailgating gates, CCTV and environmental monitoring. Risk assessments must consider physical threats alongside cyber threats, and incident response plans must account for hardware failures and disasters.
2. How is ISO 27001 different for on‑prem vs cloud?
In cloud environments, the provider secures the infrastructure (data centers, networking, hardware) while customers secure their workloads. This shared responsibility model means that misconfigurations by customers are often the cause of breaches. In on‑prem environments, your organisation owns all security controls. Therefore, ISO 27001 audits for on‑prem vendors scrutinise physical security, patch management, HVAC systems and backup handling more closely. Buyers expect evidence that you manage every layer of the stack, whereas cloud vendors can rely on provider certifications for some controls.
3. What documents are required for ISO 27001 on‑prem?
At a minimum you need an ISMS scope statement, information security policy, risk assessment & treatment methodology and a Statement of Applicability. On‑prem teams should also document asset inventories, access control procedures, incident response and disaster recovery plans, backup and retention policies, and business continuity plans. Audit records—including internal audit reports, corrective action logs and management review minutes—are required for initial certification and surveillance audits.
4. How long does ISO 27001 implementation take for on‑prem systems?
Timelines vary by company size and complexity. Secureframe notes that small‑to‑medium businesses can be audit‑ready in about four months and complete certification within six months. Larger organisations with multiple data centers and legacy systems may take 9–12 months. Konfirmity’s managed service typically reduces internal effort to around 75 hours per year, compared to 550–600 hours when self‑managed. After certification, the certificate is valid for three years, with surveillance audits in years one and two.
5. What are common audit issues in on‑prem ISO 27001 setups?
Auditors frequently flag incomplete asset inventories, outdated risk assessments and inadequate physical security. Shared or undocumented administrative credentials violate access control requirements. Failure to patch firmware or maintain HVAC systems leads to non‑conformities. Business continuity plans that do not consider loss of physical premises or power outages may fail Annex A 5.29 and 5.30 controls. Evidence gaps—such as missing logs or outdated training records—also delay certification. Organisations can avoid repeat findings by maintaining asset registers, performing regular internal audits and embedding security into operational processes.





.svg)






.svg)
.svg)