Modern enterprises can no longer treat information security as a siloed IT problem. The biggest cyber‑incidents over the last two years — from ransomware to credential stuffing and supply‑chain breaches — share a common thread: people. In 2025, IBM’s Cost of a Data Breach Report found that 68 % of breaches involve a human element. Human error, negligence or malicious insiders caused an estimated 95 % of breaches according to Huntress’s 2025 breach statistics. Even in highly automated technology companies, insiders can mishandle data, fall for phishing scams or walk away with privileged credentials. The Ponemon Institute’s latest insider threat study put the average annual cost of insider incidents at $17.4 million and noted that 83 % of organisations experienced an insider attack last year. For healthcare, the average cost of a data breach remains the highest across industries at $7.42 million, while U.S. breaches across industries climb to $10.22 million. These figures show why strong “people” controls are essential for any information security management system (ISMS).
Over the last 25 years, our team at Konfirmity has supported more than 6,000 audits across SOC 2, ISO 27001, HIPAA, GDPR and other frameworks. We’ve seen first‑hand that an ISMS only succeeds when its human processes — hiring, onboarding, access management and offboarding — are designed thoughtfully and continuously operated. This guide offers an in‑depth look at ISO 27001 HR security controls, explains how they fit within the ISO 27001:2022 standard and other frameworks, and provides step‑by‑step guidance, real‑world examples and ready‑to‑use templates. It is written for CTOs, CISOs, security leaders and compliance officers who need to demonstrate strong human controls to enterprise buyers and regulators.
ISO 27001 and the Role of People Controls
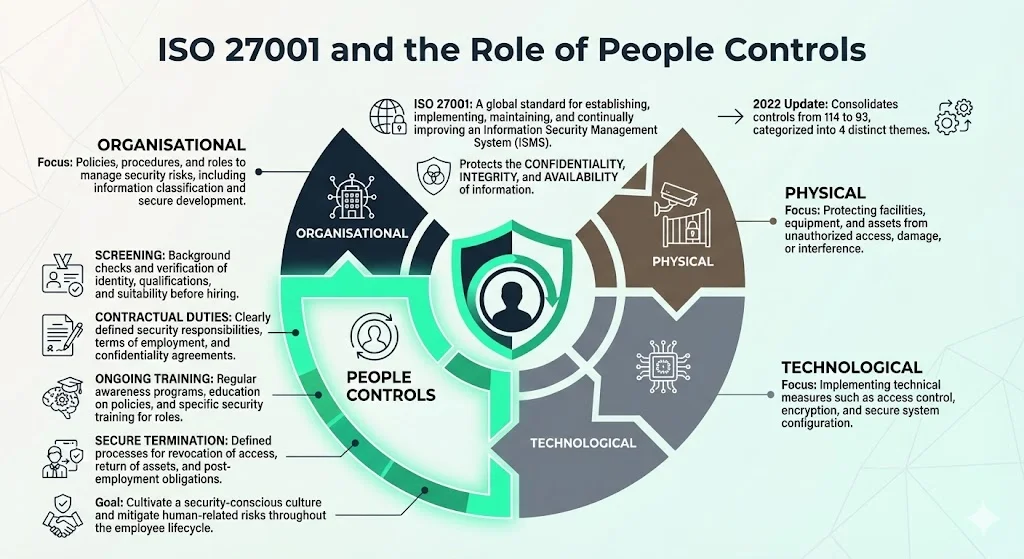
ISO 27001 is an international standard that defines requirements for establishing, implementing, maintaining and continually improving an ISMS. Its purpose is to protect the confidentiality, integrity and availability of information through a risk‑management process that encompasses people, processes and technology. ISO 27001’s structure consists of 11 main clauses (4–10) covering context, leadership, planning, support, operation, performance evaluation and improvement, and an Annex A with a catalogue of security controls.
The 2022 revision of ISO 27001 introduced a major update: Annex A’s 114 controls were consolidated into 93 controls grouped into four themes — organisational, people, physical and technological. This re‑organisation helps organisations map controls to risk areas more intuitively. The people theme corresponds largely to what older versions called Annex A.7: Human Resource Security. It emphasises policies and processes across the employee lifecycle: pre‑employment screening, contractual obligations, ongoing training and secure termination.
Why HR Security Matters for Enterprise Sales
Enterprise procurement teams now scrutinise vendors’ security posture before purchase. HyperComply notes that security questionnaires routinely exceed 250 questions and require input from multiple departments, delaying deals. Buyers expect vendors to have a mature ISMS with ISO 27001 HR security controls or comparable frameworks in place. Evidence of strong HR processes — background checks, confidentiality agreements, least‑privilege access, security awareness training and defined offboarding — demonstrates that the organisation takes insider risk seriously. Without such evidence, deals stall regardless of product quality.
SOC 2 attestation also intersects with human processes. A SOC 2 Type I report evaluates whether controls are properly designed at a point in time; it can be completed in weeks. A SOC 2 Type II report tests those controls over an observation period of 3–12 months and is more rigorous. Many enterprise clients accept only Type II reports because they prove that controls operate effectively over time. Thus, organisations selling to enterprises must implement HR controls that generate continuous evidence: onboarding forms, training logs, access reviews and termination checklists.
In healthcare and regulated industries, HR controls are not optional. The HIPAA Security Rule requires covered entities to designate a security official, implement workforce security procedures, manage information access, train staff and establish incident response and contingency plans. A recent enforcement illustrates the consequences of neglecting these duties: in February 2025, the U.S. Department of Health and Human Services (HHS) imposed a $1.5 million civil money penalty on Warby Parker after investigators discovered failures to conduct a thorough risk analysis and to implement sufficient security measures, leading to a credential‑stuffing attack that exposed almost 200,000 records. Similar resolution agreements in 2025 required providers like PIH Health to pay penalties and adopt corrective action plans after phishing attacks compromised employee email accounts. These cases make clear that regulators expect thorough human‑centric controls.
Deep Dive into ISO 27001 People Controls
ISO 27001:2022’s people controls span pre‑employment, during employment and post‑employment. The following table summarises key controls, their ISO references and purposes:
Each of these controls contributes to reducing human‑driven risk. For example, the Verizon 2025 Data Breach Investigations Report shows that 68 % of breaches involve a human element. By vetting candidates and ensuring that employees understand security obligations, organisations reduce the likelihood of accidents and sabotage. By enforcing NDAs and termination procedures, they prevent departing staff from walking away with sensitive data. And by training employees to recognise phishing and social engineering, they reduce susceptibility to attacks (phishing remains the top initial vector at 16 % of breaches).
Practical Implementation Guide
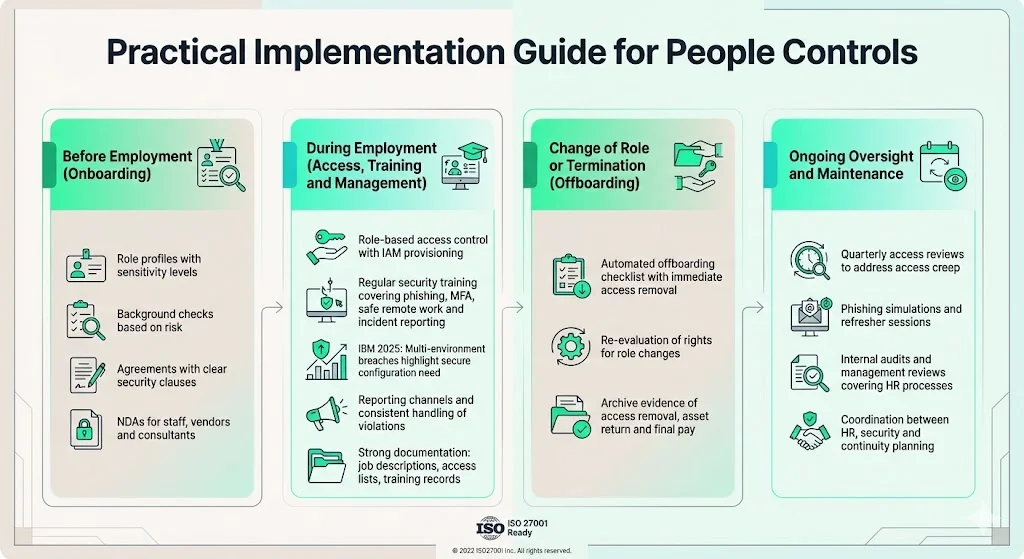
1. Before Employment (Onboarding)
- Define role profiles and sensitivity levels. Identify job functions and assign a sensitivity level based on access to confidential data or critical systems. For example, a software developer with production database access might be rated high sensitivity.
- Perform appropriate background checks. For high‑sensitivity roles, conduct criminal history checks, education verification and reference checks. Ensure checks comply with local labour and data‑protection laws; disproportionate checks could violate regulations.
- Draft employment or contractor agreements with explicit security clauses. Include confidentiality obligations, acceptable use rules, intellectual property ownership and consequences for violations. Ensure agreements are countersigned before granting access. Collect digital or physical signatures and maintain copies as evidence.
- Execute NDAs. Separate NDAs may be necessary for vendors or consultants. Store executed NDAs with personnel files.
2. During Employment (Access, Training and Ongoing Management)
- Implement role‑based access control (RBAC). Work with IT to ensure that new hires receive only the permissions required for their role. Use an identity and access management (IAM) system to automate provisioning and enforce least privilege. Document which roles can access which systems and keep this mapping in your Statement of Applicability (SoA).
- Provide security awareness training. Conduct training as part of onboarding and schedule refreshers at least semi‑annually. Training should cover phishing, password hygiene, use of multi‑factor authentication (MFA), incident reporting, data handling and safe remote work. Keep logs of attendance, completion and quiz results for audit evidence. IBM’s 2025 report found that multi‑environment breaches (spanning on‑premises and cloud) were the costliest at $5.05 million and slowest to contain. Training should therefore emphasise secure configuration and environment segregation.
- Establish incident reporting and disciplinary procedures. Provide anonymous and open channels for employees to report suspected incidents or policy violations. HR and security should jointly manage investigations and apply disciplinary action consistently. Transparent processes encourage reporting and support fairness.
- Maintain thorough documentation. Personnel files should include job descriptions, background checks, signed agreements, training logs, access rights and role‑change history. Treat these records as part of your ISMS documentation; they serve as evidence during ISO 27001 and SOC 2 audits.
3. Change of Role or Termination (Offboarding)
- Trigger an offboarding checklist as soon as notice is given. Immediate steps include revoking all system access, recovering company devices, disabling physical badges, and resetting credentials. Use an automated offboarding workflow integrated with your IAM/HRIS to reduce oversights.
- Re‑evaluate access for role changes. When employees change departments or take on new duties, re‑assess their access rights and adjust accordingly. Document the change and maintain least privilege.
- Archive documentation. Maintain records of offboarding activities, such as access revocation, asset return and final pay. Ensure that NDAs and confidentiality obligations remain enforceable. Retain logs for the period required by your retention policy or relevant laws.
4. Ongoing Oversight and Maintenance
- Periodic access reviews. At least quarterly, review user access to critical systems to confirm that permissions still align with roles. Remove or adjust excessive privileges. This practice addresses the risk of access creep.
- Refresher training and phishing simulations. Reinforce training through simulations and spot‑checks. Simulated phishing campaigns can reveal gaps; track click rates and follow up with targeted coaching.
- Conduct internal audits and management reviews. ISO 27001 requires internal audits to assess the effectiveness of your ISMS. Include HR processes in the audit scope. Management reviews should evaluate training effectiveness, incident reports and performance metrics.
- Integrate HR controls with incident response and business continuity. Ensure that your business continuity plan covers the absence of key staff, backup responsibilities, remote work arrangements and cross‑training. The HIPAA Security Rule mandates contingency planning, and ISO 27001’s Annex A 17 requires incident management and continuity controls.
Ready‑to‑Use Templates and Resources
Practical execution is easier when you have templates. Below is an overview of materials that can be adapted to your organisation.
- Role‑Sensitivity Classification Matrix – A simple table that lists job titles, critical data accessed, sensitivity level (low/medium/high) and required background checks. Use this to justify screening and access decisions.
- Background Check Consent Form – A template requesting candidate consent for criminal, educational and reference checks, including a summary of how data will be used and stored.
- Employment Contract Security Clause – Boilerplate language covering confidentiality obligations, acceptable use, return of company property and post‑termination responsibilities.
- Onboarding Security Checklist – Step‑by‑step tasks such as verifying identity documents, issuing credentials, provisioning accounts, scheduling training and documenting acceptance of policies.
- Security Training Log – A spreadsheet or database capturing employee name, training module, completion date, quiz score and next due date. This record helps demonstrate continuous compliance.
- Incident Reporting Form – A standard form for employees to report suspected security events, with fields for date, description, systems affected and reporter contact information. Provide an anonymous submission option.
- Offboarding Checklist – A detailed list covering account deactivation, hardware return, wiping of personal devices used for remote work, final pay settlement and exit interview.
- Role‑Change Request Form – A document used by managers to request additional or reduced access when an employee’s duties change. Include approval workflow and effective dates.
Addressing Common Challenges
Implementing HR controls is not without obstacles. Here are typical challenges and mitigation strategies:
- Legal and privacy constraints on background checks. Countries have different rules on what employers can review. Conduct only the checks necessary for role risk, obtain informed consent and comply with local data‑protection laws. For example, the EU’s General Data Protection Regulation (GDPR) emphasises data minimisation and purpose limitation; you must justify why each piece of information is collected.
- Employee pushback on NDAs, access restrictions or training. Resistance often stems from poor communication. Explain that controls are part of building customer trust and meeting contractual obligations. Keep training short and relevant to job functions. Incentivise compliance through recognition or gamification.
- Offboarding oversights. In our 6,000+ audits, we have seen multiple breaches traced to former employees retaining VPN access or cloud credentials. Use automated offboarding triggers tied to HRIS events, maintain a thorough asset register and assign joint ownership of the process between HR and IT. Schedule exit audits and confirm that all tokens and keys are revoked.
- Administrative burden. Small teams may feel overwhelmed by documentation. Adopt tools that automate policy distribution, training tracking and access provisioning. Conduct periodic audits rather than constant checks. Managed services like Konfirmity deliver end‑to‑end support: we design controls, implement them inside your stack and maintain evidence year‑round so your team spends roughly 75 hours per year versus 550–600 hours if you self‑manage.
Why HR Security Controls Matter for Enterprise Sales
For companies selling to large enterprises, strong HR security controls directly impact revenue. Procurement teams often require evidence of ISO 27001 certification, SOC 2 Type II reports or HIPAA compliance before signing. Without a documented and operational HR security programme, deals stall or clients choose competitors.
ISO 27001 HR security controls help reduce risk by preventing data leaks and insider threats. IBM’s 2025 study shows that malicious insider breaches average $4.92 million per incident. By vetting employees, limiting privileges and enforcing NDAs, organisations significantly cut this risk. In our experience, companies that adopt a managed HR security programme see fewer findings during audits, accelerate procurement cycles and improve customer trust. Conversely, companies that treat compliance as a “paper exercise” or rely on one‑off consultancy often face surprises during observation periods, leading to failed audits and lost deals.
Conclusion
Human error and insider threats remain the most significant drivers of breaches. In 2025, the average breach cost fell slightly but remains $4.44 million globally, and malicious insider incidents average $4.92 million. Healthcare breaches still cost $7.42 million and take 279 days to contain. To protect data, satisfy regulators and win enterprise clients, companies must treat HR controls as first‑class citizens of their security programme.
ISO 27001 HR security controls provide a clear framework for managing human risks across the employee lifecycle. When implemented correctly and integrated with SOC 2, HIPAA and GDPR requirements, these controls build resilience, reduce insider risk and accelerate sales. The templates and processes described here — from role classification to offboarding — help busy teams operationalise controls without drowning in paperwork. In the end, security that looks good on paper but fails under pressure is a liability; security built into everyday human processes is an asset that pays dividends in trust, compliance and operational excellence.
FAQs
1. What are the four types of controls in ISO 27001?
The 2022 version of ISO 27001 groups controls into four themes: Organisational, People, Physical and Technological. Organisational controls address policies, roles and risk management; people controls cover HR security; physical controls protect facilities and equipment; technological controls cover IT systems and network security.
2. What is ISO 27017 and ISO 27018?
ISO/IEC 27017 provides guidelines for applying ISO 27002 controls to cloud environments. It adds seven cloud‑specific controls addressing shared roles and responsibilities, removal of customer assets, segregation in virtual environments, virtual machine hardening, administrator’s operational security, monitoring of cloud services, and alignment of virtual and physical networks. These measures help cloud service providers and customers understand division of responsibilities and secure their infrastructure.
ISO/IEC 27018 focuses on protecting personally identifiable information (PII) in public clouds. It guides cloud providers on selecting and implementing security controls to protect PII and helps organisations demonstrate compliance with data‑protection regulations.
3. What is Annex A.7 Human Resource Security?
Annex A.7 (now part of the People theme in the 2022 edition) comprises controls covering screening, terms and conditions of employment, security awareness and training, disciplinary process, responsibilities after termination or change of employment, confidentiality or non‑disclosure agreements, remote working and information security event reporting. These controls ensure that human risks are managed before, during and after employment.
4. What is the ISO for security controls?
ISO 27001 is the standard that defines requirements for an ISMS and references security controls in Annex A. An organisation must conduct a risk assessment, select appropriate controls, document them in a Statement of Applicability, implement them, and demonstrate effectiveness through internal audits and external certification.
5. How often should security awareness training be refreshed?
Best practice is to provide training at onboarding and every 6–12 months thereafter. The frequency may depend on risk level and regulatory requirements. Regular simulations (e.g., quarterly phishing tests) help keep awareness high.
6. Do GDPR or data‑privacy laws affect background checks and NDAs?
Yes. Under GDPR, organisations must ensure that personal data collected during background checks is adequate, relevant and limited to what is necessary for the purpose (data minimisation). Consent must be freely given, and candidates have rights to access and rectification. NDAs must not unduly restrict whistleblowing or rights provided by labour laws. Consult legal counsel to tailor checks and agreements for each jurisdiction.
7. What is SOC 2 Type II and how does it relate to HR controls?
A SOC 2 Type II report examines how controls operate over time (3–12 months), making evidence of HR controls critical. Auditors will review onboarding documentation, training logs, access reviews and offboarding records to verify operating effectiveness. Without well‑documented human processes, the report may contain exceptions, delaying or jeopardising customer contracts.
8. How long does it take to prepare for SOC 2 or ISO 27001?
Timelines vary by organisation size and maturity. Konfirmity typically brings clients to SOC 2 Type II readiness in 4–5 months versus the 9–12 months often seen when teams self‑manage. Preparation for ISO 27001 certification may overlap and can take 6–9 months. The key is to design controls that are operationally embedded, not just created for the audit.
9. Do HR controls help with HIPAA and other frameworks?
Yes. HIPAA’s Security Rule mandates workforce security, access management, training and incident procedures. GDPR requires lawful processing and confidentiality. SOC 2, ISO 27001 and CMMC all include controls around people. Implementing ISO 27001 HR security controls provides a foundation that can be mapped to multiple frameworks, reducing duplication of effort.





.svg)






.svg)
.svg)