Enterprise buyers and regulators are no longer satisfied with glossy compliance decks. They look for concrete proof that a service can continue operating under failure and comply with privacy rules across every territory it touches. The average cost of a breach reached $4.88 million in 2024 according to IBM, and by 2025 U.S. breaches cost an average of $10.22 million. At the same time, more than 144 countries have enacted privacy laws and financial institutions faced $4.6 billion in penalties in 2024. Customers now demand assurance that their data will remain available and protected everywhere they do business. This is why ISO 27001 Multi‑Region Architectures are gaining traction: they allow software‑as‑a‑service (SaaS) providers to support global customers, meet strict uptime commitments, and satisfy a growing patchwork of laws. This article examines how to design, secure, and document multi‑region environments through the lens of ISO 27001, drawing on Konfirmity’s experience supporting more than 6 000 audits over 25 years. Our goal is to equip CTOs, CISOs and compliance leaders with the insight needed to build resilient architectures that stand up to auditors and buyers alike.
Why Multi‑Region Design Is Becoming the Norm for Enterprise SaaS
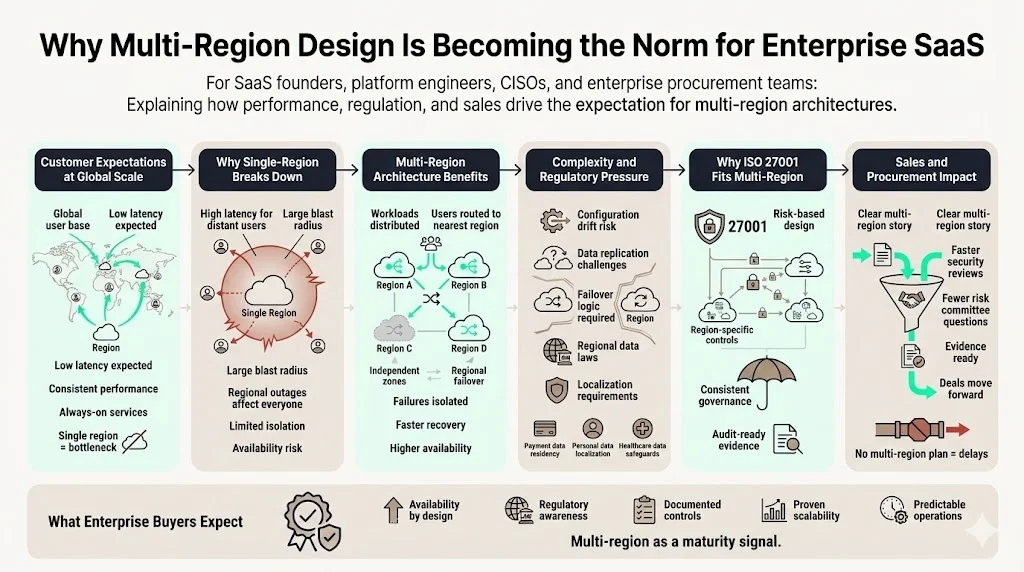
When planning multi‑region environments for ISO 27001, the SaaS business model thrives on scale and availability. Customers from New York to New Delhi expect low latency and consistent performance. Single‑region deployments can’t meet these expectations because network distance introduces latency and increases the blast radius of outages. Multi‑region deployments distribute workloads across independent geographic zones. Users connect to the nearest region, reducing round‑trip times and isolating failures to a single area. A study of streaming services shows that global platforms like Netflix and Slack use this approach to improve performance and resiliency.
High availability comes at a cost, however. Duplicating services and data across regions introduces complexity. Development teams must manage configuration drift, data replication, and failover logic. For regulated industries, the challenge is amplified by local laws. India’s Reserve Bank requires payment data to remain in the country; cross‑border copies must be deleted within 24 hours. China’s Cybersecurity Law compels domestic storage of personal and critical business data. Financial services regulators worldwide have enacted more than 135 localization laws, driving banks to build region‑specific platforms. Healthcare organizations must implement physical, technical and administrative safeguards for protected health information (PHI), including encryption and business‑associate agreements. ISO 27001 multi‑region architectures are often the only practical way to satisfy these conflicting demands while still delivering the scale and responsiveness customers expect.
From a business perspective, multi‑region strategies also help close deals faster. Enterprise procurement teams routinely issue security questionnaires and request evidence of compliance with ISO 27001, SOC 2, HIPAA, GDPR and other frameworks. In our experience, lacking a clear multi‑region story delays deals by months and invites scrutiny from risk committees. Conversely, organizations that design regions deliberately, map data flows and keep audit artefacts ready see deals move forward smoothly.
What ISO 27001 Actually Requires (and What It Does Not)
When building ISO 27001 Multi‑Region Architectures, it is important to understand that ISO 27001 is not a rigid checklist. Instead, the standard adopts a risk‑based approach that recognizes organizations vary in size, sector and technology. URM Consulting notes that ISO 27001 does not prescribe specific controls; it requires organizations to identify risks and select controls appropriate to their context. The standard’s annex provides a catalogue of 93 control objectives (reduced from 114 in the 2013 revision) but leaves implementation details to the organization. This means ISO 27001 does not mandate a single‑region or multi‑region setup. Instead, it expects organizations to define their information security management system (ISMS) scope, perform a risk assessment (Clause 6.1.2), and document the chosen controls in a Statement of Applicability (SoA).
The standard distinguishes between prescriptive rules and control objectives. A prescriptive rule might require encryption of all data at rest, whereas a control objective might state “ensure unauthorized access to information is prevented.” The chosen method—encryption, tokenization, or strict access control—is left to the implementer. This flexibility is beneficial for multi‑region systems: some regions may require cryptographic secrets to stay local, while others allow centralized secret management. By mapping risks and documenting how each control objective is met per region, organizations can prove compliance without sacrificing architectural autonomy.
Clause 6.1.2, the heart of ISO 27001’s risk management process, requires organizations to define risk criteria, identify and assess risks to confidentiality, integrity and availability, and document treatment plans. For multi‑region architectures, the risk assessment should include region‑specific threats such as internet latency, cross‑border data transfers, and local regulatory penalties. Healthcare providers, for instance, must address threats like ransomware and insider abuse of PHI. The risk assessment forms the basis for selecting controls and establishing the SoA. In short, ISO 27001’s flexibility allows multi‑region designs, provided organizations can justify their choices through a documented risk management process.
Understanding Multi‑Region Architectures in an ISO 27001 Context
“Multi‑region” refers to deploying computing, storage and networking resources in two or more geographically distinct data centres. Each region operates independently but can replicate data and services to others. The two most common patterns are active‑active and active‑passive, illustrated below.
In an active‑active setup, identical environments run simultaneously in multiple regions. Traffic is distributed between them, and data is replicated bi‑directionally. This delivers high throughput and fault tolerance; if one region fails, the others continue to serve requests seamlessly. Enterprises often choose active‑active for mission‑critical workloads where downtime is unacceptable. However, it requires careful consistency management and conflict resolution.
An active‑passive architecture designates one region as the primary and maintains a secondary region as a warm standby. The secondary region receives replicated data but does not serve traffic until failover is initiated. This approach reduces resource consumption and simplifies data consistency at the cost of slower failover and possible service interruption. Active‑passive is suitable for workloads with lower tolerance for transient outages or budget constraints.
A third pattern gaining popularity is regional isolation with shared services. Each region hosts an autonomous stack (application, database, user authentication) and shares only a minimal set of global services such as billing or analytics. The design principle, articulated by engineering teams at Linear, is to ensure that if one region experiences problems the others remain unaffected. Regional isolation simplifies compliance because data rarely crosses borders, reducing risk of violating localization laws. It also conforms to zero‑trust principles by limiting the blast radius of compromises.
When designing multi‑region environments under ISO 27001, security teams should consider how redundancy planning supports the standard’s availability objectives. Controls such as uninterruptible power supplies, fault‑tolerant infrastructure and regular failover testing map directly to Annex A controls on availability and backup. At the same time, teams must address security implications: replicating data across regions enlarges the attack surface, and inconsistent logging can impede incident response. The next sections examine these complexities.
Data Sovereignty and Data Localization Considerations
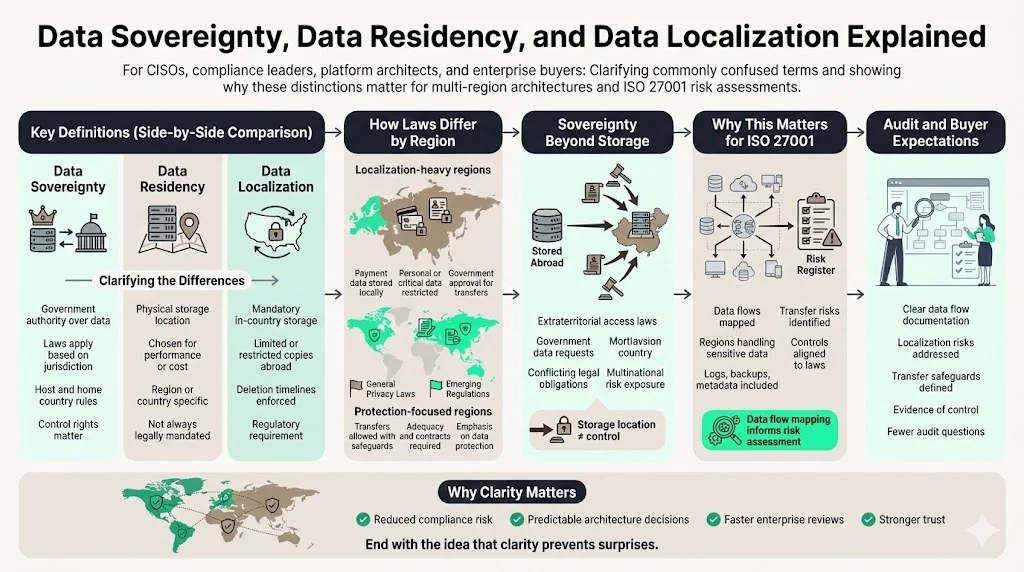
Before architecting multi‑region systems, it is critical to distinguish data sovereignty, data localization and data residency. Oracle defines data sovereignty as a government’s right to regulate data stored within its borders; organizations storing data abroad must comply with both the host and home countries’ laws. Data residency refers to the geographic location where data is stored—often chosen for performance or cost reasons. Data localization goes further, requiring that certain data be stored within a country’s borders; copies may exist abroad under strict conditions. The infographic below summarizes these concepts:
The divergence between sovereignty and localization is stark. The Reserve Bank of India mandates that payment data be stored only in India and that any foreign copy be deleted within 24 hours. China requires personal and critical data to stay within its borders and subjects cross‑border transfers to government approval. Russia and Nigeria enforce similar laws. By contrast, the European Union’s GDPR does not insist on domestic storage but restricts transfers to countries without adequate protection and mandates strong safeguards such as standard contractual clauses. Canada’s PIPEDA and Brazil’s LGPD adopt similar stances, focusing on protection rather than mandatory localization.
Data sovereignty concerns extend past storage location to control rights. The U.S. CLOUD Act allows federal agencies to access data held by American companies even if stored abroad. China’s Intelligence Law requires domestic companies to share data with authorities. These extraterritorial claims create conflicting obligations for multinational companies. ISACA notes that cross‑border data flows necessitate navigating overlaps between data jurisdiction, applicable laws and local compliance. Organizations must monitor changes across jurisdictions and adapt accordingly.
In practice, mapping data flows is an essential input to the ISO 27001 risk assessment. Complyan suggests documenting external entities, processes, data stores and flows to identify where sensitive information travels and where vulnerabilities exist. Creating accurate data flow maps reveals which regions handle personal data, logs, backups and metadata—helping teams ensure architectures comply with localization laws. During audits, these maps demonstrate that data transfer risks are understood and controlled.
Regional Compliance and Regulatory Overlap
Global compliance is not monolithic. Financial services face strict localization and privacy rules, with average breach costs around $6.08 million and more than 135 countries enforcing data localization. Healthcare organizations must implement physical, technical and administrative safeguards for protected health information and comply with GDPR’s breach‑notification deadlines and localization requirements. Government procurement introduces another layer of complexity: the U.S. CLOUD Act compels disclosure of data held by U.S. providers even if stored abroad, while GDPR restricts transfers to jurisdictions lacking adequate protections. Organizations building ISO 27001 Multi‑Region Architectures must map these overlapping obligations, ensure encryption and access controls meet local rules, and document decisions in the risk assessment and Statement of Applicability.
Regulators are increasingly prepared to levy fines when obligations are not met. AuditBoard reported that financial institutions paid $4.6 billion in penalties in 2024 and that 95% of those fines came from North America. Supervisory bodies expect proactive risk governance rather than check‑box compliance; in practice this means demonstrating real‑time control effectiveness and integrating vendor risk management.
Designing Multi‑Region Security Controls
Implementing effective controls across regions is the core of any ISO 27001 Multi‑Region Architectures programme. Identity and access should be regionalized to minimize latency and comply with localization laws while using a global governance system to enforce least‑privilege and track approvals. Encryption at rest and in transit is baseline; proposed HIPAA updates mandate it. Adopt region‑scoped secret management, ensuring keys are generated, stored and rotated locally when required. Logging and monitoring must capture events consistently across regions; SentinelOne warns that fragmented logs and cross‑border investigations hinder incident response. Use centralized aggregation with regional collectors to maintain a unified forensic timeline. Strive for control consistency but allow justified variation—for example, deploying region‑specific identity providers or cryptographic algorithms when local standards dictate. Document all decisions in the risk assessment and Statement of Applicability.
Continuous monitoring across regions is essential. Use dashboards to track anomalies in access control and log ingestion and integrate vulnerability scans into your monitoring stack. This holistic view reduces detection time and demonstrates operational maturity to buyers and regulators.
Disaster Recovery and Business Continuity Across Regions
Redundancy alone does not guarantee resilience. ISO 27001 requires organizations to define Recovery Time Objectives (RTOs) and Recovery Point Objectives (RPOs) and match replication strategies to those targets. Active‑active designs deliver near‑zero recovery but may conflict with localization laws, whereas active‑passive setups trade some delay for simplified compliance. For ISO 27001 Multi‑Region Architectures, threat models should include region failure, network outages and government intervention. Regular failover testing confirms that cross‑region failover does not inadvertently move regulated data across borders. Documenting tests and remediation actions is essential; auditors often sample this evidence. Continuity plans should also cover partial outages (e.g., degraded read‑only modes) and customer communication procedures.
Risk Management for Multi‑Region Architectures
Managing risk is the heart of ISO 27001. Multi‑region architectures introduce region‑specific risks (local compliance, geopolitical instability) and shared risks (centralized control plane failures, misconfigured replication, supplier dependencies). Dependencies on a single vendor’s backbone can cause cascading outages, and incident response across borders is complicated; evidence may reside in jurisdictions with conflicting laws. Organizations should maintain a living risk register that is updated whenever regions are added or controls change, and develop runbooks that address cross‑border incidents and engage legal counsel. Continuous review of this register during internal audits embodies ISO 27001’s continual improvement approach.
Cloud Architecture Patterns That Support ISO 27001
Architectural choices can either simplify or complicate compliance. Favor cloud‑native services that offer explicit region isolation and data residency options. Separate control planes (deployment pipelines, management APIs) from data planes (customer data storage and processing) to limit the exposure of sensitive data. Prefer region‑scoped resources and explicitly manage replication rather than relying on global services that replicate automatically. Use reference architectures mapped to ISO 27001 controls for network segmentation, identity management and monitoring, and automate deployments to avoid ad hoc cross‑region tunnels. Automation and transparency make audits smoother and reduce the risk of configuration drift.
How Auditors Review Multi‑Region Systems
Auditors begin with simple questions: which regions exist, what data lives in each, and how are controls applied consistently in ISO 27001 Multi‑Region Architectures? They review architecture diagrams and data flow maps, then sample controls such as access logs, management of encryption secrets and backup procedures. Evidence should include identity and access records, secret management logs, monitoring documentation, disaster recovery test reports and vendor contracts specifying data location and audit rights. Many audit findings stem from inconsistent controls between regions or assumptions that provider certifications extend to customer workloads. To avoid this, assemble a region‑by‑region evidence pack, ensure the Statement of Applicability references regional variations and be prepared to explain trade‑offs like centralized versus local encryption secrets.
Documentation That Makes or Breaks Multi‑Region Compliance
Clear documentation is the scaffolding for audit success. Keep up‑to‑date architecture diagrams showing regional boundaries and inter‑region links. Maintain data flow maps tied to your risk assessment and risk register. Include regional context in the Statement of Applicability and write policies that reflect geographic variation in access management, logging, incident response and disaster recovery. When expanding into a new region, document approvals, risk assessments and control implementations. These artefacts not only satisfy auditors but also bring security, engineering and legal teams together.
Common Mistakes Enterprises Make
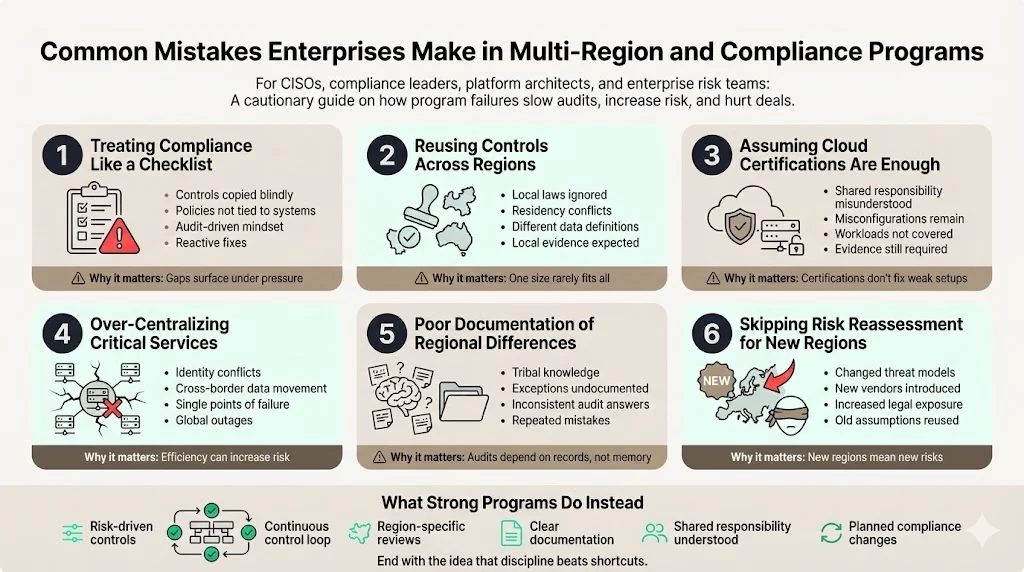
1) Treating Compliance Like a Checklist
Many enterprises approach compliance as a box-ticking task. This leads to weak controls and gaps that only show up during audits or incidents.
- Controls are copied from other regions without checking local risk
- Policies exist on paper but are not tied to real systems
- Teams focus on passing audits instead of reducing actual exposure
- New regulations trigger rushed fixes instead of planned changes
Compliance works better when controls are selected because they reduce real risk, not because they appear in a template.
2) Blindly Reusing Controls Across Regions
What works in one region may fail or even break the rules in another.
- Data residency laws may block centralized logging or storage
- Encryption, retention, and access rules often differ by country
- Legal definitions of personal or sensitive data are not consistent
- Regulators may expect local evidence, not global reports
Each region needs its own risk review before controls are reused.
3) Assuming Cloud Provider Certifications Are Enough
A common and costly assumption is that cloud certifications cover everything.
- Cloud providers secure the platform, not customer workloads
- Misconfigured storage, identity, or networking remains the customer’s issue
- Audit evidence must show how your setup meets requirements
- Shared responsibility is often misunderstood by non-technical teams
Certifications help, but they do not protect poorly configured systems.
4) Over-Centralizing Critical Services
Centralization feels efficient, but it can create legal and operational trouble.
- Central identity systems may conflict with local access rules
- Global monitoring can move sensitive data across borders
- Central secret stores can become single points of failure
- Outages or breaches affect every region at once
Some services must stay regional, even if that adds complexity.
5) Poor Documentation of Regional Differences
Enterprises often rely on tribal knowledge instead of clear records.
- Regional exceptions are known by people, not written down
- Control differences are lost during staff changes
- Audit responses vary depending on who answers
- Launching new regions repeats old mistakes
Clear documentation saves time and reduces risk during audits.
6) Skipping Risk Reassessment for New Regions
Launching a new region is not just a deployment task.
- Threat models change with geography and regulation
- Local vendors and services introduce new risks
- Legal exposure increases with each jurisdiction
- Old assumptions may no longer hold
Every region deserves a fresh risk review before going live.
Practical Takeaways for Enterprise‑Focused Companies
For organizations pursuing ISO 27001 Multi‑Region Architectures, three themes stand out from Konfirmity’s 6 000‑plus audits. First, plan deliberately: map customer locations and applicable laws, and add regions only when business needs justify the complexity. Second, standardize controls and processes where possible but localize data storage, encryption secrets and logging when required by law, documenting the rationale in your risk assessment. Third, transparency builds trust—share architecture diagrams, control mappings and incident response plans with prospective customers to streamline procurement. Integrate ISO 27001 into your design phase and match controls to SOC 2, HIPAA and GDPR to maximize evidence reuse. Managed services like Konfirmity’s can reduce readiness timelines from 6–12 months to about 4–5 months with roughly 75 hours of internal effort and avoid the 550–600 hours typical of self‑managed projects.
IBM’s 2024 breach report estimates the global average cost of a data breach at $4.88 million. Poor security undermines buyer trust and slows deals, while investing in sound controls and continuous evidence pays dividends in risk reduction and commercial velocity.
Conclusion
Building ISO 27001 Multi‑Region Architectures is challenging but achievable. Success begins with a clear understanding of legal obligations, a rigorous risk assessment and thoughtful architectural patterns that balance regional autonomy with global consistency. Strong multi‑region designs reduce downtime, satisfy buyers and minimize regulatory penalties. By assigning clear risk ownership across regions, separating control and data planes, implementing region‑specific encryption and logging, and documenting everything, organizations can operate globally with confidence. As privacy laws proliferate and breach costs rise, investing in resilient architectures and human‑led compliance programs will pay dividends—freeing teams to innovate while staying secure and audit‑ready.
In the rapidly evolving cloud economy, resilience and compliance are essential differentiators that help providers win and retain demanding enterprise clients.
Frequently Asked Questions
1) Does ISO 27001 allow multi‑region systems?
Yes. ISO 27001 is a risk‑based standard that does not prescribe single‑region or multi‑region deployments. Organizations may adopt multi‑region architectures if they can identify associated risks, implement appropriate controls and document them in the Statement of Applicability. Auditors will look for evidence that risks such as cross‑border data transfer, encryption and regional failure have been addressed.
2) How does data residency affect ISO 27001?
Data residency laws dictate where data must be stored. These laws vary: India requires payment data to stay in‑country, while GDPR restricts transfers to countries without adequate protections. ISO 27001 requires organizations to identify and comply with local laws as part of their risk assessment. Therefore, data residency directly influences region placement, encryption and access controls.
3) What risks exist in multi‑region setups?
Risks include inconsistent control implementation, compliance violations due to cross‑border transfers, increased attack surface, logging fragmentation and complex incident response. SentinelOne notes that misconfigured or under‑retained logs across clouds lead to incomplete evidence and delayed investigations, and cross‑border investigations are slowed by conflicting laws. These risks must be captured in the risk register and treated through automation, regional segmentation and clear incident runbooks.
4) How do auditors assess regional controls?
Auditors review architecture diagrams, data flow maps, risk assessments and the SoA. They sample controls in each region, such as access logs, encryption secrets and backups. Evidence expectations include region‑specific policies, test reports and vendor contracts specifying data location and audit rights. Auditors also check that controls operate consistently over time and across regions.
5) What documentation is needed for multi‑region compliance?
At a minimum, organizations should maintain architecture diagrams with region boundaries, data flow maps tied to risks, a regionalized SoA, policies reflecting local requirements, and change management records for region expansion. Regularly update these artefacts to reflect changes and ensure they stay consistent with the living risk register.





.svg)






.svg)
.svg)