Most enterprise buyers ask for assurance artifacts before procurement. Questionnaires, data‑processing agreements and vendor risk reviews now arrive long before any statement of work. In 2025 the global average cost of a data breach was $4.44 million after a 9 percent drop from the previous year, yet phishing alone still cost organizations about $4.8 million per incident. Healthcare breaches remained the most expensive at $7.42 million and took roughly nine months to contain. Unsurprisingly, 81% of organizations adopted ISO 27001 by 2025 – up from 67% in 2024. Buyers no longer accept loose promises about security; they review evidence of a functioning management system. This ISO 27001 Readiness Guide (hereafter “the guide”) speaks to technical and business leaders who build programs that stand up to auditors and large customers.
Why Enterprise Buyers Expect ISO 27001 Readiness
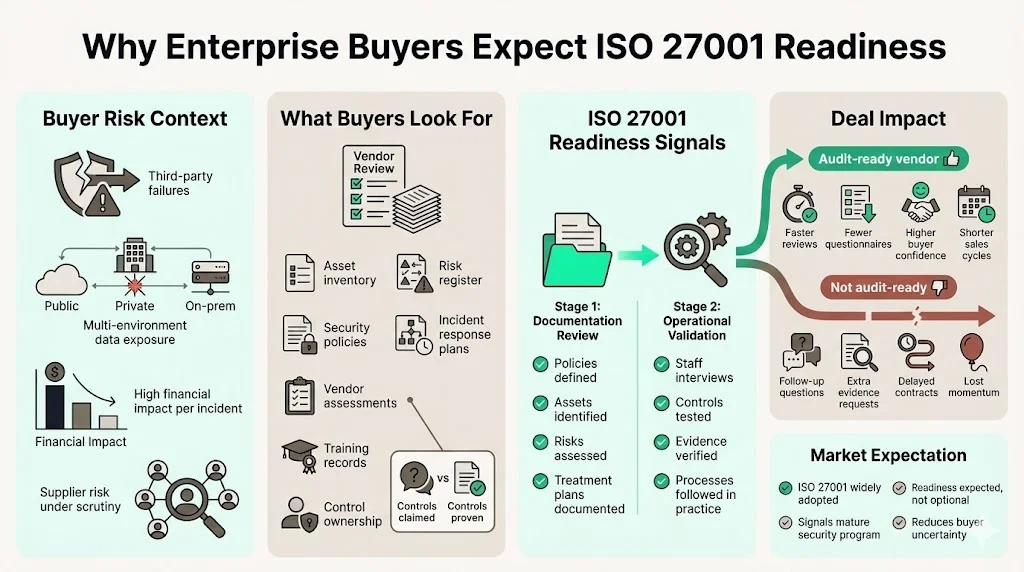
Enterprise procurement teams routinely examine a vendor’s information security posture. Third‑party failures ranked as the second most common attack vector in IBM’s 2025 breach study and cost $4.91 million per incident. Data distributed across multiple environments – public clouds, private clouds and on‑premises systems – was involved in 30% of breaches, averaging $5.05 million. Buyers see those numbers and want to know whether a potential supplier has identified its assets, assessed risks and installed controls. They will ask for policies, risk registers, incident response plans, vendor assessments and training records. They also look at adoption trends; when four‑fifths of organizations now follow ISO 27001, a vendor who is not at least audit-ready stands out in a bad way.
Deals stall when there is a gap between “controls in place” and “audit‑ready.” Teams often claim they have implemented security measures, but they struggle to produce documented evidence that an independent auditor could verify. Stage 1 of the certification audit is largely a documentation review; without clear policies, asset inventories, risk assessments and treatment plans, companies fail at this initial hurdle. Stage 2 involves an onsite review where auditors interview staff and test that controls work in practice. Buyers know that readiness for these audits correlates with the maturity of the vendor’s security program. A vendor that cannot demonstrate readiness creates doubt, increasing security questionnaires, follow‑up requests and contract delays.
How Readiness Reduces Sales Friction
Large customers weigh security heavily during procurement. A readiness program reduces friction by providing evidence quickly. The average data breach cost $4.88 million in 2024 and audits cost between $50 000 and $200 000. Investing in a readiness program costs far less than the operational or reputational impact of a breach. It also reduces the burden of responding to questionnaires; a well‑structured ISMS allows you to provide policies, risk assessments and control evidence without scrambling. Vendors with audit‑ready programs typically see fewer follow‑up questions, faster legal reviews and shorter contract cycles. They also build trust: demonstrating that you monitor vendors, test incidents and train staff shows that security is built into operations rather than bolted on for compliance.
What ISO 27001 Readiness Really Means
Readiness vs. Certification
Confusion often arises between being “aligned” with ISO 27001 and being certified. URM Consulting notes that some organizations believe they can save money by “aligning” with the standard instead of certifying, but this approach often costs more and misses business opportunities. A compliant management system might follow the standard internally, but there is no independent evaluation. Certification involves an accredited third‑party audit and a three‑year cycle of audits. Certification bodies review whether your ISMS meets the standard, whether risks are addressed and whether continuous improvement is occurring. Companies that stop at self‑declaration gain little recognition from major customers.
Stage 1 and Stage 2 audits further illustrate the distinction. Stage 1 is a high‑level documentation review. Auditors check policies, procedures, scope statements and risk registers to confirm that the ISMS has been developed in accordance with ISO 27001. Stage 2 is a deeper, onsite assessment where auditors verify that the documented controls operate effectively. Evidence of internal audits and management reviews is required. Thus, readiness means having the documentation, controls and operational practices in place so that an auditor can proceed through Stage 1 without major non‑conformities and then verify effectiveness during Stage 2.
How Readiness Fits into Information Security Management
ISO 27001 is structured around clauses 4–10, which define the management system requirements, and Annex A, which lists controls. Secureframe notes that Annex A contains 93 controls grouped into four categories—organizational, people, physical and technological—and that the 2022 edition introduced 11 new controls such as threat intelligence, cloud service security and secure coding. Clause 6.1.2 of ISO 27001 requires organizations to establish and maintain a risk assessment process and to set risk acceptance criteria, ensuring that repeated assessments produce consistent results. ISO 27001 readiness therefore requires both management system documentation and carefully selected controls that address identified risks. The standard offers flexibility: organizations decide which controls apply and explain exclusions in a Statement of Applicability (SoA).
Common Misconceptions at the Readiness Stage
Some teams think readiness is purely a paperwork task. However, controls must operate. Secureframe notes that auditors will look for high‑level policies, a regular process for reviewing those policies and evidence that roles and responsibilities are clearly defined. Vendor relationships and supplier risk management are part of the scope, as are access controls and user privileges and asset management practices. Ready organizations also recognize that human error is a major cause of incidents. DataGuard highlights that awareness training is a core requirement and that auditors look for evidence of proactive education.
Another misconception is that readiness is simply about aligning with ISO 27001. URM Consulting warns that self‑assessing alignment often fails to set appropriate scope and continual improvement, and lacks the rigor and impartiality of a certified auditor. Attempting to “avoid the unnecessary hassle of certification” can create more work when large customers demand accredited evidence.
Why Enterprise Prospects Review Readiness
Security questionnaires often ask whether you have completed an ISO 27001 gap assessment, whether your ISMS scope covers shared services and third‑party data processors, and whether you have performed an internal audit. Buyers also request evidence of business continuity and incident response plans because frameworks such as GDPR, HIPAA and NIS2 require them. Naq Cyber emphasises that robust business continuity and incident response plans are essential for compliance with standards like ISO 27001 and GDPR. IBM’s breach study found that vendor and supply chain breaches cost nearly $5 million. Prospects want proof that you manage vendor risk and monitor controls continuously.
ISO 27001 Readiness Guide: Practical Steps

Step 1: Secure Management Commitment Early
Executive sponsorship is the biggest determinant of readiness timelines. Without leadership backing, teams struggle to prioritise tasks, allocate resources and make decisions. Scrut’s readiness timeline study recommends securing a project sponsor and designating owners for each control area; strong leadership support resolves resource conflicts and keeps certification on track. Management also approves budgets for policy development, risk tools, evidence collection and training. A lack of leadership can delay readiness by months; common symptoms include stalled policies, unapproved budgets and unclear responsibilities.
Assign clear ownership for the ISMS. Identify a primary champion (often the CISO or CTO) who has authority to make decisions. Then designate control owners across IT, engineering, product, human resources and legal. Each owner should have both accountability and decision authority. Ensure that managers commit staff time—untracked commitments often derail schedules. Budget for technology (risk and evidence collection platforms), training, consultant time and certification audits. Many teams underestimate time requirements; the Scrut study estimates 2–6 months for implementation and 4–6 weeks for the external audit.
Example: One SaaS company attempted readiness without executive involvement. Engineers built controls, but there was no budget for training or evidence tools. When an enterprise prospect demanded proof, the team scrambled to update documents and conduct an ad hoc internal audit. Stage 1 feedback identified major gaps, and the sales deal slipped to the next quarter. When leadership later prioritized the program, funding and dedicated resources allowed them to finish readiness in four months.
Step 2: Define the ISMS Scope Clearly
Scoping sets boundaries for your ISMS. AuditBoard explains that the scope determines what assets and processes the risk assessment will consider and cautions against scoping too broadly or too narrowly. Overly broad scopes introduce unnecessary work; narrow scopes leave critical dependencies unprotected. Start by listing information assets—customer databases, code repositories, infrastructure, vendor services and paper records. Include physical locations, cloud environments and SaaS platforms. Identify processes that handle sensitive data, such as product development, customer support and HR onboarding.
Explicitly include shared services and third‑party tools that process, transmit or store customer data. Clause 4.3 of ISO 27001 requires organisations to control externally provided services. Large customers often ask whether cloud providers, analytics platforms or ticketing systems fall under scope. Align the scope with enterprise expectations by matching it to the data processed on behalf of clients. Document the scope in a statement that lists included assets and exclusions, with justifications for exclusions. For instance, an internal marketing system that does not handle customer data may be excluded.
Example scope statement: “The ISMS applies to all products and services that process, store or transmit customer data, including our production platform, supporting infrastructure, employee laptops, code repositories and SaaS tools (Jira, GitHub, AWS, GCP). It excludes marketing tools not processing customer data.”
Step 3: Build an Asset Management Inventory
Asset management is foundational. Secureframe stresses that asset management controls ensure companies identify information assets and assign responsibilities. Start by cataloguing information assets (databases, application servers, source code, encryption keys, credentials), physical assets (laptops, servers, backup media) and intangible assets (intellectual property, licenses). Classify data by sensitivity (public, internal, confidential, restricted) and record owners for each asset. Map assets to systems and vendors so that third‑party dependencies are visible. Controls should include processes for adding and decommissioning assets, ensuring updates to inventories when new services or staff join.
Auditors often spot gaps early when asset inventories are incomplete. Common issues include missing SaaS tools, untracked cloud services and undocumented configurations. Address these before an external audit. Use automated tools where possible to synchronise asset lists with real systems.
Step 4: Perform a Risk Assessment
Clause 6.1.2 of ISO 27001 mandates an information security risk assessment process. The process must define risk acceptance criteria, ensure repeatable assessments and identify risk owners. AuditBoard describes the assessment as the systematic process to identify, analyse and evaluate information security risks. A risk assessment informs everything from your Statement of Applicability to resilience strategies. Risk program owners typically include IT compliance managers, CISOs and internal audit teams, but effective risk management requires cross‑functional input.
Key steps:
- Identify threats and vulnerabilities: Gather stakeholders to brainstorm potential threats (phishing, malware, insider threats, unpatched systems) and vulnerabilities (lack of access controls, outdated software). Include regulatory requirements like GDPR, HIPAA and NIS2 in the context. According to Hightable, risk assessments must consider confidentiality, integrity and availability.
- Analyse and score risks: Evaluate the likelihood of each threat occurring and the impact on business operations. Use qualitative scales (e.g., high, medium, low) or quantitative methods (e.g., 1–5 scoring). Hightable emphasises establishing risk acceptance criteria and ensures that repeated assessments produce consistent results.
- Assign risk owners: Each risk must have a designated owner. Hightable states that risks should be assigned to individuals or roles, not teams. This ensures accountability for remediation.
- Document findings: Record risks, scores and owners in a risk register. This register becomes part of your evidence during internal and external audits. AuditBoard highlights that the risk assessment should be updated during initial implementation, annual reviews, significant changes and pre‑audit preparation.
Example: A SaaS platform hosting customer data on AWS identified the following risk: “If an IAM misconfiguration allows excessive privileges, attackers could access all customer databases.” The likelihood was rated high, the impact high and the risk owner assigned to the cloud infrastructure manager. The risk treatment plan specified implementing least privilege policies and periodic access reviews.
Step 5: Create a Risk Treatment Plan
Once risks are identified and scored, determine how to handle them. Options include mitigating the risk (implement controls), accepting it (if below a defined threshold), transferring it (e.g., insurance) or avoiding it (changing processes). ISO 27001 requires that risk treatment decisions are linked to controls in Annex A. The plan should describe the chosen treatment, the responsible owner and target completion dates. Hightable emphasises that risk acceptance criteria and risk scoring support structured decisions.
Document the plan in a way that auditors can trace each risk to a control. For example, the previous IAM misconfiguration risk might map to control A.8.1 (Access control) and A.8.9 (Configuration management). The plan should note that implementing role‑based access and automated detection of privilege escalation will mitigate the risk. During readiness, track progress and evidence for each treatment action.
Step 6: Select and Apply Security Controls
Control selection is not about deploying every possible measure; it’s about choosing controls that mitigate identified risks while supporting business operations. Secureframe notes that ISO 27001:2022 reduced the number of controls to 93 grouped into organizational, people, physical and technological categories. The update added 11 new controls such as threat intelligence, cloud service security, business continuity readiness, configuration management and secure coding. DataGuard emphasises that the new standard introduces a focus on risk‑based thinking and new controls for emerging threats like cloud computing and social engineering.
Here’s how to select controls:
- Map risks to controls: For each risk in your register, map a corresponding control from Annex A. For example, a risk of data leakage might map to A.8.12 (Data leakage prevention).
- Balance people, process and technology: Organizational controls include policies, defined responsibilities and supplier management. People controls include training and background checks; physical controls address facility security; technological controls include encryption, logging and secure coding. Select a balanced set rather than over‑engineering a single area.
- Document exclusions: Where a control does not apply, explain why in your Statement of Applicability. For example, if you have no remote workers, you may exclude remote working controls.
- Avoid over‑engineering: Controls should be appropriate to the size and complexity of your organization. Excessive technical measures can slow agility and create friction. Focus on meeting the intent of the control with sustainable processes.
Common controls for enterprise‑facing companies include access control policies, multi‑factor authentication, encryption at rest and in transit, vulnerability management, logging and monitoring, secure software development life cycle practices, vendor risk management, incident response, and business continuity readiness.
Step 7: Write and Maintain Security Policies
Policies provide the framework for managing security. Thoropass enumerates more than twenty policies covering information security, data protection, data retention, access control, asset management, risk management, information classification and handling, security awareness, acceptable use, clear desk/clear screen, remote working, business continuity, backup, malware protection, change management, third‑party supplier security, continual improvement, logging and monitoring, network security, information transfer, secure development, physical and environmental security, cryptographic key management, encryption, and document and record management. Policies should specify roles, responsibilities and procedures, including risk management and incident response. They must be approved by leadership and communicated to employees.
Key points:
- Define scope and applicability: Policies should state to whom they apply and under what circumstances. Thoropass emphasises that accurate scope definition is necessary for implementing appropriate measures.
- Include objectives and commitments: ISO 27001 requires that the information security policy be appropriate to the organisation’s purpose and include commitments to satisfy applicable requirements and continually improve the ISMS.
- Review regularly: Policies must be reviewed at least annually or when major changes occur. Ensure that updates are documented and that new versions are communicated to staff.
Policies should be practical and readable. Complex language or unrealistic requirements reduce adoption. Use simple language, provide examples and avoid jargon. Make policies available on an intranet or knowledge base. Provide training to ensure staff understand them.
Step 8: Establish Documented Procedures
Procedures turn policies into actionable steps. While a policy might state that all incidents must be reported promptly, the incident response procedure specifies who is notified, how to collect evidence and how to communicate with stakeholders. Secureframe’s internal audit article lists documentation auditors expect: ISMS scope statements, Statements of Applicability, information security policies, risk assessments, risk treatment plans, management review minutes, corrective action reports and business continuity policies. Procedures should map to these documents and show how controls operate.
Areas where auditors expect clear procedures include:
- Access provisioning and deprovisioning: Steps to request, approve, grant and revoke access.
- Change management: Procedures for submitting change requests, assessing impact, obtaining approvals and testing before deployment.
- Incident response: Steps for detection, analysis, containment, eradication, recovery and post‑incident review. Naq Cyber’s guide details that incident response plans should define team roles, communication channels and detection methods.
- Business continuity activation: Steps for declaring a disaster, invoking the continuity plan and restoring critical services.
Ensure procedures reflect actual practice. Auditors cross‑check documentation against interviews and observations. Out‑of‑date or unused procedures are red flags. Involve process owners in drafting procedures and test them during tabletop exercises.
Example procedure outline for incident response:
- Preparation: Identify an incident response team, define roles, maintain contact lists and perform regular risk assessments.
- Detection and analysis: Document types of incidents (malware, denial of service, phishing, unauthorized access, insider threat, data breach, targeted attack) and specify detection methods.
- Containment and mitigation: Outline steps to prioritise tasks, isolate systems, block malicious activity, reset accounts and remove threats.
- Recovery and remediation: Return systems to normal operation, repair vulnerabilities and notify regulators if required.
- Post‑incident review: Conduct lessons‑learned sessions, update controls and improve training.
Step 9: Train Employees on Security Practices
Human behaviour remains a leading cause of breaches. DataGuard explains that cyber security awareness empowers employees to recognize threats, protect data and apply secure practices to support frameworks like ISO 27001 and NIS2. Awareness reduces human error, which is a major contributor to breaches. ISO 27001 requires evidence that employees and relevant stakeholders are aware of information security policies, procedures and their roles. Training supports risk mitigation, fosters a shared security mindset and demonstrates audit readiness.
Key practices:
- Onboarding training: Provide new hires with training on information security policies, acceptable use, password management, phishing awareness and incident reporting. Document completion and keep records.
- Role‑specific training: Developers should understand secure coding practices; finance teams should understand data handling; customer support should recognise social engineering.
- Annual refreshers: Offer periodic training modules or interactive sessions to reinforce awareness. Include updates on new threats, policy changes and lessons learned from incidents.
- Phishing simulations and drills: Conduct periodic phishing tests and tabletop exercises. BARR Advisory notes that 16% of breaches in IBM’s study involved attackers using AI and that phishing accounted for more than a third of AI‑powered attacks. Regular training helps staff identify suspicious messages.
- Evidence of participation: Track attendance and comprehension through sign‑in sheets or learning management systems. Auditors often request training records during Stage 1.
Example onboarding checklist:
- Read and acknowledge the information security policy, acceptable use policy and privacy statement.
- Configure multi‑factor authentication on all corporate accounts.
- Complete phishing awareness training and pass a short quiz.
- Review incident reporting procedure and know how to contact the security team.
- Sign any required confidentiality and data handling agreements.
Step 10: Test Incident Response and Continuity Plans
Testing shows whether your plans work. Naq Cyber distinguishes business continuity plans (BCPs) and incident response plans (IRPs). BCPs cover a wide range of disruptions—natural disasters, supply chain issues and cyber‑attacks—while IRPs focus specifically on cyber incidents like data breaches and malware. Evidence of robust BCPs and IRPs is necessary for compliance with ISO 27001 and other frameworks. IRPs help organisations detect, respond to and recover from incidents, minimising damage and providing structured recovery. They require defined roles, communication channels and continuous improvement.
Testing should include:
- Tabletop exercises: Simulate realistic scenarios such as ransomware or data loss. Evaluate how quickly the incident response team identifies the incident, communicates and executes containment and recovery. Record lessons learned.
- Business continuity drills: Shut down a non‑production system to simulate an outage. Assess how quickly services are restored and whether communications are effective.
- Evidence collection: Maintain records of exercises, attendees, findings and action plans. Auditors look for evidence that plans have been tested.
- Continuous improvement: Incorporate lessons learned into the next iteration of the plans. Naq emphasises that post‑incident reviews identify improvements and ensure that incident response remains current.
Step 11: Run Internal Audits
Internal audits determine whether your ISMS satisfies ISO 27001 requirements and whether controls operate effectively. ISO 27001 clause 9.2 requires internal audits at planned intervals. Secureframe advises conducting internal audits at least annually. Internal audits must be documented, performed by independent and impartial auditors and reported to management.
The internal audit process includes:
- Defining the scope and plan: Identify which clauses and controls will be audited and select an impartial internal auditor.
- Evidence collection and document review: Auditors review policies, statements of applicability, risk assessments, risk treatment plans, management reviews, corrective action reports and business continuity policies.
- Conducting the audit: Interview control owners, observe operations and verify that controls operate as documented.
- Reporting findings and corrective actions: Produce a report summarising the audit scope, objectives, findings, recommendations and corrective actions.
- Management review: Present findings to management for decision making and continuous improvement.
Internal audit findings feed directly into readiness. Addressing non‑conformities early reduces the likelihood of major findings during the certification audit. Auditors will look for evidence that internal audits and management reviews have been conducted and that corrective actions are tracked.
Step 12: Check Compliance Requirements and Gaps
Readiness includes mapping your controls to ISO 27001 clauses and Annex A controls. Use checklists, automated gap analyses and readiness platforms to identify missing or weak areas. DataGuard’s ISO 27001:2022 guide explains that organizations certified under ISO 27001:2013 have until October 31 2025 to transition. The new standard emphasises risk‑based thinking, the importance of people and culture and includes new controls addressing cloud computing and social engineering. Ensure that your readiness program accounts for these changes.
Align your readiness checks with enterprise security questionnaires. Many questionnaires reference multiple frameworks such as SOC 2, HIPAA and GDPR. Cross‑map your controls to these frameworks to reuse evidence. For example, encryption controls, access reviews and incident response are common across SOC 2 and ISO 27001. Use readiness tools that maintain evidence libraries and track observation periods. Konfirmity’s managed service automatically maps controls across frameworks and monitors evidence on an ongoing basis, reducing the internal workload.
Step 13: Prepare for the Audit Readiness Review
Audit readiness reviews often involve an independent consultant or a certification body performing a pre‑assessment. This review checks whether the ISMS meets documentation requirements and whether controls operate effectively. Bridewell explains that the certification audit consists of two stages: a Stage 1 documentation review and a Stage 2 on‑site evaluation where auditors verify processes, interview staff and examine evidence.
To prepare:
- Organise evidence: Compile policies, SoA, risk registers, risk treatment plans, internal audit reports, training records, test results and management review minutes. Keep them in a central repository with version control.
- Conduct a gap review: Perform an internal pre‑assessment (or engage a consultant) to identify any outstanding issues. Fix gaps in documentation or control operation before the Stage 1 audit.
- Educate staff: Brief employees on the purpose of the audit and their roles. Ensure they can explain processes and show where evidence is stored.
- Address last‑minute issues: Common problems include incomplete training records, outdated policies, missing asset inventories or untested incident response plans. Fix these before the audit.
Real‑World Readiness Example
A mid‑size SaaS company selling to healthcare providers sought to win enterprise deals. Initially it lacked documented policies, had no formal risk assessment and used ad hoc access controls. Konfirmity conducted a gap assessment and found missing asset inventories, incomplete vendor risk management and no incident response plan. Over five months, Konfirmity’s team worked alongside the company’s engineers to implement the steps outlined above:
- Leadership commitment: The CTO and head of operations acted as executive sponsors and allocated budget for a compliance platform and training.
- Scoping: The scope covered the production platform, supporting cloud services, code repositories and employee devices, excluding marketing tools.
- Asset inventory: Automated discovery integrated with AWS, GCP and GitHub to generate a dynamic asset list and classification.
- Risk assessment and treatment: The team identified twenty‑seven risks, scored them and developed treatment plans. Controls included least‑privilege access, data encryption, vulnerability management with a 30‑day remediation SLA and continuous monitoring.
- Policy development: Konfirmity provided templates for 25 policies, including an incident response policy, business continuity policy and access control policy. The executive team approved them.
- Procedures and training: Procedures for change management and incident response were documented. All staff completed onboarding security training and role‑specific courses.
- Incident response testing: Tabletop exercises simulated a ransomware attack. The team discovered an unclear escalation path and corrected it. BCP drills ensured the platform could fail over to a secondary region within four hours.
- Internal audit: An impartial internal auditor reviewed policies, evidence and controls and identified minor non‑conformities. Corrective actions were implemented.
- Audit readiness review: After five months, the company invited a certification body to perform Stage 1. The auditor noted no major non‑conformities. Stage 2 followed three weeks later and resulted in successful certification.
The readiness program reduced sales cycle times: enterprise prospects accepted the company’s security documentation without additional due diligence. The company estimated that it spent 80 hours of internal time rather than the 500 hours previously expected for a self‑managed program. It also reduced security questionnaire response times from two weeks to two days.
Common ISO 27001 Readiness Mistakes
- Treating readiness as a paperwork exercise: Without operational controls, policies alone fail during Stage 2 audits. Evidence must show that controls operate and are monitored.
- Ignoring staff involvement: Lack of training leads to human errors. DataGuard highlights that awareness training is a core requirement and auditors expect proof of employee education.
- Rushing control setup: Selecting controls without mapping them to risks often results in unnecessary complexity. Choose relevant controls and document exclusions.
- Underestimating effort and timelines: Implementation typically takes 2–6 months and the entire certification spans 3–12 months. Rushing leads to gaps that delay audits.
- Neglecting vendor risk management: Vendor breaches are costly. Include third‑party risk assessments and ensure vendors meet your security standards.
How ISO 27001 Readiness Helps Enterprise Sales
Security readiness shortens sales cycles. With a documented ISMS, vendors can answer security questionnaires quickly, reducing procurement delays. Evidence of incident response testing, vendor risk management and employee training instills buyer confidence. With average breach costs exceeding $4 million and vendor breaches costing nearly $5 million, enterprises prefer suppliers who can show they are audit‑ready. Readiness also means fewer follow‑up questions; buyers accept the certification as evidence of maturity. Firms that integrate readiness into their product development pipelines win deals faster, maintain trust and differentiate from competitors that rely on self‑attestation.

Conclusion
ISO 27001 readiness is a business decision as much as a security one. Certification is not about a badge; it requires building an operational program that protects data and supports business continuity. The global cost of breaches and the scrutiny from enterprise buyers mean that readiness is essential. By following structured steps—securing executive commitment, defining scope, managing assets, assessing risks, treating them, selecting appropriate controls, developing policies, establishing procedures, training employees, testing plans, running internal audits, closing gaps and preparing for external audits—companies can reduce stress and avoid last‑minute surprises. Building security into daily operations builds trust with customers and auditors alike. Programs that read well on paper but fail under incident pressure expose organisations to financial, legal and reputational damage. Start with security and arrive at compliance.
Frequently Asked Questions
1) What does ISO 27001 readiness mean?
Readiness refers to having a functioning ISMS and evidence to support it. It differs from certification in that certification involves an accredited third‑party audit. A compliant management system may follow ISO 27001 internally, but readiness means you can pass the Stage 1 documentation review and Stage 2 operational evaluation. URM Consulting notes that self‑declaration lacks the rigor and business benefits of accredited certification.
2) How long does ISO 27001 readiness take?
Timelines vary. Scrut’s timeline guidance states that implementation typically takes 2–6 months, internal audits 2–4 weeks and external audits 4–6 weeks. The entire certification process spans 3–12 months depending on organizational size and existing controls. Managed services like Konfirmity often reduce internal effort and compress the timeline.
3) Which teams should be involved in readiness efforts?
Leadership (CTO, CISO, executives) must sponsor the program and allocate resources. Control owners across IT, engineering, DevOps, product, human resources, customer support and legal should participate. Risk program owners include IT compliance managers and internal audit teams. Business unit leaders provide input on processes and data flows. Employee participation through training and awareness programs is vital.
4) What documentation is required before certification?
Auditors expect an ISMS scope statement, a Statement of Applicability, information security policies, risk assessments, risk treatment plans, management review minutes, corrective action reports, business continuity policies and records of internal audits. Evidence of training, asset inventories and incident response tests are also required. Policies should be reviewed at least annually and procedures must align with actual practices.
5) How is readiness assessed before an audit?
Organisations conduct gap assessments to compare current practices against ISO 27001 requirements. Internal audits evaluate whether the ISMS meets organizational and ISO 27001 requirements and identify non‑conformities. External consultants may perform readiness reviews to highlight gaps. During the pre‑audit, reviewers check documentation, evidence of control operation, results of internal audits and management reviews. Addressing findings before inviting the certification body increases the likelihood of a clean Stage 1 and Stage 2 audit.





.svg)






.svg)
.svg)