Most enterprise buyers will not sign a contract based only on a certificate. They expect proof that you protect data, can withstand an attack, and continually improve. The ISO 27001 Red Team Vs. Blue Team In ISO 27001 approach answers that need. ISO 27001 lays out how to build an Information Security Management System (ISMS), but auditors and procurement teams want evidence that your controls work in practice. Red and blue team tests simulate attackers and defenders, uncover weak points, and feed lessons back into the ISMS. Konfirmity has supported more than 6,000 audits over 25 years; the patterns discussed here come from that experience.
Why do enterprise clients care?
Big customers send long questionnaires, request SOC 2 or ISO 27001 reports, and ask how often you test your controls. A certificate proves you went through an audit, but it doesn’t show how your team would react to a phishing attack or a rogue insider. The StrongDM overview of ISO 27001 requirements highlights that organisations must set the scope, get leadership buy‑in, define objectives, allocate resources, run risk assessments, monitor performance, and record non‑conformities. These processes create structure, yet real resilience comes from testing. When you combine ISO 27001 compliance with regular red/blue tests, you demonstrate to clients that you validate controls, detect incidents quickly, and integrate findings into your program. This combination shortens sales cycles and satisfies due‑diligence requests.
CTA: Book a demo
Understanding red and blue teams
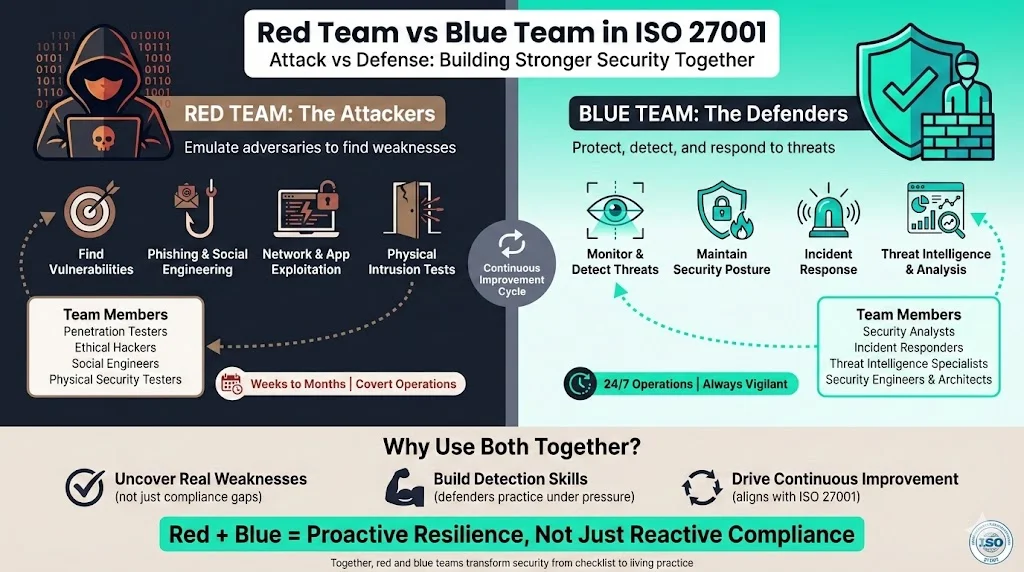
Red team
A red team emulates an adversary. The National Institute of Standards and Technology (NIST) defines it as a “group of people authorized and organized to emulate a potential adversary’s attack or exploitation capabilities against an enterprise’s security posture”. Their goal is to think like attackers, find weak points, and demonstrate impact. A red team uses technical attacks (network and application exploitation), social engineering (phishing, vishing, pretexting), and sometimes physical intrusion. Members range from penetration testers and ethical hackers to social engineers and physical security specialists. They often operate over several weeks, remain covert, and aim for specific objectives such as gaining access to sensitive data or escalating privileges. This wider scope differentiates them from a typical penetration test, which usually lists vulnerabilities in a narrow window.
Blue team
The blue team defends the organisation. NIST describes it as the group responsible for keeping an enterprise secure against mock attackers. Blue teamers monitor logs, network traffic, and endpoints, hunt for threats, respond to incidents, and maintain a secure posture. A typical blue team includes analysts who look for anomalies, incident responders who contain and eradicate threats, threat intelligence specialists who track new techniques, engineers who maintain detection tools, and architects who design the overall defence. They enforce least privilege, perform vulnerability management, run configuration audits, and conduct root‑cause analysis after incidents. In short, they keep the day‑to‑day operations of the ISMS running.
Why use both
Using only compliance checklists can give a false sense of security. Red team tests reveal misconfigurations, unpatched systems, and social engineering gaps that audits might miss. Blue team participation ensures that defenders can detect and respond to those attacks. Together, the two teams build muscle memory and expose blind spots. This cycle of attack and defence fits well with ISO 27001’s focus on continuous improvement. By regularly running such tests, you gather evidence that controls work under stress, which supports risk assessments and management reviews. The ISO 27001 Red Team Vs. Blue Team In ISO 27001 strategy helps you move from a reactive stance to proactive resilience.
How red/blue teaming matches ISO 27001
ISO 27001:2022 provides a framework for managing sensitive information. Important elements include defining the ISMS scope, obtaining leadership commitment, setting security objectives, allocating resources, conducting risk assessments, planning operations, evaluating performance, and addressing non‑conformities. Annex A lists 93 controls covering people, organisational, technology, and physical domains; companies must document which controls they apply. Regular internal audits and management reviews ensure that controls remain effective.
Gaps that compliance may leave open
Compliance audits focus on whether controls exist, not on how they perform under attack. Vulnerability scans and code reviews may not detect chained exploits, lateral movement, or social engineering. A red team may find unused administrator accounts, shared credentials, or misconfigured network segments that passed initial checks. IBM’s 2025 breach report illustrates the cost of such oversights: while the global average breach cost fell to USD 4.44 million thanks to faster detection, the average U.S. breach cost rose to USD 10.22 million, and 97% of incidents involving unauthorised artificial intelligence tools lacked proper access controls. These numbers show that even organisations with documented controls can suffer costly breaches if they do not test them.
Validating ISO 27001 controls through red team tests
Red teaming helps answer practical questions: Does multi‑factor authentication stop credential stuffing? Does network segmentation prevent lateral movement? Do staff report phishing emails? Attack simulations test the technical, physical, and human controls listed in Annex A. Findings feed into the risk treatment plan and non‑conformity log, strengthening the ISMS. Because the blue team must detect and respond, the test also validates incident response procedures and logging configurations required by ISO 27001 clauses on monitoring and improvement.
Blue team’s role in continuous improvement
The blue team turns test outcomes into lasting change. They update configurations, tune detection rules, patch vulnerabilities, improve training, and document evidence. Their ongoing monitoring supports internal audits and management reviews. Matching red/blue findings with ISO 27001 risk assessments ensures that the ISMS evolves as threats change. The ISO 27001 Red Team Vs. Blue Team In ISO 27001 approach regards compliance as a living process rather than a point‑in‑time test.
Running a red vs. blue test under ISO 27001
Effective tests follow a clear structure. The timeline below illustrates the main phases: planning, attack, defence, review, and improvement.

1) Planning
- Scope: Use your risk assessment to select systems, data, and processes to test. High‑value assets such as payment systems, customer databases, and cloud infrastructure should be priority. Match the scope with the boundaries defined in your ISMS scope document.
- Objectives: Decide what you want to learn. Goals might include testing incident response, measuring detection speed, or assessing social engineering susceptibility. Clear objectives guide the red team’s tactics and the blue team’s metrics.
- Rules of engagement: Agree on permissible techniques, forbidden actions (e.g., no data destruction), communication channels, and escalation paths. Involve legal, HR, and IT to prevent unexpected disruptions.
2) Attack (red team)
The red team launches phishing campaigns, scans networks, exploits vulnerabilities, and attempts lateral movement. They might craft custom malware, set up command‑and‑control channels, or even attempt physical entry. To maintain realism, they limit who knows the test is underway, but they respect the rules of engagement to avoid harming operations.
3) Defence (blue team)
Blue teamers monitor logs, network traffic, and endpoints, looking for anomalies. When they detect suspicious activity, they isolate affected systems, revoke compromised credentials, and block malicious domains. They then perform root‑cause analysis to trace how the red team gained access and why controls failed. This phase tests incident response runbooks, communication protocols, and leadership involvement.
4) Review and improvement
After the test, red and blue teams meet to discuss what happened. They catalogue successful exploits, missed detections, and effective defences. They produce a report that maps findings to ISO 27001 controls and other frameworks such as HIPAA and GDPR. For example, a phishing success might indicate a training gap, while a privilege escalation might reveal inadequate password management. Recommendations become actions in the risk treatment plan. The organisation then updates its policies, tunes detection rules, and schedules follow‑up audits. This continuous loop embodies the ISO 27001 Red Team Vs. Blue Team In ISO 27001 mindset.
Templates for structured tests
Konfirmity’s managed service includes templates that simplify planning and follow‑up. Rather than recreating each one here, this section summarises their purpose:
- Test plan: Outlines the scope, objectives, rules of engagement, time frame, stakeholders, and success criteria. It ensures that everyone agrees on what will be tested and how.
- Risk and control matrix: Lists assets, threats, vulnerabilities, existing controls, control gaps, and priorities. It links test findings to specific controls and risk levels.
- Findings report: Captures each vulnerability or exploit path, the control that failed, the detection gap, recommended remediation, responsible owner, and deadline. It provides a clear hand‑off from the red and blue teams to management.
- Action tracker: Tracks remediation tasks, owners, due dates, status, and verification notes. It helps the organisation stay accountable and ensures that fixes are verified.
- Monitoring checklist: Defines what to monitor (access reviews, vulnerability scans, log correlation, incident response tests), how often to do it, what metrics to collect, and when to raise issues. This checklist supports continuous evidence gathering for audits and procurement reviews.
Using these templates ensures that tests are repeatable, match ISO 27001 controls, and produce actionable outcomes.
Challenges and best practices
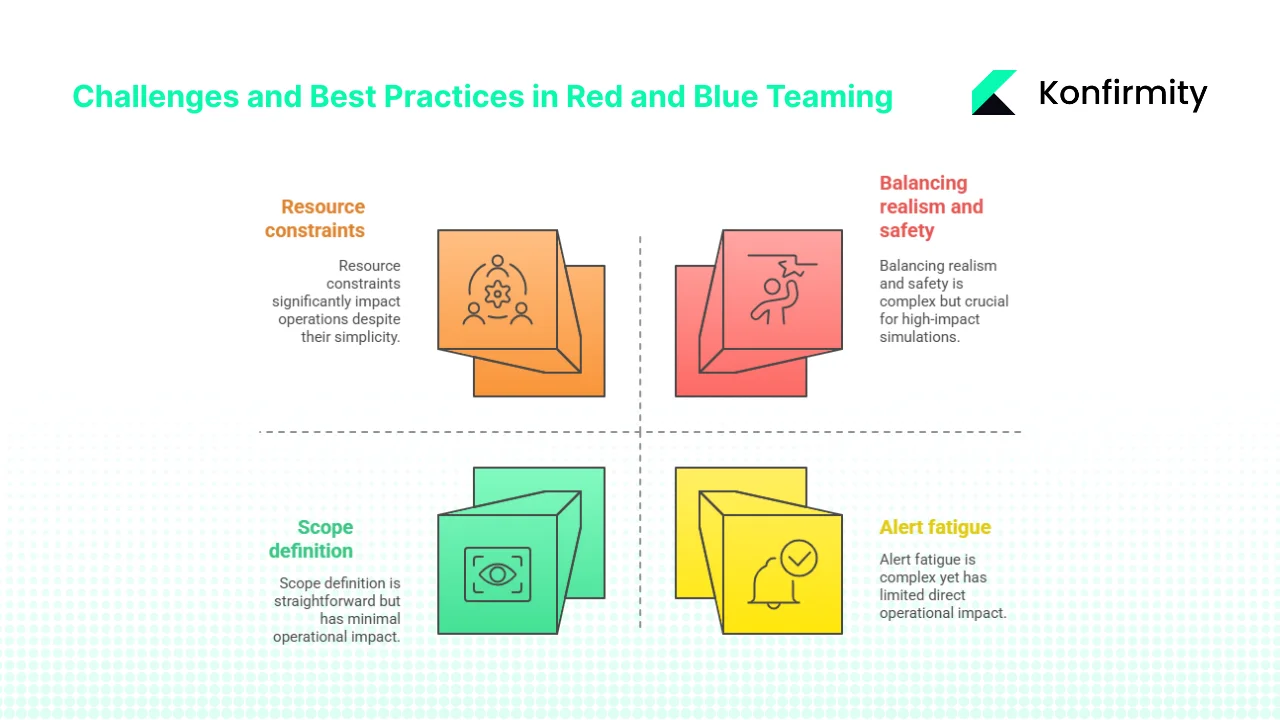
- Resource constraints: Red and blue teaming requires specialised skills and time. Many organisations are unable to spare staff to run multi‑week tests. Managed services can provide experienced testers and defenders without overburdening your team. For smaller companies, start with a limited scope focusing on your most critical assets.
- Scope definition: Without clear boundaries, tests can become unmanageable. Define systems in scope, specify objectives, and set rules of engagement at the outset. Keep the initial test targeted; expand later as you build maturity.
- Alert fatigue: Blue teams may see a flood of alerts during a test. Tuning detection thresholds, automating triage, and scheduling the test at quieter times help avoid burnout. Afterward, review the alert quality and adjust rules.
- Balancing realism and safety: Attack simulations should be realistic but not disruptive. Prohibit destructive actions, use synthetic data where possible, and require the red team to pause if operations are at risk. Store any collected data securely and follow privacy obligations.
- Documentation: Tests generate reports, evidence, and remediation plans. Organise these materials and link them to ISO 27001 clauses and other frameworks. Bear in mind that only AICPA‑accredited CPAs can issue SOC 2 reports and that SOC 2 Type 2 audits typically cover a 3–12‑month observation window. Plan your testing cadence so that evidence remains current for audits and sales questionnaires.
Adopting the ISO 27001 Red Team Vs. Blue Team In ISO 27001 mindset across these practices ensures that offensive tests and defensive monitoring support your ISMS. It ties real‑world attack simulation to governance, risk, and compliance processes.
Why this matters to enterprise sellers
Enterprise clients need confidence. They want to see that you protect their data, comply with standards, and test your defences. Combining ISO 27001 certification with red/blue tests offers tangible benefits:
- Better due‑diligence responses: Security questionnaires often ask about certifications and testing. Sharing test results alongside ISO 27001 and SOC 2 reports shows that you validate controls and fix issues.
- Shorter sales cycles: When buyers see that you test your systems, detect incidents quickly, and track remediation, they are more likely to trust you. This trust reduces the back‑and‑forth with security teams and speeds up contract approval.
- Fewer audit findings: Konfirmity’s clients that run regular red/blue tests have fewer control failures and shorter audit timelines. Our managed service typically achieves SOC 2 readiness in four to five months, compared with nine to twelve months for self‑managed efforts. Clients spend about 75 hours per year collecting evidence with our service versus more than 550 hours when doing it alone. These numbers match industry estimates that Type 2 audits can take up to 15 months if the observation window is a full year.
CTA: Book a demo
- Cross‑framework readiness: Enterprise buyers often require compliance with HIPAA, GDPR, and other regulations. The HIPAA Security Rule mandates administrative, physical, and technical safeguards such as risk analysis, workforce training, and access control. The GDPR’s data minimisation principle requires personal data to be limited to what is necessary. Red/blue tests help verify these safeguards in practice, demonstrating that controls protect electronic protected health information and personal data.
- Differentiation: Many compliance tools promise quick certification but leave internal teams to design and operate controls. Konfirmity’s human‑led managed service implements controls in your environment, monitors them year‑round, runs red/blue tests, and supports audits. This end‑to‑end approach delivers outcomes, not just software. The ISO 27001 Red Team Vs. Blue Team In ISO 27001 methodology underpins our service model.
Conclusion
ISO 27001 provides a solid framework for information security management, but real security comes from testing and improving controls. Red team tests simulate adversaries, while blue teams defend, analyse, and strengthen the environment. Together they reveal gaps that static audits miss and feed evidence back into the ISMS. For companies selling to enterprise clients, integrating red/blue tests with ISO 27001 compliance proves resilience, reduces sales friction, and prepares you for other frameworks like SOC 2, HIPAA, and GDPR. View security as an ongoing practice, run structured tests regularly, and let compliance follow. The ISO 27001 Red Team Vs. Blue Team In ISO 27001 approach delivers security that stands up to auditors, buyers, and attackers alike.
FAQ
1) What is the difference between the red team and the blue team?
The red team emulates attackers, using technical exploits, social engineering, and sometimes physical access to find weaknesses. The blue team defends by monitoring, detecting, and responding to attacks, then hardening controls. NIST defines the red team as a group authorised to emulate adversaries and the blue team as those responsible for defence.
2) What is the difference between red team and blue team certifications?
Offensive certifications (e.g., Offensive Security Certified Professional) focus on penetration testing, exploit development, and adversary tactics. Defensive certifications (e.g., GIAC Certified Incident Handler) focus on monitoring, detection, response, and threat hunting. Some broad certifications, such as CISSP, cover both but still require hands-on practice.
3) Who earns more, the blue team or the red team?
Salaries vary by region, experience, and role. Offensive roles sometimes command higher pay in consulting or bug bounty contexts due to scarcity, but experienced defensive leaders also earn high compensation. The most important factor is depth of expertise and ability to deliver results.
4) What is a red team audit?
A red team audit is a structured assessment where authorised attackers attempt to breach an organisation’s defences without prior notice to defenders. It goes past a routine penetration test by using scenario‑based attacks, social engineering, and physical intrusion. The goal is to evaluate the effectiveness of controls and incident response. Findings map to risk assessments and drive improvement. A red team audit fits within broader governance, including ISO 27001, SOC 2, HIPAA, and GDPR frameworks.
The ISO 27001 Red Team Vs. Blue Team In ISO 27001 methodology brings together offensive and defensive disciplines under a single governance model, making it easier for organisations to meet varied regulatory and customer expectations.





.svg)






.svg)
.svg)