Most enterprise buyers now ask for security assurance artifacts early in procurement. Without a functioning security program and continuous evidence, deals stall—even when teams think they’re ready on paper. The ISO 27001 Renewal Guide is written for practitioners who need to keep their certification current while operating at the pace of modern software delivery. ISO/IEC 27001 is the world’s best‑known standard for information security management systems (ISMS). It shows buyers and regulators that you manage risks to the confidentiality, integrity and availability of data. Initial certification requires months of planning and two external audits, but renewal is just as critical: certificates last three years and depend on annual surveillance audits. Letting certification lapse jeopardizes customer trust and may lead to contract losses. This guide describes why ongoing renewal matters, when to plan it and how to execute the process efficiently, drawing on Konfirmity’s experience supporting over 6,000 audits and 25+ years of combined expertise.
Why ISO 27001 Renewal Matters
ISO 27001 shows clients and regulators that you operate a risk‑driven information security management system. Enterprise buyers require ongoing evidence, and renewal prevents trust erosion. Recent data puts the average cost of a breach at USD 4.44 million, rising to USD 10.22 million in the United States, so the stakes are clear. Staying certified helps satisfy regulatory obligations, reduces due diligence friction and positions your firm as a dependable partner.
Certificates last three years; two surveillance audits occur in the interim years. If you ignore findings, the certifier may suspend your certificate. A recertification audit is required at the end of the term; schedule it three to six months before expiry to allow time for remediation.
This ISO 27001 Renewal Guide lays out the renewal cycle, tasks, templates and common pitfalls, drawing on Konfirmity’s expertise. It shows how human‑led managed compliance reduces internal effort and keeps you audit‑ready year round.
Regular renewal also signals seriousness to third‑party risk assessors and board members. Many enterprise buyers now include security questionnaire scoring thresholds that rely on valid certifications; losing the certificate due to negligence can stall or cancel deals. For example, research by AuditBoard notes that surveillance audits look at whether previous non‑conformities were remediated and will give only three months for evidence of correction. A pattern of missed corrective actions can lead to suspension, which is costly to reverse and may cause reputational damage.
In addition to buyer scrutiny, regulators and insurers increasingly tie premiums and enforcement decisions to demonstrate continuous improvement. The ISO 27001 framework enshrines the Plan–Do–Check–Act cycle; renewal offers a structured point to review risk appetite, update control design and record evidence of improvement. By integrating renewal planning into your product roadmap and change management, you avoid last‑minute scrambles and create a narrative of security maturity that is appreciated by auditors.
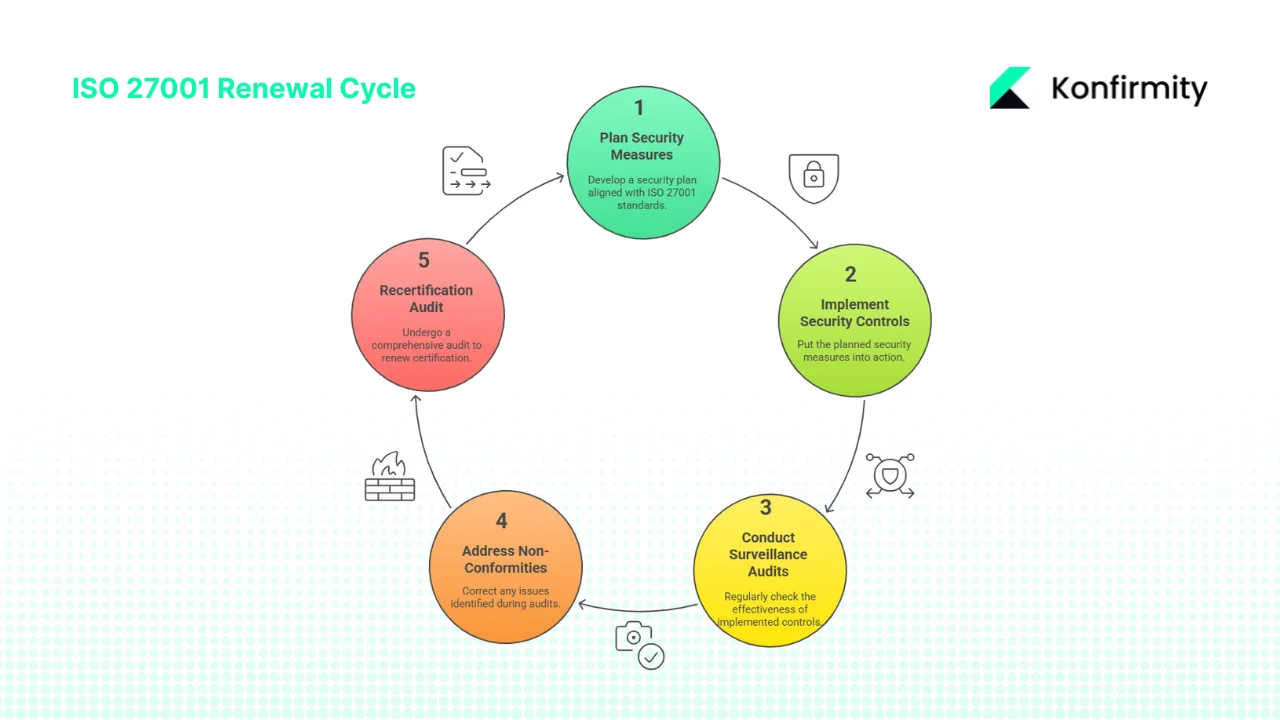
Renewal Cycle and Deadlines
The three‑year certification period
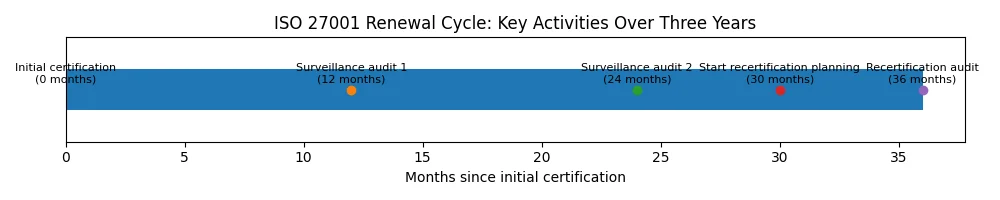
ISO 27001 certificates specify a scope statement, issue date and expiration date. The certificate remains valid for three years, provided that you pass the annual surveillance audits and address any findings. The surveillance audit schedule typically looks like this:
- Surveillance Audit 1 (Year 1): Occurs roughly 12 months after initial certification. Auditors sample controls, review documentation, check management review records and confirm that your improvement cycle is operating. Minor non‑conformities must be corrected before the next surveillance.
- Surveillance Audit 2 (Year 2): Conducted around month 24. This audit also focuses on continuous improvement, ensuring that previous findings have been resolved and that new risks are being managed.
- Recertification Planning (Months 30–33): It’s prudent to start preparing for renewal three to six months before expiry. This gives you time to address gaps without losing your current certificate. If your organization has undergone major changes—new products, acquisitions, infrastructure migrations or leadership changes—a Stage 1‑style readiness review may be appropriate to adjust the ISMS scope.
- Recertification Audit (Month 36): A full external audit verifies that the ISMS remains effective, mature and aligned with the current version of ISO 27001. The recertification process is similar to the original Stage 2 audit; it assesses policies, risk management, control operation and continual improvement. Passing the recertification audit resets the three‑year cycle.
The timeline below illustrates these milestones:
Core Steps in the ISO 27001 Renewal Process
Renewal isn’t just a single event; it’s the culmination of continuous work. Konfirmity’s ISO 27001 Renewal Guide breaks the process into seven steps that mirror the expectations of auditors and enterprise clients.
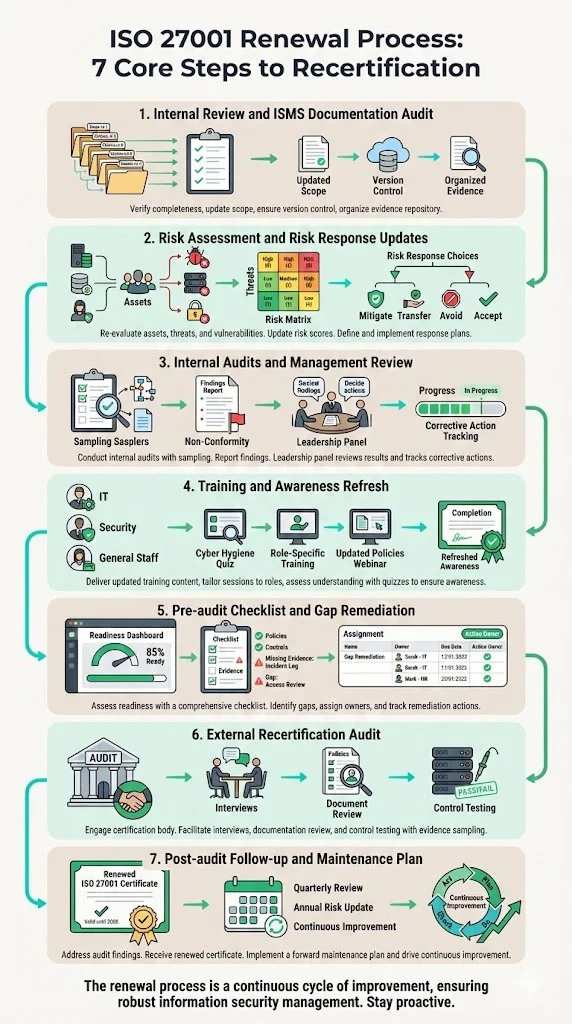
1. Internal review and ISMS documentation audit
Begin by inventorying all ISMS documents: policies, procedures, risk assessments, the Statement of Applicability (SoA), risk treatment plans, asset inventories, incident logs, training records and evidence of control operation. Auditors examine documentation first, and disorganization here leads to delays. Check that your scope statement accurately reflects current operations; changes to services, cloud environments, locations or legal entities require scope updates. A well‑maintained document repository with version control prevents duplication and ensures that staff are working from current documents. Konfirmity uses managed wikis and template libraries so clients spend less time on versioning and more on actual control operation.
2. Risk assessment and risk response updates
ISO 27001 requires periodic risk assessments. Establish the context by understanding your internal and external environment, defining the ISMS scope and setting risk criteria. Identify assets, threats and vulnerabilities—malware, ransomware, misconfigured cloud services, weak passwords or insider threats—and evaluate their likelihood and potential business impact. Use a risk scoring method to prioritize response actions. Update your risk response plan accordingly. Response options include reducing risks through controls, avoiding risky activities, transferring the risk (e.g., via cyber insurance) or accepting it if within tolerance. Document all decisions and assign owners, deadlines and evidence. Konfirmity’s risk workshops map risks to Annex A controls and cross‑framework requirements (SOC 2, HIPAA, GDPR), ensuring efficiency across audits.
3. Internal audits and management review
Internal audits are not optional. They verify that policies are followed and controls function effectively. Schedule internal audits at least annually, and rotate auditors to maintain objectivity. Auditors should sample evidence—access reviews, change‑management tickets, backup logs, incident handling records—and compare them against policies. After the audit, management must review results and decide on corrective actions and resource allocation. The AuditBoard guide notes that organizations get three months to provide proof of corrective action after surveillance audits. Handle internal audits with the same seriousness. Konfirmity’s managed service supplies experienced auditors who run tabletop exercises, produce findings and track remediation to closure.
4. Training and awareness refresh
Employees are often the weakest link. Provide annual security training tailored to roles: secure coding for developers, access control for operations teams, and phishing awareness for all staff. Track attendance, quiz scores and refresh cycles as evidence for auditors. Update training content when you deploy new tools or change policies. Risk assessments may identify new threats (e.g., generative artificial intelligence misuse) requiring additional awareness sessions. Maintaining training records demonstrates management commitment and supports continuous improvement.
5. Pre‑audit checklist and gap remediation
Build a renewal readiness checklist. Include document inventory, updated SoA, risk assessments, evidence of controls, logs of backups and incidents, internal audit reports, management review minutes, corrective action logs and training records. Verify that all non‑conformities from previous audits have been resolved. If evidence is missing—such as backup logs or change‑management approvals—rectify the gap by implementing automated logging and retention. Assign owners for each corrective action with due dates and track progress. Konfirmity provides pre‑audit readiness dashboards with status indicators, so teams see exactly where to focus.
6. External recertification audit
Engage an accredited certification body early. Supply them with updated documentation, scope statements, SoA and evidence. Expect a document review followed by operational verification. Auditors will interview personnel, inspect processes and sample controls. They will examine logs, risk assessments, incident handling records, vendor risk management, access reviews and change‑management procedures. The process is similar to the original Stage 2 audit. Address any findings promptly; major non‑conformities may require a follow‑up audit before certification is renewed. Konfirmity’s experts accompany clients during the audit, answer auditor questions and produce additional evidence on demand, reducing time‑to‑close.
7. Post‑audit follow‑up and maintenance plan
Once you pass the recertification audit, your certificate is reissued and the three‑year clock resets. Document lessons learned—what went well, where evidence was weak and which processes required last‑minute fixes. Update your maintenance plan: schedule internal audits, surveillance audits, risk assessments and training sessions for the new cycle. Maintain an audit calendar with reminders for important dates. Build continuous improvement into daily operations, so that renewal becomes a predictable event rather than a frantic project. This is how Konfirmity’s clients spend about 75 hours per year on compliance tasks versus 550–600 hours when self‑managed, and achieve SOC 2 readiness in 4–5 months instead of 9–12 months.
Common Challenges and How to Address Them
This ISO 27001 Renewal Guide explains remedies for typical problems. Even well‑resourced teams encounter obstacles during renewal. The most common issues and remedies are simple but require discipline:
- Documentation sprawl or outdated records: assign an owner, use version control and keep a central repository of current policies and procedures.
- Scope creep or business changes: update the scope statement whenever you launch new products, migrate to new infrastructure or acquire another company.
- Missing evidence of controls: automate log collection for backups, access reviews and incident response; retain evidence for the period defined in your policy.
- Unaddressed non‑conformities: log all findings, assign owners and due dates, and verify closure during internal audits.
- Resource constraints: distribute compliance tasks across teams, integrate training with regular meetings and use templates or managed services to minimize manual work.
Practical Templates and Tools
This guide offers reusable templates to streamline preparation:
- Renewal readiness checklist: a master list of policies, SoA updates, risk assessment tracker, internal audit schedule, evidence and corrective action status.
- Internal audit checklist: a list of controls to test with fields for evidence and findings.
- Management review template: an overview of audit results, risk changes, corrective actions and next audit dates.
- Risk assessment and response plan: an inventory of assets, threats, likelihood, impact and chosen risk response.
- Corrective action log: a table of findings with owners, due dates and proof of closure.
- Training log: a register of sessions, attendees, topics and refresh dates.
Automation platforms that collect evidence and map it to control requirements can further reduce effort by capturing logs and screenshots directly from your systems.
Step‑by‑Step Quick Reference
For busy practitioners, the following checklist summarizes the ISO 27001 Renewal Guide process:
- Plan the renewal cycle: mark surveillance and recertification dates in a compliance calendar; begin planning six months before expiry.
- Gather documentation: compile policies, procedures, SoA, risk assessments and evidence. Verify that scope statements reflect current operations.
- Update risk assessments: review context, identify new assets and threats, score risks and update the risk response plan.
- Conduct internal audits: test controls, collect evidence and log findings. Hold management reviews to decide on corrective actions and assign resources.
- Refresh training: provide role‑based security training and record attendance. Update content to address new threats.
- Build the pre‑audit package: complete the renewal readiness checklist, update logs and ensure non‑conformities are resolved.
- Host the external audit: work with an accredited certification body. Provide documentation, answer questions and supply additional evidence.
- Close out findings: address any non‑conformities promptly. Submit proof of remediation to the auditor.
- Reset the cycle: after certification is renewed, update the audit calendar, plan continuous compliance activities and feed lessons learned into the next cycle.
Best Practices for Continuous Compliance
Sustained compliance requires more than just passing audits; it demands operational security excellence.

Maintain a live ISMS calendar. Use tools that remind you of upcoming audits, risk assessments, training sessions and policy reviews. Automate reminders to important stakeholders so deadlines aren’t missed.
Version control documentation. Store policies, procedures and evidence in a version‑controlled repository. Label drafts and published versions clearly to prevent confusion. Archive outdated documents but keep them accessible for historical audits.
Trigger ISMS updates through change management. Ensure that product launches, infrastructure changes, vendor onboarding and organizational restructures trigger a scope review and risk assessment. Integrate compliance checkpoints into development and release workflows. When engineers deploy a new microservice processing customer data, the risk register and SoA should be updated automatically.
Promote security awareness. Conduct regular phishing simulations, share incident post‑mortems and celebrate positive security behaviors. Make security a shared responsibility across engineering, product and operations. Provide clear channels for reporting incidents and reward early detection.
Handle internal audits and management reviews as critical. Don’t view them as paper exercises. Internal audits catch issues early, while management reviews ensure leadership prioritizes resources for remediation. Document meeting minutes and decisions to demonstrate management commitment to auditors.
Working with a partner like Konfirmity ensures that experienced professionals, not just software alone guide your program. This human‑led approach provides assurance throughout the year.
Conclusion
Renewal isn’t a bureaucratic hoop—it’s an opportunity to reassess and strengthen your security posture. With breaches costing millions of dollars and regulators demanding evidence of continuous control operation, a well‑run renewal process becomes a competitive advantage. Companies selling to enterprise clients need to show ongoing commitment to information security, not just an initial certificate. Following the practices in this ISO 27001 Renewal Guide, supported by Konfirmity’s human‑led managed service, helps you maintain continuous compliance, build buyer confidence and free your teams to focus on delivering value. Security that looks good in documents but fails under incident pressure is a liability. Build the program once, operate it every day and let certification follow. This ISO 27001 Renewal Guide reinforces that message.
FAQ
1. How often do you need to renew ISO 27001?
ISO 27001 certificates remain valid for three years. Surveillance audits occur in years one and two, and a full recertification is required at the end of year three. Schedule the audit a few months before expiry to avoid losing your certificate.
2. How do you renew ISO 27001 certification?
Update your documentation, risk assessments and controls. Perform internal audits and management reviews, fix any gaps, then hire an accredited certification body for the recertification audit. Provide evidence such as logs, training records and updated scope statements. Address findings promptly.
3. How do you maintain ISO 27001 certification?
Maintain continuous compliance through annual internal audits, risk reviews, management meetings, training and evidence collection. Pass surveillance audits by showing auditors that controls operate effectively and resolve any non‑conformities quickly.
4. What is the ISO 27001 recertification audit?
It’s a full audit at the end of the three‑year cycle that resembles the original Stage 2 audit. Auditors review your ISMS, talk to staff, examine logs and evaluate improvements. Passing the audit renews your certificate for another three years.





.svg)






.svg)
.svg)