Most enterprise procurement teams now ask hard questions about how vendors protect data and prove it. Failure to answer can stall or kill deals. Breaches cost organisations an average of $4.44 million in 2025 and reach $10.22 million in the United States. Regulators have been equally unforgiving: the Irish Data Protection Commission hit Meta with a €1.2 billion fine in 2023, pushing cumulative GDPR penalties above €5.88 billion by January 2025. Within healthcare, the Office for Civil Rights closed 22 penalty cases in 2024 and early 2025. These numbers explain why enterprise buyers, particularly in regulated sectors, demand evidence that access control is more than a policy document. This guide, written by Konfirmity founder Amit Gupta, explores ISO 27001 Role‑Based Access Control For ISO 27001, why it matters for large contracts, and how to implement it.
Why enterprise buyers care deeply about access control
Enterprise procurement questionnaires and data‑protection agreements are no longer polite inquiries; they are gatekeepers for revenue. Buyers expect vendors to show that only authorised individuals can reach sensitive systems and that access is reviewed regularly. Several factors amplify this demand:
- Huge breach costs – Data breaches remain costly. DeepStrike’s 2025 statistics put the global average at $4.44 million, with ransomware present in 44 % of incidents and healthcare breaches costing $7.42 million. Varonis notes that breaches taking longer than 200 days to contain cost $5.01 million.
- Regulatory enforcement – The General Data Protection Regulation (GDPR) continues to set records; Meta’s €1.2 billion fine shows that inadequate data controls carry enormous financial risk. In the United States, the Office for Civil Rights’ 22 enforcement cases in 2024 underscore that small practices are not immune.
- Supply‑chain scrutiny – Third‑party attacks doubled in 2025, and healthcare partners are often the weakest link. Buyers expect vendors to show that partners follow strong access control processes.
- Audit readiness as a sales accelerator – Deals now hinge on being “audit‑ready.” Konfirmity’s experience across 6,000+ audits shows that vendors who demonstrate evidence of role ownership, periodic access reviews, and least‑privilege practices cut procurement cycle time by months. Without this, questions about segregation of duties, joiner/mover/leaver processes and privileged‑account management cause delays.
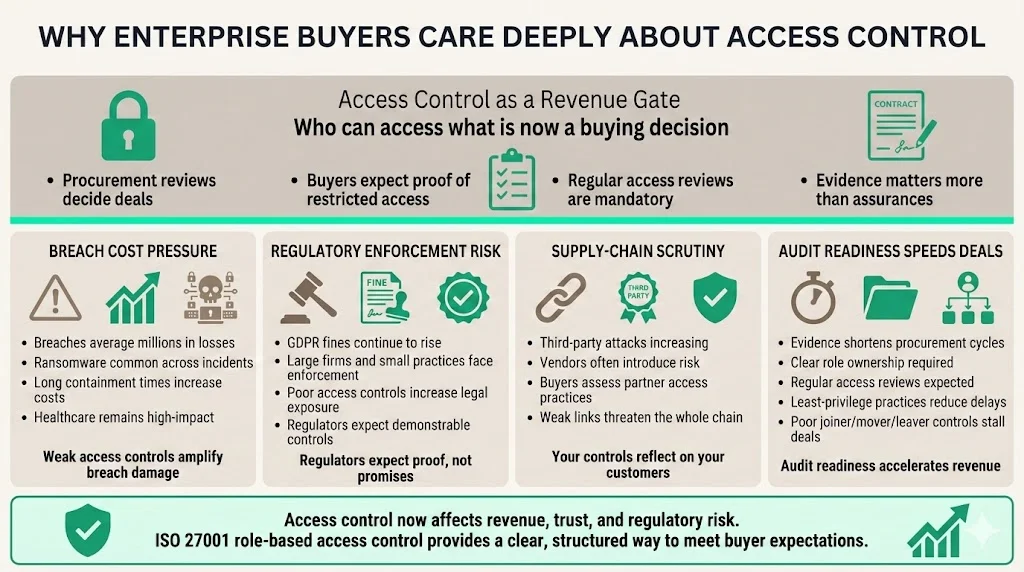
For technical leaders, these drivers translate into a simple reality: access control is no longer optional. It is a business‑enabling control that affects revenue, reputation and regulatory exposure. ISO 27001 Role‑Based Access Control For ISO 27001 provides a framework to meet these expectations with precision.
How ISO 27001 Role‑Based Access Control supports trust, audits and large contracts
ISO 27001 is the internationally recognised standard for establishing an Information Security Management System (ISMS). It requires organisations to identify risks, implement controls and continuously improve. Annex A of ISO 27001:2022 lists 93 controls organised into four categories: 37 organisational, eight people, 14 physical and 34 technological. Access control is one of these organisational controls and is further elaborated in Annex A.9 and A 5.15 of the 2022 update.
Enterprise buyers care about ISO 27001 because it pairs risk‑based thinking with operational evidence. When vendors implement ISO 27001 Role‑Based Access Control For ISO 27001, they can show that:
- Only authorised users can access sensitive systems – Annex A.9 requires policies that restrict network and system access to approved individuals and ensure that users cannot change security settings.
- Access aligns with job duties – Role‑based models map permissions to real job functions and enforce least‑privilege rules.
- Evidence exists for auditors – Annex A.9 emphasises user registration, provisioning, review and removal. Logs must capture access attempts, user actions and exceptions for audit and incident response.
- Controls span people and technology – ISO 27001 divides controls into organisational, people, physical and technological categories. Access control touches all four: policies and approval workflows (organisational), training and user responsibilities (people), badge access and secure rooms (physical), and authentication systems (technological).
Konfirmity’s clients often choose ISO 27001 certification because it shortens sales cycles. Large enterprises trust the rigour of ISO 27001 and see role‑based access control as evidence that vendors can enforce segregation of duties, manage privileged accounts and sustain controls across observation windows. When combined with other frameworks such as SOC 2 and HIPAA, ISO 27001’s structured approach to access control allows cross‑mapping. Common controls such as encryption at rest and access reviews satisfy multiple frameworks, reducing duplication.
What you will gain from this guide
This guide demystifies ISO 27001 Role‑Based Access Control For ISO 27001. Readers will get:
- A plain‑language explanation of ISO 27001 and the purpose of access control within the standard.
- Practical steps to design, implement and operate a role‑based access control program that aligns with ISO 27001, SOC 2, HIPAA and GDPR.
- Ready‑to‑use templates covering policies, role definitions, user‑access reviews and permission matrices.
- Insights from Konfirmity’s 6,000+ audits and 25+ years of combined expertise—patterns that go wrong and best practices that accelerate deals and audits.
Before diving into implementation, it’s important to understand the foundations of ISO 27001 access control.
ISO 27001 and access control in plain terms
ISO 27001 exists to help organisations manage information risks. It requires companies to define the scope of their ISMS, identify assets, assess risks and implement controls. Access control sits at the core of this system. The standard’s purpose is to ensure confidentiality, integrity and availability of information. Without the right people, processes and technologies controlling access, these aims fail.
Annex A 5.15 of ISO 27001:2022 states that organisations must implement access controls based on business and security requirements. This includes classifying information, mapping access rights to entities (humans, devices and services), and applying the principle of least privilege. Access controls must be consistent with information classification and reviewed regularly.
Access control is not just a technology problem; it is part of a broader security program. Policies define who approves access, who owns roles and how to handle exceptions. Training ensures users understand their responsibilities. Physical controls restrict entry to server rooms or offices. Technological controls enforce authentication and authorisation. Together, these form a defence against insider threats, compromised credentials and vendor risks.
Where role‑based access control fits in
Many organisations start with ad‑hoc permission assignments. Over time, they discover the chaos this creates: employees accumulate privileges across projects and positions, leading to “privilege creep.” Role‑based access control (RBAC) offers a structured alternative. RBAC groups permissions into roles linked to job functions. Users inherit permissions by being assigned to roles rather than receiving individual grants.
NIST defines RBAC as a model where access rights are based on roles and tasks. The principle of least privilege—granting only the minimal rights necessary—is integral to RBAC. Compared to discretionary models where resource owners decide permissions, RBAC centralises decisions and scales better for enterprises. Mandatory access control (MAC) suits government settings with strict classification, but it is inflexible for businesses. RBAC strikes a balance between security and usability; 94.7 % of companies use it.
RBAC supports confidentiality, integrity and availability. By mapping access to job duties, it enforces segregation of duties, reducing fraud and error. RBAC also makes offboarding safer; when a user leaves, removing them from roles revokes all associated permissions. For system availability, RBAC prevents unqualified changes to critical services. In regulated environments, role‑based controls align with risk management and reduce the likelihood of violations.
Common risks that RBAC mitigates include privilege drift, orphaned accounts, unreviewed access and insider abuse. Strong governance frameworks combine RBAC with joiner, mover and leaver processes, multi‑factor authentication and periodic reviews.
ISO 27001 Annex A.9 – Access control explained
Annex A.9 of ISO 27001:2013 (corresponding to Annex A 5.15 in the 2022 revision) lays out the specifics of access control. The goal is to ensure that access to information and systems is authorised, approved and appropriate. The relationship with risk management is clear: uncontrolled access increases the likelihood and impact of incidents, so controls must align with identified risks.
Annex A.9 covers four areas:
- Business requirements for access control – Organisations must define an access control policy (A.9.1.1) and enforce network controls (A.9.1.2). These policies set the tone for role definitions, approval workflows and network segmentation.
- User access management – This includes registration and provisioning, management of privileged rights, management of secret authentication information (passwords and cryptographic material), review of user access rights and timely removal of access. Without formal provisioning and deprovisioning processes, roles become bloated and orphaned accounts remain active.
- User responsibilities – Users must safeguard their authentication information and follow policies. Training and awareness reduce the risk of credential compromise.
- System and application access control – This emphasises secure log‑on procedures, password management and session controls. Multi‑factor authentication (MFA) is encouraged. Logging and monitoring of access events support forensic investigations.
Together, these requirements ensure that access is granted intentionally, documented and monitored. They also establish a clear link between risk assessment and control implementation.
What auditors look for
Auditors reviewing access controls focus on evidence rather than promises. Based on our experiences and guidance from audit firms:
- Clear policies – Documentation must exist for access control policies, joiner/mover/leaver procedures and role definitions. Auditors want to see that these policies are approved and updated.
- Proof of role ownership – Each role should have an owner responsible for defining permissions and approving assignments. Auditors check that the role owner approves access requests.
- Evidence of regular reviews – Organisations should conduct periodic access reviews (quarterly or more often) to verify that users still need their assigned roles and permissions. These reviews must be documented and show outcomes, such as removal of unnecessary access.
- Logs tied to monitoring – Access decisions and changes should be logged and tied to a monitoring system. Linford & Co. emphasise that documentation, authorization and timeliness are critical; missing approvals or incomplete offboarding are common reasons for audit findings.
Auditors also look at onboarding, access changes and offboarding. They check whether approvals are captured for each event, whether access is revoked promptly, and whether reviews include all systems. Failing to include SaaS tools or third‑party platforms is a frequent mistake.
Role‑based access control fundamentals
What RBAC means in practice
In an RBAC system, there are three core elements: users, roles and permissions. Users represent people, service accounts or machines that need access. Roles describe a set of permissions aligned with job functions. Permissions define actions on resources—such as read, write or administer—within systems. A well‑designed RBAC model ensures that users cannot perform functions outside their roles and that roles only contain necessary permissions.
RBAC definitions vary slightly by source, but a common model uses five static elements: users, roles, permissions, operations and objects. Permissions are applied to operations on objects (e.g., “modify invoice” or “read customer data”). This structure encourages consistent access decisions and helps automate enforcement.
RBAC vs other access models
Discretionary Access Control (DAC) allows resource owners to decide who can access their resources. This flexibility can lead to inconsistent security and is suitable mainly for small teams. Mandatory Access Control (MAC) uses strict classifications (e.g., “Top Secret”) and is often mandated in government contexts. Attribute‑Based Access Control (ABAC) grants access based on attributes such as user type, location or time. ABAC can be extremely granular but complex to manage.
RBAC stands out because it balances structure and scalability. It uses the idea of hierarchies—senior roles inherit permissions from junior ones—and separation of duties. Constrained RBAC introduces static or dynamic separation of duties to prevent conflicts of interest. Symmetric RBAC enables administrators to review permissions both by user and by role, facilitating audits. This layered approach makes RBAC flexible enough for complex enterprises while preserving least‑privilege principles.
Security roles and user permissions
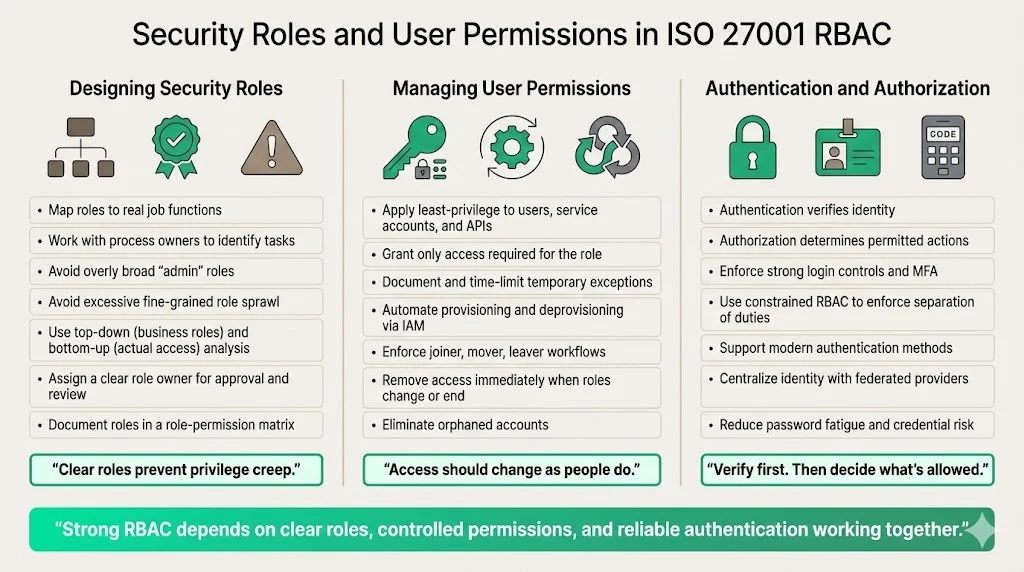
Designing security roles
Designing roles begins with mapping them to real job functions. Engage process owners to identify tasks and required system interactions. Avoid creating overly broad roles—“Admin” with sweeping privileges—because they become magnets for privilege creep. Conversely, avoid “role explosion,” where too many fine‑grained roles create confusion. StrongDM’s analysis calls this “role sprawl” and notes that roles often persist long after a project ends. To prevent this, adopt a top‑down approach (define roles based on business functions) and a bottom‑up approach (analyse actual permissions used).
Assigning role owners is critical. Each role should have a manager responsible for defining and approving membership. This ensures accountability and allows periodic review. Document roles in a matrix listing systems covered, permission sets and approval owners.
Managing user permissions
The principle of least privilege, a cornerstone of NIST 800‑53, dictates that individuals should have only the rights required for their roles. Apply this principle across users, service accounts and APIs. When exceptions occur—such as temporary access for troubleshooting—document them, set expiration dates and remove them promptly. Automate provisioning and deprovisioning through identity‑and‑access management (IAM) tools to reduce human error.
Joiner/mover/leaver workflows are essential to maintain RBAC integrity. When a new person joins, provisioning should create accounts and assign roles based on their job. As individuals move within the organisation, update their roles and remove old privileges to prevent access creep. When employees or contractors leave, disable accounts across all systems immediately. Orphaned accounts are a common vector for attacks and audit findings.
Authentication and authorization
RBAC operates after authentication. Authentication verifies identity—often through usernames, passwords and multi‑factor tokens. ISO 27001 Annex A.9 encourages secure log‑on procedures, strong passwords and multi‑factor authentication. Once the identity is verified, RBAC determines authorisation: which roles the user has and what actions they can perform. Constrained RBAC models enforce separation of duties by preventing users from holding conflicting roles in the same session.
Common authentication methods include hardware tokens, biometrics, one‑time passwords and authenticator apps. In many organisations, federated identity providers (such as SAML or OAuth providers) centralise authentication and pass user attributes to the RBAC system. Using modern authentication helps reduce password fatigue and reduces the risk of credential compromise.
RBAC as a security control
RBAC and security governance
RBAC supports governance by making role ownership explicit. Each role is tied to a business process and has an owner accountable for its definition and membership. This accountability enables internal reviews and reduces ambiguity about who can grant or revoke access.
RBAC also supports internal review cycles. Because roles group permissions, reviewing a role’s membership is easier than reviewing individual user permissions. Access reviewers can focus on whether users still need the roles assigned to them rather than inspecting dozens of system‑level rights.
RBAC and compliance requirements
ISO 27001 Role‑Based Access Control For ISO 27001 is central to certification. Evidence of role definitions, least‑privilege assignments and periodic reviews helps satisfy Annex A.9 and shows auditors that controls operate over time. SOC 2 Type 2 audits have observation windows of three to twelve months. Having RBAC with automated logging supports continuous evidence. For HIPAA and GDPR, RBAC helps limit access to protected health information and personal data. For example, GDPR Article 32 requires appropriate technical and organisational measures for data processing. Mapping RBAC controls across frameworks via a common control framework allows reuse of evidence.
Monitoring and audit readiness
Logging and monitoring are vital to prove that RBAC is working. Systems should capture successful and failed log‑ons, role assignments, privileged operations and changes to roles. Logs must be tied to monitoring tools that analyse patterns and alert on anomalies. During audits, these logs demonstrate that access decisions were enforced and reviewed.
Access reviews should be periodic and risk‑based. High‑risk roles (such as those with production or financial system access) warrant monthly or quarterly reviews, while lower‑risk roles may be reviewed annually. Document review outcomes and track remediation actions. When auditors find issues—such as missing approvals or delayed removal of access—document root causes and improvements. Continuous monitoring reduces surprises and ensures that evidence is fresh when auditors arrive.
Step‑by‑step walkthrough to implement ISO 27001 RBAC
Implementing ISO 27001 Role‑Based Access Control For ISO 27001 requires structured steps. The process below reflects Konfirmity’s practices and typical audit expectations.
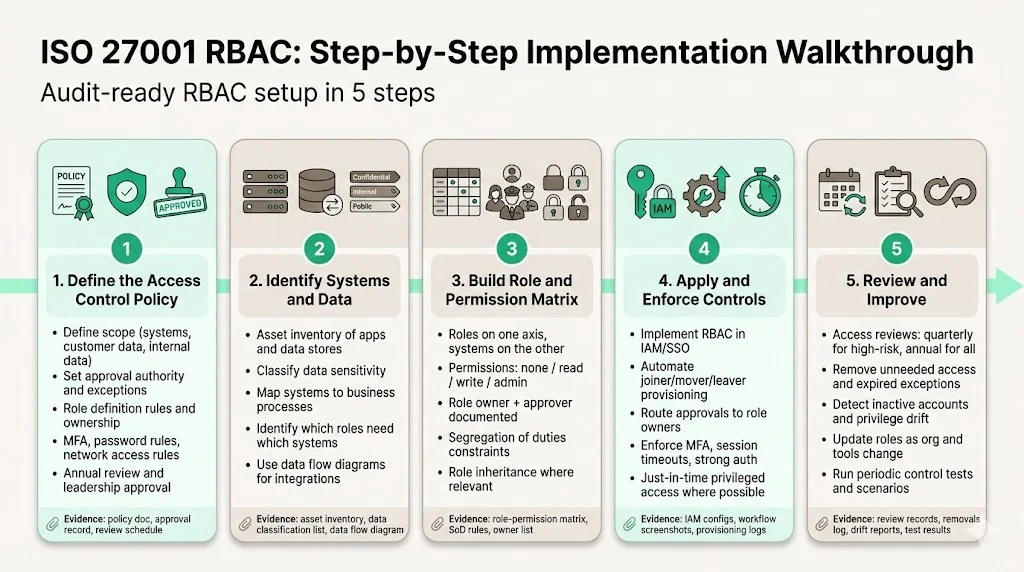
Step 1: Define the access control policy
Begin by writing an access control policy that outlines intent and scope. Identify what information is covered (e.g., customer data, internal systems) and align it with business goals and risk appetite. Specify who approves access, how roles are defined, and how exceptions are handled. Include network access controls, password requirements and MFA. Ensure the policy is reviewed and approved by leadership and updated annually.
Step 2: Identify systems and data
Create an asset inventory and classify data by sensitivity. Link applications and data stores to business processes. Identify which roles need access to each system. For example, finance systems may require roles such as “Accounts Payable Clerk” (read/write invoices) and “Accounts Payable Approver” (approve payments). Use data flow diagrams to understand how information moves across systems and which integrations exist.
Step 3: Build a role and permission matrix
Develop a matrix listing roles down one axis and systems across the other. For each intersection, specify the permission level (none, read, write, administer). Document who owns the role and who approves assignments. At this stage, consider hierarchical roles: junior roles inherit from senior ones. Include segregation of duties constraints, such as preventing one person from both submitting and approving expenses. This matrix becomes the foundation for provisioning and review.
Step 4: Apply and enforce controls
Implement RBAC in your identity and access management system. Use automation to provision accounts and assign roles based on HR events (joiner, mover, leaver). Configure approval flows so that requests route to role owners. Enforce MFA, strong passwords and session timeouts on critical systems. Where possible, use just‑in‑time privileged access so that elevated rights expire automatically.
Step 5: Review and improve
Schedule periodic access reviews—quarterly for high‑risk roles and at least annually for all roles. During the review, role owners should confirm that members still need their access and remove privileges that are no longer required. Use tooling to detect inactive accounts, privilege drift and expired exceptions. Update roles as the company grows, splits departments or adopts new systems. Regularly test your controls by simulating access change scenarios to ensure processes work as intended.
Templates for ISO 27001 role‑based access control
Templates streamline adoption of ISO 27001 Role‑Based Access Control For ISO 27001 and provide auditors with consistent evidence. Below are outlines for four useful templates.
1. Access control policy template
2. Role definition template
3. User access review template
4. RBAC matrix template
Common mistakes enterprise buyers flag
Despite best intentions, some access control implementations fall short. Buyers and auditors frequently flag the following issues:
- Overly broad roles – Roles with wide privileges become de facto administrator accounts. This contradicts least‑privilege principles and raises the impact of credential compromise.
- Missing access reviews – Without scheduled reviews, privilege creep goes unnoticed and orphaned accounts persist. Audit evidence becomes stale.
- Weak audit trails – Failing to log access events or preserve logs for the required retention period makes it impossible to prove controls were effective.
- Manual processes that do not scale – Spreadsheets and emails can work for small teams but break down as organisations grow. Without automation, approvals are inconsistent and evidence is scattered.
Avoiding these pitfalls requires commitment to process design, automation and continuous improvement.
Conclusion
ISO 27001 Role‑Based Access Control For ISO 27001 is not a checkbox exercise. It is a discipline that underpins trust, protects sensitive data and accelerates enterprise deals. The combination of clear policies, defined roles, automated provisioning and rigorous reviews provides evidence that controls are working. In a world where data breaches cost millions and regulators impose billion‑euro fines, strong access control is a business imperative. Human‑led, managed security and compliance programs—like those delivered by Konfirmity—ensure that controls are implemented inside your stack, monitored continuously and ready for auditors. Security that looks good on paper but fails in practice is a liability. Build the program once, operate it daily and let compliance follow.
FAQs
1 ) What is the role of ‑based access control in ISO 27001?
Role‑based access control refers to assigning permissions based on defined roles tied to job functions. ISO 27001’s access control requirements emphasise that access should be granted on a need‑to‑know basis, approved by role owners and reviewed regularly. RBAC supports structured access decisions by aligning permissions with roles rather than individuals.
2 ) What are the four types of controls in ISO 27001?
ISO 27001:2022 organises its 93 controls into four categories: 37 organisational controls (e.g., policies and procedures), eight people controls (training and awareness), 14 physical controls (facility access) and 34 technological controls (technical measures such as encryption).
3 ) What is an access control policy in ISO 27001?
An access control policy defines how an organisation restricts access to information and systems. Under ISO 27001 Annex A.9, the policy must cover network controls, user provisioning and deprovisioning, management of privileged rights, password standards, MFA requirements, and periodic reviews.
4 ) What are the four models of RBAC?
According to ANSI/INCITS 359‑2004, the RBAC standard defines four models. Flat (core) RBAC is the basic model with users, roles and permissions. Hierarchical RBAC adds role hierarchies so that senior roles inherit permissions. Constrained RBAC introduces separation of duties to prevent conflicting roles. Symmetric RBAC allows administrators to review permissions by user and by role, facilitating audits.





.svg)






.svg)
.svg)