In the current enterprise environment, passing an audit is no longer about showing a policy document that says you monitor your systems. It is about proving that you actually do it, every single day.
Enterprise buyers, particularly in 2025 and 2026, have become sophisticated. They understand that a "paper program" offers zero protection against supply chain attacks or ransomware. With the global average cost of a data breach reaching $4.88 million, the stakes are financial, not just regulatory. Consequently, the depth of evidence required for ISO 27001 certification has intensified. Auditors now demand granular proof of continuous monitoring, incident detection, and log integrity.
This is where Security Information and Event Management (SIEM) ceases to be just a technical tool and becomes the backbone of your Information Security Management System (ISMS).
A SIEM solution aggregates log data from across your infrastructure—servers, firewalls, applications, and identity providers—and correlates that data to spot anomalies. But raw data is not enough. You need specific SIEM Use Cases For ISO 27001 to translate that noise into actionable compliance signals. These use cases are the predefined rules, alerts, and workflows that prove to an auditor you are in control of your environment.
This article details the technical and operational strategies required to deploy SIEM effectively. We will examine the specific ISO 27001 controls that SIEM satisfies, provide technical templates for high-priority use cases, and explain how to position this infrastructure to close enterprise deals faster.
Why SIEM Matters for ISO 27001 Compliance
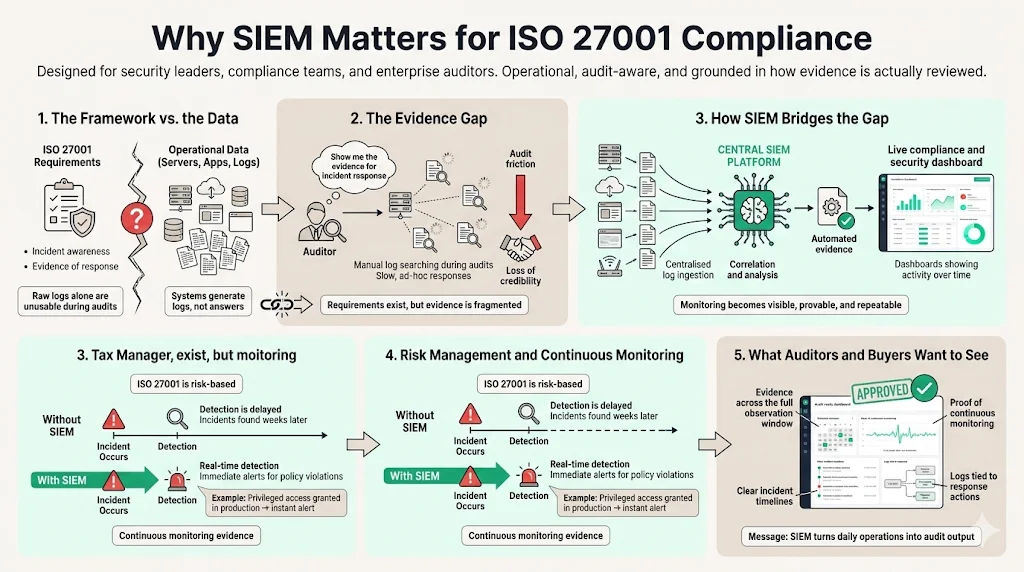
There is often a significant disconnect between the requirements of a framework and the raw data generated by a tech stack. ISO 27001 requires you to know when an incident occurs and to have a trail of evidence showing how you handled it. Your servers and applications generate this evidence in the form of logs, but without a system to ingest and analyze them, that evidence is invisible.
The Evidence Gap
In our work supporting over 6,000 audits, we frequently see organizations fail not because they lacked security tools, but because they lacked centralized visibility. An auditor might ask, "Show me all privileged access attempts from last Tuesday." If your team has to manually SSH into five different servers to grep through text files, you have already lost credibility. The audit becomes a friction point rather than a validation of your maturity.
SIEM bridges this gap. It turns the abstract requirement of "monitoring" into concrete artifacts. When you implement structured SIEM Use Cases For ISO 27001, you automate the collection of evidence. Instead of scrambling during the audit observation window, you point to a dashboard that has been tracking compliance status in real-time throughout the year.
Risk Management and Continuous Monitoring
ISO 27001 is fundamentally a risk management standard. It asks you to identify threats and implement controls to mitigate them. Without SIEM, your ability to detect threats is passive and delayed. You might discover a breach weeks after it happens—a dangerous lag given that the average time to identify and contain a breach is now 258 days.
With active SIEM use cases, you move to continuous monitoring. You detect policy violations—such as a developer granting themselves admin rights in production—the moment they happen. This capability is essential for meeting the stringent requirements of modern enterprise procurement teams, who often require proof of "continuous monitoring" in their security addenda.
At Konfirmity, we emphasize that compliance is a byproduct of good security. If you build a durable monitoring apparatus using SIEM, the audit becomes a natural output of your daily operations, rather than a frantic event.
How SIEM Maps to ISO 27001 Controls
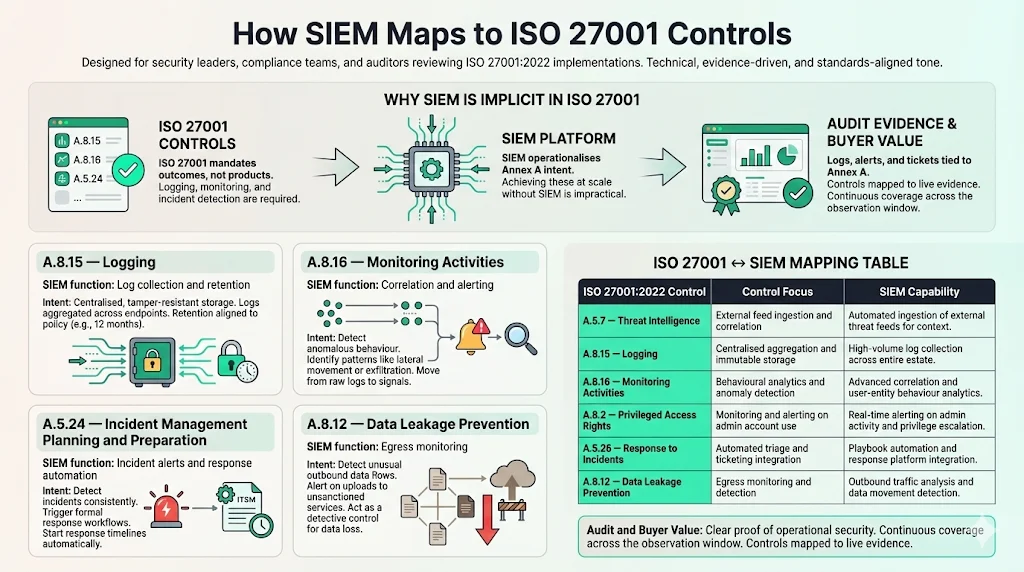
To maximize the value of your SIEM investment, you must map its capabilities directly to the Annex A controls of ISO 27001:2022. While the standard does not explicitly mandate "Buy a SIEM," it mandates outcomes that are nearly impossible to achieve at scale without one.
Here is how the core functions of SIEM support specific control intents:
A.8.15 Logging
This is the most direct mapping. Control A.8.15 requires that logs recording user activities, exceptions, faults, and information security events are produced, kept, and regularly reviewed.
- SIEM Function: Log Collection & Retention.
- Intent: The SIEM acts as the "Write Once, Read Many" (WORM) repository, ensuring that logs are aggregated from all endpoints and stored securely for the retention period defined in your policy (typically 12 months for ISO 27001 and SOC 2).
A.8.16 Monitoring Activities
This control requires networks, systems, and applications to be monitored for anomalous behavior.
- SIEM Function: Correlation and Alerting.
- Intent: SIEM applies logic to the raw logs to identify patterns, such as lateral movement or data exfiltration, satisfying the requirement to detect unexpected behavior.
A.5.24 Information Security Incident Management Planning and Preparation
You must have procedures to detect and report incidents.
- SIEM Function: Incident Alerts & Response Automation.
- Intent: SIEM triggers the incident response workflow. It converts a raw log (e.g., "Malware detected on Host A") into a ticket in your ITSM tool (e.g., Jira or ServiceNow), starting the formal clock on response times.
A.8.12 Data Leakage Prevention
This control focuses on detecting and preventing the unauthorized extraction of data.
- SIEM Function: Egress Monitoring.
- Intent: SIEM Use Cases For ISO 27001 can be configured to alert on spikes in outbound traffic or uploads to unsanctioned cloud storage, serving as a detective control for data leakage.
Control Mapping Table
Top SIEM Use Cases For ISO 27001
This section details the specific use cases you should implement. For each, we define the problem, the specific SIEM capability, and a template for the logic. These templates are designed to be platform-agnostic, applicable whether you use Splunk, Datadog, Sumo Logic, or Microsoft Sentinel.
1) Real-Time Threat Detection
The Problem: Attackers rarely use a single exploit. They probe, escalate privileges, and move laterally. ISO 27001 requires you to assess and treat these risks continuously. Relying on manual log review to catch a brute-force attack is impossible given the volume of data, especially since stolen credentials are involved in over 30% of breaches.
The SIEM Capability: Correlation. The SIEM looks for a sequence of events across time and distinct systems.
ISO 27001 Tie-In: Supports A.8.16 (Monitoring Activities) and A.5.7 (Threat Intelligence).
Template: Brute Force followed by Successful Login
- Objective: Detect an attacker who guesses a password after multiple failures.
- Log Sources: Identity Provider (Okta, Azure AD), Linux /var/log/auth.log, Windows Event ID 4625 (Fail) & 4624 (Success).
- Logic:
- Group events by User_ID and Source_IP.
- Count Action=Login_Failure > 5 within 10 minutes.
- Followed immediately by Action=Login_Success for the same User_ID.
- Severity: Critical.
- Action: Trigger P1 incident; lock user account temporarily via SOAR automation.
2) Log Aggregation and Centralized Log Analysis
The Problem: During an audit, an auditor will ask to see logs from a specific date six months ago. If those logs were stored locally on a server that has since been terminated (common in auto-scaling cloud environments), you have a non-conformity.
The SIEM Capability: Retention and Indexing.
ISO 27001 Tie-In: Supports A.8.15 (Logging) and ensures the integrity of information.
Template: Standard Ingestion and Normalization Policy
- Objective: Ensure all in-scope systems are sending logs and they are parsed correctly.
- Log Sources: All.
- Logic:
- Heartbeat Check: Alert if Log_Volume from Source_Type=Firewall or Source_Type=Production_DB drops to 0 for > 60 minutes.
- Field Extraction: Ensure critical fields (Timestamp, User, Source_IP, Action, Resource) are normalized to a common schema (e.g., CIM or OCSF).
- Action: Alert DevOps team to check the logging agent (e.g., Fluentd or Filebeat).
3) Compliance Monitoring & Reporting
The Problem: Audits are expensive in terms of human capital. Manually compiling access reviews or incident lists consumes hundreds of hours.
The SIEM Capability: Reporting and Dashboards.
ISO 27001 Tie-In: Supports Clause 9.1 (Monitoring, measurement, analysis and evaluation).
Template: Compliance Report Schedule
- Objective: Automate the evidence gathering for monthly or quarterly reviews.
- Report 1: Access Review. List all active users, their roles, and last login date. Highlight users inactive > 90 days.
- Report 2: Incident Summary. List all alerts triggered in the last 30 days, their resolution status, and time-to-resolve.
- Report 3: Change Management. List all changes to production security groups or firewall rules.
- Format: Generate PDF/CSV automatically on the 1st of every month and email to the CISO and Compliance Officer.
4) Threat Intelligence Integration
The Problem: You might see traffic going to an IP address, but without context, you do not know it is a known Command & Control (C2) server.
The SIEM Capability: Enrichment.
ISO 27001 Tie-In: Supports A.5.7 (Threat Intelligence).
Template: Feed Management and Prioritization
- Objective: Detect communication with malicious entities.
- Data Sources: Firewall logs, DNS logs, Threat Intel Feed (e.g., CrowdStrike, AlienVault OTX).
- Logic:
- Compare Destination_IP or DNS_Query in outbound traffic logs against the Indicator_List in the Threat Intel feed.
- Filter for Confidence > High.
- Action: Block IP at the firewall automatically; alert SOC.
5) Incident Alerts & Response Automation
The Problem: Detecting an issue is useless if the notification sits in an email inbox that nobody checks on weekends. ISO 27001 requires a defined incident response procedure.
The SIEM Capability: Alerting and Orchestration.
ISO 27001 Tie-In: Supports A.5.24 (Incident Management).
Template: Alert Logic + Response Escalation
- Objective: Ensure timely response to critical issues.
- Logic:
- If Severity = Critical (e.g., Ransomware detected), trigger PagerDuty to the on-call engineer immediately.
- Create a ticket in Jira/ServiceNow with the tag Type=Security_Incident.
- Include relevant log snippets in the ticket description for faster triage.
- SLA: Acknowledge within 15 minutes.
6) Vulnerability & Change Monitoring
The Problem: Unmanaged changes are a leading cause of breaches. A developer might open port 22 (SSH) to the world for "testing" and forget to close it. Recent reports indicate that common misconfigurations and lack of MFA remain top cloud risks.
The SIEM Capability: Configuration Monitoring.
ISO 27001 Tie-In: Supports A.8.19 (Installation of software on operational systems) and A.8.20 (Networks security).
Template: Change Detection Rule
- Objective: Detect unauthorized configuration changes.
- Log Sources: CloudTrail (AWS), Activity Logs (Azure), Audit Logs (GCP).
- Logic:
- Filter for event names: AuthorizeSecurityGroupIngress, UpdateGateway, StopLogging.
- Exclude the automation user (Terraform/Jenkins service account) to find manual changes made via the console (Console actions are high risk).
- Action: Alert Security Engineering to verify the change was approved via Change Control.
7) Access Control & Privileged Activity Tracking
The Problem: Privileged users hold the keys to the kingdom. ISO 27001 mandates strict control over the allocation and use of these rights.
The SIEM Capability: User Behavior Analytics (UBA).
ISO 27001 Tie-In: Supports A.8.2 (Privileged access rights).
Template: Privileged Access Monitoring Dashboard
- Objective: Monitor usage of "Break Glass" or root accounts.
- Log Sources: Unix sudo logs, Windows Event ID 4672 (Special Privileges Assigned).
- Logic:
- Alert immediately on any login by the root or Administrator account (Note: Best practice is to use named accounts and escalate privileges, not log in as root directly).
- Alert on sudo usage for sensitive commands (e.g., rm -rf, chmod 777, visudo).
- Action: Review with the user to confirm business justification.
Designing Strong SIEM Use Case Templates
Implementing SIEM Use Cases For ISO 27001 is not as simple as turning on "default" rules. Default rules generate noise. To build durable controls, you must follow a structured design methodology.
Define Objectives
Start with the "Why." Do not ingest logs just to have them. Are you trying to detect data exfiltration? Are you trying to prove that access was revoked for terminated employees? Define the objective clearly. For example, "We need to ensure that no production data is downloaded to personal devices."
List Required Log Sources
Identify where the data lives. If you want to track file access, do you need logs from the file server, the endpoint EDR, or the DLP solution? Ensure these sources are configured to send the correct level of verbosity. A common mistake is leaving logs at "Error" level when "Information" level is needed to see successful login attempts.
Build Detection Rules and Scoring
Avoid binary alerts for low-fidelity events. Instead, use a risk-scoring model.
- User logs in from a new city: Score +10 (Not an alert yet).
- User accesses a sensitive file they rarely touch: Score +20.
- User attempts to export 500 records: Score +30.
- Total Score 60: Threshold crossed -> Trigger Alert.
This approach reduces false positives and prevents alert fatigue.
Establish Reporting Formats
Decide how the output should look before you build the rule. Does the auditor need a CSV list? Does the CISO need a pie chart? Configure the SIEM to generate these formats automatically. This is where the concept of "Outcome-as-a-Service" shines—we build the end state (the report) into the initial design.
Implementing SIEM at Enterprise Scale
Deploying SIEM for a small startup is vastly different from an enterprise implementation. Scale introduces complexity in data volume, cost, and correlation.
Deployment Architecture
For modern enterprises, we typically recommend a cloud-native architecture.
- Collectors: Lightweight agents (like OpenTelemetry or vendor-specific agents) sit on the edge nodes or servers. They compress and encrypt data before transmission.
- Data Lake / Cold Storage: To manage costs, not all data needs to be in "hot" storage (expensive, searchable in milliseconds). Logs required strictly for ISO 27001 retention (1 year) but rarely queried can be routed to cheaper object storage (e.g., AWS S3 Infrequent Access).
- Correlation Engine: This is the "hot" layer where your SIEM Use Cases For ISO 27001 run. Only high-value data needed for immediate detection flows here.
Handling High Volume
Ingesting everything is cost-prohibitive. You must filter.
- Drop: Debug logs, load balancer health checks (unless investigating an issue), and noisy application operational logs.
- Aggregate: instead of logging 1000 firewall "accept" packets, log a summary: "1000 packets accepted from IP X to IP Y in 1 minute."
Integration with SOC and Vulnerability Management
The SIEM cannot stand alone. It must feed into the broader security ecosystem.
- Vulnerability Data: Feed scan results (from Tenable, Qualys) into the SIEM. This allows you to correlate an attack (Intrusion Prevention System log) with a target's vulnerability status. An attack against a patched server is an incident; an attack against a vulnerable server is a crisis.
SIEM Operational Considerations
Building the SIEM is the easy part. Operating it year-round is where most internal teams struggle. This is why Konfirmity advocates for a managed approach—technology requires human oversight.
Managing Alert Fatigue
If your SOC analysts receive 500 alerts a day, they will investigate zero. They will simply click "Resolve All." This is "normalization of deviance," and it is dangerous.
- Tune Regularly: Review the noisiest alerts weekly. If an alert has a 90% false positive rate, tune the logic or disable it.
- Contextualize: Ensure the alert includes context (User, Asset criticality) so the analyst can make a fast decision.
Data Protection and Retention Policies
Ironically, the SIEM itself is a high-risk asset because it holds sensitive data.
- Access Control: Only authorized security personnel should have access to SIEM data. Implement Role-Based Access Control (RBAC).
- Encryption: Logs must be encrypted in transit (TLS) and at rest.
- Retention: Automate the deletion of logs after the retention period (e.g., 365 days) to comply with GDPR data minimization principles.
Workflow for Risk Assessment
Feed SIEM insights back into your ISO 27001 risk assessment. If your SIEM shows a 300% increase in phishing attempts, your next risk assessment should reflect "Phishing" as a higher likelihood risk, and you should adjust your controls (e.g., better email filtering or training) accordingly. This cycle of Measure -> Analyze -> Improve is the heart of the ISO 27001 continuous improvement requirement.
Wrap-Up: Business Value for Enterprise Clients
Implementing SIEM Use Cases For ISO 27001 is an investment, but the return on investment (ROI) for enterprise clients is tangible and immediate.
First, it reduces the friction of sales cycles. When a Fortune 500 buyer sends a security questionnaire asking, "How do you detect malicious insiders?", you do not answer with a vague paragraph. You provide a screenshot of your Privileged User Monitoring dashboard. This level of maturity builds trust instantly.
Second, it drastically reduces audit costs. By automating evidence collection through SIEM, you save hundreds of engineering hours. Konfirmity clients typically spend around 75 hours per year on audit tasks, compared to the 550–600 hours typical of self-managed programs.
Finally, it provides quantifiable risk reduction. Organizations that deploy security AI and automation extensively save an average of $2.2 million in breach costs. You move from a reactive posture, hoping nothing breaks, to a proactive posture where you have visibility into every corner of your estate.
At Konfirmity, we believe that you should start with security and arrive at compliance. A properly implemented SIEM is the ultimate expression of this philosophy. It is not just about checking a box for an auditor; it is about building a nervous system for your enterprise that detects threats, preserves evidence, and proves to your customers that their data is safe.
If you are ready to move beyond "compliance manufacturing" and build a durable, audit-ready security program, we are ready to execute.
FAQ
1) Does ISO 27001 require a SIEM solution?
ISO 27001 does not mandate SIEM by name, but it does require continuous monitoring, logging, and incident detection—capabilities that are operationally difficult to achieve at scale without a SIEM.
2) SIEM supports which ISO 27001 controls?
SIEM directly supports A.8.15 (Logging), A.8.16 (Monitoring Activities), A.5.24 (Incident Response), and A.5.7 (Threat Intelligence), along with several access control requirements.
3) How does SIEM support audit evidence collection?
SIEM centralizes logs, keeps a historical record (WORM), timestamps events, and produces exportable reports. This allows you to provide auditors with instant proof of compliance without manual data gathering.
4) What are common SIEM use cases for compliance?
SIEM Use Cases For ISO 27001 typically include automated compliance reporting, log retention verification, alerting on policy violations (like unauthorized admin access), and audit trail generation for sensitive data access.
5) How should SIEM alerts tie into incident response?
Alerts should trigger documented response workflows. High-severity alerts should automatically generate tickets in your ITSM tool, assign owners, and initiate the response SLAs defined in your incident response policy.





.svg)



.svg)
.svg)