Most organizations approach ISO 27001 training as a checkbox compliance exercise—develop generic security awareness modules, assign them to employees, track completion rates, and present a tidy spreadsheet to auditors. This approach creates a fundamental gap between documented training programs and actual security competence—a gap that becomes apparent when auditors probe beyond completion logs or when incidents expose workforce vulnerabilities that training should have addressed.
The global ISO 27001 certification market reached $18.59 billion in 2025, driven by enterprise buyers who demand evidence that vendors maintain robust information security management systems. When you sell to enterprise clients, your security posture extends beyond technical controls to include how your workforce understands, implements, and maintains those controls. Competence is about having specific knowledge, skills, and experience to perform a job effectively as it relates to information security—it's a role-specific requirement, distinct from general awareness but equally critical for certification readiness.
This guide provides practical frameworks for designing training modules aligned with your risk assessment, raising employee awareness across your organization, integrating training with security controls and risk management processes, and documenting evidence that satisfies audit requirements. Drawing from 6,000+ completed audits, we address the implementation realities organizations face when building training programs under resource constraints while meeting enterprise client expectations.
What Is ISO 27001 & Why Training Matters?
ISO 27001 Clause 7.2, also known as the competence clause, requires organizations to determine the necessary competence of people doing work under their control that affects information security performance. The standard establishes requirements for information security management systems across ten core clauses: context of the organization, leadership, planning, support, operation, performance evaluation, and improvement. Organizations seeking certification must demonstrate systematic implementation of policies, controls, risk management processes, and documented evidence of operational effectiveness.
For companies selling to enterprise clients, ISO 27001 certification functions as a prerequisite for vendor qualification processes. Enterprise procurement teams evaluate supplier security through questionnaires, on-site assessments, and third-party attestations. Certification signals that your organization maintains documented security policies, conducts regular risk assessments, implements technical and administrative controls, and—critically—ensures personnel possess competence to execute security responsibilities.

Linking to Training, Awareness & Employee Culture
Human error is one of the biggest risk factors. Any information security management system depends fundamentally on people: employees handling sensitive data, following documented procedures, recognizing threats, reporting incidents, and maintaining security controls in daily operations. Technical safeguards provide necessary protection, but without workforce competence and awareness, even sophisticated controls fail when employees misconfigure systems, fall victim to phishing attacks, or bypass security procedures.
Awareness is a specific ISO 27001 requirement—Clause 7.3. Awareness (Clause 7.3) is about ensuring all people under the organization's control are aware of the information security policy, their contribution to the ISMS, and the implications of not conforming. Awareness is a universal requirement for all personnel, while competence is targeted to specific roles. Training bridges this distinction by providing role-based instruction that builds both general awareness and specialized competence where security responsibilities demand it.
Studies show that ongoing security awareness training can reduce the risk of employee-driven cyber incidents by up to 72 percent, and companies that consistently engage in security awareness training experience a remarkable 70 percent reduction in security incidents. This data demonstrates training's measurable impact on organizational risk posture—not merely compliance theater but actual risk reduction that enterprise clients expect from certified vendors.
What Enterprise-Selling Companies Should Know
When selling to enterprise clients, buyers scrutinize compliance, security policies, and evidence of training programs during vendor security assessments. Procurement teams request documentation of training completion, awareness program structure, role-based competency frameworks, and evidence that security responsibilities are understood across your workforce. Enterprise clients recognize that vendors with inadequately trained staff introduce supply chain risk regardless of technical control implementation.
Framing training beyond tick-box compliance demonstrates that you control the people and process dimensions of security, not just the technical layer. Auditors will evaluate whether training aligns with your documented risk assessments, whether employees understand their specific ISMS roles, and whether your organization maintains evidence proving training effectiveness. Organizations treating training as administrative burden rather than risk management investment signal operational immaturity to both auditors and enterprise buyers.
Understanding the Training Requirements in ISO 27001
Which Clauses Refer Explicitly to Training and Awareness
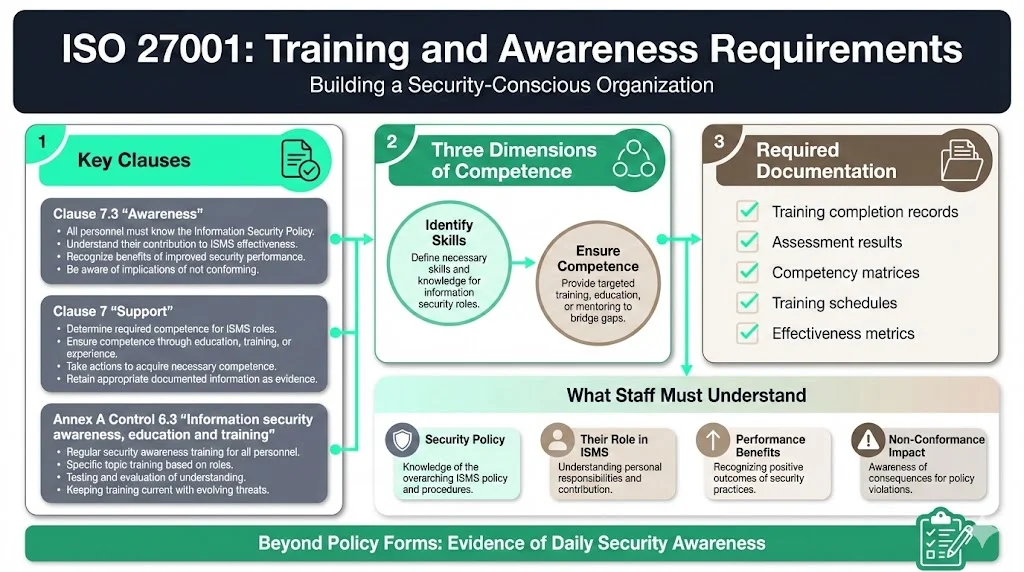
ISO 27001 Clause 7.3, titled "Awareness," sets out the requirements for raising information security awareness. This includes ensuring that all staff are aware of the importance of information security, the organization's information security policy, and their own responsibilities in relation to information security. Clause 7 "Support" encompasses competence, awareness, and communication requirements that form the foundation for training obligations.
Organizations must identify the skills, knowledge, and experience needed for each role that impacts the Information Security Management System (ISMS), ensure that people in those roles possess them, and keep documented evidence of their competence. This requirement extends beyond general security awareness to role-specific competence: security architects must understand threat modeling and control design; developers must follow secure coding practices; system administrators must implement access controls correctly; and HR personnel must handle employee data according to classification policies.
Annex A Control 6.3 focuses on raising awareness of the significance of information security, advocating good practice, and encouraging conformity to relevant policies and regulations. It stresses the need for staff to receive suitable instruction in information security, including regular policy refreshers pertinent to their roles.
What "Training Requirements" Means in Practice
Competence requirements manifest in three dimensions: identifying required skills and knowledge for security-affecting roles, ensuring personnel possess or acquire necessary competence through education and training, and retaining documented evidence proving competence levels. Auditors will look at training plans and want to see evidence that competence is maintained. This is usually in the form of looking at plans for the coming 12 months to see if any competence gaps or ongoing training requirements have been considered and documented.
Awareness requirements demand that employees understand the information security policy, recognize their contribution to ISMS effectiveness, comprehend benefits of improved security performance, and acknowledge implications of non-conformance. Organizations must demonstrate this awareness exists not merely through policy acknowledgment forms but through evidence that employees recognize security responsibilities in their daily work.
Documentation and evidence form the third dimension. ISO 27001 mandatory documents include records of training, internal audit programs, and monitoring results. Records of training, skills, experience, and qualifications document evidence of personnel competence in information security roles. Auditors expect training completion records, assessment results, competency matrices mapping roles to required skills, training schedules, and evidence demonstrating program effectiveness through metrics and incident trends.
Relating Training to Risk Management and Security Controls
Training programs cannot exist as generic security education divorced from your organization's specific risk profile. Annex A contains a list of 93 security controls, grouped into four themes: organizational, people, physical and technological. Your risk assessment identifies threat scenarios relevant to your organization—data breaches, ransomware, insider threats, supply chain compromises, compliance violations. Training must address how employees recognize, prevent, and respond to these identified risks.
Controls within Annex A specify security measures your organization implements to treat identified risks. People controls include practices like employee background checks and security awareness training. The controls in this section require every employee to be clearly aware of their information security responsibilities. Training ties directly to control implementation: if you implement access control measures (A.5.15), employees must understand authentication requirements and privilege management; if you implement incident response procedures (A.5.26), staff must know how to recognize and report security events; if you implement mobile device management (A.6.7), users must follow secure configuration and usage policies.
Why This Matters for Enterprise-Client Vendors
Demonstrating training programs aligned with documented risks and implemented controls provides evidence of professional development and systematic control over the human security layer. Enterprise clients conducting vendor assessments evaluate whether your workforce possesses competence to protect client data, maintain confidentiality, recognize threats, and execute security procedures. Training documentation helps fulfill client compliance requirements and supports certification claims during procurement evaluations.
Organizations that cannot demonstrate role-based competence and organization-wide awareness introduce workforce risk that enterprise buyers will identify during due diligence. Vendor security questionnaires specifically probe training program structure, completion rates, awareness testing, and evidence of ongoing security education—questions that demand substantive answers beyond "yes, we train employees annually."
Designing a Training Framework for Busy Teams
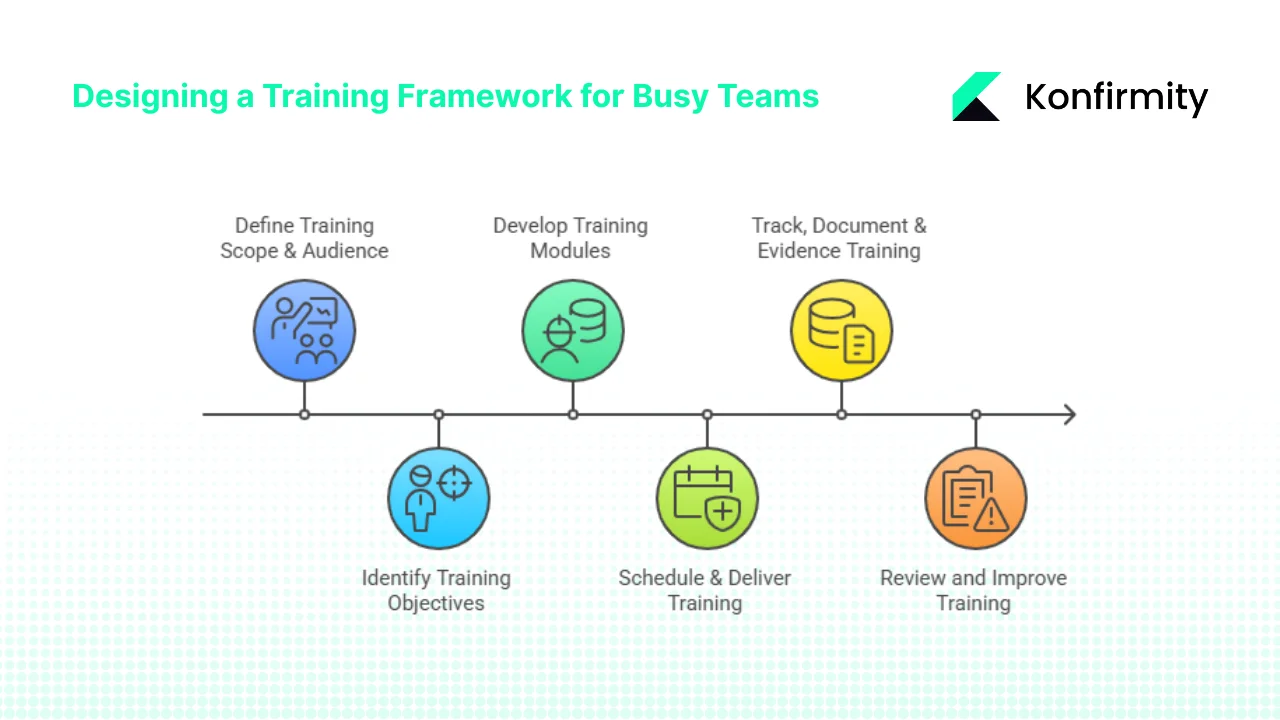
Step 1: Define Training Scope & Audience
Begin by mapping which employee categories and roles require what level of training. Technical staff need deep competence in secure system administration, vulnerability management, and incident response. Non-technical staff require awareness of phishing recognition, data handling procedures, password hygiene, and incident reporting. Management needs understanding of risk management frameworks, compliance obligations, ISMS performance metrics, and leadership responsibilities. Contractors and temporary personnel require onboarding training covering security policies applicable to their access levels.
Determine what information assets and systems your ISMS scope encompasses—this boundary defines what data, applications, and infrastructure your training must address. If your scope includes customer data processing systems, training must cover data protection obligations; if it includes development environments, training must address secure coding and change management; if it includes remote work arrangements, training must cover endpoint security and secure remote access procedures.
Step 2: Identify Training Objectives Based on Risk & Controls
Use your risk assessment to identify key threat scenarios requiring workforce awareness: phishing and social engineering attacks, password compromise, malware infection, unauthorized data access, insider threats, physical security breaches. Map training modules to implement controls—if you've implemented multi-factor authentication (MFA) as an access control measure, training must ensure employees understand MFA usage and recognize authentication bypass attempts.
Training objectives should specify measurable outcomes: employees will recognize phishing indicators and report suspicious messages through designated channels; system administrators will follow documented change management procedures when modifying production systems; developers will conduct security testing before deploying code changes; managers will review access permissions quarterly and remove unnecessary privileges.
Step 3: Develop Training Modules
Typical training curricula include foundational modules covering ISMS overview and ISO 27001 fundamentals, information security policy and organizational objectives, roles and responsibilities across the workforce, and security culture expectations. Role-specific modules address technical competencies: secure system configuration for administrators, secure software development practices for engineering teams, data classification and handling for personnel with data access, vendor security management for procurement staff, and physical security procedures for facilities personnel.
Threat-specific modules focus on recognizing and responding to common attack vectors: identifying phishing emails and reporting procedures, creating strong passwords and using password managers, recognizing social engineering tactics, handling sensitive data securely, and responding to suspected security incidents. Control-specific modules explain implemented safeguards: access control policies and authentication requirements, encryption usage for data protection, mobile device security and acceptable use, backup procedures and disaster recovery, and incident response workflows.
Use engaging formats rather than lecture-based content. Short online modules of 15 to 30 minutes accommodate busy schedules and improve completion rates. Interactive scenarios present realistic situations requiring security decisions. Knowledge checks and quizzes reinforce learning and provide evidence of comprehension. Live sessions for complex topics enable discussion and questions. Refresher training maintains awareness between comprehensive training cycles.
Step 4: Schedule & Deliver Training
Prioritize high-risk roles first—employees with access to sensitive data, system administrators with privileged credentials, customer-facing personnel handling external communications, and management responsible for security decisions. Establish training cadence: onboarding training for new hires covering foundational awareness and role-specific requirements, periodic refresher training at six- or 12-month intervals maintaining awareness and addressing emerging threats, and role-specific deep dives when responsibilities change or new controls are implemented.
ISO 27002 suggests establishing an information security awareness, education, and training program in line with your information security policies. It also says that awareness, education, and training should take place "periodically," as well as for new joiners. Often, organizations take this to be at least annually, but to truly keep security fresh in employees' minds, you may want to give refresher training as frequently as every six months.
Ensure training is practical and scenario-based rather than theoretical. Present realistic examples employees encounter in their work environments. Use actual incident examples (anonymized appropriately) to illustrate consequences of security failures. Provide clear guidance on what actions to take when encountering suspicious activity. Make reporting mechanisms obvious and accessible.
Step 5: Track, Document & Evidence Training
Maintain comprehensive records documenting who completed training, when training occurred, assessment results demonstrating comprehension, and any follow-up actions for employees requiring additional instruction. Link training evidence to audit readiness—training records constitute mandatory documented information under Clauses 7.2 and 7.3.
ISO 27001 mandatory documents include records of training, internal audit programs, and monitoring results. Clause 8.2 and 8.3 require results of the information security risk assessment and information security risk treatment. Clause 9.1 requires access control policy, evidence of ISMS monitoring and tracking metrics. Clause 9.2 requires a documented internal audit process and completed internal audit reports. Training documentation supports multiple audit requirements simultaneously.
Implement a tracking system capturing employee name and role, training modules assigned and completed, completion dates, quiz or assessment scores, manager approval for role-based competence verification, and scheduled refresher training dates. Automated learning management systems streamline tracking and generate audit-ready reports. Spreadsheet-based tracking suffices for smaller organizations provided documentation remains current and accessible.
Step 6: Review and Improve Training
Use metrics to evaluate training effectiveness: completion rates indicating engagement and program reach, quiz scores measuring comprehension and knowledge retention, incident trends revealing whether training reduces security events, phishing simulation results demonstrating behavioral change, and audit findings identifying training gaps requiring remediation.
After a year of ongoing training, the average click-through rate on a phishing simulation will dip below five percent, which is approximately a 70 percent reduction. This quantifies expected training impact—measurable behavioral improvement demonstrating program effectiveness.
Update training modules based on new risks identified in periodic risk assessments, control changes following ISMS reviews or audits, business growth expanding scope or introducing new systems, regulatory changes imposing new compliance obligations, and incident response lessons learned from security events. Training programs require continuous improvement aligned with ISMS maintenance—static training content becomes obsolete as threat landscapes and organizational contexts evolve.
Practical Examples & Templates
Example Training Modules
Module A: ISMS and ISO 27001 Overview for All Staff (15 minutes)
- What is information security and why it matters to our organization
- Overview of ISO 27001 and our certification objectives
- Structure of our ISMS and how policies protect information assets
- Every employee's role in maintaining security and compliance
- Reporting security concerns and incidents through proper channels
Module B: Risk Management & Your Role in Identifying Risks (20 minutes)
- How we identify and assess information security risks
- Common threat scenarios affecting our industry and organization
- Recognizing potential security issues in daily work activities
- Your responsibility to report observed vulnerabilities or threats
- How risk management connects to controls you encounter daily
Module C: Security Controls in Your Organization (25 minutes)
- What controls we implement and why they exist
- Access controls: authentication, passwords, MFA, least privilege
- Data protection: classification, handling, encryption, disposal
- Physical security: badge access, visitor management, clean desk
- What you must do to maintain control effectiveness in your role
Module D: Incident Reporting & Breach Response (20 minutes)
- How to spot potential security incidents or policy violations
- Recognizing phishing, malware, unauthorized access, data leaks
- Step-by-step incident reporting procedures and escalation paths
- What happens after you report an incident
- Examples of real incidents and how proper reporting prevented harm
Module E: Role-Specific Deep Dive (30-45 minutes)
- Developers: secure code practices, vulnerability testing, change control
- System administrators: privileged access management, patch management, monitoring
- HR personnel: handling employee data, background checks, termination procedures
- Sales teams: protecting client information, secure communication, data sharing policies
Template Assets for Busy Teams
Training Record Log Template
Refresher Schedule Calendar Template
Incident Reporting Flowchart Template
- Observe suspicious activity or potential security incident
- Do not attempt to investigate or resolve independently
- Report immediately via [email/phone/portal]
- Provide: what you observed, when it occurred, systems affected, your contact information
- Security team acknowledges receipt within 2 hours
- Security team investigates and determines severity
- You receive update on resolution and any follow-up actions required
Quiz Template: ISMS Overview Assessment
- What is the purpose of our information security policy? (Multiple choice)
- Which of the following are considered security incidents requiring reporting? (Select all that apply)
- What is your primary responsibility regarding information security in your role? (Short answer)
- How should you handle confidential client data? (Multiple choice)
- What should you do if you receive a suspicious email claiming to be from IT requesting your password? (Multiple choice)
How to Adapt Templates for Enterprise-Client Vendor Context
Include sections addressing "How we protect client data under our ISMS"—useful for sales teams during client onboarding conversations and procurement discussions. Explain that client data receives classification levels determining handling requirements, that access controls limit who can view or modify client information, that encryption protects data in transit and at rest, and that incident response procedures include client notification protocols when their data is affected.
Provide a "client-facing training summary" document that can be shared with enterprise clients demonstrating how your workforce is trained. This summary should outline training program structure and frequency, topics covered in awareness and role-specific training, competence requirements for employees handling client data, evidence of training completion and effectiveness metrics, and how training aligns with relevant compliance frameworks clients require.
Time-Efficient Rollout Advice
Keep modules short—15 to 30 minutes for non-security staff accommodates attention spans and busy schedules. Use e-learning or micro-learning platforms for distributed sales and development teams working remotely or across locations. Automate tracking where possible using learning management systems that record completion, send reminders, and generate compliance reports. Leverage existing security policies and documented controls as training content rather than creating materials from scratch—your documented ISMS already contains the substance training must communicate.
Integrating with Certification, Compliance & Continuous Improvement
Training as Part of Your Certification Readiness
ISO 27001 requires evidence that all employees understand their role in maintaining information security. Training should cover security awareness, reporting procedures, and daily best practices. Evidence of training constitutes one category of documented information auditors will request during Stage 1 documentation review and Stage 2 certification audit.
ISO/IEC 27001:2013 Clause 7.2 requires organizations to ensure persons are competent based on appropriate education, training, or experience. Annex A control A.7.2.2 requires appropriate awareness education and training and regular updates in organizational policies and procedures, as relevant. Training links to Clauses 4 through 10 covering ISMS establishment, leadership, planning, support, operation, performance evaluation, and improvement. Training also links to Annex A controls across all four themes: organizational controls specifying policy and procedure training, people controls requiring awareness and competence development, physical controls demanding understanding of security areas and equipment protection, and technological controls necessitating technical competence for system administration and secure configuration.
Training Tied to Compliance and Security Controls
Employees must understand security policies not as abstract documents but as practical guides governing daily activities. Training translates documented policies into actionable knowledge: what the acceptable use policy permits and prohibits, how the access control policy determines who can access what systems, why the data classification policy requires marking sensitive documents, and when the incident response policy obligates reporting security events.
Training reinforces how risk management and control implementation work in practice. Employees learn that security controls are not arbitrary restrictions but deliberate safeguards addressing identified risks. Explaining the "why" behind controls improves compliance—personnel who understand that MFA prevents credential compromise are more likely to use it correctly than those who view it as inconvenient friction imposed by IT.
Training supports the culture needed for ongoing compliance through internal audits, management reviews, and control monitoring. ISO 27001 is all about continuous improvement. Organizations maintaining certification must demonstrate ISMS effectiveness over three-year certification cycles with annual surveillance audits. Training programs that treat awareness as one-time events fail to sustain the security culture's continuous improvement demands.
Maintaining Momentum Post-Certification
ISO 27001 certification is not "set and forget." Ongoing training forms part of continual improvement required for maintaining certification. The ISO 27001 certification holds validity of three years; it, however, requires the organization to undergo Periodic Surveillance Audits every year. The Periodic Surveillance Audits are mandatory to maintain your ISO 27001 certification.
Use training refreshers addressing emerging threats not covered in initial training cycles, updates for new risks identified in annual risk assessments, training on new controls implemented following ISMS changes, and corrective actions addressing training gaps identified during internal audits or surveillance audits. Schedule refresher training at intervals ensuring awareness remains current—annual refreshers for general awareness topics, semi-annual for roles with elevated security responsibilities, and ad-hoc training when incidents reveal knowledge gaps requiring immediate remediation.
Align Training with Your Enterprise Client Strategy
Emphasize to enterprise clients during procurement evaluations that your workforce is trained, competent, and aware of security policies protecting their data. Use training proof and policies as part of vendor security documentation included in responses to RFPs and security questionnaires. Link training metrics and audit findings into client reporting or vendor assurance engagements—demonstrating training completion rates, assessment results, and incident trends provides transparency that enterprise buyers value.
Organizations that cannot substantiate training claims during vendor assessments introduce doubt about operational security maturity. Enterprise clients evaluating multiple vendors will favor suppliers who provide concrete evidence of workforce competence over those offering vague assurances.
Checklist for Busy Teams
Pre-Training Preparation
- Obtain management buy-in and assign ISMS training program ownership
- Define ISMS scope to determine what training must address
- Identify employee roles and categories requiring different training levels
- Review risk assessment to identify threat scenarios training must cover
- Map training requirements to implement Annex A controls
Training Development
- Develop foundational ISMS overview module for all personnel
- Create role-specific technical competence modules for security-affecting roles
- Build threat awareness modules addressing phishing, social engineering, password security
- Design incident reporting training explaining recognition and escalation procedures
- Establish refresher training schedule and content updates
Training Deployment
- Schedule onboarding training for new hires
- Deliver initial training to existing workforce in priority order
- Track completion using learning management system or tracking spreadsheet
- Administer knowledge assessments measuring comprehension
- Document training completion dates and assessment results
Documentation & Evidence
- Maintain training records linking employees to completed modules
- Retain quiz results and competence assessments
- Document follow-up actions for employees requiring additional training
- Prepare training evidence organized by clause and control for audit submission
ISMS Integration
- Map training program to information security policy requirements
- Link training topics to relevant Annex A controls
- Connect training to risk treatment plans addressing identified threats
- Align training schedule with internal audit calendar and management review cycle
Review & Improvement
- Review training metrics quarterly: completion rates, assessment scores, incident trends
- Update training content annually or when risks, controls, or policies change
- Analyze audit findings identifying training gaps requiring remediation
- Solicit employee feedback on training relevance and effectiveness
- Benchmark training effectiveness using industry metrics (phishing simulation results, incident reduction)
Client-Facing Assets
- Prepare training program summary for inclusion in vendor security documentation
- Document how training addresses client data protection requirements
- Compile training evidence for RFP responses and security questionnaires
- Include training metrics in periodic reporting to enterprise clients requiring vendor oversight
Conclusion
Embedding training into your ISMS implementation addresses ISO 27001 training requirements while delivering measurable risk reduction and operational security improvements. For companies selling to enterprise clients, comprehensive training programs function as competitive differentiators during vendor evaluations—you demonstrate not merely that controls exist on paper but that your workforce possesses competence to implement and maintain those controls effectively.
Training requirements under Clauses 7.2 and 7.3 and Annex A Control 6.3 demand organizations ensure workforce competence for security-affecting roles and organization-wide awareness of security policies, ISMS contributions, and implications of non-conformance. Organizations achieving certification must document training programs, maintain completion records, assess training effectiveness through metrics and behavioral indicators, and demonstrate continuous improvement through updated content addressing emerging risks and audit findings.
The frameworks, module examples, and templates provided enable organizations to fast-track training program rollout while aligning with certification requirements, compliance obligations, and enterprise client demands. Training programs treat workforce awareness as strategic investment rather than administrative burden to position organizations to pass certification audits, satisfy client security requirements, and reduce security incidents through measurable behavioral change. Training is not auxiliary to information security management—it is foundational to ISMS effectiveness and organizational risk posture.
FAQ Section
1) Does ISO 27001 require security training?
Yes. ISO 27001 mandates that personnel who perform tasks affecting the ISMS must be competent (Clause 7.2). Organizations must determine the necessary competence of people doing work under their control that affects information security performance, identify the skills, knowledge, and experience needed for each role that impacts the ISMS, ensure that people in those roles possess them, and keep documented evidence of their competence. Clause 7.3 requires that employees are aware of the information security policy, the importance of information security, the organization's information security policy, and their own responsibilities in relation to information security.
2) What are the mandatory requirements of ISO 27001?
Core mandatory requirements include establishing an information security management system defining scope and boundaries, conducting leadership commitment through policy approval and resource allocation, performing risk assessment and risk treatment identifying threats and implementing controls, documenting security policies covering access control, incident response, and acceptable use, implementing applicable controls from Annex A's 93 controls across organizational, people, physical, and technological categories, developing training and awareness programs ensuring competence and awareness, conducting internal audits evaluating ISMS conformance and effectiveness, and maintaining continual improvement through management reviews, corrective actions, and performance monitoring.
3) What is required to achieve ISO 27001 certification?
Organizations must define ISMS scope specifying what information assets, systems, and processes certification covers; conduct risk assessment identifying information security threats and vulnerabilities; perform gap analysis comparing current state against ISO 27001 requirements; implement policies and controls addressing identified risks and gaps; train staff ensuring competence for security-affecting roles and awareness across the organization; collect evidence documenting control implementation, training completion, policy compliance, and ISMS performance; undergo Stage 1 audit where certification body reviews documentation for completeness and conformance; complete Stage 2 audit where auditors verify controls operate effectively and ISMS meets requirements; remediate any non-conformities identified during audit; and receive certification valid for three years subject to annual surveillance audits.
4) How do you become ISO 27001 certified?
The certification process begins with ISMS preparation: document scope, conduct risk assessment, develop policies, implement controls, establish training programs, and collect evidence. Select an accredited certification body recognized by national accreditation bodies ensuring certification holds international recognition. Schedule Stage 1 documentation review where auditors examine ISMS documentation identifying gaps requiring remediation before Stage 2. Address Stage 1 findings through documentation updates, additional evidence collection, or control implementation. Complete Stage 2 certification audit where auditors verify operational effectiveness through interviews, evidence sampling, and control testing. Remediate any non-conformities issued during Stage 2 within specified timeframes. Receive ISO 27001 certification upon successful completion. Maintain certification through internal audits, management reviews, continuous improvement, and annual surveillance audits conducted by certification bodies ensuring ongoing ISMS effectiveness over a three-year certification period.





.svg)






.svg)
.svg)