Most enterprise buyers now request assurance artifacts before procurement. Without operational security and continuous evidence, deals stall even when teams think they’re “ready” on paper. IBM’s 2025 Cost of a Data Breach report estimated the global average cost of a breach at $4.44 million, and confirmed that attackers routinely exploit known, unpatched vulnerabilities. In practice, more than 60% of breaches exploited weaknesses with available patches. This article explains why vulnerability management is essential when selling to enterprise and healthcare clients, how it fits into ISO 27001 and other frameworks, and what auditors expect. It draws on Konfirmity’s experience supporting over 6,000 audits and more than 25 years of combined expertise to show what works in the field.
Why vulnerability management matters when selling to enterprise clients
Enterprise and healthcare buyers treat security as a qualifier. Procurement teams ask for current SOC 2 Type II reports, ISO 27001 certificates, HIPAA attestations, and detailed responses to security questionnaires. In 2025, companies pursuing SOC 2 saw compliance as a “front‑door key” to closing serious deals. Without credible evidence of controls, even strong products struggle to progress beyond due‑diligence. Vulnerability management is a visible control area because it directly protects customer data and shows operational maturity. When technical weaknesses are left unmanaged, deals stall, renewal terms lengthen, and contractual clauses become more onerous. For healthcare providers handling electronic protected health information (ePHI), patching vulnerabilities is not optional—it is required under the HIPAA Security Rule’s technical safeguards. Buyers compare vendors based on how quickly they identify, prioritize, remediate, and monitor vulnerabilities and whether those processes are repeatable and audited.

How ISO 27001 vulnerability management fits into broader information security expectations
ISO 27001:2022 defines an Information Security Management System (ISMS) that covers policies, procedures, and controls to manage information risks. Vulnerability management appears explicitly in Clause 12.6.1 (Management of technical vulnerabilities) which requires organizations to “obtain information about technical vulnerabilities in a timely fashion, evaluate exposure, and take appropriate measures to address the associated risk”. The clause connects vulnerability handling to risk assessment, asset management, and continual improvement. Under Annex A of the standard, control A.8.8 requires a risk‑based, documented process for discovering, prioritizing, treating, and reviewing technical vulnerabilities. Rather than simply running a scanner, ISO 27001 expects organizations to integrate vulnerability management into their ISMS—complete with defined roles, ownership, timelines, and evidence. For companies pursuing SOC 2, HIPAA, or GDPR compliance in parallel, a single vulnerability management program can satisfy multiple frameworks. SOC 2’s Security trust service criteria emphasize change management, patch deployment, and vulnerability response; HIPAA requires risk-based safeguards and documentation; GDPR articles 32–34 mandate technical measures proportionate to risks to personal data. A risk‑based vulnerability program therefore serves as a common denominator across frameworks and directly supports enterprise sales by building trust.
Common gaps enterprises flag during vendor security reviews
Konfirmity’s audit experience shows that most vendor reviews uncover similar gaps:
- Ad‑hoc scanning without context: Vendors often present high volumes of findings but cannot show how they prioritize or link them to business risk. Auditors describe such programmes as “ad hoc”.
- Incomplete asset coverage: Without a complete inventory of cloud accounts, applications, and dependencies, scans miss critical systems. Missing assets are flagged during audits as blind spots.
- Weak prioritization logic: Teams rely solely on CVSS scores and ignore exploitability, asset criticality, or data sensitivity. Modern guidance emphasizes using exploit availability and business impact to prioritize.
- Lack of documented follow‑up: Findings linger in spreadsheets without clear ownership, remediation records, or acceptance. Survey data show that 41% of organizations struggle with third‑party risk and supplier compliance; vulnerability findings are part of that challenge.
- Over‑reliance on tools: Automated scanners alone do not satisfy auditors. ISO 27001 and SOC 2 expect manual testing, penetration testing, and threat intelligence to complement scans.
This article explains how to build a robust vulnerability management programme that addresses these gaps and stands up to enterprise buyer scrutiny.
ISO 27001 Vulnerability Management Explained
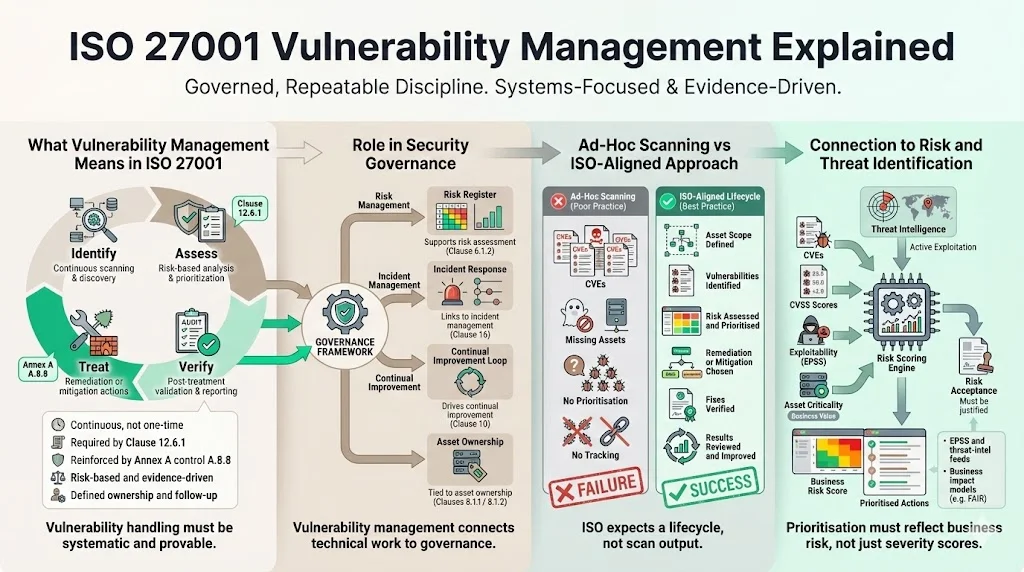
What vulnerability management means in the context of ISO 27001
In ISO 27001, vulnerability management is a continuous discipline that identifies, assesses, prioritizes, and addresses technical weaknesses across systems. Clause 12.6.1 states that organizations must obtain information about vulnerabilities, evaluate exposure, and take measures to address risk. Annex A’s control A.8.8 reinforces that vulnerability handling must be risk‑based, systematic, and evidence‑driven. This goes beyond occasional scans. It requires documented processes, defined responsibilities, risk evaluation, treatment planning, and follow‑up. The goal is to reduce the likelihood and impact of incidents rooted in unpatched systems while providing evidence for audits and customer due‑diligence.
How it supports information security and security governance
Vulnerability management underpins multiple security objectives. It ensures that weaknesses are detected before attackers exploit them. By linking vulnerabilities to risk assessments (ISO 27001 §6.1.2), organizations can prioritize treatment based on asset criticality, data sensitivity, and exploitability. Asset management (Clauses 8.1.1 and 8.1.2) ensures that scans cover all relevant systems and that each asset has an owner responsible for remediation. Incident management (Clause 16) requires logging and responding to exploited vulnerabilities; a critical unpatched vulnerability may constitute an incident even without signs of compromise. Continual improvement (Clause 10) mandates that recurring findings and missed SLAs feed back into corrective actions. A structured vulnerability programme therefore strengthens governance by tying technical actions to risk, accountability, and improvement.
Difference between ad hoc scanning and a structured ISO‑aligned approach
Ad‑hoc scanning often produces long lists of CVEs without context. This approach misses assets, lacks prioritization, and fails to track remediation. In contrast, ISO‑aligned vulnerability management follows a lifecycle: define asset scope, identify vulnerabilities, assess and prioritize risk, treat weaknesses, verify fixes, and monitor for improvement. The Wiz vulnerability management lifecycle describes six stages—identification, assessment, prioritization, remediation and mitigation, verification and validation, and reporting and improvement—mirroring ISO requirements. The same article notes that asset visibility is critical, prioritization must reflect business risk, remediation is not always the answer, and verification through re‑scanning is essential. The NIST framework similarly lists identification, assessment, mitigation, remediation, verification, and continuous monitoring. ISO 27001 therefore expects a structured, repeatable process grounded in risk rather than one‑off scans.
How vulnerability management connects to risk assessment and threat identification
Risk assessment is the starting point for all ISO 27001 controls. Vulnerabilities feed into risk assessments as threat sources. Clause 6.1.2 requires evaluating the likelihood and impact of identified risks to determine treatment options. Without linking vulnerability data to risk, organizations cannot justify remediation priorities or risk acceptance decisions. Threat intelligence informs the identification stage by highlighting which CVEs are actively exploited or have proof‑of‑concept exploits. Many scanners now integrate with the National Vulnerability Database (which adds more than 2,000 new entries monthly) and with Exploit Prediction Scoring Systems (EPSS). By combining CVSS scores, exploitability, asset criticality, and business impact—using models like FAIR—teams can prioritize what matters most to the organization.
Where Vulnerability Management Lives in ISO 27001
Relevant ISO 27001 clauses and Annex A controls
Vulnerability management touches several clauses:
- Clause 6.1.2 – Risk assessment: vulnerabilities are inputs into the risk assessment process, which determines likelihood and impact and defines treatment plans.
- Clause 8.1.1 – Asset inventory: a complete inventory of hardware, software, cloud services, and APIs is needed to scope vulnerability scans.
- Clause 8.1.2 – Asset ownership: each asset must have an owner responsible for remediation and risk acceptance.
- Clause 12.6.1 – Technical vulnerabilities: organizations must obtain vulnerability information, evaluate exposure, and take measures to address risk.
- Clause 10 – Continual improvement: recurring vulnerabilities or missed deadlines trigger corrective actions and process enhancements.
- Annex A – Control A.8.8: requires a documented, risk‑based vulnerability process with defined responsibilities, timelines, and evidence.
Risk assessment and treatment requirements
ISO 27001 mandates that organizations assess risks and decide how to treat them: avoid, mitigate, transfer, or accept. Vulnerability management provides data about the likelihood and impact of exploitation; risk assessments translate those into business terms. When vulnerabilities are high severity and actively exploited, treatment is usually mitigation or remediation—patching, configuration changes, or compensating controls. For lower‑risk or low‑impact weaknesses, organizations may accept the risk temporarily but must document the rationale and obtain approval. Auditors expect to see this rationale recorded in the risk register and aligned with the Statement of Applicability (SoA). Failure to tie vulnerability treatment to risk assessments often results in non‑conformities.
Asset management responsibilities
A complete asset inventory underpins effective vulnerability management. The Wiz article notes that overlooking cloud resources with severe vulnerabilities delays urgent remediation. Clause 8.1.1 requires maintaining an up‑to‑date inventory of hardware, software, cloud services, and APIs. Asset owners (Clause 8.1.2) must be defined so that vulnerabilities have clear accountability. Shadow IT, unmanaged SaaS applications, and inherited infrastructure from acquisitions can create blind spots. Konfirmity often discovers missing assets during onboarding; these gaps are documented as risks and addressed through discovery tools, interviews, and configuration reviews. Without accurate asset scope, vulnerability scans produce false negatives and audits may fail due to coverage gaps.
Security controls tied to technical weaknesses
Annex A control A.8.8 focuses on technical vulnerabilities, but other controls intersect. Change management (A.8.32) ensures that patches and configuration changes follow a defined process to avoid introducing new risks. Supplier relationships (A.5.21) require that third‑party services adhere to vulnerability management requirements; 41% of organizations cite third‑party risk as a major challenge. Secure development (A.8.25–A.8.28) mandates that applications are tested for vulnerabilities during development and before release. Monitoring and logging (A.8.16) helps detect exploited vulnerabilities and verify remediation. A holistic view ensures vulnerabilities across infrastructure, applications, and suppliers are addressed consistently.
How vulnerability management supports compliance without being a standalone control
Vulnerability management is not a standalone requirement; it supports numerous controls. For SOC 2, vulnerability handling demonstrates adherence to the Security trust service criteria by evidencing change management, timely remediation, and incident response. For HIPAA, it supports the technical safeguard requiring regular review of system activity and risk management. For GDPR, it helps demonstrate that appropriate technical measures are in place to protect personal data and that any high‑risk vulnerabilities have been addressed to meet the accountability principle. A single ISO aligned programme reduces duplicated effort across frameworks and ensures that evidence collected for one audit can support others. Konfirmity frequently leverages vulnerability data across SOC 2, HIPAA, and GDPR audits to satisfy multiple control objectives.
Role of leadership, ownership, and security policies
Executive sponsorship is critical. The management review process (Clause 9.3) must consider the effectiveness of vulnerability management and allocate resources accordingly. Policies define the scope, roles, and timelines. Without management backing, vulnerability remediation slips and exceptions accumulate. In Konfirmity’s audits, programmes with dedicated security leadership and clear accountability demonstrate shorter remediation times and fewer findings. Conversely, programmes where patching is a “best effort” often struggle, leading to findings such as “no clear treatment timelines by severity”. Leadership must approve risk acceptances, allocate resources for patching, and enforce deadlines.
Core Elements of an ISO 27001‑Aligned Vulnerability Management Programme
Building an effective programme requires structured processes. This section outlines practical steps that align with ISO 27001 and other frameworks while reflecting patterns observed across thousands of audits.
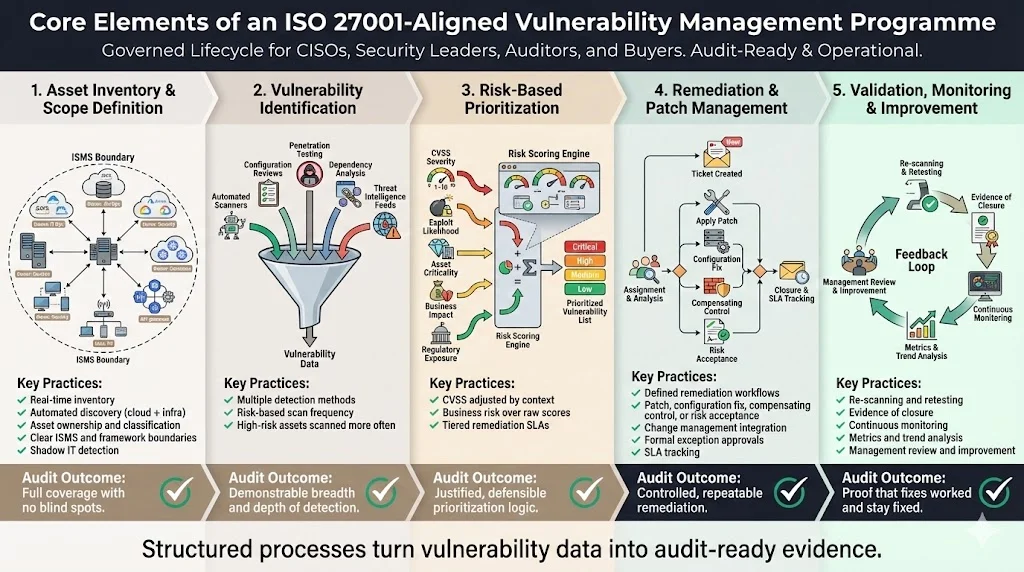
Asset inventory and scope definition
Asset management comes first. Without an inventory, vulnerability management is blind. Organizations should:
- Maintain a real‑time asset inventory: include on‑premises servers, virtual machines, containers, serverless functions, databases, endpoints, network devices, and cloud services. Use discovery tools (AWS Config, Azure Resource Graph, Google Cloud Asset Inventory) to automate inventory collection.
- Map ownership and classification: classify assets by criticality and data sensitivity (production vs. staging). Tie each asset to an owner responsible for remediation, risk acceptance, and budget decisions.
- Define scope boundaries: delineate which systems are in scope for ISO 27001 (ISMS boundary) and other frameworks (e.g., HIPAA environment or SOC 2 system). Include third‑party services, APIs, and inherited infrastructure. Document dependencies such as platform-as-a-service components and software libraries.
- Address shadow IT and inherited risk: perform periodic discovery and reconciliation to identify unregistered assets, rogue cloud accounts, or old environments left behind after migrations. Document these as risks and plan remediation.
In Konfirmity’s experience, organizations with complete inventories reduce audit time by 20–30% because they avoid last-minute scrambles to prove coverage. Conversely, missing assets often result in control failures.
Vulnerability identification methods
Once the asset scope is clear, organizations must identify vulnerabilities using multiple methods:
- Automated scanning: run external and internal scanners against infrastructure, applications, APIs, and cloud configurations. Include dependency and configuration analysis (SBOMs, CIS benchmarks). Ensure scanners cover containers, serverless functions, and network devices.
- Manual testing and configuration reviews: complement automated scans with manual penetration testing and configuration reviews. Manual tests uncover complex weaknesses that scanners miss. For high‑risk applications, schedule annual or semi‑annual penetration tests. Use secure configuration checklists (e.g., CIS benchmarks) for infrastructure.
- Penetration testing: while ISO 27001 does not explicitly mandate penetration testing, auditors often expect it for high-risk systems, especially when customers or regulators require it. Pen tests identify chained vulnerabilities and business logic flaws. Record scope, methodology, findings, and remediation status. For SOC 2 Type II, align pen tests with the observation period to ensure evidence is current.
- Threat intelligence and incident learnings: subscribe to vendor advisories, vulnerability databases (NVD), threat intelligence feeds, and security mailing lists. Evaluate how new CVEs affect your assets and adjust scanning. Use lessons from incidents to refine detection and scanning (e.g., scanning for Log4j‑like patterns after exploitation). Consider exploit prediction systems (EPSS) to prioritise vulnerabilities based on exploitation likelihood.
Konfirmity typically establishes scanning cadences based on asset risk—critical internet‑facing assets weekly, internal infrastructure monthly, and low‑risk systems quarterly. For healthcare environments, we sometimes increase cadences due to ePHI sensitivity.
Risk‑based prioritization
Identifying vulnerabilities produces data; prioritizing them turns data into action. Effective prioritization uses multiple factors:
- Severity and exploitability: consider CVSS scores but adjust based on exploit availability and active attacks. High severity with proof-of-concept exploits demands immediate attention; medium severity with no exploit can be scheduled later.
- Asset and business criticality: vulnerabilities on databases with sensitive data or customer-facing systems carry greater risk. Map each vulnerability to the asset’s classification and business process. For example, a CVSS 7.5 flaw on an Internet-facing payment gateway may outrank a CVSS 9.0 flaw on an internal test server.
- Quantitative risk models: use models like FAIR or risk scoring to translate technical severity into financial and operational impact. These models help justify remediation budgets and document risk acceptance.
- Regulatory and contractual obligations: certain vulnerabilities—especially on systems handling personal data—may trigger regulatory reporting or contractual obligations. For example, ePHI exposures under HIPAA require risk-based risk analysis and documentation.
Auditors expect to see a documented prioritization logic that combines severity, exploitability, asset criticality, and business impact. They will review tickets or registers to confirm that high‑risk findings were addressed within defined SLAs. Konfirmity often advises clients to define tiered remediation timelines (e.g., critical vulnerabilities patched within 7 days, high within 30 days, medium within 60 days, low within 90 days) and to document exceptions for valid reasons (e.g., vendor patch not available). This risk-based approach demonstrates maturity and reduces negotiation with auditors.
Remediation and patch management
Patching is the most visible aspect of vulnerability management and often the most challenging. Effective remediation involves:
- Defined workflows: integrate vulnerability remediation into change management processes. Use ticketing systems (e.g., Jira, ServiceNow) to assign tasks, track progress, and capture approvals. Record whether remediation involves applying a patch, changing configuration, deploying compensating controls, or accepting the risk. Include testing and rollback plans.
- Coordinated teams: involve engineering, IT, DevOps, and security teams. Clarify who applies patches (e.g., sysadmins, SRE), who tests applications (e.g., QA), and who verifies closure (security team). For managed service providers, coordinate with customer teams to avoid service disruption.
- Patch management schedules: adopt a cadence (e.g., monthly “Patch Tuesday” cycles) but allow urgent out-of-band updates for critical vulnerabilities. Document patch windows and maintenance outages. Align with vendor release cycles and cloud provider update schedules.
- Exceptions and delayed fixes: document reasons for delays (e.g., vendor patch not available, high risk of service disruption). Obtain formal risk acceptance from asset owners or management. ISO 27001 requires approval and periodic review of exceptions.
- Monitoring patch failures: track metrics like mean time to remediate (MTTR), patch success rate, and open vulnerability count. According to industry reports, organizations continue to struggle with timely patching; confirmed incidents show attackers exploiting vulnerabilities that were already patched but not yet applied by affected organizations. A disciplined process reduces these gaps.
Konfirmity’s data shows that clients who implement structured patch management reduce remediation time by 30–50% compared to those with ad‑hoc processes. Without management buy‑in and integration into deployment pipelines, patching becomes a burden and leads to non‑conformities.
Validation and follow‑up
Remediation is incomplete without verification. ISO 27001 expects evidence that vulnerabilities were treated and that fixes are effective. Best practices include:
- Re‑scanning and re-testing: run targeted scans after applying patches to confirm that vulnerabilities are no longer detected. For manual fixes, perform retesting or code review. Document results as evidence.
- Evidence of closure: update the vulnerability register with closure dates, responsible persons, and references to scan reports or change tickets. Attach screenshots or artifacts demonstrating that the vulnerability is resolved.
- Continuous monitoring: schedule periodic scans to catch new vulnerabilities and verify that previously resolved ones have not resurfaced. The NIST framework emphasizes continuous monitoring as a core activity. Consider integrating scanning tools into continuous integration/continuous deployment (CI/CD) pipelines for early detection.
- Metrics and improvement: track metrics such as number of open vulnerabilities, average remediation time per severity, and repeat findings. Use these metrics in management reviews to identify trends and allocate resources. Continuous improvement under Clause 10 requires updating policies and processes based on these insights.
Vulnerability Management Policy and Supporting Templates
Policies and templates provide structure and evidence. Auditors often ask for these documents to evaluate whether practices are formalized and followed.
Vulnerability management policy
A policy sets out the purpose, scope, and responsibilities for vulnerability management. It should include:
- Purpose and scope: explain that the policy covers all systems, applications, cloud services, and third‑party dependencies within the ISMS scope and aims to identify and address technical vulnerabilities proactively.
- Roles and responsibilities: define roles such as security lead, asset owner, vulnerability management team, and change management. Specify who receives vulnerability alerts, assesses risk, approves remediation, and verifies closure.
- Identification, assessment, and remediation steps: outline the lifecycle from asset inventory through identification, prioritization, treatment, and validation. Reference ISO 27001 Clause 12.6.1 and control A.8.8 for alignment. Include timelines (SLAs) for remediation based on severity.
- Review frequency and ownership: specify that the policy is reviewed annually or after significant changes. Assign ownership to a senior executive (e.g., CISO) to ensure accountability.
- Mapping to ISO 27001 expectations: cross-reference the policy with relevant clauses and controls (risk assessment, asset management, incident management, continual improvement). Indicate how evidence (registers, tickets, scan reports) supports audits.
Vulnerability register template
A vulnerability register is a structured record capturing details about each finding. Fields should include:
- Unique identifier and date discovered
- Asset reference and owner
- Vulnerability description and source (scanner, pen test, threat intel)
- Severity (CVSS base score, exploitability, business impact)
- Priority level and remediation SLA
- Assigned responsible person
- Treatment decision (remediate, mitigate, accept) and justification
- Status (open, in progress, resolved, accepted)
- Evidence of closure (link to scan report, change ticket)
- Risk acceptance approval (if applicable)
Auditors look for registers that link vulnerabilities to assets and risk levels and provide an audit trail of status changes. Use secure, access-controlled tools to maintain the register; spreadsheets are acceptable if version-controlled and backed by policy.
Scan reports and remediation records
Scan evidence should be clear and consistent. Include:
- Scan scope and date: state whether the scan was internal or external, the tool used, and which assets were covered.
- Findings summary: show the number of vulnerabilities by severity and highlight critical issues. Avoid oversharing details that could expose vulnerabilities; provide redacted reports to customers when necessary.
- Detailed findings: list each vulnerability with CVE, description, affected hosts, and recommended remediation. Reference vulnerability IDs in the register.
- Remediation records: include change tickets, patch notes, and verification results. Consistent formatting across tools helps auditors reconcile reports with registers.
Konfirmity advises clients to maintain a “scan library” with standardized report formats, ensuring repeatable evidence for audits and customer questionnaires.
Operational Practices Auditors Expect to See
Beyond policies and templates, auditors evaluate day‑to‑day practices. They expect to see:
- Documented scanning cadence: regular scans aligned with asset criticality. For example, high‑risk external systems weekly; moderate-risk systems monthly; low-risk systems quarterly. Document deviations and justifications.
- Clear ownership and accountability: each finding assigned to an asset owner or remediation team. Escalation paths defined for overdue items. Management oversight to enforce deadlines.
- Integration with incident response processes: vulnerabilities that are exploited or actively targeted should trigger incident response. Tie vulnerability management to incident response plans and runbooks.
- Evidence of security awareness: technical teams should receive training on patching, secure configuration, and vulnerability exploitation trends. Security awareness programmes help reduce human errors and misconfigurations.
- Governance oversight and periodic reviews: management reviews should include metrics on open vulnerabilities, remediation performance, and recurring patterns. Internal audits or compliance reviews should test the effectiveness of the programme and recommend improvements.
Konfirmity’s audits show that organizations with defined cadences, clear accountability, and integrated processes have fewer findings and shorter remediation times. Conversely, those treating vulnerability management as a one‑off task face repeated non‑conformities.
Common Mistakes That Cause Audit Friction
Even well‑intentioned programmes stumble on common pitfalls:
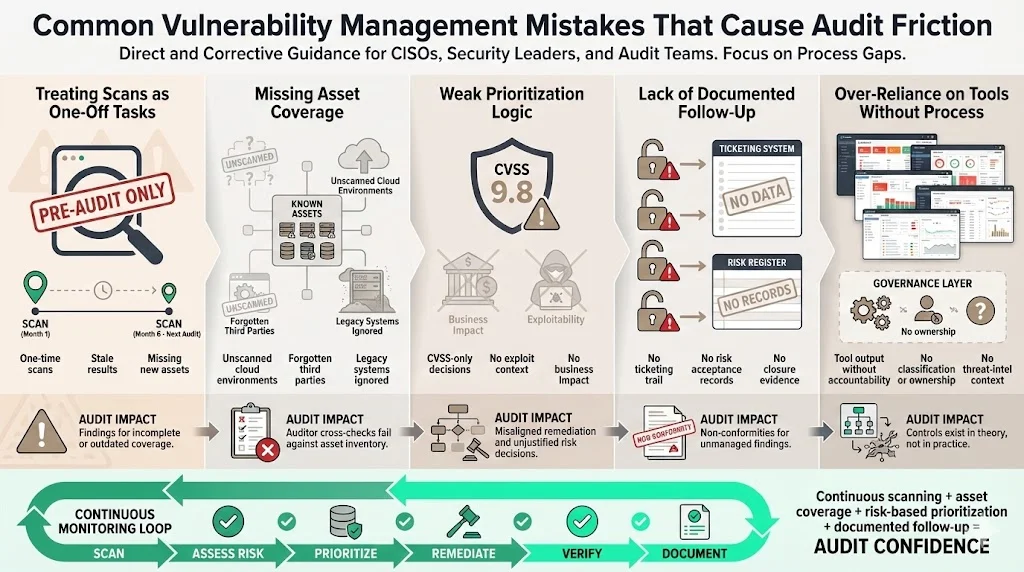
- Treating scans as one‑off tasks: vulnerability management is continuous. Organizations that run a single scan before the audit often face findings for missing coverage or stale data. Continuous scanning and monitoring are essential.
- Missing asset coverage: failing to scan all systems leads to blind spots. Common omissions include cloud accounts, third‑party integrations, and legacy systems. Auditors cross‑check asset inventories against scan reports to confirm coverage.
- Weak prioritization logic: using CVSS alone without considering exploitability or business impact results in misaligned remediation. Auditors expect a documented risk-based model.
- Lack of documented follow‑up: unresolved findings without justification lead to non‑conformities. A clear ticketing process and vulnerability register prevent this.
- Over‑reliance on tools without process: tools generate data, but without governance, classification, and accountability they become noise. Manual testing and threat intelligence remain critical.
Learning from these mistakes and embedding continuous monitoring leads to smoother audits and more credible security posture.
How Vulnerability Management Impacts Enterprise Sales
Enterprise buyers ask detailed questions about vulnerability handling because it reflects whether a vendor can protect their data. Security questionnaires often include sections on vulnerability scanning, patch management, penetration testing, and incident response. Vendors that provide audit-ready documentation—policies, registers, scan reports, and evidence of remediation—shorten procurement cycles. In SOC 2 conversations, the absence of credible evidence can stall deals for months. Conversely, handing over a current SOC 2 Type II report or ISO 27001 certificate signals operational maturity and reduces buyer friction.
ISO 27001 vulnerability management programs build trust by demonstrating that vulnerabilities are identified, prioritized, and resolved according to risk. Buyers may ask about scan cadences, patch SLAs, risk acceptance procedures, and continuous monitoring. Showing risk‑based prioritization and documented exceptions reassures customers that critical vulnerabilities will not linger. In regulated industries like healthcare and finance, patching timelines may be contractual; failure to meet them can result in penalties or lost deals. Konfirmity’s clients often report that they close enterprise deals 30–50% faster once they adopt a structured vulnerability program and can answer questionnaires confidently. Our “human‑led, managed security and compliance” approach provides dedicated experts who implement controls, operate them daily, and prepare evidence so that teams spend roughly 75 hours/year on compliance instead of 550–600 hours when self-managed. Typical ISO 27001 or SOC 2 readiness with Konfirmity takes 4–5 months, compared to 9–12 months in traditional self-service models. The difference lies in implementing real security controls—not just generating artifacts—and providing continuous evidence that stands up to auditors, buyers, and attackers.
Conclusion
Vulnerability management is not a checkbox; it is a continuous discipline that reduces business risk and accelerates enterprise sales. ISO 27001 requires organizations to obtain vulnerability information, evaluate exposure, and address risk through a structured, risk-based process. Effective programmes start with a complete asset inventory, use multiple identification methods, prioritize based on business impact and exploitability, and track remediation through defined workflows. Verification and continuous monitoring close the loop. Policies and templates provide structure, but leadership support and day‑to‑day practices make the difference. Investing in a human‑led, managed security programme pays dividends: fewer audit findings, faster buyer approvals, and better resilience against real threats. Security that reads well in documents but fails in practice is a liability. Build the programme once, operate it daily, and let compliance follow.
Frequently Asked Questions
1. What does ISO 27001 require for vulnerability management?
ISO 27001 requires organizations to obtain information about technical vulnerabilities, assess their exposure, and address risk in a timely manner. Control A.8.8 mandates a risk‑based, documented process with defined roles, treatment timelines, and evidence. The process must integrate with risk assessment, asset management, incident response, and continual improvement.
2. How often should vulnerability scans run?
Auditors expect regular scanning based on asset criticality. High‑risk internet‑facing systems are often scanned weekly; internal systems monthly; low‑risk systems quarterly. Significant changes (e.g., new deployments, major upgrades) should trigger ad‑hoc scans. Continuous monitoring and threat intelligence help adjust frequencies when new exploits emerge.
3. Is penetration testing mandatory?
ISO 27001 does not explicitly mandate penetration testing, but auditors often expect it for high-risk or customer-facing systems, especially when SOC 2, HIPAA, or contractual clauses require it. Pen tests complement automated scanning by uncovering complex vulnerabilities and verifying controls. A well‑designed program combines automated scanning, manual testing, and threat intelligence.
4. What evidence do auditors ask for?
Auditors typically review vulnerability management policies, asset inventories, scan reports, vulnerability registers, change tickets, and risk acceptance documentation. They look for evidence of identification, prioritization, treatment, verification, and continuous improvement. Clear documentation and audit trails simplify reviews.
5. How are vulnerabilities prioritized?
Prioritization combines severity (CVSS), exploitability, asset criticality, and business impact. Models like FAIR can quantify potential financial or operational impact. Risk-based prioritization helps allocate resources effectively and demonstrates to auditors that critical issues are addressed promptly.





.svg)





.svg)
.svg)