Most enterprise buyers now request evidence of security controls and compliance before they even consider a vendor. Deals stall if teams treat security as an after‑thought. Modern procurement questionnaires ask for ISO 27001 certificates, penetration‑test reports, HIPAA Business Associate Agreements, SOC 2 Type II attestation, data‑protection addenda and the details behind your access controls, logging and supplier oversight. Paper promises don’t satisfy seasoned auditors, and a breach can cost millions. IBM’s 2025 Cost of a Data Breach report found that the global average cost of a breach was USD 4.44 million. Customers have little tolerance for “trust us” statements; they want proof that you operate securely and continuously. Combining ISO 27001 with the Zero Trust security model offers a structured, risk‑based way to deliver that assurance.
This article, written from the perspective of Konfirmity’s founder after supporting over 6,000 audits, explains how ISO 27001 and Zero Trust complement each other. You’ll learn practical steps, ready‑made templates and real‑world examples to help busy engineering and security leaders build an audit‑ready program without endless spreadsheets or naïve “tick‑box” tooling. Our goal is to show how to start with security and arrive at compliance, not the other way around.
What Is ISO 27001 & Why It Matters to Enterprise‑Selling Companies
ISO / IEC 27001 is the leading international standard for information security management systems (ISMS). Published jointly by the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC), it defines requirements for establishing, implementing, maintaining and continuously improving an ISMS. An organisation certified to ISO 27001 has adopted policies, procedures and technical and physical controls to protect data across paper, digital and cloud environments. The standard enshrines the classic confidentiality‑integrity‑availability triad: it requires that information assets are kept confidential, remain accurate and available to authorised users. An effective ISMS covers people, processes, technologies and physical facilities, not just IT systems.
For companies that sell to enterprise or regulated clients, ISO 27001 carries tangible business value:
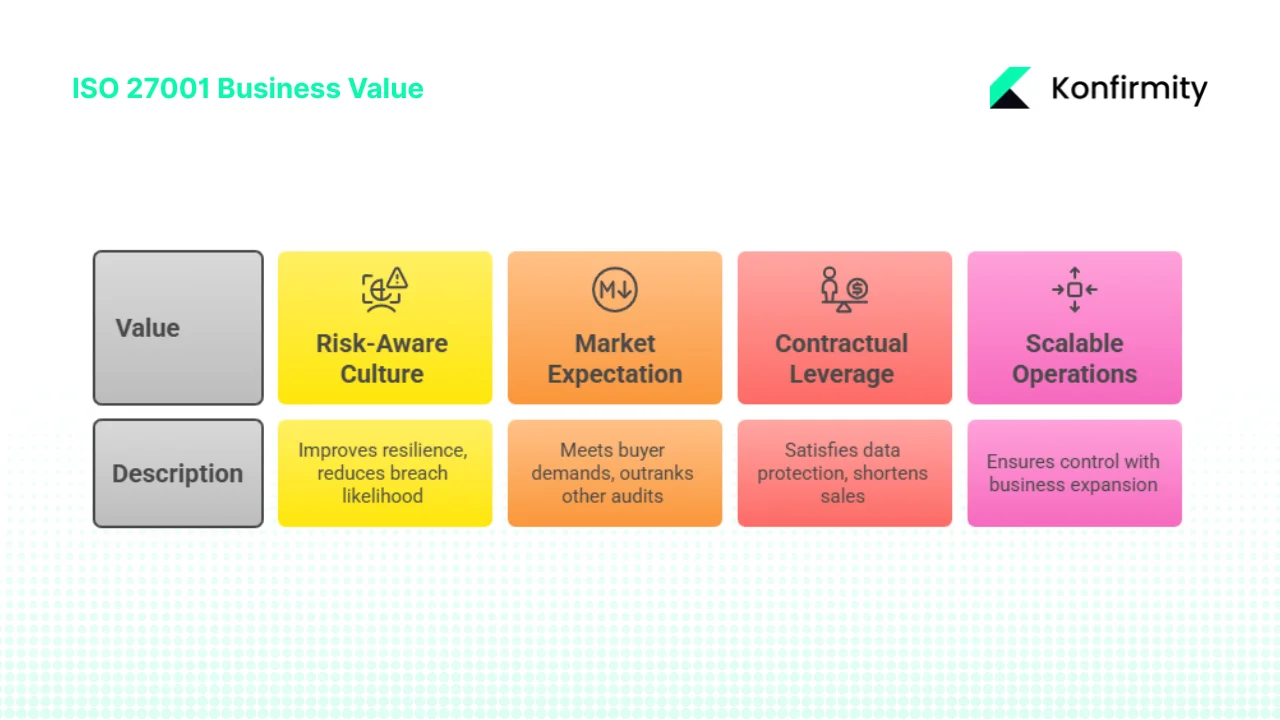
- Risk‑aware culture and governance. ISO 27001 forces executives and engineers to document scope, perform risk assessments, implement controls, and monitor effectiveness. These disciplines improve operational resilience and reduce the likelihood of costly breaches. IBM’s report underscores the stakes: breaches with non‑compliance factors cost more on average.
- Market expectation. Enterprise buyers increasingly expect ISO 27001 alongside SOC 2, HIPAA or GDPR readiness. NAVEX’s 2025 benchmark showed that 81% of organisations report current or planned ISO 27001 certification in 2025 (up from 67% in 2024). For many procurement teams, ISO 27001 or SOC 1 now outrank SOC 2 as the most important audit.
- Contractual and regulatory leverage. The ISMS framework satisfies data‑protection clauses in DPAs and BAAs, demonstrates reasonable security controls under HIPAA, and complements statutory requirements under GDPR or India’s DPDP Act. Vendors with ISO certification answer security questionnaires faster and shorten sales cycles.
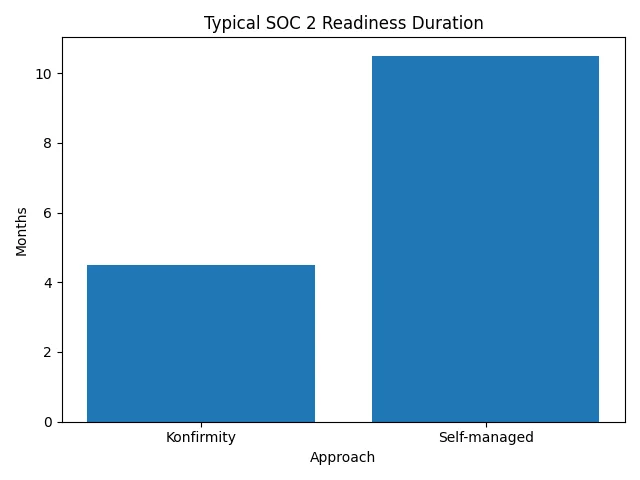
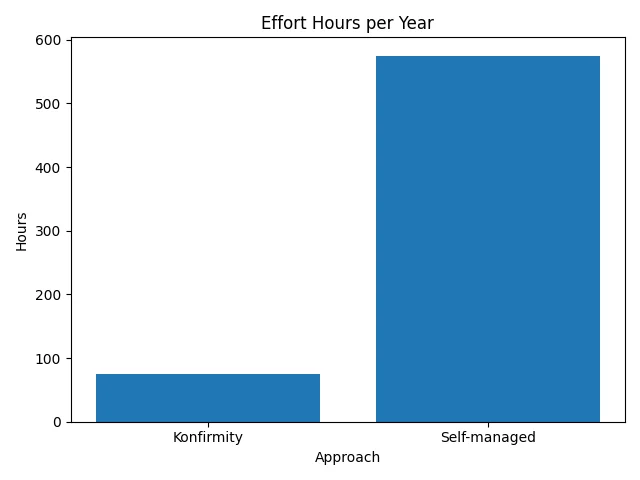
- Scalable operations. ISO 27001 emphasises continuous improvement. As your business expands across new regions or services, the ISMS ensures control of scale with growth. Konfirmity’s data shows that, with a managed program, typical SOC 2 or ISO 27001 readiness can be achieved in 4–5 months rather than the 9–12 months often observed when teams DIY the process. Similarly, ongoing evidence collection can take 75 hours per year with our managed service versus 550–600 hours for self‑managed programs.
Key Components & Structure of ISO 27001
ISO 27001:2022 is structured into 11 clauses and Annex A. Clauses 0–3 provide context and definitions. Clauses 4–10 are mandatory; they outline the management‑system requirements every certified organisation must implement. Understanding these clauses is crucial for designing an ISMS:
Annex A provides a catalogue of 93 security controls grouped into four domains: organizational, people, physical and technological. Organisational controls (37) include policies, responsibilities, threat intelligence and asset management. People controls (8) cover hiring, training, NDAs, remote working and incident reporting. Physical controls (14) deal with secure areas, equipment protection and supporting utilities. Technological controls (34) cover malware protection, logging, network segregation and secure development. During implementation you select relevant Annex A controls based on risk assessment and justify any exclusions in the Statement of Applicability.
What ISO 27001 Certification Means for Your Business
Achieving ISO 27001 certification demonstrates to customers and regulators that your organisation has a systematically managed security programme. Certification signals commitment to protecting sensitive data, builds trust with enterprise clients and supports due‑diligence processes. It helps satisfy contractual and regulatory requirements under HIPAA, GDPR or India’s DPDP Act, and reduces the burden of answering detailed security questionnaires. For scale‑ups and SaaS providers, ISO certification enables faster expansion into regulated industries and international markets. Importantly, certification is not a one‑time task. After the initial audit, your organisation undergoes annual surveillance audits and recertification every three years. This cadence ensures the ISMS remains effective and that non‑conformities are addressed. Konfirmity’s experience shows that organisations with a managed program see fewer audit findings and shorter sales cycles because evidence is continuously maintained.
What Is Zero Trust and Why It Complements ISO 27001
Zero Trust Security Model — Core Idea
The Zero Trust paradigm shifts security from a perimeter‑centred model to one that assumes no implicit trust. According to NIST SP 800‑207, zero trust treats every user and device as untrusted until verified, regardless of whether they are inside or outside the network. It focuses on protecting resources (assets, services and workflows) rather than networks. Key tenets include:
- Secure communication regardless of location. All communication must be encrypted and authenticated; network location alone should not imply trust.
- Per‑session access with least privilege. Access to individual resources is granted on a per‑session basis, with the least privileges necessary and continuous evaluation of identity and device posture.
- Dynamic policy decisions. Access decisions consider user identity, device state, behaviour patterns and environmental attributes; policies adapt to risk levels.
- Continuous monitoring and enforcement. The enterprise monitors all assets and enforces dynamic authentication and authorization for each request. MFA, device compliance checks and micro‑segmentation are expected measures.
Why Traditional Perimeter‑Based Security Falls Short
Historically, corporate networks relied on VPNs and firewalls to establish a trusted perimeter. Once users were “inside,” lateral movement was largely unchecked. Today’s realities—remote work, SaaS adoption, bringing‑your‑own‑device policies and complex supply chains—render this model obsolete. As NIST points out, zero trust assumes attackers may already be on your network and that devices may be unmanaged or compromised. Perimeter‑centric models also fail to account for cloud workloads and APIs, making them vulnerable to credential theft and misconfigurations.
How ISO 27001 and Zero Trust Complement Each Other
ISO 27001 provides governance: it mandates risk assessment, documented policies, senior leadership involvement, internal audits and corrective actions. Zero Trust provides architecture and operational controls: micro‑segmentation, least privilege, continuous verification and device posture checks. Many Annex A controls align directly with Zero Trust, such as identity and access management, network segregation, secure configuration and monitoring. Implementing Zero Trust principles helps meet ISO 27001 requirements for access control, asset management, monitoring and ongoing improvement, while the ISMS ensures these controls are risk‑driven, documented and audit‑ready. Together, they offer a holistic, risk‑aware security posture that both satisfies auditors and thwarts real‑world threats.
Step‑by‑Step Practical Guide to Implement ISO 27001 + Zero Trust for Busy Teams
This guide draws on Konfirmity’s experience building and operating ISMS and Zero Trust programs across hundreds of SaaS and services companies. Each step maps to ISO 27001 clauses and Zero Trust principles, with templates you can adapt.
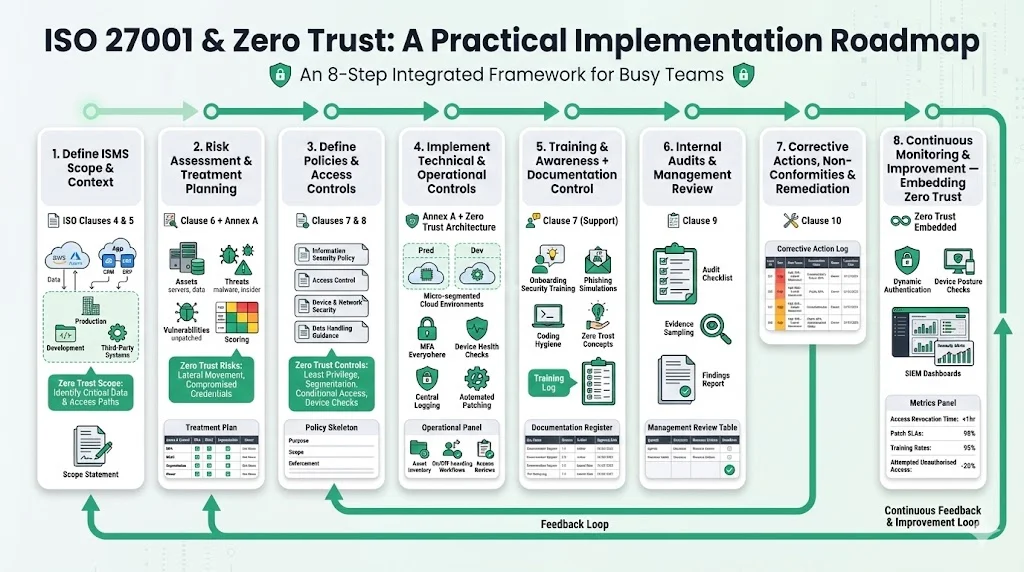
Step 1: Define ISMS Scope & Context (Clauses 4 & 5)
- Identify business units and systems. List the products, customer‑facing services, back‑office systems, cloud platforms and third‑party integrations relevant to your enterprise clients. Include data flows for customer data, internal data and sensitive intellectual property.
- Determine boundaries. Specify what parts of your business are in scope—production environments, development systems, SaaS components, on‑premise infrastructure—and justify any exclusions.
- Document scope and objectives. Create a formal scope statement and high‑level objectives for the ISMS. Align them with business strategy and regulatory obligations. This documentation is part of Clause 4 and Clause 5 requirements.
Step 2: Risk Assessment & Treatment Planning (Clause 6 + Annex A)
- Conduct a risk assessment. Identify assets (e.g., databases, APIs, laptops), threats (unauthorised access, malware, insider abuse), vulnerabilities (misconfigurations, unpatched software) and impacts (service disruption, data breach). Rate likelihood and impact to calculate risk levels.
- Align with Zero Trust. Map risks to Zero Trust concerns—lateral movement, compromised credentials, unsecured devices and cloud misconfigurations. Consider remote workers, contractors and third‑party integrations.
- Create a risk‑treatment plan. Select Annex A controls to mitigate each risk. For example, implement MFA and RBAC for the database, micro‑segment networks to prevent lateral movement and enforce device posture checks. Document residual risk and assign owners. Use a risk‑register spreadsheet with columns for asset, threat, likelihood, impact, control(s), residual risk, owner and review date. A simple example is shown below:
Step 3: Define Policies & Access Controls (Clauses 7 & 8)
- Document key policies. Draft or update your information‑security policy, access‑control policy, system and network security policies, data‑handling guidelines, remote‑access standards, device management procedures and asset‑management policy. These documents satisfy ISO 27001’s support and operation clauses and are crucial evidence for auditors.
- Implement Zero Trust controls. Enforce least privilege by assigning roles with just‑enough rights. Segment networks (production vs. development, customer data vs. internal tools). Deploy identity and access management (IAM) platforms supporting MFA, single sign‑on and device compliance checks. Use conditional access policies based on risk signals (device health, location, time of day).
- Policy template skeleton. Each policy should include purpose, scope, responsibilities, definitions, controls and enforcement. For instance, an access‑control policy might state that all users must authenticate with MFA, that privileged accounts require approval and that periodic access reviews are conducted.
Step 4: Implement Technical & Operational Controls (Annex A + Zero Trust Architecture)
- Deploy technical controls. Introduce zero‑trust network access or secure VPN solutions. Configure micro‑segmentation on your cloud network (e.g., separate VPCs or Kubernetes namespaces). Ensure all workloads and endpoints enforce MFA and device posture checks. Encrypt data at rest and in transit. Enable logging and centralised monitoring across applications, infrastructure and security tools. Adopt secure configuration baselines and automated patch management.
- Operational measures. Maintain an asset inventory with classification (e.g., confidential, restricted). Establish onboarding/off‑boarding procedures that align with least privilege and ensure deprovisioning. Define role descriptions and privileges. Perform regular access reviews and privilege audits.
- Example. A SaaS firm serving enterprise clients might isolate production workloads in a dedicated cloud account, restrict access through a zero‑trust network access service that validates user identity and device health, enforce MFA for all administrative actions, restrict database queries to customer‑success roles and log every query. The development environment cannot reach production; data pipelines are encrypted; and backups are stored in a separate account with limited access.
Step 5: Training & Awareness + Documentation Control (Clause 7 Support)
- Security awareness training. Conduct onboarding and recurring training on phishing, social engineering, secure coding, data handling, password hygiene and Zero Trust principles. Use phishing simulations and measure completion. Maintain a training schedule and attendance log.
- Competence and awareness evidence. Keep records of each employee’s training, qualifications and certifications. ISO 27001 mandates documented evidence of competence.
- Document control. Maintain a documentation register that tracks policies, procedures, change records, audit logs, risk assessments and treatment plans. Include version numbers, authors and approval dates. ISO 27001 requires documents and records to be controlled with date and revision number.
Step 6: Internal Audits & Management Review (Clause 9)
- Plan internal audits. Schedule periodic internal audits to evaluate whether controls are implemented and effective. Use an audit checklist covering each clause and relevant controls. Document findings, non‑conformities and improvement opportunities.
- Conduct management reviews. At defined intervals (often quarterly or semi‑annual), senior management should review the ISMS performance, audit results, risk status, incidents, corrective actions and resource needs. This ensures leadership commitment and informs strategic decisions.
- Templates. Use an internal audit plan with columns for clause/control, evidence required, auditor, date and status. Use management review minutes with agenda items, decisions, action items, owners and deadlines.
Step 7: Corrective Actions, Non‑Conformities & Remediation (Clause 10)
- Document non‑conformities. When internal audits or incidents reveal deviations from policies or control failures, record them with details of the issue, severity, root cause and corrective actions. Assign owners and track remediation to closure.
- Drive continual improvement. Feed lessons learned back into the risk assessment and control design. Update policies and procedures accordingly. Continuous improvement is a core requirement of ISO 27001 and helps align your security posture with emerging threats.
- Corrective action log template. Create a log with fields for non‑conformity description, severity, root cause analysis, corrective action, owner, deadline and completion date.
Step 8: Continuous Monitoring & Improvement — Embedding Zero Trust in the ISMS Lifecycle
- Regularly review risk assessments and scope. As your business evolves—new products, geographies, partnerships—update the scope and risk register. Evaluate whether new threats (e.g., AI misuse, supply‑chain attacks) require new controls.
- Continuous monitoring. Collect and analyse logs from identity providers, endpoint management, firewalls, application servers and cloud infrastructure. Use security information and event management (SIEM) tools or managed detection and response services to identify anomalies. Enforce continuous authentication and authorisation; re‑authenticate sessions based on risk signals (time, location, device posture). NIST emphasises that authentication and authorisation must be dynamic and strictly enforced before granting access.
- Improvement cycle. Use metrics—e.g., mean time to revoke access, patching SLAs, number of unauthorised access attempts, training completion rates—to measure effectiveness. Adjust policies and controls based on audit findings, incidents or changing regulatory requirements. Repeat the audit and management review cycle to ensure long‑term resilience.
Real‑World Examples & Templates
Konfirmity SaaS Provider Example
A mid‑stage SaaS company serving financial institutions approached Konfirmity to prepare for ISO 27001 certification. We scoped only production systems that stored customer data, excluding marketing tools. Our risk assessment identified threats such as privileged account misuse, API abuse and insecure CI/CD pipelines. We implemented Zero Trust micro‑segmentation between development and production, enforced MFA and device compliance on all administrative accounts, and deployed continuous log monitoring. Policies for access control, asset management and incident response were documented and approved by leadership. We ran internal audits after three months, logged non‑conformities (e.g., stale user accounts), remediated them and prepared evidence. The organisation achieved certification in five months with no major audit findings. Sales cycles shortened because procurement teams could review audit reports and policies without extended questionnaires.
Remote Consultancy Example
A professional‑services firm with consultants working from multiple countries needed to secure client data subject to GDPR and HIPAA. We scoped all workstations, collaboration tools and cloud storage. Zero Trust controls included enforcing device compliance (full‑disk encryption, endpoint detection and response), MFA on all SaaS applications, and role‑based access to client folders. Network segmentation limited access between client projects. Employees received training on privacy regulations and secure remote work practices. Internal audits uncovered issues with timely off‑boarding; a corrective‑action plan improved HR and IT coordination. The firm passed ISO 27001 and HIPAA audits and now demonstrates compliance proactively during client engagements.
Plug‑and‑Play Templates
Konfirmity provides templates that busy teams can adapt:
- Risk Register. Spreadsheet capturing asset, threat, likelihood, impact, risk level, control(s), residual risk, owner and review date (see example above).
- Policy Skeletons. Documents with placeholders for company name, scope, definitions, roles and responsibilities, controls, exceptions and enforcement. Examples include information‑security policy, access‑control policy, asset‑management policy and incident‑response plan.
- Training Schedule & Attendance Log. Tracker listing mandatory training topics (phishing, secure coding, data handling, privacy, incident reporting), dates, attendees and completion status.
- Internal Audit Checklist. Template mapping ISO 27001 clauses and Annex A controls to evidence items, audit questions, observations and status.
- Non‑Conformity Log. Register for recording issues, root causes, corrective actions, owners, deadlines and closure dates.
- Management Review Minutes. Document capturing agenda, participants, decisions, action items and deadlines.
Common Challenges, Pitfalls & How to Avoid Them
1) Complexity and bandwidth. Integrating Zero Trust architecture with ISO 27001 can feel like a second full‑time job, especially for small teams. Start with critical assets and gradually expand the scope. Use managed services or platforms to automate evidence collection and monitoring. Konfirmity reduces the burden by integrating into your tech stack and providing dedicated experts; our clients spend roughly 75 hours per year on evidence, versus 550–600 hours when self‑managed (illustrated below).
2) Resistance to change. Staff accustomed to open access may view Zero Trust as restrictive. Secure buy‑in through clear communication of benefits (reduced breach risk, smoother audits) and involve team leads early. Leadership commitment is mandatory under Clause 5dsalta.com.
3) Documentation overload. ISO 27001 requires many documents and records. Use templates and control libraries to avoid reinventing the wheel. Adopt version control and assign owners. Automate evidence capture where possible.
4) Keeping up with maintenance. Once certified, you must maintain controls, perform periodic audits and adjust to new threats. Embed the ISMS into normal operations. Assign dedicated ownership and allocate budget for ongoing monitoring, training and improvement.
Why ISO 27001 + Zero Trust Gives a Competitive Advantage in Enterprise Sales
Enterprise buyers evaluate vendors on both compliance and technical rigor. Presenting an ISO 27001 certificate alongside a mature Zero Trust architecture signals that you operate a managed, risk‑based security programme, not a “tick‑box” compliance project. It demonstrates that you have policies, governance, and continuous evidence (ISO 27001) and robust technical measures (Zero Trust) like micro‑segmentation, MFA and continuous monitoring. This dual assurance addresses both legal obligations and real‑world threat mitigation. It also reduces the risk of breaches—which now average USD 4.44 million globally—and minimises the time buyers spend on due diligence. Vendors that invest in these programs close deals faster, command higher trust and can enter regulated markets more easily.
Conclusion
ISO 27001 and Zero Trust are complementary frameworks for building a resilient, audit‑ready security posture. ISO 27001 provides governance, risk management, documentation and continual improvement, while Zero Trust delivers technical controls and a mindset that assumes breaches are inevitable and trust must be earned each time. Together, they enable organisations to protect data, satisfy regulators and accelerate enterprise sales. For busy teams, the path to certification doesn’t have to be daunting. Use templates, phased rollouts and dedicated experts to build controls inside your stack, monitor them continuously and feed improvements back into your ISMS. Security that reads well but fails under incident pressure is risky; build your program once, operate it every day, and let compliance follow.
FAQs
1) What is the ISO standard for Zero Trust?
There is no separate ISO standard named “Zero Trust.” The Zero Trust paradigm is described by NIST SP 800‑207, which defines zero trust as the shift from implicit trust in network perimeters to continuous verification of users and devices. Organisations implement Zero Trust principles using frameworks like ISO 27001:2022, which already require risk‑based management, access control, continuous monitoring and improvement.
2) What are the four categories of ISO 27001 controls?
Annex A of ISO 27001:2022 comprises 93 controls grouped into four domains: organisational controls (37 controls) covering policies, responsibilities, threat intelligence and asset management; people controls (8 controls) covering pre‑employment screening, training, NDAs, remote working and event reporting; physical controls (14 controls) covering secure areas, clear desks, secure cabling and equipment maintenance; and technological controls (34 controls) covering malware protection, backups, logging, network segregation and secure development.
3) What is Zero Trust in cybersecurity?
Zero Trust is a security architecture and mindset that assumes no implicit trust. Every access request is authenticated and authorised based on user identity, device posture and context before being granted. Access is granted only with the least privileges necessary, sessions are continuously verified and networks are micro‑segmented to limit lateral movement. Continuous monitoring collects telemetry to adapt policies and detect anomalies.
4) Which ISO 27001 clauses are mandatory for certification?
Clauses 4 through 10 of ISO 27001 are mandatory. They cover context of the organisation (scope and interested parties), leadership (management commitment and policy), planning (risk assessment and objectives), support (resources, competence and documentation), operation (implementing controls), performance evaluation (monitoring, internal audits and management review) and improvement (handling non‑conformities and continual improvement). In addition, organisations must select and implement relevant Annex A controls based on their risk profile and justify any exclusions in the Statement of Applicability.





.svg)






.svg)
.svg)