When you're trying to sell to large companies or healthcare organisations, you quickly find that technical promises aren’t enough. Procurement teams now insist on documented assurance that you have disciplined security and privacy practices. Without that assurance, deals stall under lengthy questionnaires or die altogether. Preparing for a SOC 2 audit – and proving that you operate controls every day – can be the difference between a smooth contract and months of delay. This article explains why SOC 2 Audit Preparation matters, how to scope and execute it, and how Konfirmity’s managed approach reduces friction for you and your customers.
Why SOC 2 preparation matters when selling to enterprise customers
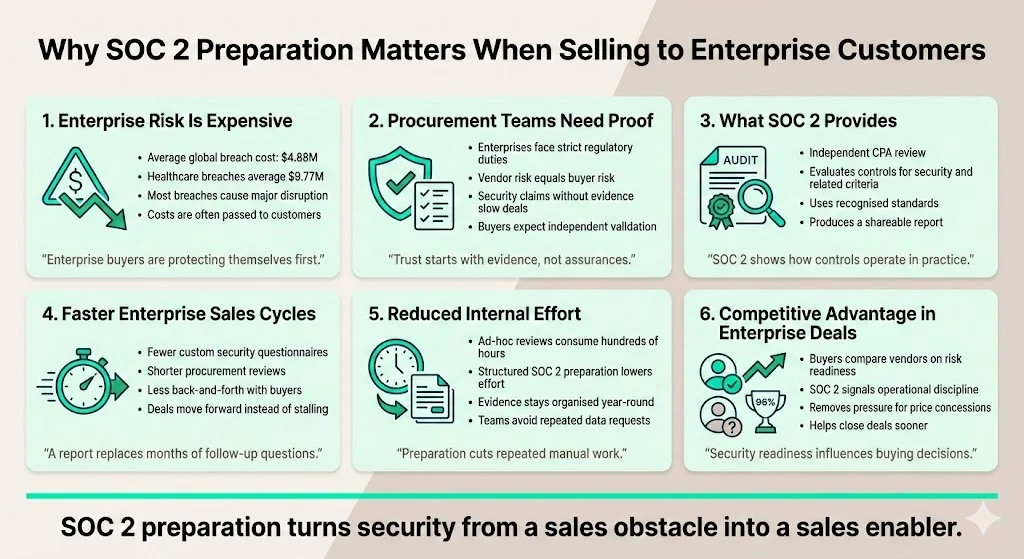
Enterprise buyers and healthcare entities face escalating attack costs and strict regulatory obligations. IBM’s 2024 Cost of a Data Breach report found the average global breach cost reached US $4.88 million, and healthcare breaches still averaged US $9.77 million despite a 10.6 percent drop from 2023. The same study reported that 70 percent of breached organisations experienced significant disruption and 63 percent passed breach costs onto customers. Faced with these numbers, enterprise procurement teams seek assurance that vendors will not expose them to additional risk.
A SOC 2 report satisfies this need because it demonstrates that an independent certified public accountant (CPA) has reviewed your control environment against recognised criteria. AuditBoard explains that SOC 2 is a “report on controls at a service organisation relevant to security, availability, processing integrity, confidentiality or privacy”. These reports let customers assess your security posture quickly instead of dragging you through bespoke questionnaires. Without a report, early‑stage companies often watch deals languish in procurement queues or face discount demands to compensate for the perceived risk.
Konfirmity has supported 6,000 + audits over 25 years. Our teams routinely see enterprises cut their security review time from months to weeks once they can share a current SOC 2 report. Instead of spending 550–600 internal hours on ad‑hoc evidence gathering, our managed service reduces that to around 75 hours spread across the year. Fewer questions and faster approvals translate into revenue realised sooner and fewer opportunities lost to competitors.
Quick clarity on SOC 2 Type I vs Type II
There are two kinds of SOC 2 reports. A Type I report evaluates the design of your controls at a single point in time. It tells customers that you have designed controls consistent with the Trust Services Criteria. However, it does not prove that those controls operate day‑to‑day. A Type II report evaluates both design and operating effectiveness over a period of time, typically three to twelve months. This observation window allows auditors to sample activities such as access reviews, incident response exercises or change‑management records to see whether you followed your own processes.
Type I is quicker to achieve but provides limited assurance. Type II takes longer because of the observation period but carries more weight with enterprise buyers. Many firms start with a Type I to satisfy initial customer requests then move to Type II the following year. Konfirmity recommends starting your SOC 2 Audit Preparation at least three months before you want your Type I report and six months before your Type II window to ensure your controls are in place before the audit window starts.
What SOC 2 is and why enterprise buyers care
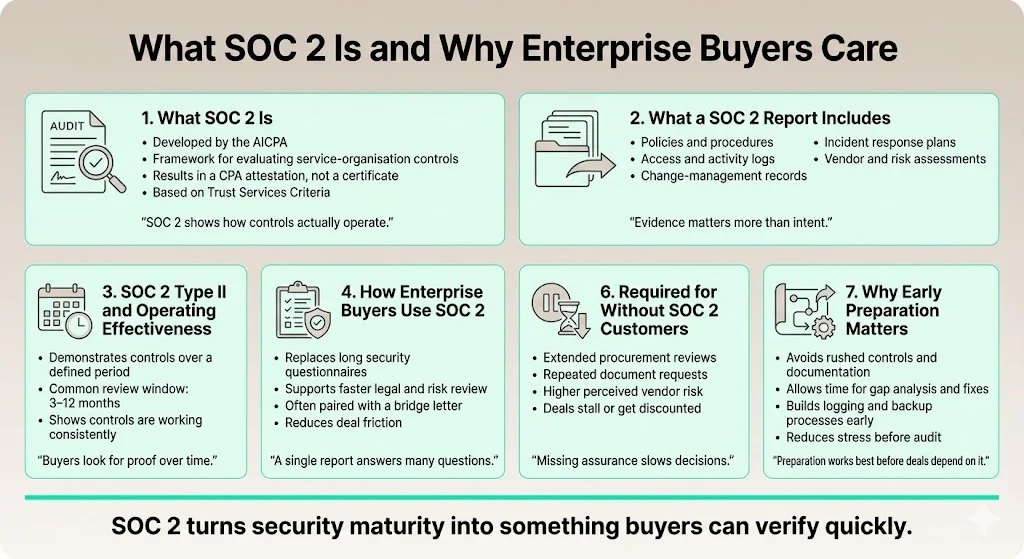
The American Institute of Certified Public Accountants (AICPA) publishes the SOC 2 framework, which comprises requirements, criteria and guidance for CPAs performing service‑organisation control audits. A SOC 2 report is not a certificate; it is an attestation by a CPA that your system and organisation controls satisfy selected Trust Services Criteria. AuditBoard points out that to receive a SOC 2 report you must provide auditors with evidence and documentation demonstrating your policies, procedures and technical measures. In practice this means access logs, change‑management records, incident response plans, vendor assessments and other artefacts.
Enterprise buyers use SOC 2 reports to streamline due‑diligence. Instead of sending lengthy security questionnaires, they ask for your report and often an accompanying “bridge letter” for periods after the report. A current Type II report showing that you operated controls over, say, a six‑month window can eliminate or reduce procurement questionnaires. Without one, procurement teams may request multiple documents and hold your deal in legal review for months. Missing or weak SOC 2 readiness is one of the most common reasons we see deals stall. It also prevents you from landing business with regulated customers like healthcare providers who are required to obtain assurances about vendors’ security practices under frameworks like HIPAA.
Early‑stage companies should begin SOC 2 Audit Preparation well before they start selling to enterprises. Building controls after a big customer demands them often leads to rushed documentation and high stress. Starting early allows you to map your product architecture, set up logging and backup processes, and document procedures without interrupting development. It also gives you time to run internal gap analyses and remediate issues before an auditor arrives.
Understanding the SOC 2 audit scope
Your audit scope defines which systems, services and data the auditors will assess. Getting the scope right is critical: over‑scoping wastes time on systems that customers never interact with; under‑scoping will trigger exceptions when buyers see that key components were excluded. In practice, scope includes the production systems that deliver your product or service, the infrastructure they run on, supporting services like identity providers, CI/CD pipelines and customer support tools, and the data flows between them.
A good starting point is to map your architecture and data flows, showing where customer data enters, how it moves through your systems, and where it is stored. Identify all third‑party services involved, such as cloud providers, payment processors, or analytics platforms. For each component, document its purpose, the data it handles, and whether it is owned by you or a vendor. This mapping helps you choose the appropriate Trust Services Criteria and ensures auditors focus on what matters to customers.
Align your scope with enterprise expectations. For example, if a customer uses your product to process personal data, they will expect you to include not only your application servers but also your storage, backups, and key vendors in scope. If you operate multiple products, decide whether to combine them in a single report or produce separate reports per product. Konfirmity helps clients right‑size their scope early, avoiding last‑minute scope changes that lengthen the audit.
The Trust Services Criteria explained
The SOC 2 framework revolves around five Trust Services Criteria defined by the AICPA:
- Security (Common Criteria) – protecting information from vulnerabilities and unauthorised access. This criterion is required in every SOC 2 report. Controls typically cover organisation structure, endpoint security, firewalls, user access, incident response and vendor management.
- Availability – ensuring systems are available for use when needed, focusing on business continuity, disaster recovery and capacity planning. Customers with zero‑downtime expectations will look for tested backup and failover procedures and clear service‑level commitments.
- Processing Integrity – verifying that systems process data completely, accurately and on time. Controls address input validation, transaction logging and monitoring to ensure that information processing supports intended outcomes.
- Confidentiality – protecting sensitive information by limiting its access, storage and use. Controls include data classification, encryption, secure deletion and contractual measures to protect intellectual property or customer secrets.
- Privacy – safeguarding personal information according to applicable laws and standards. This criterion aligns with frameworks like HIPAA and GDPR and requires controls around data minimisation, consent, notice, and breach notification.
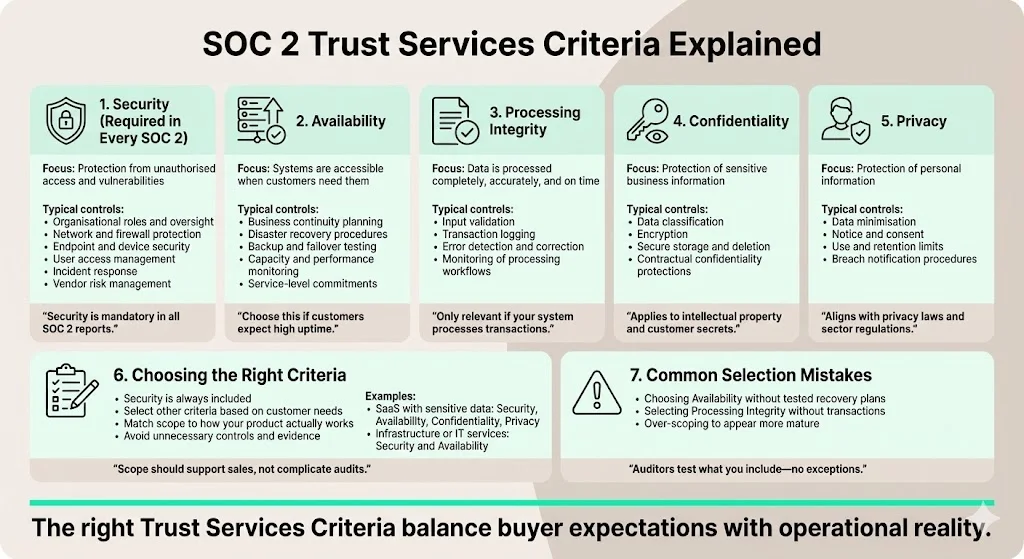
Security is mandatory; the other criteria are optional. Choose criteria based on your customers’ needs. For example, a SaaS platform storing sensitive user data and offering continuous deployment should select Security, Availability, Confidentiality and Privacy. A vendor delivering computer services might choose only Security and Availability. Avoid chasing all criteria just to look more impressive; excessive scope leads to unnecessary controls and evidence requirements. Conversely, omitting a criterion that matters to your biggest customer could result in a delayed deal. Konfirmity works with clients to prioritise criteria that will satisfy buyer demands while keeping the scope manageable.
Common mistakes include picking Availability without having tested business continuity plans, or selecting Processing Integrity when your product has no transaction processing. Auditors will test whichever criteria you include, so choose wisely.
Building strong internal and security controls
SOC 2 auditors examine both internal controls (organisational processes, policies and governance) and security controls (technical measures that secure systems and data). Internal controls demonstrate how management sets expectations, segregates duties, approves changes and monitors performance. Security controls show that you implement technical safeguards like firewalls, encryption, access control and intrusion detection.
Core areas that auditors review include:
- Access control – ensuring that only authorised personnel can access systems and data. Controls include role‑based access, single sign‑on, multi‑factor authentication, periodic access reviews, and termination procedures. Auditors look for documented access review schedules and evidence that former employees’ accounts are promptly removed.
- Network security – protecting networks through segmentation, firewalls, intrusion detection/prevention systems and secure configuration management. Evidence might include firewall rules, network diagrams, penetration test results and vulnerability management reports.
- Data protection – encrypting data at rest and in transit, managing encryption keys, performing regular backups and secure deletion, and maintaining retention schedules. Demonstrate that backups are tested and that encryption meets industry standards.
- Monitoring and logging – collecting logs from critical systems, centralising them, and monitoring for anomalous activity. Show that logs are immutable, retained for an appropriate period, and reviewed regularly.
- Incident response – having a documented plan for detecting, triaging, containing and eradicating incidents, with defined roles and communication pathways. Show evidence of tabletop exercises or actual incident reports and how lessons were integrated into process improvements.
Each control maps back to one or more Trust Services Criteria. For instance, monitoring and logging support Security (detecting unauthorised access) and Availability (detecting outages). Data protection supports Confidentiality and Privacy. Konfirmity implements these controls within our clients’ environments and operates them year‑round, rather than leaving them with a checklist.
Risk management and gap analysis
Effective risk management is the backbone of a successful SOC 2 program. The U.S. Department of Health and Human Services notes that conducting a risk analysis is the first step in identifying and implementing safeguards under the HIPAA Security Rule. The guidance emphasises that risk analysis is foundational and must account for an organisation’s size, complexity and environment. SOC 2 is not prescriptive about risk methodology either, but auditors expect to see a structured process that identifies potential threats and vulnerabilities, evaluates their likelihood and impact, and prioritises treatment.
Running a practical gap analysis helps translate risk findings into action. Start by listing each Trust Services Criteria you have selected and the controls you believe satisfy them. Then test whether those controls exist, are documented, and operate consistently. Identify gaps where controls are missing, informal or poorly documented. For example, you might discover that your change‑management process is informal, or that you lack evidence of quarterly access reviews. Prioritise gaps based on their impact on security and on your ability to demonstrate compliance. High‑impact gaps – such as lacking encryption for backups or not conducting security training – should be addressed immediately. Lower‑impact gaps can be scheduled for later sprints.
Konfirmity uses a risk‑based approach: we rank risks using a common vulnerability scoring system (CVSS) to ensure that remediation aligns with the likelihood and impact of threats. Our clients typically complete remediation in 4–5 months for their first audit cycle, compared with 9–12 months when handled internally. We also use integrated ticketing and dashboards to track remediation tasks and evidence collection, ensuring nothing is missed.
Policy and process documentation
Auditors care about documentation because they cannot rely on verbal assurances. Written policies and procedures demonstrate management intent and provide a baseline for evaluating whether controls are designed correctly. Required IT security policies usually include information security, acceptable use, access control, incident response, change management, vendor management, and disaster recovery. For each policy, include objectives, scope, responsibilities and specific procedures. Avoid copying templates verbatim; instead, adjust them to fit your organisation’s technology and risk profile.
Process documentation must reflect reality. If your access control policy requires quarterly reviews, maintain records showing each review date, who performed it, and the results. For change management, keep a log of change requests, approvals, deployments and rollbacks. If you use infrastructure‑as‑code, include pull requests and pipeline runs as evidence. Auditors may sample random changes from the observation window and ask for corresponding tickets, approvals and test results.
Clear and current documentation also helps your team operate effectively. Use concise language, define acronyms, and keep documents easily accessible. Review policies annually or after major changes. Konfirmity provides policy templates tailored to your technology stack and ensures that they evolve alongside your systems.
Control testing and evidence collection
During the audit, auditors test both the design and the operating effectiveness of controls. Design testing answers “does the control exist and is it suitable for the objective?” Operating effectiveness testing answers “did the control work consistently during the audit period?” For Type I, only design is tested; for Type II, both are tested across the observation window.
Evidence examples include:
- Access review logs – lists of active accounts, reviewers’ sign‑off, and actions taken, proving that user access is reviewed and adjusted.
- Change‑management tickets – showing that changes are documented, approved, tested and deployed according to policy.
- Monitoring alerts and incident reports – demonstrating that incidents were detected, triaged and resolved, and that lessons were captured.
- Backup and recovery test results – evidence that backups are taken, stored securely and can be restored.
- Vendor assessments – reports or questionnaires showing that you evaluated your vendors’ security posture and addressed any gaps.
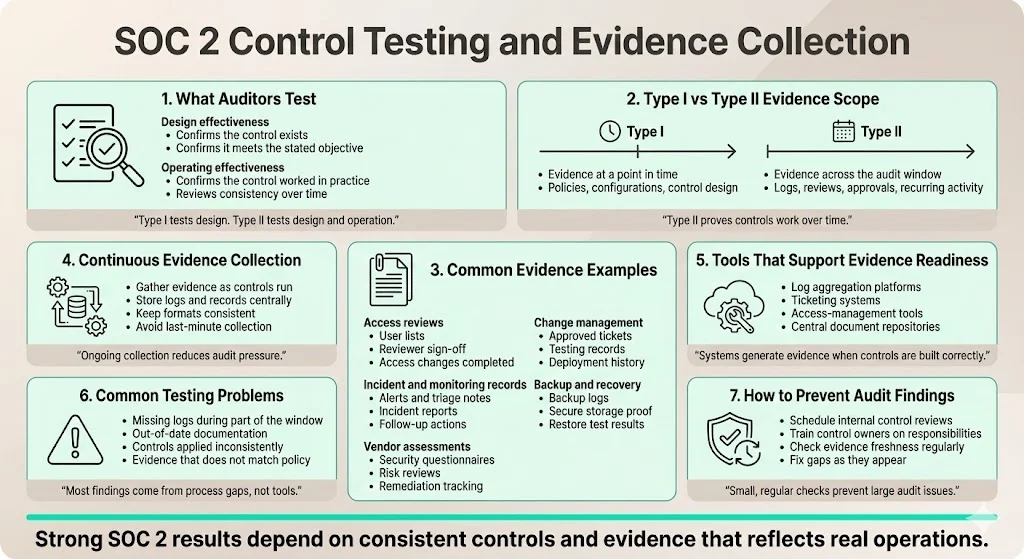
Organise evidence continuously rather than scrambling before the audit. Tools like log aggregators, ticketing systems and document repositories help. Konfirmity implements automated evidence collection: our agents pull logs and configuration data from infrastructure in real time, store them in audit‑friendly formats, and surface exceptions for remediation. This reduces last‑minute stress and ensures that evidence reflects actual operations.
Common testing issues include stale evidence (e.g., missing logs for part of the window), incomplete documentation, and inconsistent processes. Address these by scheduling regular internal audits and by training control owners on their responsibilities.
Employee training and security awareness
Employee behaviour has a direct effect on audit outcomes and real‑world security. Breaches often start with compromised credentials or phishing. The HIPAA Journal article cited earlier notes that human factors like staffing shortages and training gaps contribute significantly to breach costs. Auditors expect to see ongoing training covering topics such as secure coding, access control, incident reporting, phishing awareness, privacy principles and regulatory obligations.
Training should be tailored to different roles. Engineers need guidance on secure development practices, vulnerability remediation and infrastructure hardening. Support teams should know how to handle sensitive customer data and recognise social engineering. Sales and marketing should understand how to collect and store personal information lawfully and how to respond to security inquiries without making unsubstantiated statements.
Track completion of training and include records in your evidence. Many organisations use a learning management system (LMS) to assign courses, send reminders and record scores. Keep training content up to date with emerging threats and include refresher sessions annually or when significant changes occur. Konfirmity includes security awareness training as part of our managed service and ties course completion records directly into the audit evidence repository.
Vendor assessment and third‑party risk
Modern software companies depend on a chain of cloud services and third‑party tools. Each vendor introduces potential vulnerabilities and compliance obligations. TrustNet emphasises that vendor risk management is critical to SOC 2 compliance because a breach at a vendor can compromise your data. Buyers know this; they will ask how you evaluate and monitor your vendors.
Identify which vendors are in scope for your audit by mapping your data flows. If a vendor processes or stores customer data, provide evidence of their security posture. Acceptable evidence includes their own SOC 2 Type II report, ISO 27001 certificate, or security questionnaire responses. Review these documents at least annually and track any exceptions. For high‑risk vendors, perform deeper assessments or request remediation actions. Maintain a vendor list with contract dates, data types processed, and the security artefacts you’ve collected.
Shared responsibility is often overlooked. If you host on a cloud provider, understand which controls are your responsibility and which are the provider’s. Document how you ensure the provider meets its obligations. Keep vendor assessment records audit‑ready by storing them in a central repository with renewal reminders. Konfirmity’s service includes vendor assessment workflows integrated with our risk management platform.
Preparing for the auditor review
Auditors perform a readiness review before fieldwork begins. They evaluate whether your policies and controls are properly documented, whether you’ve collected sufficient evidence, and whether your scope and criteria are appropriate. Conduct internal walkthroughs of each control to ensure that owners know their processes and can produce evidence on demand. Mock reviews simulate the questions auditors will ask and highlight gaps.
Align your teams before the audit starts. Communicate the timeline, responsibilities and expectations. Ensure that engineering knows when the auditors will need access to logs, that HR knows how to prove employee onboarding and off‑boarding procedures, and that leadership is available for interviews. Clear communication with auditors is essential: answer questions candidly, provide requested documentation promptly and avoid trying to hide issues. Auditors are partners in improving your security posture.
SOC 2 audit timeline and expectations
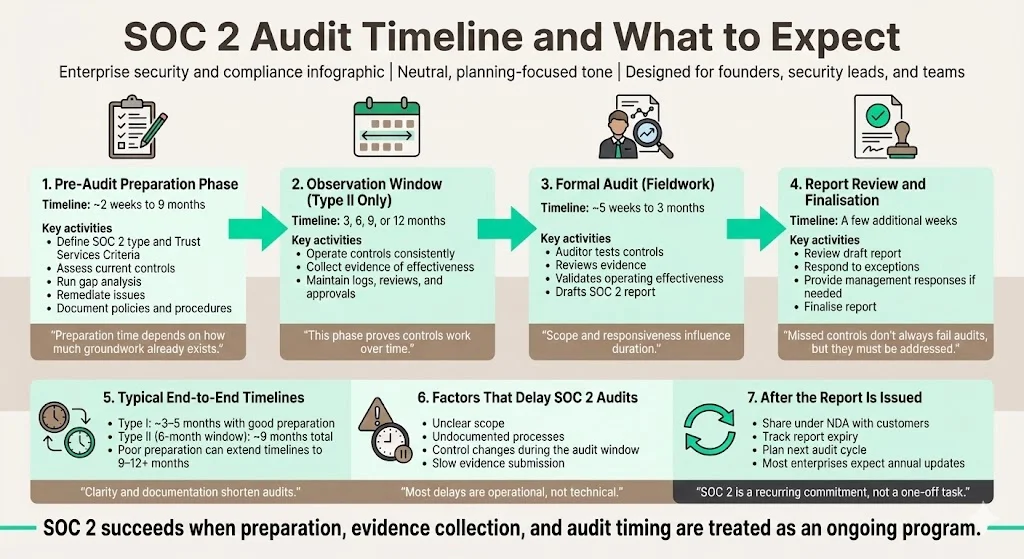
The pre‑audit phase of a SOC 2 program can range from two weeks to nine months depending on how much groundwork you have already done. During this phase you define your report type and criteria, assess your current state, conduct a gap analysis and remediate issues. For a Type II report you then enter an audit window of three, six, nine or twelve months during which you collect evidence of operating effectiveness. Finally, the formal audit phase lasts one to three months, during which auditors test your controls and draft the report. The actual audit typically takes five weeks to three months, depending on scope and number of controls.
These timelines vary widely. A small company with simple services and good preparation might complete a Type I report within three months. A Type II report with a six‑month observation window might take nine months end‑to‑end. Factors that extend audits include unclear scope, undocumented processes, changes in systems during the window, or delays in providing evidence. Automating evidence collection and maintaining documentation reduces these delays.
Konfirmity clients typically achieve Type I readiness in 4–5 months and Type II readiness in 6–7 months because we start implementation early and run continuous monitoring. Our managed model means the same experts who design your controls also operate them, so there’s no hand‑off risk. Compared with self‑managed efforts that often stretch to 9–12 months, this saves both time and internal effort. We engage CPAs who are experienced in auditing cloud‑native companies and coordinate the engagement schedule so that fieldwork does not collide with product releases.
After fieldwork, expect a few weeks for the auditor to draft the report and for you to review it. If exceptions are found – for example, if a quarterly access review was missed – you will have an opportunity to provide management responses or evidence of remediation. Once final, the report can be shared with customers under a nondisclosure agreement. Keep track of your report expiry and plan the next audit cycle accordingly; many customers require updated reports every twelve months.
Post‑audit actions and continuous compliance
Passing the audit is not the end of the road. Review any findings and implement corrective actions promptly. Use the audit as feedback to improve your controls, policies and documentation. For example, if the auditor notes inconsistent change‑management records, revise your processes and train staff accordingly. Document your remediation and include it in the next audit.
Continuous compliance means operating your controls every day, not just before the audit. Maintain regular access reviews, vulnerability scans and incident response drills. Monitor logs continuously and investigate anomalies. Keep policies updated and ensure new systems go through the same control design and documentation process. Use your SOC 2 report actively in sales cycles: create a trust portal where customers can request the report under NDA, include a summary of your controls on your website, and train your sales team to answer security questions accurately. A current, unqualified Type II report often shortens procurement cycles drastically.
Conclusion: security is a business decision
SOC 2 Audit Preparation is not a paperwork exercise; it is a business decision. With breach costs rising and customers demanding assurance, you must build real controls that operate under pressure. A report that looks good on paper but fails to withstand an incident will do little to protect your customers or your reputation. Start by implementing the right controls inside your technology stack, conduct a risk‑based gap analysis, document your processes, test continuously and involve your vendors.
Konfirmity’s human‑led, managed security and compliance service delivers outcomes rather than checklists. We build and operate your program, monitor controls year‑round, gather evidence automatically, and coordinate audits so that you stay focused on your product. Our clients experience shorter sales cycles, fewer audit findings and the ability to reuse controls across SOC 2, ISO 27001, HIPAA and GDPR. Build the program once, operate it daily, and let compliance follow.
FAQs
1. How do you prepare for a SOC 2 audit?
Start by defining your audit scope and selecting the Trust Services Criteria relevant to your product. Document your policies and processes, implement technical and organisational controls, run a gap analysis to identify weaknesses, remediate those gaps, and collect evidence as you operate the controls. Conduct mock audits and ensure your team is ready for the auditor’s questions. Konfirmity’s managed service accelerates this work by providing templates, implementing controls and automating evidence collection.
2. What are the requirements for a SOC 2 audit?
You need documented security controls aligned with the Trust Services Criteria, covering areas like access management, change management, data protection, logging and incident response. You must maintain policies and procedures, show evidence that controls operate effectively over the observation period, demonstrate risk management and vendor oversight, and provide documentation of management’s assertion and system description.
3. What are the five criteria for SOC 2?
Security is mandatory in every SOC 2 audit; the other criteria – Availability, Processing Integrity, Confidentiality and Privacy – are optional and selected based on customer needs. Each criterion focuses on a different aspect of trust, from protecting information to ensuring systems are available, accurate, confidential and compliant with privacy laws.
4. How long does a SOC 2 audit take?
The pre‑audit phase can range from two weeks to nine months, the audit window (for Type II) can be three to twelve months, and the formal audit phase typically lasts one to three months, making the entire process five weeks to three months of auditor involvement. The total timeline depends on your scope, chosen criteria and how prepared you are before fieldwork.





.svg)






.svg)
.svg)