Most enterprise buyers now ask for evidence of strong internal controls before they let a new provider into their environment. Security questionnaires, business associate agreements, data protection addenda and detailed audit reports come before purchase orders. Without operational security and continuous evidence, deals stall even when teams think they are ready on paper. This SOC 2 Budgeting Guide shows technical and business leaders how to plan for a SOC 2 program, what drives costs, and how to allocate resources without surprises.
What SOC 2 Is and Why It Matters?
Service Organization Control 2 (SOC 2) is an attestation report on controls at a service organization relevant to security, availability, processing integrity, confidentiality or privacy. A SOC 2 report is provided to third parties as proof that a company’s internal controls meet the requirements of the American Institute of Certified Public Accountants (AICPA). It is not a certification; rather, a licensed CPA firm examines your controls and issues an opinion. The report covers the controls that protect data when it is stored, processed or transmitted for customers. A SOC 2 attestation is voluntary, but most SaaS providers and cloud service organizations working with regulated industries must provide it to demonstrate a mature control environment. Failing to meet these expectations can lead to longer procurement cycles, repeated audits and a loss of trust.

The SOC 2 framework includes five Trust Services Criteria (TSC) published by AICPA: Security (common criteria), Availability, Processing Integrity, Confidentiality and Privacy. Security is always required; the other criteria are optional and are added based on business needs. The TSC maps directly to internal control objectives, such as risk management, change management, logical and physical access, system operations and vendor oversight. By choosing which criteria apply to your service, you define the scope of the audit and, by extension, the budget. Including Confidentiality or Privacy, for example, adds requirements for encryption, data classification and third‑party privacy commitments. Defining scope early prevents scope creep and sets a clear baseline for resourcing.
Why Does Budgeting Matters?
Complying with SOC 2 is not cheap. The direct audit fee is only one piece of the puzzle. Organizations also spend on readiness assessments, remediation projects, new tools, continuous monitoring, penetration testing, vendor due‑diligence and internal staff time. Bright Defense estimates that small to medium businesses spend $20,000–$50,000 for a SOC 2 audit alone, while larger organizations can spend $100,000 or more. Drata notes that a Type I audit for a small to midsize company costs $7,500–$15,000, rising to $60,000 or more for large companies, while Type II audits start around $12,000 and can exceed $100,000. Preparation, remediation and ongoing maintenance can double those figures. Internal resources often invest hundreds of hours collecting evidence, responding to auditor queries and updating policies. Hidden costs such as lost engineering productivity and delayed sales need to be factored in as well.
Effective budgeting serves three purposes. First, it aligns security and compliance goals with business strategy. Organizations that tie SOC 2 spending to risk management and IT governance can prioritize controls that matter most and avoid waste. Second, it reduces the chance of last‑minute surprises that derail audits or sales deals. A well‑planned SOC 2 Budgeting Guide accounts for readiness assessments, remediation projects, tools, audit fees, vendor management and continuous monitoring. Third, it makes it easier to get executives to buyin. Finance leaders want numbers and outcomes. A thoughtful budget shows how investing in a SOC 2 program reduces sales friction, lowers the risk of breaches and simplifies future audits.
The Compliance and Risk Context
SOC 2 sits at the crossroads of compliance, cybersecurity and risk management. While frameworks such as ISO 27001, HIPAA and GDPR define broad governance requirements, SOC 2 translates those principles into control objectives that are understandable to enterprise buyers. The AICPA’s security criteria incorporate the Committee of Sponsoring Organizations of the Treadway Commission (COSO) principles for internal control. The criteria require that companies establish a control environment, evaluate risks, perform monitoring activities and manage change. They also require vendors and third parties to meet similar standards; the common criteria CC9.2 specifies that entities must assess and manage risks associated with vendors and business partners.
Failing to meet these requirements has tangible costs. IBM’s 2025 Cost of a Data Breach Report found that the global average cost of a data breach fell from $4.88 million in 2024 to $4.44 million in 2025, but costs in the United States hit $10.22 million—an increase of 9%. Organizations using security AI and automation cut breach lifecycles by 80 days and saved nearly $1.9 million on average, underscoring the value of continuous monitoring and evidence collection. Effective vendor management also matters. Weaknesses in vendor oversight can expose sensitive data and jeopardize service quality; the SOC 2 vendor management criteria emphasise assessing and managing risks associated with key subservice organizations.
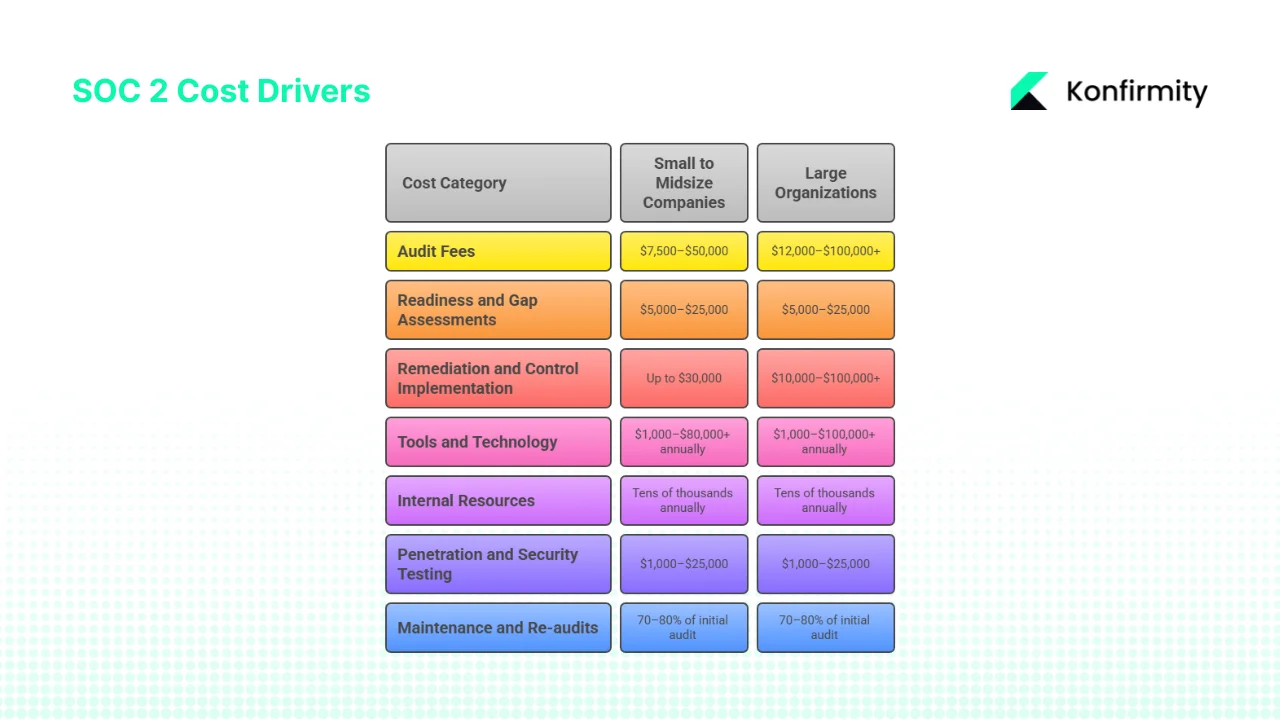
Understanding SOC 2 Cost Drivers
Budgeting for SOC 2 requires knowing where the money goes and what drives variation. The main cost categories include:
- Audit fees: Only a licensed CPA firm can issue a SOC 2 report. Drata notes that audit fees range from $7,500–$15,000 for Type I and $12,000–$20,000 for Type II for small to midsize companies, while large organizations can see fees up to $100,000. Bright Defense places SMB audit fees between $20,000 and $50,000 and large‑company fees over $100,000.
- Readiness and gap assessments: A pre‑audit gap analysis helps identify missing controls and is typically $5,000–$25,000. Consulting firms may bundle this cost with the audit.
- Remediation and control implementation: Implementing missing policies, configuring logging, enforcing multi‑factor authentication and improving access reviews can cost up to $30,000. Bright Defense notes that remediation costs range from $10,000 to $100,000+ depending on maturity.
- Tools and technology: Organizations often adopt new tools for endpoint protection, vulnerability scanning, centralized logging or mobile device management. Drata mentions that upgrades can cost $1,000–$100,000+ per year. Continuous monitoring platforms cost $5,000–$20,000+ annually. Compliance platforms like Vanta and Thoropass range from $10,000 to over $80,000 a year, excluding auditor fees.
- Internal resources: Engineering, security and operations teams invest time to collect evidence, draft policies and support audits. Bright Defense estimates 100–300+ hours of staff time per year. At a blended rate of $100/hour, that represents tens of thousands of dollars in opportunity cost.
- Penetration testing and security testing: While not always mandatory, many enterprise buyers expect an annual penetration test; costs range from $5,000–$25,000 for pen tests and $1,000–$5,000 for vulnerability scans.
- Maintenance and re‑audits: SOC 2 reports are valid for 12 months. Annual re‑audits typically cost 70–80% of the initial audit fee. Continuous monitoring and evidence collection add to recurring costs.
What drives costs upward? Choosing a Type II audit instead of Type I increases auditor time and evidence collection. Adding multiple trust services criteria—such as Availability, Confidentiality or Privacy—broadens the scope and adds controls around redundancy, encryption, data classification and privacy practices. Large organizations with multiple systems, geographies and complex technology stacks require more audit hours and more extensive evidence. Finally, control maturity matters. Organizations with few existing policies or inconsistent access reviews will spend more on remediation. Aligning controls with other frameworks such as ISO 27001 or HIPAA can increase the upfront work but may pay dividends through control reuse and reduced future audits.
Budget Ranges and Benchmarks
The table below summarizes typical budget ranges for SOC 2 programs. These ranges combine audit fees, readiness, remediation, tooling and internal effort, and they illustrate how cost increases with complexity:
These ranges are starting points, not price guarantees. Each organization’s context—industry, regulatory obligations, existing controls and risk tolerance—will influence final numbers. For example, healthcare companies handling electronic protected health information (ePHI) may need to implement HIPAA safeguards and undergo BAAs, increasing costs. Financial technology firms may map to PCI DSS. Taking a risk‑based approach and aligning scope with business drivers is essential.
Step‑by‑Step SOC 2 Budget Planning Process
Developing a SOC 2 budget involves more than picking a number. This process helps break down assumptions, allocate tasks and plan for long‑term sustainability.
- Define scope and goals: Identify the trust services criteria relevant to your business. Most start with Security and Availability; Confidentiality and Privacy may be required if you handle sensitive data. Decide whether you want a Type I or Type II report. Map the systems, data flows, and geographies in scope. Understand regulatory drivers such as HIPAA, GDPR or state privacy laws and decide whether to integrate multiple frameworks.
- Conduct a readiness assessment: Compare your current controls to the criteria. A readiness assessment or gap analysis, costing $5,000–$25,000, identifies missing policies, weak access controls, inadequate logging and gaps in incident response. Use this assessment to prioritize remediation efforts.
- Estimate cost components: Break down costs into categories—auditor fees, tools, internal labor, consulting, remediation, penetration testing and ongoing monitoring. Use worksheets with realistic ranges. For example, audit fee estimate = $12,000, tooling subscription = $15,000, internal labor = 200 hours; adjust based on your scope.
- Allocate resources and timing: Determine who will manage the program. Security leaders may own controls, while operations teams handle logging and backups. Create a timeline: 3–6 months for readiness, 6–12 months for a Type II cycle, with observation periods of at least 3 months for the first Type II.
- Build a multi‑year budget: SOC 2 is an annual commitment. Year 1 is heavy on readiness and remediation; subsequent years focus on maintenance and re‑audits. Include a contingency buffer for scope changes, vendor turnover or regulatory updates. Plan for new trust services criteria, additional regions or acquisitions.
- Select vendors and audit partners: Budget for external auditors, consultants, penetration testers and vendor risk tools. Choosing the right auditor influences both cost and timeline. Smaller CPA firms may be cheaper but may lack industry recognition; large firms may charge more but have established processes. Consider managed services like Konfirmity that bundle control implementation, continuous monitoring and audit coordination in an outcome‑as‑a‑service model.
- Monitor, review and adjust: Set quarterly checkpoints to compare actual spending against the plan. Track internal hours, consultant invoices and tool subscriptions. Adjust for scope changes, new vendors or emerging regulations. Continuous monitoring is essential; collect evidence year‑round to avoid a scramble at audit time. Link these reviews to IT governance and risk management processes to inform broader budgeting decisions.
CTA: Book a demo
Practical Examples and Templates
Scenario 1: Early‑Stage SaaS Vendor – A seed‑stage software company processes minimal personal data and needs a SOC 2 report to close its first enterprise deal. The team chooses a Type I audit covering security only. They complete a gap assessment, implement key policies (access control, change management, incident response) and use a basic compliance platform for evidence collection. Costs: $7,500–$15,000 for the audit, $5,000–$10,000 for the gap assessment, $5,000–$15,000 for remediation, $5,000–$10,000 for tools and 100 hours of internal time. Total budget $25,000–$60,000. The report is ready within three months and unlocks several new contracts.
Scenario 2: Mid‑Market Growth Vendor – A growth‑stage SaaS provider with multiple products and 200 employees targets regulated industries. They need a Type II report covering Security, Availability and Confidentiality. They allocate six months to readiness, including a detailed gap assessment and remediation of logging, access reviews and backup processes. Costs: audit fee $12,000–$70,000, readiness assessment $10,000–$25,000, remediation & tooling $20,000–$50,000, penetration testing $10,000, continuous monitoring platform $15,000, internal labor 200+ hours. Total budget $80,000–$180,000. Benefits include faster vendor onboarding, fewer security questionnaires and improved incident response.
Scenario 3: Large Enterprise Vendor – A multinational cloud provider serves thousands of customers across regulated sectors. They pursue a Type II report covering all five criteria across multiple regions. The audit involves multiple auditors, dedicated compliance teams and extensive vendor risk management. Costs: audit fee $70,000–$120,000, readiness and remediation $50,000–$200,000, tools and monitoring $50,000+, third‑party risk platform $20,000, penetration testing $25,000, internal labor 300+ hours. Total budget $250,000–$700,000+. The investment aligns with high transaction volumes and strict regulatory oversight.
For busy teams, use these templates:
- Budget worksheet: List cost categories—auditor fees, gap assessment, remediation, tools, penetration testing, consultants, internal labor, maintenance—and assign ranges. For each category, include quantity (e.g., hours) and unit cost.
- Resource allocation template: Create a matrix of tasks vs roles (security, engineering, operations, compliance, finance). Assign hours and responsibilities. Include vendors and their deliverables.
- Timeline (Gantt) template: Plot readiness assessment, policy drafting, control implementation, evidence collection, audit window and report issuance. Add post‑audit maintenance tasks.
The bar chart below visualizes how cost categories differ between small and large organizations. Small companies spend most of their budget on audit fees and readiness, while large organizations allocate more to auditor fees and remediation:
Common Pitfalls and How to Avoid Them
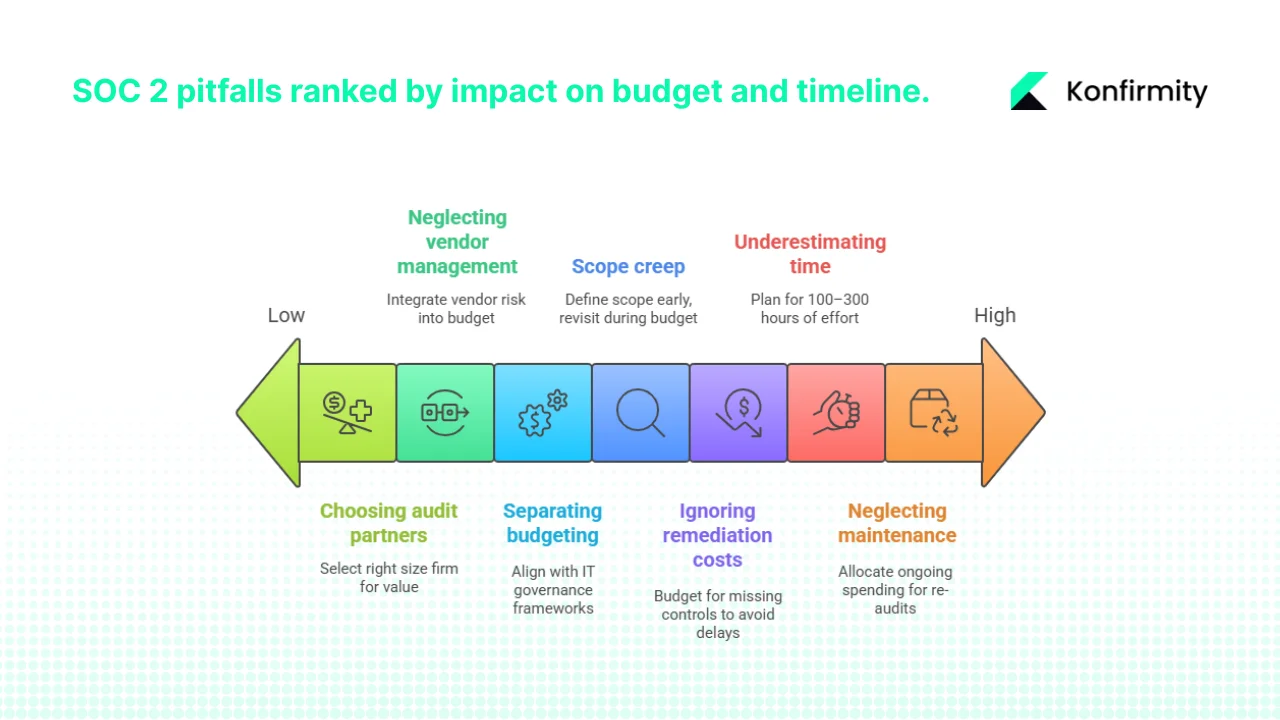
- Underestimating internal time and opportunity costs: Engineers and security teams spend weeks on evidence gathering and remediation. Plan for at least 100–300 hours.
- Scope creep: Adding new trust services criteria or geographic regions late in the process increases cost and timeline. Define scope early and revisit only during budget cycles.
- Ignoring remediation costs: Maturity gaps require time and investment. Failing to budget for missing controls can delay audits and frustrate teams.
- Choosing expensive audit partners without matching size and scope: Big Four firms may cost more with no added benefit for small companies. Consider mid‑sized CPA firms or managed services for better value.
- Neglecting maintenance and continuous monitoring: SOC 2 is not a one‑time project. Annual re‑audits and continuous evidence collection require ongoing spending.
- Overlooking vendor management: The SOC 2 common criteria require assessing and managing risks associated with vendors. Failing to integrate vendor risk management into budgeting exposes your organization to third‑party weaknesses.
- Separating budgeting from IT governance: Budgets should align with broader risk management frameworks (ISO 27001, NIST CSF, HIPAA). Aligning SOC 2 budgets with existing IT budgets helps justify spending and avoids duplication.
Making the Business Case
Convincing leadership to invest in a SOC 2 program requires tying spending to value. Emphasize that SOC 2 is more than a compliance exercise; it is a strategic enabler. Explain that enterprise buyers often require SOC 2 reports to finalize contracts. Show how delays in obtaining a SOC 2 report translate into lost revenue. Use IBM’s breach statistics to demonstrate the financial impact of weak controls—average U.S. breach costs of $10.22 million dwarf the investment in SOC 2. Highlight that a well‑run SOC 2 program reduces repetitive security questionnaires, accelerates sales cycles and builds customer trust. Present a slide-ready summary: “Year 1 spend: $X for readiness and audit; Year 2 spend: $Y for maintenance and re‑audit. Expected benefits: improved control environment, reduced buyer due‑diligence time, stronger vendor management.” Integrate these numbers into the existing IT and security budget rather than requesting ad‑hoc funds.
Template Download and Checklist
To help teams get started, prepare a simple spreadsheet with the categories described above. Each row should include: cost category, description, unit cost, quantity, total, responsible owner and due date. Use formulas to compute totals and compare against budget. Create a readiness checklist with items such as: policies documented, asset inventory complete, access control processes defined, audit logging enabled, security training program in place, vendor list updated, penetration test scheduled, gap assessment completed. Establish a budget review checklist with quarterly review dates, triggers for scope changes (e.g., new product line, regulatory change, vendor expansion) and contract renewal dates for auditors and tools.
Conclusion
Selling to enterprise clients demands more than marketing claims. It requires demonstrable, sustainable control practices. A SOC 2 Budgeting Guide gives leaders a blueprint for meeting these expectations without derailing growth. The cost of SOC 2 is not just the auditor’s fee; it includes readiness assessments, remediation, tools, internal hours and annual re‑audits. By defining scope early, breaking down cost categories, allocating resources thoughtfully and reviewing progress regularly, organizations can build a program that supports sales, strengthens security and satisfies auditors. Human‑led managed services like Konfirmity—backed by 6,000+ audits and 25+ years of expertise—focus on implementing controls inside your stack and operating them year‑round. We start with security and arrive at compliance. Start your budgeting process today, download the template and set a realistic timeline so that security promises stand up to buyers, auditors and attackers.
FAQs
1) What is the typical cost of a SOC 2 audit?
For small to midsize companies, Type I audit fees are about $7,500–$15,000 and Type II fees $12,000–$20,000. Larger organizations can spend $30,000–$100,000 or more. These figures exclude readiness, remediation, tools and internal labor, which often double the total cost.
2) How long does the SOC 2 process take?
A Type I audit can be completed in 1–3 months if your controls are in good shape. A Type II audit typically takes 6–12 months, including an observation window of at least three months to test control effectiveness.
3) Does the budget only cover the auditor fee?
No. Budgeting must include gap assessments, remediation work, tools, penetration tests, consultants, internal resources and ongoing monitoring. Auditor fees are often less than half of the total spend.
4) What if we add more trust services criteria later?
Expanding scope to include Availability, Confidentiality, Processing Integrity or Privacy introduces additional controls—redundancy, encryption, data classification, privacy practices—and increases costs. Plan for scope changes by including contingency funds and aligning budgets with business priorities.
5) How can we reduce SOC 2 compliance costs?
Start with security only, then expand criteria as needed. Use automation tools for evidence collection and monitoring to save internal hours. Reuse controls across frameworks—ISO 27001, HIPAA and GDPR share many requirements. Consider managed services that provide bundled pricing and hands‑on support.
6) Is SOC 2 enough for enterprise clients?
SOC 2 is widely accepted, but some industries require additional frameworks. Healthcare companies often need HIPAA, while European clients expect GDPR compliance. Mapping controls across frameworks reduces duplication.
7) How often do we need to budget for SOC 2?
SOC 2 reports must be refreshed annually. Plan for yearly re‑audits (70–80% of the initial audit fee) and continuous monitoring costs.
8) What internal resources need budgeting?
Security operations, IT, engineering, compliance, finance and vendor management teams all contribute. Expect 100–300+ hours per year of internal work.
9) Does company size affect cost?
Yes. Larger organizations with more systems and employees have more complex environments, leading to higher audit fees and more evidence collection.
10) Can we include vendor management and third‑party risk in the SOC 2 budget?
Yes. The AICPA common criteria require assessing and managing risks associated with vendors. Budget for due‑diligence tools, third‑party audits and contract reviews to meet enterprise buyers’ expectations.





.svg)






.svg)
.svg)