Enterprise buyers and healthcare providers have become far more rigorous about vendor security. Recent surveys show that the proportion of companies suffering breaches costing more than USD 1 million jumped from 27% to 36% between 2023 and 2024. IBM‑linked studies estimate the average cost of a breach in 2025 at USD 4.88 million, a ten percent increase over 2023. Cloud‑related incidents and data spread across multiple environments now account for 40% of breaches, and only four percent of organisations can respond quickly. Against this backdrop, procurement teams ask for concrete evidence that vendors handle sensitive data responsibly, and compliance documents often decide whether a deal moves forward.
A SOC 2 Compliance Checklist gives security leaders a structured way to prepare for independent assessments and to reassure enterprise clients. By mapping requirements to controls, documentation and evidence, teams can methodically build and test their security program. This article explains what SOC 2 is, why it matters in enterprise sales and healthcare, and how to build and use a practical checklist. We’ll cover the differences between Type 1 and Type 2 reports, the Trust Service Criteria (TSC), pre‑audit preparation, control implementation, templates for busy teams and the audit process. Throughout, I’ll speak from twenty‑five years of technical and audit experience and Konfirmity’s work supporting more than 6,000 audits as a human‑led, managed security and compliance partner.
What SOC 2 Is and Why Enterprise Clients Care
The American Institute of Certified Public Accountants (AICPA) developed SOC 2 reports to provide assurance about a service organisation’s controls relevant to security, availability, processing integrity, confidentiality and privacy. Unlike SOC 1, which focuses on financial reporting, SOC 2 targets operational and data protection controls. For enterprise clients, it has become a common prerequisite because it demonstrates that a vendor’s security program is designed and (in the case of Type 2) operates effectively over time. Healthcare providers often require it alongside HIPAA compliance to protect electronic protected health information (ePHI).
Type 1 vs. Type 2 Reports
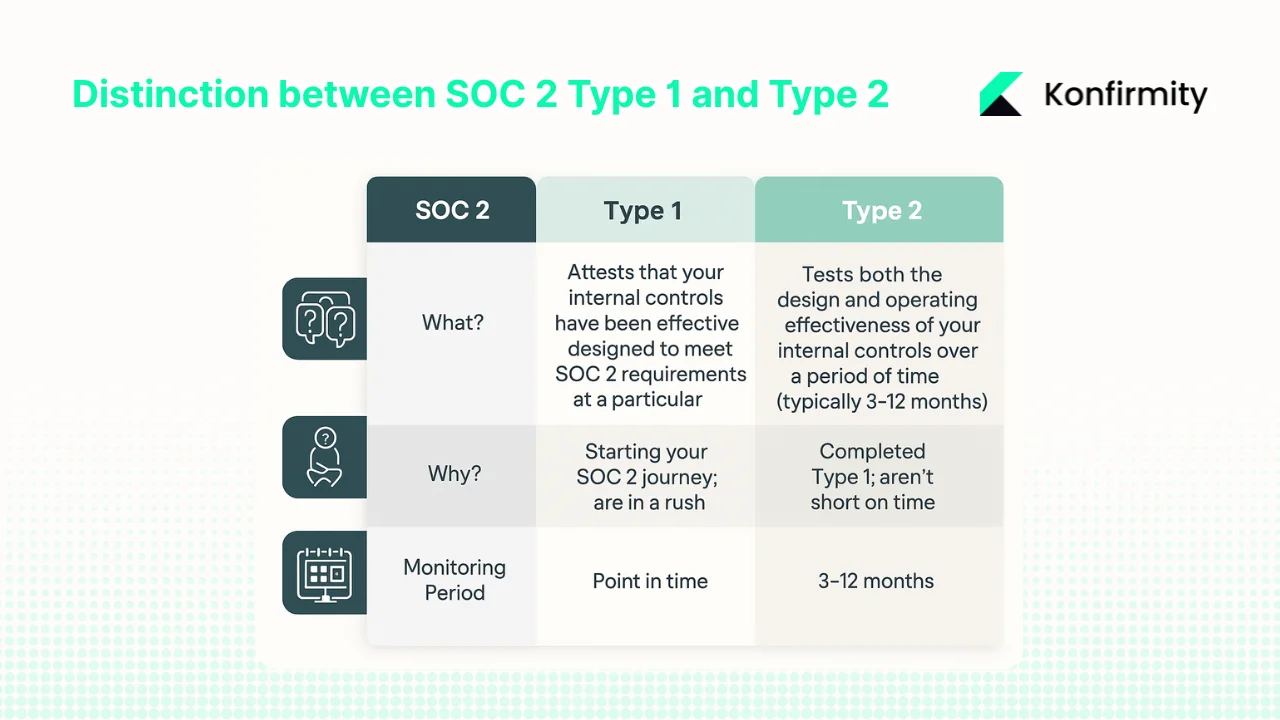
A SOC 2 Type 1 report evaluates whether controls have been designed and implemented at a specific point in time. It provides a snapshot, which can help early‑stage companies show that they have controls documented and functioning. A Type 2 report goes further: auditors test the operating effectiveness of those controls over a period of six to twelve months. Because the evidence covers an observation window, Type 2 attestation signals to customers that the organisation maintains its controls, not just that it designed them.
Enterprise procurement teams increasingly insist on Type 2 reports. They need proof that vendors manage access rights, monitor activity and handle incidents continuously, not just at the moment of documentation. In fields like healthcare and financial services, where data breach costs are highest (USD 9.77 million and USD 6.08 million respectively), many buyers refuse to sign contracts without a Type 2 attestation.
Trust Service Criteria: The Pillars of SOC 2
The SOC 2 framework is built on five Trust Service Criteria. Security is mandatory; it addresses access control, intrusion detection, system monitoring and encryption. The other four are optional depending on the scope of services:
- Availability: Can the system meet uptime commitments and recover from disruptions? Controls include redundancy, disaster recovery and service‑level objectives.
- Processing integrity: Does the system process data accurately and completely? Controls address input validation, change management and error logging.
- Confidentiality: Is sensitive information restricted to authorised personnel? Controls include role‑based access, encryption and masking.
- Privacy: Does the organisation handle personal data in accordance with its notice and applicable laws? Controls relate to consent, data retention and disposal.
An effective SOC 2 compliance program maps each relevant criterion to policies, procedures and control evidence. Security must always be covered; the others are selected based on client expectations and regulatory obligations. For example, a healthcare SaaS provider may include confidentiality and privacy, while a fintech platform may add processing integrity and availability.
Preparing Your SOC 2 Compliance Checklist: Pre‑Audit Steps
Preparing for a SOC 2 audit is not just about writing policies. It involves defining objectives, boundaries, risks and ownership. Konfirmity has found that skipping this planning stage is the main cause of rushed projects and audit findings. Below are the steps we recommend.
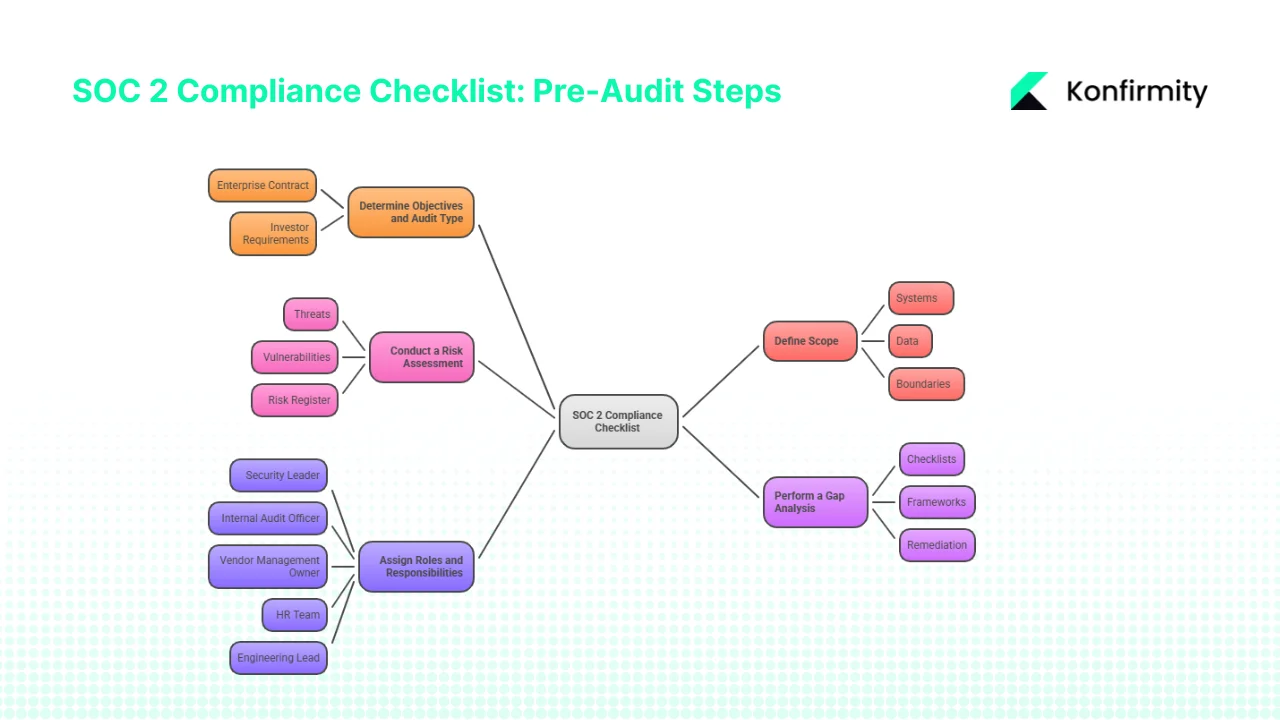
1) Determine Objectives and Audit Type
Identify why you need SOC 2. Is it required to unlock an enterprise contract? Are investors asking for proof of controls? If clients insist on Type 2 attestation, don’t waste time with a Type 1; build your program to meet the longer observation period. If your controls are still nascent, a Type 1 can be a stepping stone. The decision should be tied to customer requirements and the maturity of your program.
2) Define Scope: Systems, Data and Boundaries
Scope sets the boundaries of your SOC 2 program. List all systems, services and components that handle customer data. Include production workloads, supporting infrastructure, identity providers, ticketing systems and third‑party integrations. Map each component to the Trust Service Criteria. For instance, if you process healthcare data in multiple clouds, confidentiality and privacy are mandatory; if you run a global SaaS platform, availability controls may be in scope.
Pay special attention to vendors and subcontractors. Many enterprise buyers ask for a list of your third‑party providers. You must track which vendors have access to sensitive systems or data, verify their security posture, and maintain contracts that require them to follow appropriate standards.
3) Conduct a Risk Assessment
Risk assessment is the foundation for control selection. NIST’s Risk Management Framework describes a seven‑step process: prepare, categorise, select, implement, assess, authorise and monitor. Even if you don’t follow that process verbatim, you should identify threats and vulnerabilities affecting systems in scope, estimate their likelihood and impact, and decide which controls to implement. Consider threats such as credential theft (which accounts for 16% of breaches), phishing attacks fuelled by generative technology, unpatched vulnerabilities (breach costs increase sharply when vulnerabilities are exploited) and insider misuse.
Document the results in a risk register. Each entry should include a description of the risk, likelihood, impact, existing controls, planned mitigations and an owner responsible for tracking remediation. Review and update the register regularly, and ensure the board or executive leadership is aware of top risks.
4) Perform a Gap Analysis or Readiness Assessment
A gap assessment compares your current controls against SOC 2 criteria and identifies deficiencies. Use checklists or frameworks (e.g., ISO 27001 Annex A, NIST SP 800‑53 controls) to ensure coverage. Document which policies or technical controls are missing. For example, you might have multi‑factor authentication for customer accounts but not for internal administrative accounts; or you may lack a formal incident response plan. Prioritise remediation based on risk impact and the time needed to implement changes. In our experience, companies that start with a realistic gap assessment reduce audit findings by 40% compared with those that assume they are ready.
5) Assign Roles and Responsibilities
SOC 2 readiness touches every team: engineering, operations, security, HR, legal and finance. Assign clear owners for each domain:
- Security leader (CISO or head of security): owns policy creation, control implementation and response to audit requests.
- Internal audit or compliance officer: manages documentation, coordinates evidence collection and liaises with the external auditor.
- Vendor management owner: maintains the vendor inventory, conducts due diligence and ensures contractual clauses are in place.
- HR or people team: oversees background checks, onboarding/offboarding procedures and employee training.
- Engineering lead: implements technical controls, such as access management, logging and encryption.
Use project management tools to track tasks, due dates and dependencies. Busy teams often allocate part‑time resources and underestimate the workload; our managed service reduces internal hours from 550‑600 to around 75 per year by automating evidence collection and providing dedicated experts.
CTA: Book a demo
Building the SOC 2 Compliance Checklist: Controls, Policies and Examples
A SOC 2 Compliance Checklist is not a generic template; it needs to reflect your systems, risks and obligations. However, certain categories are common across most audits. For each, I’ve provided practical guidance, sample checklist items and example documentation prompts. Remember to keep language clear and assign an owner to each item.
1) Security Policies and Access Controls
Access control violations are one of the leading causes of data breaches. The Verizon Data Breach Investigations Report indicates that 68% of breaches involve a human element and credential theft is the most common initial vector. To mitigate these risks:
- Establish a formal security policy approved by management. Outline the objectives, scope and authority. Reference frameworks like ISO 27001 for baseline controls.
- Document access control procedures. Enforce role‑based access, least‑privilege and segregation of duties. Require multi‑factor authentication for all privileged accounts. Review user access at least quarterly. Automate detection of stale accounts and enforce access revocation within one business day of termination.
- Monitor privileged access. Use a central logging solution (e.g., SIEM) to record administrative actions and detect unusual patterns. As IBM‑s cost report shows, breaches contained within 200 days cost about USD 4.07 million compared with USD 5.46 million when detection is slower; effective logging reduces dwell time.
Example template item:
2) Vendor Management
Third‑party providers can introduce weaknesses. Only two percent of organisations consistently improve cyber resilience across all areas, and many breaches trace back to subcontractors. A good vendor management program includes:
- Inventory of third parties: Maintain a catalogue of vendors and sub‑processors who access systems or data. Classify them by risk level.
- Due diligence and contract clauses: Assess each vendor’s security posture. Request their SOC 2 or ISO 27001 reports, evaluate control gaps and ensure contracts include confidentiality and security obligations.
- Ongoing monitoring: Re‑assess vendors periodically. Track security incidents, review audit reports and ensure corrective actions.
Checklist item example: VM-02: Complete vendor risk assessment for all new vendors before contract execution. Record assessment results and approval status in vendor management tools.
3) Incident Response, Monitoring and Logging
Rapid detection and response reduce breach costs. The average time to detect and contain a breach is 258 days, and faster detection can save USD 1.39 million per incident. To strengthen your incident program:
- Incident response plan: Document roles, communication channels, escalation paths and post‑mortem procedures. Include criteria for notifying customers and regulators.
- Logging and monitoring: Log user and system events across production environments. Configure alerts for suspicious activity, such as multiple failed login attempts or unusual data access. Retain logs for a defined period (e.g., one year) to support forensic analysis.
- Testing: Conduct tabletop exercises and red team drills annually. Evaluate detection coverage and refine playbooks.
Checklist item example: IR-04: Conduct annual incident response test; document lessons learned and update plan.
4) Data Encryption and Confidentiality
Data encryption protects confidentiality and is required by many clients. The Onspring guide notes that confidentiality controls include encryption, NDAs and access controls. To meet this criterion:
- Encrypt data in transit and at rest: Use TLS for network communications and encrypt storage volumes, backups and databases. For SaaS applications, verify that cloud providers support encryption by default.
- Classify information: Identify sensitive fields (PII, PHI, financial records) and mark them as confidential. Define retention periods and destruction procedures. Maintain records of who owns each dataset.
- Secure disposal: Define processes for securely wiping media and decommissioning hardware or virtual machines that store sensitive data. Document evidence of destruction.
5) Employee Training and Security Awareness
The human element is involved in the majority of breaches. Effective training is a cost‑effective defence. Include:
- Onboarding and annual training: Provide mandatory security awareness training covering phishing, password hygiene, social engineering, acceptable use and reporting procedures.
- Role‑specific training: Offer advanced modules for system administrators and developers on topics such as secure coding, patch management and incident response.
- Tracking and metrics: Record completion rates, quiz scores and phishing simulation results. Use this data to improve training and identify high‑risk departments.
6) Audit Procedures and Compliance Documentation
SOC 2 audits require evidence. Keep documentation organised:
- Policy and procedure documentation: Maintain up‑to‑date policies with management approval. Review them annually or when significant changes occur.
- Control evidence repository: Store logs, screenshots, configurations, third‑party reports and other evidence in a secure repository. Label each item with the related control ID and audit period.
- Internal reviews: Conduct periodic checks to verify that documents are current and reflect actual practices. Use checklists to ensure that control evidence is collected consistently.
7) Controls Assessment and Continuous Monitoring
After designing and implementing controls, assess their effectiveness regularly. Continuous monitoring reduces the risk of stale evidence and ensures that deviations are detected quickly.
- Self‑assessments: Map each control to the relevant TSC and evaluate whether it operates as intended. Document any deficiencies and remediation plans.
- Monitoring metrics: Track metrics such as failed login attempts, patch status, vulnerability age, incident response times and vendor assessment dates.
- Dashboard and reporting: Create dashboards that summarise control health for senior leadership. Provide weekly or monthly updates to maintain visibility.
8) Risk Management Integration
Risk management should drive control selection and monitoring. Build processes to:
- Maintain a risk register: As described earlier, identify risks, assign owners and document mitigation plans. Review the register at least quarterly.
- Link risk assessments to control updates: When new threats emerge (e.g., a surge in phishing campaigns or a critical vulnerability like MOVEit), update controls accordingly. Document decisions and track progress.
- Embed risk discussions into governance: Present the top risks and mitigation status to executive leadership and, where applicable, the board. This ensures accountability and helps secure resources for remediation.
Templates and Example Structures for Busy Teams
For organisations with limited resources, templates save time. Konfirmity provides ready‑made spreadsheets and checklists that map controls to evidence and owners. A typical worksheet has columns for control ID, description, TSC, owner, evidence location, status and review date. For instance:
Busy teams should reuse existing frameworks (ISO 27001 Annex A, NIST SP 800‑53, CIS Controls) as starting points. Identify where controls overlap and avoid duplicating work. Allocate part‑time resources to gather evidence; automation tools can pull logs from cloud providers, CI/CD pipelines and identity systems without manual intervention. Konfirmity integrates similar capabilities into its managed service.
CTA: Book a demo
The Audit Process: From Readiness to Report
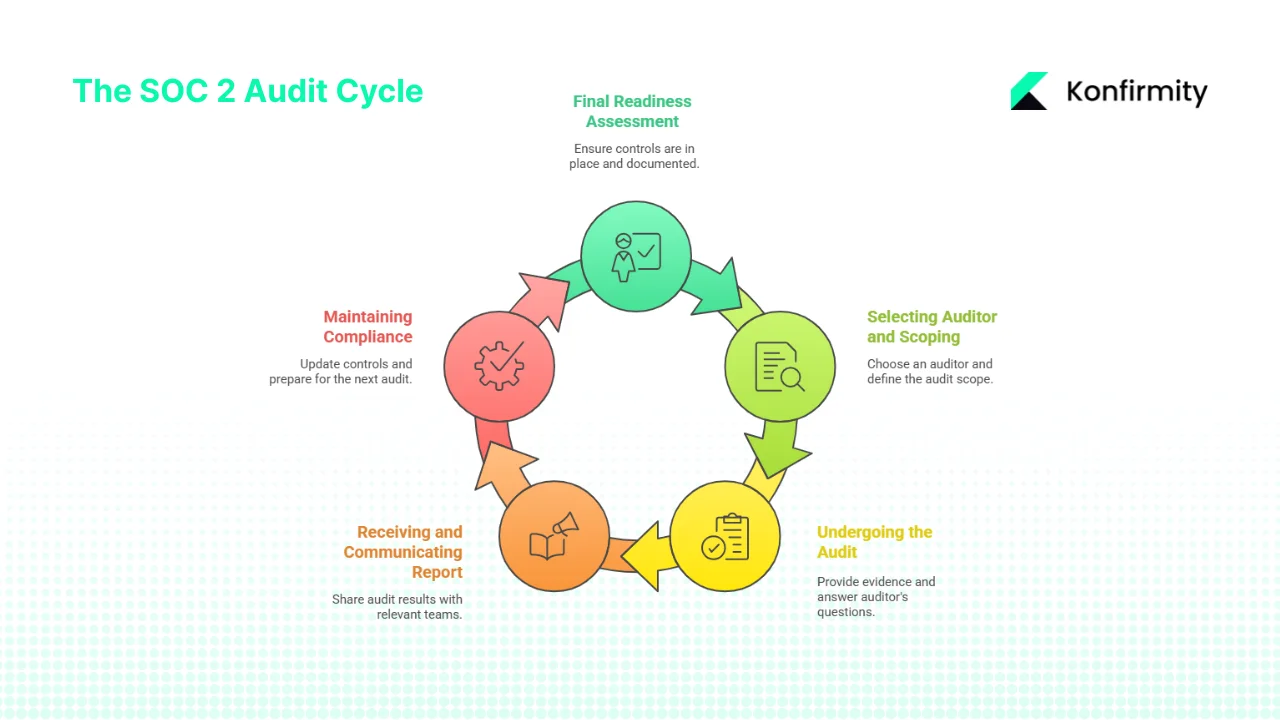
1) Final Readiness Assessment
Before engaging an external auditor, perform a readiness review. Validate that all controls are designed, documented and operating. Conduct internal tests to verify that evidence exists for each control. Address any gaps before scheduling the audit. A mock audit reduces surprises and helps teams get comfortable with the process.
2) Selecting an Auditor and Scoping the Report
Choose a CPA firm experienced in SOC 2. Discuss the scope: which systems and TSCs are included, the observation period, and any carve‑outs. Decide whether to pursue Type 1, Type 2 or both. Type 2 is more rigorous, covering at least six months. Work with the auditor to set expectations for evidence submission and communication.
3) Undergoing the Audit
During the audit, expect requests for documentation, screenshots, logs and interviews. Auditors will test access reviews, change management records, incident response activities and vendor due diligence. Provide timely responses and ensure that the evidence is organised. For enterprise‑selling companies, your prospects may issue their own security questionnaires referencing your SOC 2 report. Align internal messages to ensure consistent responses.
4) Receiving the Report and Communicating Results
After the audit, the auditor will issue a report. For Type 2, it includes an opinion on the operating effectiveness of controls, test procedures and results. Communicate the outcome to sales, marketing, legal and product teams so they know how to reference it during procurement discussions. Many organisations share the report under a non‑disclosure agreement to reassure potential customers.
5) Maintaining Compliance and Preparing for the Next Period
SOC 2 is an ongoing commitment. Maintain your controls, update documentation as systems change and monitor evidence continuously. Schedule periodic internal reviews and track remediation actions. Plan to renew your attestation annually; many enterprise clients and healthcare payers expect yearly evidence. Automation tools and managed services like ours help maintain audit readiness year‑round, reducing the burden on internal teams.
Common Challenges and How to Overcome Them
1) Lack of documentation: Teams often implement technical controls but fail to document them. Start early with a gap assessment and assign owners. Use templates to capture policies, procedures and evidence.
2) Manual evidence collection: Without automation, collecting logs and screenshots is time‑consuming. Invest in tools or managed services that integrate with your cloud providers, CI/CD systems and identity platforms to capture evidence automatically.
3) Vendor weaknesses: Your security posture is only as strong as your weakest vendor. Maintain an up‑to‑date inventory, include security and confidentiality clauses in contracts, and require third‑party attestation when feasible.
4) Training fatigue: Employees may treat annual training as a check box. Keep modules short and relevant to specific roles. Use phishing simulations and quizzes to reinforce learning. Tie training completion to performance goals and emphasise that strong security unlocks customer deals.
5) Scope creep: Changes in products, regions or infrastructure can expand the audit scope unexpectedly. Define the scope clearly at the start and revisit it whenever the business changes (new features, acquisitions, geographies). Document the rationale for including or excluding components.
Case Example: Scaling Security Amid Rapid Growth
Consider a hypothetical healthcare SaaS company, MedCloud. Initially, MedCloud focused on building its platform and had ad‑hoc security practices. When a hospital network insisted on a SOC 2 Type 2 report as a condition of partnership, MedCloud realised it needed a structured approach.
The company engaged Konfirmity for a readiness assessment. We mapped their infrastructure and discovered missing controls: no formal change management, incomplete access reviews and no documented incident response plan. We helped MedCloud conduct a risk assessment, implement role‑based access, establish logging pipelines and develop policies. Within five months, MedCloud passed a Type 2 audit and secured the hospital contract. It now maintains continuous monitoring through our managed service, spending around 70 internal hours per year instead of the estimated 550 hours they had tried to self‑manage.
CTA: Book a demo
Checklist Summary and Practical Next Steps
Below is a high‑level checklist grouping the items discussed. Use it as a living document and adapt it to your environment:
- Pre‑Audit Preparation
- Determine audit objectives (Type 1 vs. Type 2, TSC scope)
- Define scope of systems, data, regions and vendors
- Conduct a risk assessment and document a risk register
- Perform a gap analysis and remediation plan
- Assign roles and responsibilities; schedule milestones
- Determine audit objectives (Type 1 vs. Type 2, TSC scope)
- Controls and Policy Implementation
- Create formal security policies
- Implement access controls and periodic reviews
- Maintain vendor inventory and conduct due diligence
- Develop incident response plan and logging
- Encrypt data at rest and in transit; classify information
- Deliver employee training and track metrics
- Document policies, procedures and evidence in a central repository
- Create formal security policies
- Audit Readiness
- Conduct a readiness assessment (mock audit)
- Select an experienced auditor; scope the engagement
- Prepare evidence for each control; ensure it covers the observation period
- Collaborate with the auditor during testing; answer questions promptly
- Conduct a readiness assessment (mock audit)
- Continuous Monitoring and Improvement
- Perform regular control assessments and monitor metrics
- Update the risk register and adapt controls to new threats
- Review vendor performance and renew contracts
- Plan for annual SOC 2 renewals and integrate results into sales messaging
- Perform regular control assessments and monitor metrics
30–60–90‑Day Plan for Busy Teams
- Weeks 1 – 2: Assign a SOC 2 project leader, define objectives and scope, list all systems and vendors, and draft a risk register.
- Weeks 3 – 4: Conduct a detailed risk assessment and gap analysis. Identify missing controls. Start drafting policies and procedures.
- Month 2: Implement remediation actions. Establish access reviews, encryption, logging, incident response and training programs. Engage a managed service or automation tool to reduce manual effort.
- Month 3–4: Finalise policies, complete documentation and conduct a readiness assessment. Fix any remaining gaps.
- Month 4–6: Engage the auditor, provide evidence and undergo the audit. After receiving the report, share it internally and embed the results into your sales and marketing processes.
- Post‑Audit: Set up continuous monitoring, update metrics and plan for the next audit period.
Conclusion
Enterprise and healthcare buyers judge vendors on their ability to protect data and operate securely. Data breaches are growing in scale and cost: the global average hit USD 4.88 million in 2025, and organisations with mature security programs experience fewer million‑dollar breaches. SOC 2 attestation is a powerful signal that you take security seriously. But to deliver real assurance, you need a well‑designed control environment, continuous evidence collection, and year‑round operations. SOC 2 compliance checklists are not just about passing an audit; they are tools for building a disciplined program that stands up to buyers, auditors and attackers.
As a practitioner who has guided hundreds of companies through SOC 2 readiness, I urge you to start with security and let compliance follow. Engage experts who will implement controls within your stack, monitor them continuously and handle evidence collection. Avoid the trap of treating compliance as a one‑time exercise. A living checklist, backed by a human‑led managed service, turns a certification requirement into a competitive advantage.
FAQ
1) What is the SOC 2 Type 2 compliance checklist?
A SOC 2 Type 2 compliance checklist is a structured list of tasks, controls and evidence that organisations use to prepare for a SOC 2 Type 2 audit. It covers design and operational effectiveness of controls over an observation period, typically six to twelve months. The checklist maps each Trust Service Criterion to specific policies, procedures, control implementations and documentation.
2) What are the five criteria for SOC 2?
The five Trust Service Criteria are security (mandatory), availability, processing integrity, confidentiality and privacy. Security addresses protection against unauthorised access and is required for all SOC 2 reports. The other criteria are optional based on the services provided and the needs of customers.
3) What is required to be SOC 2 compliant?
To achieve SOC 2 attestation, you must define the scope of systems and services, conduct a risk assessment, implement controls mapped to the Trust Service Criteria, document policies and procedures, collect evidence of control operation over the audit period and engage a qualified CPA firm to perform the examination. Continuous monitoring and improvement are essential.
4) How often is SOC 2 compliance required?
SOC 2 is not a certification that expires at a fixed date; each Type 2 report covers a specific period (usually six to twelve months). Most organisations renew their attestation annually to provide continuous assurance to clients and regulators. Maintaining control effectiveness throughout the year is critical.





.svg)






.svg)
.svg)