Enterprise buyers increasingly insist on security assurance before they sign a contract. SOC 2 is a voluntary attestation that evaluates how well a service provider protects customer data, and ISO 27002 is an international code of practice for selecting and maintaining security controls. Mapping SOC 2 controls to ISO 27002 lets vendors satisfy both standards without duplicating work. In the following sections you’ll learn how to align the frameworks, use real‑world examples and build a mapping process.
Recent breach reports reveal U.S. incidents costing about $10.22 million on average and a spike in enforcement actions. With regulators and buyers demanding evidence, mapping SOC 2 controls to ISO 27002 helps companies implement real controls rather than paper promises and gain a competitive edge.
What Are SOC 2 Controls?
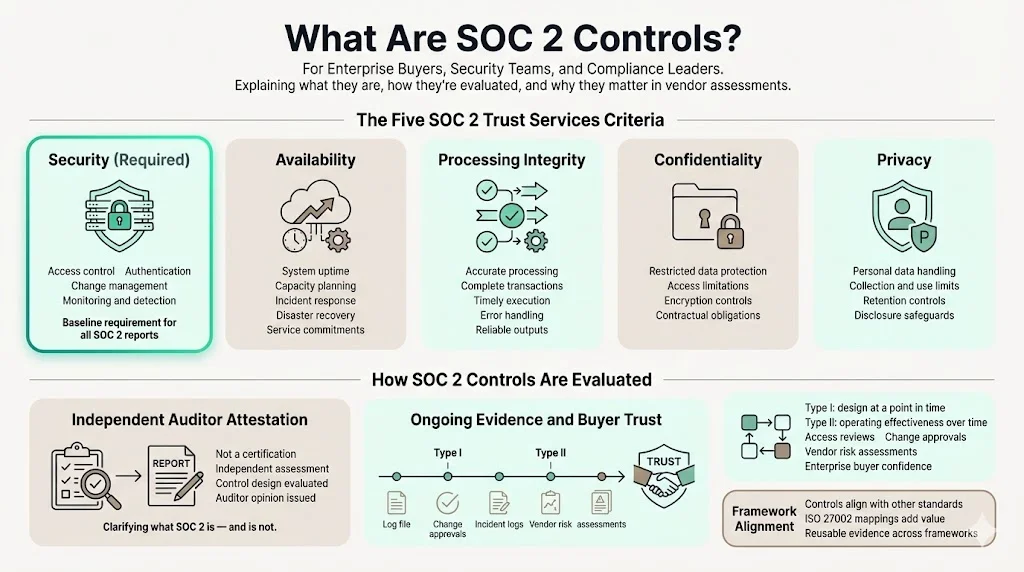
SOC 2 evaluates a service organisation’s controls against five high‑level criteria: Security, Availability, Processing Integrity, Confidentiality and Privacy. Security covers access control, authentication, change management and monitoring. Availability addresses whether systems meet uptime commitments; Processing Integrity concerns the accuracy and timeliness of processing; Confidentiality relates to protecting restricted data; and Privacy covers how personal information is collected and used.
Unlike a certification, a SOC 2 report is an independent auditor’s attestation about how controls are designed and, for a Type II report, how they operate over a period. Because evidence must show controls working in practice, SOC 2 demands ongoing artefacts such as access reviews, change‑management approvals, incident logs and third‑party assessments. Enterprise buyers rely on these reports to gauge whether a vendor’s internal controls meet industry expectations and to reduce their own risk. In later sections we’ll show how SOC 2 Controls Mapped To ISO 27002 makes these controls even more valuable.
Why SOC 2 Matters to Enterprise Buyers
Enterprise buyers view SOC 2 reports as proof that a vendor’s controls are not just documented but operating. Many financial institutions require them for due diligence. An unqualified SOC 2 Type II report signals that controls governing access, availability, incident management and data confidentiality meet industry‑accepted criteria. In our work supporting thousands of audits, we’ve seen sales cycles stall when a vendor cannot present a current report. Conversely, vendors who maintain continuous evidence and link their controls to ISO 27002 often satisfy buyer questionnaires quickly and move to contract faster.
What Is ISO 27002?
ISO 27002 is part of the ISO 27000 family. While ISO 27001 defines requirements for an information‑security management system, ISO 27002 provides the detailed control guidance used to implement that system. In 2022 the standard was modernised: controls were grouped into four themes—organisational, people, physical and technological—and reduced from 114 to 93. New controls address threat intelligence, data masking, cloud services and secure coding. For example, access control and supplier monitoring controls clarify how to grant, review and revoke access and oversee third‑party services. Each control comes with attributes (control type, security property and cybersecurity concept) that make it easier to cross‑reference SOC 2 criteria with ISO 27002 and other frameworks.
Understanding these controls is essential when pursuing SOC 2 Controls Mapped To ISO 27002 because the detailed guidance allows you to meet both frameworks with one implementation.
The Role of ISO 27002 in Information Security and Cybersecurity
ISO 27002 bridges the gap between high‑level requirements and day‑to‑day controls. Its guidance is descriptive, so teams tailor controls to their context while preserving confidentiality, integrity and availability. Risk management drives control selection, aligning ISO 27002 with other frameworks that encourage continuous monitoring and incident response. Because the 2022 edition introduces controls for threat intelligence, cloud services and secure coding, adopting ISO 27002 helps vendors demonstrate readiness for modern architectures. Combined with ISO 27001 certification, ISO 27002 gives auditors a clear view of how controls are implemented.
Why Map SOC 2 Controls to ISO 27002?
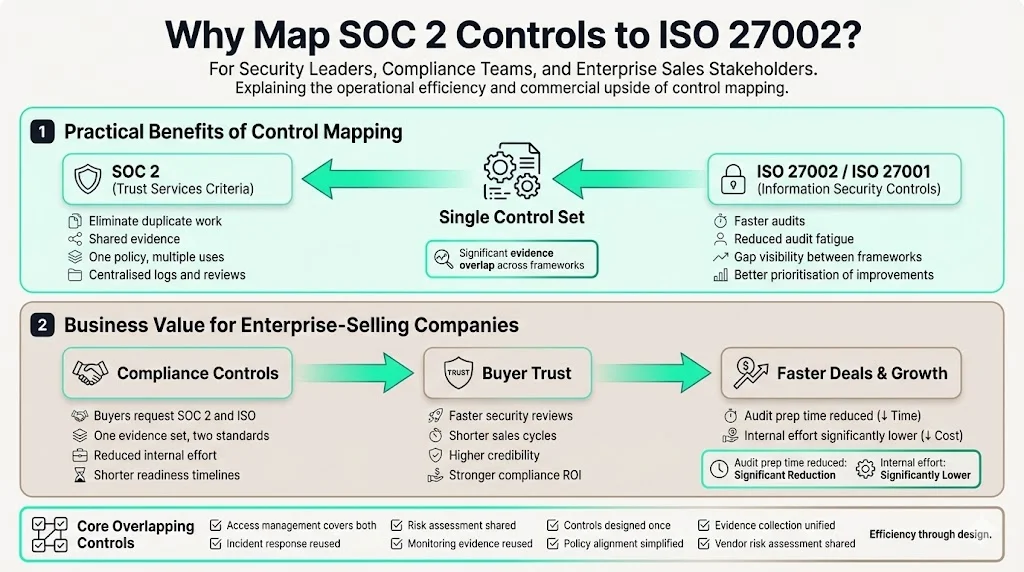
Practical Benefits
Mapping controls across frameworks eliminates duplicate effort. Guidance from Vanta notes that overlapping SOC 2 and ISO 27002 requirements can be satisfied simultaneously, reducing redundant work. A-LIGN’s 2025 benchmark report found that roughly 43% of SOC 2 evidence can also satisfy ISO 27001 requirements. Centralising evidence—policies, logs and reviews—makes audits faster and frees resources for security improvements. Mapping also reveals where one framework covers gaps in the other, helping teams prioritise enhancements.
By focusing on SOC 2 Controls Mapped To ISO 27002, you ensure that each control implementation delivers value across both standards rather than standing alone.
Business Value for Enterprise‑Selling Companies
Buyers often ask for both SOC 2 and ISO certifications. Secureframe’s 2026 trends report found that ISO 27001 adoption rose to 81% in 2025. Having SOC 2 Controls Mapped To ISO 27002 means vendors can provide evidence for both frameworks at once, accelerating sales cycles and boosting credibility. It also improves return on compliance investment: one well‑designed access‑management programme or incident‑response playbook can satisfy both standards. In our experience, concurrent readiness shortens audit preparation from 9–12 months to 4–5 months and reduces internal effort by roughly 75%.
How SOC 2 Controls Align With ISO 27002
Mapping Logic Overview
Both frameworks share a common purpose: safeguarding confidentiality, integrity and availability of data. SOC 2’s Trust Services Criteria are conceptual categories, while ISO 27002 provides granular controls. Mapping involves identifying where SOC 2 criteria correspond to ISO 27002 controls and documenting how a single control implementation meets requirements in both frameworks. This mapping exercise reveals overlaps, highlights where ISO 27002 demands additional detail (e.g., specific authentication methods) and surfaces gaps where a control may be required by one framework but not the other. When mapping, teams should consider the control objective, evidence requirements and risk coverage. The attributes in ISO 27002 (control type, security property, cybersecurity concept, operational capability and domain) help cross‑reference SOC 2 criteria to the appropriate ISO controls.
Example Mappings
The following table illustrates how selected SOC 2 criteria align with ISO 27002 controls. Each pair shows a high‑level mapping; teams should tailor these mappings to their environment and risk posture. ISO control numbers refer to the 2022 edition, with corresponding references from Schellman’s mapping table.
These mappings demonstrate that many controls share similar objectives. However, there are areas where ISO 27002 introduces additional depth. For instance, control 5.7 Threat intelligence and control 8.11 Data masking are unique to ISO 27002:2022. Conversely, SOC 2’s Privacy criterion may require evidence under frameworks like ISO 27701 or regional privacy laws. Understanding these overlaps and gaps is essential for tailoring your control environment.
Typical Overlap and Gaps
In our experience, the strongest alignment occurs around access control, change management, incident management and business continuity. These areas map neatly because both SOC 2 and ISO 27002 share the goals of ensuring only authorised users access systems, changes are approved, incidents are detected and handled promptly, and systems remain available. Gaps typically arise in the level of prescriptiveness. ISO 27002 provides detailed guidance on topics such as secure coding, threat intelligence, data masking and physical security that may not be explicitly covered in SOC 2 but are implied under the Security criterion. On the other hand, SOC 2 emphasises demonstrating operating effectiveness over a period, which means your mapping must include evidence of control operation—logs, reviews and reports—where ISO 27002 may only require documented policy and procedures.
Mapping Process for Busy Teams
Aligning SOC 2 controls to ISO 27002 is a structured project. A simple approach is to (1) inventory existing controls and evidence, (2) map SOC 2 criteria to ISO 27002 controls using a matrix, (3) note where your controls fully match, partially match or require new procedures, (4) link evidence to both frameworks and (5) revisit the mapping whenever standards or your environment change.
Tools and Best Practices
Start by building a matrix that lists each SOC 2 criterion and its corresponding ISO 27002 controls. Use a spreadsheet or GRC platform to automate the mapping and link policies, logs and access reviews to control owners and review dates. Integrating these tools with your repositories and ticketing systems keeps audit‑ready evidence without manual export. Our managed service maintains this mapping year‑round so clients provide inputs once.
Modern governance tools support version control and change tracking. When SOC 2 or ISO 27002 updates, you can identify changed controls and update your mapping without starting over. Keeping the mapping as a living document ensures your team always knows which controls apply and which evidence is required.
Our experience across more than 6,000 audits shows that a well‑structured matrix speeds up preparation by roughly 75%. Clients using this approach complete SOC 2 and ISO 27001 readiness in 4–5 months instead of 9–12. By focusing on SOC 2 Controls Mapped To ISO 27002, you build a central nerve system for your programme.
Maintaining Dual Compliance
Aligning SOC 2 controls with ISO 27002 is not a one‑off project. It requires embedding security practices into daily work—vulnerability scans, patching, access reviews and third‑party assessments. ISO 27002’s focus on threat intelligence, data masking and secure configuration complements SOC 2’s demand for ongoing evidence. Embedding these practices into software development and IT operations ensures you always have logs, tickets and approvals to support your SOC 2 Controls Mapped To ISO 27002.
From a compliance perspective there are two cycles: the SOC 2 Type II observation window (often 6–12 months) and the annual ISO 27001 surveillance audit. Keeping SOC 2 Controls Mapped To ISO 27002 up to date ensures evidence collected for one cycle supports the other. For example, quarterly access reviews or incident‑response exercises can serve both frameworks. When new controls like secure coding or data masking appear, update your matrix and integrate the practice into operations.
Clients often ask how to maintain compliance without overloading their teams. The key is designing processes that generate evidence as a by‑product of good practice. For instance, when developers open a pull request in Git, the system automatically logs peer review, testing and security scans, satisfying change‑management evidence for both frameworks. Similarly, our vendor‑management workflow collects contract approvals and due‑diligence questionnaires in one system, producing evidence for SOC 2 CC3 and ISO 27002 5.22. Building controls into the tools your team already uses means you achieve cross‑framework compliance without extra steps.
Reviewing Mappings Over Time
The compliance landscape shifts rapidly. ISO 27002 was updated in 2022 and may evolve again; SOC 2 points of focus are periodically refreshed by the AICPA. Threats also change: IBM’s 2025 report noted that artificial intelligence is accelerating phishing and that malicious insiders cost companies $4.92 million on average. Such developments require you to revisit your control environment and mapping at least annually. When frameworks change or new risks emerge, update your SOC 2 Controls Mapped To ISO 27002 matrix to add new controls, adjust evidence and retire outdated procedures. This proactive approach prevents last‑minute scramble before audits and ensures that your programme reflects real‑world threats.
Common Challenges and How to Avoid Them
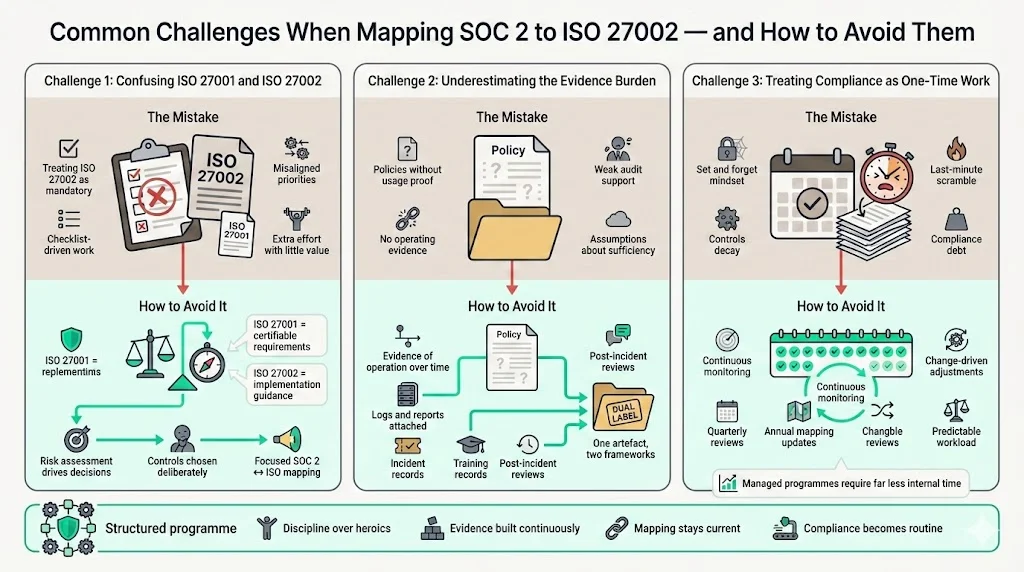
Teams starting SOC 2 Controls Mapped To ISO 27002 often fall into three traps. First, they conflate ISO 27002 with ISO 27001. ISO 27001 sets certifiable requirements for an information‑security management system, while ISO 27002 provides non‑mandatory guidance on how to implement controls. Treating ISO 27002 as a checklist can lead to unnecessary work or misaligned priorities. Instead, use ISO 27002 to inform your control design and rely on your risk assessment to determine which controls are appropriate. This understanding keeps your SOC 2 Controls Mapped To ISO 27002 focused and efficient.
Second, organisations underestimate the evidence burden. SOC 2 is an attestation that proves controls operate over time. ISO 27002 emphasises detailed control implementation but does not prescribe observation periods. If you design controls to satisfy ISO 27002 only, you might document policies without collecting operation evidence. To avoid this, ensure that each mapped control includes specific logs, tickets or reports demonstrating that it is not only defined but used. For example, an incident‑response plan should be supported by incident logs, post‑mortem analyses and evidence of training. Such artefacts serve both frameworks and help auditors understand how the control functions in practice.
Third, teams sometimes underestimate the ongoing workload. Compliance is not “set it and forget it”. After initial attestation or certification, you must maintain controls, update them when business processes change and prepare for surveillance audits. Underestimating this commitment leads to compliance debt and panic before renewal. A disciplined programme of continuous monitoring, quarterly reviews and annual mapping updates keeps you ready year‑round. In our experience, clients using our managed service spend about 75 hours per year on compliance activities versus 550–600 hours in a typical self‑managed programme. By keeping this mapping current, you turn compliance into a predictable process rather than a crisis.
Conclusion
Mapping SOC 2 controls to ISO 27002 is more than an administrative exercise; it’s a strategic way to align your security investments with buyer expectations and international standards. The frameworks share common goals but differ in structure and depth. By identifying overlaps and addressing gaps, you can implement controls once and satisfy multiple audits. Businesses selling to enterprise clients will find that demonstrating SOC 2 Controls Mapped To ISO 27002 accelerates procurement, reduces due‑diligence friction and builds trust.
The stakes are high. Data breaches in the U.S. cost an average of $10.22 million, and regulatory enforcement is increasing. As more organisations pursue ISO 27001 certification, clients expect vendors to prove both operational security (SOC 2) and alignment with international control frameworks. A robust mapping ensures that your policies, access reviews, change‑management records and incident logs serve both needs. It also positions you for HIPAA, GDPR and other requirements because many of the same controls—access management, encryption, audit logging—apply across regulations.
Security that “reads” well but fails under incident pressure is a liability. Build controls that operate daily, generate evidence automatically and adapt to evolving standards. Keep your SOC 2 Controls Mapped To ISO 27002 current and integrated into business processes instead of spreadsheets. When done right, you avoid non‑compliance costs and give your sales team the evidence they need. And when things change—as they inevitably do—you’ll adjust quickly, because your mapping is a living, breathing part of your programme.
Konfirmity believes that security should lead and compliance should follow. Our human‑led, managed service embeds experts in your team to implement controls, monitor them continuously and collect evidence year‑round. This approach reduces internal effort by about 75% while improving real security. Build the programme once, operate it daily and let compliance come naturally.
Build SOC 2 controls into your daily workflows using ISO 27002 guidance; this gives you resilience and buyer confidence. Cross‑framework alignment ensures that when incidents occur or auditors ask questions, you have real evidence. This alignment accelerates enterprise deals significantly.
FAQ
1. How do SOC 2 controls align with ISO 27002 controls?
SOC 2’s Trust Services Criteria correspond conceptually to categories of ISO 27002. For example, SOC 2’s access‑control criteria map to ISO 27002 controls 5.15 (Access control), 5.17 (Authentication information) and 5.18 (Access rights). Incident‑response criteria map to ISO controls 6.8 (Information security event reporting), 5.29 (Information security during disruption) and 5.30 (ICT readiness for business continuity). By identifying one‑to‑one or many‑to‑one relationships, teams can implement a single control (e.g., a documented incident‑response process) that satisfies both frameworks.
2. Is ISO 27002 the same as ISO 27001 for SOC 2 mapping?
No. ISO 27001 defines the requirements for establishing, implementing, maintaining and continually improving an ISMS, and certification confirms that your ISMS meets those requirements. ISO 27002 provides detailed control guidance and is often used with ISO 27001 but focuses on implementation rather than certification. When mapping SOC 2 controls, ISO 27002 offers the specific controls to reference; ISO 27001 ensures those controls are selected through risk management and embedded within an ISMS.
3. Why do enterprise buyers ask for both SOC 2 and ISO alignment?
Enterprise clients operate in multiple jurisdictions and industries, so they need evidence that a vendor meets both local and international standards. SOC 2 demonstrates that controls operate effectively over an observation period and satisfies U.S. audit expectations. ISO 27001/27002 offers globally recognised control guidance and is often required for doing business in Europe and Asia. Secureframe’s 2026 trends report found that ISO 27001 certification is gaining momentum, with 81 % of organisations reporting current or planned certification in 2025. Clients therefore request both SOC 2 reports and ISO certifications to cover regional regulatory requirements and assess vendor maturity.
4. Can one control satisfy both SOC 2 and ISO 27002?
Yes—when a control’s objective and implementation align with both frameworks. For example, a robust access‑management programme that enforces least privilege, requires multi‑factor authentication, logs access and performs periodic reviews can satisfy SOC 2 CC6.1/CC6.2 and ISO 27002 controls 5.15–5.18 simultaneously. Similarly, a documented incident‑response plan that covers detection, reporting, investigation and recovery can meet SOC 2’s incident‑management criteria and ISO 27002 controls 6.8, 5.29 and 5.30. The key is to ensure evidence demonstrates both design and operation over time.
5. How often should SOC 2 to ISO 27002 mappings be reviewed?
Review mappings at least annually or whenever your control environment, business processes or the frameworks themselves change. ISO 27002 was updated in 2022, introducing new controls and consolidating existing ones. The AICPA periodically revises SOC 2 points of focus. Additionally, new threats (e.g., AI‑driven phishing) and regulatory developments (e.g., HIPAA settlements) may require additional controls or evidence. Regularly revisiting your mapping ensures your programme remains current and audit‑ready.





.svg)






.svg)
.svg)