Most enterprise buyers ask service providers to prove that they can keep data safe and control how long it is stored. Without these proofs, due‑diligence reviews stall even when teams think they are ready on paper. As data protection laws mature and breach costs climb, retention practices have become a gatekeeper for business. In this SOC 2 Data Retention Guide I unpack how data retention sits at the core of trust in enterprise SaaS. The goal is to clarify what the SOC 2 framework expects, walk through practical steps for creating policies that support sales, and provide templates and answers to common questions. We will cover the requirements under the AICPA Trust Services Criteria, the link to confidentiality and privacy, intersections with regulations like GDPR and HIPAA, and common pitfalls. Throughout the article I share what our team at Konfirmity has learned from supporting more than six thousand audits and twenty‑five years of combined compliance work.
What Is SOC 2 and Why Data Retention Matters
Service Organization Control 2 (SOC 2) is part of the System and Organization Controls framework developed by the American Institute of Certified Public Accountants. It applies to cloud and service providers that handle customer information. A SOC 2 report shows that a company meets the Trust Services Criteria—security, availability, processing integrity, confidentiality, and privacy—through a formal external audit. Unlike SOC 1, which focuses on financial reporting, SOC 2 examines the broader information environment.

Confidentiality and privacy are optional criteria but they are increasingly in scope for enterprise SaaS providers because clients want assurance that their sensitive data will be managed carefully. The confidentiality criteria evaluate how organizations protect confidential information across its entire life cycle. That includes controlling access, applying encryption, establishing data classification, and putting retention and disposal procedures in place. The privacy criteria focus on personally identifiable information (PII) and require organizations to manage consent, data collection, and retention ethically. Security remains mandatory for every SOC 2 report and overlaps heavily with the other criteria.
Data retention is a foundational aspect of these criteria because it links security controls with compliance obligations. Confidentiality requires that sensitive information is kept only as long as necessary and then disposed of securely, while privacy demands that personal data is collected for a defined purpose and erased once that purpose is fulfilled. Auditors will look for clear policies that specify how data is stored, accessed, retained and deleted. Without these policies, organizations struggle to prove that they meet the Trust Services Criteria, which delays procurement and exposes them to regulatory penalties.
The Role of Data Retention in SOC 2
Data retention is the practice of managing information from creation through disposal. In the SOC 2 context, retention means answering three questions:
- What data do we have and how sensitive is it? Organizations need a data classification scheme that labels information such as logs, backups, configuration files, customer PII, and intellectual property. The AuditBoard guide notes that confidentiality controls include data classification, retention policies, encryption standards, and secure endpoints.
- How long should we keep each data type? SOC 2 does not prescribe fixed durations. It requires companies to define retention timelines based on business needs and applicable laws. Bright Defense points out that confidentiality controls include restricting access, defining retention timelines, and verifying secure deletion. The privacy criteria likewise govern the collection, use, retention and disposal of personal information.
- How will we protect data while stored and dispose of it at the end of its life? Secure storage involves encryption, role‑based access controls, tamper‑evident logging, and segregation of duties. Secure disposal means using methods such as cryptographic wiping or physical destruction and documenting these actions. AuditBoard lists retention and disposal procedures among the critical confidentiality controls.
When properly executed, a retention program supports other controls. For instance, log retention ensures that security events can be investigated, while retention policies for backups align disaster‑recovery planning with confidentiality requirements. Data retention also provides evidence for audits. Without audit logs and disposal records, it is difficult to prove that controls operated consistently over the observation period.
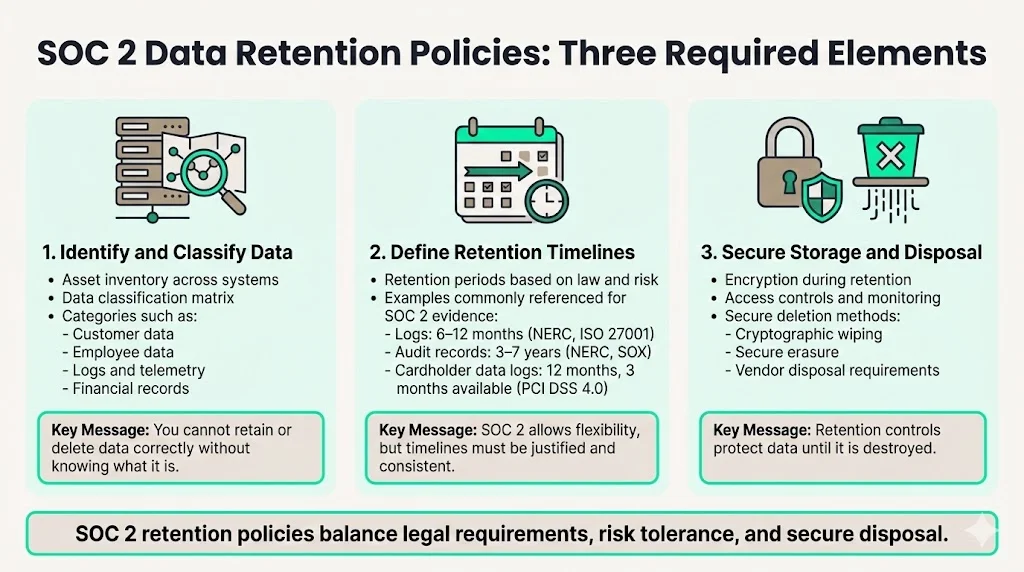
SOC 2 Data Retention Requirements
The AICPA Trust Services Criteria do not mandate specific durations for data retention. Instead, they require organizations to design and enforce policies that identify data types, assign retention timelines, and describe secure storage and disposal procedures. The Bright Defense guide explains that confidentiality controls entail restricting access to authorized personnel, defining retention timelines, and verifying secure deletion at the end of the lifecycle. Auditors expect to see that policies are applied consistently across all systems and that exceptions are documented.
Retention policies must address three key elements:
- Identification and classification of data types: Companies must maintain an asset inventory and a data classification matrix. AuditBoard’s step‑by‑step guide recommends starting with a data classification policy that defines all data across the organization.
- Retention timelines for each category: SOC 2 leaves the duration to the service provider’s discretion. Organizations typically base retention periods on legal requirements and risk tolerance. For example, many frameworks and regulations provide guidance: the North American Electric Reliability Corporation (NERC) specifies six months for log retention and three years for audit records; ISO 27001 recommends keeping at least twelve months of logs to demonstrate control effectiveness; the Sarbanes‑Oxley Act requires financial audit logs to be retained for seven years; PCI DSS 4.0 mandates twelve months of history with three months readily available for cardholder data. These examples illustrate typical durations used for SOC 2 evidence.
- Secure storage and disposal procedures: Retention policies must describe how data is protected during the retention period and the methods used to destroy it securely. Bright Defense highlights that retention and disposal controls involve keeping data only as long as necessary and deleting it using secure methods like cryptographic wiping. AuditBoard’s confidentiality controls similarly call for retention and disposal procedures and vendor management to ensure third parties follow comparable standards.
Trust Services Criteria Touchpoints
Data retention connects directly to several Trust Services Criteria:
- Confidentiality: This criterion requires companies to protect sensitive information by limiting its access, storage, and use. Retention policies demonstrate that data is stored securely and destroyed when no longer needed.
- Privacy: The privacy criteria focus on PII. Organizations must align retention with privacy laws and ensure that personal data is collected, used, retained, disclosed and disposed of lawfully. AuditBoard points out that privacy controls include consent management, data collection practices, and privacy notices.
- Audit and Evidence: Evidence of controls is essential for a SOC 2 report. Log retention is critical because it provides the proof needed to show that controls were operating consistently during the observation period. AuditBoard explains that logs help investigators understand what happened during incidents, and without them, organizations may not be able to prove compliance.
Industry and Regulatory Overlaps
Although SOC 2 does not impose fixed retention periods, organizations must align with external laws and frameworks. Here are some examples:
- GDPR: Article 5 of the European Union’s General Data Protection Regulation states that organizations must not store personal data longer than necessary. Recital 39 explains that controllers should establish time limits for erasure or periodic review. The GDPR does not specify exact periods but requires controllers to justify retention based on lawful purposes. Penalties for excessive storage can be significant; for instance, France’s data protection authority fined a clairvoyance company €250,000 for storing customer data six years after the relationship ended.
- HIPAA: The HIPAA Privacy Rule requires covered entities to retain certain records for six years from the date of creation or last effective date. This applies not only to medical records but also to documentation that proves compliance, such as policies, procedures, and authorizations. HIPAA also emphasizes that entities protect the privacy of Protected Health Information (PHI) through appropriate safeguards.
- ISO 27001: ISO 27001 requires organizations to produce and regularly review logs of user activities and security events (Clause A.12.4.1). While it does not specify retention durations, AuditBoard suggests that maintaining at least twelve months of logs helps meet the requirement and support incident response.
- NERC: Electric power providers must retain logs for six months and audit records for three years.
- SOX: The Sarbanes‑Oxley Act mandates that publicly traded companies keep audit logs for seven years.
- PCI DSS 4.0: Organizations handling payment card data must retain twelve months of log history, with three months immediately accessible.
These overlapping requirements often drive SOC 2 retention policies. For example, healthcare SaaS providers may adopt a six‑year retention period for logs containing PHI to satisfy HIPAA. Financial technology vendors may align with SOX by keeping audit logs for seven years. Global software firms subject to GDPR may justify shorter retention periods for PII but must document the rationale and implement periodic reviews.
Building a SOC 2‑Ready Data Retention Policy
Creating a retention policy involves four fundamental steps: defining scope, setting principles, assigning responsibilities, and integrating with broader controls.
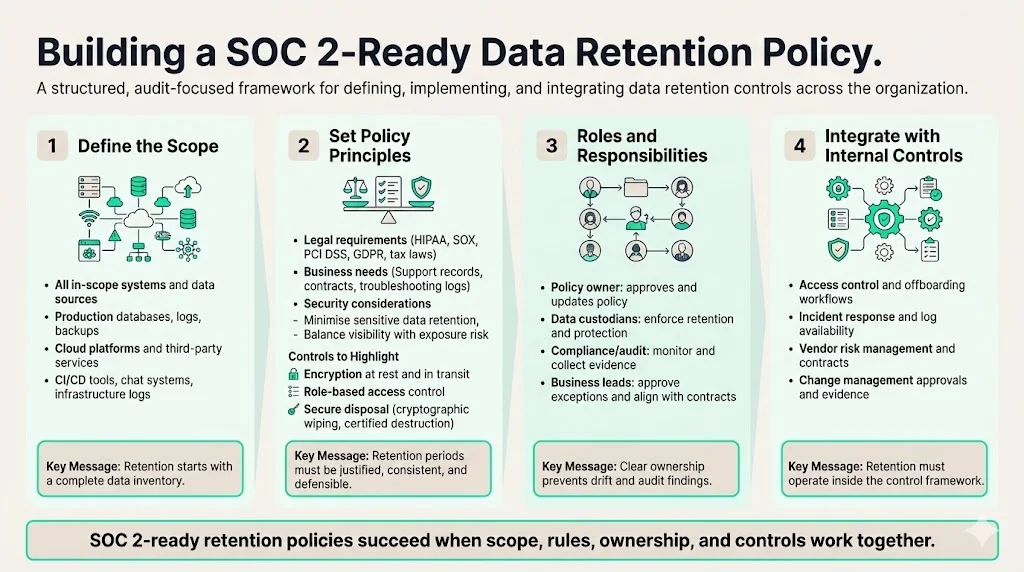
1) Define the Scope
Begin by identifying all systems and data types that fall within your SOC 2 scope. This includes customer‑facing applications, back‑office systems, cloud platforms, and third‑party services. Map each data source—such as production databases, logging systems, backups, configuration repositories, and employee records—to business processes and regulatory requirements. In our experience, SaaS vendors often overlook logs generated by infrastructure tools, chat platforms, and continuous integration pipelines, which can be critical for investigations. AuditBoard’s step‑by‑step guidance stresses the need for a complete inventory and classification of data based on sensitivity and compliance needsauditboard.com.
2) Set Policy Principles
Once you have defined the scope, determine the retention timelines for each category of data. Consider the following factors:
- Legal obligations: Align retention periods with applicable regulations such as HIPAA, SOX, PCI DSS, GDPR, and local tax laws. For example, if a jurisdiction requires retention of financial records for seven years, adopt that standard to avoid conflict.
- Business needs: Sales teams may need to retain customer support data to meet contractual obligations. Engineering teams may require system logs for at least twelve months to troubleshoot incidents. At Konfirmity we typically see organizations adopt one to two years of log retention for operational visibility, matching ISO 27001 and PCI DSS recommendations.
- Security considerations: Longer retention improves investigative capability but increases exposure risk. Limit retention of sensitive PII to the minimum necessary to comply with obligations like GDPR’s storage limitation principle.
Define how data is protected during retention. Mandate encryption at rest and in transit, role‑based access controls, and separation of duties between those who manage encryption keys and those who administer storage. Specify disposal procedures, such as secure deletion using cryptographic wipe tools, decommissioning of media, or verified destruction by a certified vendor. Document the chain of custody for all disposal activities to provide evidence during audits.
3) Roles and Responsibilities
A robust policy clearly assigns ownership:
- Policy owner: Typically the CISO or head of compliance, responsible for drafting, approving, and updating the policy.
- Data custodians: Teams that manage systems containing customer data (e.g., DevOps, database administrators, IT operations) are accountable for implementing retention rules, configuring systems to enforce timelines, and ensuring encryption and access controls.
- Compliance or audit function: This team monitors adherence, conducts periodic reviews, and produces evidence for auditors. They also train staff on policy requirements and coordinate across legal, security, and engineering teams.
- Business unit leads: Managers of customer success, finance, and product must ensure retention aligns with contract obligations and customer commitments. They approve exceptions and manage communication with clients about data deletion.
4) Integration with Internal Controls
Retention policies should be integrated with broader risk management and privacy efforts, not treated as an isolated document. Map retention requirements into your organization’s control framework and risk register. For instance:
- Link retention to access control reviews so that when a user is offboarded, their associated data is flagged for disposal. This prevents orphaned data from lingering indefinitely.
- Integrate retention with incident response. Logs must be available for investigation and reporting; define how long they remain accessible and when they are archived.
- Align retention with vendor risk management. Contractual agreements should specify how vendors handle and destroy your data. AuditBoard recommends including third‑party controls for confidentiality and privacy.
- Tie retention to change management. If you modify the retention period for a system, update the policy and notify stakeholders. Use ticketing tools to capture approvals and maintain evidence.
Step‑by‑Step Implementation Guide
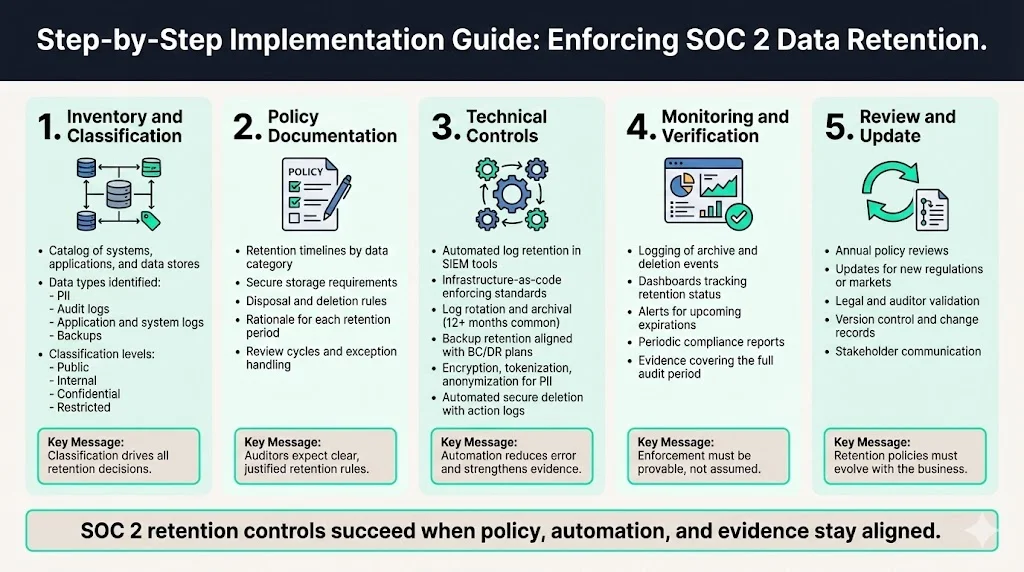
1) Inventory and Classification
Compile a catalog of all systems, applications, and data stores. For each item, identify the data types stored (e.g., PII, audit logs, application logs, database backups). Classify them based on sensitivity and compliance needs—public, internal, confidential, restricted. The Sprinto guide on SOC 2 notes that privacy criteria focus on how organizations collect, use, retain, disclose, and dispose of personal information, highlighting the importance of classification.
2) Policy Documentation
Draft a data retention policy that covers each data category. The policy should include definitions, retention timelines, secure storage requirements, and disposal protocols. Make sure to document the rationale for each retention period to demonstrate risk‑based decision making. Include procedures for periodic review and a mechanism to handle exceptions. Align the policy language with your privacy notice and contractual commitments.
3) Technical Controls
Automate retention whenever possible. Configure log management solutions (e.g., SIEMs) to enforce retention periods and archival. Use infrastructure‑as‑code tools to deploy standard configurations across environments. For system logs, set rotation and archival schedules—common practice is to store logs for at least twelve months for audit readiness. For backups, align retention with your business continuity plan and storage costs. For PII, implement encryption, tokenization, and anonymization to reduce exposure risk. Use automation scripts to trigger secure deletion once retention periods expire, generating logs of each action.
4) Monitoring and Verification
Retaining data is only part of the equation; you must also prove that retention rules are followed. Set up logging on retention actions themselves, including when data is archived or deleted. AuditBoard stresses that logs are indispensable for investigations and compliance. Use monitoring dashboards to track upcoming expiration dates and verify that deletions occur on schedule. Create periodic reports summarizing retention activity and share them with your compliance function. During SOC 2 audits, auditors will ask for evidence that policies were enforced consistently over the observation period.
5) Review and Update
Regulations, contracts, and business models evolve. Schedule policy reviews at least annually or whenever there are major changes in your environment. Assess whether retention periods remain appropriate, especially when entering new markets with different regulations. For example, if you expand into healthcare, you may need to adopt HIPAA’s six‑year retention requirement for logs. Similarly, new privacy laws may shorten permissible retention for PII. Engage legal counsel and external auditors to validate changes. Maintain version control and ensure that all stakeholders are aware of updates.
Templates and Practical Tools
Below are two sample templates: a data retention policy outline and a retention schedule table. These can be copied into your compliance documentation and adapted to your organization’s needs.
Sample Data Retention Policy Template
- Policy Overview: Provide a brief statement on why data retention is important for your company and how the policy supports SOC 2 controls, confidentiality, privacy, and applicable laws.
- Definitions: Define key terms: personal data, confidential data, log data, backups, retention, disposal, encryption, role‑based access, etc.
- Scope: Describe which systems, data types, business units, and third‑party services are covered by the policy. Reference your asset inventory.
- Retention Requirements: For each data category, state the retention period, the legal or business rationale, and the responsible team.
- Security During Retention: Outline encryption standards, access controls, monitoring, and any segregation of duties.
- Deletion and Disposal Procedures: Describe secure deletion methods (cryptographic wiping, physical destruction) and documentation of deletion events.
- Roles and Responsibilities: Identify policy owners, custodians, compliance officers, and business unit leads along with their tasks.
- Training and Awareness: Require periodic training for employees on retention obligations and secure data handling.
- Review and Update:Describe the schedule for policy review and update procedures.
Retention Schedule Example
Sample Deletion and Disposal Checklist
- Confirm that data has reached the end of its retention period (via automated job or manual review).
- Verify that no legal holds apply to the data.
- Use secure wiping tools or certified destruction services to destroy the data.
- Record the deletion event in the audit log, including timestamp, system, data category, and responsible individual.
- Review logs of deletion events periodically for completeness and anomalies.
Common Challenges and How to Overcome Them
- Balancing Legal Retention With Minimal Storage: Organizations often hold on to data longer than necessary because they fear losing evidence. However, privacy laws like GDPR require companies to keep data only as long as needed. The key is to categorize data accurately and assign retention periods based on regulatory requirements, contractual obligations, and risk tolerance. Use automation to delete data promptly once the period ends. Document exceptions and involve legal counsel for ambiguous cases.
- Managing Large Data Volumes: Log and backup data can accumulate quickly, causing storage costs to rise and making it harder to produce evidence. Adopt tiered storage—store recent logs in high‑speed systems and archive older logs in cost‑effective cold storage. AuditBoard suggests that logs should be readily available and capable of being produced as evidence even when archived. Implement compression and indexing to optimize storage.
- Aligning Across Departments: Data retention touches security, legal, engineering, product, and customer success. Misalignment leads to inconsistent practices. Establish a cross‑functional committee to own retention. Provide training so that each department understands the policy. Use centralized ticketing and documentation to track retention actions and ensure visibility.
- Vendor Compliance: Many SaaS providers rely on third‑party vendors for hosting, analytics, and support. If a vendor fails to delete data when required, your compliance is at risk. Include retention requirements in contracts, perform regular vendor assessments, and require attestation of deletion. AuditBoard mentions that vendor management is a key aspect of confidentiality and privacy controls.
- Evidence Collection During Observation Periods: A SOC 2 Type II audit includes an observation window of six to twelve months. If retention policies are not enforced consistently during this period, auditors may issue findings. Start implementing retention controls before the observation period begins. Use automation and monitoring to prevent gaps.
Conclusion
A mature data retention program is no longer optional for enterprise‑focused SaaS providers. Buyers and regulators expect companies to know exactly what data they have, why they keep it, and how they will delete it. The SOC 2 Data Retention Guide underscores that retention policies support the confidentiality and privacy criteria of the AICPA’s Trust Services framework and intersect with multiple regulations. Defining retention periods, applying secure storage and disposal, and integrating these controls into everyday operations help build trust and unlock sales.
In my experience leading Konfirmity, the companies that succeed are those that treat security as a core operating principle, not an afterthought. They implement controls inside their infrastructure, automate evidence collection, and maintain them year‑round. They avoid the pitfall of “compliance manufacturing” that produces paper‑thin policies with no operational substance. Instead, they build durable programs that stand up to auditors, buyers, and attackers. When you start with security and accountability, compliance and data retention follow naturally.
FAQs
1) What is the SOC 2 data retention policy?
A SOC 2 data retention policy is a document that outlines how an organization manages information throughout its lifecycle to meet the Trust Services Criteria. It identifies data types, defines how long each type is kept, and specifies secure storage and disposal methods. Retention policies are not one‑size‑fits‑all; they must reflect the organization’s legal obligations, contractual commitments, and risk appetite. Confidentiality controls require defining retention timelines and verifying secure deletion, while privacy controls govern the collection, use, retention, disclosure and disposal of personal information.
2) What is the 7‑year retention rule?
SOC 2 itself does not mandate a seven‑year retention period. However, certain laws and frameworks do. The Sarbanes‑Oxley Act requires publicly traded companies to keep financial audit logs for seven years. Many organizations adopt this as a baseline for logs and financial records even if SOC 2 is the primary framework. For medical records under HIPAA, the requirement is six years. The right retention period depends on the data type and applicable laws.
3) How long is a SOC 2 report valid?
A SOC 2 report does not technically expire, but it reflects a snapshot of control effectiveness over a defined period. Industry practice treats SOC 2 Type II reports as valid for twelve months after the end of the observation period. After that, customers and auditors expect a new report. Because threats evolve and controls may drift, organizations typically schedule annual audits to maintain trust and show continuous improvement.
4) What is the recommended data retention period?
There is no universal answer. Retention periods should be based on legal requirements, contractual obligations, business needs, and risk assessments. Common practice is to retain system logs for at least 12–24 months, backups in line with business continuity plans, and personal data only as long as required to fulfill the original purpose. HIPAA requires six years for records relating to PHI, while SOX demands seven years for financial audit logs. Your policy should clearly define and document these durations to support SOC 2 audits and demonstrate accountability.





.svg)






.svg)
.svg)