Most enterprise customers will not accept promises about security at face value. In an era where the global average cost of a data breach reached USD 4.88 million in 2024 and one third of companies surveyed by PwC experienced breaches exceeding US$1 million, buyers are rightfully sceptical. Instead of marketing claims, they want to see concrete evidence that systems are protected, resilient and compliant. SOC 2 auditing provides a structured way to present that evidence, yet too many vendors treat it as a paperwork exercise. This guide explains why clear SOC 2 evidence requirements matter, how auditors use evidence to test controls and how strong evidence shortens enterprise sales cycles. The article is written for security and engineering leaders selling to large enterprises who need to understand what “audit‑ready” means in practice.
Why enterprise customers care so much about proof, not promises
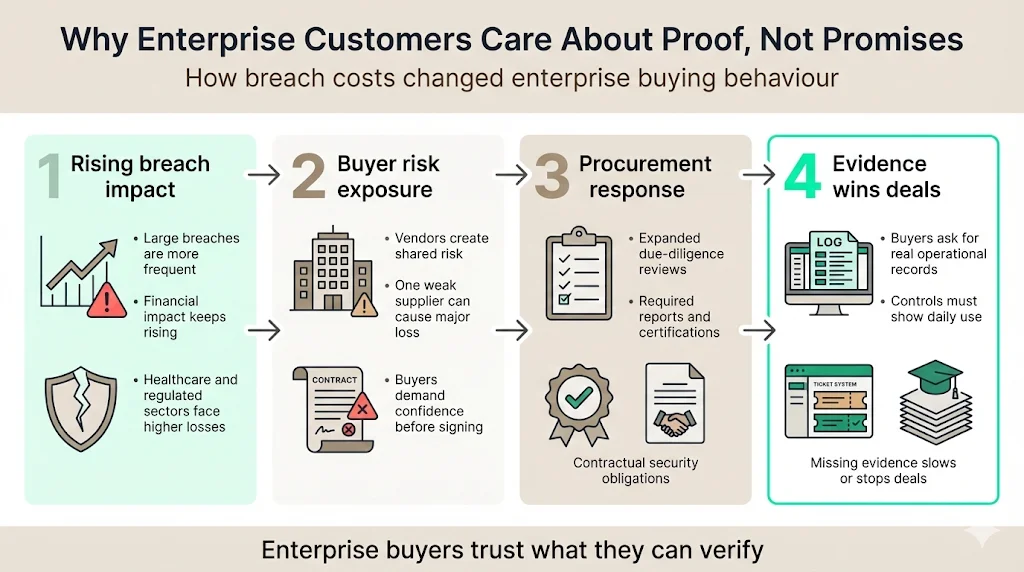
Public reports of mega-breaches and high-profile ransomware incidents have increased both the cost and the risk of doing business. PwC’s 2024 Global Digital Trust Insights survey found that the proportion of businesses experiencing a data breach costing more than US$1 million jumped from 27 % to 36 %. IBM’s 2024 Cost of a Data Breach Report showed that breach costs increased 10 % year-over-year to an average of USD 4.88 million, the largest jump since the pandemic. Healthcare organizations were hit even harder, with average breach costs reaching USD 5.3 million. For enterprise buyers, these figures translate into hard requirements: before procuring a software or services vendor, they need to trust that the provider’s security program will not expose them to similar losses.
Procurement teams have responded by expanding due-diligence questionnaires and requiring attestation reports before signing contracts. Larger customers now routinely ask for a SOC 2 report, ISO 27001 certification, HIPAA Business Associate Agreements (BAAs) or GDPR Data Processing Agreements (DPAs). They then verify controls and evidence beyond the report itself. In our experience at Konfirmity, buyers often request log files, change management tickets, training records and penetration test results to confirm that controls actually work. Without operational evidence, deals stall and procurement teams look elsewhere.
How SOC 2 evidence supports trust during security reviews and procurement

SOC 2 is an attestation framework defined by the American Institute of Certified Public Accountants (AICPA). It requires service organizations to design and operate controls that protect customer data according to a set of Trust Services Criteria (TSC). A SOC 2 report, issued by an independent CPA firm, demonstrates that the organization has implemented appropriate controls. But the report is only as convincing as the evidence behind it. Auditors base their opinion on logs, records and test results, not on policy statements alone. According to a guide from Cynomi, auditors require access logs, permission change history, security policies, risk assessments, training records, incident response documentation and backup schedules. For Type II audits, evidence must cover the observation period (often 6–12 months) and include population listings, sample selections and proof of remediation. Evidence of this depth signals to customers that controls are not just designed correctly but are operating effectively over time.
Konfirmity sees this dynamic every day in enterprise sales. Our clients report that when they package their SOC 2 report with supporting evidence—such as quarterly access reviews, monthly vulnerability scan results, and documented incident responses—procurement teams complete security reviews faster. Without evidence, follow‑up questions drag on and deals slip into the next fiscal quarter. Evidence transforms trust from an aspiration into an operational reality.
What this guide covers and who it is for
This article provides a practitioner‑level breakdown of SOC 2 evidence requirements for companies selling to enterprise clients. It explains the difference between SOC 2 Type I and Type II from an evidence point of view, maps each Trust Services Criterion to the kind of proof auditors expect and offers step‑by‑step guidance on collecting evidence. It also highlights common mistakes that auditors and buyers notice and suggests tools and approaches to streamline evidence management. While the focus is on SOC 2, the principles apply to ISO 27001, HIPAA, GDPR and other frameworks that rely on control documentation and evidence. The guide speaks to CTOs, CISOs, compliance officers and business leaders who need to build or improve their evidence program to support enterprise sales.
Quick framing of SOC 2 Type I vs Type II from an evidence point of view
SOC 2 offers two types of attestation reports:
- Type I evaluates whether controls are designed effectively at a single point in time. It is a snapshot that answers the question: are the right policies and processes in place today? Because it examines design only, Type I audits can be completed in a matter of weeks. Evidence for Type I mainly includes policies, system descriptions and high‑level configuration screenshots.
- Type II assesses both the design and operating effectiveness of controls over a period, typically 3–12 months. This deeper review requires evidence of consistently enforced policies, logs and processes. Auditors want to see records of access reviews, vulnerability scans, incident responses and change approvals spanning the observation window. Venn’s SOC 2 guide notes that Type II reports are what customers in regulated industries usually ask for because they represent greater rigor and trustworthiness.
In general, Type I is useful as an initial assurance for early‑stage companies, but enterprise buyers increasingly require Type II. At Konfirmity, we advise most clients to plan for a Type II audit from the start; the observation period may begin with a shorter window (e.g., three months) and later extend to annual audits.
What Are SOC 2 Evidence Requirements?
Plain explanation of SOC 2 evidence
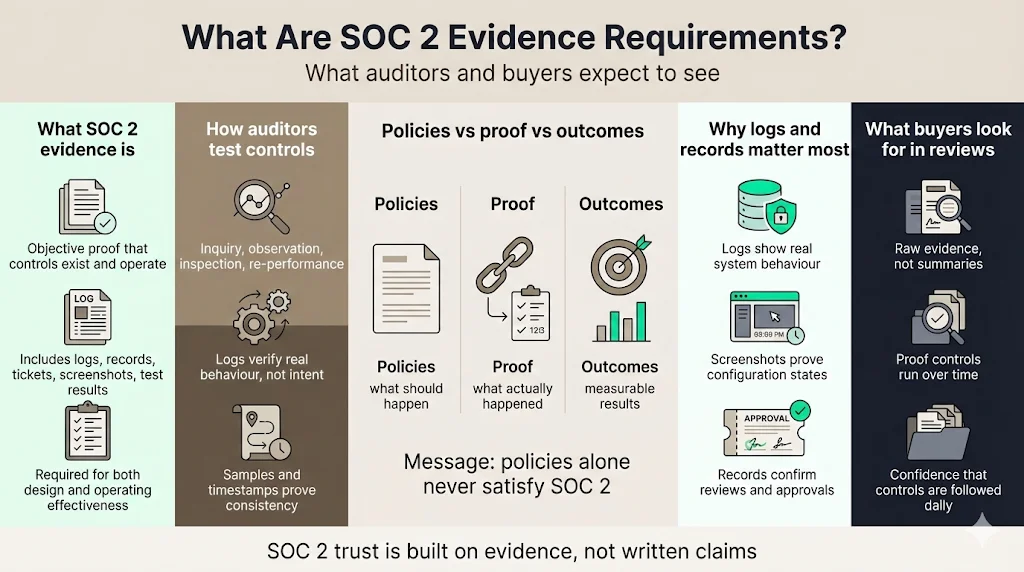
Evidence in the context of SOC 2 is any objective information that demonstrates that a control exists and operates as described. It includes policies, procedures, records, logs, tickets, screenshots and test results. According to Cynomi, auditors assess whether controls are designed effectively and operating consistently. To make that assessment, they expect specific evidence such as access logs, permission change history, information security and privacy policies, risk assessment reports, security awareness training records, incident response documentation, monitoring tool alerts and backup test results. For Type II, they also require population listings, sample selections, timestamps and evidence of remediation.
How auditors use evidence to test controls
Auditors use a combination of inquiry, observation, inspection and re‑performance to verify that controls work. Policies and written descriptions establish intent; logs, configuration settings, and audit trails provide proof. For example, an access-control policy might require multi‑factor authentication (MFA) for all admin accounts. Auditors will examine authentication logs to confirm MFA enforcement and may sample specific user accounts to verify configuration. Evidence of change management might include ticket histories, code commit logs and approval workflows. The purpose of evidence is to show that controls are not theoretical; they have been executed, monitored and updated when necessary.
Difference between policies, proof and outcomes
Policies articulate what should happen. Proof shows what did happen. Outcomes demonstrate the effect. Auditors and enterprise buyers know that policies without evidence are meaningless; this is why documentation alone cannot satisfy SOC 2. Vista InfoSec emphasises that organizations must provide formal evidence—documents, logs and records—that highlight implemented policies, procedures and measures to verify compliance. Logging and monitoring evidence matters more than written claims because it shows that teams follow policies consistently. Outcome evidence, such as reduced incident frequency or improved mean time to recover (MTTR), further demonstrates that the security program delivers results.
Why screenshots, logs and records matter more than written claims
Logs and records are immutable sources of truth. A well‑written policy may describe encryption requirements, but only a database configuration screen or API call demonstrates that encryption at rest is enabled. Screenshot evidence of a vulnerability scan, a ticket approval in a change management system or a record of a quarterly access review provide tangible proof that controls were executed. In the words of the Cynomi guide, the key is to show not just that policies exist, but that they’re being followed consistently. Enterprise customers increasingly request raw logs during security reviews because they know that paper controls can be manufactured quickly; logs reveal the operational reality.
SOC 2 Trust Services Criteria and Their Evidence Focus
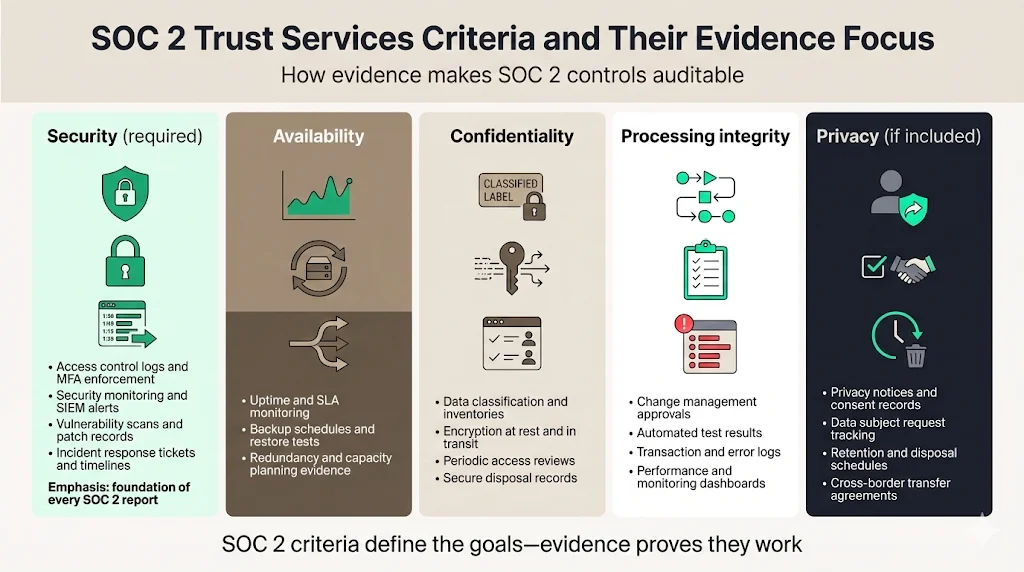
SOC 2 revolves around five Trust Services Criteria. While only Security is mandatory, many enterprise customers expect all five. The criteria define high‑level objectives; evidence makes these objectives auditable.
Security (Common Criteria)
Security is the foundation of SOC 2 and is required in every report. It focuses on protecting information from unauthorized access. Evidence should demonstrate that logical and physical access is controlled and monitored. Key evidence includes:
- Access control logs and role assignments: Authentication logs, MFA enforcement, and least‑privilege permission changes prove that only authorized users can access sensitive systems. Venn notes that security controls must cover logical access, physical safeguards, system configuration, vulnerability management and user behavior monitoring.
- Security monitoring records: Records of intrusion detection or SIEM alerts and sign‑offs showing that anomalies were investigated and resolved.
- Vulnerability management reports: Evidence of regular vulnerability scans, patch management activities and remediation tickets.
- Incident response documentation: Incident tickets, post‑mortem analyses and resolution timelines show how quickly and effectively the organization responds to threats. In a Type II audit, auditors check whether incidents were logged and handled according to the incident response plan.
Availability
Availability measures whether systems remain operational and accessible to meet service commitments. Evidence covers uptime, backups and recovery. Onspring’s guide explains that availability is about measuring how well infrastructure holds up under pressure. Required evidence includes:
- Uptime monitoring and SLA reports: Logs from monitoring tools demonstrating adherence to service level agreements (SLAs) and recovery time objectives (RTOs).
- Backup and disaster recovery tests: Backup schedules, retention policies and records from restore tests. Venn emphasises that availability controls should include documented business continuity and disaster recovery plans with tested restorations.
- Capacity and redundancy: Proof of failover configurations, multi‑region deployments or load‑balancing architectures that maintain service in the event of failures.
Confidentiality
Confidentiality governs the protection of sensitive information by restricting access, storage and use. Evidence includes data classification policies, encryption settings and access control lists. Onspring notes that confidentiality controls may include data encryption, non‑disclosure agreements, role‑based access policies and access control lists, and auditors will assess whether access rights are reviewed regularly and whether sensitive fields are masked or redacted. Evidence should show:
- Data classification and inventory: Policies and inventories that classify data by sensitivity and document where it resides.
- Encryption configurations: Screenshots or configuration files showing encryption at rest and in transit, key management practices and rotation schedules.
- Access reviews: Records of quarterly or monthly reviews of user permissions, including removal of access for terminated employees.
- Data handling and disposal logs: Records demonstrating that confidential data is stored appropriately and securely destroyed when no longer needed.
Processing Integrity
Processing integrity ensures that systems operate correctly, processing data completely, accurately and in a timely manner. Evidence should show that data transformations, transactions and workflows have controls against errors, omissions and unauthorized changes. Onspring states that controls include quality assurance testing, change management procedures, transaction logging, error logging and input validation. Evidence includes:
- Change management tickets and approval logs: Demonstrate that all production changes follow a defined process with approvals and rollback plans.
- Automated test results: Reports from unit tests, integration tests and user acceptance tests that verify software functions correctly.
- Transaction and error logs: Audit trails showing that transactions are recorded and validated, with anomalies identified and corrected.
- System monitoring dashboards: Screenshots or exports showing throughput metrics, latency and error rates.
Privacy (If Applicable)
Privacy is concerned with the collection, use, retention and disposal of personal information. Evidence must demonstrate compliance with privacy policies and applicable laws such as GDPR or HIPAA. Onspring explains that privacy controls may include policies governing user rights, data retention schedules, secure disposal and consent management platforms. Evidence includes:
- Privacy notices and consent records: Records showing that users were informed and consented to data processing activities.
- Data subject request logs: Documentation of requests for access, correction or deletion of personal data and how they were fulfilled.
- Retention and disposal schedules: Evidence that personal data is retained only as long as necessary and securely disposed of thereafter.
- Cross‑border transfer agreements: DPAs and standard contractual clauses demonstrating lawful international data transfers.
Step‑by‑Step Breakdown of SOC 2 Evidence Requirements
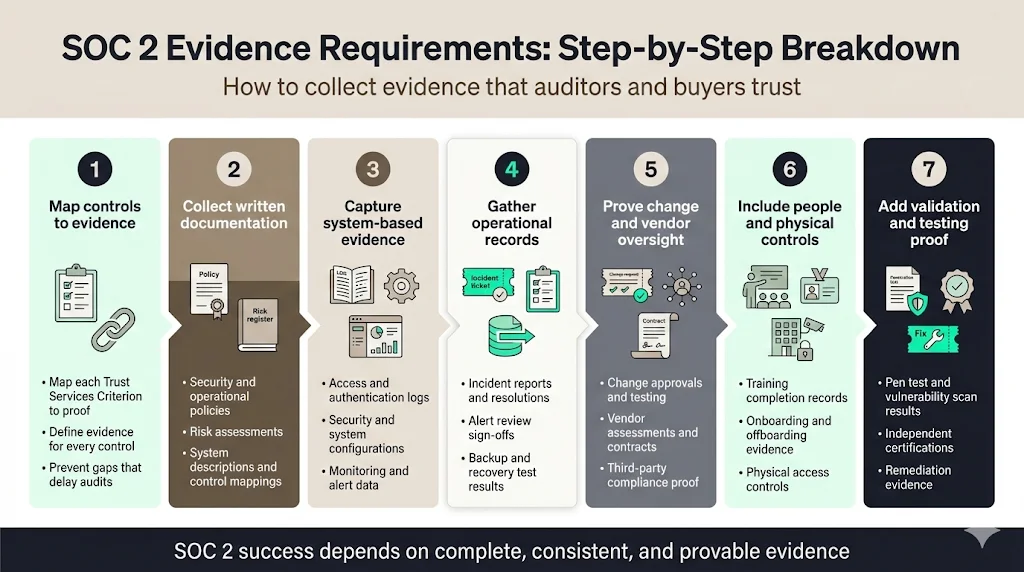
Step 1: Map controls to evidence
The first step is to map each control to specific evidence. For every requirement in the Trust Services Criteria, identify the artifact that proves compliance. Cynomi provides a useful mapping: for example, the Security criterion requires multi‑factor authentication; evidence includes authentication logs and access policy documentation. Availability requires disaster recovery testing; evidence is recovery plans and test logs. Processing Integrity requires input validation; evidence is code documentation and test cases. This mapping ensures that no control is left without proof. Konfirmity’s experience across 6,000+ audits shows that missing evidence is the most common cause of audit delays.
Step 2: Collect written documentation
Written documentation forms the foundation of evidence. This includes:
- Policies and procedures: Information security policy, access control policy, incident response plan, change management policy, business continuity and disaster recovery policies. Vista InfoSec notes that administrative policies related to security programs—including incident management, data classification and physical access policies—must be in place.
- Risk assessments: Regular risk assessments document identified threats, vulnerabilities and mitigation strategies. HIPAA guidance emphasises that a complete and thorough Security Risk Analysis is foundational and must be updated regularly.
- Management descriptions: Detailed descriptions of the system, including infrastructure, data flows, processes and control objectives. Vista InfoSec explains that management description documents provide auditors with a detailed view of the organization’s systems and controls.
- Statement of applicability (SoA): For ISO 27001, the SoA maps each Annex A control to its implementation status; while not part of SOC 2, maintaining a similar mapping for SOC 2 controls can help cross‑framework alignment.
Step 3: Capture system‑based evidence
System‑based evidence comes directly from technology and includes logs, configurations and monitoring data. Auditors expect evidence at a granular level. Venn’s guidance states that evidence may include system configuration screenshots, access logs, change records, monitoring alerts, policy documents and training records. Examples include:
- Access logs: Export authentication and authorization logs from identity providers (e.g., Okta, Azure AD) showing login attempts, MFA challenges and account lockouts.
- System configurations: Take snapshots or exports of security settings, such as encryption at rest, network firewall rules and IAM role definitions.
- Audit trails: Ensure that application and infrastructure logs are retained for the observation period. Evidence should demonstrate retention and tamper‑proof storage.
- Monitoring dashboards: Provide metrics and alerts from SIEMs, endpoint detection and response (EDR) tools and vulnerability scanners.
Konfirmity uses automated collectors to pull logs and configuration data continuously, reducing manual effort and ensuring completeness. This approach also helps maintain evidence when teams or systems change.
Step 4: Gather operational records
Operational records show how people and processes perform over time. Vista InfoSec highlights the need for operational documents, including data flow diagrams, risk management programs, compliance programs, privacy documents and incident management records. Additional records include:
- Incident tickets and reports: Evidence of incidents, root-cause analyses and corrective actions. These records demonstrate adherence to incident response procedures.
- Monitoring and alert review sign‑offs: Evidence that security alerts were reviewed and resolved. A simple screenshot of a SIEM dashboard is insufficient; auditors expect sign‑off records showing that designated staff reviewed alerts and documented their actions.
- Backup and recovery procedures: Records of backup jobs, restoration tests and disaster recovery exercises. Availability evidence is strongest when it shows both the plan and results of tests.
- Performance and capacity reports: Reports showing that the organization monitored uptime, throughput and resource utilization and addressed issues proactively.
Step 5: Prove change and vendor oversight
Change management and vendor oversight are areas where auditors often find gaps. Evidence should include:
- Change management tickets and approval records: Systems such as Jira or ServiceNow should show request, approval, testing and deployment for each change. Code repositories can provide commit logs and pull request approvals.
- Testing and rollback evidence: For major changes, include test plans, test results and evidence of fallback procedures. Onspring notes that change-management procedures and transaction logging ensure processing integrity.
- Vendor risk management documentation: Contracts, service level agreements and third‑party security questionnaires. Venn emphasises that SOC 2 compliance extends to third parties and recommends conducting due diligence and maintaining vendor inventories. Evidence may include vendor assessment reports, contract clauses requiring security controls and SOC 2 reports from critical vendors.
- Third‑party risk proof: For healthcare, this includes Business Associate Agreements (BAAs). HIPAA guidance warns that during audits, organizations have only ten days to supply documentation, including policies, BAAs and proof of training.
Step 6: Include people and physical controls
People and physical controls are often overlooked but essential. Evidence must show that staff are properly trained and facilities are secure.
- Training records: Evidence that employees completed security and privacy training, including the date, topics covered and attendance. HIPAA audits expect detailed training documentation with authenticated participant lists. For SOC 2, auditors want to see role‑based training for developers, operations staff and executives.
- Onboarding and offboarding records: Proof that background checks were performed, access was provisioned based on least privilege and revoked promptly upon termination. Vista InfoSec mentions HR documentation including evidence of removing physical and system access for terminated employees.
- Physical security: Evidence of visitor logs, badge records, CCTV logs and physical access controls for data centers or offices. While many organizations operate in the cloud, co‑location sites and office spaces still need physical security evidence.
Step 7: Add validation and testing proof
Validation and testing evidence strengthens confidence in controls. This includes:
- Penetration test and vulnerability scan results: Reports showing identified vulnerabilities and remediation actions. Provide summary results and detailed remediation tickets.
- Independent audit or certification reports: ISO 27001 certificates, HIPAA compliance attestations, PCI DSS certifications and GDPR audit reports. While these frameworks are distinct, evidence can be reused across them when controls overlap.
- Internal audit reports and test results: Evidence from internal audits or control testing performed by the risk or compliance team. For example, results of quarterly access reviews, code reviews or configuration audits.
- Remediation evidence: Tickets, code commits and deployment logs demonstrating that issues identified in tests were addressed. Cynomi advises being ready with proof of remediation—tickets, commits and approvals—for Type II evidence.
SOC 2 Evidence Examples by Control Type

Access Controls
Access controls protect systems by limiting who can log in and what they can do. Evidence should include:
- Login logs: Authenticator logs from identity providers, showing successful and failed login attempts and MFA usage.
- Role change records: Documentation of role assignments and changes, including approvals.
- Offboarding proof: Records showing that user accounts were disabled or removed when employees or contractors left. For HR controls, Vista InfoSec emphasises the need to document removal of physical and system access for terminated employees.
- Access reviews: Evidence of periodic reviews (monthly or quarterly) that validate user permissions and confirm least‑privilege principles.
Security Monitoring
Security monitoring tracks events and anomalies. Evidence includes:
- Alert logs: Logs of security alerts from SIEM or EDR systems. Provide context such as severity and resolution steps.
- Review sign‑offs: Records showing that analysts reviewed alerts, documented findings and escalated incidents when necessary. Venn notes that centralised logging, anomaly detection and real-time alerting are primary security controls.
- Incident follow‑ups: Post‑incident reports, root‑cause analyses and corrective action plans demonstrating continuous improvement.
Change Management
Change management ensures that updates to systems are authorized, tested and documented. Evidence should include:
- Ticket screenshots: Screenshots of change tickets with status, approvals and links to code commits or deployment scripts.
- Approval records: Evidence that appropriate stakeholders reviewed and approved changes before deployment.
- Deployment logs: Automated deployment logs showing successful completion, test results and rollback procedures.
- Separation of duties: Records showing that developers cannot approve their own changes and that code reviews are performed by independent engineers.
Vendor Risk Management
Vendor risk management is critical because third parties can introduce vulnerabilities. Evidence includes:
- Vendor reviews: Assessments of vendor security posture, including SOC 2 reports, ISO 27001 certificates, or penetration test results.
- Security questionnaires: Completed questionnaires evaluating the vendor’s controls and practices.
- Contract clauses: Contracts or BAAs that require vendors to maintain security controls, notify of breaches and allow right to audit. HIPAA guidance notes that organizations should centralize BAAs and be able to produce them within ten days during an audit.
- Third‑party monitoring: Logs or reports demonstrating ongoing monitoring of vendor performance and compliance.
Evidence Collection Timelines: Type I vs Type II
Evidence timelines differ significantly between Type I and Type II. As Secureframe explains, Type I looks at controls at a specific point in time. Evidence is collected once and does not need to demonstrate continuous operation. Type I audits are ideal for quickly proving that basic controls exist, and they can be completed in a matter of weeks.
For Type II, auditors evaluate whether controls operated effectively over a period—typically three to twelve months. Evidence must cover the entire observation window. Venn’s guide clarifies that this deeper review requires evidence of consistently enforced policies, logs and processes. Auditors may sample specific days, weeks or months within the period to verify continuous operation. They might request population listings (all change tickets during the period), select random samples and inspect supporting evidence (approvals, commits) to verify compliance. Consequently, teams must maintain complete records and ensure that logs are retained for the entire window. Continuous evidence collection is crucial; manual snapshots at the end of the period often miss data.
What gets sampled and why
During a Type II audit, auditors cannot inspect every record. They use sampling to gain reasonable assurance that controls operate consistently. For example, they might sample a subset of user access changes and verify that each change followed the approval process. They might sample vulnerability scans across the period to see if scans were performed regularly and that findings were remediated. Sampling techniques vary by auditor, but evidence must be complete enough to support any sample. Incomplete logs or missing tickets raise exceptions. Our team recommends over‑collecting evidence to reduce the risk of gaps.
Common SOC 2 Evidence Mistakes Enterprise Auditors Catch
Based on Konfirmity’s delivery of 6,000+ audits, we see recurring pitfalls that delay or jeopardize certifications:
- Policies without proof: Organizations often produce policies but no logs or records showing they are enforced. Auditors will flag this. Venn notes that evidence should include system configuration screenshots and logs, not just policies.
- Logs that stop too early: Logs must cover the full observation period. If log retention is only 30 days, a six‑month audit window will have gaps. Set retention policies that match your SOC 2 timeline.
- Manual processes with no record: Many teams conduct manual reviews (e.g., quarterly access reviews) via meetings or emails without capturing evidence. Always record the review, list participants, decisions and date.
- Evidence that doesn’t match control wording: If a control requires quarterly reviews, providing annual reports will result in an exception. Map controls carefully and collect evidence that matches frequency and scope.
- Stale or inconsistent documents: Old policies, outdated org charts or mismatched versions of procedures create confusion. Centralize documentation and update it regularly. HIPAA guidance stresses that policies should be specific to the organization and stored centrally for easy access.
How to Prepare SOC 2 Evidence for Enterprise Security Reviews
Enterprise buyers often request evidence outside the formal audit, especially during vendor risk assessments. Preparing evidence proactively accelerates sales cycles:
- Package SOC 2 reports with supporting proof: When sharing a SOC 2 report under NDA, include evidence artifacts such as sample access reviews, vulnerability scan summaries and incident response procedures. This demonstrates transparency and reduces follow‑up questions.
- Use evidence to speed vendor risk reviews: Provide customers with vendor risk management documentation showing that you evaluate your own suppliers, maintain BAAs or DPAs, and conduct security questionnaires. Venn emphasises that third‑party management must be included in SOC 2 compliance; buyers appreciate seeing this practice.
- Be prepared for custom requests: Buyers may ask for proof of specific controls (e.g., encryption at rest for a healthcare customer). Maintaining organized evidence allows you to respond quickly.
- Redact sensitive details: When sharing logs, ensure sensitive information is redacted. Focus on showing timestamps, actions and outcomes without exposing secrets.
Tools and Systems That Help Manage SOC 2 Evidence
GRC platforms vs. manual tracking
Managing evidence manually using spreadsheets, shared drives and email threads is labor‑intensive and error‑prone. Venn points out that manual evidence collection is one of the most time‑consuming parts of SOC 2 and leads to delays and inconsistencies. Governance, Risk and Compliance (GRC) platforms automate evidence collection, enforce workflows and centralize documentation. Examples include tool suites like Secureframe, Vanta, Drata and TrustCloud. These systems integrate with cloud providers, identity management platforms and ticketing systems to pull logs automatically. They also provide dashboards showing control status and evidence coverage.
Automating evidence collection
Automated collectors can capture system configurations, access logs, change records and vulnerability scan results without manual intervention. This reduces the risk of missing data and ensures evidence covers the entire observation period. Venn describes how secure enclave technology captures configuration states, enforcement logs and endpoint posture data directly from a protected workspace. Such automation creates auditor‑ready evidence while respecting user privacy. Konfirmity deploys agents within customers’ stacks to collect evidence continuously, reducing internal workload by up to 75 % compared to manual processes. We estimate that our managed service consumes around 75 hours per year of client involvement versus 550–600 hours for self‑managed SOC 2 readiness.
Keeping evidence consistent across audit cycles
Evidence management is not a one‑and‑done effort. Controls evolve as systems change, and evidence must reflect those changes. Regular internal audits and control reviews help ensure evidence remains complete and current. Venn advises organizations to perform periodic internal reviews and maintain structured workflows to track and store evidence centrally. Documenting remediation and updating control mappings after each audit prevents last‑minute scrambling. Tools that support version control for policies and evidence help teams maintain consistency across annual audits.
Final Thoughts
Enterprise buyers and healthcare customers have learned to look past promises and focus on proof. SOC 2 evidence requirements force organizations to design, operate and document real security controls. Clean, comprehensive evidence builds buyer confidence and shortens deal cycles. Conversely, weak evidence or missing logs raise red flags and invite deeper scrutiny. The most effective programs treat security as an operational discipline rather than a compliance exercise.
At Konfirmity, we have supported more than 6,000 audits and have over 25 years of combined expertise in security and compliance. We see that companies who start with security and arrive at compliance—implementing controls inside their stack and maintaining continuous monitoring—experience smoother audits and faster sales. Our human‑led, managed service delivers outcomes as a service: we execute control implementation, run the program year‑round and keep you audit‑ready. We don’t just advise—we operate. By investing in evidence collection and integrating it into daily workflows, organizations avoid the yearly fire drill and turn compliance into a trust accelerant.
Frequently Asked Questions About SOC 2 Evidence Requirements
1) What evidence is required for SOC 2?
Evidence includes policies, risk assessments, security training records, system configurations, access logs, change management tickets, monitoring alerts, incident reports, backup and recovery test results and vendor management documentation. For Type II audits, the evidence must cover the entire observation period and include proof of remediation.
2) How detailed should SOC 2 evidence be?
Evidence should be clear enough for an auditor to follow the full trail without guessing. Cynomi explains that auditors need specific evidence like access logs, permission change history, security policies, risk assessment reports, training records and incident documentation. Logs should include timestamps and user identifiers; tickets should show approvals, dates and outcomes. Provide population listings and sample selections when asked.
3) Who reviews SOC 2 evidence?
Independent CPA firms perform SOC 2 audits. However, enterprise customers and their security teams often review evidence as part of procurement due diligence. They may request additional proof beyond the audit report, especially when the vendor handles regulated data.
4) How often is SOC 2 evidence collected?
For Type II audits, evidence should be collected continuously. Venn notes that the observation period can range from three to twelve months, and auditors expect evidence covering this entire period. Regular internal reviews and automated evidence collection ensure readiness for audits and customer inquiries at any time.





.svg)






.svg)
.svg)