Microservices have become the default pattern for modern SaaS platforms. According to survey data, 85% of enterprises now deploy microservices and manage complex applications with numerous services. Microservices promise autonomy, rapid deployment and infinite scaling, but they also multiply entry points. Every service exposes its own API, and cross‑service calls happen over the network, increasing the attack surface and requiring careful authentication, authorisation, encryption and observability. In 2023 a report showed that API calls represented 71% of all web traffic and companies had to manage an average of 421 APIs, with machine‑learning discovery finding 30.7% more endpoints than teams reported. Attacks targeting API business logic accounted for 27% of attacks, up 10% from the previous year.
At the same time, enterprise buyers insist on rigorous assurance. SOC 2 is one of the most recognised frameworks in North America. A 2025 Vanta survey found that 85% of enterprise buyers require a SOC 2 report before signing contracts and 70% of deals are delayed or lost when vendors lack this assurance. SOC 2 provides confidence that a service organisation has designed and operates controls across security, availability, processing integrity, confidentiality and privacy. For SaaS providers, SOC 2 is no longer optional; it’s a gatekeeper for revenue.
This guide unpacks the intersection of microservices and SOC 2. We’ll discuss why distributed architectures introduce unique compliance challenges, map trust services criteria to microservices controls, and walk through a step‑by‑step plan to achieve a successful SOC 2 audit. Throughout the discussion you’ll see checklists, real‑world examples and patterns drawn from Konfirmity’s experience delivering managed compliance programmes. By the end, you’ll understand how to build a durable control environment that satisfies auditors and accelerates enterprise sales.
What Is SOC 2 and How It Applies to Microservices
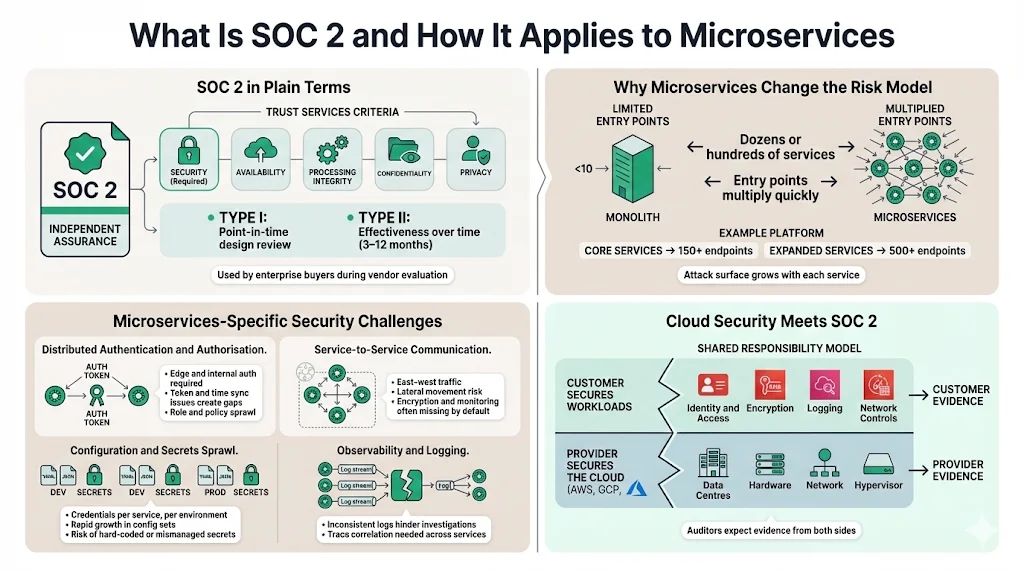
SOC 2 in Plain Terms
SOC 2 is an attestation framework developed by the American Institute of Certified Public Accountants (AICPA). Its purpose is to assess whether a service organisation’s controls are suitably designed and operating effectively. SOC 2 reports are organised around five Trust Services Criteria (TSC): security (required), availability, processing integrity, confidentiality and privacy. Security is mandatory; the other criteria are optional and depend on customer needs. A Type I report evaluates control design at a specific point in time, while a Type II report evaluates design and operating effectiveness over a period (typically 3–12 months).
SOC 2 fits into corporate risk management by providing third‑party assurance to customers and regulators. Enterprise clients use SOC 2 reports to evaluate vendors before procurement, matching expectations for other frameworks such as ISO 27001 and HIPAA. Without such evidence, vendors face long questionnaires and sales delays. A 2025 survey shows that not having a SOC 2 report can lead to weeks of security questionnaires and potential deal loss.
Why Microservices Pose Unique Challenges
Traditional monolithic applications have a single perimeter and a few entry points. In contrast, microservices architectures distribute functionality across dozens or hundreds of services. Each service exposes multiple endpoints, which multiplies potential vulnerabilities. Breaking a monolith into 40 microservices can create hundreds or thousands of entry points. Real‑world examples show that a typical e‑commerce platform with five core services — authentication, product catalog, shopping cart, payment processing and order management — exposes 154 endpoints, and once additional services for notifications or analytics are added, the attack surface can exceed 500.
Other complexities include:
- Distributed authentication and authorisation: Microservices require authentication at the edge and between services. A misconfiguration in token validation or time synchronisation can create security gaps. Managing hundreds of roles and policies across services is non‑trivial.
- Service‑to‑service communication: East‑west traffic inside clusters often lacks encryption or monitoring by default. Compromising a single service can allow lateral movement across the network.
- Configuration and secrets sprawl: Each service maintains its own credentials, certificates and environment variables. With dozens of services across multiple environments, configuration sets multiply rapidly (e.g., 40 services × 3 environments × 5 categories = 600 distinct sets). Without automation, secrets may be mismanaged or hard‑coded.
- Observability and logging: Without consistent logging and trace correlation, investigating incidents across many services becomes difficult.
Cloud Security Meets SOC 2
Most microservices run on public cloud platforms such as AWS, Google Cloud Platform (GCP) or Microsoft Azure. Each provider operates under a shared responsibility model. For example, the AWS SOC 2 guidance states that AWS is responsible for the security of the cloud (data centres, hardware, network and hypervisor), while customers are responsible for security in the cloud, including identity management, data encryption, logging and network controls. Customers must know which SOC 2 controls AWS helps address and which remain their responsibility.
The shared responsibility model means that even though AWS implements physical and virtual security measures (supporting physical access controls CC6.4), customers must implement tenant‑specific controls such as identity roles, encryption policies, backup strategies and logging configurations. SOC 2 auditors will expect evidence of both provider‑side assurances and customer‑implemented controls. Cloud‑native services like AWS IAM, KMS, Config and CloudTrail can help implement and monitor these controls.
Core Security Controls for SOC 2 in Microservices
Below is a checklist of core controls for microservices environments seeking SOC 2 compliance. Each control area maps to multiple Trust Services Criteria.
Authentication & Authorisation
- API gateway vs. service‑specific enforcement: An API gateway (or ingress controller) can centralise authentication for external clients, while internal services should still enforce identity and access checks. Consider using a service mesh with sidecars to manage mutual TLS (mTLS) for east‑west traffic and propagate identity tokens across services.
- Token‑based authentication: Use standards such as JWT or OAuth 2.0 for stateless tokens. Ensure that services validate token signatures and expiry, and propagate the authenticated principal across calls. NIST SP 800‑204 emphasises the need for authentication and access management, service discovery and secure communication protocols in microservices.
- mTLS for service‑to‑service trust: mTLS ensures that both parties present certificates, protecting against man‑in‑the‑middle attacks. Tools like Envoy or Istio can automate certificate rotation and enforce encryption.
- Role‑based and attribute‑based access: Adopt least privilege by defining roles and attributes for each service. Use policy‑as‑code frameworks (e.g., Open Policy Agent) to centralise authorisation rules and test them consistently.
Encryption & Data Protection
- Data in transit: Enforce TLS 1.2 or higher for all external and internal service communication. mTLS should be mandatory for east‑west traffic.
- Data at rest: Use cloud KMS (cryptographic management services) to encrypt storage volumes, databases and object stores. Rotate cryptographic material regularly and enforce strict access policies.
- Secrets management: Eliminate hard‑coded credentials. Store secrets in managed vaults (AWS Secrets Manager, HashiCorp Vault) and automate rotation. Avoid base64‑encoded Kubernetes secrets, as they are merely encoded.
Logging, Monitoring & Auditing
- Central log aggregation: Collect logs and metrics from all services into a central platform (e.g., ELK, Grafana Loki, CloudWatch Logs). Include structured fields (timestamp, service name, trace ID, user ID) to enable correlation.
- Distributed tracing: Implement trace propagation (OpenTelemetry, Jaeger). Traces allow teams to follow a request across services, measure latency and detect anomalies.
- Audit readiness: Ensure logs are immutable and retained for the audit window. Use CloudTrail (AWS) or Audit Logs (GCP) for event history. SOC 2 Type II requires evidence over a period (3–12 months), so continuous monitoring is essential.
Network & Service Segmentation
- Zero trust principles: Do not trust internal traffic by default. Enforce network policies (Kubernetes NetworkPolicies or cloud firewalls) to allow only necessary communication between services. Start with a deny‑all stance and explicitly allow required connections.
- Service mesh: Deploy a mesh (Istio, Linkerd) to manage east‑west encryption, authentication and traffic control. The mesh enforces mutual TLS, provides identity for each service and collects telemetry.
- Environment isolation: Separate development, staging and production networks. Use separate accounts or projects in cloud providers to limit blast radius.
Change Management & CI/CD Controls
- Version control: Maintain versioned repositories for infrastructure and application code. Protect branches and require code review.
- Pipeline guardrails: Implement scanning for vulnerabilities and misconfigurations in build pipelines. Enforce automated tests and policy checks before deployment.
- Change approvals and rollback: Maintain documented change management procedures. Pre‑define rollback plans and implement canary or blue/green deployments to reduce risk.
- Separation of duties: Ensure the person approving a change is not the one who developed it. Use service accounts with restricted permissions for deployment tasks.
Mapping Trust Services Criteria to Microservices Controls
This section maps the five Trust Services Criteria to microservices controls described above:
Step‑by‑Step Guide to Achieving SOC 2 with Microservices
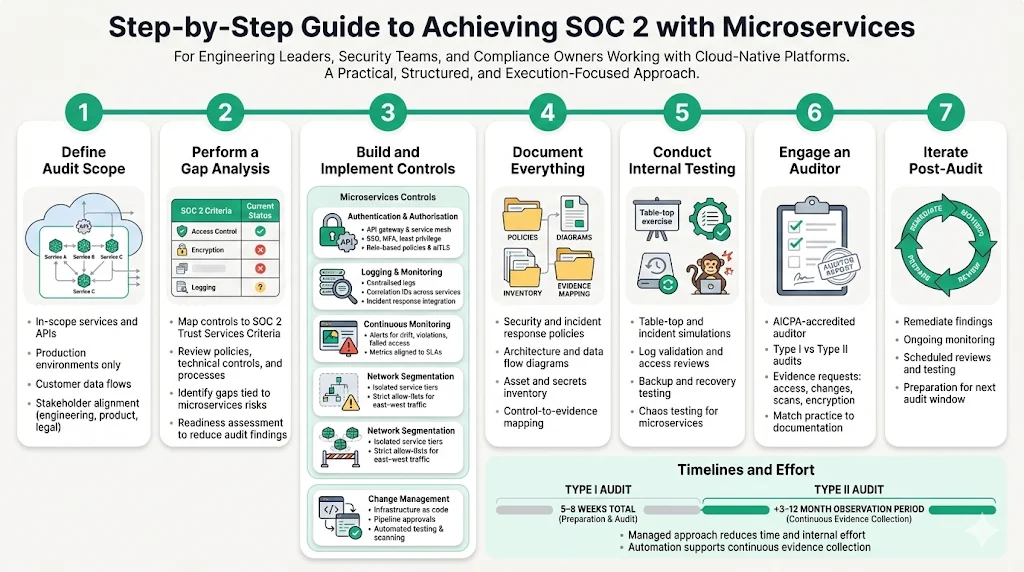
Drawing on our experience with thousands of audits, we suggest the following sequence to achieve SOC 2 compliance for a microservices platform. Each step includes tasks and examples.
Step 1: Define Audit Scope
Identify which services, APIs, environments and data flows will be included. Focus on production systems that process customer data. For example, scope could include only production APIs and the identity provider subsystem, excluding non‑customer‑facing internal tools. Document data classification and flow through each service. Engage stakeholders from engineering, product and legal to agree on the scope.
Step 2: Perform a Gap Analysis
Compare existing controls against SOC 2 requirements and microservices risks. Use frameworks like AICPA’s TSC guidance, NIST SP 800‑204 and your cloud provider’s shared responsibility model to identify gaps. Evaluate policies (password complexity, incident response), technical controls (TLS, access reviews) and operational processes (change management). A professional readiness assessment often costs around $15 K but can save time and reduce findings.
Step 3: Build & Implement Controls
This is where most of the effort lies. Focus on:
- Harden authentication and authorisation: Deploy an API gateway for edge clients and a service mesh for internal calls. Implement single sign‑on (SSO) and multi‑factor authentication. Use least privilege for service accounts. Example: At one healthcare client, our team integrated Okta for SSO, enforced role‑based policies via OPA, and configured mTLS in Istio. This reduced lateral movement risk and satisfied CC6.x criteria.
- Set up centralised logging and monitoring: Implement structured logging across services. Use a log aggregation platform and integrate with your incident response process. For example, using AWS CloudWatch Logs and X‑Ray with custom correlation IDs allowed our team to trace incidents across 50 services.
- Establish continuous monitoring: Configure alerts for policy violations, unusual network traffic or failed logins. Use AWS Config or equivalent to detect drift. Match metrics to SLAs (service agreements).
- Define network segmentation: Use Kubernetes NetworkPolicies or cloud security groups to isolate services. In one e‑commerce engagement we created separate subnets for front‑end and back‑end services with strict allow‑lists, blocking east‑west traffic except for authorised flows.
- Implement change management: Introduce infrastructure as code (IaC) and pipeline controls. Enforce code review, automated testing and vulnerability scanning. Document every change for later evidence.
Step 4: Document Everything
Documentation is crucial for audit readiness. Create policies for security, incident response, vendor management and data handling. Build architectural diagrams and data flow maps. Capture runbooks for on‑call procedures. Maintain an asset inventory of services, endpoints, cryptographic materials and secrets. Document how each control addresses a TSC and cross‑reference to evidence. Without solid documentation, auditors will not have enough assurance, even if controls exist.
Step 5: Conduct Internal Testing
Before inviting an auditor, validate your controls. Conduct table‑top drills, smoke tests and simulated incidents. Verify that logs include necessary fields, failover works, backup restores succeed and access reviews are performed. For microservices, run chaos engineering experiments (e.g., stop a service, cut off a network route) to ensure resilience and discover hidden dependencies. Test your incident response runbooks.
Step 6: Engage an Auditor
Select an AICPA‑accredited auditor with microservices experience. Provide them with system descriptions, policies, diagrams and evidence. For Type I, the audit will verify control design at a point in time; for Type II, the observation period may last 3–12 months. During the audit, respond promptly to requests. Auditors may ask for logs demonstrating access reviews, change approvals, vulnerability scan results, encryption configurations and backups. They may also verify that your procedures match what’s documented.
Step 7: Iterate Post‑Audit
After receiving your report, address any exceptions or auditor observations. SOC 2 is not a one‑time exercise; controls must operate consistently. Implement continuous monitoring and remediation tracking. Schedule periodic access reviews, vulnerability management and incident response tests. Use automation to collect evidence (e.g., AWS Config, GuardDuty, CloudWatch, third‑party solutions). Plan for the next audit window and adjust your programme based on changes in services or business requirements.
Timelines and Effort
Many organisations underestimate the timeline. A typical SOC 2 Type I takes five weeks to two months to complete, with 1–3 months of preparation and 2–6 weeks for report creation. A Type II adds an observation period of 3–12 months. At Konfirmity, we help clients achieve readiness in 4–5 months, compared with 9–12 months when self‑managed. Our managed service reduces internal effort from 550–600 hours to around 75 hours per year by automating evidence collection, performing vendor risk assessments and running continuous monitoring.
Examples & Snippets
To make the abstract concrete, here are example checklists, evidence artifacts and diagrams.
Example Authentication Checklist
- API gateway enforces SSO and MFA for external clients.
- Service mesh enforces mTLS for all inter‑service communication.
- JWT tokens are signed with strong cryptographic material; expiry set to reasonable duration.
- OPA policies define role‑based access for each service.
- Regular review of roles and permissions.
Example Encryption Checklist
- All external and internal communications use TLS 1.2+.
- Data stores (databases, storage, caches) are encrypted at rest via KMS.
- Secrets are stored in a managed vault and rotated regularly.
- Backups are encrypted and tested for restores.
Example Logging Evidence
Auditors will expect logs showing access reviews, configuration changes and incident handling. Provide:
- Centralised logs with correlation IDs linking requests across services.
- Access review records documenting user or service access changes.
- Change management logs from your version control and CI/CD pipeline.
- Incident response logs including detection time, investigation steps and resolution.
Risks to Watch & How to Mitigate Them
Even with a programme in place, certain risks can jeopardise compliance and security:
- Vendor risk and third‑party dependencies: Enterprise buyers scrutinise third‑party services (payment processors, analytics, messaging providers). Maintain a vendor inventory, conduct due diligence and obtain SOC 2 or ISO 27001 reports from critical vendors. Define data sharing agreements and monitor vendor performance.
- Misconfigurations and drift: Cloud misconfigurations (open S3 buckets, excessive IAM privileges) are a leading cause of breaches. Use tools like AWS Config or GCP Configuration Manager to detect drift. Review infrastructure as code regularly.
- Shadow services: In microservices environments, engineers sometimes spin up ad‑hoc services outside the compliance scope. Implement service discovery and inventory scanning to detect undocumented APIs. Enforce registration of new services in a central catalogue.
- Logging gaps: Without consistent logging and tracing across services, incidents can go unnoticed. Enforce logging standards and use automated agents (e.g., Fluent Bit) to forward logs. Retain logs for the entire audit window.
- Over‑permissioned tokens: Avoid broad service or user roles. Use least privilege and separate duties. Periodically review and revoke unnecessary permissions.
Tools & Frameworks You Can Use
Building SOC 2 controls for microservices doesn’t mean reinventing the wheel. Consider these categories:
- Cloud‑native tools:
- AWS: IAM for access control, KMS for encryption, Config for drift detection, CloudTrail for logging, GuardDuty for threat detection, Security Hub for centralised findings.
- GCP: Cloud IAM, KMS (cryptographic management service), Cloud Audit Logs, Security Command Center.
- Azure: Azure Active Directory, Vault (cryptographic storage), Security Center, Activity Logs.
- AWS: IAM for access control, KMS for encryption, Config for drift detection, CloudTrail for logging, GuardDuty for threat detection, Security Hub for centralised findings.
- Open‑source security tooling:
- Service mesh: Istio, Linkerd for mTLS and traffic policy enforcement.
- OPA for policy as code.
- Vault for secrets management.
- Prometheus and Grafana for metrics.
- Fluent Bit for log forwarding.
- Service mesh: Istio, Linkerd for mTLS and traffic policy enforcement.
- Compliance automation platforms: Tools like Konfirmity, Vanta, Secureframe or Drata automate evidence collection, control monitoring and policy management. They reduce manual effort, integrate with cloud and SaaS services, and support multiple frameworks (SOC 2, ISO 27001, HIPAA, GDPR). For example, using Vanta reduces security questionnaire responses by up to 80% and cuts onboarding time by weeks. Konfirmity distinguishes itself by providing a human‑led managed service, not just software; we embed ourselves in your engineering workflows, implement controls and maintain them continuously.
Practical Tips for Ongoing Compliance
SOC 2 is not about generating a report once a year. Here are practical habits to sustain compliance:
- Continuous monitoring: Set up alerting for compliance drift, including expired certificates, unused accounts, or missing patches. Use automation to collect evidence in real time. Avoid relying solely on manual snapshots during the audit window.
- Periodic access reviews: Quarterly, review user and service access lists. Remove unused accounts and rotate credentials. Document the review and approvals.
- Incident response practice: Conduct regular incident response drills. Simulate breaches, evaluate detection and containment processes, and document lessons learned.
- Training and awareness: Educate engineers and product teams on SOC 2 requirements, microservices security and privacy obligations. Provide onboarding training and annual refreshers. Encourage secure coding practices and point out the cost of non‑compliance.
- Policy upkeep: Update policies when new services are introduced, when the organisation changes, or when frameworks are updated. For example, ISO 27001:2022 reduced the number of Annex A controls from 114 to 93 and grouped them into four categories (organisational, people, physical, technological). Adjust your policies to reflect these changes.
- Vendor and supply‑chain reviews: Add vendor monitoring to your compliance cycle. Evaluate the SOC 2 or ISO 27001 status of your vendors and require updates. Maintain up‑to‑date Business Associate Agreements (BAAs) for HIPAA covered entities and Data Processing Agreements (DPAs) for GDPR.
Conclusion
Microservices revolutionised software development by allowing teams to build and deploy independent services at scale. However, this modularity comes with greater complexity. Each service becomes an entry point, requiring strong authentication, encryption, segmentation and observability. When coupled with enterprise clients’ demand for SOC 2 reports, microservices teams face a unique set of challenges.
A methodical approach rooted in security pays off. Start by defining your audit scope, performing a gap analysis, and building controls around identity, encryption, logging, network segmentation and change management. Document every policy and data flow, test your systems, and engage auditors when ready. Maintain continuous monitoring and iterate after each audit. Tools like service meshes, identity providers, log aggregators and compliance automation platforms can lighten the load, but they don’t replace thoughtful design.
Konfirmity’s human‑led managed service approach illustrates that security and compliance go hand in hand. By building real controls and operating them daily, we help organisations achieve SOC 2 Microservices And SOC 2 compliance faster, reduce internal burden and, most importantly, protect customer data. Security that looks good on paper but fails under incident pressure is a liability. Build the programme once, operate it daily, and let compliance follow.
FAQ
1. Do I need SOC 2 for every microservice?
No. Scope your audit to services that handle customer data or support the core product. Secondary services may not need to be in scope, but you must consider dependencies and potential data flows. Auditors will expect a rationale for what is included and excluded.
2. How long does SOC 2 certification take?
SOC 2 Type I audit typically takes five weeks to two months once preparation is complete. Preparation can take one to three months depending on control maturity. A Type II audit adds an observation window of three to twelve months.
3. Can automation replace manual audit preparation?
Automation tools can collect evidence, monitor controls and manage policies, reducing manual work dramatically. However, they can't design your control environment or make decisions about risk. A human‑led programme is still necessary to interpret requirements, design controls and remediate issues. Tools complement, not replace, expertise.
4.What if I use multiple cloud providers?
You need to apply the shared responsibility model for each provider. Understand what each cloud provider secures and what you must secure (identity, data, logging). Document how controls are implemented across AWS, GCP and Azure, and provide evidence from each. Use multi‑cloud tools or service meshes that span environments.
5. How does logging support audit evidence?
Logs provide the raw data for auditors to verify that controls operated effectively over the audit window. Maintain structured, tamper‑evident logs with timestamps, user and service identities, and event descriptions. Retain logs for the required period (often 12 months). Use log aggregation tools to extract and present evidence during audits.





.svg)






.svg)
.svg)