Most enterprise technology deals come with long security questionnaires and procurement gates. Security leaders on the other side of the table are no longer satisfied with polished documents; they want evidence that your controls work under pressure. In this context, Red Team Vs. Blue Team In SOC 2 isn’t just a theoretical discussion—it’s about how offensive and defensive practices influence compliance outcomes. Drawing on more than 25 years of combined expertise and 6,000+ audits at Konfirmity, this article explains why both teams matter for SOC 2 readiness and enterprise sales. You’ll learn how the trust service criteria work, the roles of red and blue teams, how to integrate their feedback into your program, and how to demonstrate resilience to auditors and buyers.
What SOC 2 Is and Why It Matters
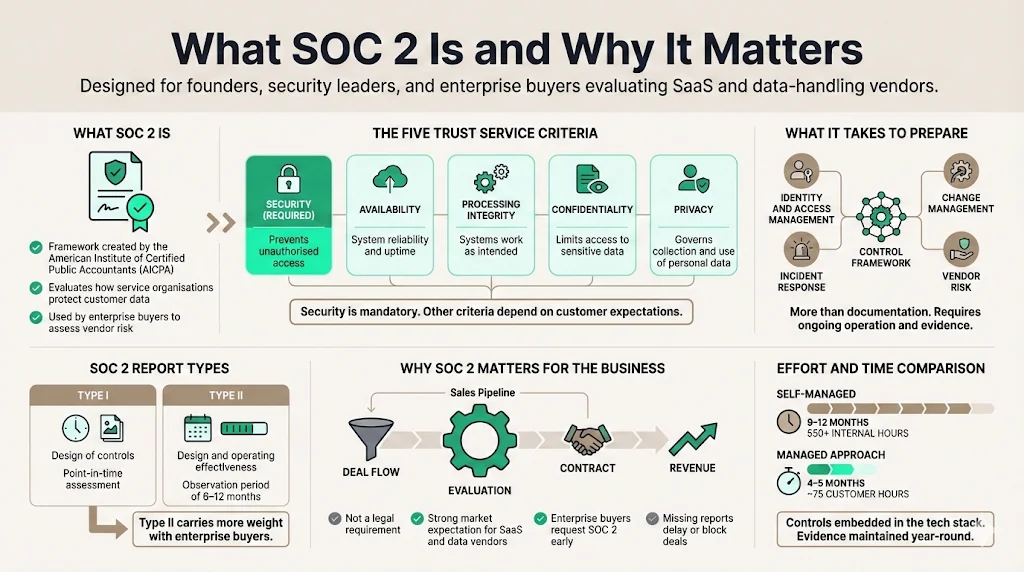
SOC 2 is a framework established by the American Institute of Certified Public Accountants (AICPA) that evaluates service organizations on five trust service criteria: security, availability, processing integrity, confidentiality and privacy.
- Security covers measures to prevent unauthorized access, which is mandatory for all SOC 2 reports.
- Availability relates to system reliability and uptime.
- Processing integrity ensures systems function as intended without errors or manipulation.
- Confidentiality restricts sensitive data to authorized individuals.
- Privacy addresses the collection and use of personal information.
There are two report types. A Type I audit assesses whether controls are designed appropriately at a single point in time, while a Type II report examines their operating effectiveness over an observation window, typically six to twelve months. Although SOC 2 isn’t a legal requirement, it has become a market expectation, especially for software-as-a-service providers and vendors handling critical data. Enterprise buyers ask for SOC 2 reports to gauge risk; without one, deals stall.
Preparing for SOC 2 involves more than producing documents. It requires implementing and maintaining controls across identity management, change management, incident response, vendor risk and more. Many teams underestimate the workload. A self‑managed program can take nine to twelve months and hundreds of internal hours. Through Konfirmity’s managed service, we typically achieve readiness in four to five months with about 75 hours of customer effort compared with more than 550 hours self‑managed. Our approach builds controls inside your technology stack and maintains evidence year‑round so you’re always audit‑ready.
Red Team Vs. Blue Team: Core Concepts
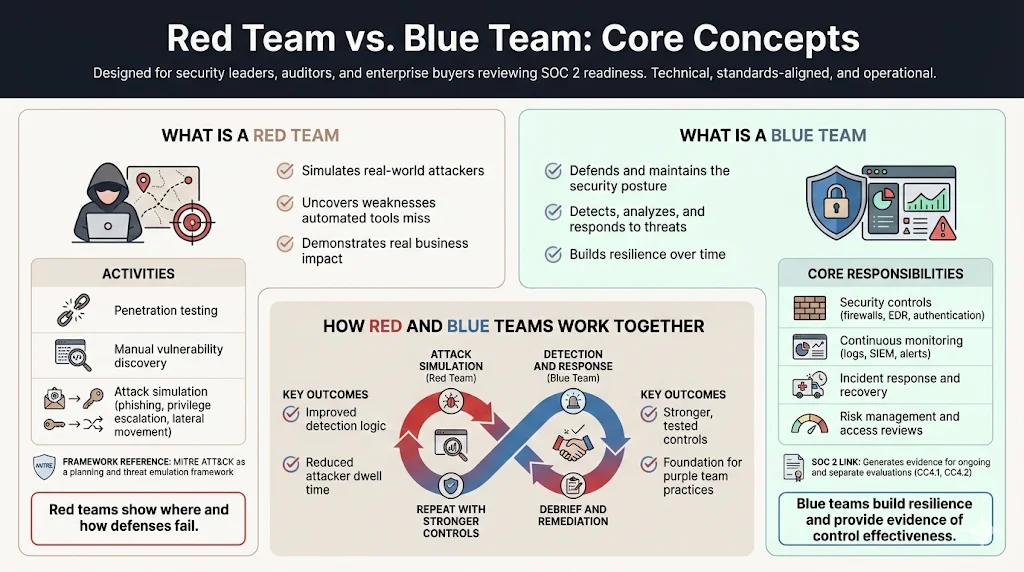
What Is a Red Team
The National Institute of Standards and Technology (NIST) defines the red team/blue team approach as two organized groups: one emulating a potential adversary’s capabilities and the other defending an enterprise’s security posture. A red team “improves enterprise information assurance by demonstrating the impacts of successful attacks and by demonstrating what works for the defenders”. In practice, a red team comprises offensive security professionals who simulate real‑world attacks to uncover weaknesses that automated scanning misses. Activities include:
- Penetration testing: targeted attempts to exploit misconfigurations, flawed code, or weak authentication. While SOC 2 doesn’t explicitly mandate penetration testing, auditors expect organizations to perform regular tests as part of ongoing evaluations and vulnerability management.
- Vulnerability identification: manual probing combined with automated scanning to find misconfigured services or insecure software.
- Attack simulation: chaining exploits, phishing employees, escalating privileges and moving laterally to mimic advanced persistent threats.
Red teams operate with stealth and persistence, often using frameworks like MITRE ATT&CK to plan operations. MITRE notes that ATT&CK provides a “common language and framework that red teams can use to emulate specific threats and plan their operations”. By acting like adversaries, red teams reveal where defenses break down and highlight business impacts of a breach.
What Is a Blue Team
The blue team is the group responsible for defending an organization. NIST describes the blue team as maintaining the enterprise’s security posture against the red team’s attacks over a significant period. Blue team members include security analysts, incident responders, system administrators and risk managers. Their mission is to detect, analyze and respond to threats, continuously improve controls and ensure resilience. Key tasks include:
- Security controls: deploying and managing tools like firewalls, endpoint detection and response (EDR) platforms, and authentication mechanisms.
- Continuous monitoring: reviewing logs, tuning Security Information and Event Management (SIEM) systems and triaging alerts to spot anomalies.
- Incident response: investigating suspicious activity, containing threats, eradicating malware and recovering systems.
- Risk management: performing threat modeling, vulnerability scanning and access reviews.
Blue teams play a crucial role in SOC 2 readiness. SOC 2 criteria CC4.1 and CC4.2 require organizations to perform ongoing and separate evaluations of controls and communicate deficiencies. Blue team activities—log review, vulnerability management and incident response—generate the evidence auditors inspect during the observation period.
How Red and Blue Teams Work Together
On paper, red and blue teams appear adversarial. In reality, they are complementary. A well‑run security program uses offensive testing to inform defensive improvements. The feedback loop works like this:
- Attack simulation: The red team launches a controlled attack—phishing an employee, exploiting a misconfiguration, pivoting laterally.
- Detection and response: The blue team monitors alerts, investigates anomalies and applies controls to contain the attack.
- Debrief and remediation: Both teams meet to discuss what worked, what failed and which controls need strengthening.
- Repeat: Subsequent exercises incorporate lessons learned and test updated defenses.
By cycling through attack and defense, an organization refines its detection logic, reduces dwell time and hardens its posture. This collaboration underpins a purple team, which we discuss later.
Why Red Vs. Blue Team Matters for SOC 2

Mapping Practices to SOC 2 Criteria
SOC 2’s security criteria (commonly called “Common Criteria”) require organizations to identify and assess risks, implement mitigation measures, and continuously monitor and respond to incidents. Red team tests and blue team monitoring both provide evidence that these controls operate effectively. For example:
- Vulnerability management (CC7.1 & CC6.6): Auditors expect organizations to identify new vulnerabilities promptly and remediate them. Red team engagements, combined with automated scans, demonstrate that your program finds and addresses weaknesses.
- Incident response (CC7.2): Blue team activities—incident detection, logging, analysis, and response—illustrate how quickly you can contain threats. They support metrics such as mean time to detect (MTTD) and mean time to respond (MTTR), which we cover later.
- Ongoing evaluations (CC4.1): SOC 2 encourages a mix of ongoing and separate evaluations. Red team tests provide separate evaluations, while blue team monitoring constitutes ongoing evaluations.
Beyond SOC 2, other regulations reinforce this approach. In December 2024 the U.S. Department of Health and Human Services proposed strengthening the HIPAA Security Rule. The proposed rule would require vulnerability scanning every six months and penetration testing at least annually, as well as encryption of electronic protected health information (ePHI) at rest and in transit. These requirements mirror the proactive and defensive duties of red and blue teams.
Real Costs of Weak Controls
The cost of ignoring real security is substantial. IBM’s 2024 Cost of a Data Breach report found that the global average breach cost rose 10 percent over the prior year to USD 4.88 million. Business disruption and post‑breach customer support drove this spike. Organizations deploying security automation reduced breach costs by an average of USD 2.2 million, highlighting the financial benefit of mature detection and response capabilities. Breaches involving stolen credentials took 292 days to identify and contain, while phishing attacks lasted an average of 261 days. These long timelines underscore the need for constant monitoring and rapid response.
Enterprise buyers know these numbers. When you hand them a SOC 2 report, they want evidence that you can spot and stop threats quickly. Red team results and blue team metrics provide that assurance. A report full of policies without operational evidence may check a box but will not satisfy security‑minded procurement teams.
Security Testing Types and When to Use Them

Penetration Testing vs. Red Teaming
Penetration testing is a structured assessment that identifies technical weaknesses. Auditors often expect annual penetration tests covering all in‑scope systems. These tests use a combination of automated scanning and manual verification to reveal misconfigurations, missing patches and common vulnerabilities. They generally follow a predictable pattern and provide a snapshot of your security posture at a point in time.
Red team engagements go further. They mimic the tactics, techniques and procedures of real adversaries to test not only your systems but also your people and processes. A red team might craft a phishing email that tricks an employee into clicking a link, then exploit a misconfiguration to gain privileged access and exfiltrate data. Because red teams operate stealthily over weeks or months, they assess how well your blue team detects lateral movement, logs suspicious activities and responds. They are best suited for organizations that have already addressed obvious vulnerabilities and want to test their resilience.
When deciding which to use, consider maturity and risk. Start with frequent penetration tests to establish a baseline. Once you’ve remediated obvious issues and implemented logging and incident response processes, run red team engagements to stress those controls.
Ongoing Security Assessments
Security is not a one‑time event. Blue teams perform continuous assessments to maintain readiness:
- Log review and SIEM tuning: Monitoring system and application logs, updating correlation rules and reducing false positives.
- Threat intelligence and vulnerability scanning: Using feeds and scanners to detect emerging threats. The ISO 27001:2022 update introduced a new control (A.5.7) for threat intelligence and a control for data masking, reflecting the need to embed proactive intelligence into security programs.
- Alert triage and incident response: Investigating suspicious alerts, containing incidents and performing root cause analyses.
- Access reviews and change management: Verifying least privilege, reviewing approvals for elevated rights and ensuring changes are documented.
SOC 2 auditors review evidence from these activities during the observation period. They sample logs, review incidents and verify that the team followed policies and responded appropriately. Without continuous assessments, controls drift and evidence becomes stale, risking audit findings.
Practical Examples
Example 1: Red team exercise – A security team commissions a red team to test their new Single Sign‑On (SSO) service. The red team crafts spear‑phishing emails to target engineers, successfully compromises an account and escalates privileges to an internal customer database. They uncover an overlooked misconfiguration in the identity provider. The exercise demonstrates how a real attacker could move laterally from a compromised workstation to sensitive data. Remediation includes tightening privilege escalation paths, hardening SSO settings and training staff.
Example 2: Blue team defense exercise – During a scheduled exercise, the blue team monitors alerts from their SIEM and endpoint detection tools. They detect unusual file encryption patterns on a development server, identify it as a simulated ransomware payload and isolate the host. They follow their incident response plan, restore from backups within service‑level agreements and document the incident. Evidence collected—alerts, response timelines, containment actions—illustrates compliance with SOC 2 control objectives and demonstrates resilience to customers.
Example 3: Combined exercise – A combined red and blue team exercise begins with the red team executing a complex attack scenario over six weeks. They exploit an external API, pivot through a container cluster and exfiltrate data. The blue team initially misses early indicators but eventually detects anomalous network traffic. After the exercise, both teams debrief. Lessons include improving network segmentation, enriching logs, and automating alerts for suspicious container activity. The combined exercise delivers a realistic narrative to present to auditors and prospects, showing how the organization responds to advanced threats.
Tools, Techniques and Best Practices
Red Team Tools and Techniques
Red teamers use a mix of open‑source and proprietary tools to simulate attacks:
- Offensive toolsets: Exploitation frameworks such as Metasploit, Cobalt Strike, Sliver and custom scripts.
- Reconnaissance and scanning: Tools like Nmap, Nessus or masscan to map networks and discover vulnerable services.
- Phishing and social engineering: Crafting emails and payloads to trick employees.
- Attack chains: Using the MITRE ATT&CK framework to plan tactics and techniques. ATT&CK gives red teams and defenders a shared language.
Documentation is essential. A quality red team report includes exploited vulnerabilities, attack paths and remediation steps. Auditors look for evidence that findings were addressed.
Blue Team Tools and Techniques
Blue team operations rely on:
- Security Information and Event Management (SIEM): Aggregates logs from systems, applications and networks; performs correlation and alerting.
- Endpoint detection and response (EDR) and managed detection and response (MDR): Provide visibility into endpoint behavior, detect malware and support remote response actions.
- Incident response workflows: Playbooks, runbooks and ticketing systems to coordinate investigation and containment.
- Asset inventory and vulnerability management: Identifying assets in scope, scanning for vulnerabilities and tracking remediation.
- Risk-based prioritization: Using scores (e.g., CVSS) to prioritize fixes and set service‑level agreements (SLAs) for remediation.
Blue team effectiveness depends on constant tuning. Without refining detection logic, teams drown in noise and miss true threats.
Enterprise Support and Evidence Preparation
For enterprise and healthcare buyers, evidence matters. To satisfy procurement and auditors:
- Collect structured evidence: Maintain logs of access reviews, change approvals, incident reports and vulnerability scans. Document dates, participants and actions.
- Map evidence to trust service criteria: For each SOC 2 control, show the related policy, operational implementation and proof that it operated over the observation period.
- Sanitize reports for customers: Provide attestation letters, summary test results and remediation status without exposing sensitive details.
- Re‑use across frameworks: Map controls across ISO 27001, HIPAA and GDPR. The ISO 27001:2022 update consolidates controls into four categories and introduces new controls for threat intelligence and data masking, making cross‑framework mapping more straightforward.
Konfirmity’s managed service handles these tasks. We implement controls in your environment, collect evidence continuously and prepare artifacts for auditors and enterprise buyers. Our experts attend audit meetings, answer control questions and support you through observation windows.
Bridging the Gap: Purple Team and Integrated Security
As organizations mature, they often move from separate red and blue teams to a purple team model. A purple team facilitates collaboration between offensive and defensive specialists, ensuring knowledge transfer and faster improvements. According to industry guidance, purple teaming involves iterative cycles: the offensive side identifies vulnerabilities, shares them with defenders, and both groups collaborate to remediate and validate fixes. This integrated approach accelerates the detection of blind spots, helps teams tune detection rules and reduces the time between discovering a weakness and deploying a fix.
By combining red and blue perspectives, a purple team aligns testing with operational realities. For SOC 2, this means your evidence tells a coherent story: you identify risks, respond to incidents and continuously improve controls.
Metrics and KPIs for SOC 2 and Security Programs
Metrics quantify how well your security program performs. Auditors and enterprise customers want to see numbers, not just narratives.
Red Team Metrics
- Time to compromise: How long does it take the red team to achieve its objective? A shorter time indicates that an attacker could quickly breach defenses; longer times suggest resilience.
- Number of exploitable paths: Counting the ways the red team moved from an initial foothold to sensitive data reveals the breadth of exposure.
- Detection rate: Out of all activities attempted, how many were detected by the blue team? High detection rates indicate strong monitoring.
Blue Team Metrics
- Mean time to detect (MTTD): The average time between the start of a security incident and its detection. According to security guidance, MTTD is calculated by dividing the total detection time by the number of incidents. Lower MTTD means threats are spotted faster.
- Mean time to respond (MTTR): The average time from detection to containment and recovery. MTTR is found by dividing total response time by the number of incidents.
- Detection coverage: The percentage of attack techniques covered by your alerts. Use frameworks like MITRE ATT&CK to map coverage.
When presenting metrics, include context. For instance, if your MTTD is eight hours but the breach lifecycle for stolen credentials is 292 days, you can demonstrate that your program significantly reduces dwell time.
Common Challenges and How to Overcome Them
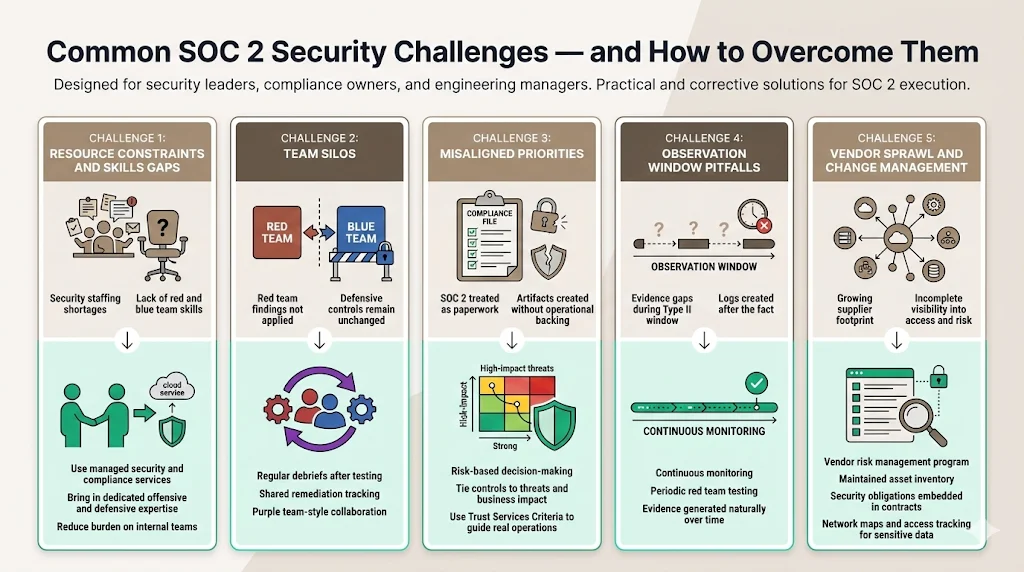
- Resource constraints and skills gaps. IBM’s report notes that more than half of breached organizations faced severe security staffing shortages. Red and blue team activities require specialized skills that many companies lack. Managed services like Konfirmity provide dedicated expertise so your internal team doesn’t have to become penetration testers and incident responders overnight.
- Team silos. When red and blue teams operate in isolation, findings don’t translate into improvements. Instituting a purple team or regular debriefs fosters collaboration and ensures that lessons from offensive tests feed into defensive tuning.
- Misaligned priorities. Some leaders still view SOC 2 as a compliance exercise rather than a security obligation. This mindset leads to “compliance manufacturing”—producing artifacts to satisfy auditors without strengthening controls. A risk‑based approach ties controls to threats and business impact. Use the trust service criteria to guide decisions and provide evidence of real operations.
- Observation window pitfalls. For Type II audits, evidence must cover an observation period of three to twelve months. Teams sometimes scramble to generate logs after the fact, which auditors may reject. By implementing continuous monitoring and periodic red team tests, you ensure evidence is naturally generated.
- Vendor sprawl and change management. As companies adopt new services, keeping track of suppliers and managing access becomes harder. Implement a vendor risk program, maintain an asset inventory, and require contracts to include security obligations—particularly for health data, where HIPAA’s proposed updates call for inventories and network maps.
Conclusion
The comparison of Red Team Vs. Blue Team In SOC 2 illustrates a broader truth: security and compliance are inseparable. Offensive testing shows you where defences crack; defensive operations keep threats from causing harm. SOC 2 demands evidence of both. A mature program marries red and blue practices, guided by the trust service criteria, and provides continuous evidence that controls work in practice.
Konfirmity’s experience—supporting 6,000+ audits and more than 25 years of combined expertise—shows that building an operational program beats chasing paperwork. We implement controls in your environment, run regular offensive tests, operate the monitoring stack and deliver clean reports to auditors and customers. Our approach shortens readiness cycles, reduces customer effort and enhances security posture.
Security that reads well but fails under incident pressure is a liability. Invest in both red and blue capabilities, integrate them through purple teaming and let compliance follow naturally.
Frequently Asked Questions (FAQ)
1. What’s the difference between a red team and a blue team?
A red team simulates adversaries by exploiting vulnerabilities and chaining attacks to demonstrate the impact of a breach. A blue team defends the organization by deploying controls, monitoring for threats and responding to incidents. Red teams focus on offensive testing; blue teams focus on detection, response and continuous improvement.
2. Is the SOC a blue team or a red team?
The term “Security Operations Center” (SOC) refers to a function responsible for monitoring, detection and response. It is essentially a blue team. SOC 2, however, is an attestation framework that evaluates both preventive and detective controls. A mature program includes offensive testing (red team) and defensive operations (blue team) to meet SOC 2 criteria.
3. What is the difference between red team and blue team in the military?
The red/blue team concept originated in military war‑gaming exercises, where the red team played the role of the aggressor and the blue team defended. Cybersecurity adopted these roles to simulate digital attacks and defenses. The principles remain: one side tests tactics and capabilities; the other practices detection and response.
4. What are the three tiers of a SOC?
Most security operations centers use a tiered model:
- Tier 1: Front‑line analysts who monitor alerts, perform initial triage and handle low‑complexity incidents.
- Tier 2: More experienced analysts who conduct deeper investigations, perform root cause analysis and coordinate response.
- Tier 3: Subject‑matter experts and threat hunters who handle complex cases, develop detection logic and assist with tool tuning.
These tiers align with the increasing sophistication of threats. SOC 2 doesn’t prescribe tiers, but auditors expect that incident response duties are assigned to personnel with appropriate expertise and that responses are well‑documented.





.svg)






.svg)
.svg)