Most enterprise procurement processes now insist on evidence of operational security before contracts are signed. Buyers ask for attestation reports, breach histories and service level commitments. A SOC 2 Risk Assessment Guide helps companies answer these requests. Without a structured risk assessment and continuous evidence collection, deals stall even when teams believe they are ready on paper. This article explains why risk assessment matters, defines core concepts and walks through a practical process you can run today. It draws on our work delivering more than 6,000 audits and 25+ years of combined expertise across frameworks such as SOC 2, ISO 27001, HIPAA and GDPR.
Why SOC 2 matters for enterprise sales
Enterprise buyers routinely insist on assurance that vendors can protect sensitive data and keep services running. Without a current SOC 2 report, deals often stall. Unaddressed risks carry heavy financial consequences: IBM’s 2025 breach report lists a global average cost of $4.44 million and a U.S. average of $10.22 million, with healthcare breaches costing $7.42 million and taking 279 days to contain. These figures make robust security a sales prerequisite.
From our experience at Konfirmity, buyers look beyond policy documents. They demand evidence that controls operate daily. A sound risk assessment delivers that evidence, reduces incident likelihood and shows auditors that your program is grounded in reality.
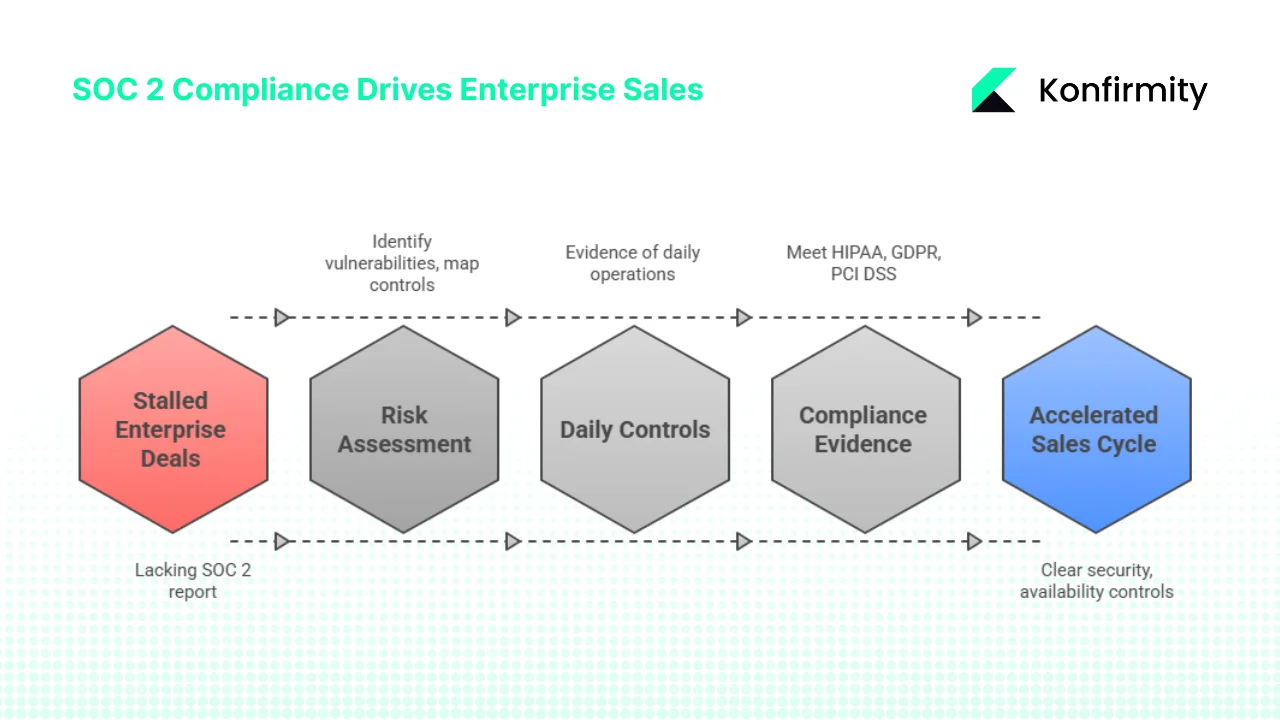
Enterprise procurement teams also use SOC 2 reports to compare vendors and ensure contractual obligations can be met. Without clear evidence of security and availability controls your offering may be excluded early in the buying cycle. Our clients often need to respond to detailed questionnaires covering encryption, access management, incident response, vendor oversight and privacy. A risk assessment helps answer these questions quickly because you’ve already catalogued assets, identified vulnerabilities and mapped controls. It also demonstrates a culture of transparency and risk management that resonates with CISOs and procurement committees. In regulated sectors such as healthcare and finance, buyers often expect evidence of compliance with HIPAA, GDPR, PCI DSS or ISO 27001 in addition to SOC 2. A robust risk assessment program shows you have the foundation to meet multiple frameworks without duplicating work.
What is a SOC 2 risk assessment and why it matters
A SOC 2 risk assessment is a structured way to identify threats, gauge their likelihood and impact and plan controls. It spans technology, people and processes and is a proactive tool to prevent problems. Done well, it builds trust, safeguards reputation and reduces legal exposure.
The AICPA’s Common Criteria 3 makes risk assessment mandatory. Practically, this means listing risks, scoring them, mapping them to controls and updating the register regularly. Include vendor and fraud risks; otherwise auditors can issue qualified opinions.
A robust assessment guides you to invest in the right controls. It also aligns with frameworks like ISO 27001 and NIST 800‑53, allowing one program to satisfy multiple obligations.
Risk assessments also deliver operational value. They expose process gaps, highlight training needs and inform incident response. Cross‑functional participation—engineering, product, legal, HR and finance—fosters a security culture and creates a baseline for continuous improvement. Aligning SOC 2 with other frameworks like HIPAA and GDPR reduces duplication and speeds readiness for future audits.
Core concepts and terms
Understand these key terms before proceeding:
- Information assets: data, systems, endpoints and people—anything you need to protect.
- Threats and vulnerabilities: technical (unpatched software), procedural (weak offboarding), human (phishing) and vendor risks.
- Risk scoring: evaluate likelihood and impact to produce inherent and residual scores.
- Internal controls: tools and practices that reduce risk: encryption, access management, segmentation, logging and vendor clauses.
- Risk treatment: options include mitigating, accepting, transferring or avoiding a risk.
- Continuous monitoring: maintain a risk register, track owners and update controls regularly.
- Vendor assessment: evaluate third parties against standards such as SOC 2 and NIST guidelines.
- Audit procedures: auditors expect documented risk assessments and evidence of control operation.
These concepts are interconnected. You start by identifying assets and threats, score the risk and then select controls to reduce the inherent exposure. Risk treatment decisions—whether to mitigate, accept or transfer—must be recorded along with who is responsible. A living risk register ties all this information together and becomes the single source of truth for audits and internal reviews. Regular updates ensure that controls keep pace with new technologies, business changes and regulatory requirements.
Step‑by‑step SOC 2 risk assessment process
This SOC 2 Risk Assessment Guide sets out nine steps that integrate lessons from auditors, the AICPA, NIST and Konfirmity’s delivery work. It prioritises efficiency and evidence without sacrificing security.

Step 1: Define scope and objectives
Begin with your contractual obligations and service levels. Choose which Trust Services Criteria apply—security is mandatory; availability, processing integrity, confidentiality and privacy depend on your services. Define the systems, data flows and vendors in scope. Linford notes that objectives must be clear enough to enable risk identification.
Documenting scope in detail avoids surprises during the audit. For example, if your SaaS platform processes personal data for EU customers you may need to include the privacy criterion and GDPR‑specific controls. If you offer 24/7 uptime guarantees, then availability is likely in scope. Scope documents should include diagrams of data flows, lists of third‑party providers and statements of service commitments, so everyone understands what is covered.
Step 2: Build or reference an asset inventory
Compile a list of servers, databases, applications, endpoints and third‑party tools, including laptops and mobile devices. Assign sensitivity levels and note owners and locations to show where controls must be strongest.
Classify assets into categories such as public, internal, confidential and restricted to align with handling requirements. Consider non‑technical assets too: intellectual property, customer contracts and staff knowledge are also assets. Some organizations use configuration management databases or automated discovery tools to keep inventories up to date. Having a complete inventory helps you see where sensitive data lives and which vendors have access.
Step 3: Identify risks — threats and vulnerabilities
Brainstorm technical, process, human and vendor threats. Map each risk to the relevant Trust Services Criteria: ransomware affects security and availability; data leaks hit confidentiality and privacy. Include vendor risk: NIST stresses regular vendor assessments.
Consider internal (misconfigurations, excessive privileges), external (DDoS, supply‑chain exploits), human (phishing, insider fraud) and process failures (poor offboarding) and identify the affected asset and impact.
Step 4: Evaluate existing controls
Document existing controls such as multi‑factor authentication, segmentation, encryption, change management and vendor clauses. Check that they are well designed and operating effectively. Audit evidence must cover the full observation period. Record gaps where controls are absent or weak.
Evaluating design confirms that the control addresses the risk; operating effectiveness verifies it works. Evidence includes logs, access review records, change tickets, vulnerability scans and vendor attestations. Automate manual processes where possible to reduce errors.
Step 5: Risk scoring and prioritisation
Score each risk’s likelihood and impact (for example on a scale from 1 to 5) to produce inherent and residual scores. Use a three‑by‑three risk matrix (green/yellow/red) to highlight priorities. Decide whether to mitigate, accept, transfer or avoid each risk. The diagram below illustrates this approach:

When scoring, align the scale with your organisation’s risk appetite. A likelihood of 5 might represent a high probability (occurs weekly), while an impact of 5 might represent catastrophic impact (major customer outage or legal liability). Residual risk scoring helps you see the effect of controls and justify additional investment. Document the rationale behind each score so that others understand why a risk was prioritised.
Step 6: Map controls to Trust Services Criteria and other standards
Map each control to the relevant Trust Services Criteria and, where applicable, to frameworks such as ISO 27001, NIST 800‑53 or HIPAA. For example, encryption at rest supports confidentiality and aligns with NIST’s guidance to use AES for stored data and TLS for data in transit.
Mapping helps auditors verify that your controls meet the required objectives. It also streamlines multi‑framework compliance by showing where a single control can satisfy multiple standards. For instance, a vulnerability management program may address both SOC 2 security and ISO 27001 Annex 8. Keep a cross‑reference matrix that links each control to the TSC and any applicable regulatory requirement.
Step 7: Document reporting — risk register and risk assessment report
Maintain a risk register listing each risk, its scores, controls, treatment plan, owner and status. Summarise the assessment in a report covering scope, methodology, findings and mitigation plans, and obtain leadership sign‑off.
Include deadlines, status updates and evidence links in the register. Reports should summarise high‑severity risks, residual risk by category and include a heatmap to help executives prioritise.
Step 8: Execute the risk treatment and mitigation plan
For high and medium risks, assign owners and implement the controls. Examples: use multi‑factor authentication and awareness training to counter credential theft; automate patching to address unpatched systems; strengthen vendor contracts and review their SOC 2 reports. Track progress in the register and involve IT, HR, legal and other teams.
Mitigation combines technical and organisational measures such as least‑privilege access, environment separation, dual approvals and data loss prevention. Explain the rationale behind each action plan so stakeholders understand why it matters.
Step 9: Continuous monitoring and periodic review
Risk assessment is not a one‑time task. Conduct at least one full review per year and re‑evaluate after mergers, new products or changes in law. Type 2 audits require evidence of ongoing monitoring. Update the register and adjust controls as threats evolve.
Continuous monitoring should include automated vulnerability scanning, log reviews, access certification and vendor performance tracking. When incidents occur, use them as opportunities to reassess risks and improve controls. Document lessons learned and feed them back into your risk management program.
Common pitfalls and how to avoid them
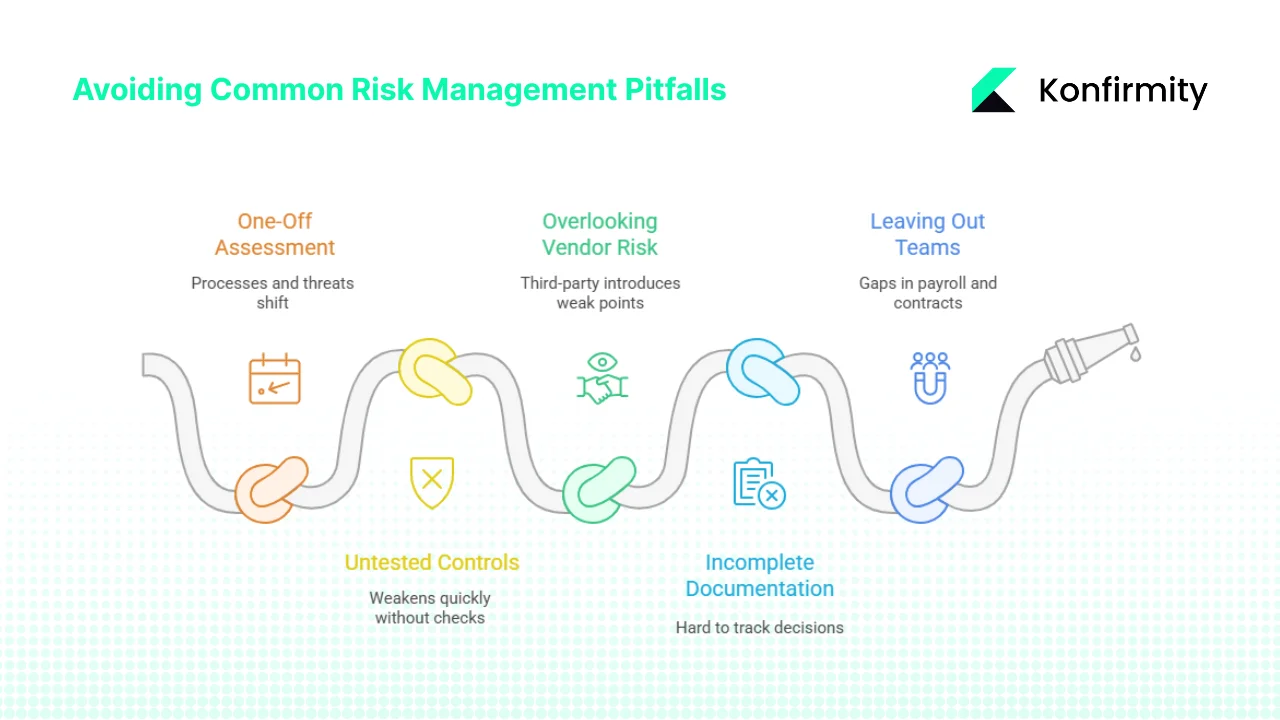
1) Treating risk assessment as a one-off task
Pitfall: Some teams complete a single assessment and treat it as finished. This leaves blind spots as processes, tech, and threats shift over time.
How to avoid it:
- Set a fixed review schedule, such as quarterly or twice a year.
- Keep the assessment active by updating it whenever a major change happens.
- Make someone clearly responsible for tracking review dates.
2) Relying on controls that are never tested
Pitfall: Controls may look solid on paper but weaken fast if no one checks them.
How to avoid it:
- Test controls on a recurring basis.
- Use a simple checklist to track what was tested and when.
- Fix gaps right after you find them, rather than saving them for a later phase.
3) Overlooking vendor risk
Pitfall: A third-party service can introduce weak points if you take it at face value.
How to avoid it:
- Assess vendors before you bring them in.
- Review their security reports, policies, and incident history.
- Repeat this review each year to catch changes in their practices.
4) Keeping incomplete documentation
Pitfall: Missing or scattered records make it hard to track decisions, justify controls, or support audits.
How to avoid it:
- Maintain a single risk register instead of scattered files.
- Add entries whenever you detect a new risk or change an existing one.
- Keep simple fields: description, owner, impact, likelihood, control, and status.
5) Leaving out non-technical teams
Pitfall: Focusing only on engineering or IT leaves gaps in areas like payroll, contracts, or hiring.
How to avoid it:
- Bring finance, HR, legal, and other groups into the discussion.
- Ask each group to identify risks tied to their daily work.
- Hold short cross-team check-ins so nothing gets missed.
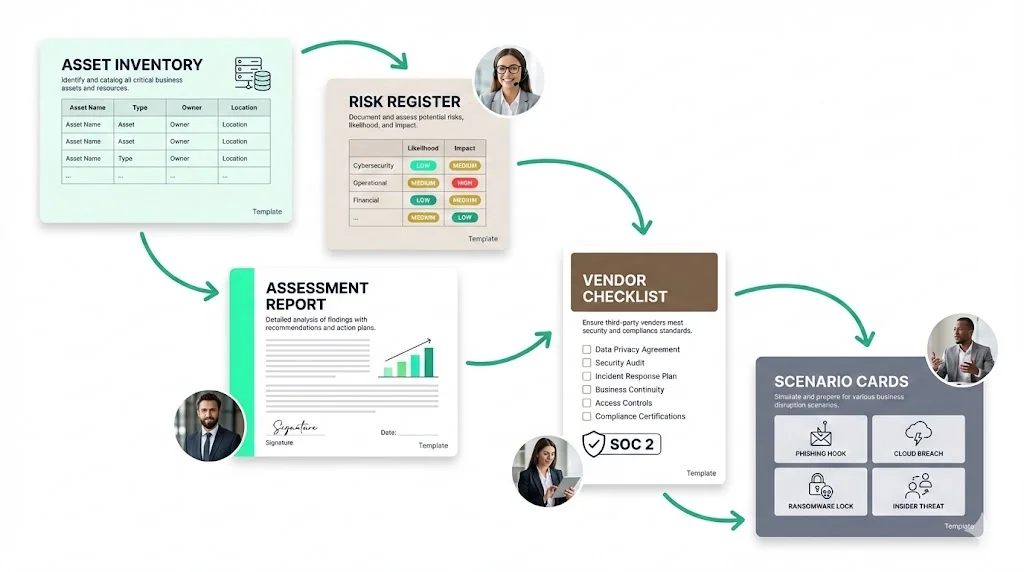
Examples and templates for busy teams
Templates can streamline the work. Below are simplified examples:
Asset inventory – Record each asset’s type, sensitivity, owner and location. For instance, your customer database (high sensitivity) belongs to engineering and is stored in a U.S. data centre, while your HR system (medium sensitivity) is hosted by a cloud provider.
Risk register – Track each risk, its scores, controls and treatment. For example, a phishing risk might score high; existing controls include multi‑factor authentication and training; treatment might involve simulations and stricter filters.
Risk assessment report – Include an executive overview, scope, methodology, findings, control mapping, mitigation plan and leadership sign‑off.
Vendor checklist – List vendors, services, data accessed, their SOC 2 or equivalent status, security documentation, contractual clauses and review dates. Payment processors should provide a SOC 2 report and agree to timely breach notification.
Example scenarios – Credential theft can be mitigated with multi‑factor authentication and awareness training. Vendor data leaks require SOC 2 reports and contract clauses. Ransomware calls for backups and network segmentation. Insider fraud demands access reviews and segregation of duties.
How SOC 2 risk assessment fits into your wider security program
Risk assessment is the heart of a SOC 2 program. It guides policies, incident response, data protection and vendor management. A risk‑based approach, as outlined in the NIST Cybersecurity Framework, helps you prioritise resources and map controls to multiple frameworks. Third‑party assessments ensure vendors meet security requirements. The register also dictates which controls auditors will test. Continuous monitoring, supported by tools and human oversight, keeps evidence current and reduces internal effort.
A good risk register informs your security policy, service level objectives, tooling choices and training programs. Integrating it across frameworks prevents duplication and helps you respond quickly to regulatory changes. At Konfirmity, we build central risk functions that support SOC 2, ISO 27001 and HIPAA, reducing effort while increasing maturity.
Timelines, effort and sales impact
Time to readiness depends on your current maturity. From our 6,000+ audits we’ve seen that self‑managed programs often take nine to twelve months and consume 550–600 hours in discovery, control implementation and evidence collection. A managed approach with experts and automation can reduce the timeline to four or five months and the internal effort to about 75 hours. This difference matters: a timely SOC 2 report accelerates procurement and keeps deals from slipping to the next quarter. Investing in a structured risk assessment and managed program delivers both security improvements and commercial returns.
When and how often to run a SOC 2 risk assessment
Conduct a risk assessment at least annually and after major events such as mergers, new products, significant vulnerabilities or regulatory changes. For Type 1 audits, auditors check design at a point in time. For Type 2 audits they require evidence of ongoing monitoring throughout the audit window. Make the risk register part of your regular compliance cadence by updating it quarterly and reviewing vendors semi‑annually.
Conclusion
SOC 2 risk assessment is the foundation of an effective security program and a necessary prerequisite for a successful audit. The steps outlined here help you identify what matters, weigh each risk, implement controls and maintain evidence. Policy documents alone don’t satisfy buyers; they need proof that controls operate continuously.
At Konfirmity we see that with a dedicated team and automation most organisations reach SOC 2 readiness in four to five months, versus nine to twelve months when they go it alone. Our human‑led managed service supports more than 6,000 audits and draws on over 25 years of combined expertise. We implement controls inside your environment, monitor them daily and help you stay compliant year‑round. Build a program that works under pressure and let compliance follow.
As you build your program, remember that SOC 2 is a continuous endeavour rather than a check‑box exercise. Start with security and arrive at compliance. Engage a partner that works alongside your team to implement controls, monitor them daily and provide guidance. The payoff is enduring trust with enterprise customers and reduced risk of costly incidents.
Frequently asked questions
1) What is the SOC 2 risk assessment requirement?
Under Common Criteria 3, organizations must document how they identify, analyse and treat risks, including fraud and changes. Auditors can issue qualified opinions if this is missing.
2) What are the five criteria for SOC 2?
The five Trust Services Criteria are security, availability, processing integrity, confidentiality and privacy. Security is mandatory; the others are optional based on services and commitments. Each adds additional objectives to your risk assessment.
3) What is a SOC 2 assessment tool?
Assessment tools are software or managed services that automate asset discovery, vulnerability scanning, risk scoring, evidence collection and reporting. They help maintain a live risk register and support continuous monitoring. However, tools alone aren’t enough; you still need experts to interpret results and design controls.
4) What is the SOC 2 compliance checklist?
This SOC 2 Risk Assessment Guide summarises the core tasks: define scope and objectives, build an asset inventory, perform a risk assessment, implement controls mapped to the Trust Services Criteria, document a risk register and policies, conduct continuous monitoring, manage vendor risk, collect evidence over the observation period and prepare for the audit. We deliver this as part of our managed service, saving clients hundreds of hours and ensuring they are always ready for auditor review.





.svg)





.svg)
.svg)