In the current enterprise market, security is no longer just a technical requirement; it is a commercial necessity. Most enterprise buyers now request assurance artifacts before procurement discussions even begin. If you cannot provide a SOC 2 Type II report, you are often disqualified before you can pitch. However, possessing the report is not enough. Sophisticated buyers and rigorous auditors demand proof that your security controls function continuously, not just during a two-week observation window. This is where Security Information and Event Management (SIEM) becomes the backbone of your compliance program.
For many organizations, SIEM is a misunderstood acronym. It is often viewed as a noisy, expensive repository for logs that no one reads. In reality, a properly tuned SIEM is the primary engine for demonstrating the "Operating Effectiveness" of your controls. It collects and correlates security events across your systems to detect threats and, crucially for compliance, generates the hard evidence auditors require. With the average cost of a data breach in the U.S. reaching an all-time high of $10.22 million in 2025, and security automation saving organizations an average of $1.9 million per breach, the financial case for a robust SIEM is as strong as the compliance case.
The purpose of this article is to detail how SIEM Use Cases For SOC 2 help organizations meet Trust Services Criteria and operationalize security controls. We will move beyond theory into the practical application of log management for audit readiness. At Konfirmity, having supported over 6,000 audits across 25 years of combined experience, we know that security which looks good on paper but fails under scrutiny is a liability. We advocate for a human-led, outcome-driven approach: build the controls once, operate them daily, and allow compliance to follow naturally.
What is SIEM?
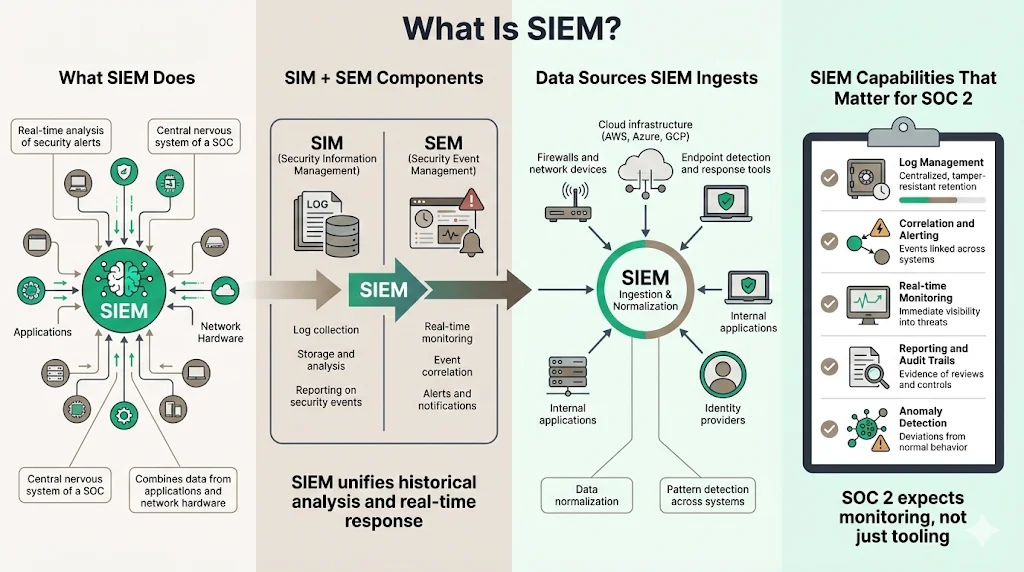
At its core, Security Information and Event Management (SIEM) provides real-time analysis of security alerts generated by applications and network hardware. It is the central nervous system of a Security Operations Center (SOC).
SIEM combines two functions:
- SIM (Security Information Management): collecting data from log files for analysis and reporting on security threats and events.
- SEM (Security Event Management): real-time monitoring, correlation of events, and notification.
In the context of modern security operations, SIEM acts as the aggregator. It ingests data from your firewalls, cloud infrastructure (AWS, Azure, GCP), endpoint protection platforms (EDR), identity providers (Okta, Azure AD), and internal applications. It then normalizes this data into a standard format and applies logic to detect patterns that indicate a threat.
Key Capabilities That Matter to SOC 2
For a SOC 2 audit, you are not just proving you have a firewall; you are proving you monitor it. The following SIEM capabilities are vital:
- Log Management: Centralized retention of logs to prevent tampering and ensure availability for forensics.
- Correlation and Alerting: Connecting a login attempt on one server with a file download on another to identify a breach.
- Real-time Monitoring: Immediate visibility into the security posture of the organization.
- Reporting and Audit Trails: Automated generation of evidence showing that reviews and checks occurred.
- Anomaly Detection: Identifying deviations from established baselines, such as a user logging in from an unfamiliar country.
SOC 2 Basics & SIEM’s Role in Compliance
SOC 2 (System and Organization Controls 2) is an auditing procedure developed by the American Institute of Certified Public Accountants (AICPA). It ensures your service providers manage your data to protect the interests of your organization and the privacy of its clients.
Unlike a checklist certification, SOC 2 Type II tests the operating effectiveness of your controls over a period (typically 6–12 months).
Relevant Trust Services Criteria
SIEM directly supports several Trust Services Criteria (TSC):
- Security (Common Criteria): This is mandatory. It requires systems to be protected against unauthorized access. SIEM fulfills controls related to intrusion detection, access monitoring, and incident response.
- Availability: Controls to ensure systems are available for operation and use. SIEM monitors system uptime logs and performance metrics.
- Confidentiality: Information designated as confidential is protected. SIEM tracks access to sensitive data repositories to ensure only authorized personnel view specific files.
- Processing Integrity & Privacy (Optional): While less common for early-stage SaaS, SIEM helps here by tracking data processing errors or consent management logs.
Why SIEM is Essential
Without a SIEM, achieving the required level of continuous monitoring is nearly impossible. Auditors will ask for a population of alerts generated during the audit period. If you rely on manual checks, you will likely fail to provide complete evidence.
SIEM Use Cases For SOC 2 drive audit readiness by:
- Supporting Continuous Monitoring: Automating the "watch" function over your infrastructure 24/7/365.
- Driving Documentation: Every alert creates a ticket; every ticket creates an audit trail.
- Improving Incident Detection and Response: SOC 2 Control CC7.3 specifically requires entities to evaluate security events to determine if they are incidents. SIEM is the tool that performs this evaluation.
How to Structure SIEM Use Cases for SOC 2
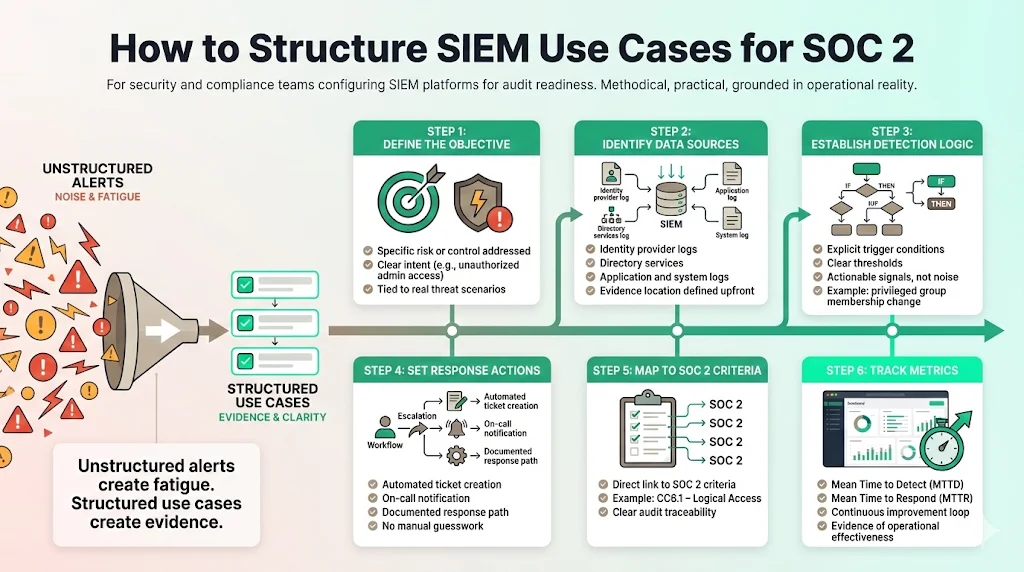
Before implementing specific rules, you must have a framework. Randomly turning on alerts leads to "alert fatigue"—a state where teams ignore warnings because there are simply too many false positives. At Konfirmity, we see this frequently: companies purchase expensive tools like Splunk or Datadog but fail to configure them for their specific risk profile.
To build effective SIEM Use Cases For SOC 2, follow this structure for every rule:
- Define Objective: What risk or SOC 2 control does this address? (e.g., "Detect unauthorized administrative access").
- Identify Data Sources: Where does the evidence live? (e.g., Active Directory logs, Okta system logs).
- Establish Detection Logic: What constitutes a trigger? (e.g., "User added to Domain Admins group").
- Set Response Actions: What happens next? (e.g., "Create P1 ticket in Jira, page on-call engineer").
- Map to SOC 2 Criteria: Link it to the specific control (e.g., CC6.1 - Logical Access).
- Track Metrics: Measure Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR).
This structured approach transforms raw data into a defensible compliance posture.
Core SIEM Use Cases For SOC 2
Below are the essential use cases we implement for clients. These cover the majority of the Security Trust Services Criteria requirements regarding monitoring and anomaly detection.
A. Security Monitoring
Goal: Continual tracking of security events across the production environment. Data Sources: Firewalls (WAF), Endpoint Detection (EDR), Cloud Infrastructure (AWS/GCP/Azure). Detection Approach: Signature-based and threshold-based. Example: A dashboard displaying real-time blocks from the Web Application Firewall (WAF) and malware blocks from endpoint agents. SOC 2 Mapping: CC7.2 - The entity monitors system components and the operation of those components for anomalies that are indicative of malicious acts, natural disasters, and errors.
B. Log Management & Correlation
Goal: Centralize and protect logs from modification while correlating events across disparate systems. Data Sources: Operating systems, applications, network devices. Detection Approach: Normalization of timestamps and user IDs to create a unified timeline. Example: Correlating a VPN login from an unusual IP address with a subsequent distinct database access attempt. SOC 2 Mapping: CC7.1 - Detection and monitoring procedures are implemented to identify (1) changes to configurations that result in the introduction of new vulnerabilities, and (2) susceptibilities to newly discovered vulnerabilities.
C. Incident Detection & Alerting
Goal: Detect unauthorized access attempts and policy violations immediately. Data Sources: Authentication logs (Okta, AD), Server logs (/var/log/auth.log, Windows Event Logs). Detection Approach: Threshold violations. Example: Detecting a brute-force attack (e.g., 10 failed login attempts in 1 minute followed by a successful login). SOC 2 Mapping: CC7.3 - The entity evaluates security events to determine whether they could or have resulted in a failure of the entity to meet its objectives (security incidents).
D. Threat Detection (including Anomaly Detection)
Goal: Use behavioral models to find hidden threats that bypass standard rules. Data Sources: Network traffic flows (VPC Flow Logs), User behavior analytics. Detection Approach: Statistical deviation from a baseline. Example: A developer account suddenly downloading 5GB of data from a sensitive S3 bucket at 3 AM on a Sunday. SOC 2 Mapping: CC6.8 - Unauthorized or malicious software is prevented or detected.
E. User Activity Tracking
Goal: Monitor privileged accounts and high-risk behaviors to prevent insider threats. Data Sources: Identity Provider logs, Bastion host logs. Detection Approach: Whitelist/Blacklist monitoring. Example: Flagging any access to production databases by a user who is not in the "DBA" group, or access occurring outside of an approved change window. SOC 2 Mapping: CC6.1 - The entity implements logical access security software, infrastructure, and architectures over protected information assets to protect them from security events to the extent it meets the entity’s objectives.
F. Vulnerability Assessment Integration
Goal: Tie SIEM to vulnerability scanners to prioritize alerts based on asset risk. Data Sources: Scanners (Tenable, Qualys, Inspector). Detection Approach: API ingestion and severity tagging. Example: An alert triggers when an exploit attempt matches a known vulnerability (CVE) present on the target server. SOC 2 Mapping: CC7.1 - To identify configuration changes and new vulnerabilities.
G. Compliance Reporting & Audit Trails
Goal: Auto-generate reports to show controls are active and effective over time. Data Sources: SIEM system logs (internal audit). Detection Approach: Scheduled reporting. Example: A weekly report showing all changes to firewall rules, reviewed and signed off by the Security Officer. SOC 2 Mapping: CC2.2 - The entity communicates information to improve security knowledge and awareness. (Also supports the general requirement for evidence of review).
H. Risk Management Support
Goal: Aggregate signals to assess overall risk posture for leadership. Data Sources: All integrated feeds. Detection Approach: Aggregation and scoring. Example: A "Risk Score" dashboard that drops when patching is delayed or incident volume spikes, used for quarterly management reviews. SOC 2 Mapping: CC3.2 - The entity identifies risks to the achievement of its objectives across the entity.
Step-by-Step Examples (Practical Guides)
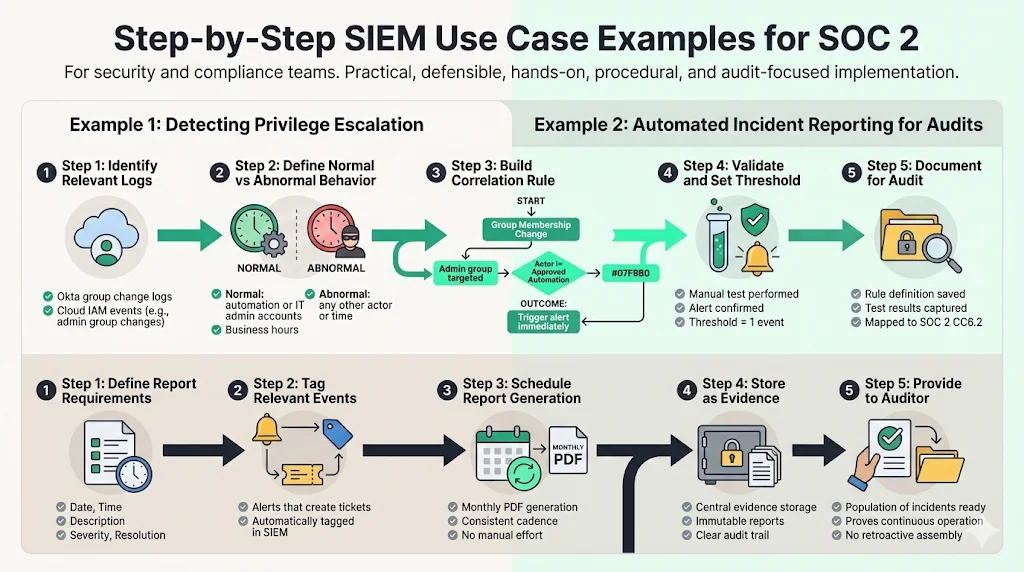
To demonstrate how SIEM Use Cases For SOC 2 work in the field, let us look at two practical implementations.
Example 1: Detecting Privilege Escalation
Privilege escalation is a precursor to many major breaches. An attacker gains low-level access and tries to grant themselves admin rights.
- Identify Relevant Logs: Focus on Identity Provider logs (e.g., Okta "Add User to Group") or Cloud IAM logs (AWS CloudTrail AddUserToGroup).
- Define Patterns: Normal behavior involves a specific automation account or IT Manager account making these changes during business hours. Abnormal behavior is any other account doing this.
- Build Correlation Rule:
- Logic: IF Event = "Group Membership Change" AND Group = "Admins" AND Actor != "IT_Automation_Bot" THEN Trigger Alert.
- Validate: Test by having a designated engineer manually add a user to the admin group. Ensure the alert fires.
- Set Thresholds: For this specific risk, the threshold should be 1. Any occurrence is worth investigating.
- Document: Save the rule definition and the test results. This is your evidence for Control CC6.2 (manage access).
Example 2: Automated Incident Report for SOC 2 Audit
Auditors will ask for a list of all incidents during the audit period. Scrambling to compile this from emails is a recipe for failure.
- Define Requirements: The report must show Date, Time, Description, Severity, and Resolution.
- Pull Log Sets: Configure the SIEM to tag any alert that resulted in a "Ticket Creation" action.
- Schedule Report: Set the SIEM to generate a PDF summary of these tagged events on the first of every month.
- Export and Tag: Store these reports in a "Compliance Evidence" folder (or let a managed service like Konfirmity handle the repository).
- Attach to Evidence: When the auditor asks for "Population of Incidents," you provide the folder of generated PDFs. This proves the process was continuous, not fabricated retroactively.
Best Practices for SIEM Use Cases in SOC 2
Implementing a SIEM is not a "set it and forget it" task. It requires operational discipline.
- Prioritize Data Sources: Start with the sources that align with your highest risks. For most modern enterprises, this means your Identity Provider (Okta/Google Workspace), your Cloud Provider (AWS/Azure), and your Endpoint controls (CrowdStrike/SentinelOne).
- Tune Alerts to Reduce Noise: Alert fatigue is the enemy of security. If your team receives 500 alerts a day, they will investigate zero. We recommend a "tuning phase" of 2–4 weeks where rules run in "silent mode" to gauge volume before going live.
- Use Behavior Analytics: Static rules fail against dynamic threats. Utilize User and Entity Behavior Analytics (UEBA) where possible. If a marketing manager accesses the production database, that is an anomaly regardless of the time of day.
- Maintain Retention Policies: SOC 2 typically looks back 12 months. Ensure your SIEM storage (or cold storage archive) retains logs for at least one year. While the audit period might be six months, having a full year of data supports year-over-year analysis and broader investigations.
- Review and Update Use Cases: Technology changes. If you migrate from Jenkins to GitHub Actions, your CI/CD monitoring rules must change. Review your use cases quarterly.
Challenges & How to Overcome Them
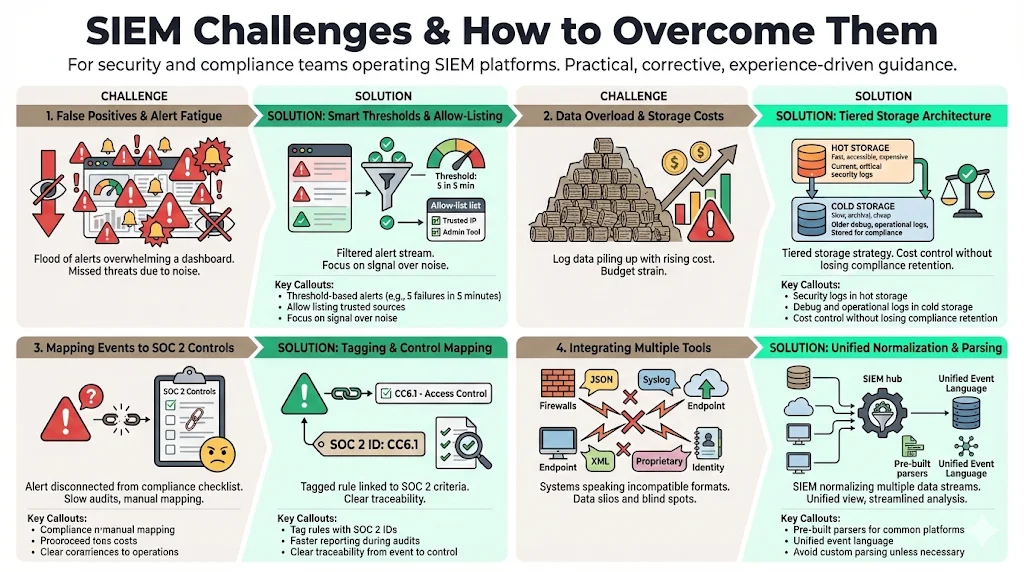
1) False Positives and Alert Fatigue
- Challenge: The SIEM flags every failed login, including users who simply mistyped their password.
- Solution: Implement "thresholding." Only alert after 5 failed attempts in 5 minutes. Use "allow listing" for known scanners or safe internal IPs (with caution).
2) Data Overload and Storage Costs
- Challenge: In 2025, cloud log volume is expensive. Ingesting every debug log can bankrupt the security budget.
- Solution: Be selective. Ingest security-relevant logs into hot storage for analysis. Send debug/operational logs to cheaper cold storage (like Amazon S3 Glacier) for retention compliance without the analysis cost.
3) Mapping Security Events to Compliance Controls
- Challenge: Translating a "Port 22 Open" alert to a SOC 2 requirement.
- Solution: Use a tagging schema. Tag rules with "CC6.6" or "CC7.2" directly in the SIEM logic. This makes reporting efficient during the audit.
4) Integrating Multiple Tools
- Challenge: Your firewall speaks one language; your cloud provider speaks another.
- Solution: This is the primary function of the SIEM. Ensure you select a SIEM with pre-built parsers for your specific tech stack. Avoid custom parsing unless necessary, as it incurs high maintenance debt.
Conclusion
Implementing robust SIEM Use Cases For SOC 2 is not merely about checking a box for an auditor. It is about proving to your enterprise clients that you are a responsible custodian of their data. The difference between a company that scrambles for two weeks before an audit and one that operates continuously is visible in the sales cycle. Buyers trust partners who can demonstrate operational maturity.
At Konfirmity, we believe in an outcome-as-a-service model. We don't just advise you on what rules to write; we help implement the controls, monitor the output, and ensure the evidence is ready when the auditor arrives. A self-managed SOC 2 preparation can take 9–12 months and consume 550–600 internal hours. With a managed approach, readiness is often achieved in 4–5 months with significantly less internal friction.
Security that exists only in policy documents is a risk waiting to materialize. Build the program once, operate it daily, and let compliance be the natural result of good security.
FAQ Section
Q1: How does SIEM support SOC 2 compliance?
SIEM supports compliance by centralizing logs, detecting potential threats in real-time, generating required incident reports, and providing immutable audit trails that align directly with SOC 2 Trust Services Criteria.
Q2: What data sources should be included in SIEM for SOC 2?
You should include logs from network devices (firewalls), servers, identity and access management systems (IdP), endpoints (laptops/workstations), cloud infrastructure services, and critical applications holding customer data.
Q3: How do you map SIEM alerts to SOC 2 controls?
Start by defining the control objective (e.g., "Prevent unauthorized access"). Then, design your detection rules to spot violations of that objective. Finally, tag the alert rule with the specific Control ID (e.g., CC6.1) to streamline evidence gathering.
Q4: What’s a common mistake when building SIEM use cases?
The most common mistake is turning on all default rules, creating a flood of noisy alerts that lack business context. This leads to alert fatigue, where genuine threats are missed because the team is overwhelmed by irrelevant data.





.svg)




.svg)
.svg)